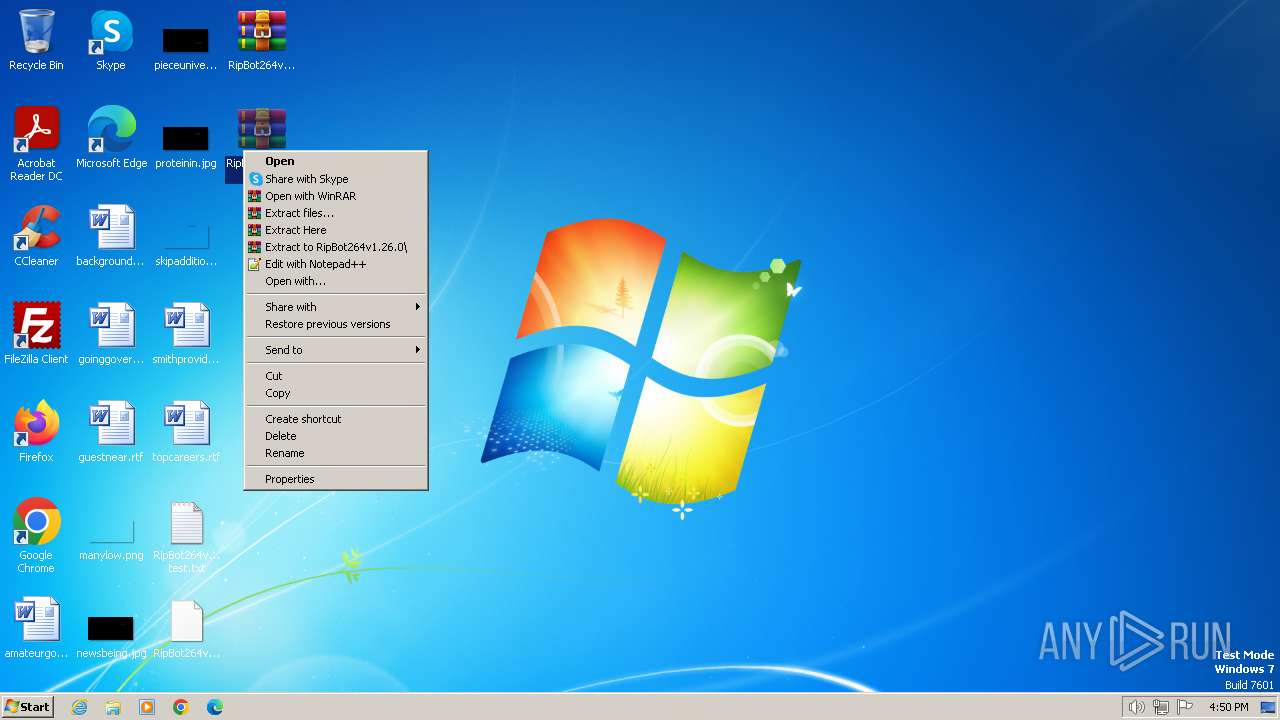
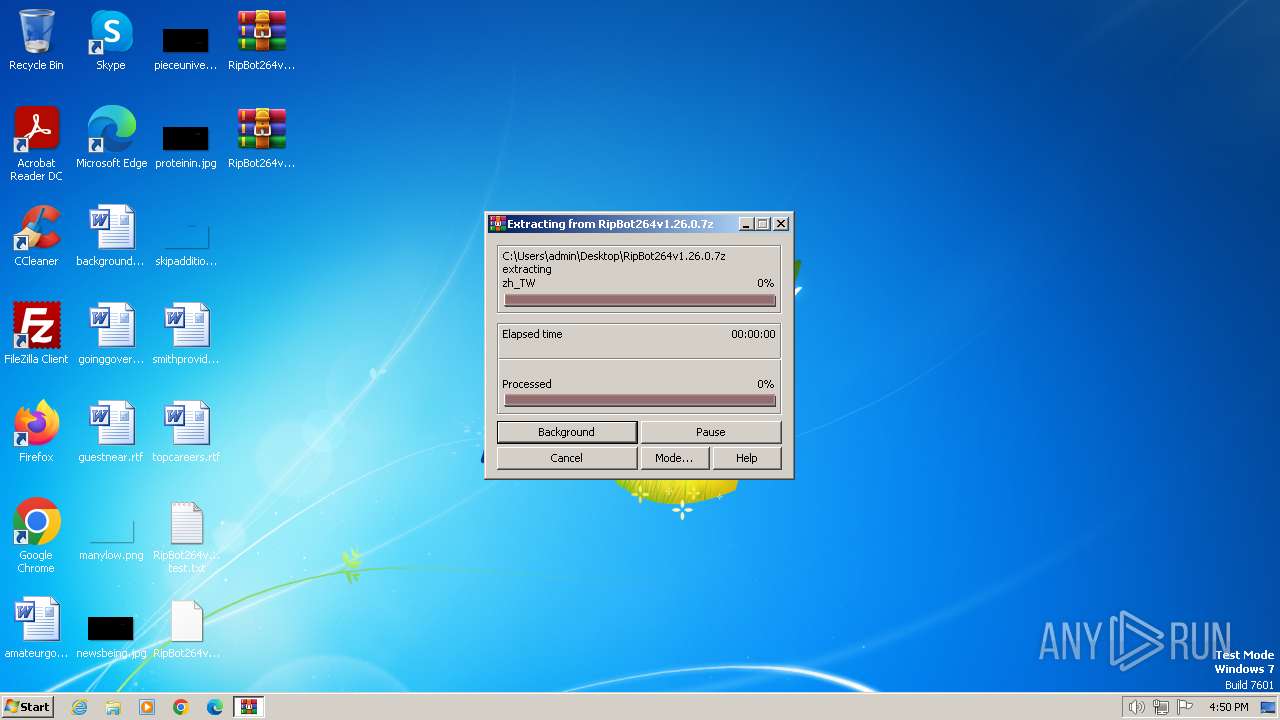
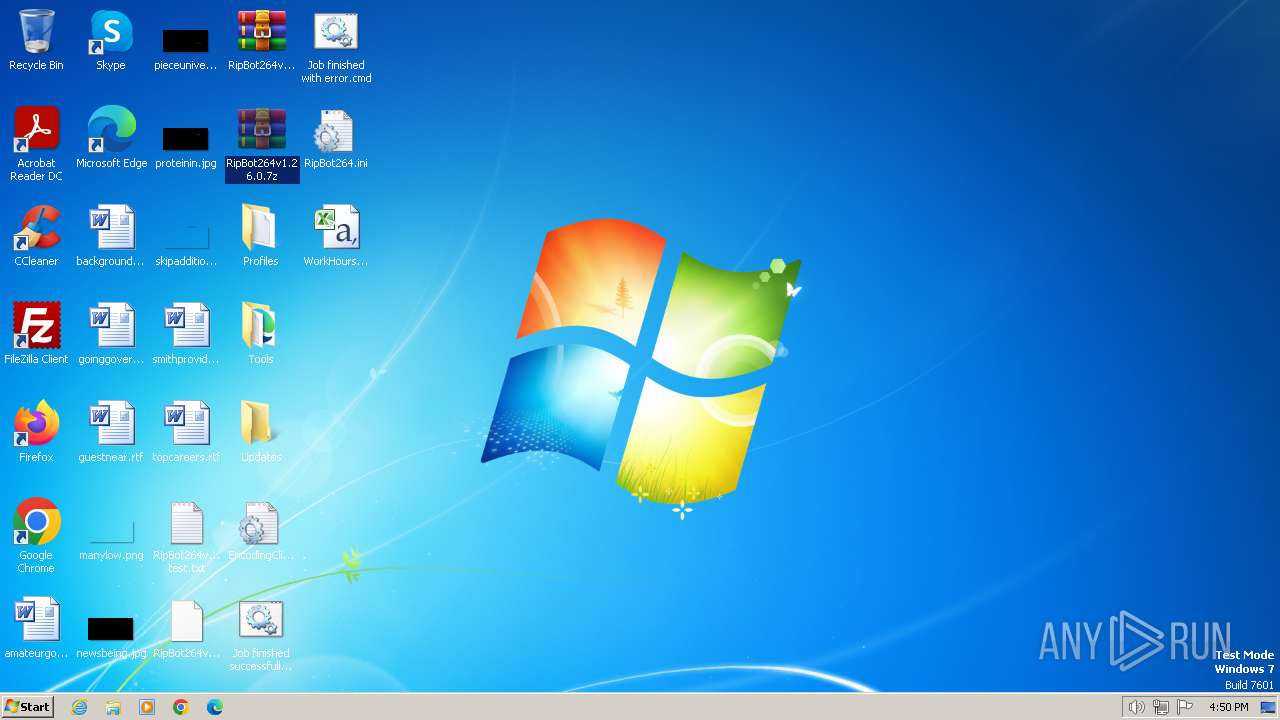
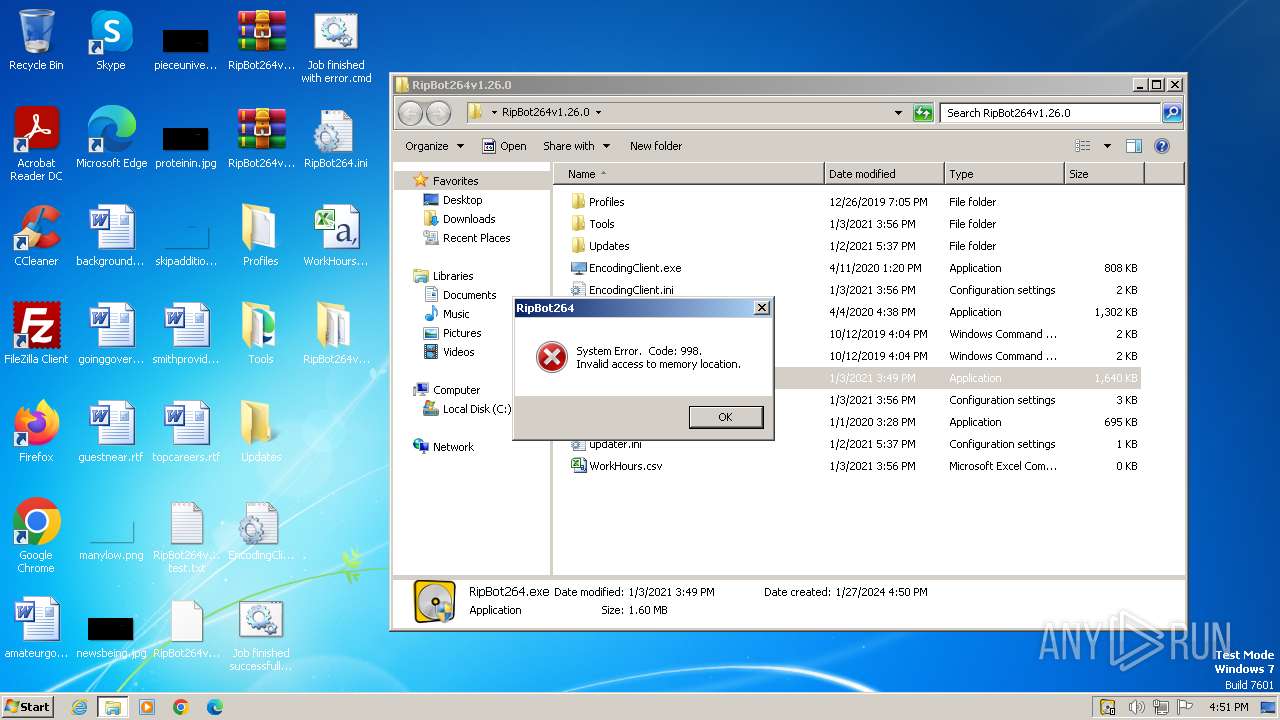
| File name: | RipBot264v1.26.0 test.txt |
| Full analysis: | https://app.any.run/tasks/a14a392f-afe9-409d-9058-f6962a3c878c |
| Verdict: | Malicious activity |
| Analysis date: | January 27, 2024, 16:49:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 2693F68FEA5B9CD86DF884FABB12523C |
| SHA1: | A6B46668EBC7DDA8E975D800B26C179351D7A532 |
| SHA256: | DFACD08D2362DDD17D97B2ED05448822462C636C72A99C5688FC27EA1DEA7E47 |
| SSDEEP: | 3:EKxTOBs:EMTr |
MALICIOUS
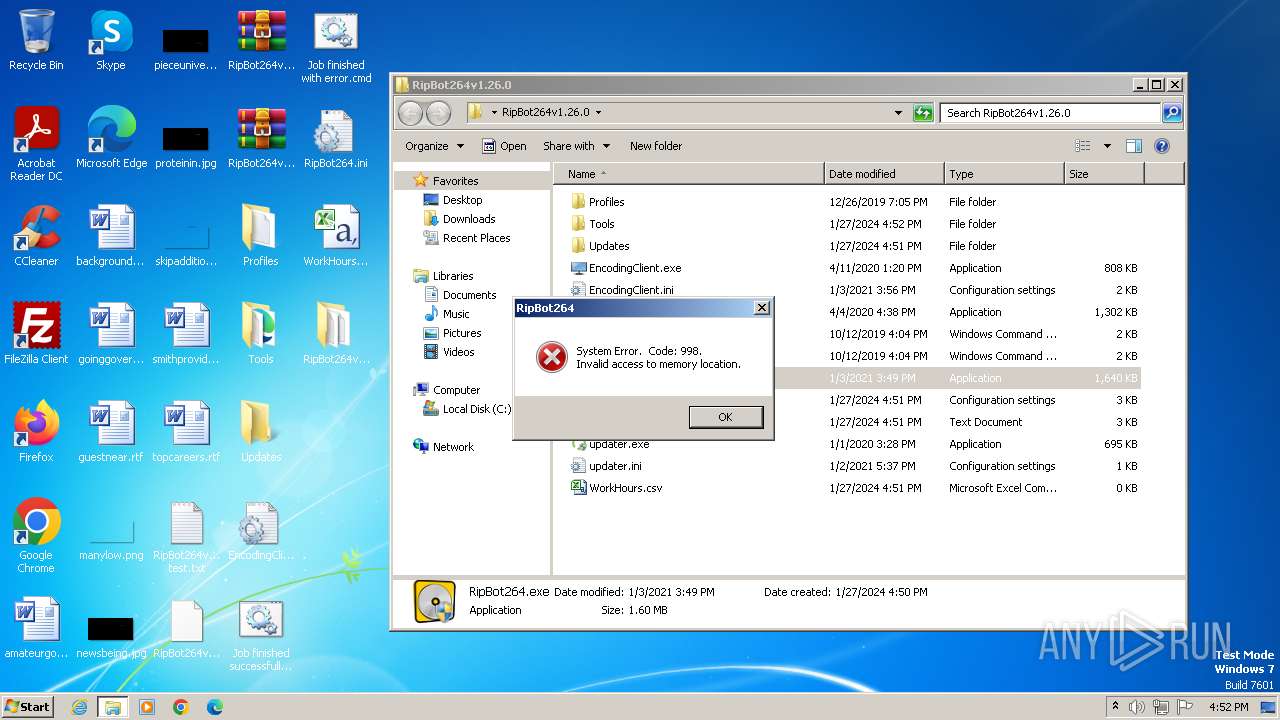
Registers / Runs the DLL via REGSVR32.EXE
- RipBot264.exe (PID: 3320)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3400)
The process checks if it is being run in the virtual environment
- WinRAR.exe (PID: 3400)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3400)
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 3400)
Reads the Internet Settings
- updater.exe (PID: 3604)
- RipBot264.exe (PID: 3320)
- updater.exe (PID: 3640)
- RipBot264.exe (PID: 3092)
Executable content was dropped or overwritten
- xcopy.exe (PID: 3644)
Reads Internet Explorer settings
- RipBot264.exe (PID: 3320)
- RipBot264.exe (PID: 3092)
Reads Microsoft Outlook installation path
- RipBot264.exe (PID: 3320)
- RipBot264.exe (PID: 3092)
INFO
Manual execution by a user
- WinRAR.exe (PID: 2688)
- WinRAR.exe (PID: 2240)
- WinRAR.exe (PID: 3400)
- RipBot264.exe (PID: 3416)
- RipBot264.exe (PID: 3584)
- RipBot264.exe (PID: 3960)
- RipBot264.exe (PID: 3092)
- msedge.exe (PID: 984)
- updater.exe (PID: 1376)
- updater.exe (PID: 1628)
- EncodingClient.exe (PID: 3892)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3400)
- WinRAR.exe (PID: 2688)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2688)
- xcopy.exe (PID: 3644)
- WinRAR.exe (PID: 3400)
Checks supported languages
- RipBot264.exe (PID: 3584)
- updater.exe (PID: 3604)
- RipBot264.exe (PID: 3320)
- updater.exe (PID: 3640)
- RipBot264.exe (PID: 3092)
- updater.exe (PID: 1628)
- EncodingClient.exe (PID: 3892)
Reads the computer name
- updater.exe (PID: 3604)
- RipBot264.exe (PID: 3320)
- updater.exe (PID: 3640)
- RipBot264.exe (PID: 3092)
- EncodingClient.exe (PID: 3892)
Creates files in the program directory
- RipBot264.exe (PID: 3320)
- xcopy.exe (PID: 3644)
Checks proxy server information
- updater.exe (PID: 3640)
- RipBot264.exe (PID: 3320)
- RipBot264.exe (PID: 3092)
Reads the machine GUID from the registry
- updater.exe (PID: 3640)
- RipBot264.exe (PID: 3320)
- RipBot264.exe (PID: 3092)
Creates files or folders in the user directory
- updater.exe (PID: 3640)
- RipBot264.exe (PID: 3320)
- RipBot264.exe (PID: 3092)
Create files in a temporary directory
- updater.exe (PID: 3640)
Application launched itself
- msedge.exe (PID: 1796)
- msedge.exe (PID: 984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
100
Monitored processes
38
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
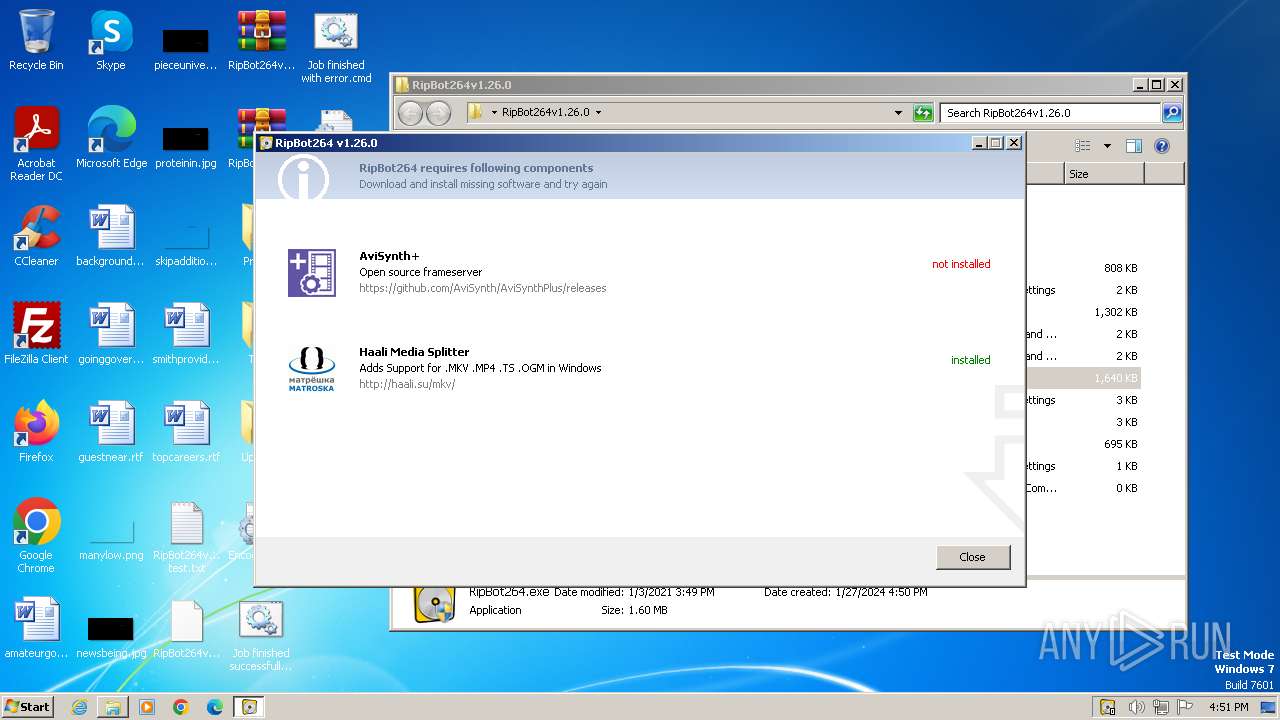
| 984 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --flag-switches-end --do-not-de-elevate https://github.com/AviSynth/AviSynthPlus/releases | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
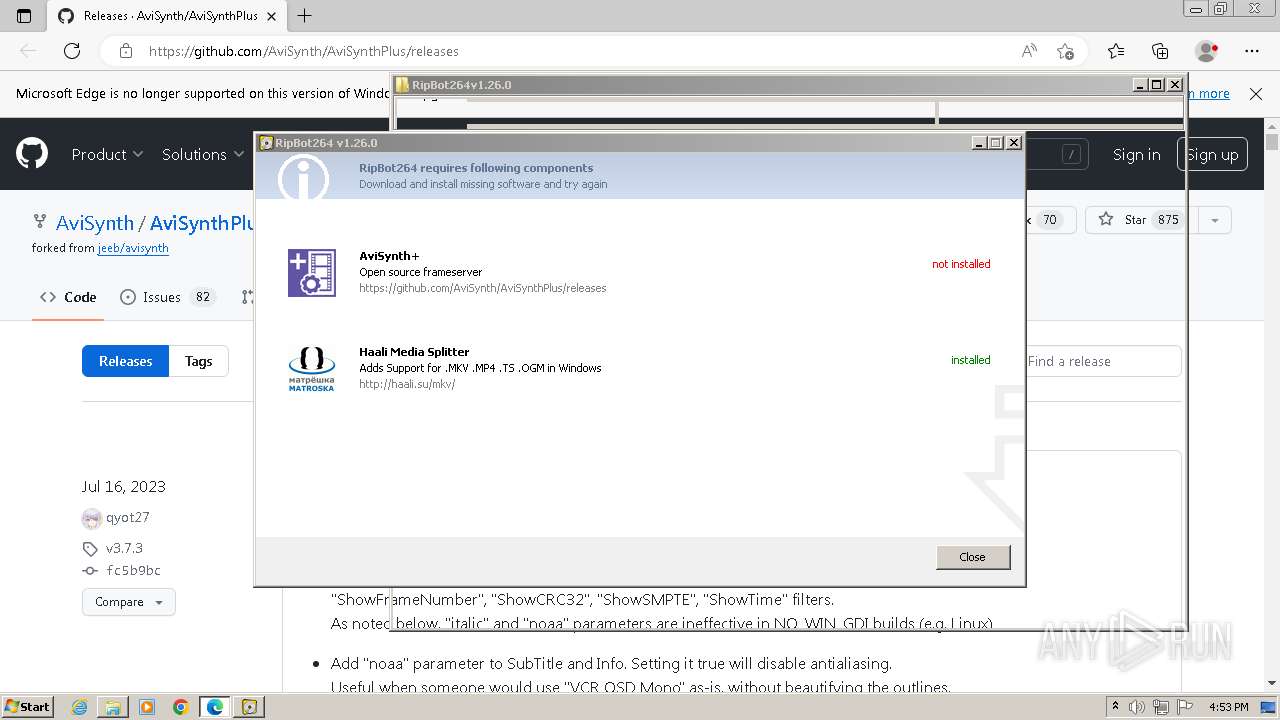
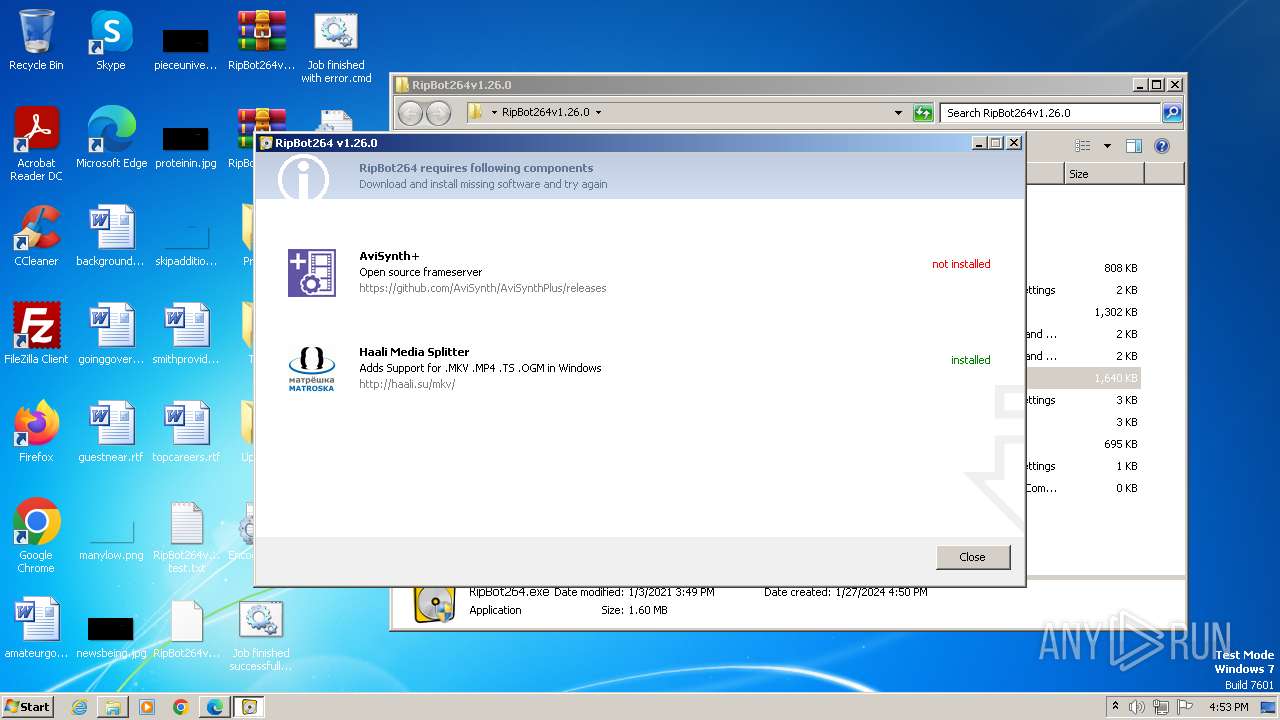
| 1376 | "C:\Users\admin\Desktop\RipBot264v1.26.0\updater.exe" | C:\Users\admin\Desktop\RipBot264v1.26.0\updater.exe | — | explorer.exe | |||||||||||
User: admin Company: Atak_Snajpera Integrity Level: MEDIUM Description: RipBot264 Updater Exit code: 3221226540 Version: 1.0.4.0 Modules
| |||||||||||||||
| 1484 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1536 --field-trial-handle=1316,i,11781941647065765224,1368217849909603784,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1192 --field-trial-handle=1316,i,11781941647065765224,1368217849909603784,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6411f598,0x6411f5a8,0x6411f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1628 | "C:\Users\admin\Desktop\RipBot264v1.26.0\updater.exe" | C:\Users\admin\Desktop\RipBot264v1.26.0\updater.exe | explorer.exe | ||||||||||||
User: admin Company: Atak_Snajpera Integrity Level: HIGH Description: RipBot264 Updater Exit code: 0 Version: 1.0.4.0 Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3808 --field-trial-handle=1316,i,11781941647065765224,1368217849909603784,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1796 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://github.com/AviSynth/AviSynthPlus/releases | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | RipBot264.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1904 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6411f598,0x6411f5a8,0x6411f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1936 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\RipBot264v1.26.0 test.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
30 268
Read events
30 155
Write events
112
Delete events
1
Modification events
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
254
Suspicious files
183
Text files
1 037
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2240 | WinRAR.exe | C:\Users\admin\Desktop\RipBot264v1.26.0.7z | — | |
MD5:— | SHA256:— | |||
| 2688 | WinRAR.exe | C:\Users\admin\Desktop\Job finished successfully.cmd | text | |
MD5:091B30800E48407A763D389EDE02F085 | SHA256:CEBE82A50548E79D5CB923462ABDA566BC0E45B0B4AA9575927F790A2D1F1D68 | |||
| 2688 | WinRAR.exe | C:\Users\admin\Desktop\Profiles\avc\[BASE 1.3] Simple Mobile Device.txt | text | |
MD5:E7D89A8924AE52E9A0831F2982651C75 | SHA256:D639660F35C33EFE2C106080157A285AC220362DF0154DCD327687FB115E66FF | |||
| 2688 | WinRAR.exe | C:\Users\admin\Desktop\Profiles\avc\[BASE 3.0] iPOD Classic . Zune.txt | text | |
MD5:84C151F069EFA6118C6D3CC44CC2C016 | SHA256:CA3BC4EA5D348019589499D2E2D625CC277044F1766CA30E1F9860F4FBE26490 | |||
| 2688 | WinRAR.exe | C:\Users\admin\Desktop\Profiles\avc\[HIGH 4.0] FHD . Interlaced.txt | text | |
MD5:271FCF7CFECEED9B5B21671DF678B424 | SHA256:14BB20FCD460B8A45632DA31109E078799C560BA033F58F4C50F0FED72101A7C | |||
| 2688 | WinRAR.exe | C:\Users\admin\Desktop\Profiles\Audio.txt | text | |
MD5:F4293DD96D5E7FF5954B587E8C16A119 | SHA256:5A0D739043E9929D82CC33E94C729BE18CF561DE9552592D99E0FFA17E1DBB98 | |||
| 2688 | WinRAR.exe | C:\Users\admin\Desktop\Profiles\avc\[HIGH 4.0] FHD . Progressive.txt | text | |
MD5:2FC5D4EBF55A81E67A988E0BD5137091 | SHA256:44880A8340C58A91286362E5F2B2CA799B8C0462DE78EB00D0EAFD8031F9543A | |||
| 2688 | WinRAR.exe | C:\Users\admin\Desktop\Profiles\hevc\[MA10 x.x] 10bit . Progressive.txt | text | |
MD5:4EA7EABE590DDE8E7BDAE00E0BEC1253 | SHA256:0855223ED0B47B15CBDFC5650FF8CB9FE2A489D0A00D20448901FC95BE4CF8A8 | |||
| 2688 | WinRAR.exe | C:\Users\admin\Desktop\Profiles\avc\[MAIN 3.1] HD . iPAD . iPhone.txt | text | |
MD5:BE5356C9692851D0086548715CA5F3AC | SHA256:4C58C893001646E5AA1B08F60A6DD03AC53F0FC865A2E49F076F957B45EE2BC3 | |||
| 2688 | WinRAR.exe | C:\Users\admin\Desktop\Profiles\hevc\[MAIN x.x] 8bit . Progressive.txt | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
31
DNS requests
36
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3640 | updater.exe | GET | 200 | 213.112.19.103:80 | http://forum.doom9.org/showthread.php?t=127611 | unknown | html | 18.6 Kb | unknown |
3640 | updater.exe | GET | 200 | 37.187.156.46:80 | http://atak-snajpera.5v.pl/ripbot264update/update.zip | unknown | compressed | 2.64 Kb | unknown |
3640 | updater.exe | GET | 200 | 37.187.156.46:80 | http://atak-snajpera.5v.pl/ripbot264update/core.zip | unknown | compressed | 3.32 Mb | unknown |
3640 | updater.exe | GET | 200 | 37.187.156.46:80 | http://atak-snajpera.5v.pl/ripbot264update/downloadposter.zip | unknown | compressed | 2.63 Mb | unknown |
3640 | updater.exe | GET | 200 | 37.187.156.46:80 | http://atak-snajpera.5v.pl/ripbot264update/ffmpeg.zip | unknown | compressed | 145 Mb | unknown |
3320 | RipBot264.exe | GET | 200 | 37.187.156.46:80 | http://atak-snajpera.5v.pl/ripbot264update/changelog.zip?fakevariable=2.3283064365387E-10 | unknown | html | 58.8 Kb | unknown |
3092 | RipBot264.exe | GET | 200 | 37.187.156.46:80 | http://atak-snajpera.5v.pl/ripbot264update/changelog.zip?fakevariable=2.3283064365387E-10 | unknown | html | 58.8 Kb | unknown |
3640 | updater.exe | GET | 200 | 37.187.156.46:80 | http://atak-snajpera.5v.pl/ripbot264update/mediainfo.zip | unknown | compressed | 3.01 Mb | unknown |
3640 | updater.exe | GET | 200 | 37.187.156.46:80 | http://atak-snajpera.5v.pl/ripbot264update/mkvtoolnix.zip | unknown | compressed | 63.7 Mb | unknown |
3640 | updater.exe | GET | 200 | 37.187.156.46:80 | http://atak-snajpera.5v.pl/ripbot264update/modifychapters.zip | unknown | compressed | 205 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3640 | updater.exe | 213.112.19.103:80 | forum.doom9.org | Telenor Norge AS | SE | unknown |
3640 | updater.exe | 37.187.156.46:80 | atak-snajpera.5v.pl | OVH SAS | FR | unknown |
3320 | RipBot264.exe | 37.187.156.46:80 | atak-snajpera.5v.pl | OVH SAS | FR | unknown |
3092 | RipBot264.exe | 37.187.156.46:80 | atak-snajpera.5v.pl | OVH SAS | FR | unknown |
2452 | msedge.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
2452 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2452 | msedge.exe | 20.166.151.106:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
forum.doom9.org |
| unknown |
atak-snajpera.5v.pl |
| unknown |
github.com |
| shared |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
data-edge.smartscreen.microsoft.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3640 | updater.exe | Attempted Administrator Privilege Gain | AV EXPLOIT Potential ZIP file exploiting CVE-2023-36413 |