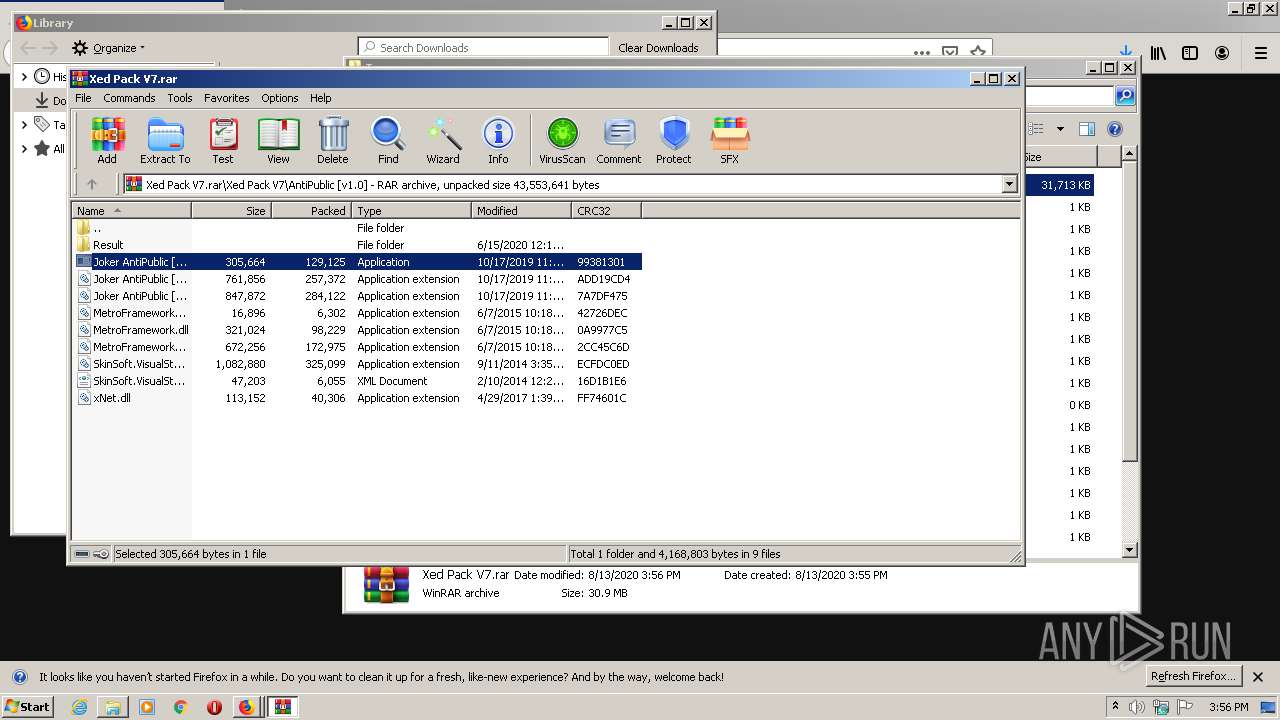
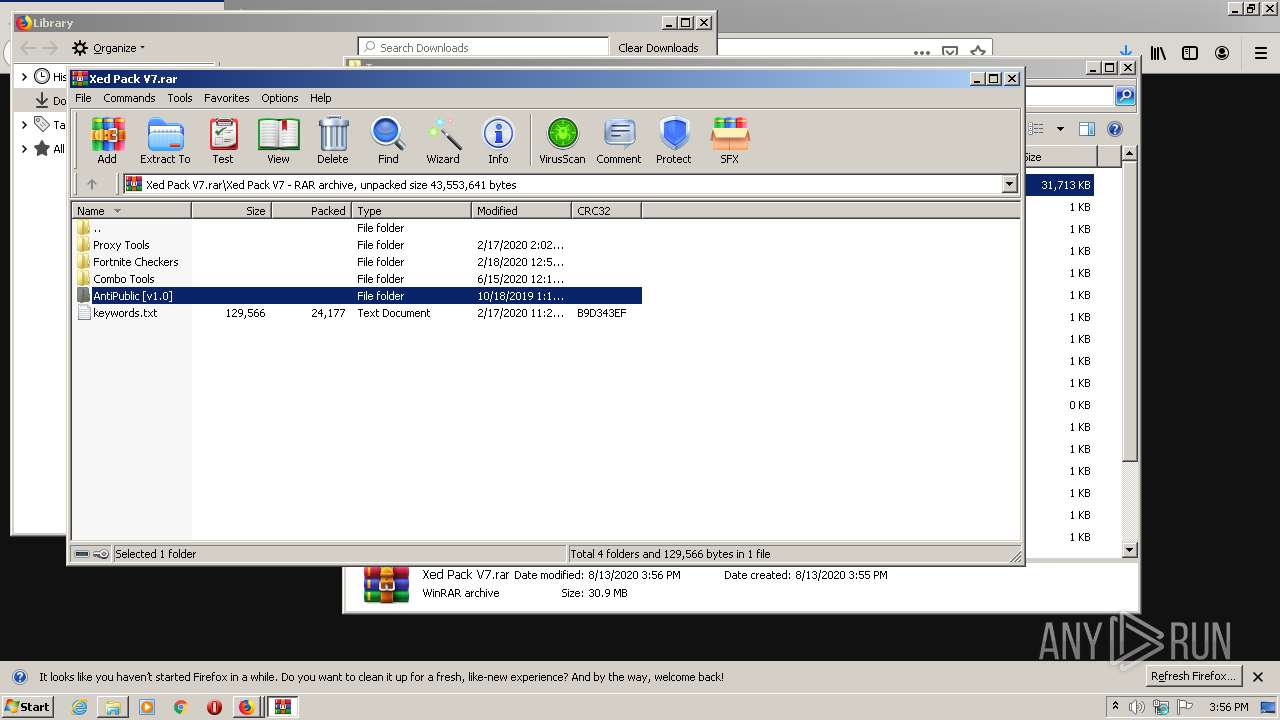
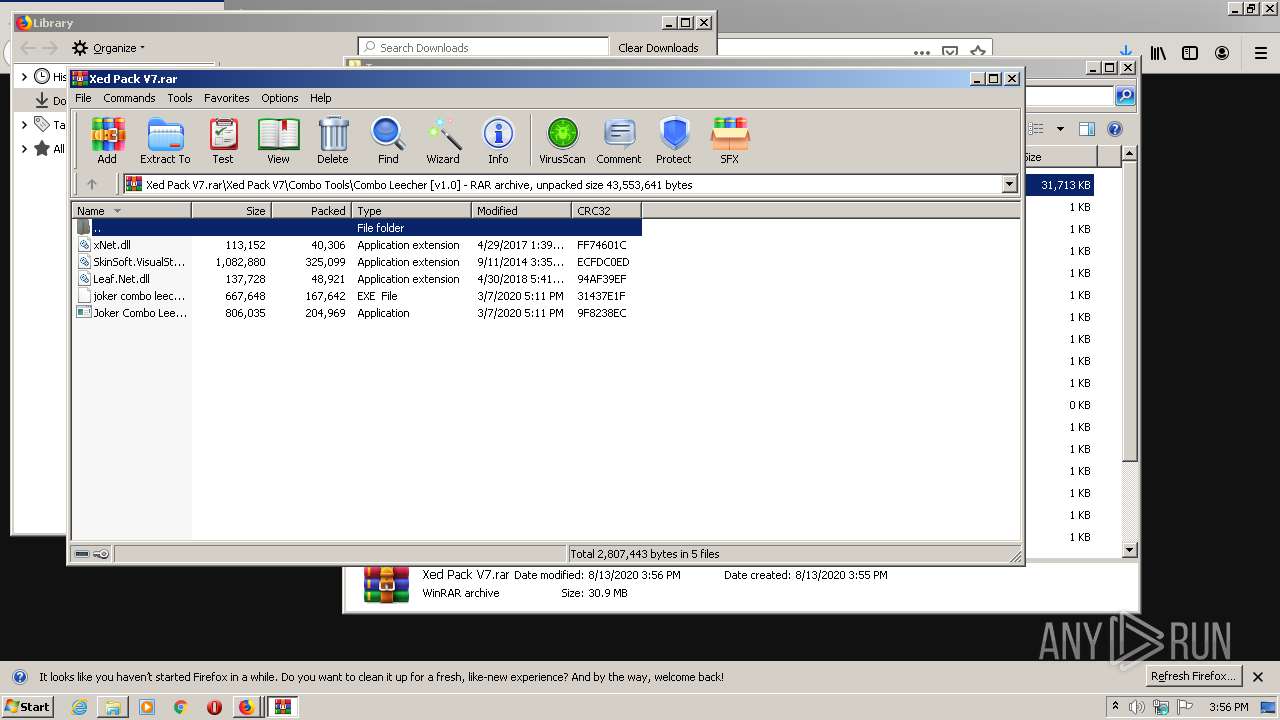
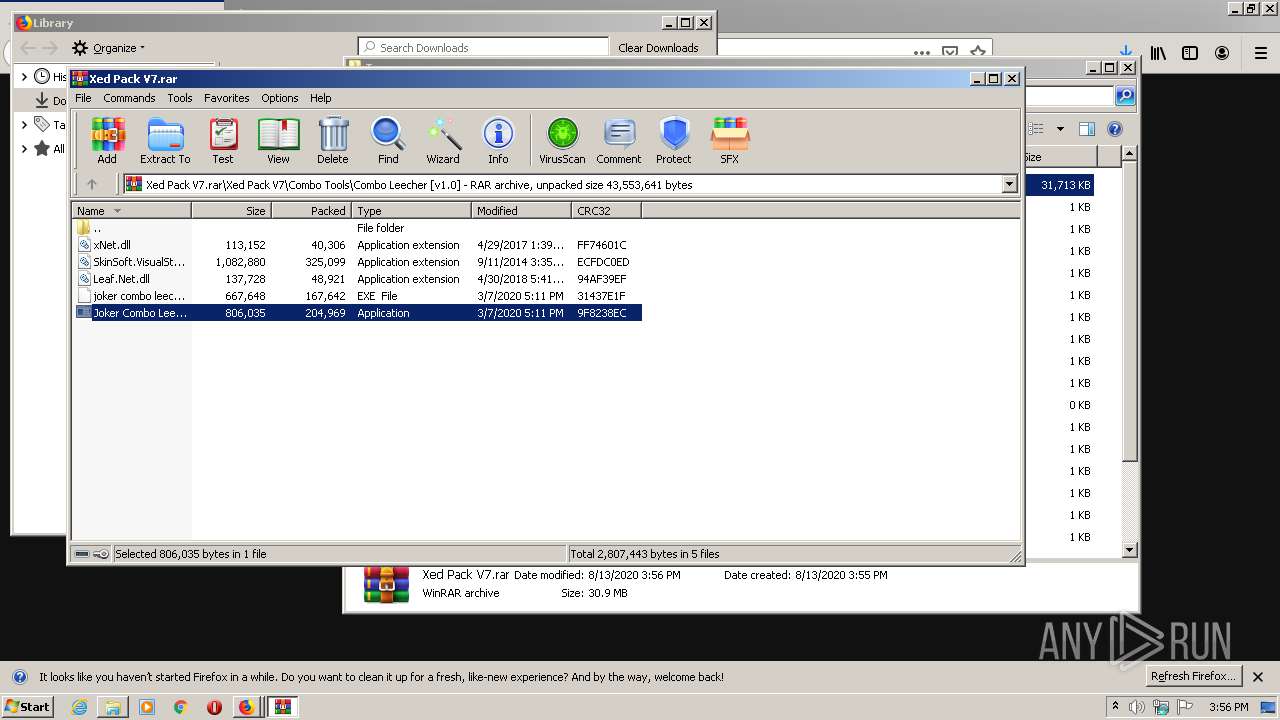
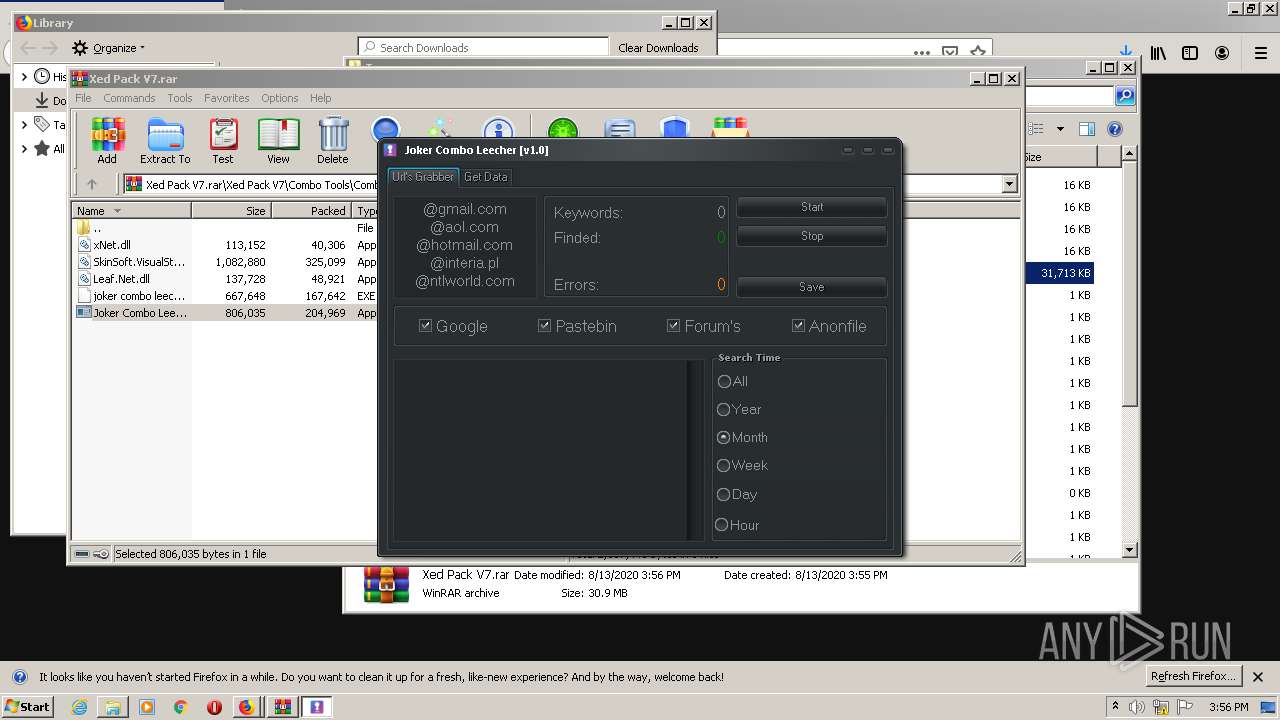
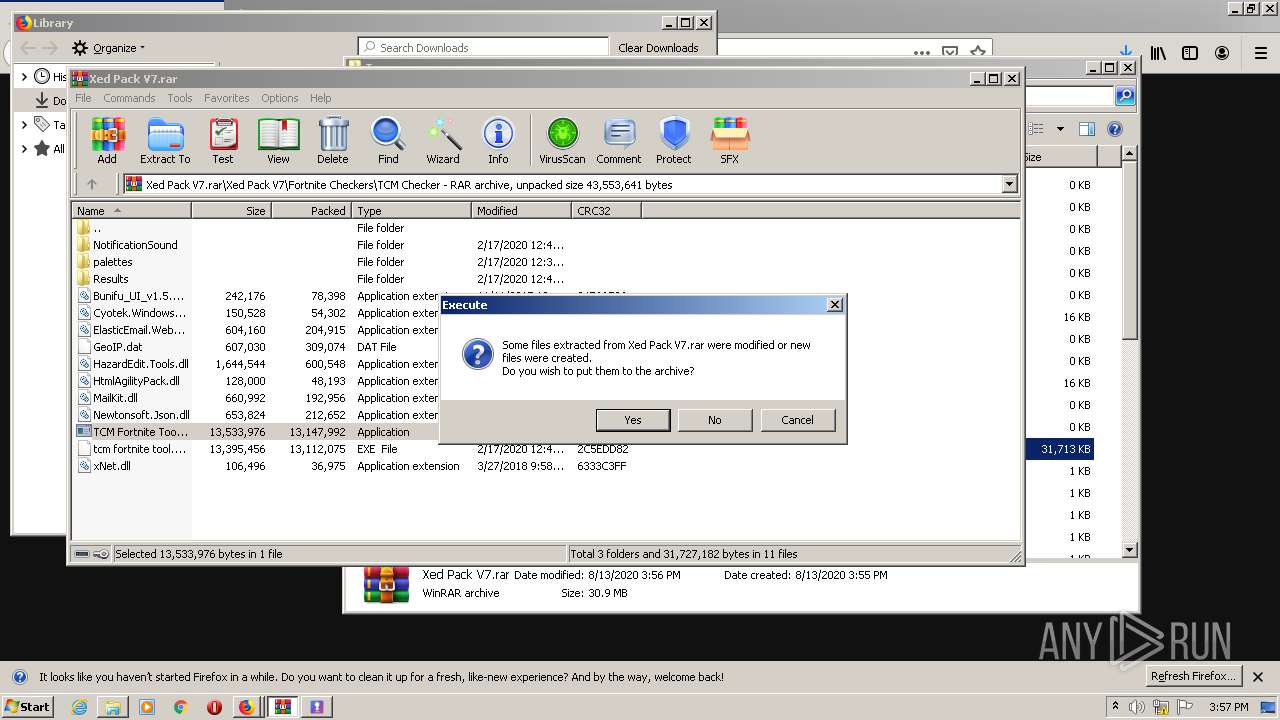
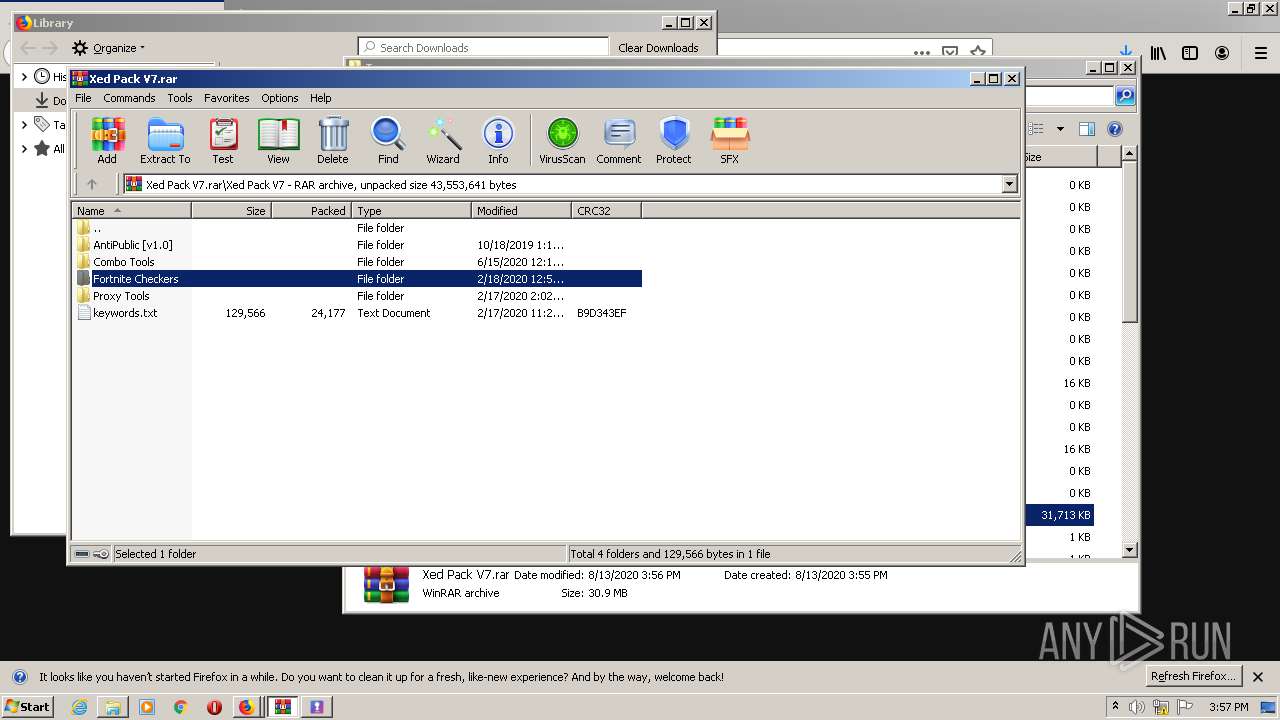
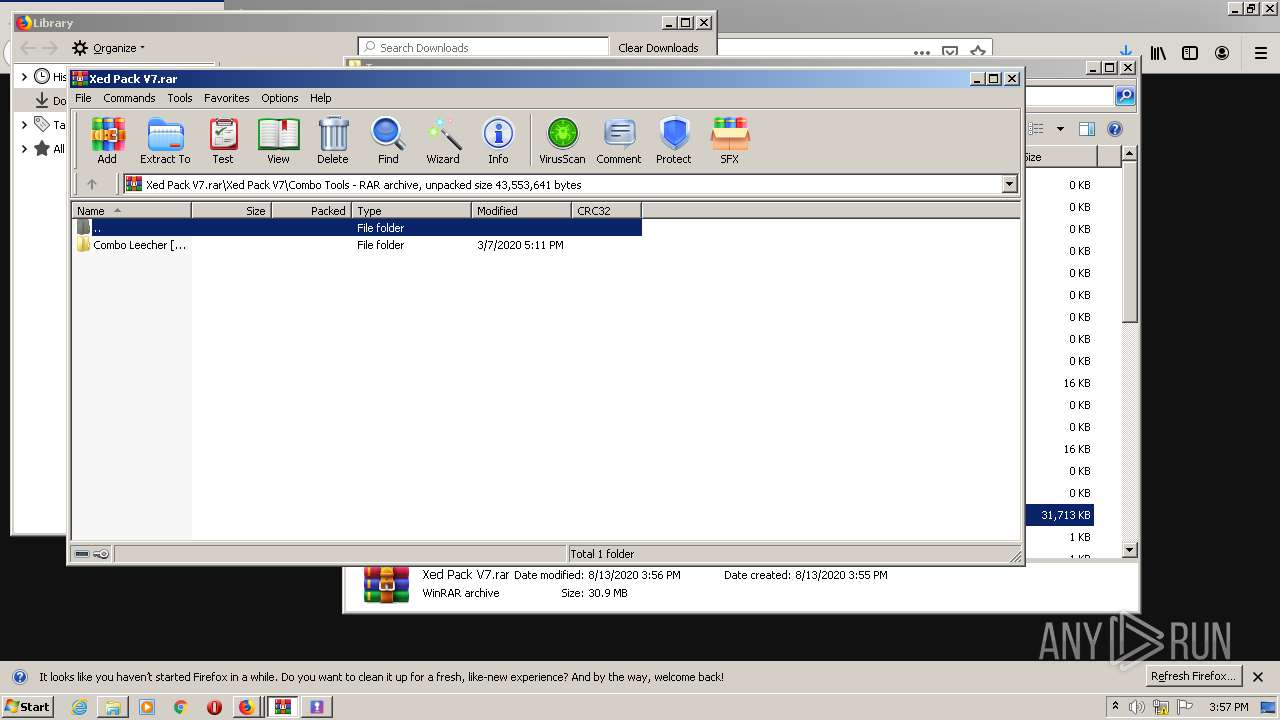
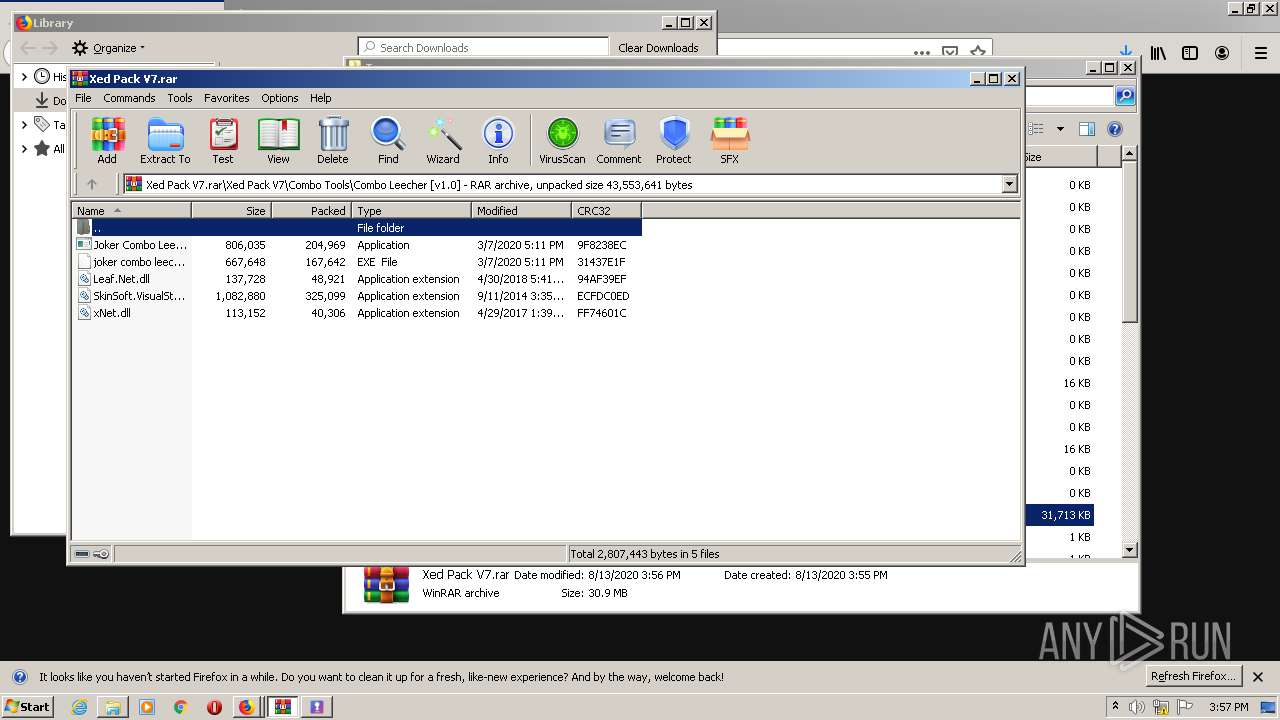
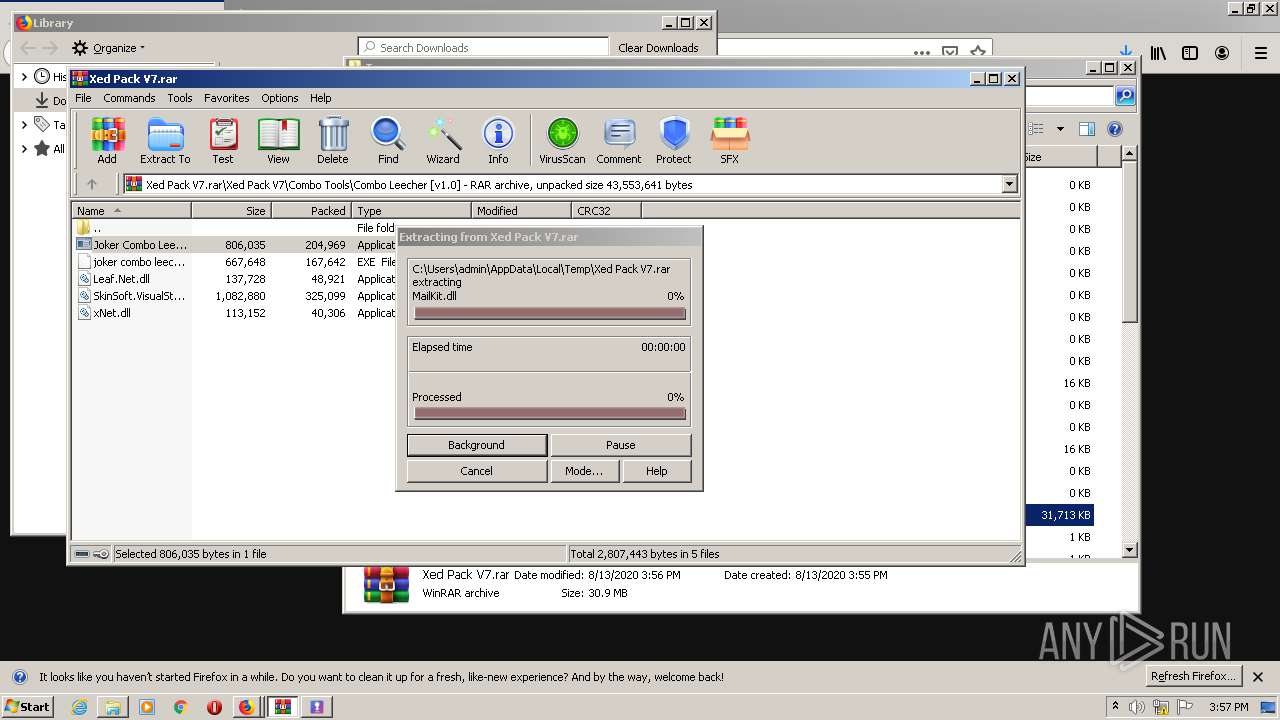
| URL: | https://anonfiles.com/t2d2m2A2o4/Xed_Pack_V7_rar |
| Full analysis: | https://app.any.run/tasks/a37f7025-e4a0-4025-9fa9-a94c6ce99ae4 |
| Verdict: | Malicious activity |
| Analysis date: | August 13, 2020, 14:55:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3135F485F22BD39A5000C7A41FE05463 |
| SHA1: | BFC11E3FF903018ECA19C47DC13F2B7007A40BE9 |
| SHA256: | DFAA0145734EF1B6081E1761990A3287F011ED9E168AE7F9BA1977696D7D8A77 |
| SSDEEP: | 3:N8M2KXBXI0axkoXn:2M2yfaxNX |
MALICIOUS
Application was dropped or rewritten from another process
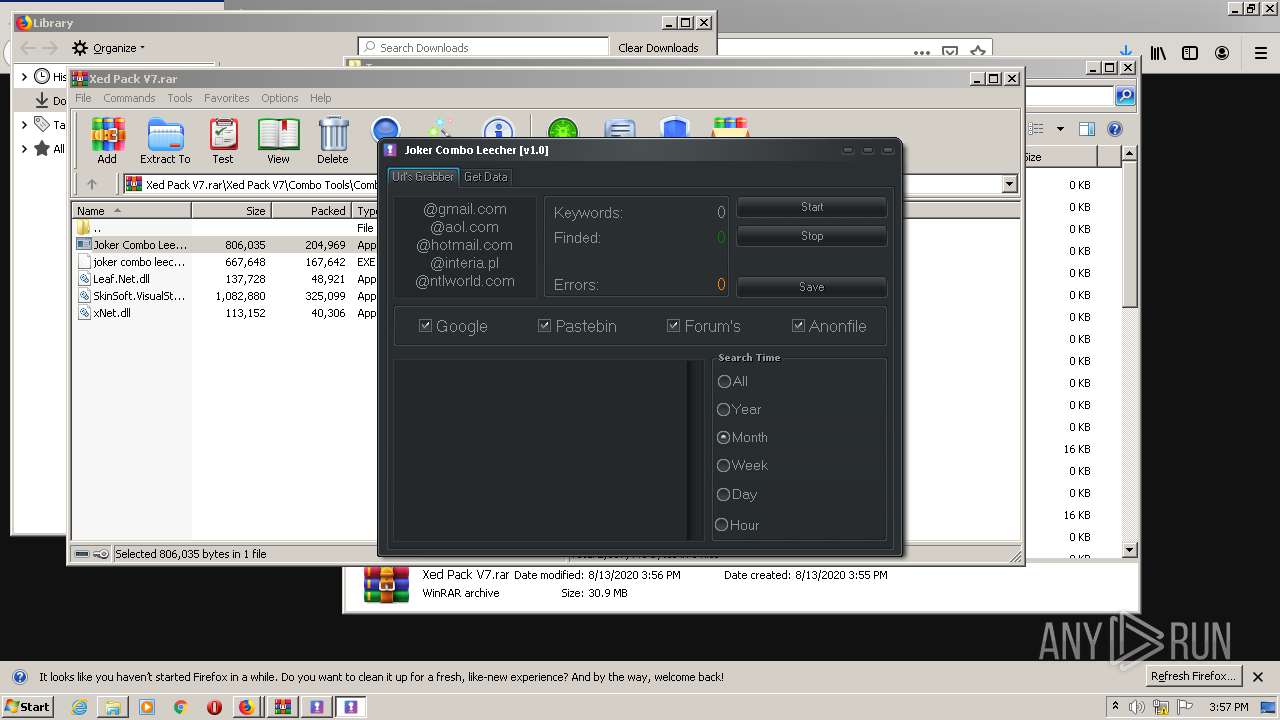
- Joker Combo Leecher [v1.0].exe (PID: 2388)
- joker combo leecher [v1.0].exe (PID: 3980)
- icsys.icn.exe (PID: 2292)
- Joker AntiPublic [v1.0].exe (PID: 1556)
- explorer.exe (PID: 2452)
- spoolsv.exe (PID: 3760)
- svchost.exe (PID: 612)
- spoolsv.exe (PID: 2440)
- OtimCLR v2.exe (PID: 3652)
- OtimCLR v2.exe (PID: 3588)
- otimclr v2.exe (PID: 2456)
- TCM Fortnite Tool.exe (PID: 3552)
- icsys.icn.exe (PID: 1584)
- explorer.exe (PID: 1988)
- TCM Fortnite Tool.exe (PID: 3076)
- icsys.icn.exe (PID: 4076)
- explorer.exe (PID: 2560)
- TCM Fortnite Tool.exe (PID: 1080)
- TCM Fortnite Tool.exe (PID: 2756)
- Joker Combo Leecher [v1.0].exe (PID: 720)
- icsys.icn.exe (PID: 2536)
- explorer.exe (PID: 3520)
- joker combo leecher [v1.0].exe (PID: 3444)
- icsys.icn.exe (PID: 3812)
- explorer.exe (PID: 2428)
- Joker Combo Leecher [v1.0].exe (PID: 3808)
- Joker Combo Leecher [v1.0].exe (PID: 1540)
Loads dropped or rewritten executable
- joker combo leecher [v1.0].exe (PID: 3980)
- Joker AntiPublic [v1.0].exe (PID: 1556)
- joker combo leecher [v1.0].exe (PID: 3444)
Changes the autorun value in the registry
- explorer.exe (PID: 2452)
- svchost.exe (PID: 612)
Uses Task Scheduler to run other applications
- svchost.exe (PID: 612)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 1712)
- schtasks.exe (PID: 3920)
- schtasks.exe (PID: 4064)
SUSPICIOUS
Executable content was dropped or overwritten
- Joker Combo Leecher [v1.0].exe (PID: 3808)
- icsys.icn.exe (PID: 2292)
- explorer.exe (PID: 2452)
- spoolsv.exe (PID: 3760)
- WinRAR.exe (PID: 3884)
- OtimCLR v2.exe (PID: 3588)
- TCM Fortnite Tool.exe (PID: 3076)
- TCM Fortnite Tool.exe (PID: 1080)
- Joker Combo Leecher [v1.0].exe (PID: 1540)
- Joker AntiPublic [v1.0].exe (PID: 1556)
Creates files in the Windows directory
- Joker Combo Leecher [v1.0].exe (PID: 3808)
- icsys.icn.exe (PID: 2292)
- explorer.exe (PID: 2452)
- spoolsv.exe (PID: 3760)
- OtimCLR v2.exe (PID: 3588)
- TCM Fortnite Tool.exe (PID: 3076)
- TCM Fortnite Tool.exe (PID: 1080)
- Joker Combo Leecher [v1.0].exe (PID: 1540)
Starts itself from another location
- Joker Combo Leecher [v1.0].exe (PID: 3808)
- icsys.icn.exe (PID: 2292)
- explorer.exe (PID: 2452)
- spoolsv.exe (PID: 3760)
- svchost.exe (PID: 612)
- OtimCLR v2.exe (PID: 3588)
- icsys.icn.exe (PID: 1584)
- TCM Fortnite Tool.exe (PID: 3076)
- icsys.icn.exe (PID: 4076)
- TCM Fortnite Tool.exe (PID: 1080)
- icsys.icn.exe (PID: 2536)
- Joker Combo Leecher [v1.0].exe (PID: 1540)
- icsys.icn.exe (PID: 3812)
Starts application with an unusual extension
- Joker Combo Leecher [v1.0].exe (PID: 3808)
- OtimCLR v2.exe (PID: 3588)
- Joker Combo Leecher [v1.0].exe (PID: 1540)
Removes files from Windows directory
- icsys.icn.exe (PID: 2292)
- explorer.exe (PID: 2452)
- spoolsv.exe (PID: 3760)
- OtimCLR v2.exe (PID: 3588)
- TCM Fortnite Tool.exe (PID: 3076)
- TCM Fortnite Tool.exe (PID: 1080)
- Joker Combo Leecher [v1.0].exe (PID: 1540)
Creates files in the program directory
- firefox.exe (PID: 3968)
Creates executable files which already exist in Windows
- icsys.icn.exe (PID: 2292)
- spoolsv.exe (PID: 3760)
Creates or modifies windows services
- svchost.exe (PID: 612)
INFO
Application launched itself
- firefox.exe (PID: 3968)
- firefox.exe (PID: 900)
Reads CPU info
- firefox.exe (PID: 3968)
Reads Internet Cache Settings
- firefox.exe (PID: 3968)
Creates files in the user directory
- firefox.exe (PID: 3968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
94
Monitored processes
37
Malicious processes
13
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | c:\windows\resources\svchost.exe | c:\windows\resources\svchost.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 720 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.46897\Xed Pack V7\Combo Tools\Combo Leecher [v1.0]\Joker Combo Leecher [v1.0].exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.46897\Xed Pack V7\Combo Tools\Combo Leecher [v1.0]\Joker Combo Leecher [v1.0].exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 900 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://anonfiles.com/t2d2m2A2o4/Xed_Pack_V7_rar" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 1080 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.45572\Xed Pack V7\Fortnite Checkers\TCM Checker\TCM Fortnite Tool.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.45572\Xed Pack V7\Fortnite Checkers\TCM Checker\TCM Fortnite Tool.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1272 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3968.13.1127063523\87029263" -childID 2 -isForBrowser -prefsHandle 2924 -prefMapHandle 2928 -prefsLen 5997 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3968 "\\.\pipe\gecko-crash-server-pipe.3968" 2944 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 1540 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.46897\Xed Pack V7\Combo Tools\Combo Leecher [v1.0]\Joker Combo Leecher [v1.0].exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.46897\Xed Pack V7\Combo Tools\Combo Leecher [v1.0]\Joker Combo Leecher [v1.0].exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1556 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.40548\Xed Pack V7\AntiPublic [v1.0]\Joker AntiPublic [v1.0].exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.40548\Xed Pack V7\AntiPublic [v1.0]\Joker AntiPublic [v1.0].exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Joker AntiPublic [v1.0] Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1584 | C:\Windows\Resources\Themes\icsys.icn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | — | OtimCLR v2.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1712 | schtasks /create /tn "svchost" /tr "c:\windows\resources\svchost.exe" /sc daily /st 15:58 /f | C:\Windows\system32\schtasks.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1988 | c:\windows\resources\themes\explorer.exe | c:\windows\resources\themes\explorer.exe | — | icsys.icn.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
1 603
Read events
1 488
Write events
115
Delete events
0
Modification events
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 121E9A0A00000000 | |||
| (PID) Process: | (900) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 111E9A0A00000000 | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3968) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithProgids |
| Operation: | write | Name: | WinRAR |
Value: | |||
Executable files
230
Suspicious files
105
Text files
108
Unknown types
76
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | — | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
| 3968 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
42
DNS requests
109
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3968 | firefox.exe | GET | 301 | 172.67.178.125:80 | http://www.24hours-news.com/super-link/windows.php?subid=737329&extcid=2991395173990764506 | US | — | — | suspicious |
3968 | firefox.exe | GET | 200 | 104.24.121.183:80 | http://www.24hours-news.com/.well-known/http-opportunistic | US | text | 100 b | suspicious |
3968 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 279 b | whitelisted |
3968 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3968 | firefox.exe | POST | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
3968 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 280 b | whitelisted |
3968 | firefox.exe | GET | 200 | 2.16.177.88:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
3968 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3968 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3968 | firefox.exe | GET | 200 | 2.16.177.88:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3968 | firefox.exe | 143.204.202.20:443 | snippets.cdn.mozilla.net | — | US | suspicious |
3968 | firefox.exe | 151.101.2.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
3968 | firefox.exe | 13.35.253.123:443 | djv99sxoqpv11.cloudfront.net | — | US | suspicious |
3968 | firefox.exe | 143.204.202.6:443 | firefox.settings.services.mozilla.com | — | US | malicious |
3968 | firefox.exe | 34.196.151.230:443 | baconaces.pro | Amazon.com, Inc. | US | malicious |
3968 | firefox.exe | 2.16.177.64:443 | shavar.services.mozilla.com | Akamai International B.V. | — | suspicious |
3968 | firefox.exe | 194.32.146.97:443 | cdn-140.anonfiles.com | — | — | unknown |
3968 | firefox.exe | 13.249.109.108:443 | bostoppa.club | — | US | unknown |
3968 | firefox.exe | 13.249.109.104:443 | depleastpo.club | — | US | unknown |
3968 | firefox.exe | 143.204.202.13:443 | content-signature-2.cdn.mozilla.net | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
anonfiles.com |
| shared |
a1089.dscd.akamai.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cs9.wac.phicdn.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |