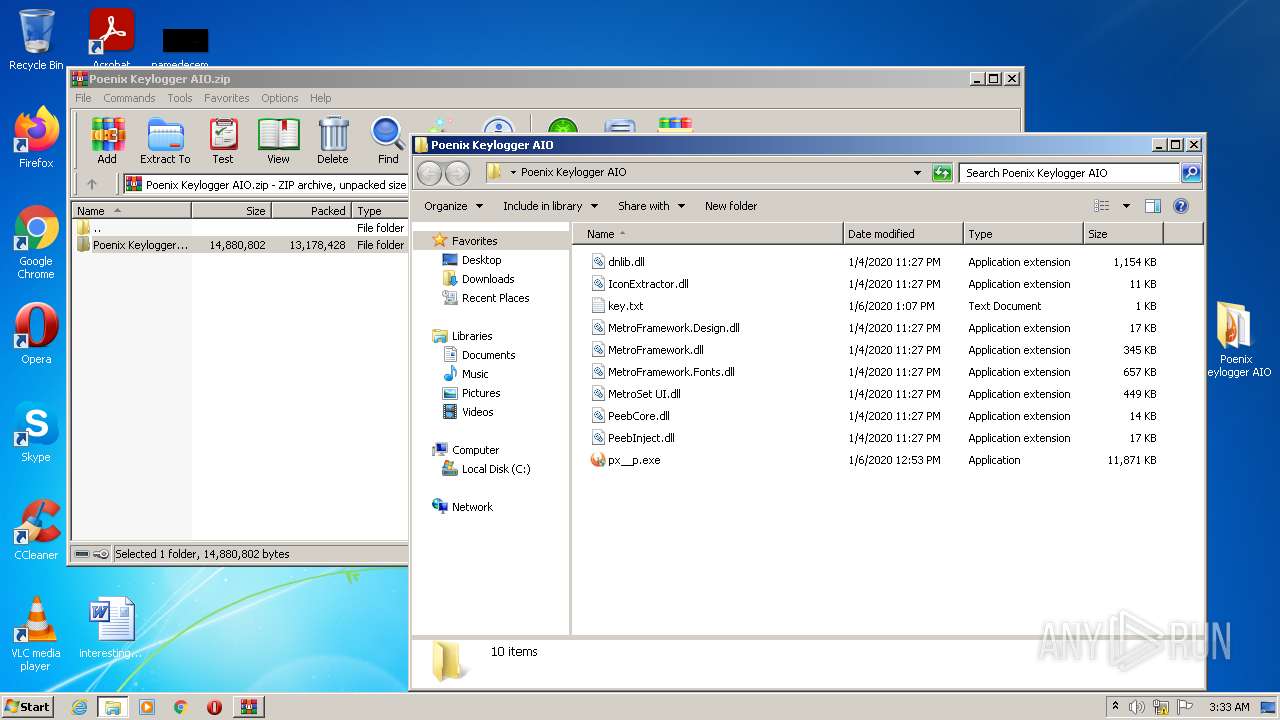
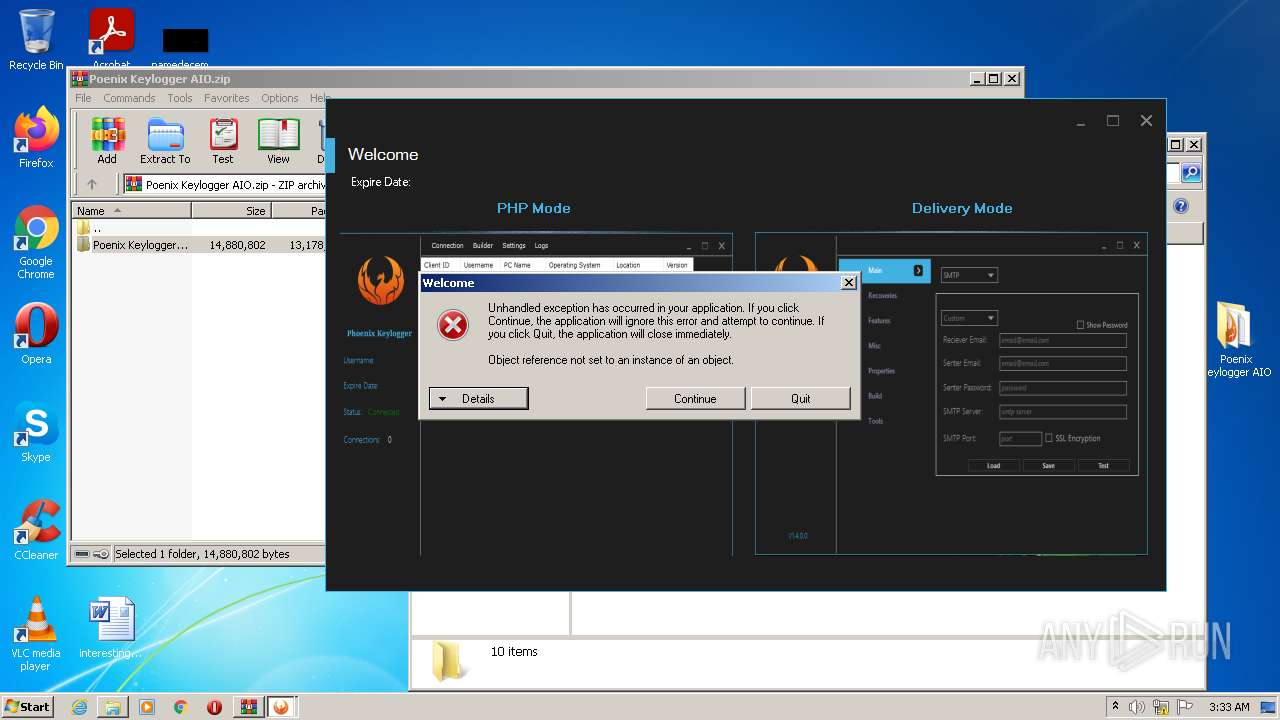
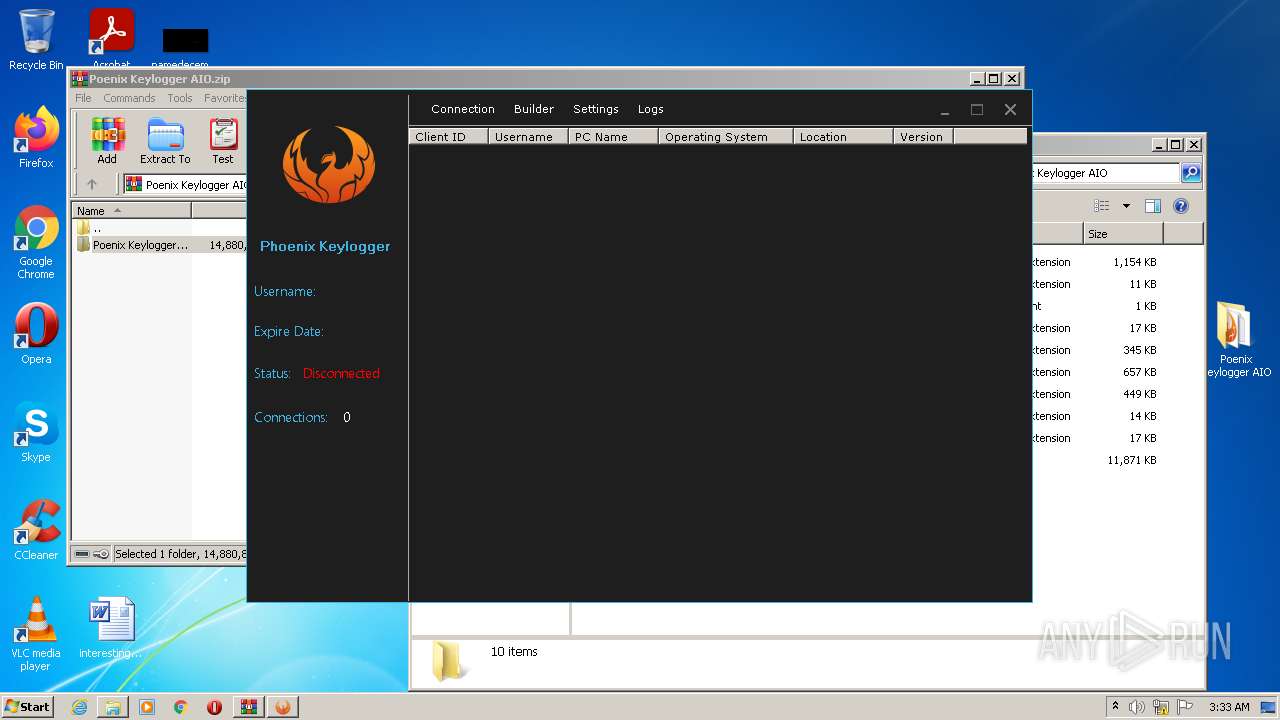
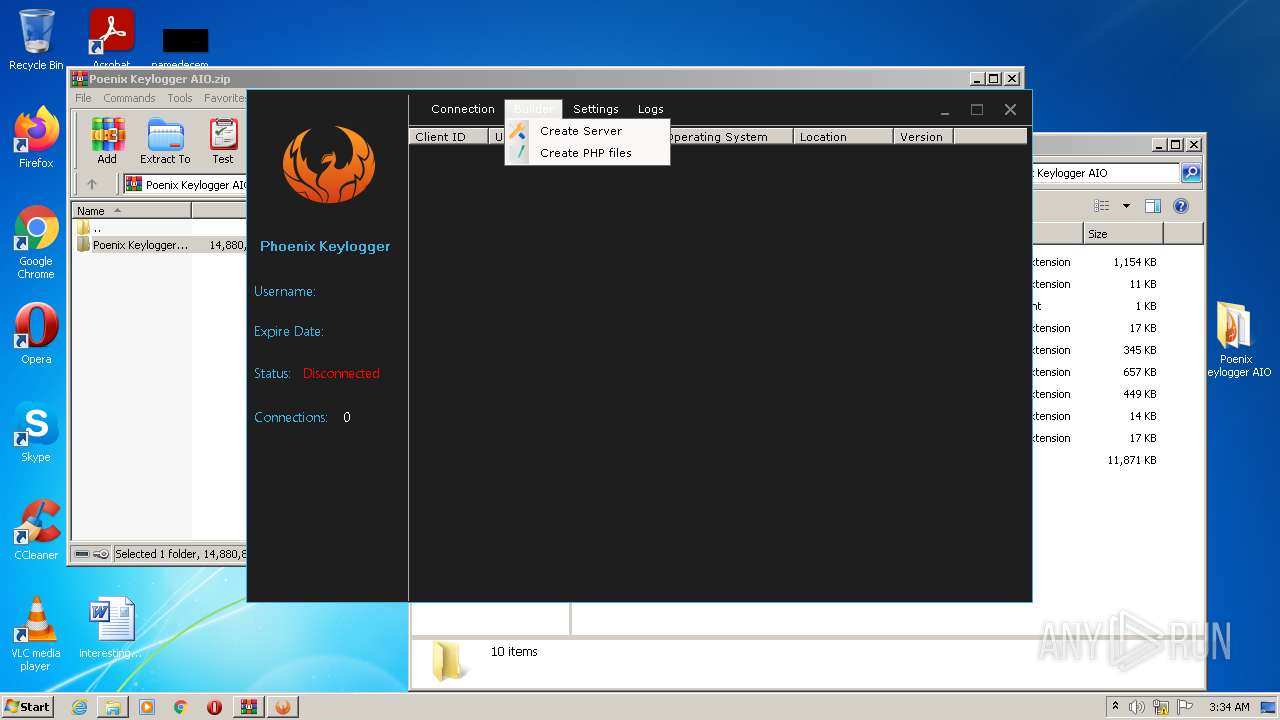
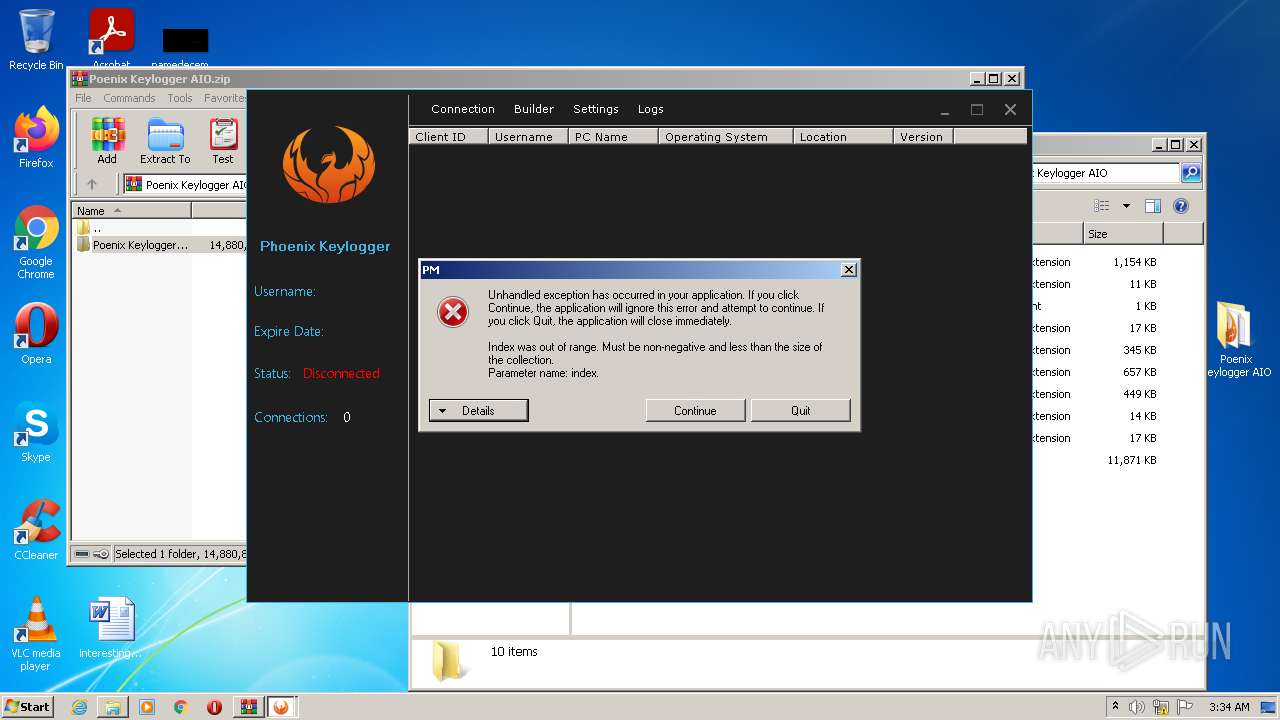
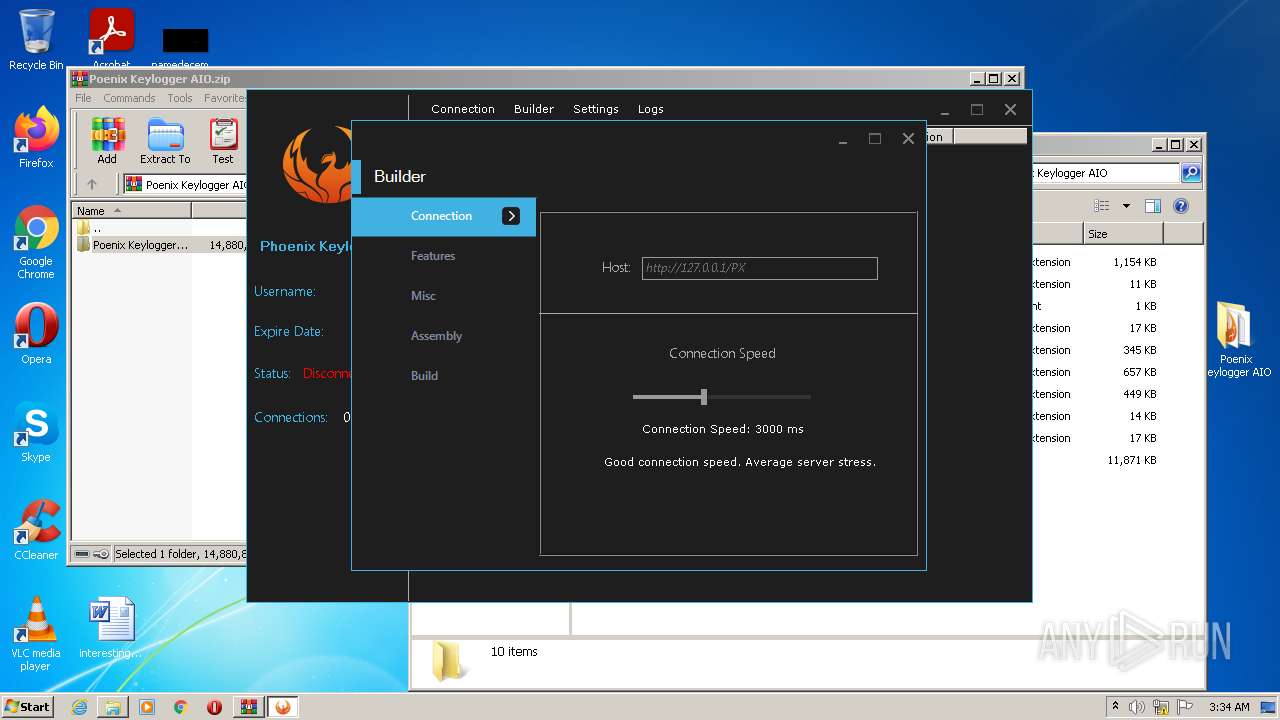
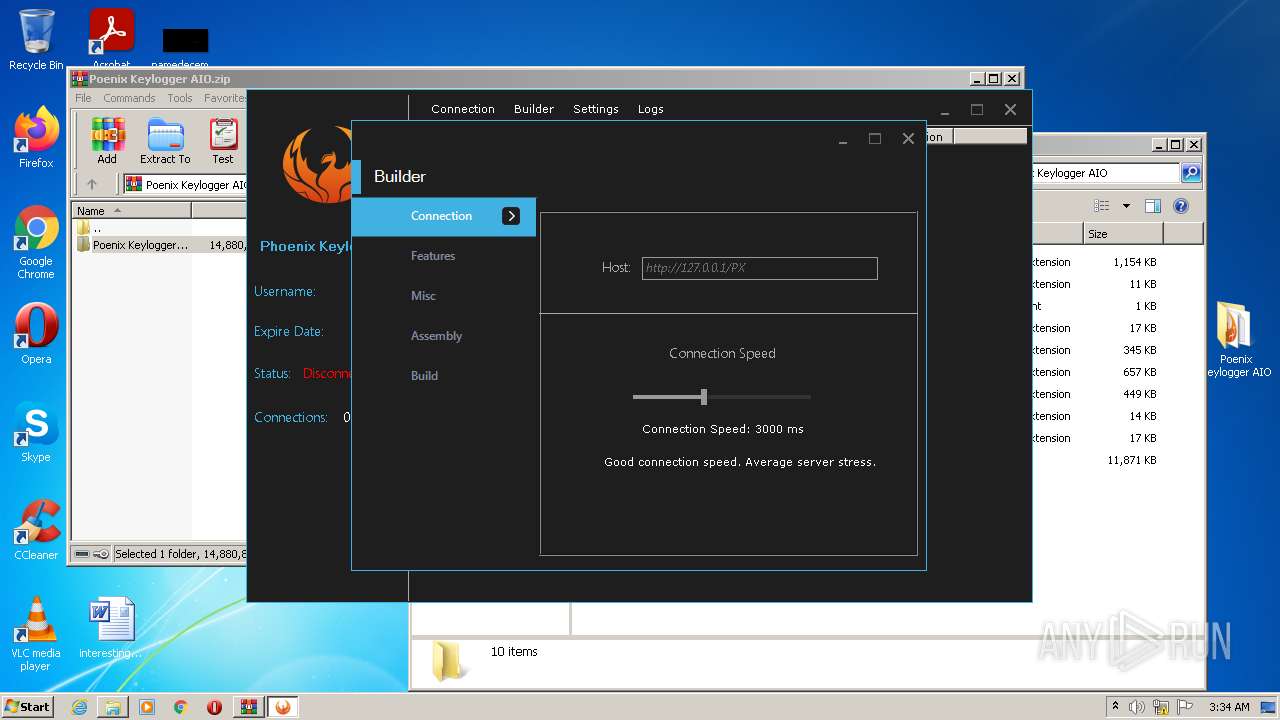
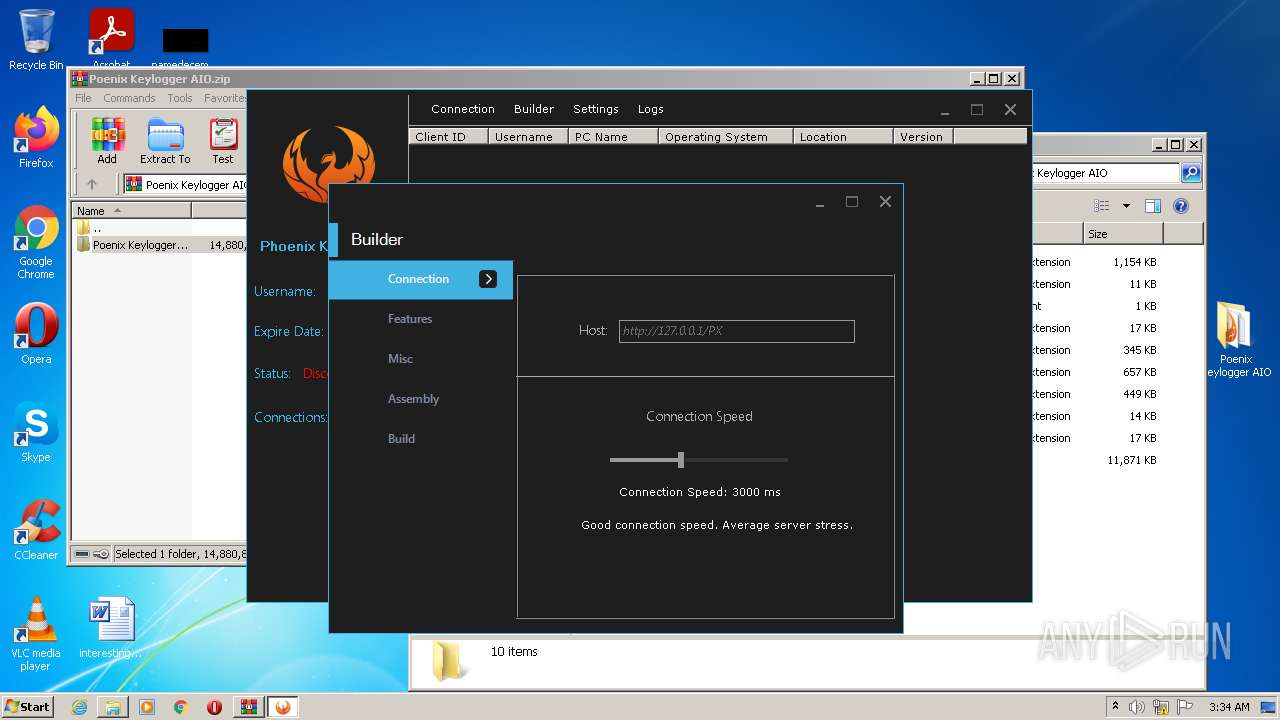
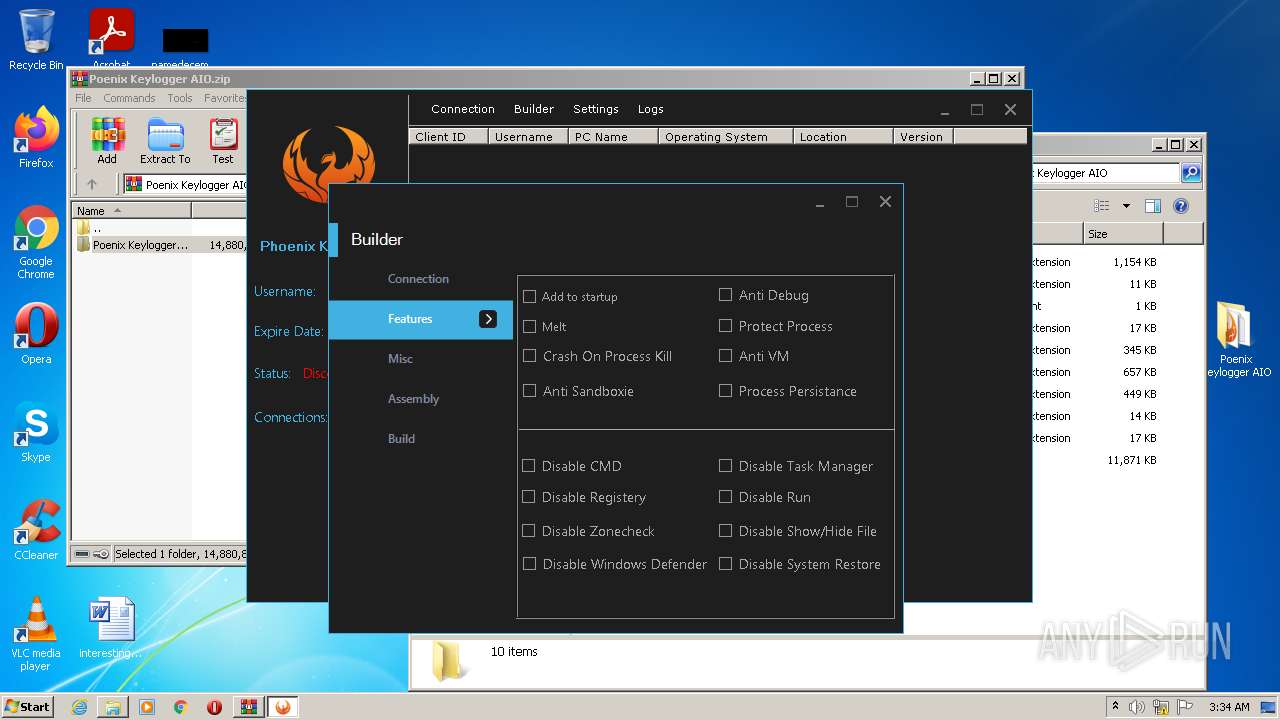
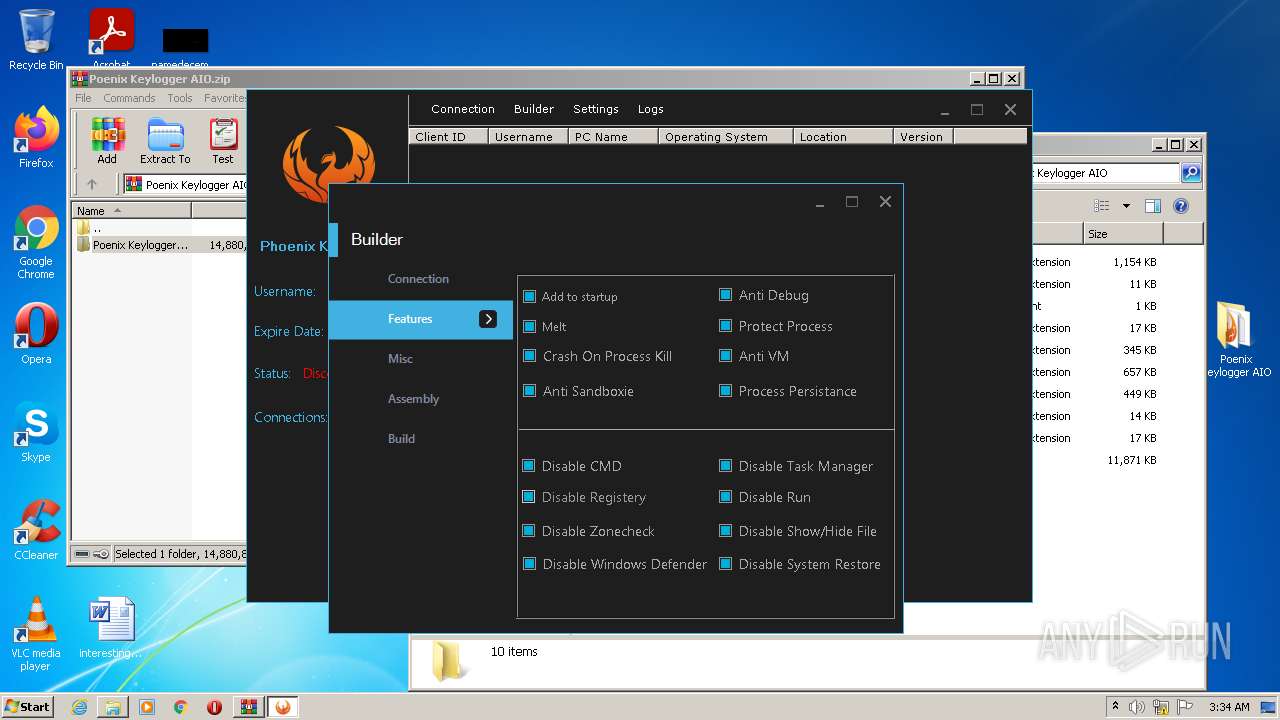
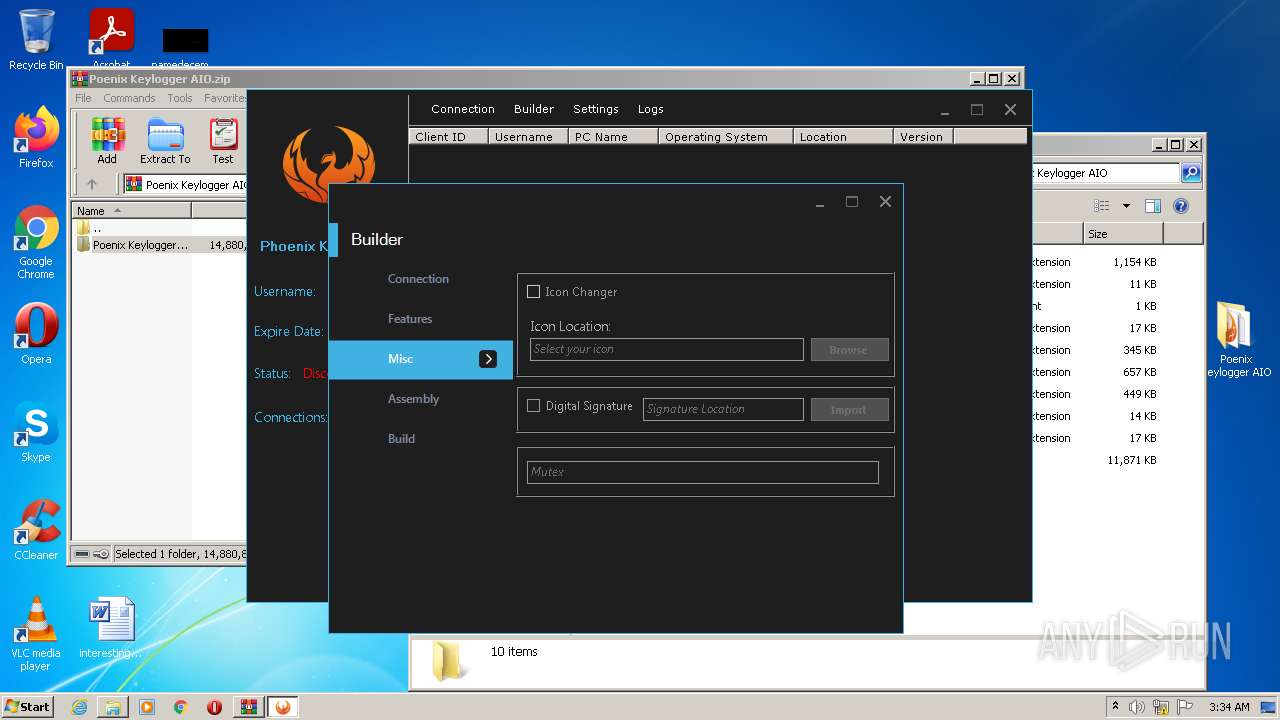
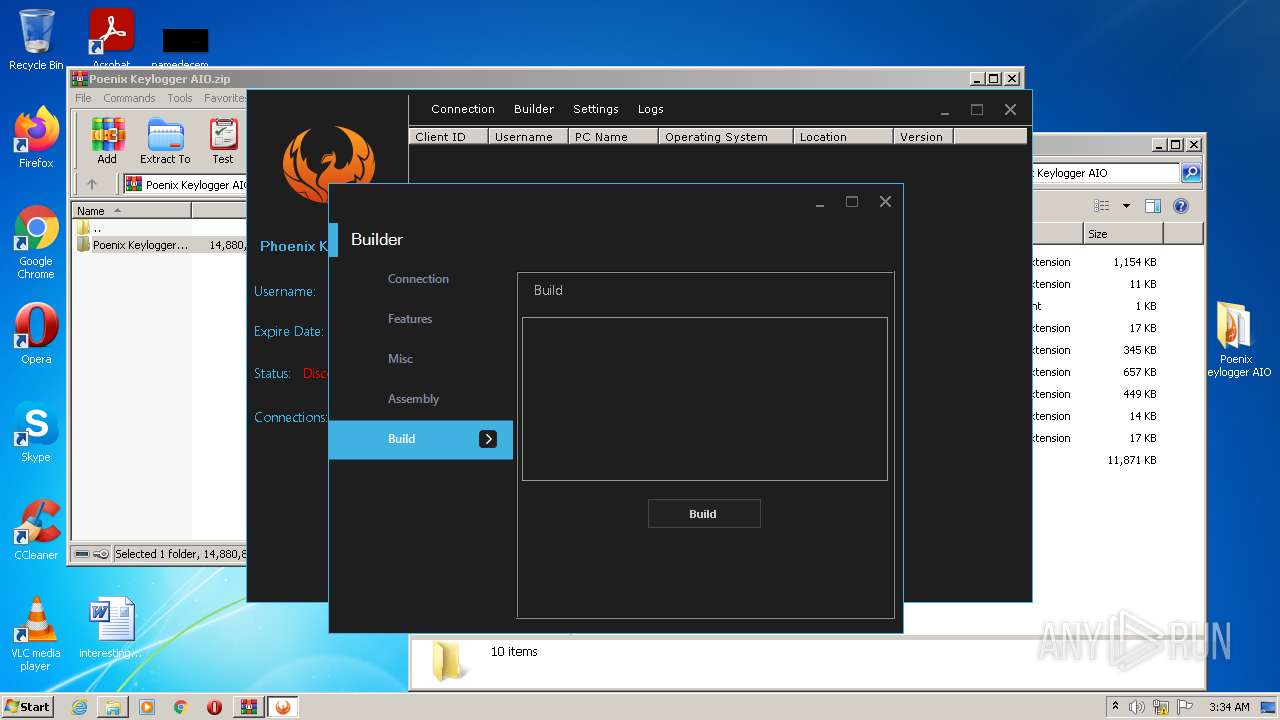
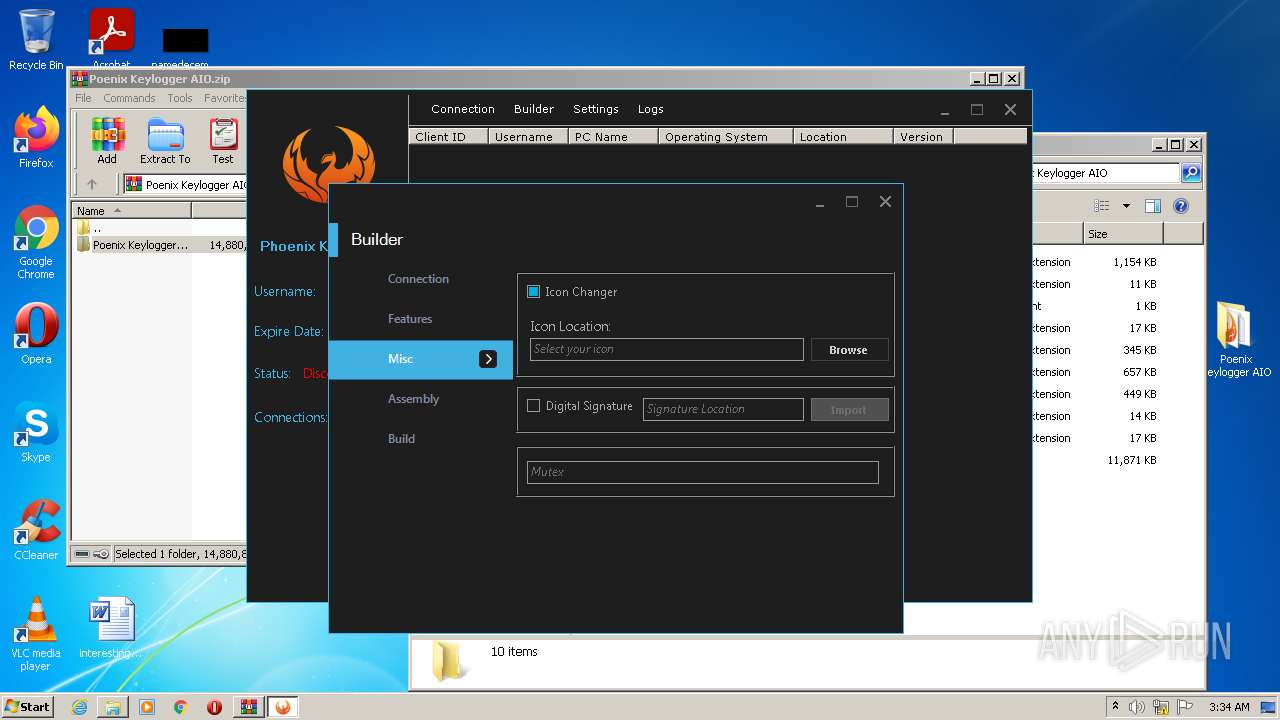
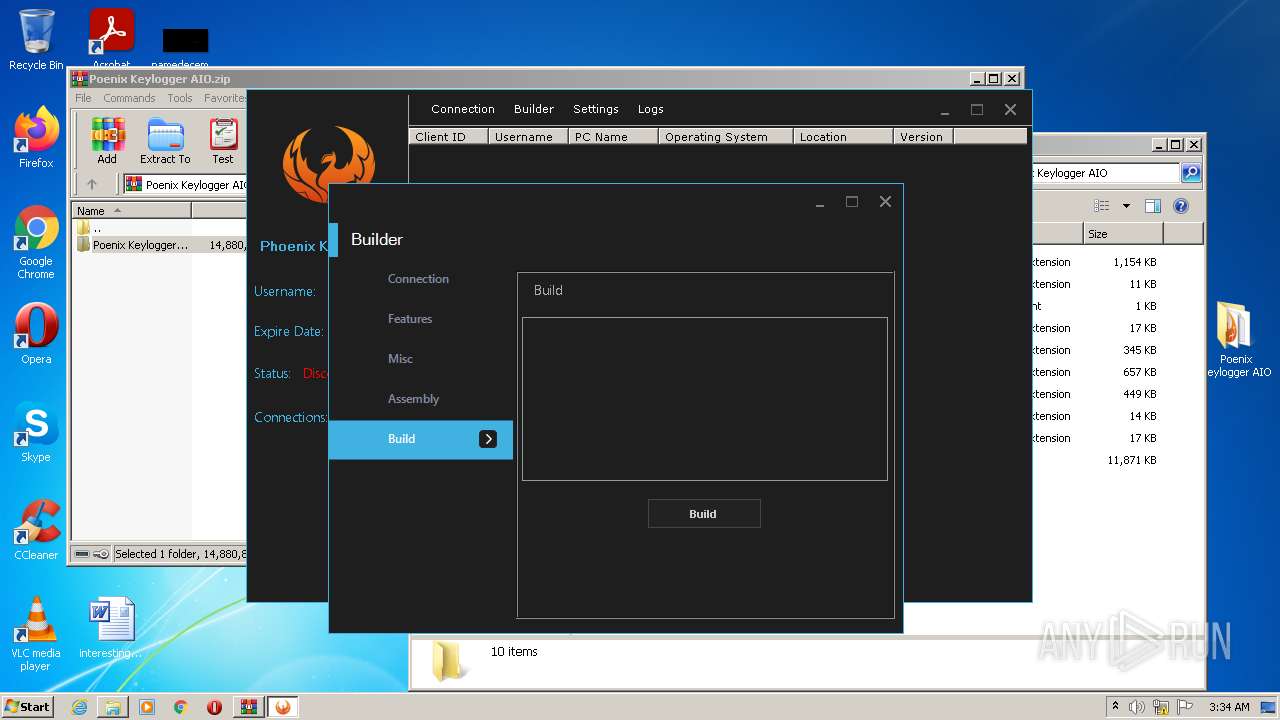
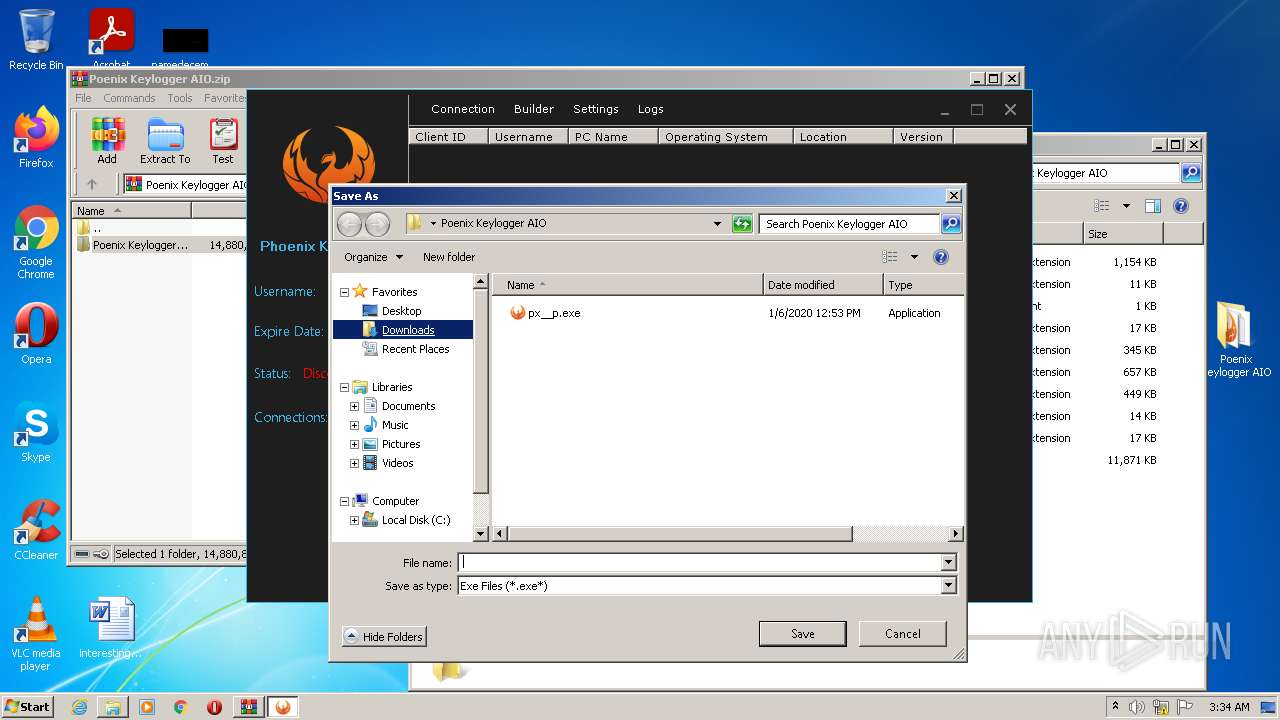
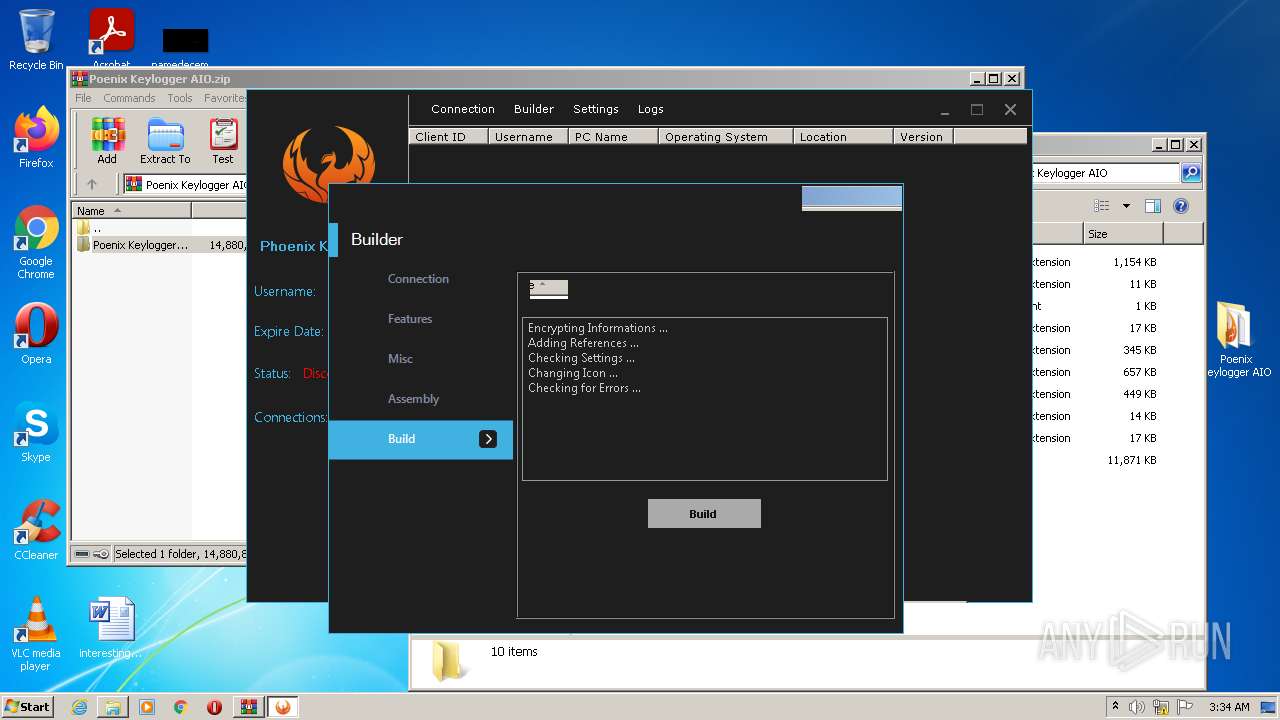
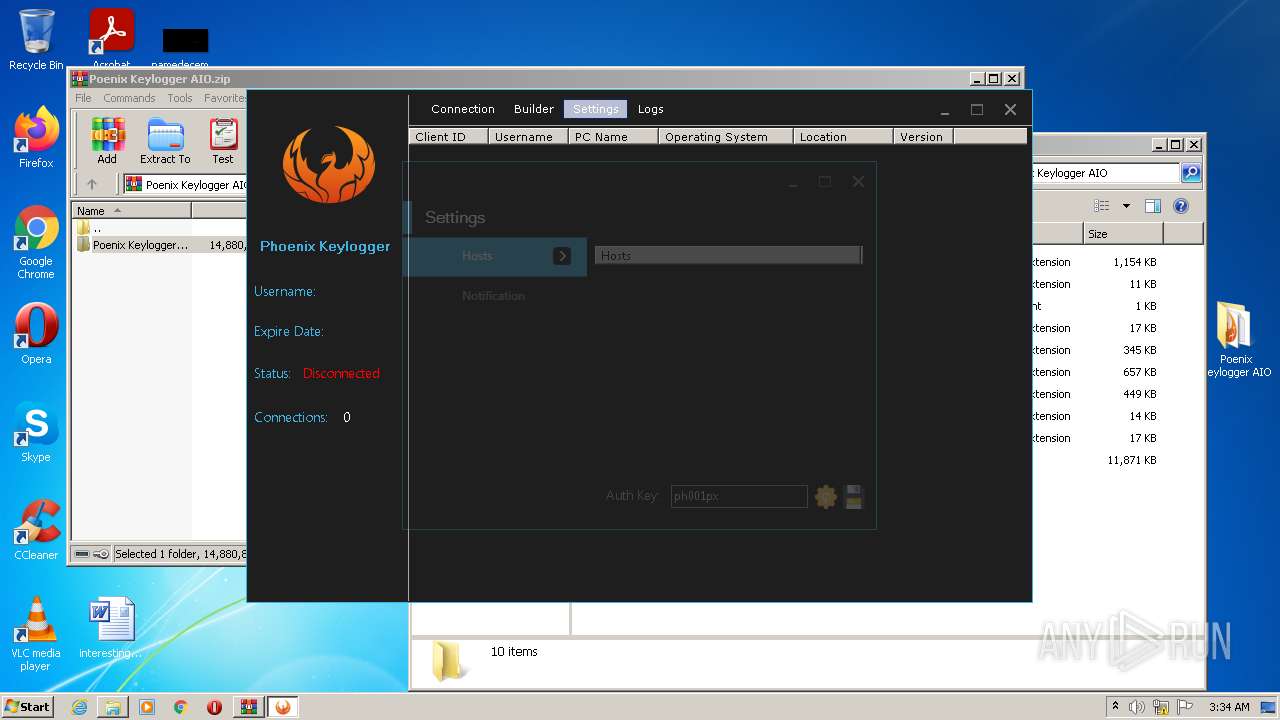
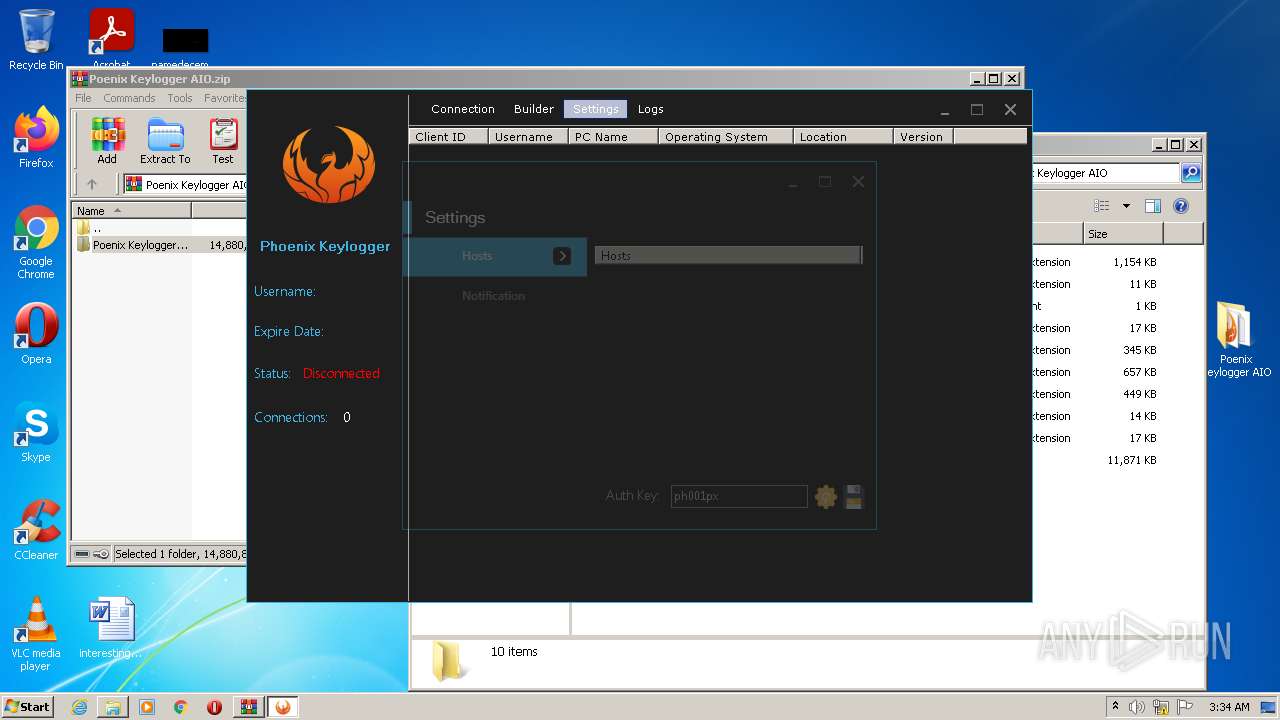
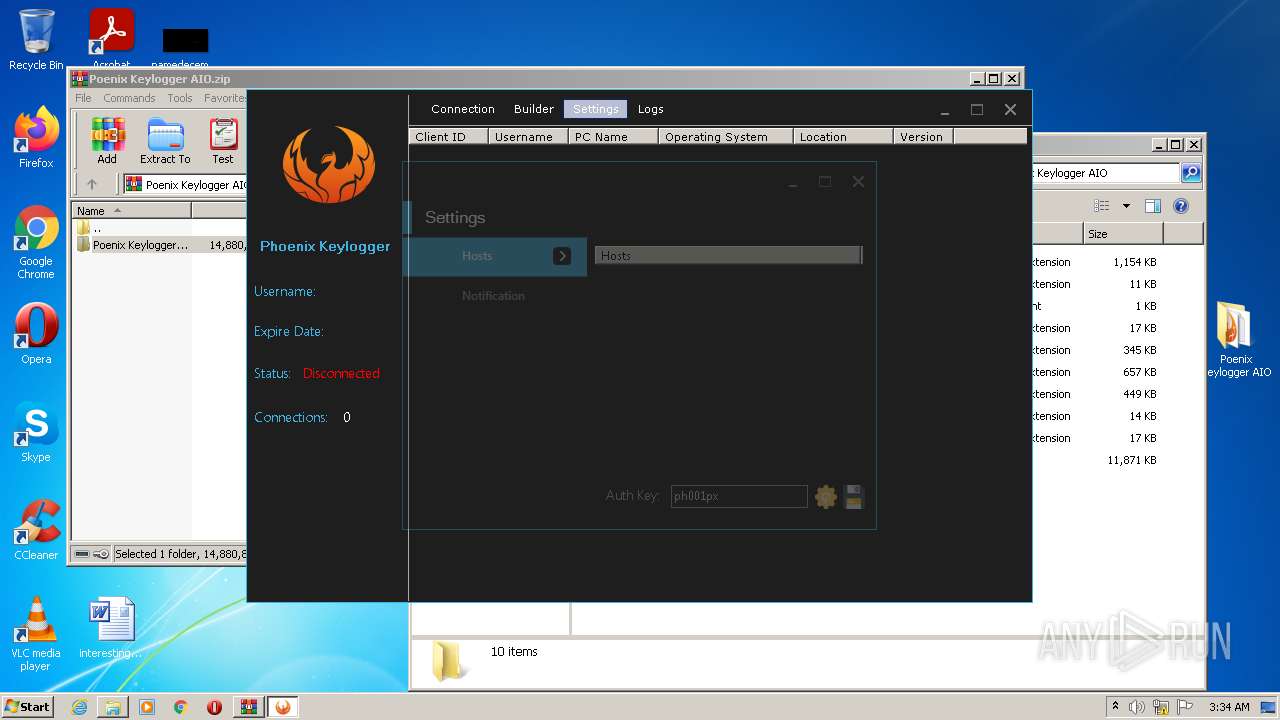
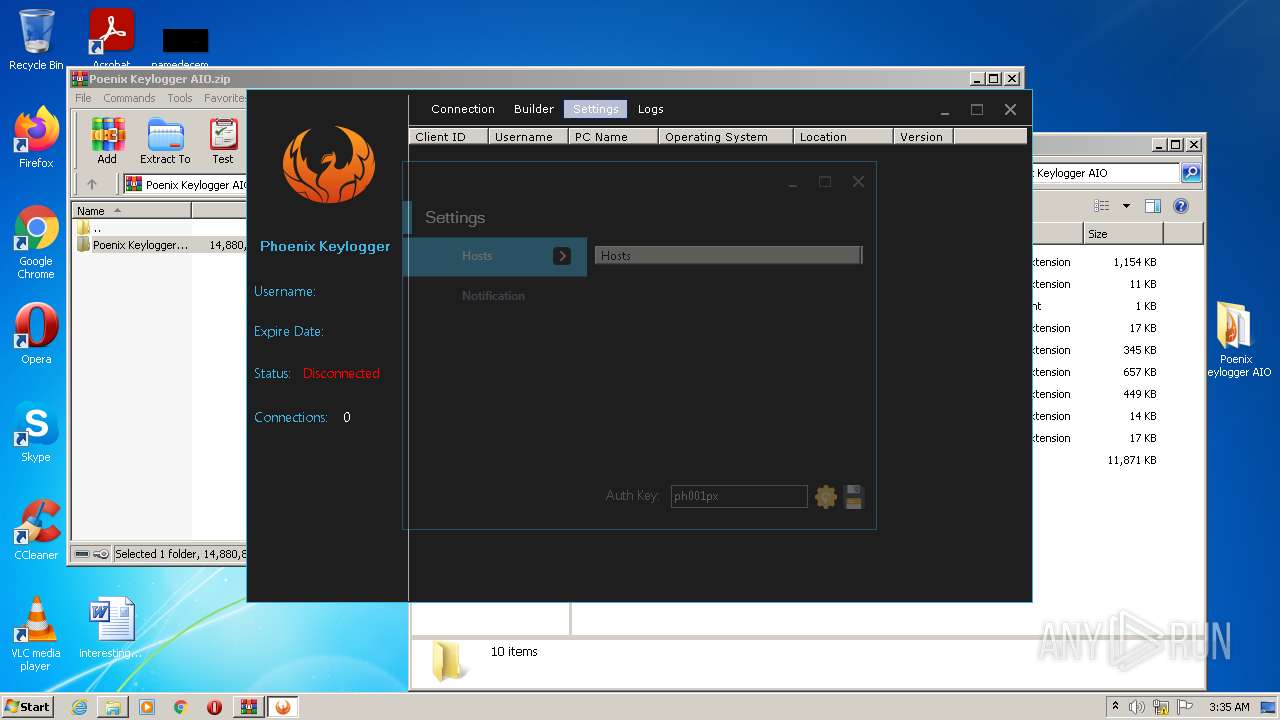
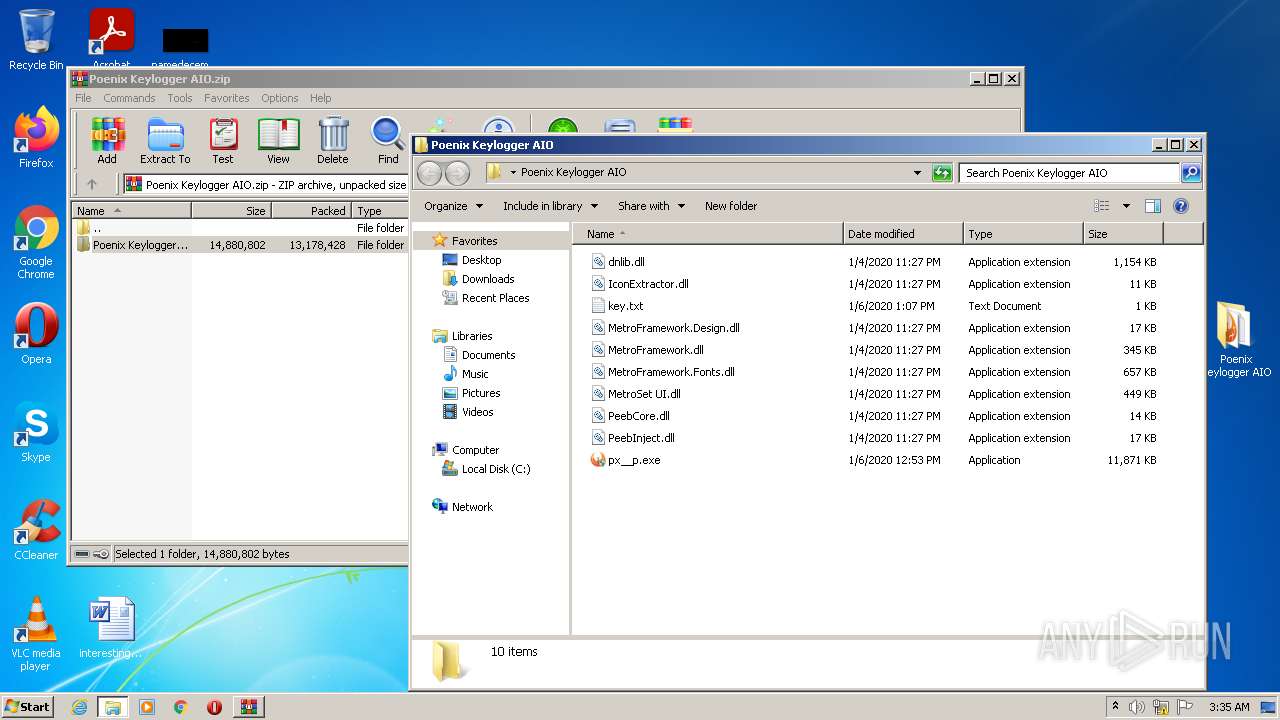
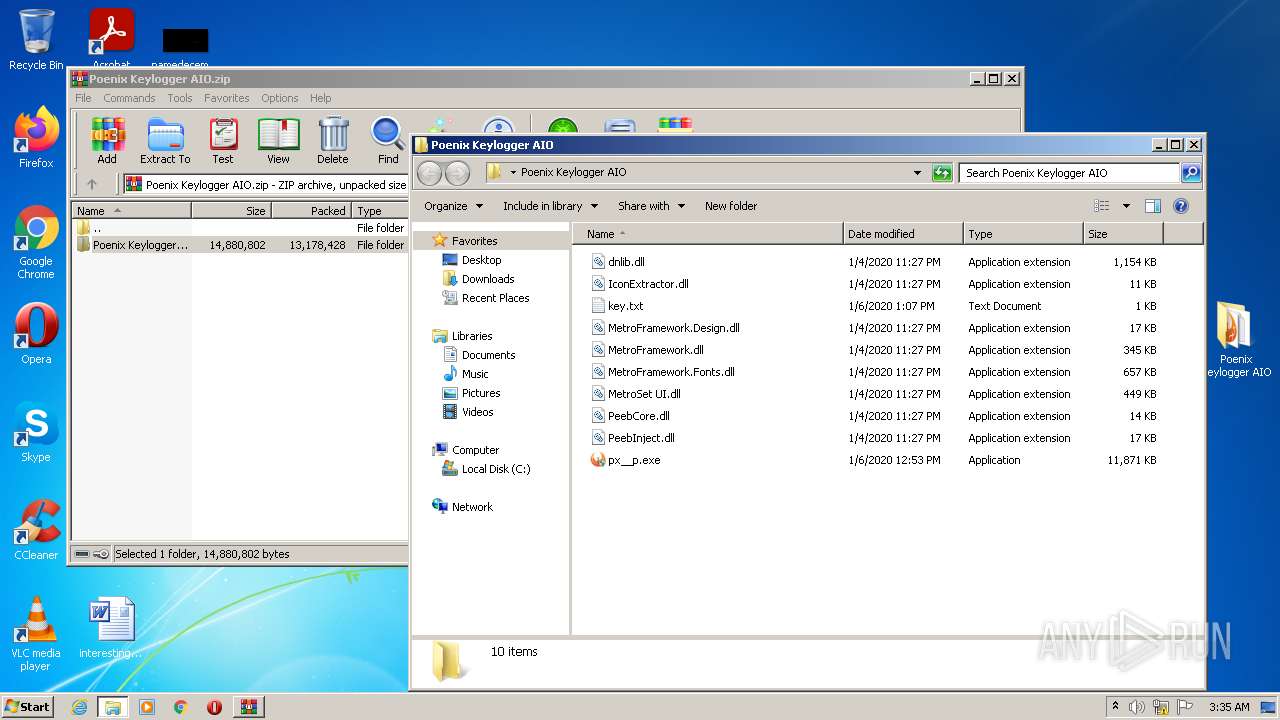
| File name: | Poenix Keylogger AIO.zip |
| Full analysis: | https://app.any.run/tasks/9215283f-14fe-4f1f-b7ae-b17ff5385347 |
| Verdict: | Malicious activity |
| Analysis date: | January 25, 2022, 03:33:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8A661305BC62C4EE76EAEF71C9965BDC |
| SHA1: | 9F01A1DA2AF1002B0930A664D0043E5C79E501AC |
| SHA256: | DF9ECD91B0D24A1D0AD7F75A48D32DFEB9DD2453005C7A42BDF9B49C81A33DD5 |
| SSDEEP: | 196608:XyP8g/e62p1vo+zBYcOHx52yF0ev9+9rGdUlufPV4ZCK46qYfgFbaqJH4YafJ27r:ie68hVdXwUiUlunuh46IaqLATEP |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2716)
- px__p.exe (PID: 3388)
- Explorer.EXE (PID: 1656)
Application was dropped or rewritten from another process
- px__p.exe (PID: 2088)
- px__p.exe (PID: 3388)
Drops executable file immediately after starts
- vbc.exe (PID: 2912)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2252)
- px__p.exe (PID: 3388)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2252)
Checks supported languages
- WinRAR.exe (PID: 2252)
- px__p.exe (PID: 3388)
- vbc.exe (PID: 2912)
- cvtres.exe (PID: 1784)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2252)
- vbc.exe (PID: 2912)
- px__p.exe (PID: 3388)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2252)
- vbc.exe (PID: 2912)
- px__p.exe (PID: 3388)
Reads internet explorer settings
- px__p.exe (PID: 3388)
Application launched itself
- Explorer.EXE (PID: 1656)
Reads Environment values
- px__p.exe (PID: 3388)
Executes scripts
- px__p.exe (PID: 3388)
Drops a file with too old compile date
- px__p.exe (PID: 3388)
INFO
Manual execution by user
- px__p.exe (PID: 2088)
- px__p.exe (PID: 3388)
Checks supported languages
- explorer.exe (PID: 3368)
Reads the computer name
- explorer.exe (PID: 3368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Poenix Keylogger AIO/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2020:01:06 14:13:05 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
51
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1656 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1784 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES20DF.tmp" "C:\Users\admin\AppData\Local\Temp\vbc76545414DBDF4E32A9A58EF5BD7CFA.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | vbc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft� Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.51209.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
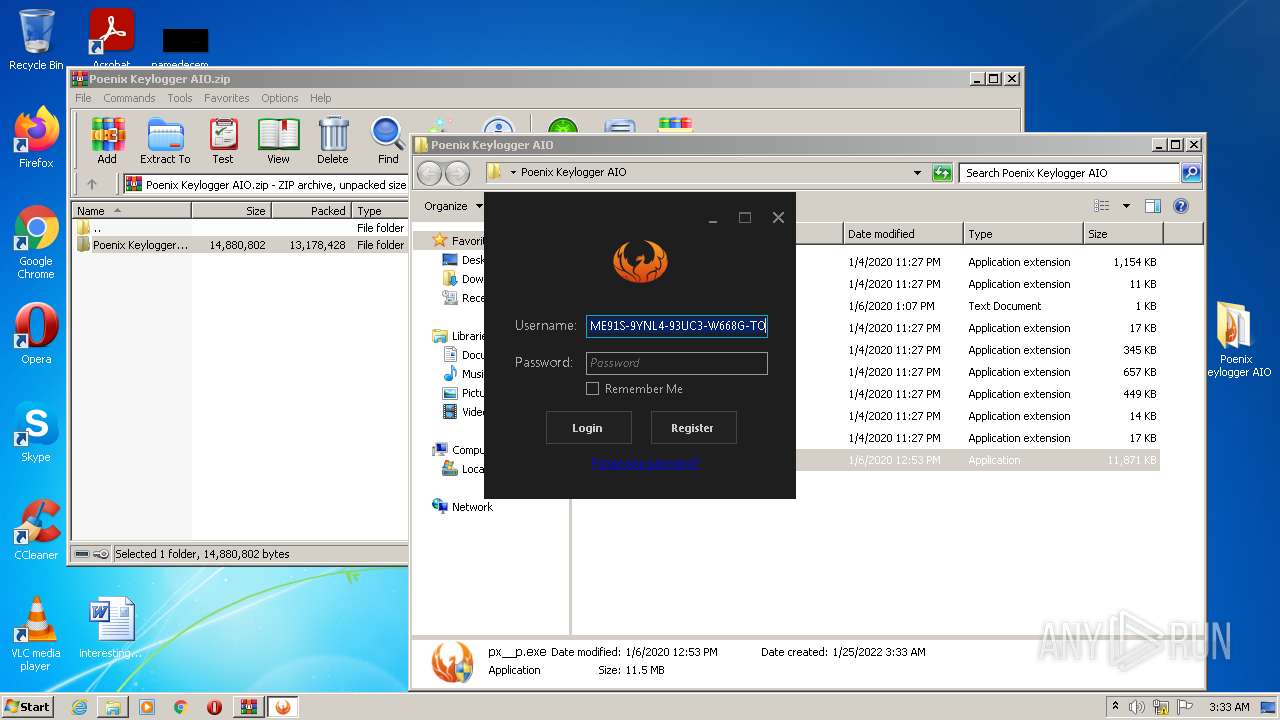
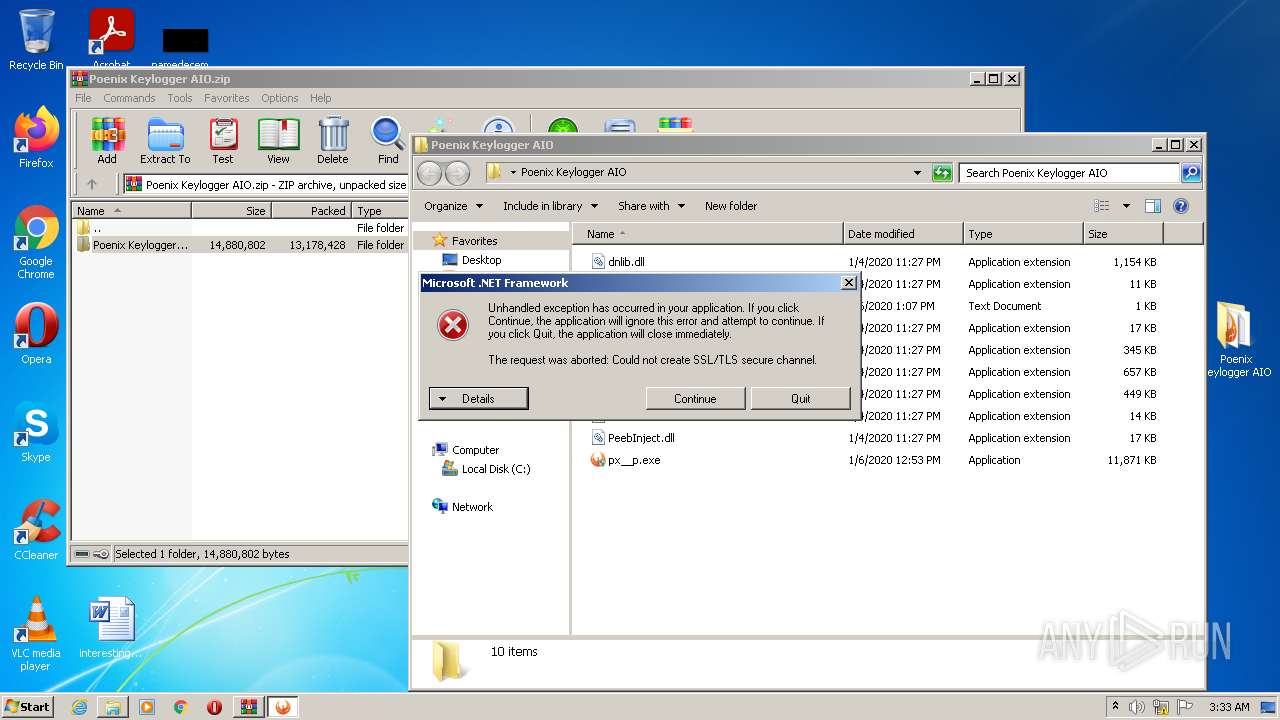
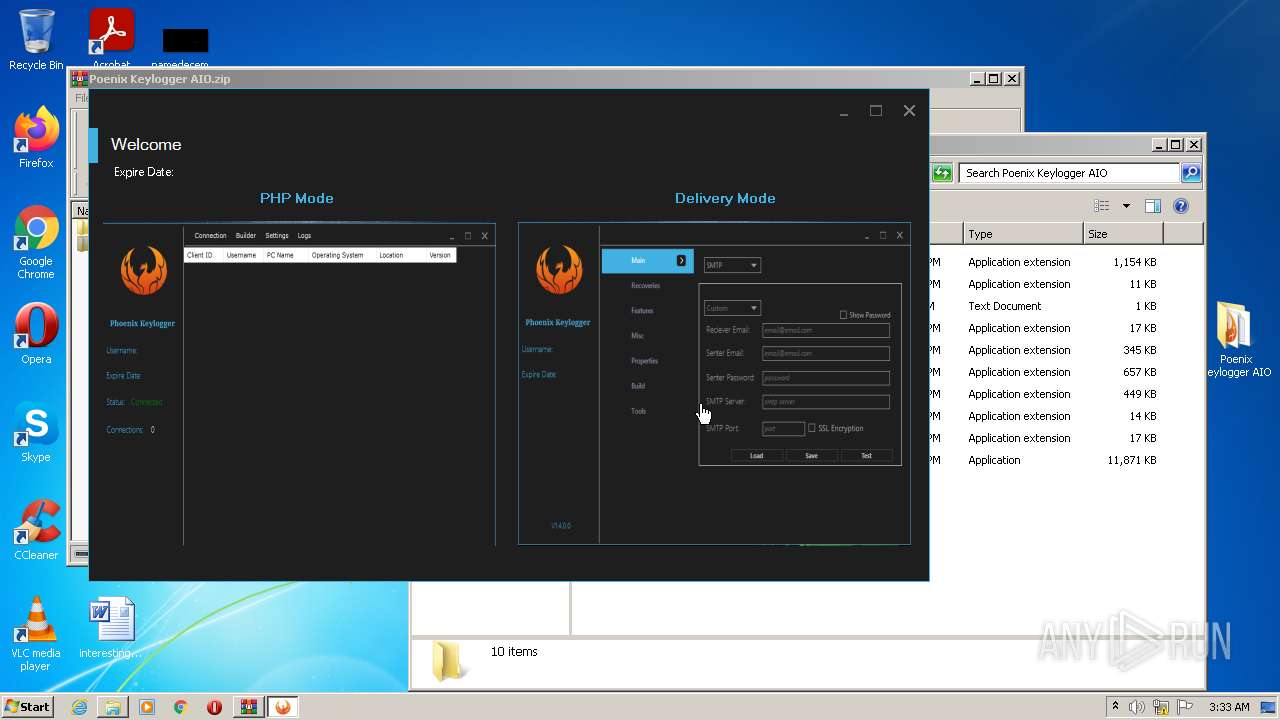
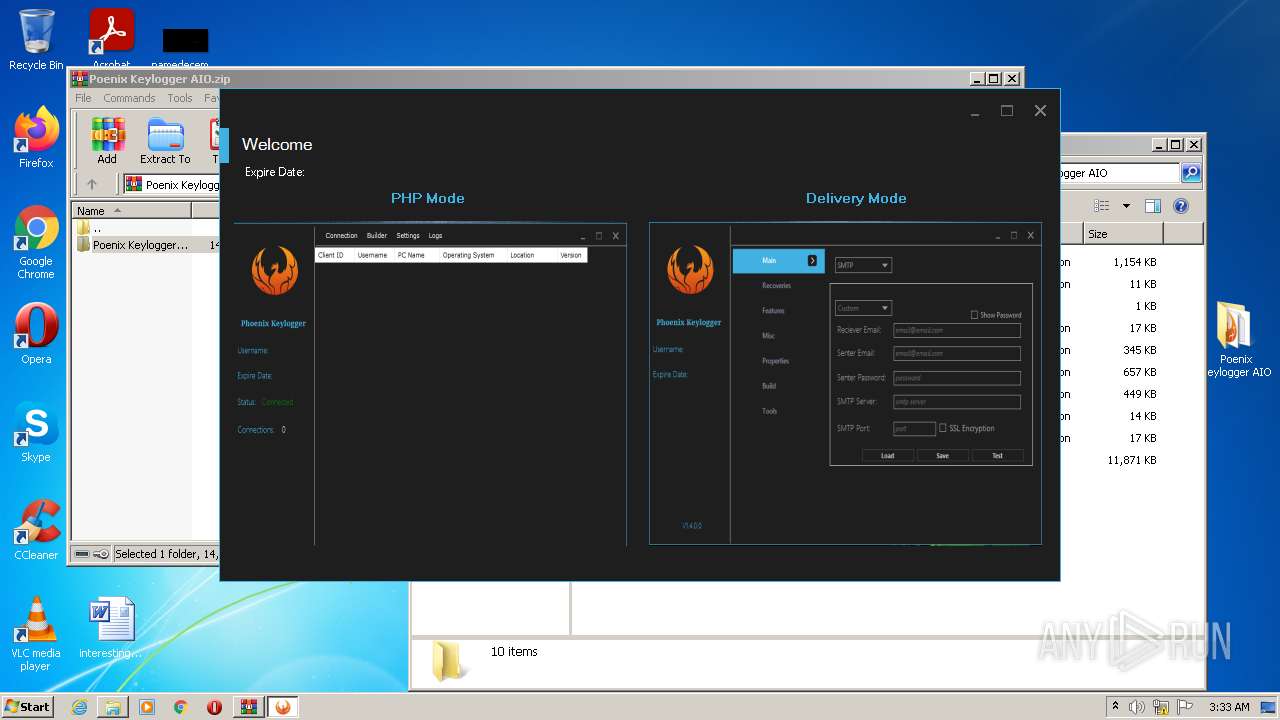
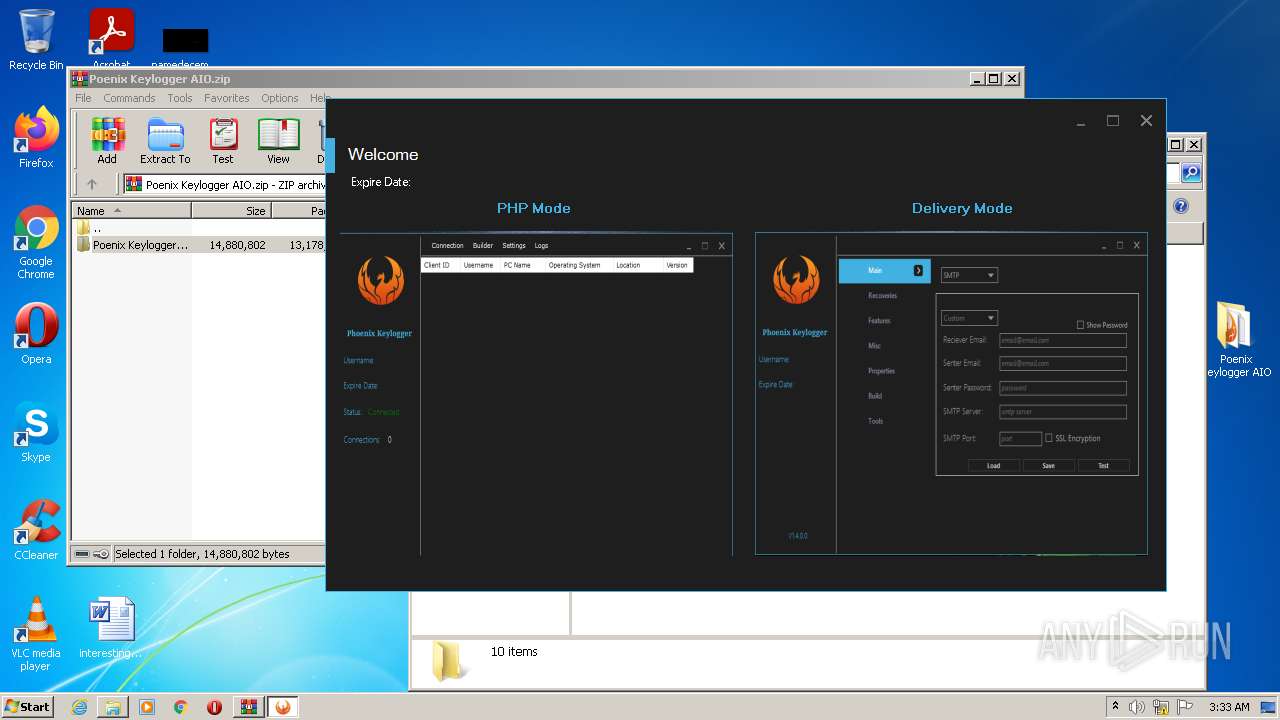
| 2088 | "C:\Users\admin\Desktop\Poenix Keylogger AIO\px__p.exe" | C:\Users\admin\Desktop\Poenix Keylogger AIO\px__p.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Phoenix Keylogger Integrity Level: MEDIUM Description: Phoenix Keylogger Exit code: 3221226540 Version: 2.1.0.0 Modules
| |||||||||||||||
| 2252 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Poenix Keylogger AIO.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2716 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2912 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" /noconfig @"C:\Users\admin\AppData\Local\Temp\hl3iyhcv.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | px__p.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 0 Version: 12.0.51209.34209 Modules
| |||||||||||||||
| 3368 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3388 | "C:\Users\admin\Desktop\Poenix Keylogger AIO\px__p.exe" | C:\Users\admin\Desktop\Poenix Keylogger AIO\px__p.exe | Explorer.EXE | ||||||||||||
User: admin Company: Phoenix Keylogger Integrity Level: HIGH Description: Phoenix Keylogger Exit code: 3489660927 Version: 2.1.0.0 Modules
| |||||||||||||||
Total events
11 561
Read events
11 178
Write events
380
Delete events
3
Modification events
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Poenix Keylogger AIO.zip | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
41
Suspicious files
1
Text files
4
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2252.26721\Poenix Keylogger AIO\dnlib.dll | executable | |
MD5:754A721EE1F1869394EC24212BBD7F30 | SHA256:A07EAF627F7CE270B0622DAD29BFCD6F8A9BC49701802F4ED2455FFEE7BC7307 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2252.26721\Poenix Keylogger AIO\IconExtractor.dll | executable | |
MD5:36B46C48D2FBCDF839F0BB96BA20B386 | SHA256:02707BE9D1E86187D99ED2DC91DF6335D093FBEC1EE4B65B5DC16161615EC2F9 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2252.26721\Poenix Keylogger AIO\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2252.26721\Poenix Keylogger AIO\MetroFramework.Fonts.dll | executable | |
MD5:65EF4B23060128743CEF937A43B82AA3 | SHA256:C843869AACA5135C2D47296985F35C71CA8AF4431288D04D481C4E46CC93EE26 | |||
| 3388 | px__p.exe | C:\Users\admin\AppData\Local\Temp\evb134A.tmp | executable | |
MD5:027EE45A325FACECD60B7DCF0A231196 | SHA256:14B9EA677E7A13A3EEDBE1DCAD830BC558E85C1DAEE864EC0E81021984FFDC16 | |||
| 3388 | px__p.exe | C:\Users\admin\AppData\Local\Temp\evb135A.tmp | executable | |
MD5:027EE45A325FACECD60B7DCF0A231196 | SHA256:14B9EA677E7A13A3EEDBE1DCAD830BC558E85C1DAEE864EC0E81021984FFDC16 | |||
| 3388 | px__p.exe | C:\Users\admin\AppData\Local\Temp\evb13FB.tmp | executable | |
MD5:5432FD5BE3C50427082EE5CE5029D019 | SHA256:2F411C2B6935C46E2877AC1FA0BAB8D1B0FA481DA890B10A2B0133424709A795 | |||
| 3388 | px__p.exe | C:\Users\admin\AppData\Local\Temp\evb145A.tmp | executable | |
MD5:F42B53932C92BFF192EAEE9349845421 | SHA256:FF9B106F1B6B72881AACDE0AB84CEF2BB5870E57F6A0459EA7DD15D3CDBCD65E | |||
| 3388 | px__p.exe | C:\Users\admin\AppData\Local\Temp\evb12DB.tmp | executable | |
MD5:36D9EF4953829179CD761082AF4A0A0B | SHA256:69877C41BA6C6794C498587D668A94C152220CE8A1F6A2BF4E6F5F7E973051E6 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2252.26721\Poenix Keylogger AIO\px__p.exe | executable | |
MD5:321DE682F6FCB7C88CDD83479A0CEBA1 | SHA256:DCEBBEA9617554DB744B97DCE95B5B55154130F1CDE5E155B677D20CFE2D712E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3388 | px__p.exe | 104.26.3.183:443 | cracked.to | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cracked.to |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |