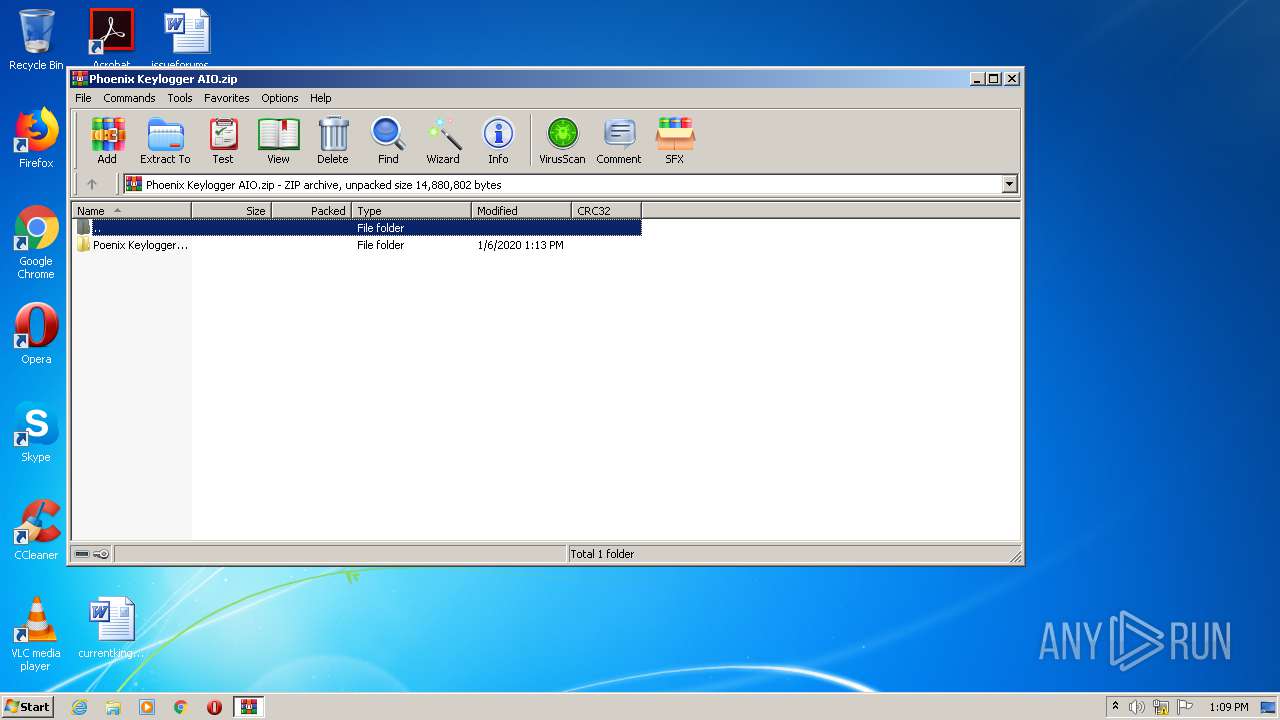
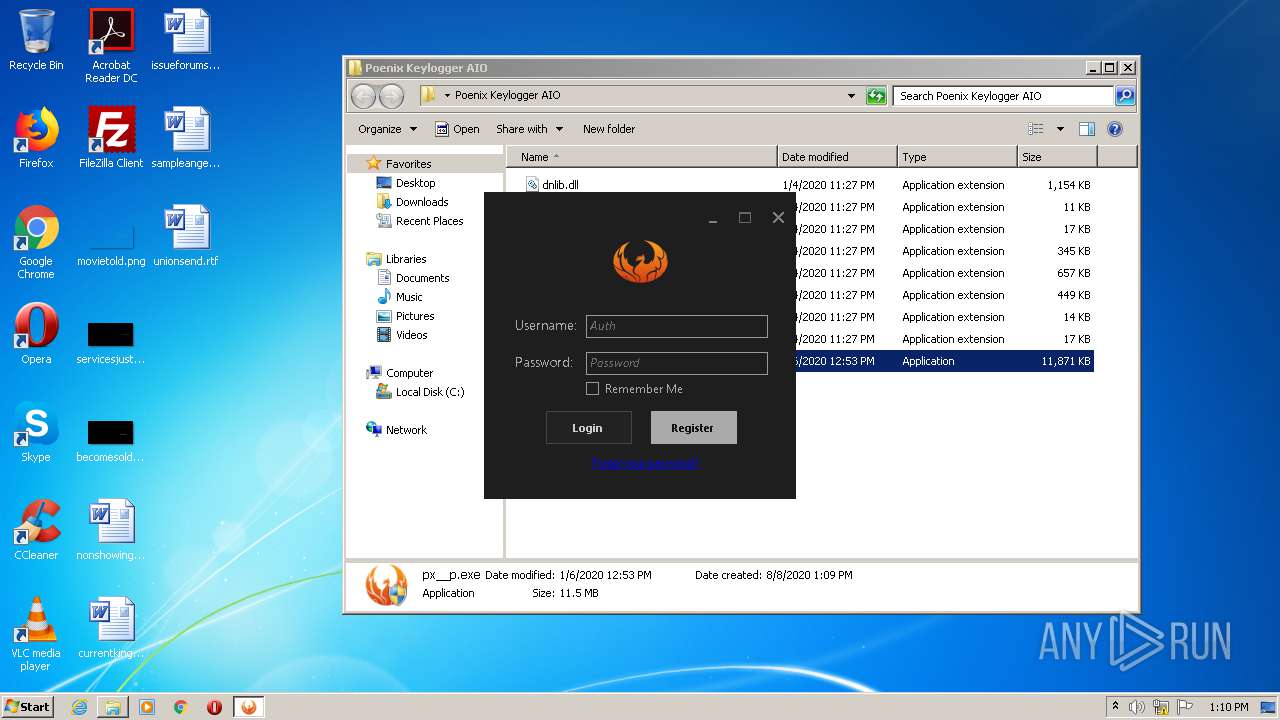
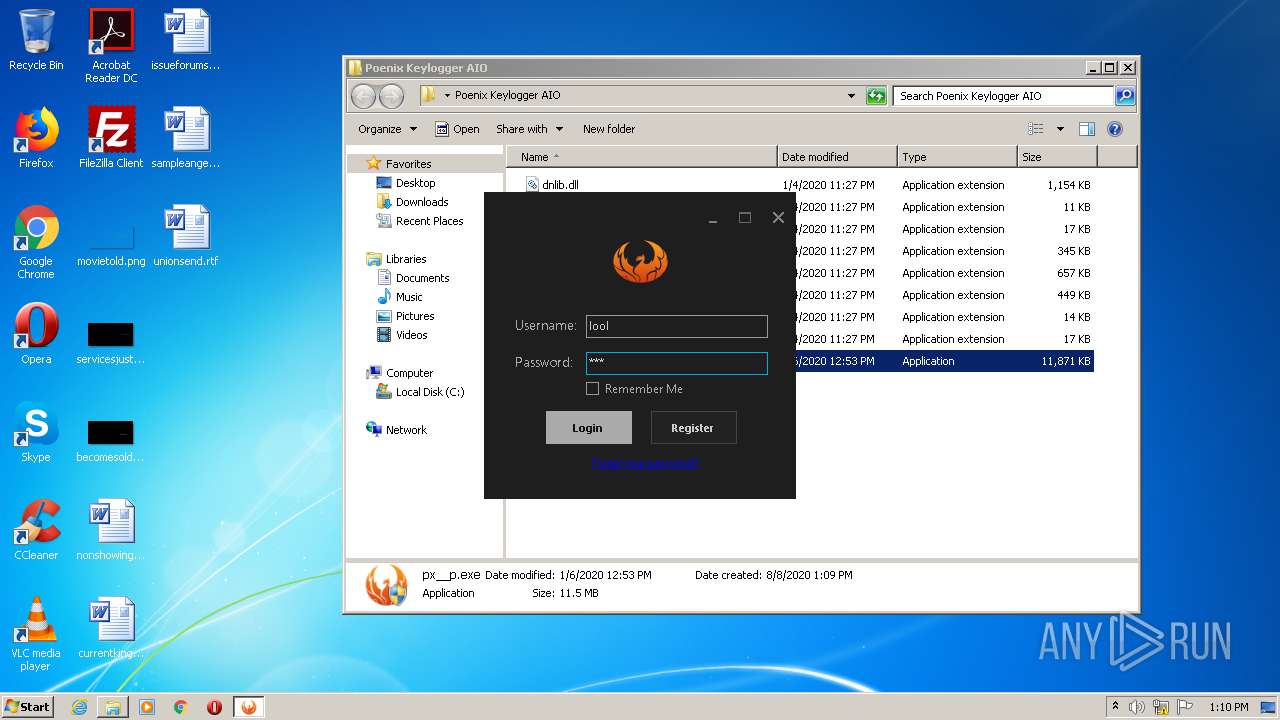
| File name: | Phoenix Keylogger AIO.zip |
| Full analysis: | https://app.any.run/tasks/91b91359-a93c-485f-a6ef-a9544935f438 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2020, 12:09:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8A661305BC62C4EE76EAEF71C9965BDC |
| SHA1: | 9F01A1DA2AF1002B0930A664D0043E5C79E501AC |
| SHA256: | DF9ECD91B0D24A1D0AD7F75A48D32DFEB9DD2453005C7A42BDF9B49C81A33DD5 |
| SSDEEP: | 196608:XyP8g/e62p1vo+zBYcOHx52yF0ev9+9rGdUlufPV4ZCK46qYfgFbaqJH4YafJ27r:ie68hVdXwUiUlunuh46IaqLATEP |
MALICIOUS
No malicious indicators.SUSPICIOUS
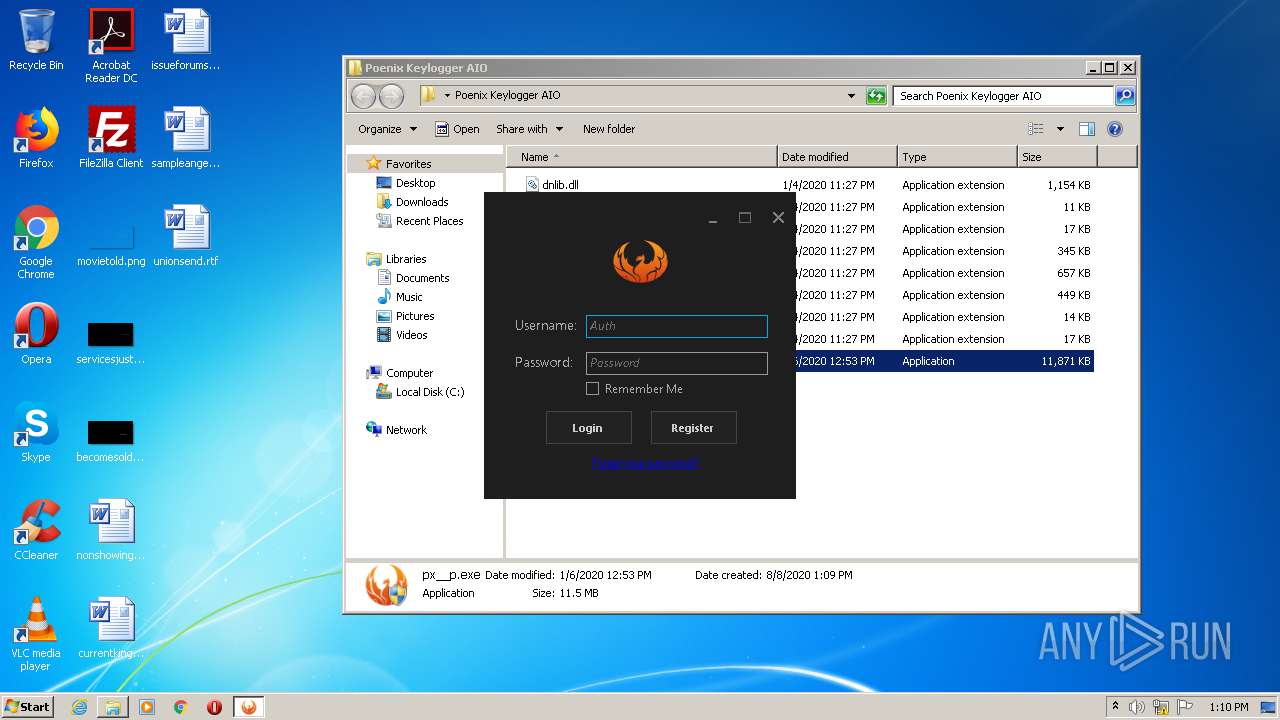
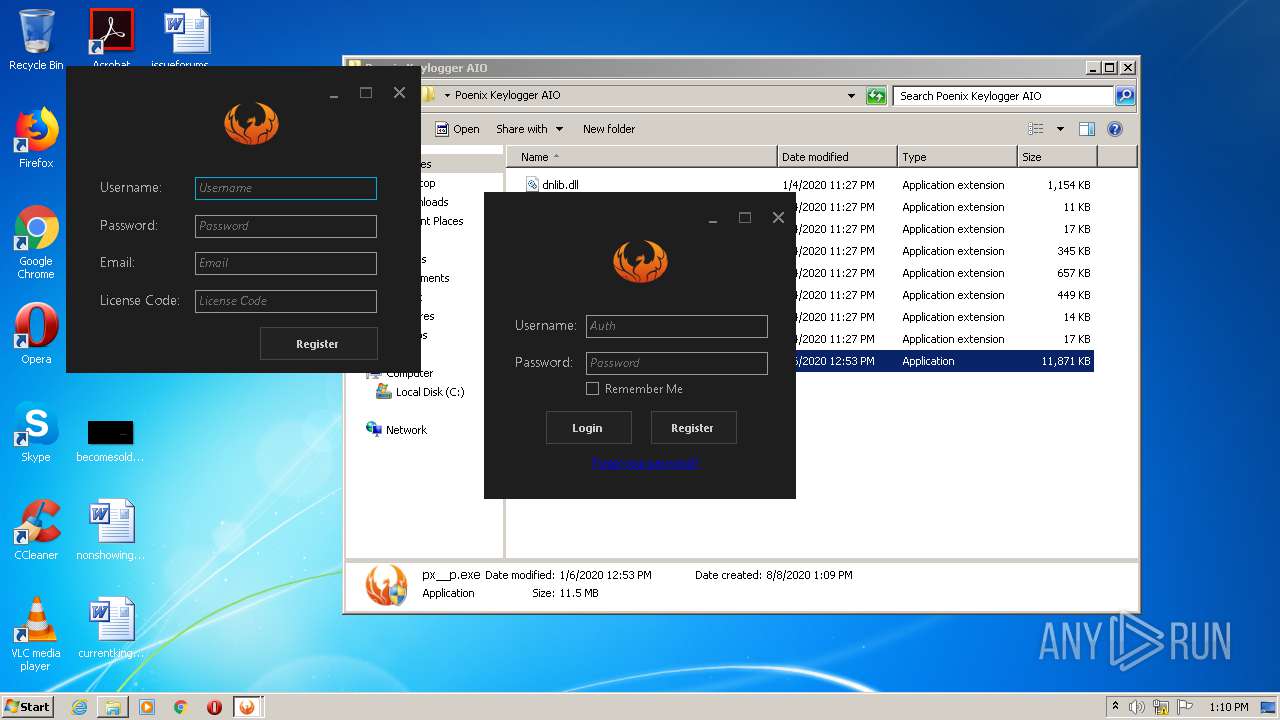
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1852)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:01:06 14:13:05 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Poenix Keylogger AIO/ |
Total processes
41
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1852 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Phoenix Keylogger AIO.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
447
Read events
427
Write events
20
Delete events
0
Modification events
| (PID) Process: | (1852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1852) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1852) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Phoenix Keylogger AIO.zip | |||
| (PID) Process: | (1852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
7
Suspicious files
0
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
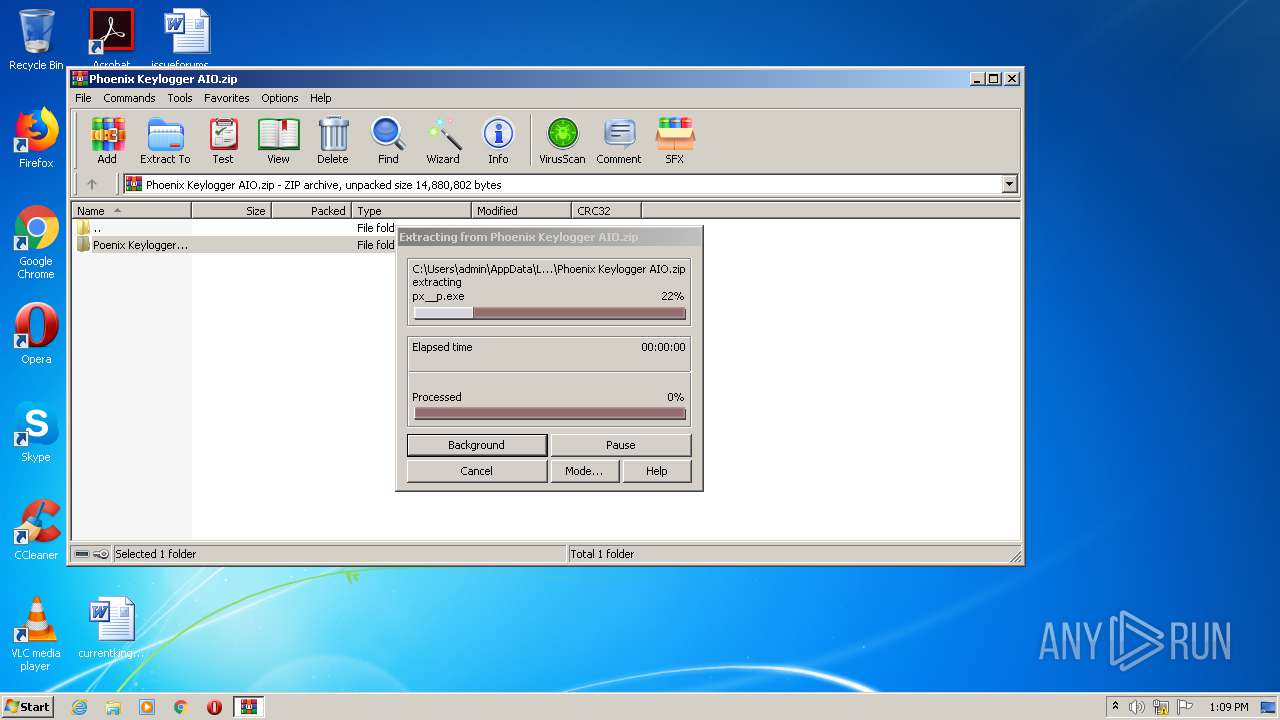
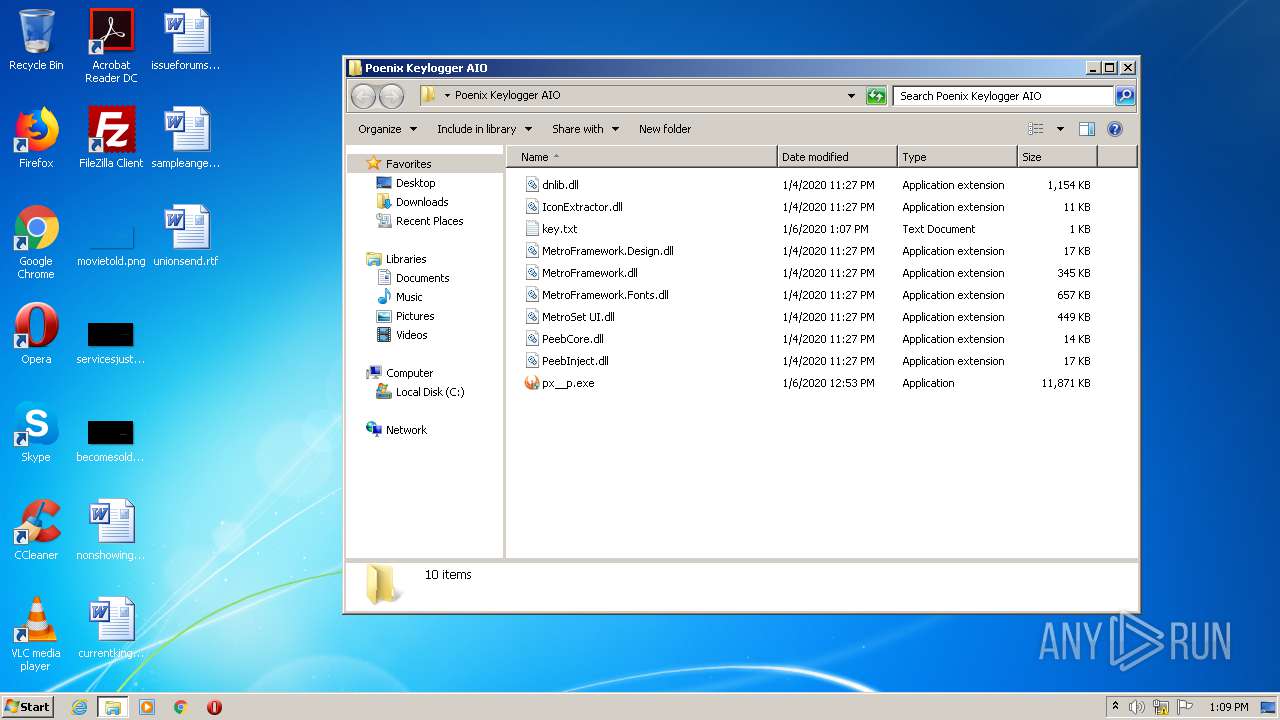
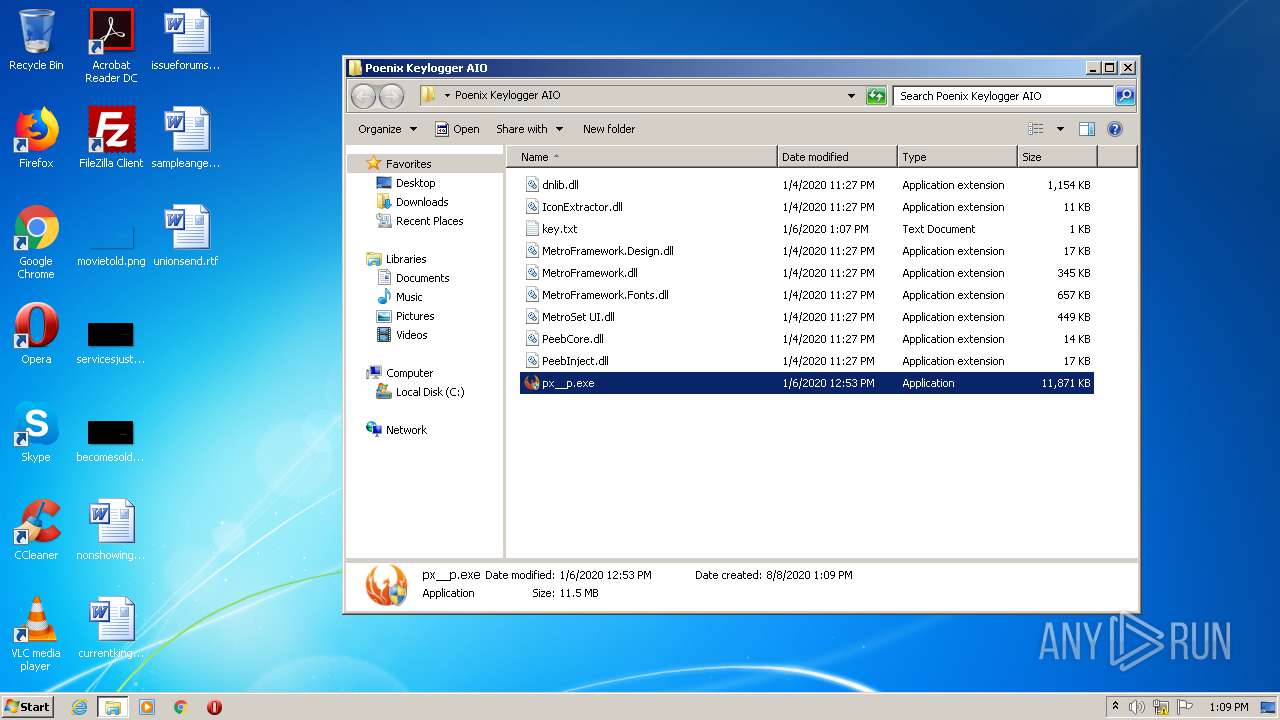
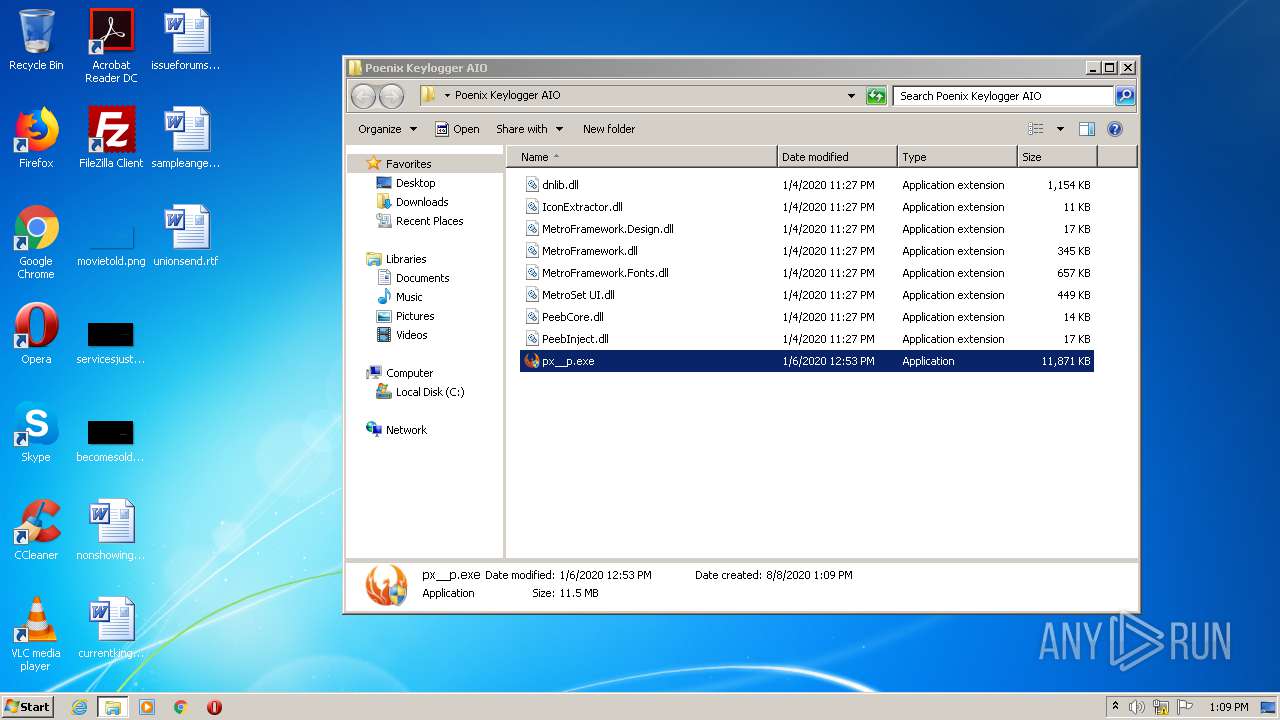
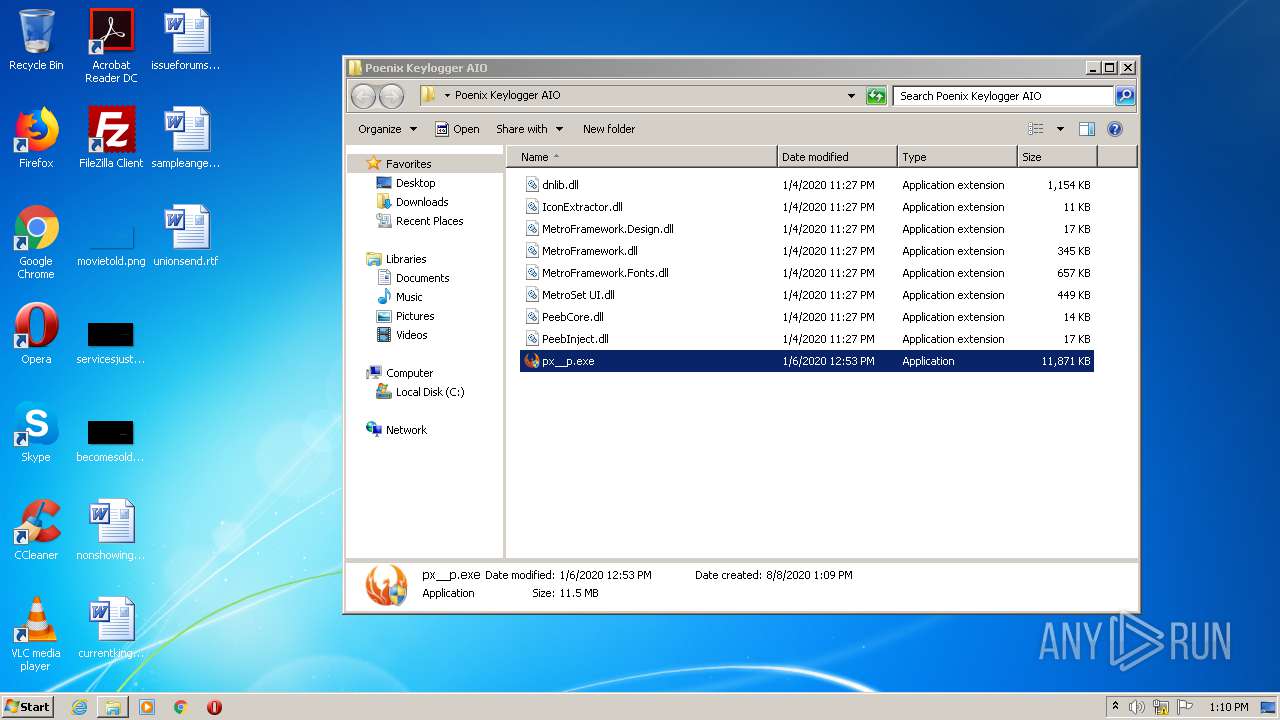
| 1852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1852.40533\Poenix Keylogger AIO\px__p.exe | — | |
MD5:— | SHA256:— | |||
| 1852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1852.40533\Poenix Keylogger AIO\IconExtractor.dll | executable | |
MD5:36B46C48D2FBCDF839F0BB96BA20B386 | SHA256:02707BE9D1E86187D99ED2DC91DF6335D093FBEC1EE4B65B5DC16161615EC2F9 | |||
| 1852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1852.40533\Poenix Keylogger AIO\dnlib.dll | executable | |
MD5:754A721EE1F1869394EC24212BBD7F30 | SHA256:A07EAF627F7CE270B0622DAD29BFCD6F8A9BC49701802F4ED2455FFEE7BC7307 | |||
| 1852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1852.40533\Poenix Keylogger AIO\MetroFramework.dll | executable | |
MD5:34EA7F7D66563F724318E322FF08F4DB | SHA256:C2C12D31B4844E29DE31594FC9632A372A553631DE0A0A04C8AF91668E37CF49 | |||
| 1852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1852.40533\Poenix Keylogger AIO\MetroSet UI.dll | odttf | |
MD5:996E8CA6FFB661DB1822B8EE73A49391 | SHA256:D405509CDD2B02CE0BD3E2087EEB9F55644B25C6269F743FF1F1B3BD0DAD526E | |||
| 1852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1852.40533\Poenix Keylogger AIO\PeebInject.dll | executable | |
MD5:CD1BC91ABAD8FE738EC3A8BCF1E7CE39 | SHA256:B0E5B2903F7CA67D36151BB8F90999E9F9598F932EC1FFFC200362206753112D | |||
| 1852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1852.40533\Poenix Keylogger AIO\PeebCore.dll | executable | |
MD5:128A51A403DDD07999E03E3A36D96579 | SHA256:90F882851DF247E60CEF36644E63A7927B243FC8F81B5CCB1ECFF8E9564D81F2 | |||
| 1852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1852.40533\Poenix Keylogger AIO\MetroFramework.Fonts.dll | executable | |
MD5:65EF4B23060128743CEF937A43B82AA3 | SHA256:C843869AACA5135C2D47296985F35C71CA8AF4431288D04D481C4E46CC93EE26 | |||
| 1852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1852.40533\Poenix Keylogger AIO\key.txt | text | |
MD5:F85BED186EDCDA64396F03C39C0CEAD3 | SHA256:FE5A222BEF09901D2391BC64951E0514A7BBE5ACC562034D428305557AC37D20 | |||
| 1852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1852.40533\Poenix Keylogger AIO\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
5
DNS requests
4
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.186.35:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
— | — | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgTGNgjpefMY157Oz%2FQTDDtD7g%3D%3D | unknown | der | 527 b | whitelisted |
— | — | GET | 200 | 88.221.141.19:80 | http://cert.int-x3.letsencrypt.org/ | US | der | 1.15 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.100.87.106:443 | cracked.to | Flokinet Ltd | RO | suspicious |
— | — | 88.221.141.19:80 | cert.int-x3.letsencrypt.org | Akamai International B.V. | US | unknown |
— | — | 2.16.186.35:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
— | — | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cracked.to |
| whitelisted |
cert.int-x3.letsencrypt.org |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |