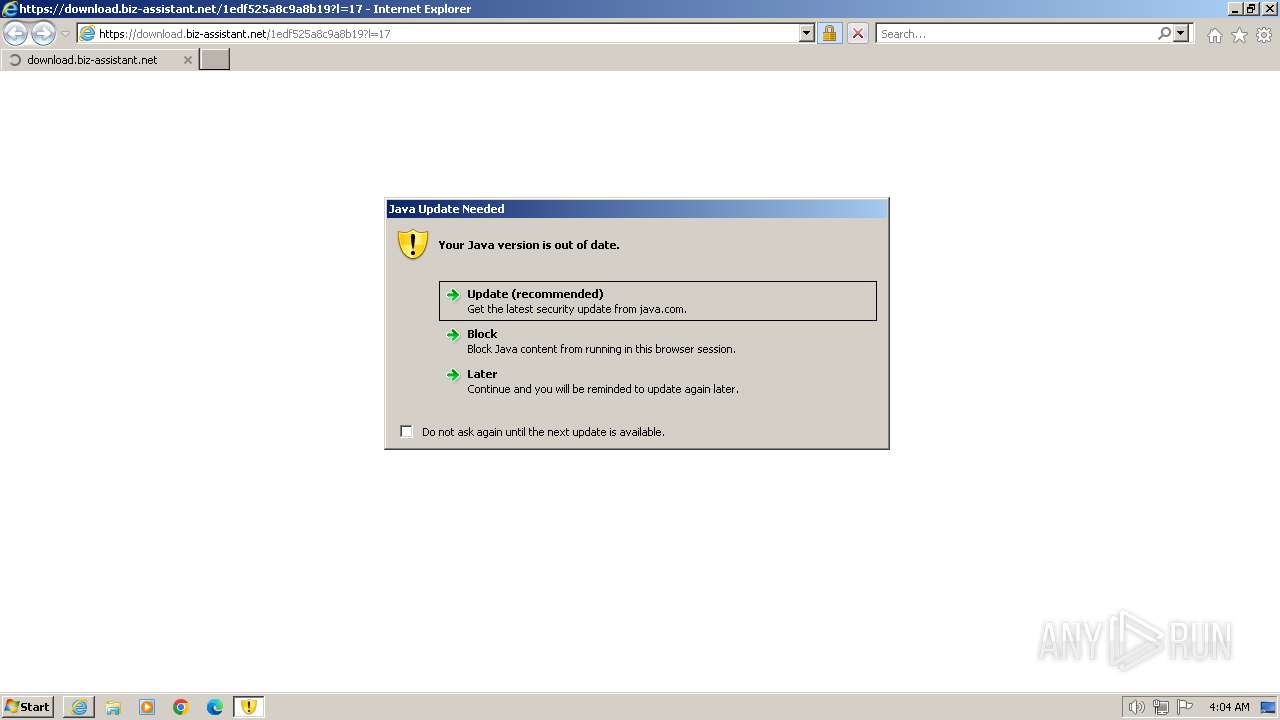
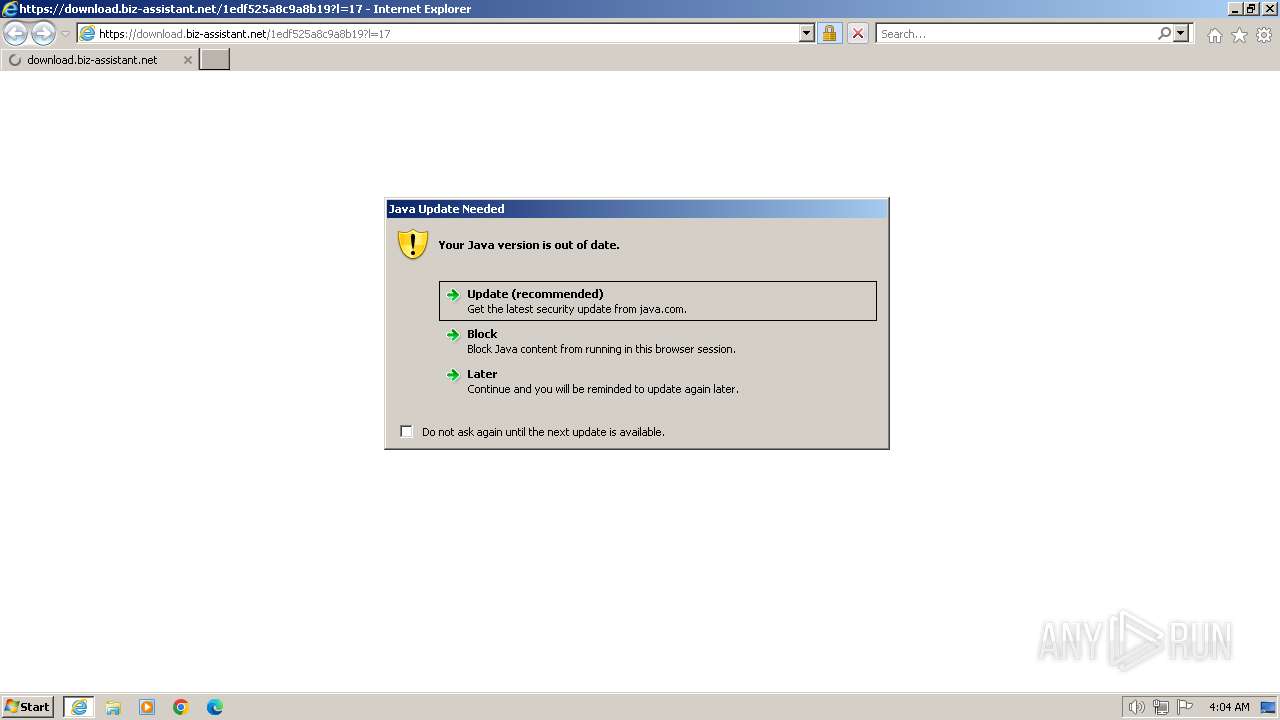
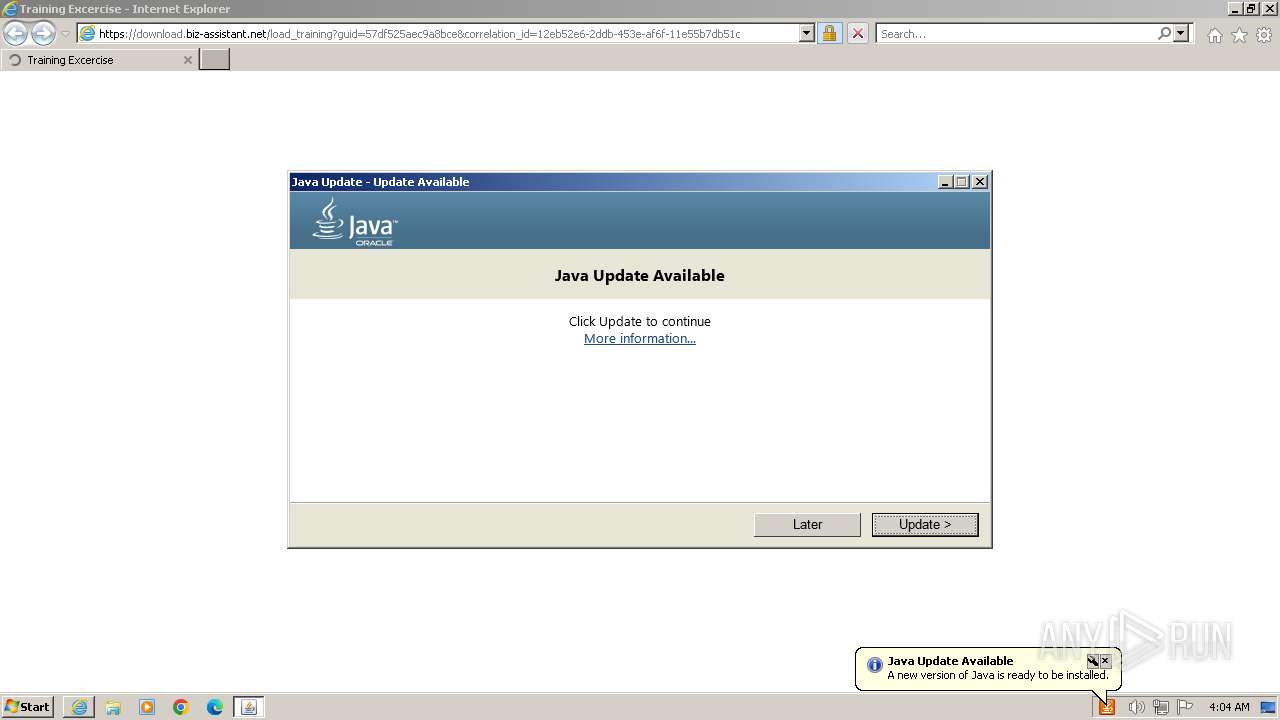
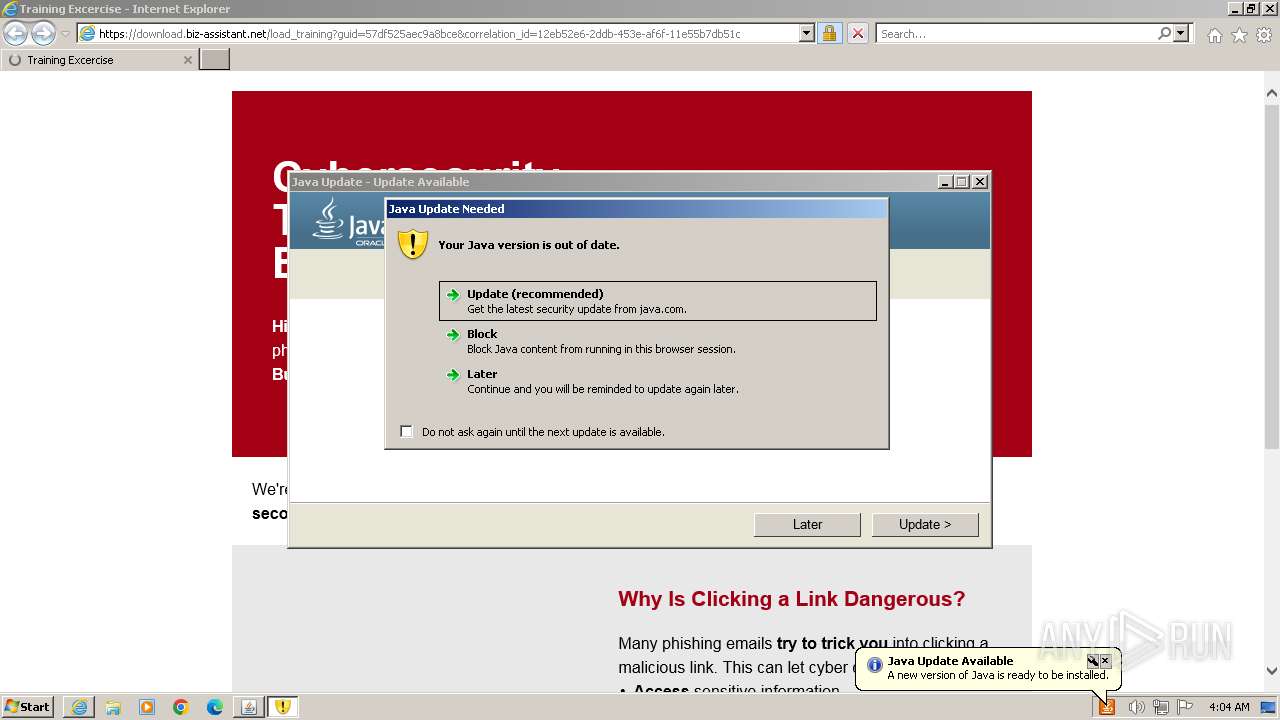
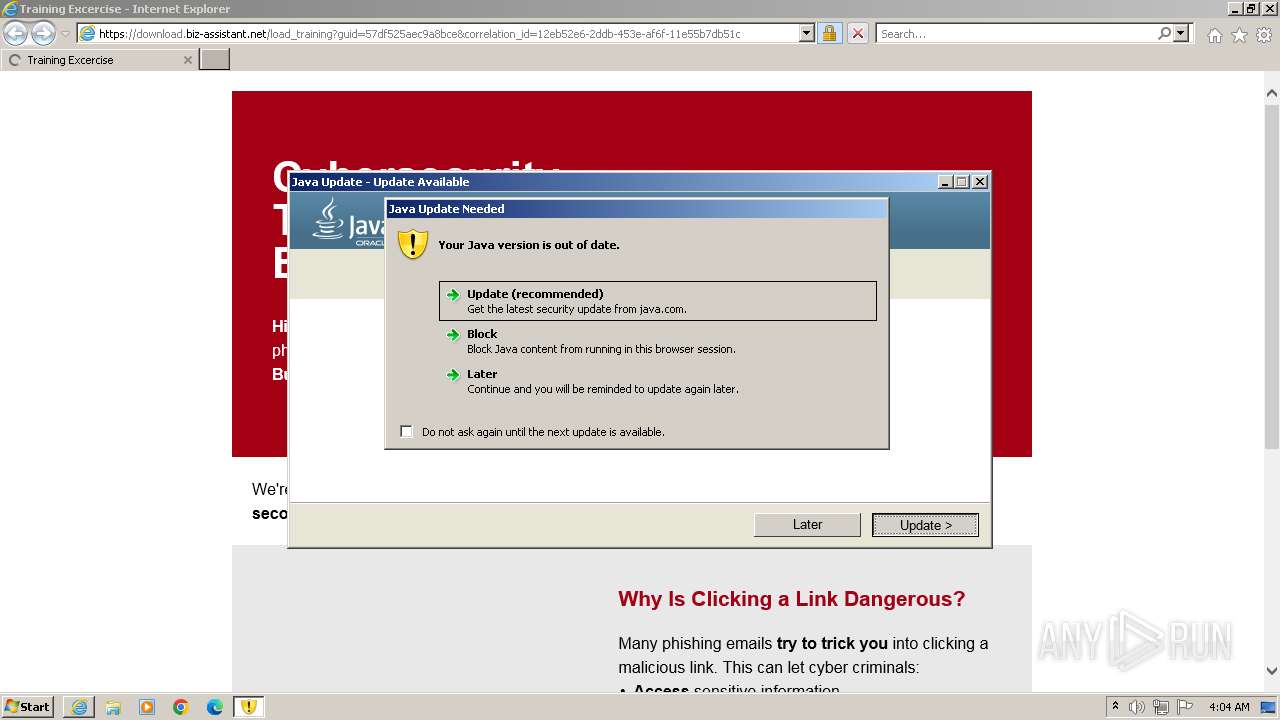
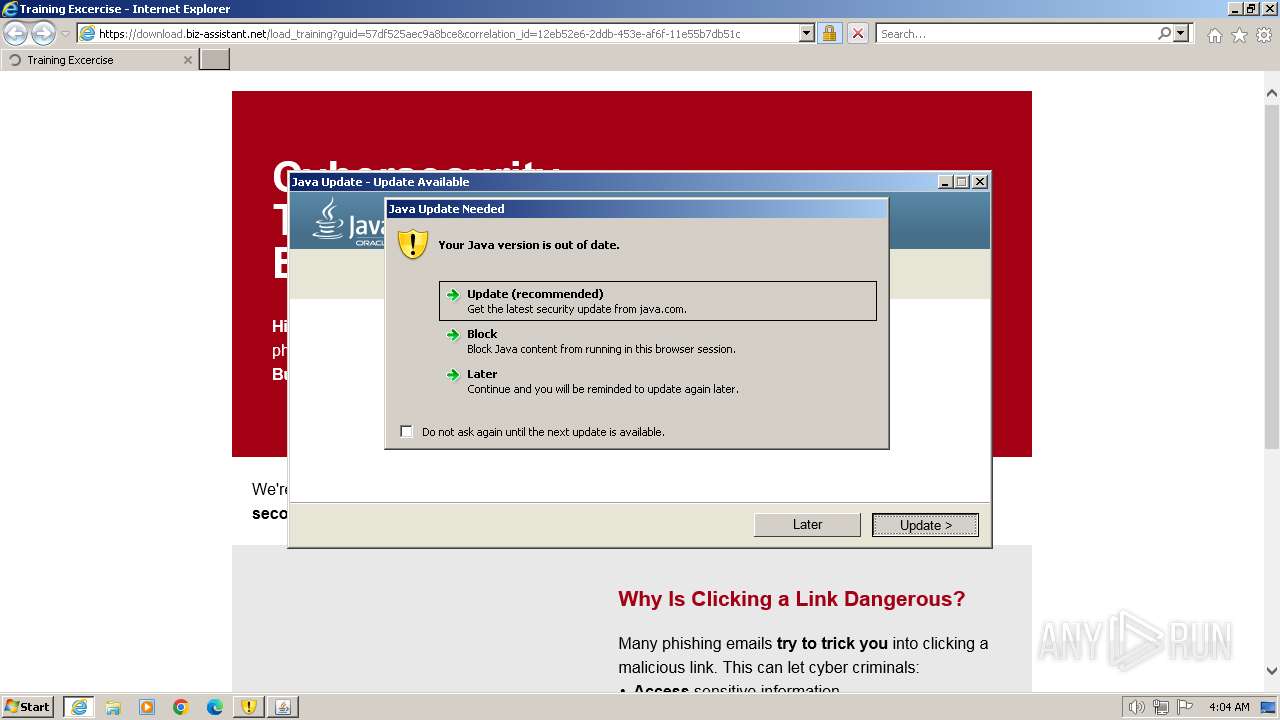
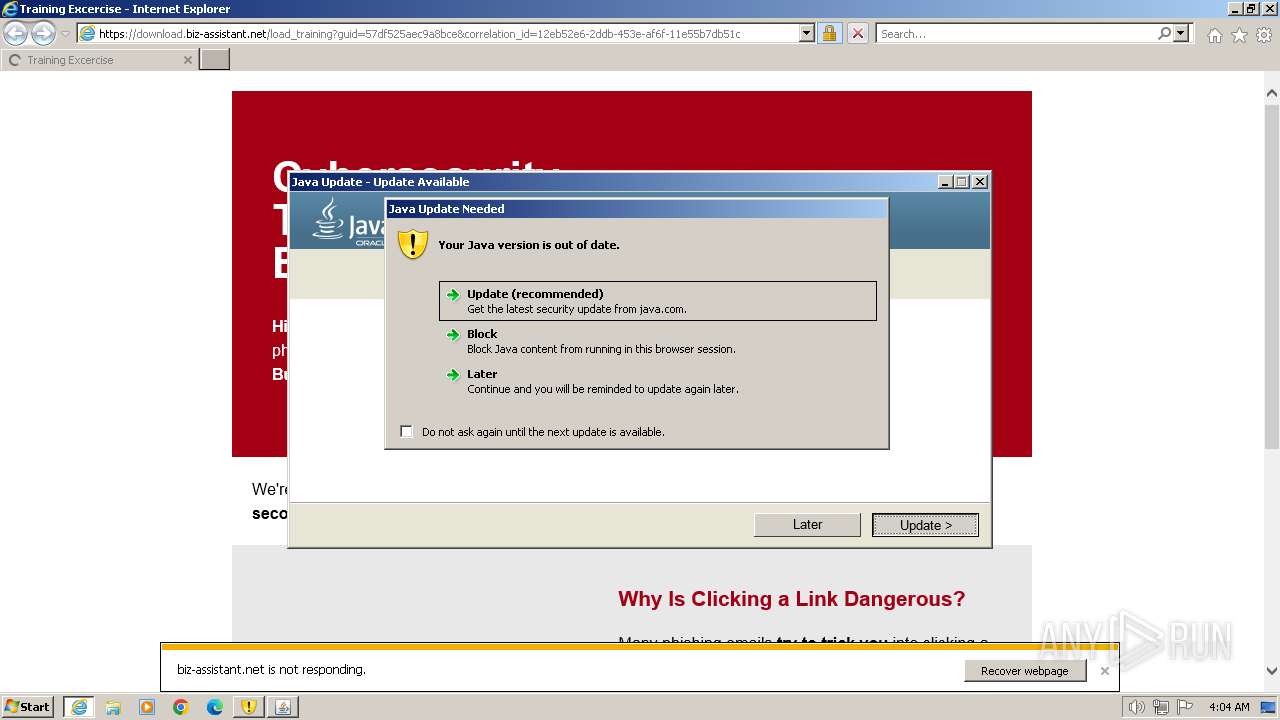
| URL: | https://download.biz-assistant.net/1edf525a8c9a8b19?l=17 |
| Full analysis: | https://app.any.run/tasks/1e3c5143-3175-40e3-834f-8dec010fefd9 |
| Verdict: | Malicious activity |
| Analysis date: | March 09, 2024, 04:03:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8E6793A9CEBE8857F9BA4AC9C47A3FF5 |
| SHA1: | 88226260FFA016551E1539414B41F2260B70F991 |
| SHA256: | DF849E135A8AE6B3FB919A41AE0B2E4BF268A8548FE79D7B7D87E38CA6523755 |
| SSDEEP: | 3:N8SElsfIEWLDlIKBW7wb:2SK3EqDlbEwb |
MALICIOUS
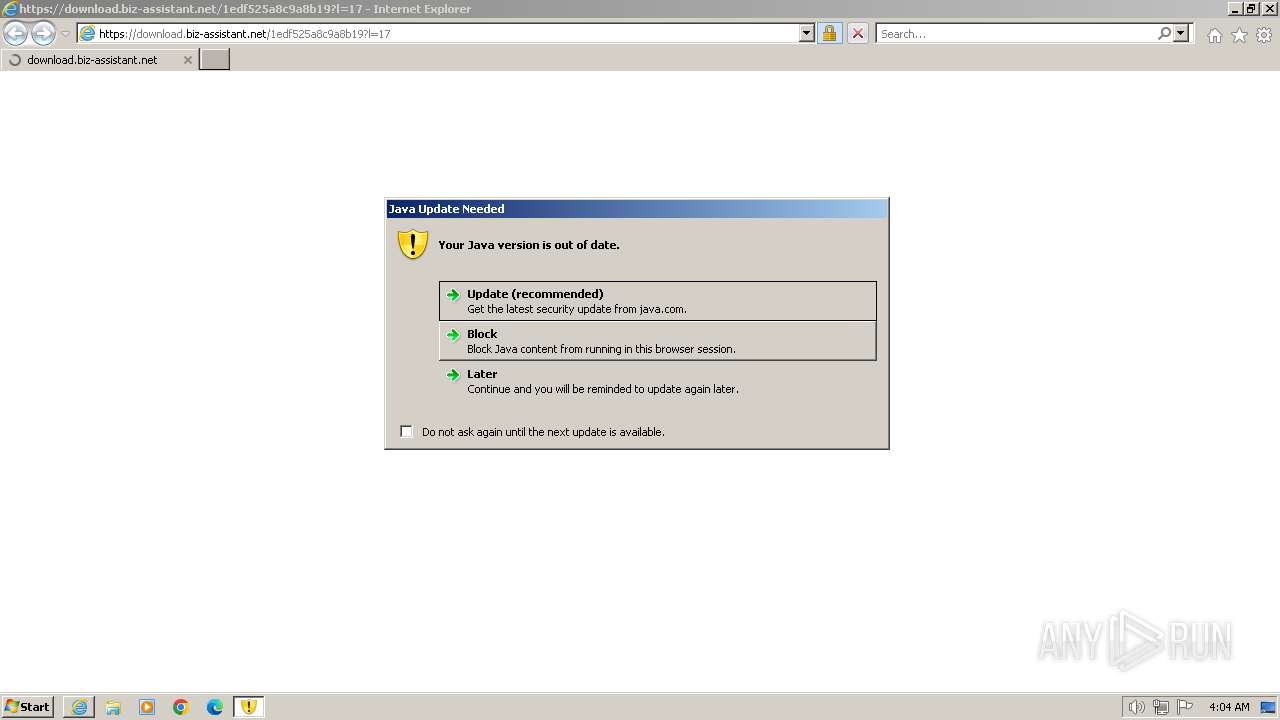
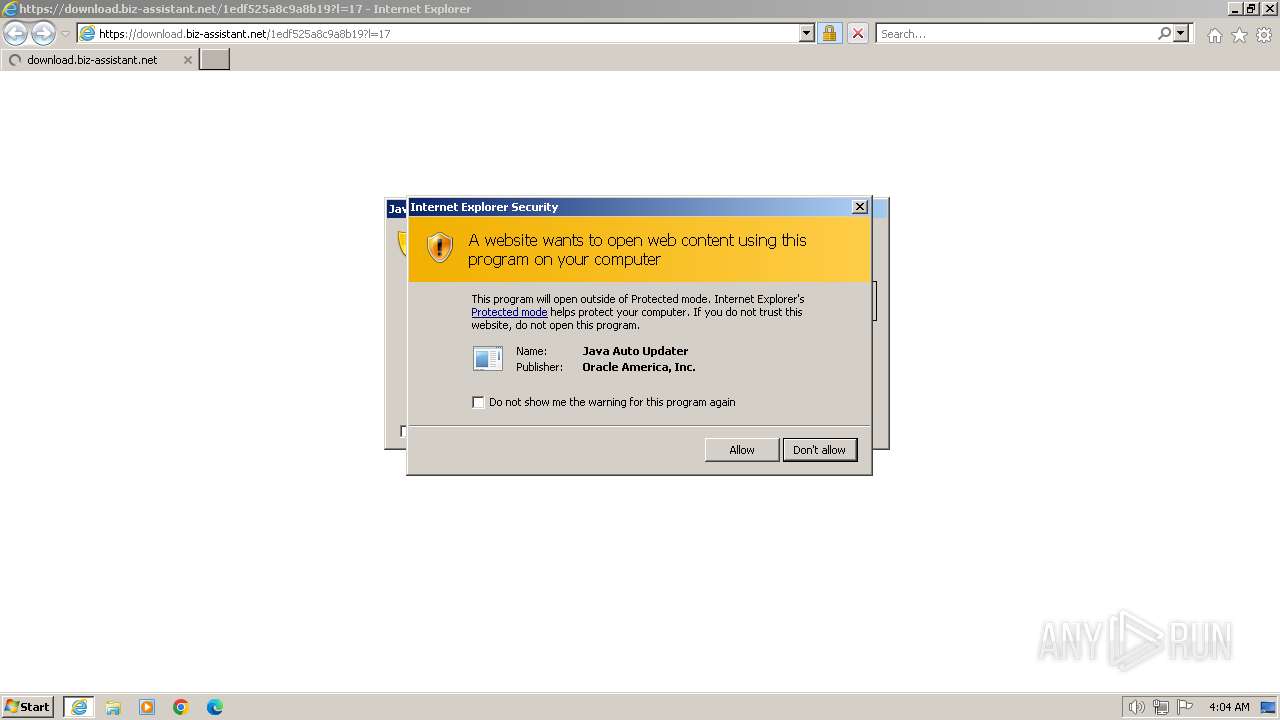
Drops the executable file immediately after the start
- jucheck.exe (PID: 2060)
- jre-8u401-windows-au.exe (PID: 2956)
SUSPICIOUS
Checks for Java to be installed
- javaw.exe (PID: 2908)
- jp2launcher.exe (PID: 2692)
- javaw.exe (PID: 2000)
- javaw.exe (PID: 3684)
- jucheck.exe (PID: 2060)
- jp2launcher.exe (PID: 2744)
- jp2launcher.exe (PID: 2404)
- jre-8u401-windows-au.exe (PID: 3272)
Reads the Internet Settings
- jucheck.exe (PID: 2060)
- jp2launcher.exe (PID: 2744)
- jre-8u401-windows-au.exe (PID: 3272)
Reads security settings of Internet Explorer
- jucheck.exe (PID: 2060)
- jp2launcher.exe (PID: 2744)
- jre-8u401-windows-au.exe (PID: 3272)
Checks Windows Trust Settings
- jucheck.exe (PID: 2060)
- jre-8u401-windows-au.exe (PID: 3272)
Reads settings of System Certificates
- jucheck.exe (PID: 2060)
- jp2launcher.exe (PID: 2744)
- jre-8u401-windows-au.exe (PID: 3272)
Reads Microsoft Outlook installation path
- jucheck.exe (PID: 2060)
- jre-8u401-windows-au.exe (PID: 3272)
Reads Internet Explorer settings
- jucheck.exe (PID: 2060)
- jre-8u401-windows-au.exe (PID: 3272)
Executable content was dropped or overwritten
- jucheck.exe (PID: 2060)
- jre-8u401-windows-au.exe (PID: 2956)
INFO
Checks supported languages
- jp2launcher.exe (PID: 2692)
- javaw.exe (PID: 3684)
- javaw.exe (PID: 2908)
- javaw.exe (PID: 2000)
- jucheck.exe (PID: 2060)
- jp2launcher.exe (PID: 2744)
- javaws.exe (PID: 1900)
- jp2launcher.exe (PID: 2404)
- jre-8u401-windows-au.exe (PID: 2956)
- jre-8u401-windows-au.exe (PID: 3272)
Application launched itself
- iexplore.exe (PID: 3864)
Connects to unusual port
- iexplore.exe (PID: 3952)
Create files in a temporary directory
- javaw.exe (PID: 2908)
- javaw.exe (PID: 3684)
- javaw.exe (PID: 2000)
- jucheck.exe (PID: 2060)
- jp2launcher.exe (PID: 2744)
- jre-8u401-windows-au.exe (PID: 2956)
Reads the computer name
- javaw.exe (PID: 2908)
- javaw.exe (PID: 3684)
- javaw.exe (PID: 2000)
- jucheck.exe (PID: 2060)
- jp2launcher.exe (PID: 2744)
- jre-8u401-windows-au.exe (PID: 2956)
- jre-8u401-windows-au.exe (PID: 3272)
Creates files in the program directory
- javaw.exe (PID: 2908)
Reads the machine GUID from the registry
- jucheck.exe (PID: 2060)
- jp2launcher.exe (PID: 2744)
- jre-8u401-windows-au.exe (PID: 3272)
Checks proxy server information
- jucheck.exe (PID: 2060)
- jp2launcher.exe (PID: 2744)
- jre-8u401-windows-au.exe (PID: 3272)
Reads the software policy settings
- jucheck.exe (PID: 2060)
- jre-8u401-windows-au.exe (PID: 3272)
Creates files or folders in the user directory
- jucheck.exe (PID: 2060)
- jp2launcher.exe (PID: 2744)
- jre-8u401-windows-au.exe (PID: 3272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
57
Monitored processes
16
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1576 | "C:\Program Files\Common Files\Java\Java Update\jucheck.exe" | C:\Program Files\Common Files\Java\Java Update\jucheck.exe | — | iexplore.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: LOW Description: Java Update Checker Exit code: 0 Version: 2.8.271.9 Modules
| |||||||||||||||
| 1900 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" -J-Djdk.disableLastUsageTracking=true -SSVBaselineUpdate | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | jucheck.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 2000 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.suppression.11.271.2" "false" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | jp2launcher.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Common Files\Java\Java Update\jucheck.exe" | C:\Program Files\Common Files\Java\Java Update\jucheck.exe | iexplore.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Update Checker Exit code: 0 Version: 2.8.271.9 Modules
| |||||||||||||||
| 2064 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2404 | "C:\PROGRA~1\Java\JRE18~1.0_2\bin\jp2launcher.exe" -sjed | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | — | iexplore.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 2560 | "C:\PROGRA~1\Java\JRE18~1.0_2\bin\jp2launcher.exe" -sjed | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | — | iexplore.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: LOW Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 2572 | "C:\PROGRA~1\Java\JRE18~1.0_2\bin\jp2launcher.exe" -sjed | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | — | iexplore.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: LOW Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 2692 | "C:\PROGRA~1\Java\JRE18~1.0_2\bin\jp2launcher.exe" -sjed | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | — | iexplore.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 1 Version: 11.271.2.09 Modules
| |||||||||||||||
| 2744 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxwbHVnaW4uamFyAC1EamRrLmRpc2FibGVMYXN0VXNhZ2VUcmFja2luZz10cnVlAC1Eam5scHguanZtPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcYmluXGphdmF3LmV4ZQAtRGpubHB4LnZtYXJncz1MVVJxWkdzdVpHbHpZV0pzWlV4aGMzUlZjMkZuWlZSeVlXTnJhVzVuUFhSeWRXVUE= -ma LVNTVkJhc2VsaW5lVXBkYXRlAC1ub3RXZWJKYXZh | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
Total events
40 924
Read events
40 309
Write events
516
Delete events
99
Modification events
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31093206 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31093206 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
4
Suspicious files
17
Text files
37
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:CC6929F1D4040566BBC3818B32B5C1DF | SHA256:39B362D50E5024ACAEAD9A50794D098FC0C87E6BFF310BD5D72CC1259C179D45 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:57FBC630D5A9CA130265DA8D94E1C5AF | SHA256:E39CCBCBD7E7AF9BDA932609B261042E13771099AD9F82D48CB71CF1E8530E84 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:C677AC7BA211DAAE5D57177574DC1E58 | SHA256:DC082A62C7BC9B0E65EB73003FBF7720AB890DE795860127F5DAFE07901A38D8 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:5F0619373E824EACD5F329910CA8B4B2 | SHA256:091A810EF87CD2D7E3FE952A2F5DC980B7D31068EEC1B03E22BEB7FB79EA21B0 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\1edf525a8c9a8b19[1].htm | html | |
MD5:AAA2161E80F4638A5E74248CB0146643 | SHA256:B45262B84807C77D8A1013A33912247E52EA883675D0BACCBFC135CAE10D73A2 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:0C49A76329DBE056B760BDF422B0A4EF | SHA256:6CA0BE7467A89049E4A84BE36ECA17D5A247BB9E5CC4D8FA34A84B4B5D8DC731 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\83D863F495E7D991917B3ABB3E1EB382_5D4D2219A09D2AC474D1CE08CC064873 | binary | |
MD5:FDDEC8E5FFA18A0AA4A76748CF09D032 | SHA256:89FDECBC800D4078EB0B9DFFAD465ACCD2443460A6C8E53A004EEFE9EE094090 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\83D863F495E7D991917B3ABB3E1EB382_5D4D2219A09D2AC474D1CE08CC064873 | binary | |
MD5:07F2533BEF431CB3104E8C75515F21D8 | SHA256:D02802B19BBA7A79ED8E79F39B3228169EE69AE2CB6E8972FD50793F822DB8FD | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:560B436811E5633AFCF65D7DF7DA5038 | SHA256:88FC4916A4720CC3CC7C0FA21850DA8F2E731CA5E65A6493EC503C6324C86CBE | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\bugsnag-2.min[1].js | text | |
MD5:85FF02DA974C920AE6BFE5F6A602183F | SHA256:9FF538F72465724FC393EA1F3C03A17233C9B7E1D440D6F8A6D0B3A836C2A9CC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
56
DNS requests
28
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3952 | iexplore.exe | GET | 200 | 108.138.2.10:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | binary | 2.02 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.49 Kb | unknown |
3952 | iexplore.exe | GET | 304 | 2.20.139.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f78d505714a595e3 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m01.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBShdVEFnSEQ0gG5CBtzM48cPMe9XwQUgbgOY4qJEhjl%2Bjs7UJWf5uWQE4UCEAttUCKs5pZVb8wIJ%2BugwJo%3D | unknown | binary | 471 b | unknown |
3864 | iexplore.exe | GET | 304 | 2.20.139.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?76ad697231f9b13b | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
3864 | iexplore.exe | GET | 304 | 2.20.139.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b23edf5cfbe16fd7 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 2.20.139.231:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?44b9e679153a488c | unknown | compressed | 67.5 Kb | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2744 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3952 | iexplore.exe | 3.105.83.130:443 | download.biz-assistant.net | AMAZON-02 | AU | unknown |
3952 | iexplore.exe | 2.20.139.235:80 | ctldl.windowsupdate.com | Akamai International B.V. | BR | unknown |
3952 | iexplore.exe | 108.138.2.10:80 | o.ss2.us | AMAZON-02 | US | unknown |
3952 | iexplore.exe | 18.245.39.64:80 | ocsp.rootg2.amazontrust.com | — | US | unknown |
3952 | iexplore.exe | 18.245.65.219:80 | ocsp.r2m03.amazontrust.com | — | US | unknown |
3952 | iexplore.exe | 3.105.83.130:49153 | download.biz-assistant.net | AMAZON-02 | AU | unknown |
3952 | iexplore.exe | 52.217.120.81:443 | tslp.s3.amazonaws.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.biz-assistant.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m03.amazontrust.com |
| unknown |
tslp.s3.amazonaws.com |
| shared |
java.com |
| whitelisted |
d2wy8f7a9ursnm.cloudfront.net |
| shared |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2744 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
2744 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |