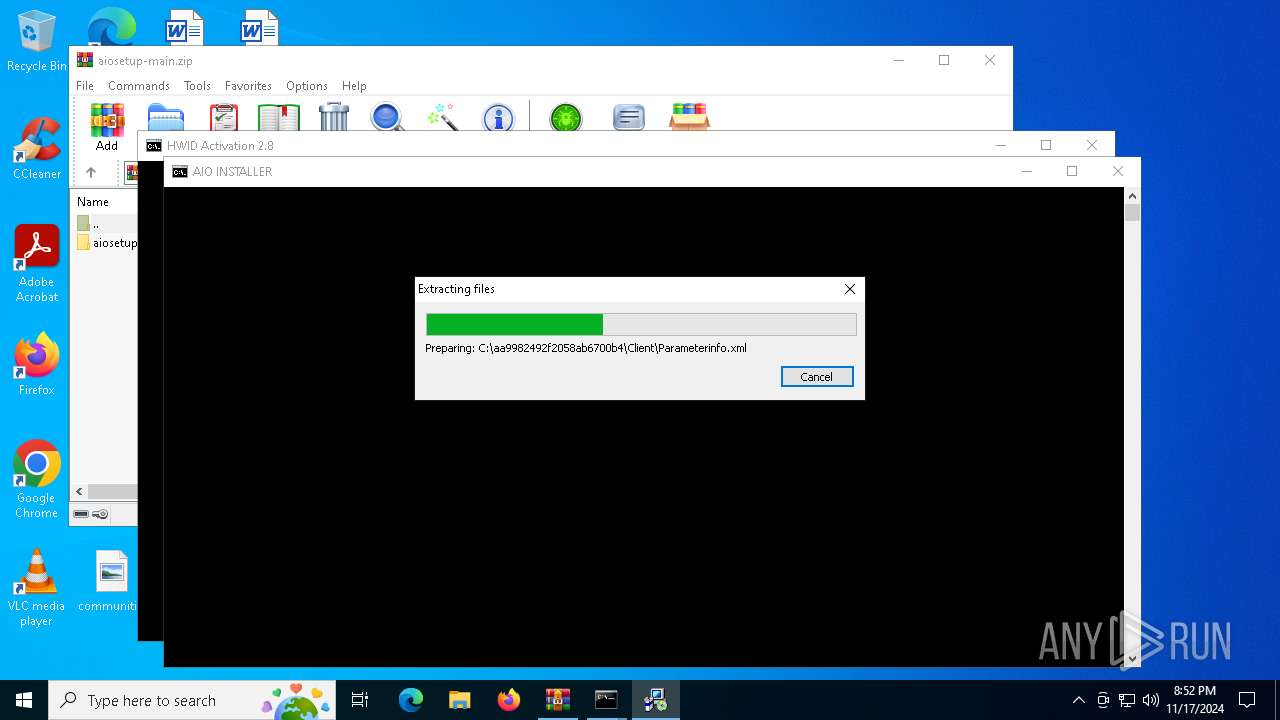
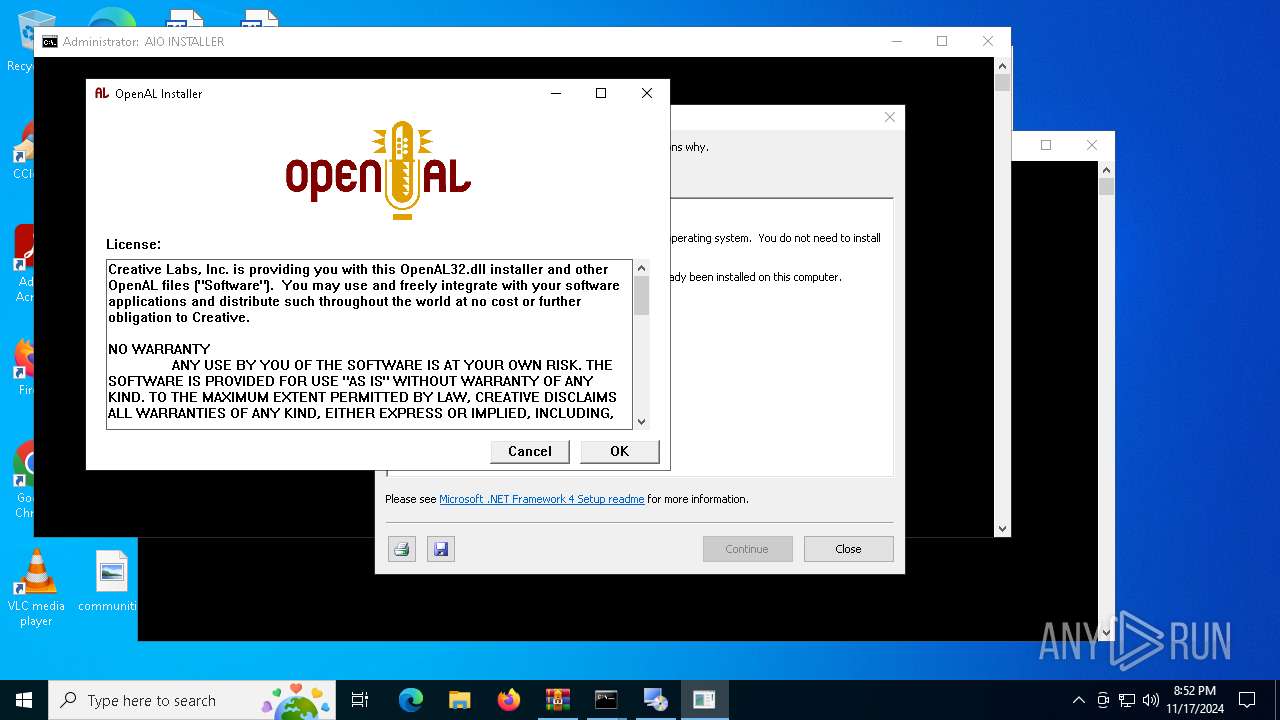
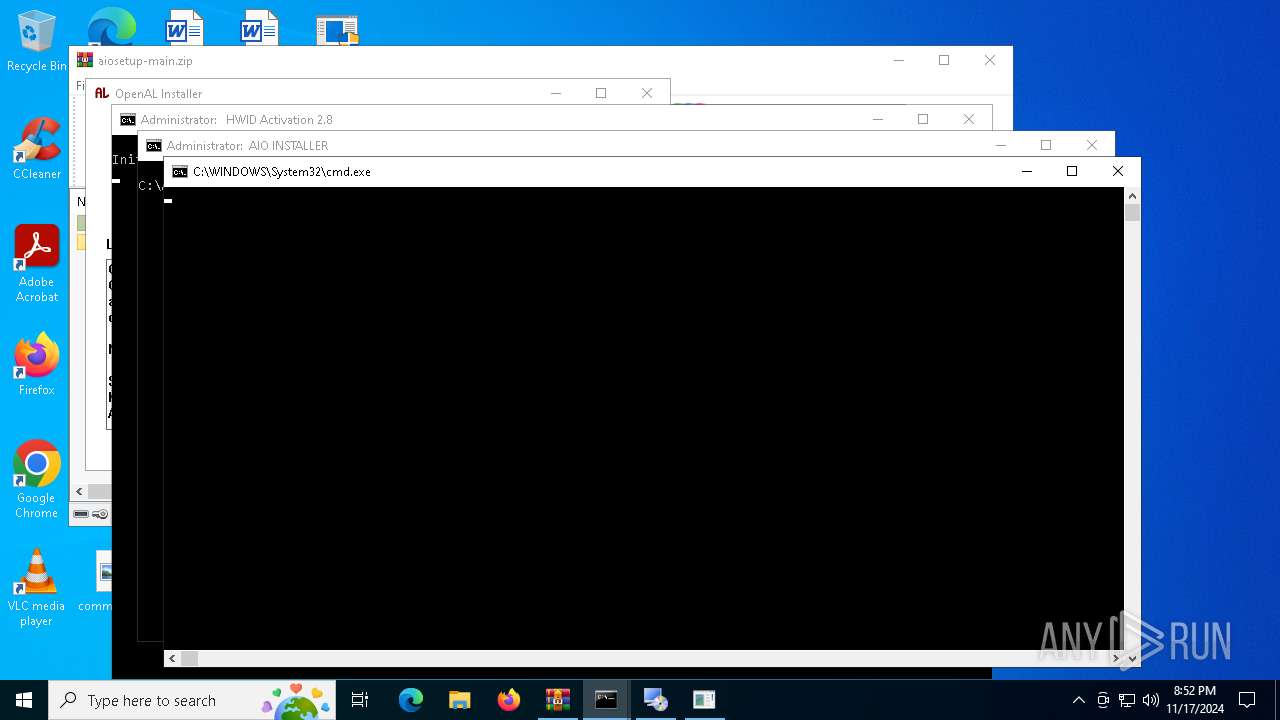
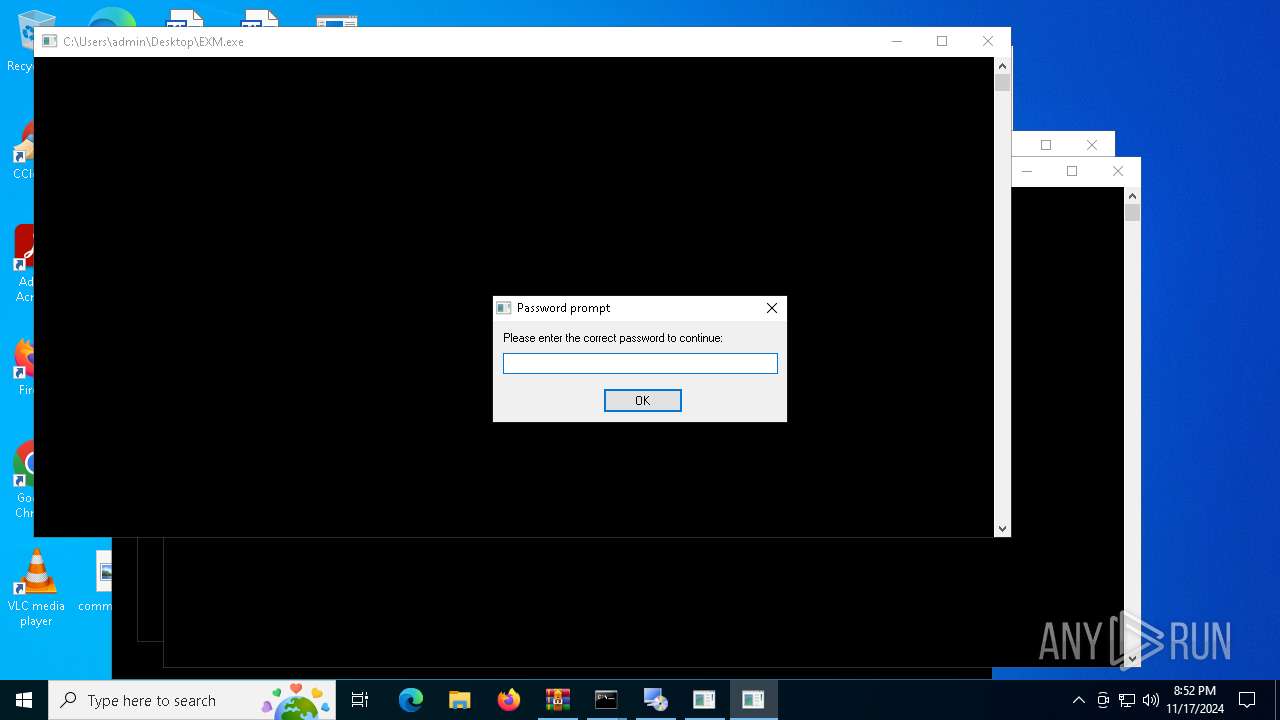
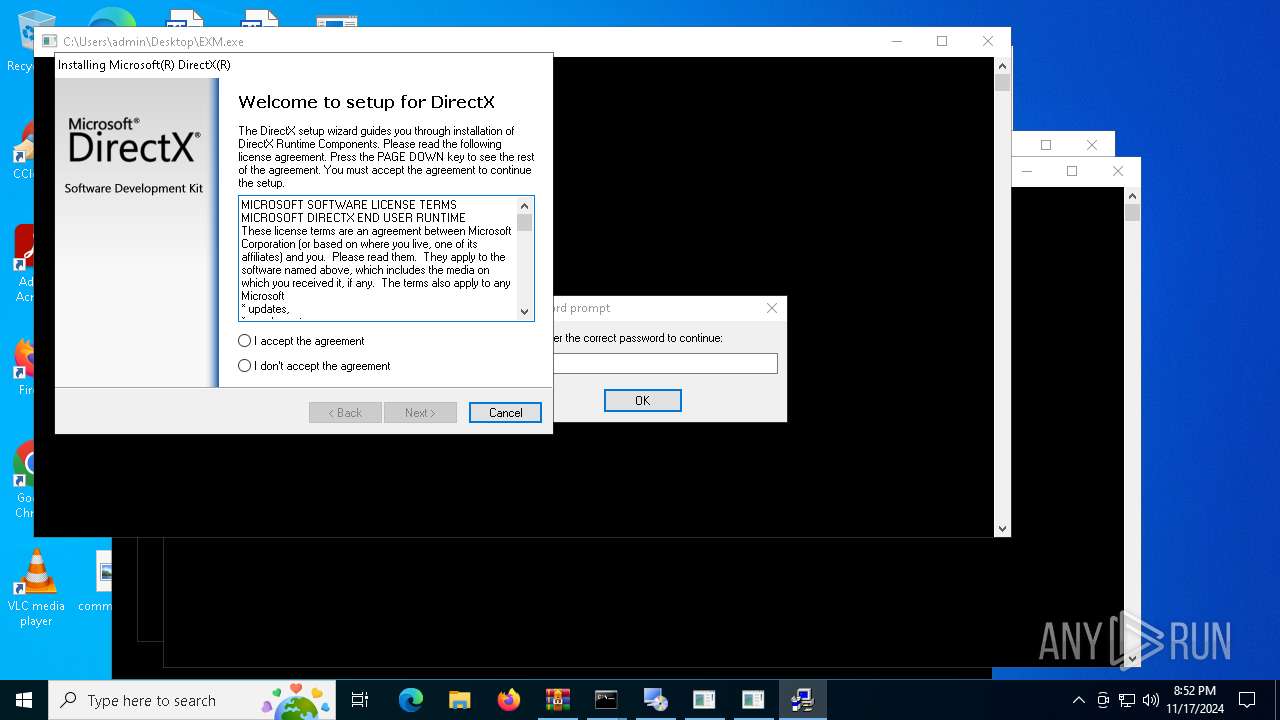
| File name: | aiosetup-main.zip |
| Full analysis: | https://app.any.run/tasks/29648063-79e6-480b-a67a-2e7ecf36d9fd |
| Verdict: | Malicious activity |
| Analysis date: | November 17, 2024, 20:51:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 18EE73828F04ECDCC8D686EF26CBF99A |
| SHA1: | 3C11E0BA5EE79860ECE1743B452BD804D3692379 |
| SHA256: | DF70F699036A080B6E48795B3E940377B4ABF8E3869C30C5C102C1DFFCEF4045 |
| SSDEEP: | 393216:YMUJc8d2PR+/l6Xp5h50kAk/EoXlnRfnDGNRQC+SS6OhaHte:Tat/m5bJtDQRjziaHs |
MALICIOUS
Probably downloads file via BitsAdmin
- powershell.exe (PID: 2280)
Executing a file with an untrusted certificate
- rdst4.exe (PID: 3600)
- rdst4.exe (PID: 3108)
SUSPICIOUS
Executing commands from ".cmd" file
- cmd.exe (PID: 6956)
- powershell.exe (PID: 6776)
- cmd.exe (PID: 7116)
Application launched itself
- cmd.exe (PID: 4680)
- cmd.exe (PID: 6956)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 1248)
- cmd.exe (PID: 6628)
- powershell.exe (PID: 4040)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6956)
- cmd.exe (PID: 4680)
- powershell.exe (PID: 3832)
- powershell.exe (PID: 6776)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 1248)
- cmd.exe (PID: 6628)
- powershell.exe (PID: 6820)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6956)
- cmd.exe (PID: 7116)
Starts SC.EXE for service management
- cmd.exe (PID: 6956)
- cmd.exe (PID: 7116)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6964)
- rdst6.exe (PID: 2076)
- rdst5.exe (PID: 4808)
- dxwsetup.exe (PID: 7160)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6204)
- cmd.exe (PID: 4692)
- cmd.exe (PID: 6956)
- cmd.exe (PID: 1248)
- cmd.exe (PID: 608)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 6860)
- cmd.exe (PID: 6516)
- cmd.exe (PID: 4080)
- powershell.exe (PID: 4040)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6204)
- cmd.exe (PID: 608)
- cmd.exe (PID: 7116)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 6400)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 1584)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6204)
- cmd.exe (PID: 608)
- cmd.exe (PID: 7116)
Starts a Microsoft application from unusual location
- rdst6.exe (PID: 6028)
- rdst6.exe (PID: 2076)
- dxwsetup.exe (PID: 7160)
- rdst5.exe (PID: 4808)
- rdst5.exe (PID: 1732)
Creates file in the systems drive root
- rdst6.exe (PID: 2076)
Executing commands from a ".bat" file
- powershell.exe (PID: 3832)
- cmd.exe (PID: 1248)
- powershell.exe (PID: 6820)
Executable content was dropped or overwritten
- rdst6.exe (PID: 2076)
- rdst5.exe (PID: 4808)
- dxwsetup.exe (PID: 7160)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6152)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7116)
Hides command output
- cmd.exe (PID: 7156)
- cmd.exe (PID: 5932)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 5932)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 4040)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 4040)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7116)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7116)
INFO
Checks operating system version
- cmd.exe (PID: 6956)
- cmd.exe (PID: 7116)
Manual execution by a user
- cmd.exe (PID: 6956)
- cmd.exe (PID: 4692)
- rdst6.exe (PID: 6028)
- rdst6.exe (PID: 2076)
- rdst4.exe (PID: 3600)
- rdst4.exe (PID: 3108)
- EXM.exe (PID: 4812)
- EXM.exe (PID: 6220)
- rdst5.exe (PID: 4808)
- rdst5.exe (PID: 1732)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6400)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 1584)
Reads the computer name
- rdst6.exe (PID: 2076)
- Setup.exe (PID: 632)
- rdst4.exe (PID: 3108)
The process uses the downloaded file
- powershell.exe (PID: 3832)
- powershell.exe (PID: 6776)
- powershell.exe (PID: 2280)
- powershell.exe (PID: 6820)
Checks supported languages
- Setup.exe (PID: 632)
- rdst4.exe (PID: 3108)
- rdst6.exe (PID: 2076)
Reads CPU info
- Setup.exe (PID: 632)
Create files in a temporary directory
- Setup.exe (PID: 632)
- rdst6.exe (PID: 2076)
- rdst5.exe (PID: 4808)
- dxwsetup.exe (PID: 7160)
Reads the machine GUID from the registry
- rdst6.exe (PID: 2076)
Starts MODE.COM to configure console settings
- mode.com (PID: 4088)
Sends debugging messages
- dxwsetup.exe (PID: 7160)
Creates files or folders in the user directory
- dxwsetup.exe (PID: 7160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:11:17 03:07:46 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | aiosetup-main/ |
Total processes
226
Monitored processes
102
Malicious processes
6
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 608 | cmd /c "powershell.exe "$f=[io.file]::ReadAllText('C:\Users\admin\Desktop\HWID_Activation.cmd') -split ':PowerShellTest:\s*';iex ($f[1])"" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | reg query "HKCU\Console" /v ForceV2 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | C:\aa9982492f2058ab6700b4\\Setup.exe /x86 /x64 /ia64 /web | C:\aa9982492f2058ab6700b4\Setup.exe | — | rdst6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Version: 10.0.30319.1 built by: RTMRel Modules
| |||||||||||||||
| 764 | find /i "FullLanguage" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 916 | powershell.exe $AssemblyBuilder = [AppDomain]::CurrentDomain.DefineDynamicAssembly(4, 1); $ModuleBuilder = $AssemblyBuilder.DefineDynamicModule(2, $False); $TypeBuilder = $ModuleBuilder.DefineType(0); [void]$TypeBuilder.DefinePInvokeMethod('SLGetWindowsInformationDWORD', 'slc.dll', 'Public, Static', 1, [int], @([String], [int].MakeByRefType()), 1, 3); $Sku = 0; [void]$TypeBuilder.CreateType()::SLGetWindowsInformationDWORD('Kernel-BrandingInfo', [ref]$Sku); $Sku | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | find /i "AutoPico" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1248 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\Aio.bat" am_admin | C:\Windows\System32\cmd.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1584 | powershell.exe "$f=[io.file]::ReadAllText('C:\Users\admin\Desktop\HWID_Activation.cmd') -split ':winsubstatus\:.*';iex ($f[1])" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | "C:\Users\admin\Desktop\rdst5.exe" | C:\Users\admin\Desktop\rdst5.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DirectX 9.0 Web setup Exit code: 3221226540 Version: 9.29.1962.0 Modules
| |||||||||||||||
Total events
63 196
Read events
63 184
Write events
12
Delete events
0
Modification events
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\aiosetup-main.zip | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3832) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (3832) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (4808) rdst5.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
| (PID) Process: | (7160) dxwsetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
40
Suspicious files
10
Text files
110
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6400 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1x4dytkj.ntb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6400 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dhfezdhw.dsv.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3832 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iobksbhb.sxj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2076 | rdst6.exe | C:\aa9982492f2058ab6700b4\header.bmp | image | |
MD5:514BFCD8DA66722A9639EB41ED3988B7 | SHA256:6B8201ED10CE18FFADE072B77C6D1FCACCF1D29ACB47D86F553D9BEEBD991290 | |||
| 3832 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p5d4e0ww.i1k.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2076 | rdst6.exe | C:\aa9982492f2058ab6700b4\SplashScreen.bmp | image | |
MD5:0966FCD5A4AB0DDF71F46C01EFF3CDD5 | SHA256:31C13ECFC0EB27F34036FB65CC0E735CD444EEC75376EEA2642F926AC162DCB3 | |||
| 2076 | rdst6.exe | C:\aa9982492f2058ab6700b4\Graphics\Rotate4.ico | image | |
MD5:BB55B5086A9DA3097FB216C065D15709 | SHA256:8D82FF7970C9A67DA8134686560FE3A6C986A160CED9D1CC1392F2BA75C698AB | |||
| 2076 | rdst6.exe | C:\aa9982492f2058ab6700b4\Graphics\Rotate7.ico | image | |
MD5:FB4DFEBE83F554FAF1A5CEC033A804D9 | SHA256:4F46A9896DE23A92D2B5F963BCFB3237C3E85DA05B8F7660641B3D1D5AFAAE6F | |||
| 2076 | rdst6.exe | C:\aa9982492f2058ab6700b4\Graphics\Print.ico | image | |
MD5:7E55DDC6D611176E697D01C90A1212CF | SHA256:FF542E32330B123486797B410621E19EAFB39DF3997E14701AFA4C22096520ED | |||
| 2076 | rdst6.exe | C:\aa9982492f2058ab6700b4\Graphics\Rotate5.ico | image | |
MD5:3B4861F93B465D724C60670B64FCCFCF | SHA256:7237051D9AF5DB972A1FECF0B35CD8E9021471740782B0DBF60D3801DC9F5F75 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
33
DNS requests
14
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7160 | dxwsetup.exe | GET | 302 | 23.212.89.111:80 | http://download.microsoft.com/download/1/7/1/1718CCC4-6315-4D8E-9543-8E28A4E18C4C/dxupdate.cab | unknown | — | — | whitelisted |
7160 | dxwsetup.exe | GET | 200 | 2.16.164.43:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7160 | dxwsetup.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | HEAD | 302 | 140.82.121.4:443 | https://github.com/Gelaxiz/aiosetup/releases/download/app/AioSetup.bat | unknown | — | — | unknown |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
github.com |
| shared |
objects.githubusercontent.com |
| shared |
updatecheck.massgrave.dev |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
download.microsoft.com |
| whitelisted |
Threats
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
dxwsetup.exe | DLL_PROCESS_ATTACH |
dxwsetup.exe | DLL_PROCESS_ATTACH |
dxwsetup.exe | DLL_PROCESS_DETACH |
dxwsetup.exe | DLL_PROCESS_DETACH |