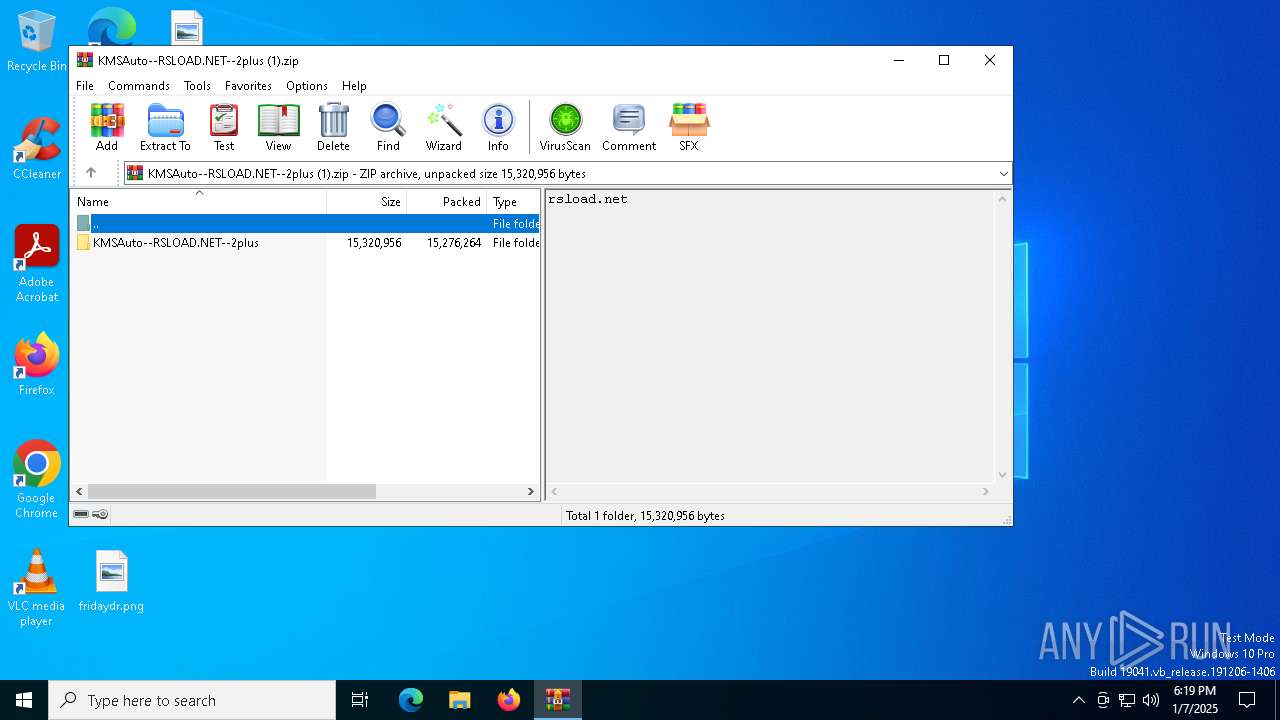
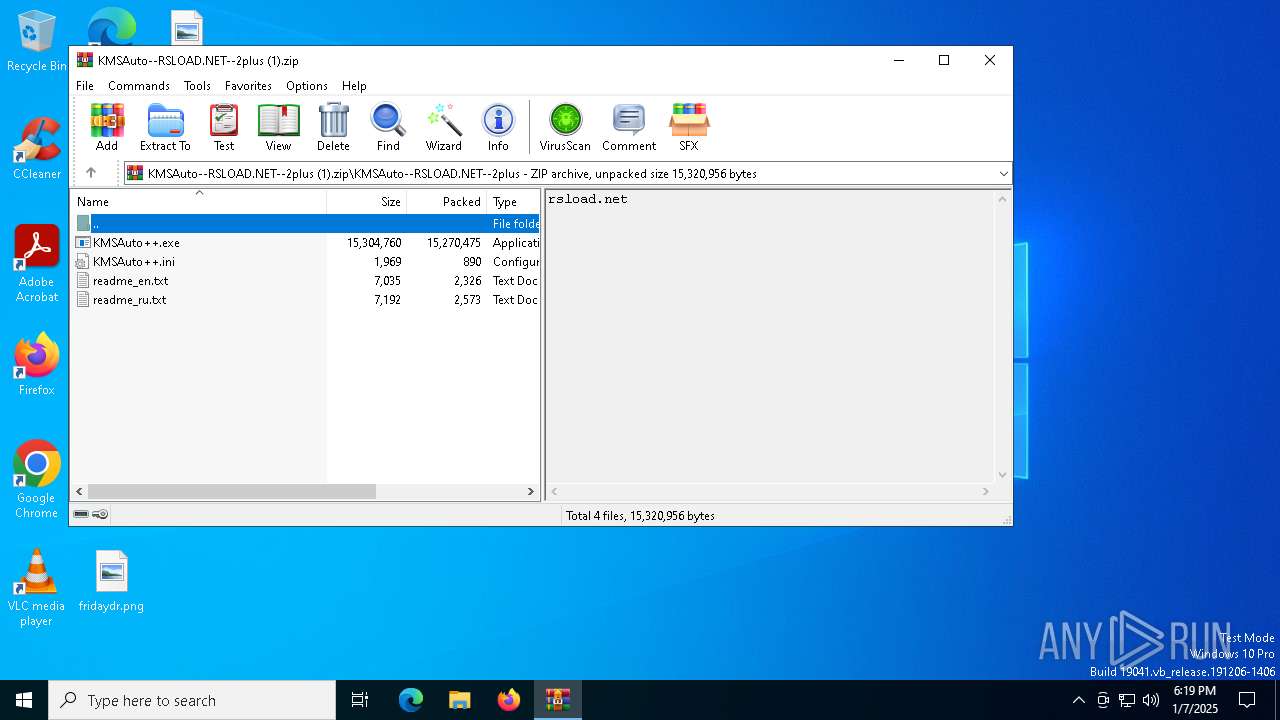
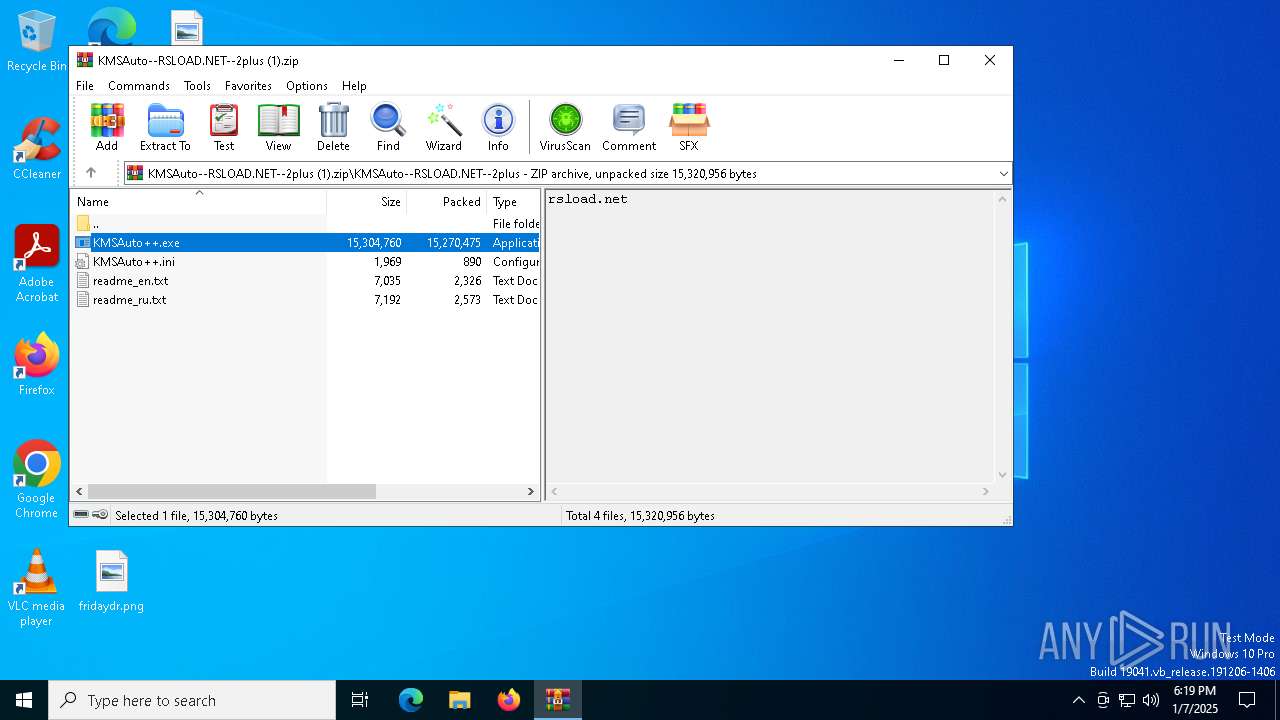
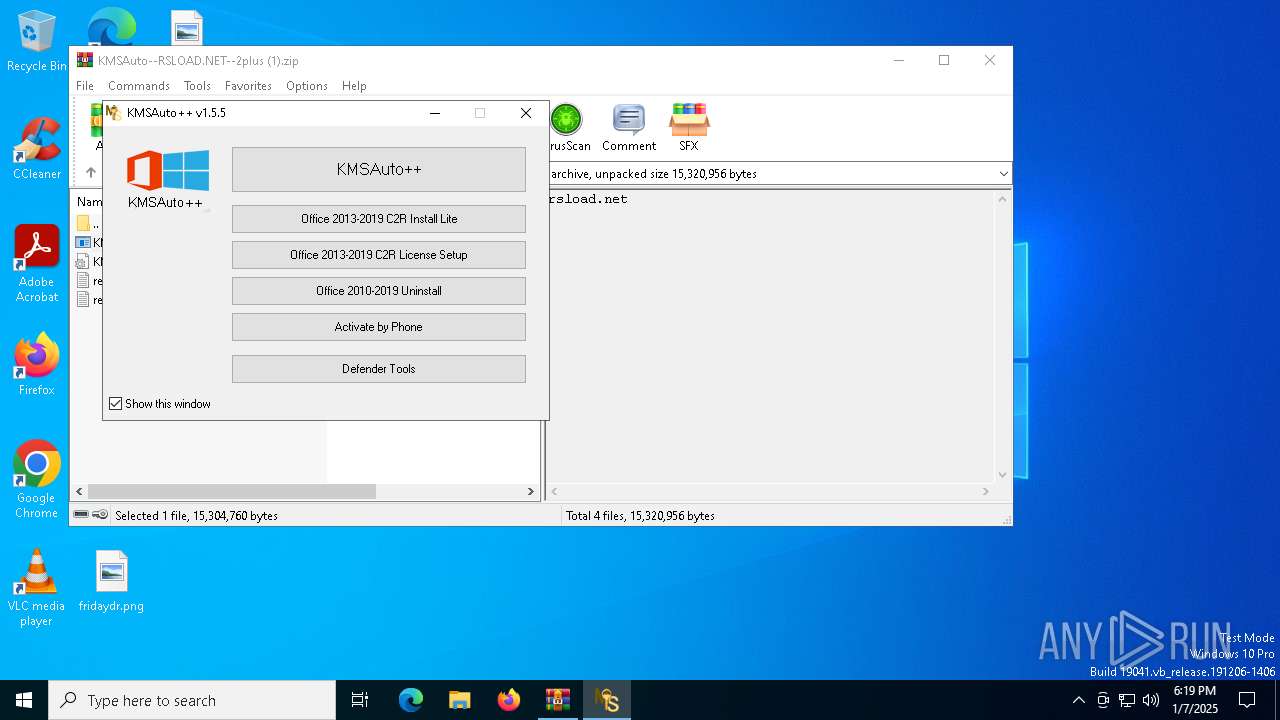
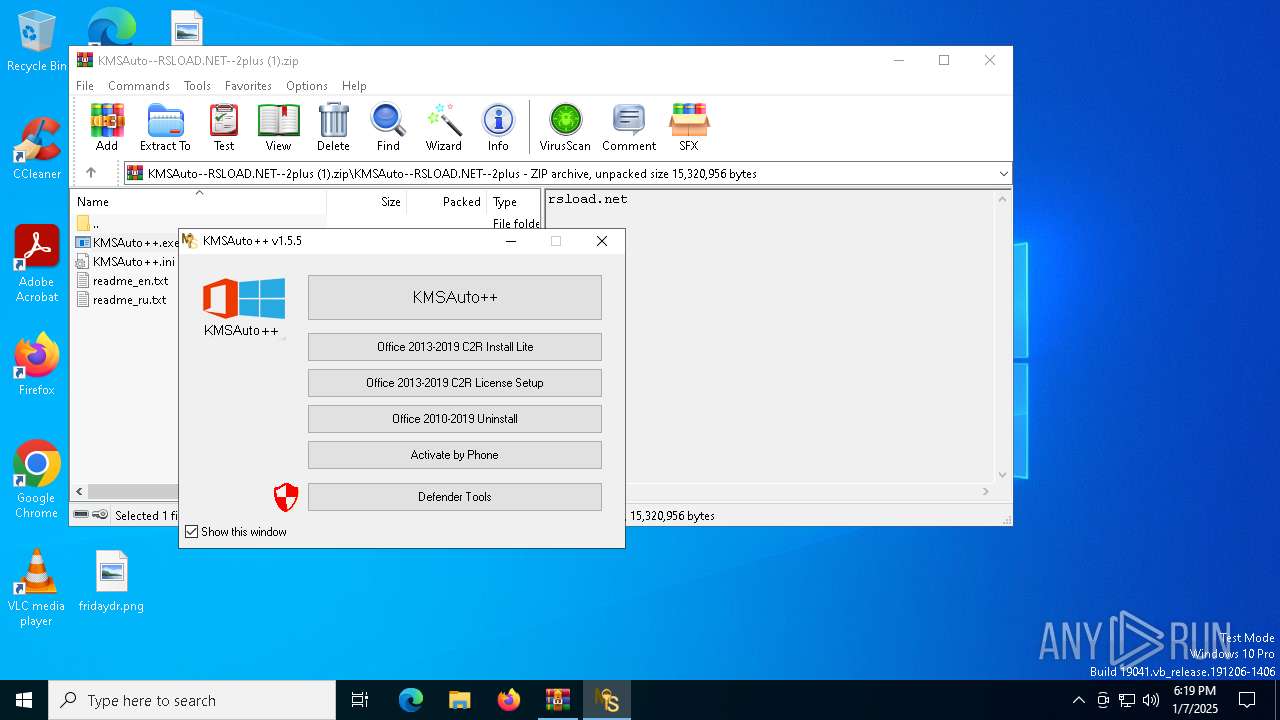
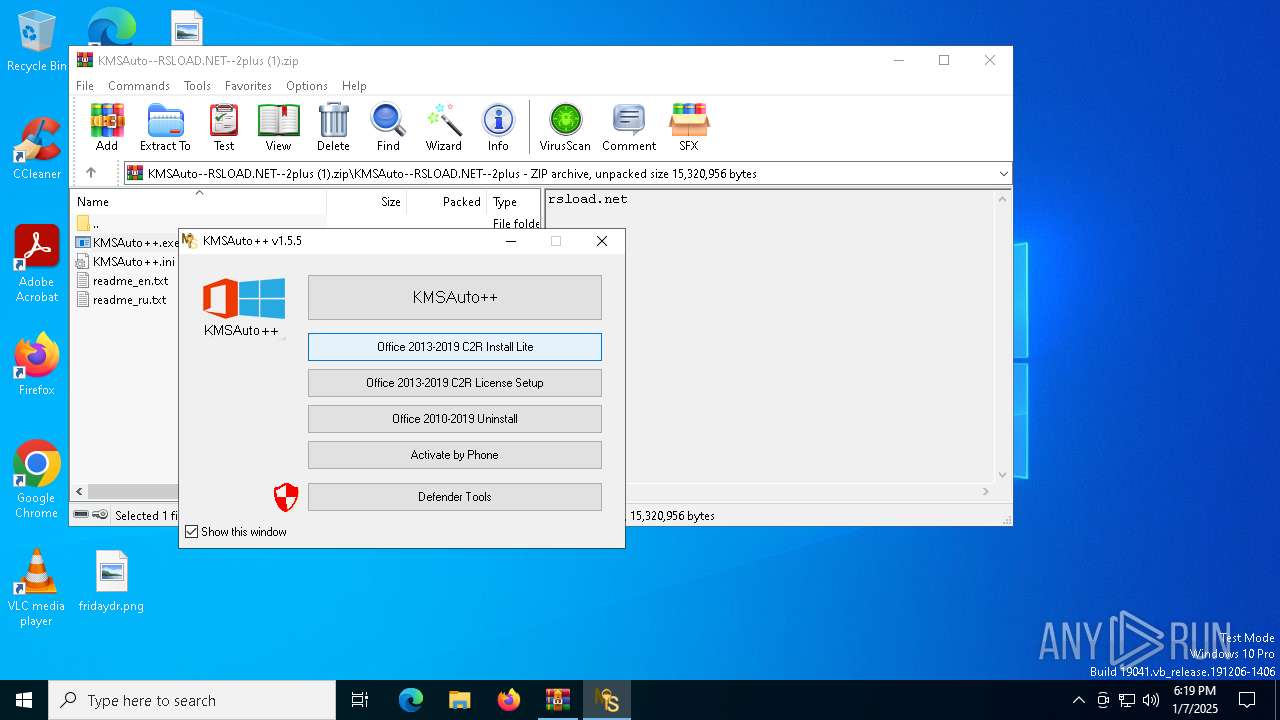
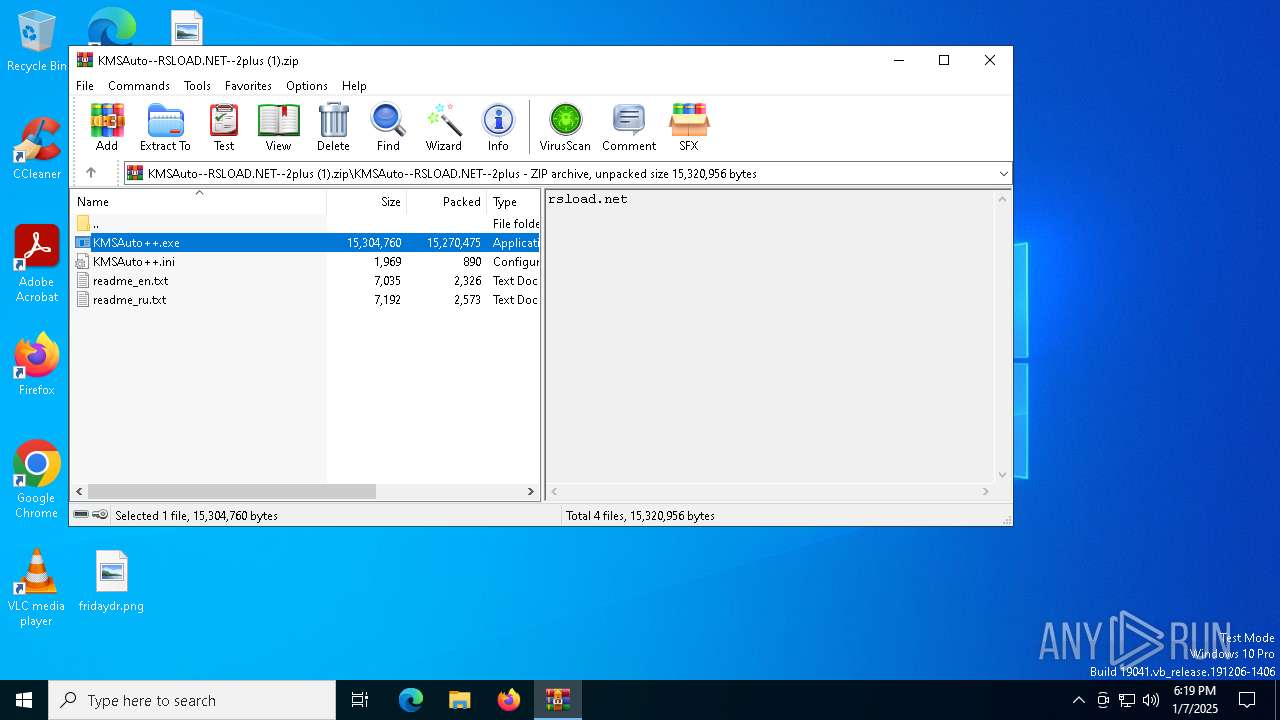
| File name: | KMSAuto--RSLOAD.NET--2plus (1).zip |
| Full analysis: | https://app.any.run/tasks/4bccf165-8e45-4e09-93a1-df96d06c9f15 |
| Verdict: | Malicious activity |
| Analysis date: | January 07, 2025, 18:19:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 1E406E34DC0E2A2B491BE23F3A5EF128 |
| SHA1: | BC5B0D977FE0BC2E3D9EE2FA15A74312CBC359E4 |
| SHA256: | DF6414FC79F56F899648547EA18D9B11FB0F08D6F3A468A198928C6A99E14104 |
| SSDEEP: | 98304:aXICjZ6vGljlZRfzUF/f7CewFHmmHBmoxg62tTuypeyjsiaNHuuLb2acLdxvHjfM:wIkwKjouylOOYCcmWFOC5CD/KxTkjSu2 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6500)
Executing a file with an untrusted certificate
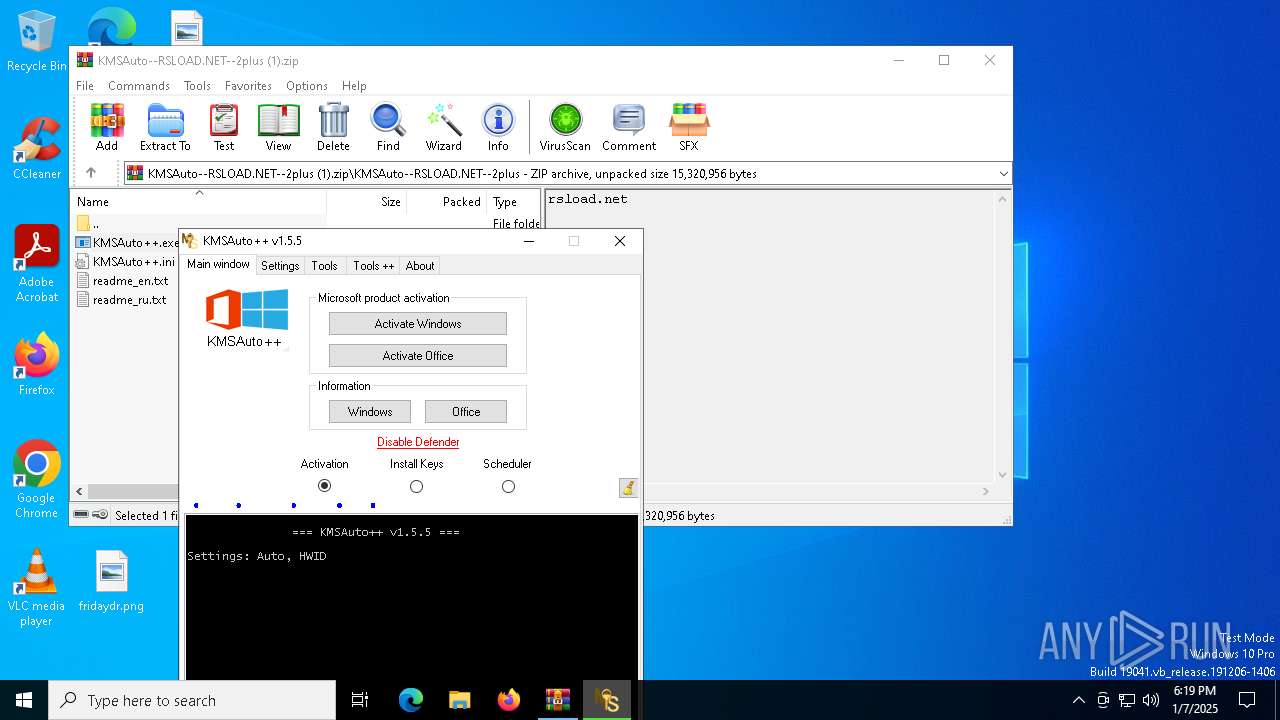
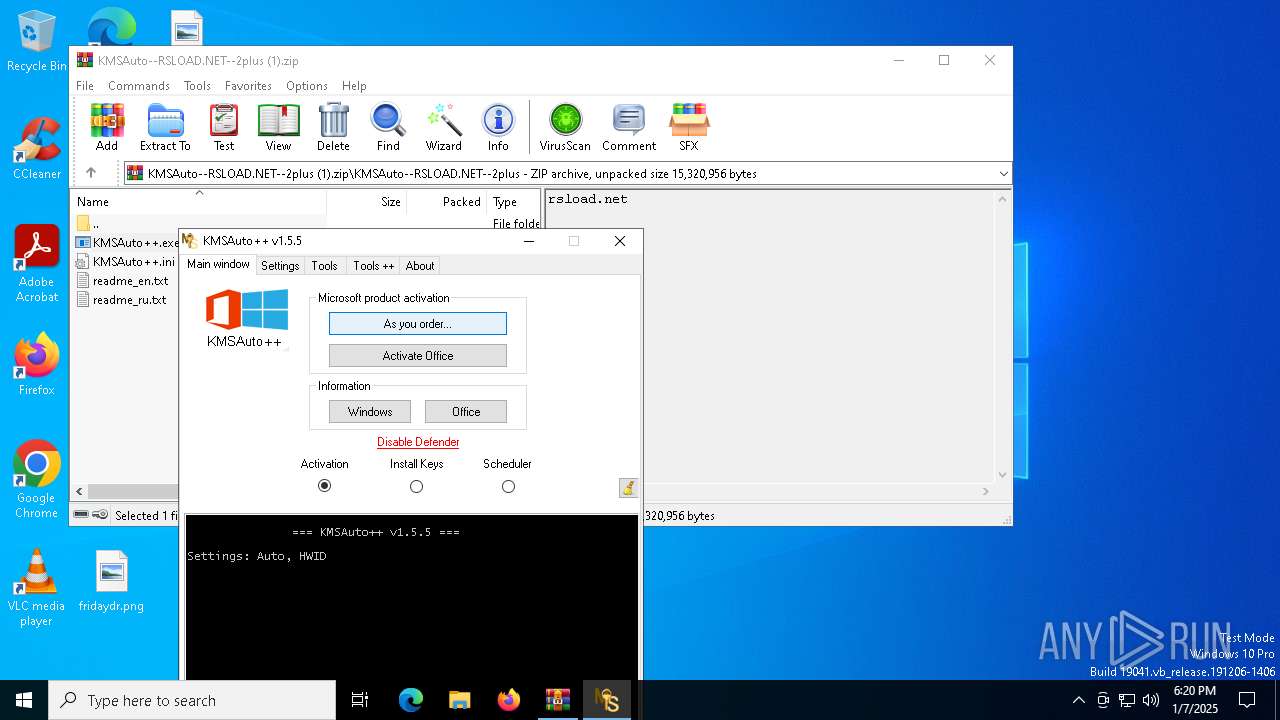
- KMSAuto++.exe (PID: 6844)
- KMSAuto++.exe (PID: 6792)
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 7136)
- cmd.exe (PID: 6880)
- cmd.exe (PID: 5872)
- cmd.exe (PID: 3092)
SUSPICIOUS
Process drops legitimate windows executable
- KMSAuto++.exe (PID: 6844)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6500)
Starts a Microsoft application from unusual location
- signtool.exe (PID: 6980)
Adds/modifies Windows certificates
- signtool.exe (PID: 6980)
Found strings related to reading or modifying Windows Defender settings
- KMSAuto++.exe (PID: 6844)
Executable content was dropped or overwritten
- KMSAuto++.exe (PID: 6844)
Starts CMD.EXE for commands execution
- KMSAuto++.exe (PID: 6844)
Uses WMIC.EXE
- KMSAuto++.exe (PID: 6844)
The process executes VB scripts
- cmd.exe (PID: 644)
- cmd.exe (PID: 6816)
- cmd.exe (PID: 6996)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 6704)
- cscript.exe (PID: 6872)
- cscript.exe (PID: 6880)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 6704)
- cscript.exe (PID: 6872)
- cscript.exe (PID: 6880)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6500)
The sample compiled with english language support
- KMSAuto++.exe (PID: 6844)
Create files in a temporary directory
- KMSAuto++.exe (PID: 6844)
Checks supported languages
- KMSAuto++.exe (PID: 6844)
Reads the software policy settings
- signtool.exe (PID: 6980)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6972)
- WMIC.exe (PID: 5256)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6500)
UPX packer has been detected
- KMSAuto++.exe (PID: 6844)
Reads product name
- KMSAuto++.exe (PID: 6844)
Reads Environment values
- KMSAuto++.exe (PID: 6844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:12:29 02:22:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | KMSAuto--RSLOAD.NET--2plus/ |
Total processes
156
Monitored processes
30
Malicious processes
2
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
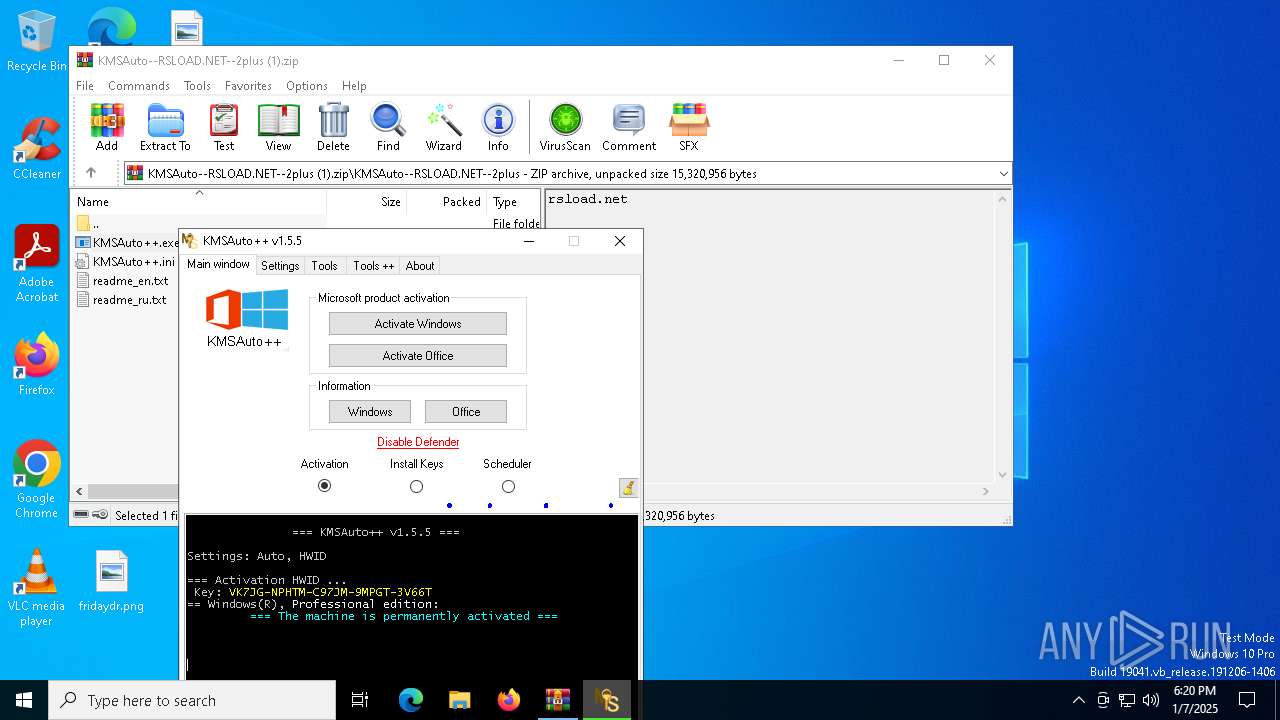
| 644 | "C:\WINDOWS\Sysnative\cmd.exe" /c cscript //nologo "C:\Users\admin\AppData\Local\Temp\slmgr.vbs" /ipk VK7JG-NPHTM-C97JM-9MPGT-3V66T | C:\Windows\System32\cmd.exe | — | KMSAuto++.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1684 | WMIC /NAMESPACE:\\root\Microsoft\Windows\Defender PATH MSFT_MpPreference call Add ExclusionPath="C:\Users\admin\AppData\Local\Temp\Rar$EXa6500.29945\KMSAuto--RSLOAD.NET--2plus\KMSAuto_Files" | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3092 | "C:\WINDOWS\Sysnative\cmd.exe" /c WMIC /NAMESPACE:\\root\Microsoft\Windows\Defender PATH MSFT_MpPreference call Add ExclusionPath="C:\WINDOWS\System32\SppExtComObjPatcher.exe" | C:\Windows\System32\cmd.exe | — | KMSAuto++.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4136 | WMIC /NAMESPACE:\\root\Microsoft\Windows\Defender PATH MSFT_MpPreference call Add ExclusionPath="C:\WINDOWS\System32\SppExtComObjPatcher.exe" | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4932 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5256 | WMIC /NAMESPACE:\\root\Microsoft\Windows\Defender PATH MSFT_MpPreference call Add ExclusionPath="C:\WINDOWS\System32\SppExtComObjHook.dll" | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5460 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5872 | "C:\WINDOWS\Sysnative\cmd.exe" /c WMIC /NAMESPACE:\\root\Microsoft\Windows\Defender PATH MSFT_MpPreference call Add ExclusionPath="C:\WINDOWS\System32\SppExtComObjHook.dll" | C:\Windows\System32\cmd.exe | — | KMSAuto++.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 361
Read events
6 346
Write events
13
Delete events
2
Modification events
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\KMSAuto--RSLOAD.NET--2plus (1).zip | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6844) KMSAuto++.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6980) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46 |
Value: | |||
Executable files
2
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6500.29945\KMSAuto--RSLOAD.NET--2plus\KMSAuto++.ini | text | |
MD5:F9EA4571821D978CA8A13384E49BAD1A | SHA256:FD1015A97100A23AF9BDF682604187CFFE974042F45EEAF65EBD56F258992076 | |||
| 6500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6500.29945\KMSAuto--RSLOAD.NET--2plus\readme_ru.txt | text | |
MD5:89921EBFDAC4677B4ECC8972B2880FA8 | SHA256:F82E3B77099BAF8C31F2C6F81F511B049EC5D08D3848834076AFD401FAB143DB | |||
| 6844 | KMSAuto++.exe | C:\Users\admin\AppData\Local\Temp\slmgr.vbs | text | |
MD5:3903BCAB32A4A853DFA54962112D4D02 | SHA256:95FC646D222D324DB46F603A7F675C329FE59A567ED27FDAED2A572A19206816 | |||
| 6500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6500.29945\KMSAuto--RSLOAD.NET--2plus\readme_en.txt | text | |
MD5:7A4FB804AF171AD041C65E3E46FD00B2 | SHA256:C7A2D7FA7DCF9A08A5179720F81B947221F0E94BC797878352ECAE52D923C939 | |||
| 6844 | KMSAuto++.exe | C:\Users\admin\AppData\Local\Temp\signtool.exe | executable | |
MD5:05624E6D27EAEF0DB0673AE627BD6027 | SHA256:962A92821F54A1E706AA989973130FDC1072C7BD8B9E6D11EA1050B46EB9D313 | |||
| 6500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6500.29945\KMSAuto--RSLOAD.NET--2plus\KMSAuto++.exe | executable | |
MD5:69FBF6849D935432BAC8B04BDB00FD68 | SHA256:D5DC790F6F220CF7E42C6C1C9F5BC6E4443CB52D07BCDEF24A6BF457153C1D86 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
31
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4684 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4684 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2356 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.21.110.146:443 | www.bing.com | AKAMAI-AS | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| unknown |
login.live.com |
| unknown |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |