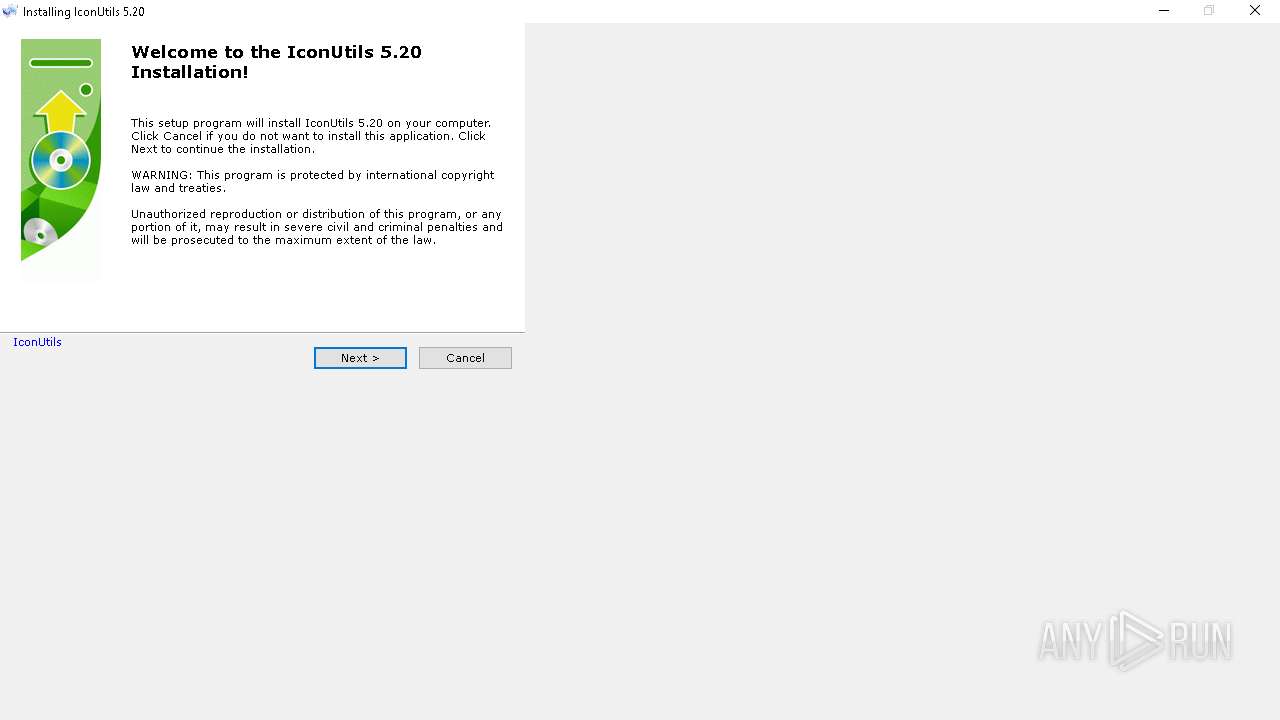
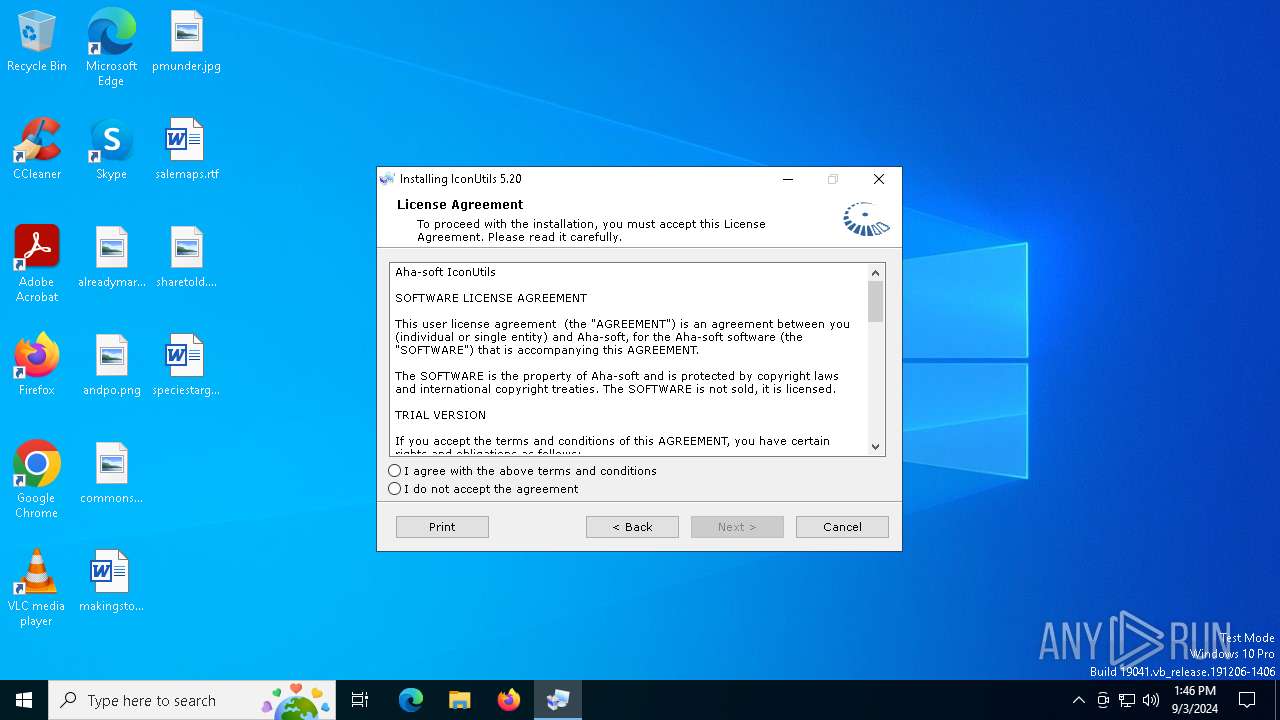
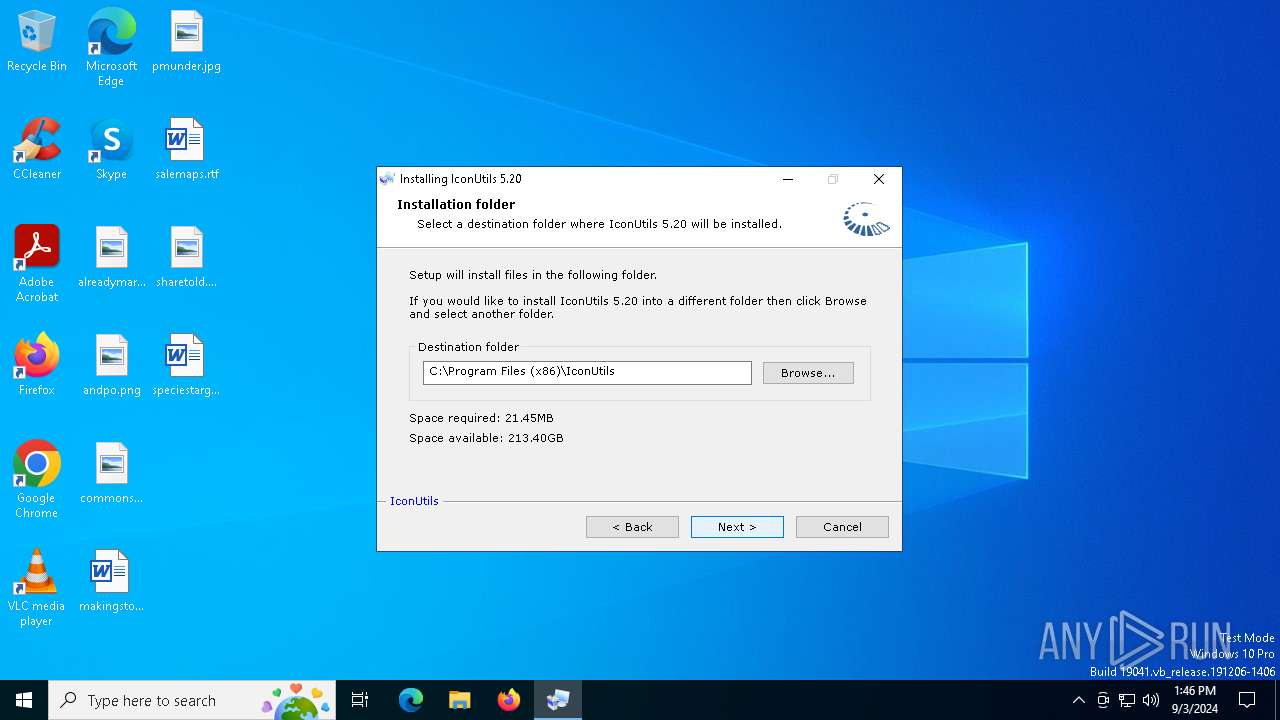
| File name: | iconutils-5-20-en-win.exe |
| Full analysis: | https://app.any.run/tasks/9f465c89-f5df-4688-9954-52044db8c48f |
| Verdict: | Malicious activity |
| Analysis date: | September 03, 2024, 13:46:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | DAB07082F58A4F5E446DD02EB1765E9D |
| SHA1: | E168B97DF6F30FED89E2342A930285FE8B221240 |
| SHA256: | DF596881757A7724C2BB7C80DB96B5B393418257D3ED0121BB1C989E9FC2E9A3 |
| SSDEEP: | 98304:77of6V1Gneofol1fTtWov5hFLvI+lM+elBlwv6+/46Ljo1k8HnUangiCiwoUQWY6:kODagMZixMPVZVP0GkTyKSCmzD8LHn |
MALICIOUS
Phishing document has been detected
- iconutils-5-20-en-win.exe (PID: 2088)
SUSPICIOUS
Reads the Windows owner or organization settings
- iconutils-5-20-en-win.exe (PID: 2088)
Executable content was dropped or overwritten
- iconutils-5-20-en-win.exe (PID: 2088)
Creates a software uninstall entry
- iconutils-5-20-en-win.exe (PID: 2088)
Searches for installed software
- iconutils-5-20-en-win.exe (PID: 2088)
INFO
Create files in a temporary directory
- iconutils-5-20-en-win.exe (PID: 2088)
Checks supported languages
- iconutils-5-20-en-win.exe (PID: 2088)
- icolover.exe (PID: 4292)
Reads the computer name
- iconutils-5-20-en-win.exe (PID: 2088)
- icolover.exe (PID: 4292)
Creates files in the program directory
- iconutils-5-20-en-win.exe (PID: 2088)
Creates files or folders in the user directory
- iconutils-5-20-en-win.exe (PID: 2088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:09:02 04:13:09+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 4096 |
| InitializedDataSize: | 196608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d20 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.20.0.0 |
| ProductVersionNumber: | 5.20.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Pre-release |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unknown (01B5) |
| Comments: | - |
| CompanyName: | Aha-Soft |
| FileDescription: | IconUtils Setup |
| FileVersion: | 5.2 |
| InternalName: | setup |
| LegalCopyright: | Copyright © 2011 Aha-Soft |
| LegalTrademarks: | - |
| OriginalFileName: | setup.exe |
| PrivateBuild: | - |
| ProductName: | IconUtils |
| ProductVersion: | 5.2 |
| SpecialBuild: | - |
Total processes
121
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Users\admin\AppData\Local\Temp\iconutils-5-20-en-win.exe" | C:\Users\admin\AppData\Local\Temp\iconutils-5-20-en-win.exe | — | explorer.exe | |||||||||||
User: admin Company: Aha-Soft Integrity Level: MEDIUM Description: IconUtils Setup Exit code: 3221226540 Version: 5.20 Modules
| |||||||||||||||
| 2088 | "C:\Users\admin\AppData\Local\Temp\iconutils-5-20-en-win.exe" | C:\Users\admin\AppData\Local\Temp\iconutils-5-20-en-win.exe | explorer.exe | ||||||||||||
User: admin Company: Aha-Soft Integrity Level: HIGH Description: IconUtils Setup Exit code: 0 Version: 5.20 Modules
| |||||||||||||||
| 4292 | "C:\Program Files (x86)\IconUtils\iconlover\icolover.exe" | C:\Program Files (x86)\IconUtils\IconLover\icolover.exe | — | iconutils-5-20-en-win.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
2 751
Read events
2 658
Write events
82
Delete events
11
Modification events
| (PID) Process: | (2088) iconutils-5-20-en-win.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\IconUtils |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\IconUtils\uninstall.exe | |||
| (PID) Process: | (2088) iconutils-5-20-en-win.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\IconUtils |
| Operation: | write | Name: | DisplayName |
Value: IconUtils | |||
| (PID) Process: | (2088) iconutils-5-20-en-win.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\IconUtils |
| Operation: | write | Name: | DisplayVersion |
Value: 5.20 | |||
| (PID) Process: | (2088) iconutils-5-20-en-win.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\IconUtils |
| Operation: | write | Name: | Publisher |
Value: Aha-Soft | |||
| (PID) Process: | (2088) iconutils-5-20-en-win.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\IconUtils |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.aha-soft.com/iconutils/ | |||
| (PID) Process: | (2088) iconutils-5-20-en-win.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.png\UserChoice |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2088) iconutils-5-20-en-win.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.png\UserChoice |
| Operation: | write | Name: | Progid |
Value: pngFile_IconLover | |||
| (PID) Process: | (2088) iconutils-5-20-en-win.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.png |
| Operation: | write | Name: | Progid |
Value: pngFile_IconLover | |||
| (PID) Process: | (2088) iconutils-5-20-en-win.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\pngFile_IconLover |
| Operation: | write | Name: | AlwaysShowExt |
Value: | |||
| (PID) Process: | (2088) iconutils-5-20-en-win.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\pngFile_IconLover |
| Operation: | write | Name: | EditFlags |
Value: 00000000 | |||
Executable files
14
Suspicious files
30
Text files
200
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | iconutils-5-20-en-win.exe | C:\Users\admin\AppData\Local\Temp\gentee73\4default.bmp | binary | |
MD5:0895D223FA59A94BED73D25D1CB5AF70 | SHA256:53228A7C924889D300C7FFE9BAA1879EE94BD9B4286E84B7B29F870E9567B82D | |||
| 2088 | iconutils-5-20-en-win.exe | C:\Users\admin\AppData\Local\Temp\gentee73\guig.dll | executable | |
MD5:8757CD8C68B85D668F15BEFC13251D5E | SHA256:96D1906EF8F1AC224830DA79BC9492AA21FFBACD4CAA4FB44CC64DEDF09047A2 | |||
| 2088 | iconutils-5-20-en-win.exe | C:\Program Files (x86)\IconUtils\splashdata\android-menu-example8.png | image | |
MD5:07DBF2D2EB0DEF83D6517CAF89C3BDF8 | SHA256:8DC28F2CEB5EA813A4D07CA36371F528FE22D5F535578A566D91C5D236E76EF4 | |||
| 2088 | iconutils-5-20-en-win.exe | C:\Users\admin\AppData\Local\Temp\gentee73\2install - 1.bmp | binary | |
MD5:E168634D6C44995C14608F16C2E28693 | SHA256:06263008AB7AB756D1254CE744B389F71B0DFFB186EBFA8BB0D2603271E9C6DA | |||
| 2088 | iconutils-5-20-en-win.exe | C:\Program Files (x86)\IconUtils\splashdata\all-icon-sets-example2.png | image | |
MD5:50BA793D3789C3DD42A81D65A3FDF109 | SHA256:E94ACDC991EC898E7FE38E7F3505971B70F50EA0F4A80F99C8FD24C184835B7F | |||
| 2088 | iconutils-5-20-en-win.exe | C:\Users\admin\AppData\Local\Temp\gentee73\5LICENSE.TXT | text | |
MD5:4BC3DDF0BE87F9F79DA4082B5F63D4A2 | SHA256:61086B414CFC101FC7D42E804CC6F5CB62462DE305CE234193227566D6934620 | |||
| 2088 | iconutils-5-20-en-win.exe | C:\Users\admin\AppData\Local\Temp\gentee73\setup_temp.gea | binary | |
MD5:07FB63AFD536E029CA909B9C34C61F60 | SHA256:93B40B49897C8788606164273C90701046190D26B1DFA6771F0DD38D27286107 | |||
| 2088 | iconutils-5-20-en-win.exe | C:\Program Files (x86)\IconUtils\uninstall.exe | executable | |
MD5:8DDE8EAC146F34625FF22EFDACC39B69 | SHA256:0C755BFB0EE3B636B44C191CDC17BD60F898586316848CC8CD5811A86F922D6B | |||
| 2088 | iconutils-5-20-en-win.exe | C:\Program Files (x86)\IconUtils\splashdata\accounting-development-example8.jpg | image | |
MD5:104D08F5D10A4A8D6982DC6426CF5AD3 | SHA256:61A6F30BBE0FAC3EF5291F16B2F822EBB044ACB6DB734CDC420E232CB7CBB75A | |||
| 2088 | iconutils-5-20-en-win.exe | C:\Program Files (x86)\IconUtils\uninstall.ini | text | |
MD5:FB0EE5021DD86A8E81C45CB8355E19F0 | SHA256:3C38B77BC240DA1A0BFF35C25E108D788574EB1F629A41E063DECACD69C7A4A4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
15
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6408 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6408 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6776 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6408 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6408 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6408 | SIHClient.exe | 13.85.23.206:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |