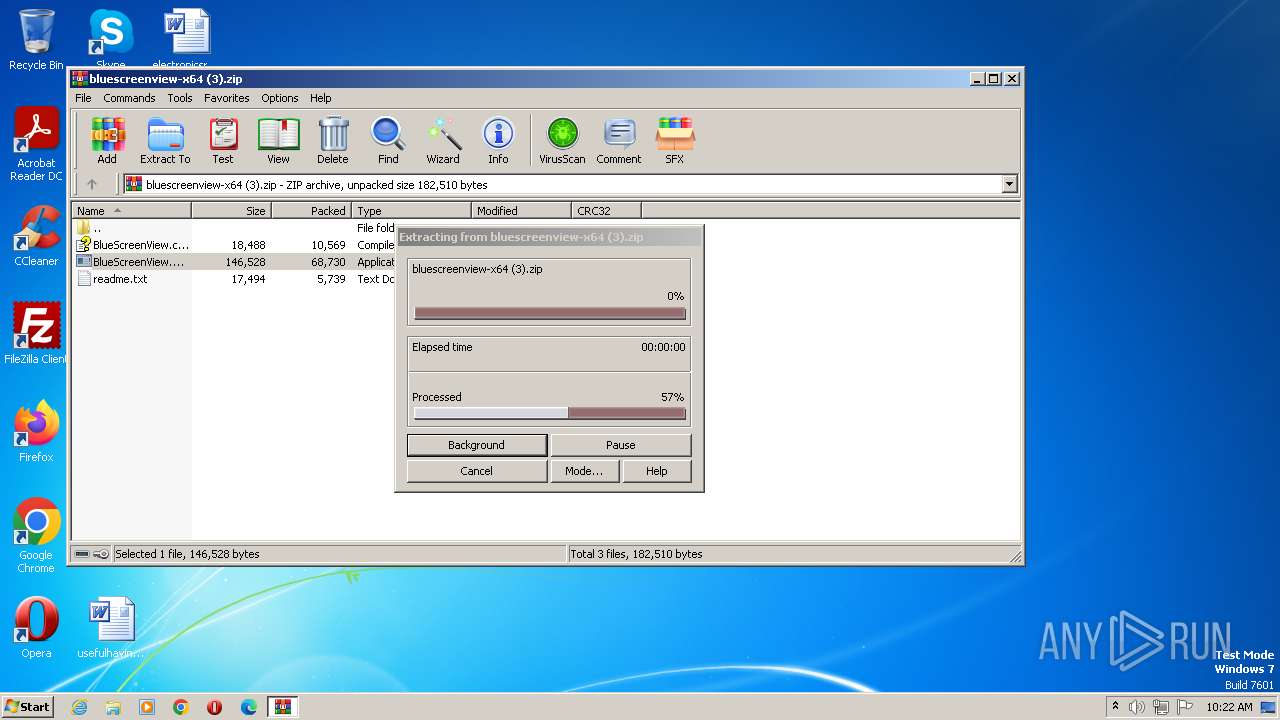
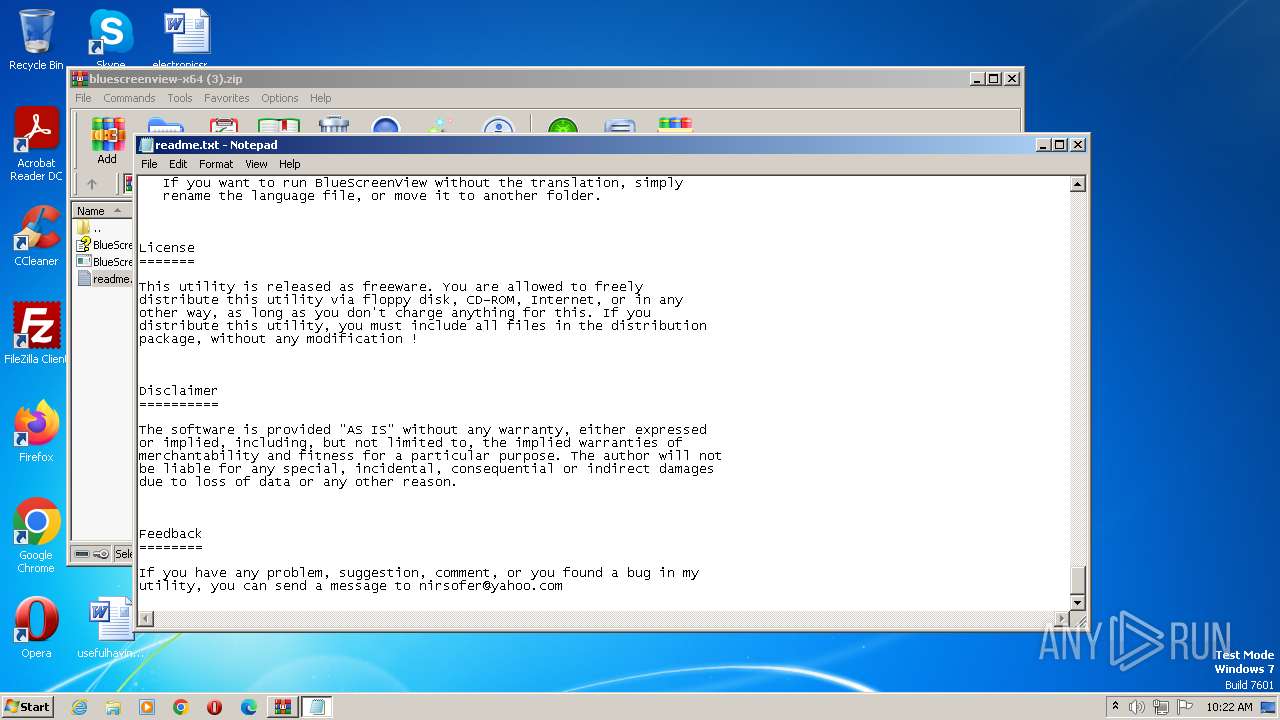
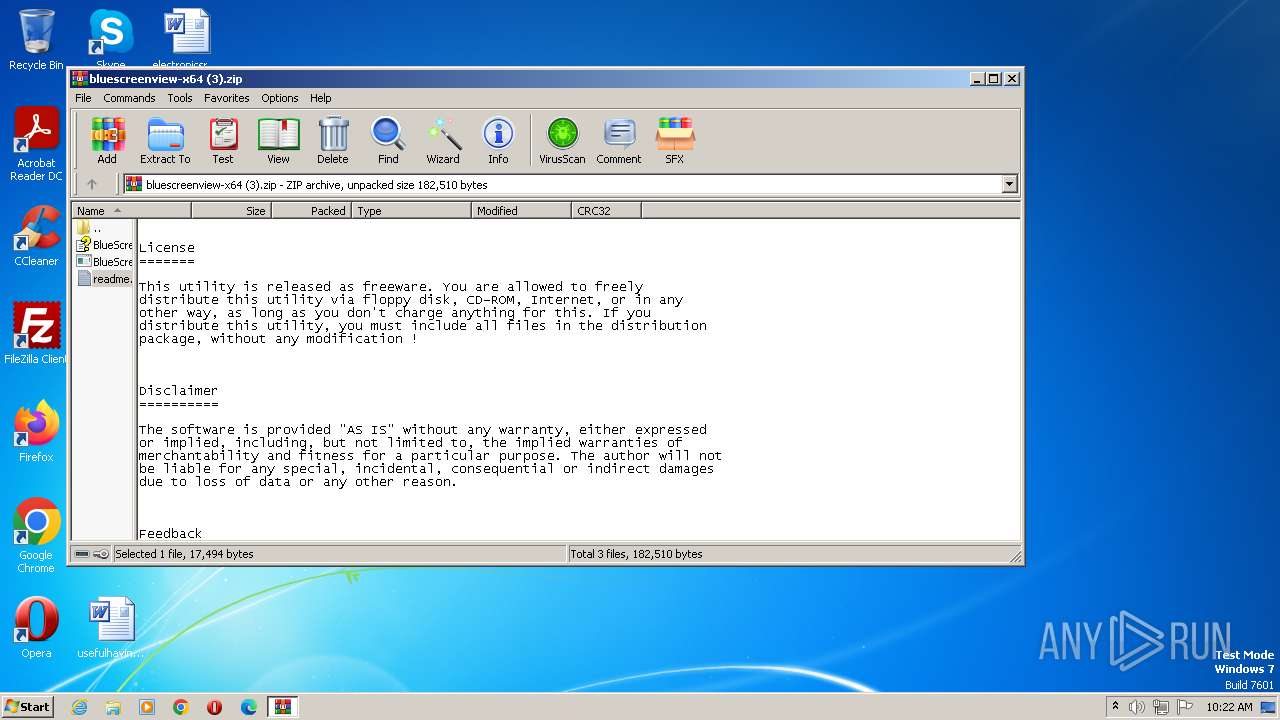
| File name: | bluescreenview-x64 (3).zip |
| Full analysis: | https://app.any.run/tasks/e99c712a-aa5d-4516-b316-d974cf51e5c4 |
| Verdict: | Suspicious activity |
| Analysis date: | September 06, 2023, 09:21:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E3A494133B25553B3835397C9ADCC502 |
| SHA1: | 6B4484A300DA934A351F2FFB8147BA5501E8EF42 |
| SHA256: | DF57D4C9418DD2771035F2F7B70952CAEB20D2269AF683A0AB0665125C821479 |
| SSDEEP: | 1536:a6hZSji4jVS8mj3qtWJt1WrXSm/X3yD3g7yK/I8lR/2y5BGpOdE5je2J/iy1f:a6Eimp0MTN/Qg7bjl5tGpr3tiq |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- hh.exe (PID: 2476)
Reads Microsoft Outlook installation path
- hh.exe (PID: 2476)
Reads Internet Explorer settings
- hh.exe (PID: 2476)
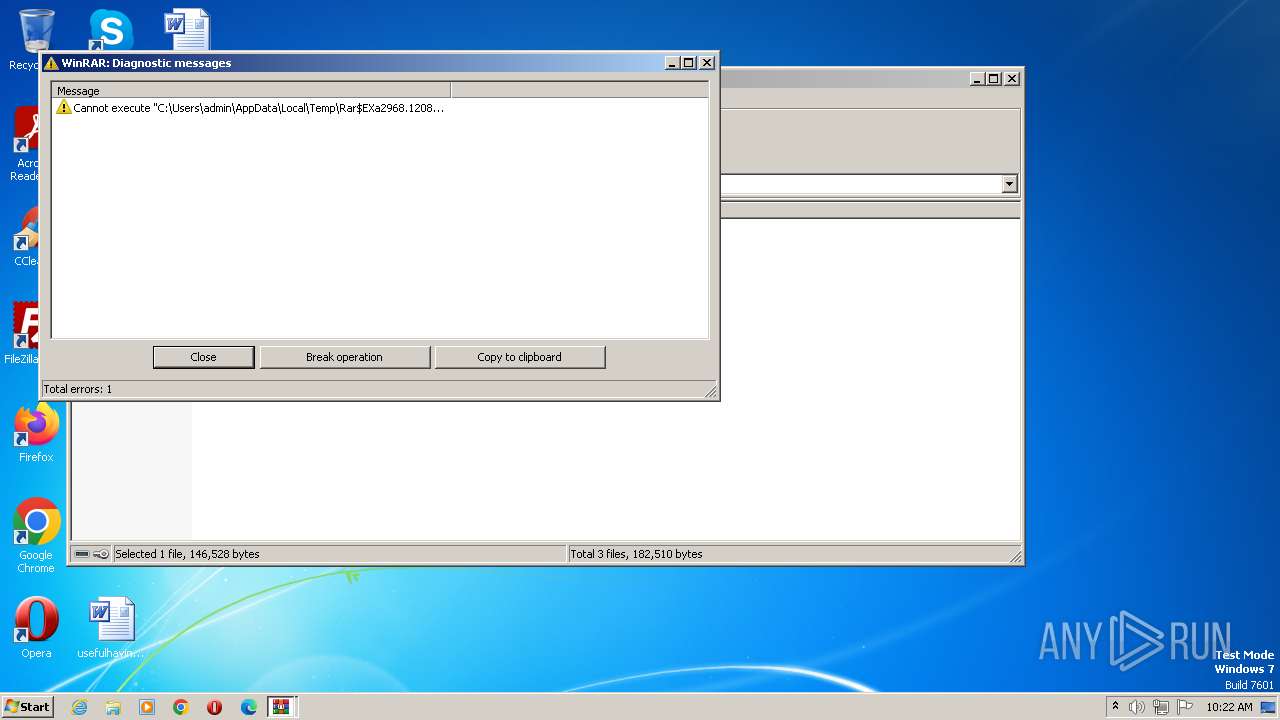
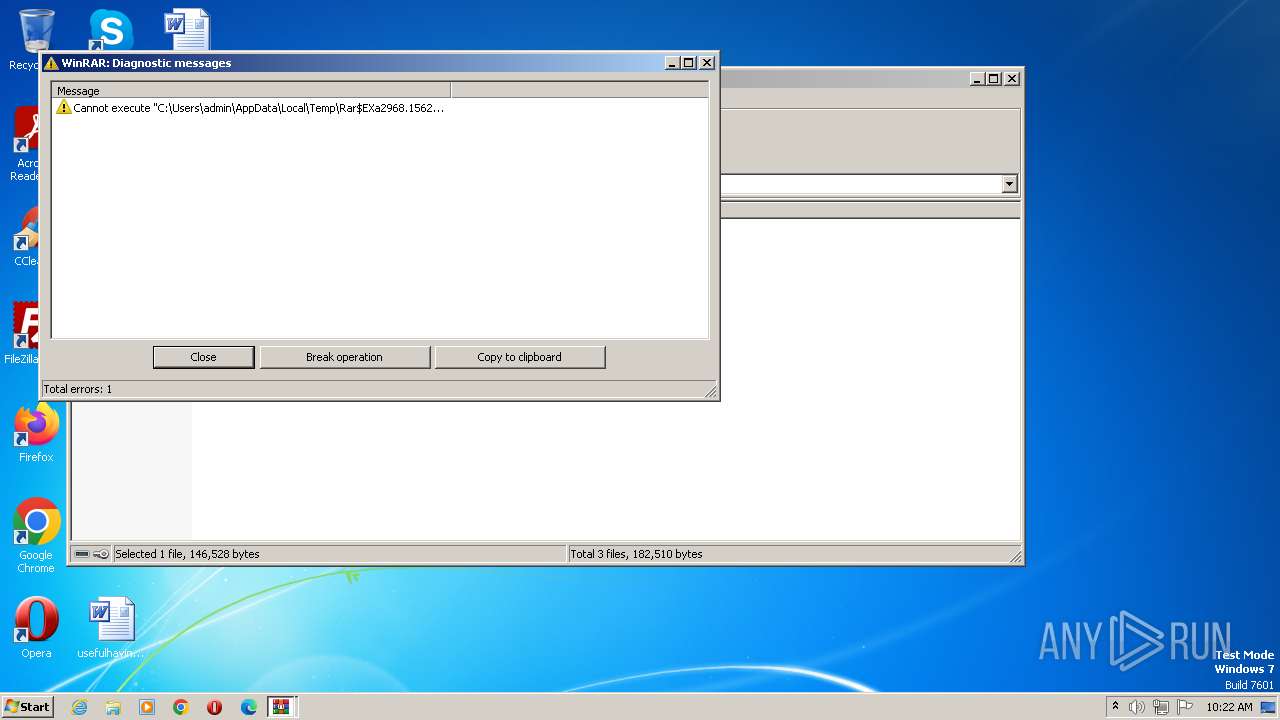
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 2968)
INFO
Create files in a temporary directory
- hh.exe (PID: 2476)
Reads the machine GUID from the registry
- hh.exe (PID: 2476)
Checks proxy server information
- hh.exe (PID: 2476)
Creates files or folders in the user directory
- hh.exe (PID: 2476)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
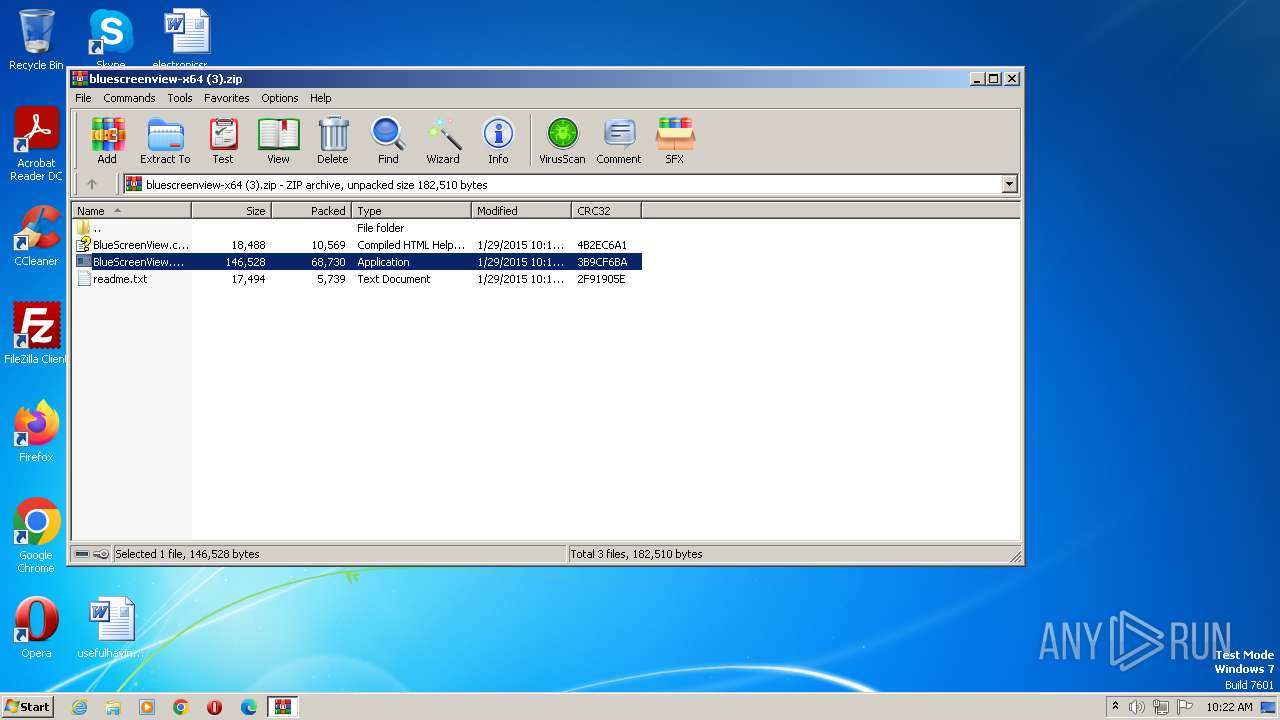
| ZipFileName: | BlueScreenView.exe |
|---|---|
| ZipUncompressedSize: | 146528 |
| ZipCompressedSize: | 68730 |
| ZipCRC: | 0x3b9cf6ba |
| ZipModifyDate: | 2015:01:29 10:11:02 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0002 |
| ZipRequiredVersion: | 20 |
Total processes
36
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1856 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2968.13582\readme.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | "C:\Windows\hh.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa2968.10713\BlueScreenView.chm | C:\Windows\hh.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2968 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\bluescreenview-x64 (3).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 506
Read events
1 478
Write events
28
Delete events
0
Modification events
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
2
Suspicious files
7
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2476 | hh.exe | C:\Users\admin\AppData\Local\Temp\~DF0F452BAE61FA9CF1.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2476 | hh.exe | C:\Users\admin\AppData\Local\Temp\~DF153BCAB84E69D0B4.TMP | binary | |
MD5:72F5C05B7EA8DD6059BF59F50B22DF33 | SHA256:1DC0C8D7304C177AD0E74D3D2F1002EB773F4B180685A7DF6BBE75CCC24B0164 | |||
| 2476 | hh.exe | C:\Users\admin\AppData\Local\Temp\IMTDEBE.tmp | binary | |
MD5:5D0E5693027A0E5ADF1D49847779B65C | SHA256:AC0710AABAAEAAC65507050647FA9D97A82639DA0D1D6B436800B177478C6D6B | |||
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2968.13582\readme.txt | text | |
MD5:ACECB7D7AF592DA7A843EF44B4500818 | SHA256:92BFF76A8CBD014A8445F6F522924DB7F29B2ADF5BDC344AC727D1C12B10E285 | |||
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2968.12080\BlueScreenView.exe | executable | |
MD5:46A20AE8BB7CDDB9A1370C640719C8DA | SHA256:09F3023554BE864F31D80F2E7E7C7E824D79A69DDF84F1F02A433E85E866282C | |||
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2968.12080\readme.txt | text | |
MD5:ACECB7D7AF592DA7A843EF44B4500818 | SHA256:92BFF76A8CBD014A8445F6F522924DB7F29B2ADF5BDC344AC727D1C12B10E285 | |||
| 2476 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\bluescreenview_icon[1].gif | image | |
MD5:24CD2FD0D73DA429FD603C8583C326DC | SHA256:2721864B146FBED038E1440DACB58438241DCA7A4749CDED31F19F81BBB01AE2 | |||
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2968.10713\BlueScreenView.chm | binary | |
MD5:D130E5001531448871BB8EF10C106B25 | SHA256:3B9D7F203E282C0AAA522F706308E2215786A2FB95E9FFB86E97168FFFFE3009 | |||
| 2476 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\main[1].css | text | |
MD5:7B11CD3A728D510B0BD92AD7E49F94FB | SHA256:B3C3AA3425B6601BB8AED17AB9894658D44B381F132A9F3562342EA534BE0BFA | |||
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2968.15629\readme.txt | text | |
MD5:ACECB7D7AF592DA7A843EF44B4500818 | SHA256:92BFF76A8CBD014A8445F6F522924DB7F29B2ADF5BDC344AC727D1C12B10E285 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |