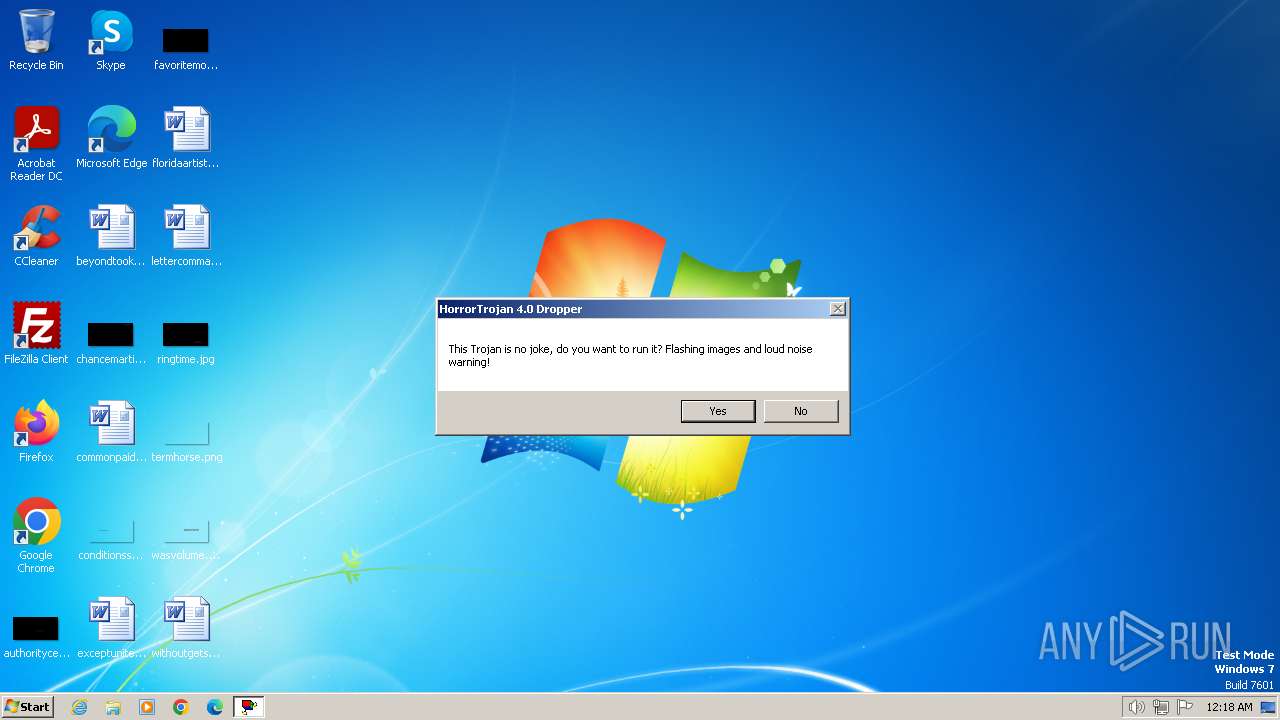
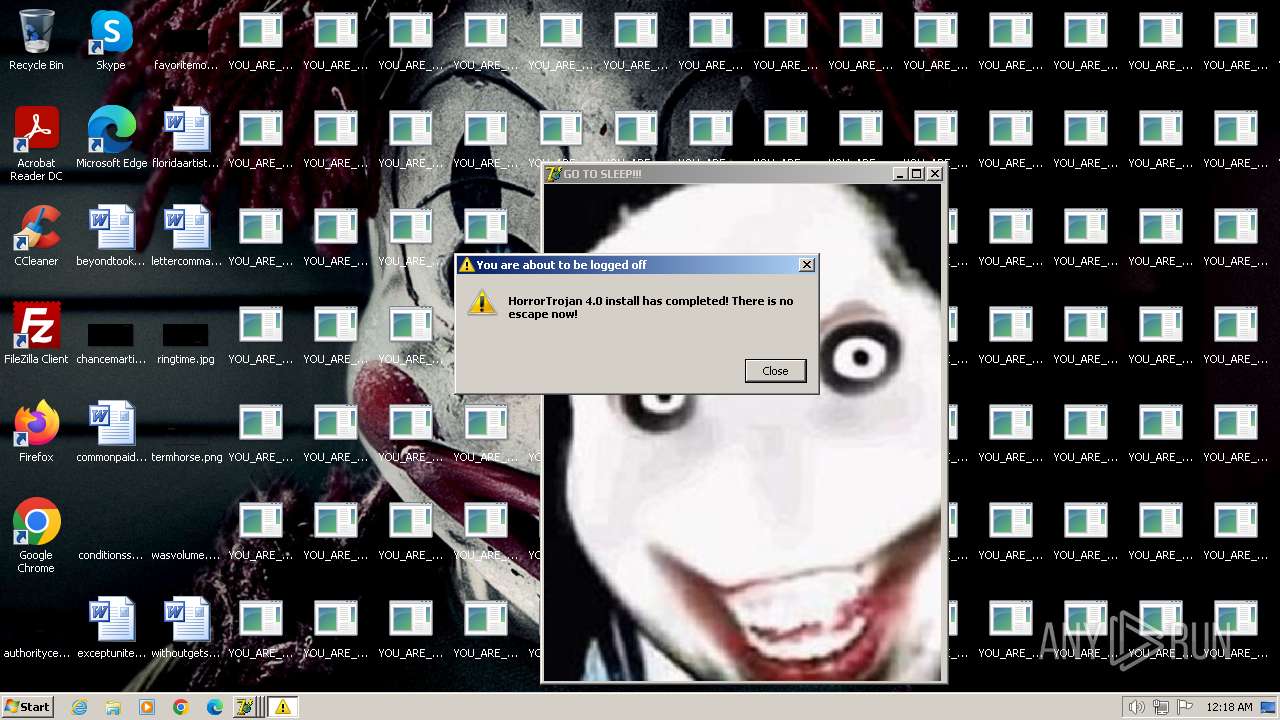
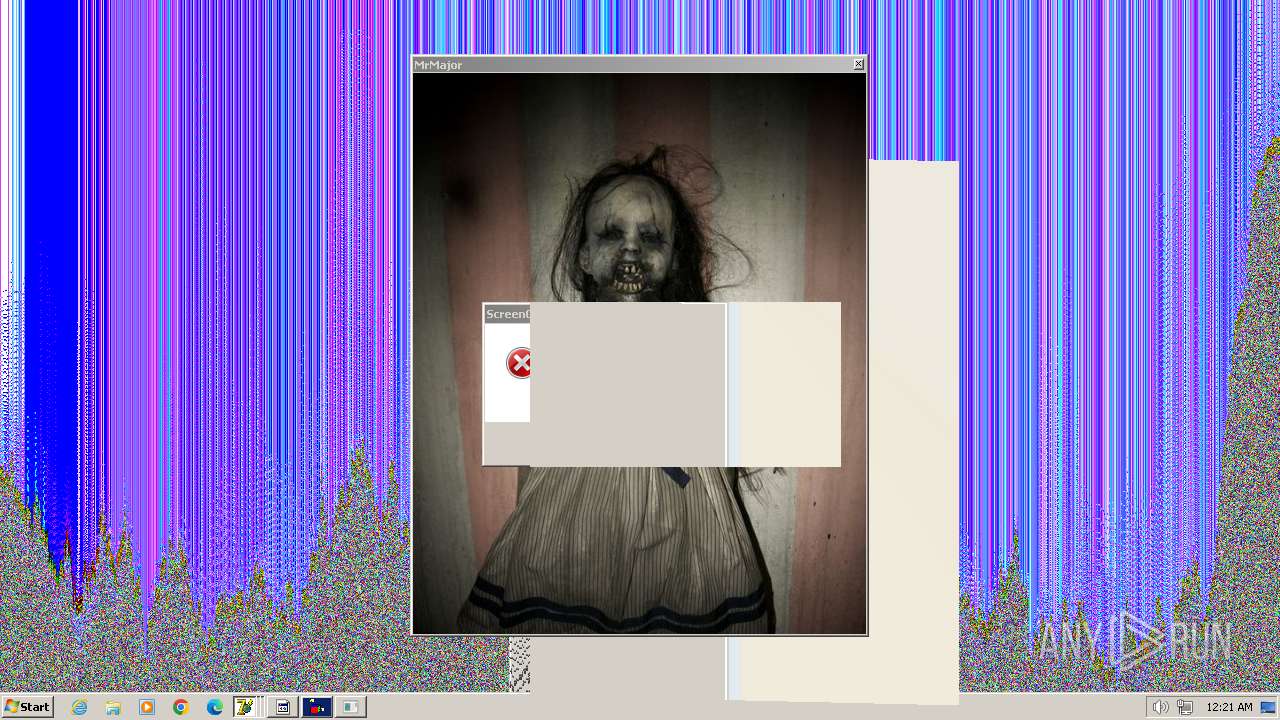
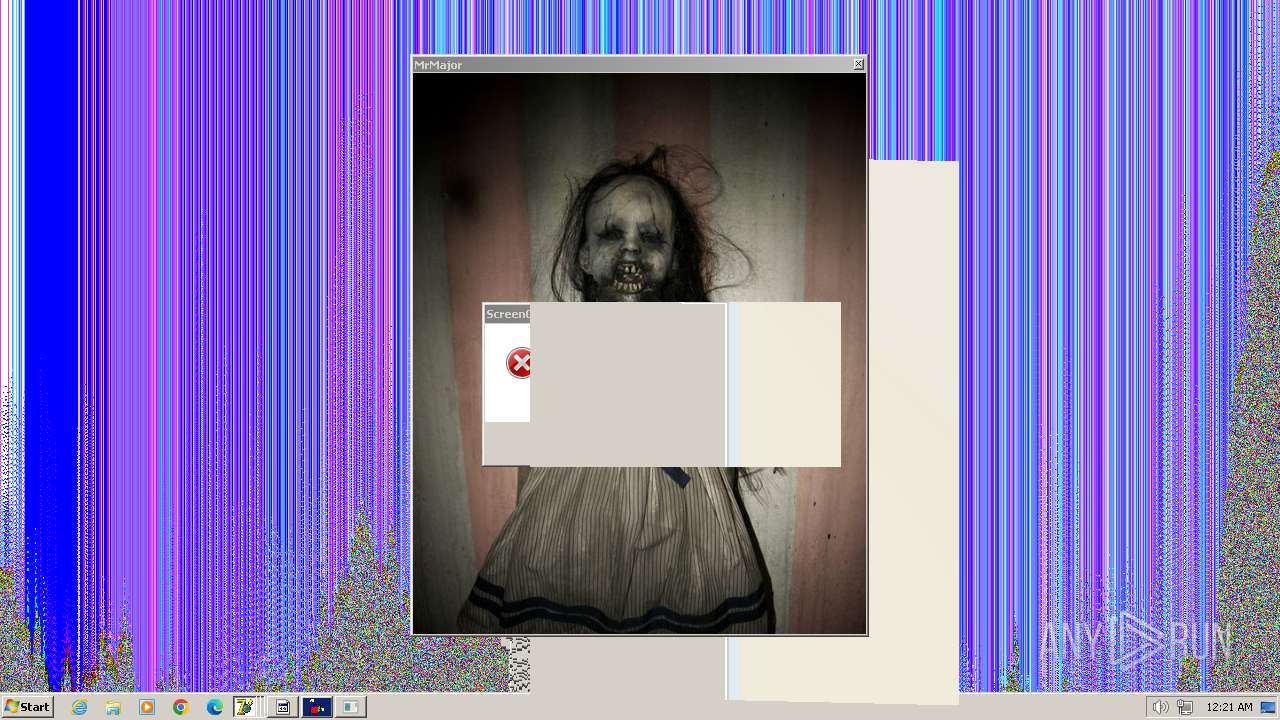
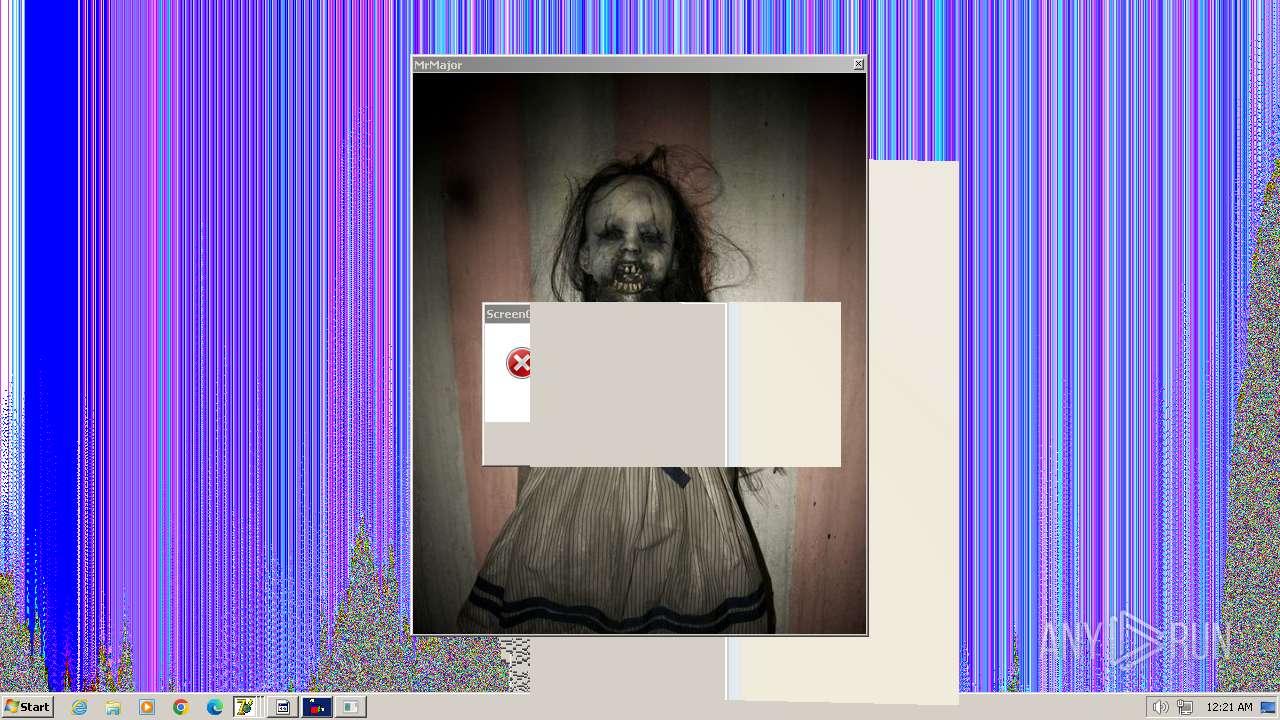
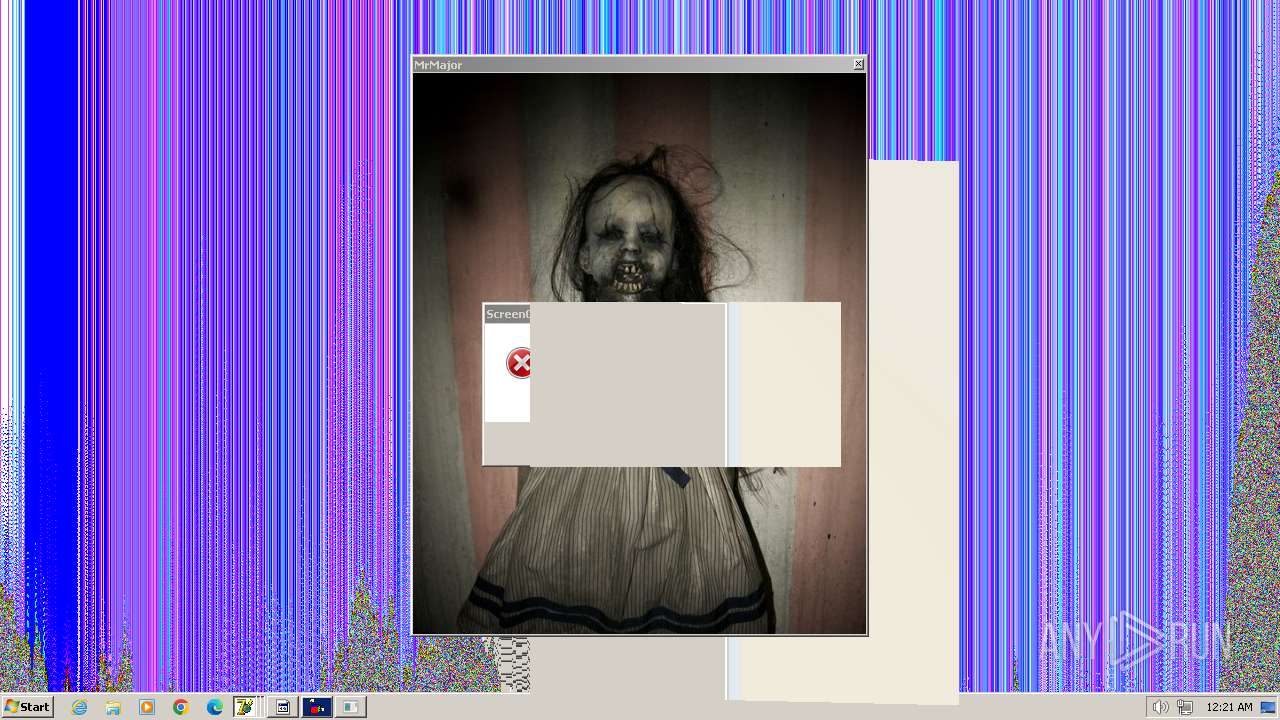
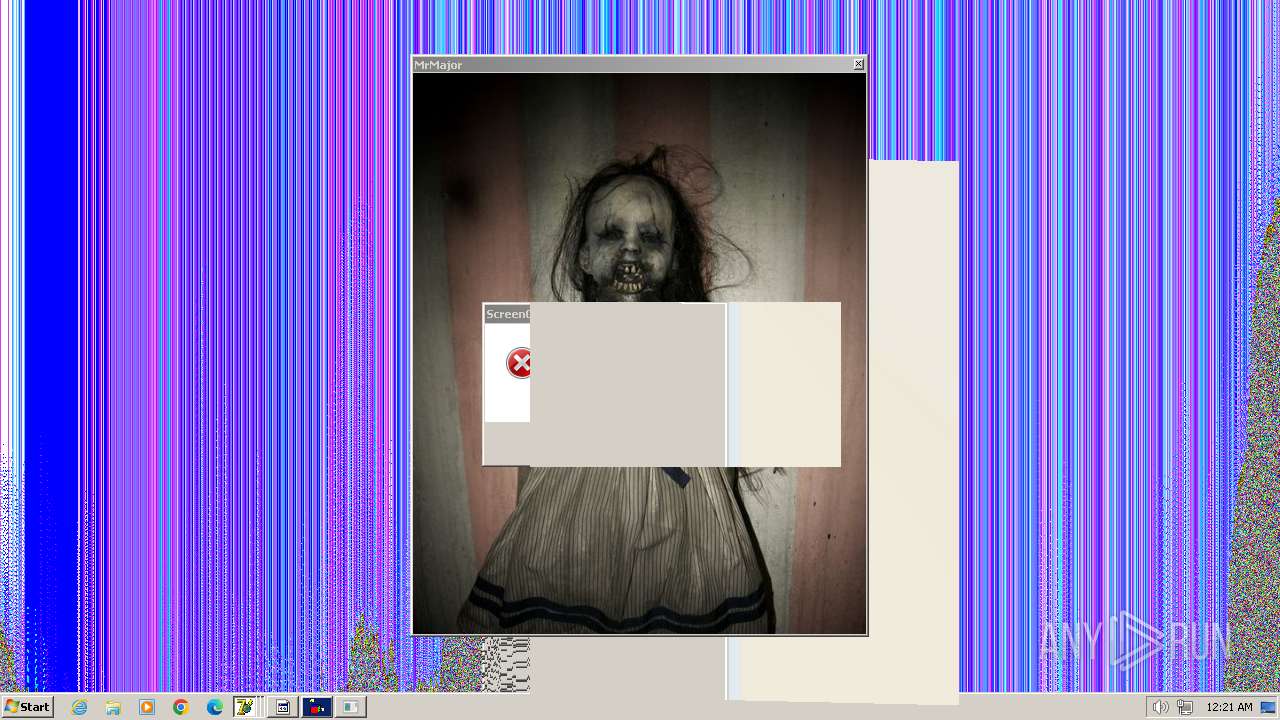
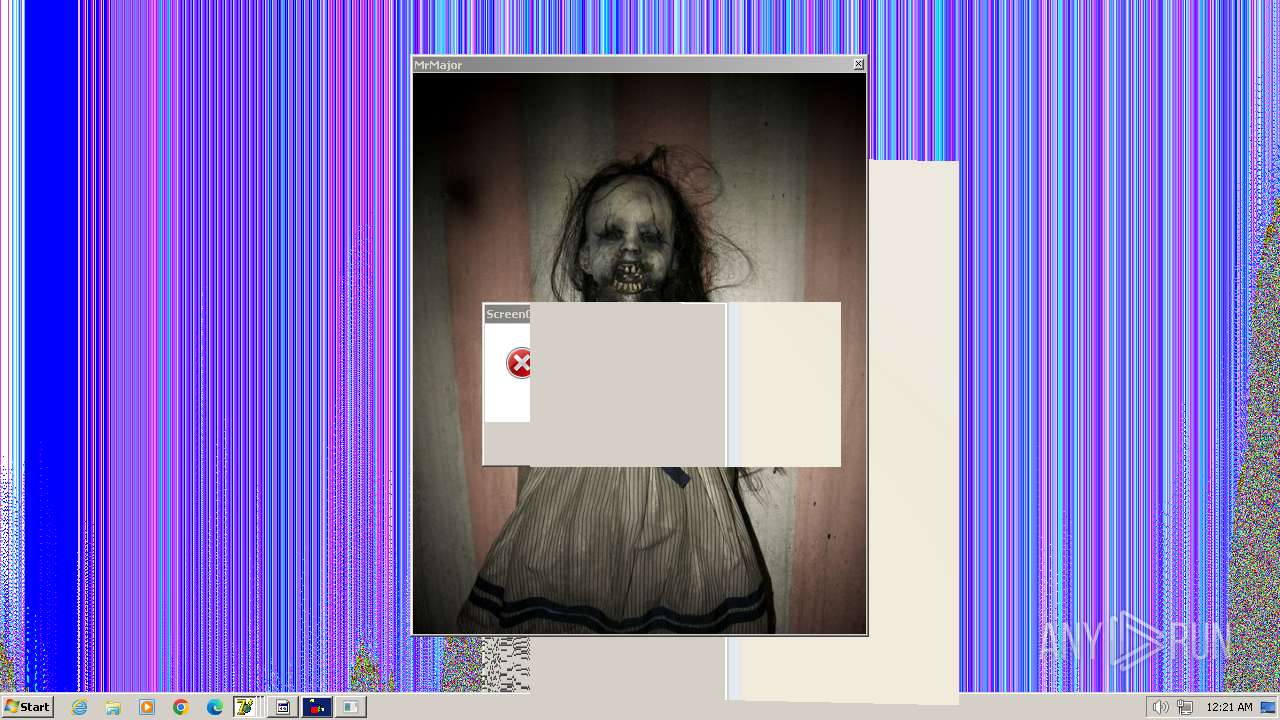
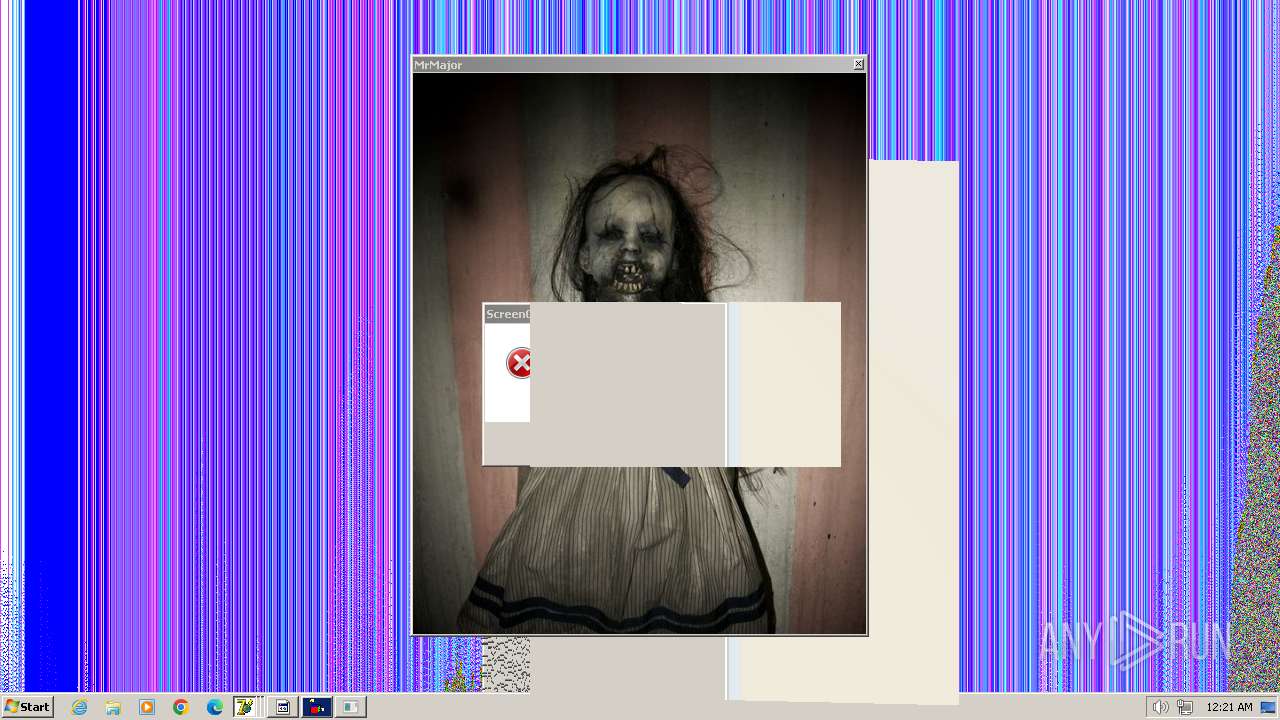
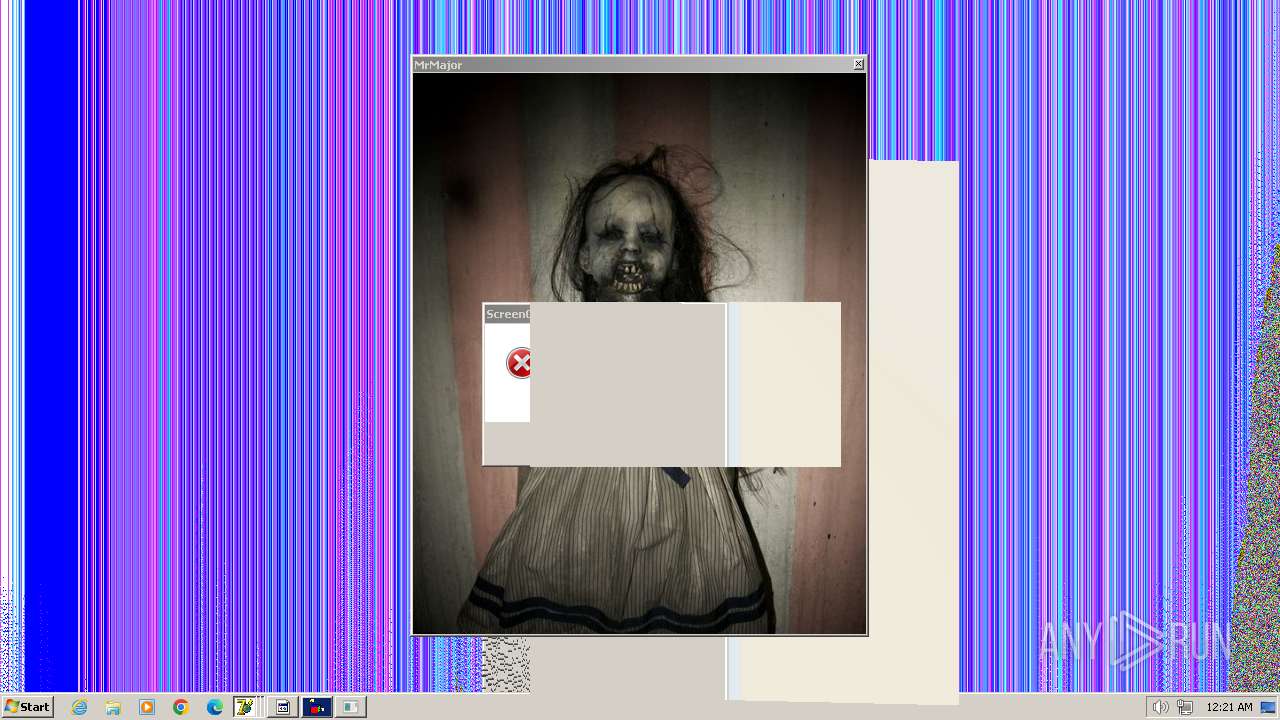
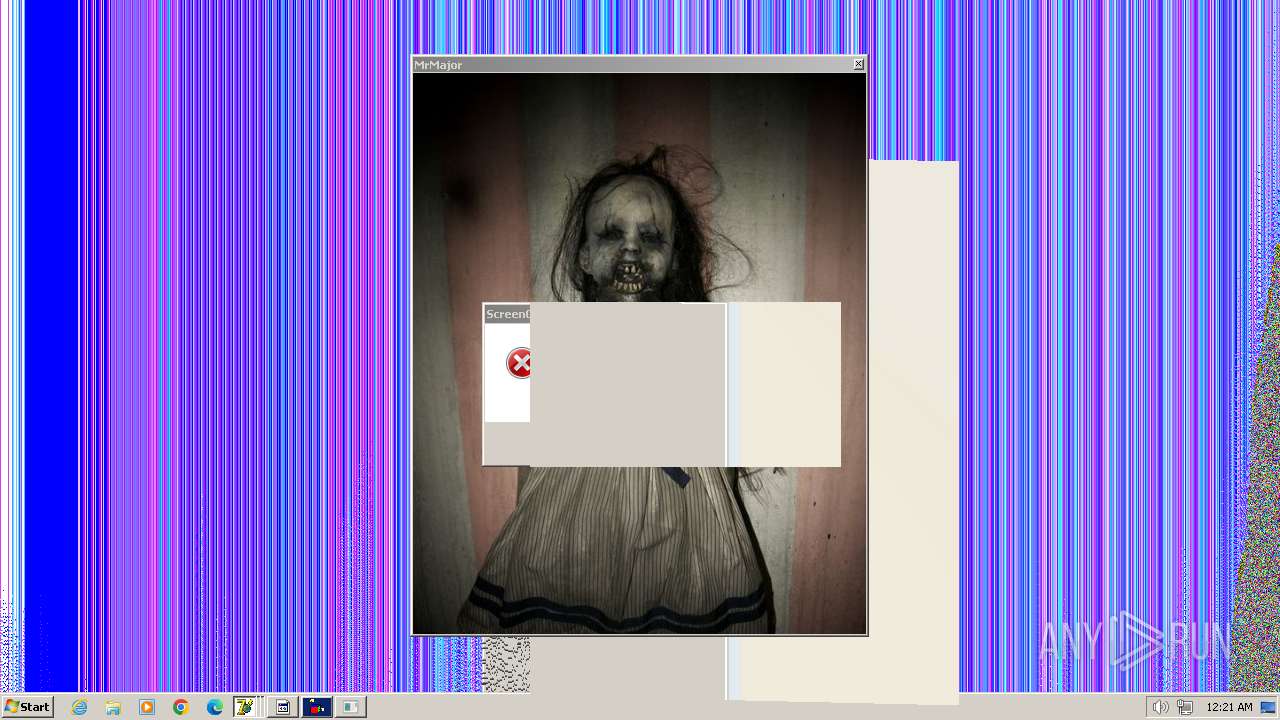
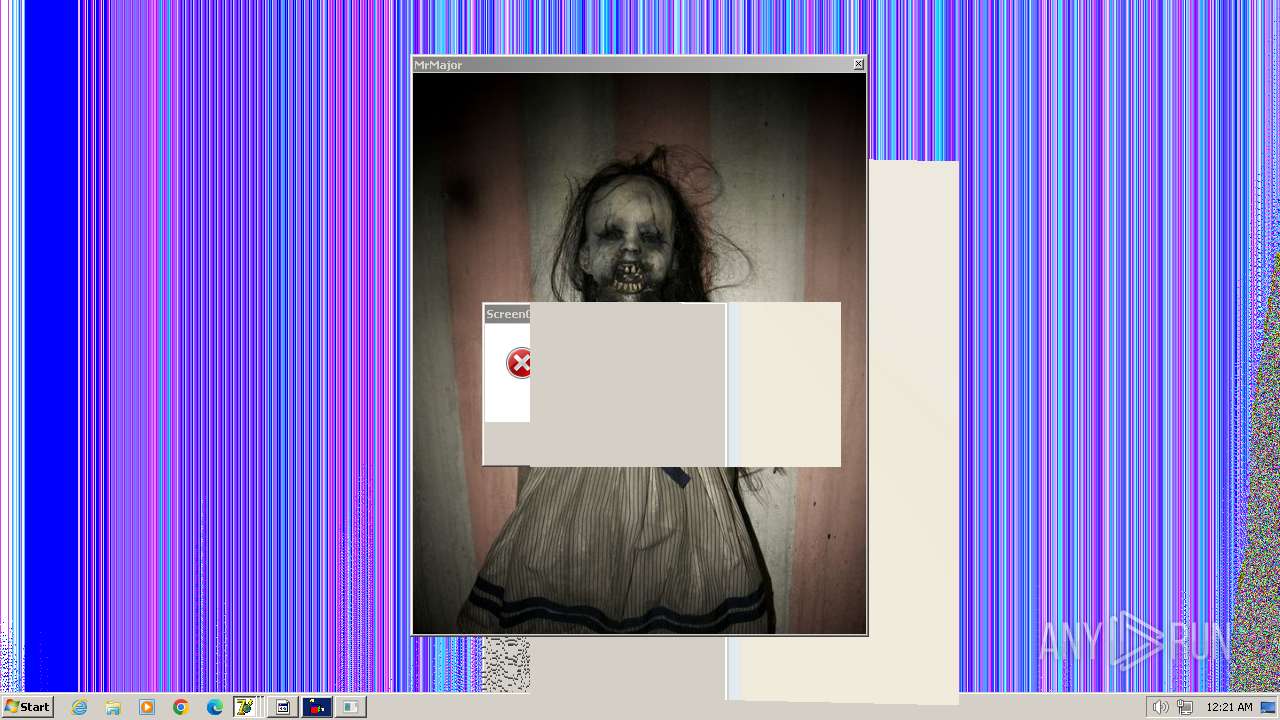
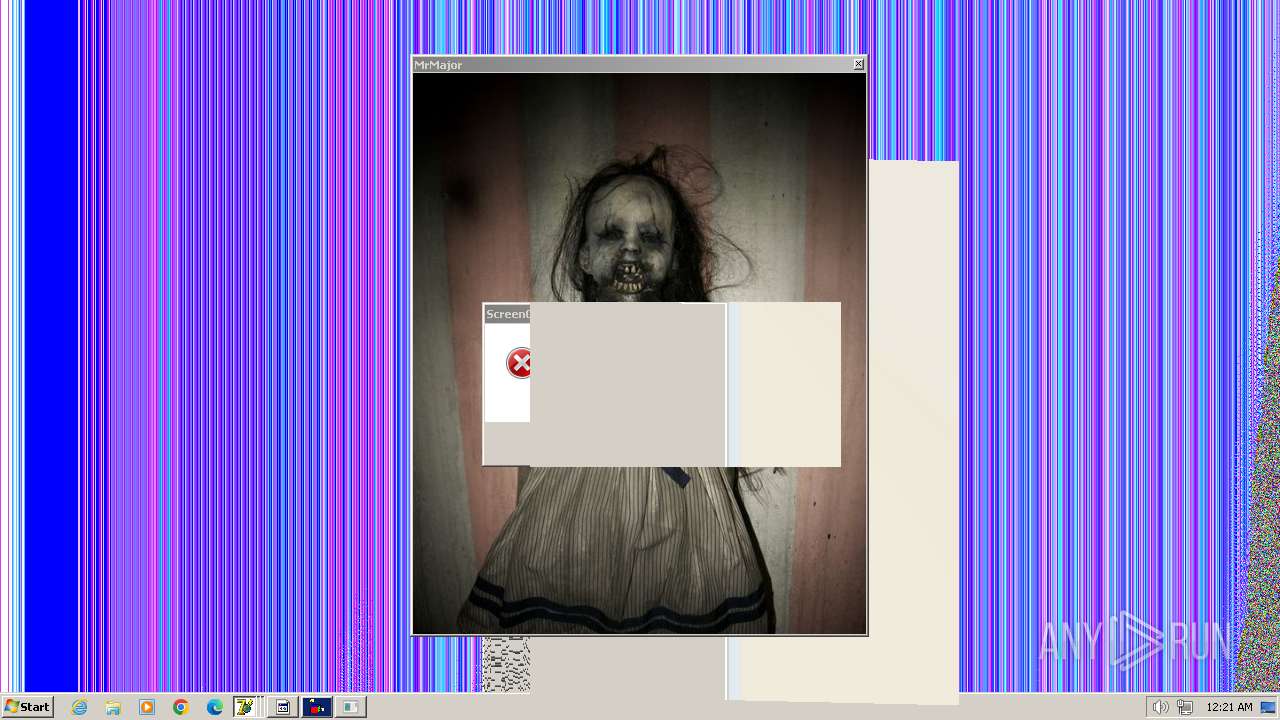
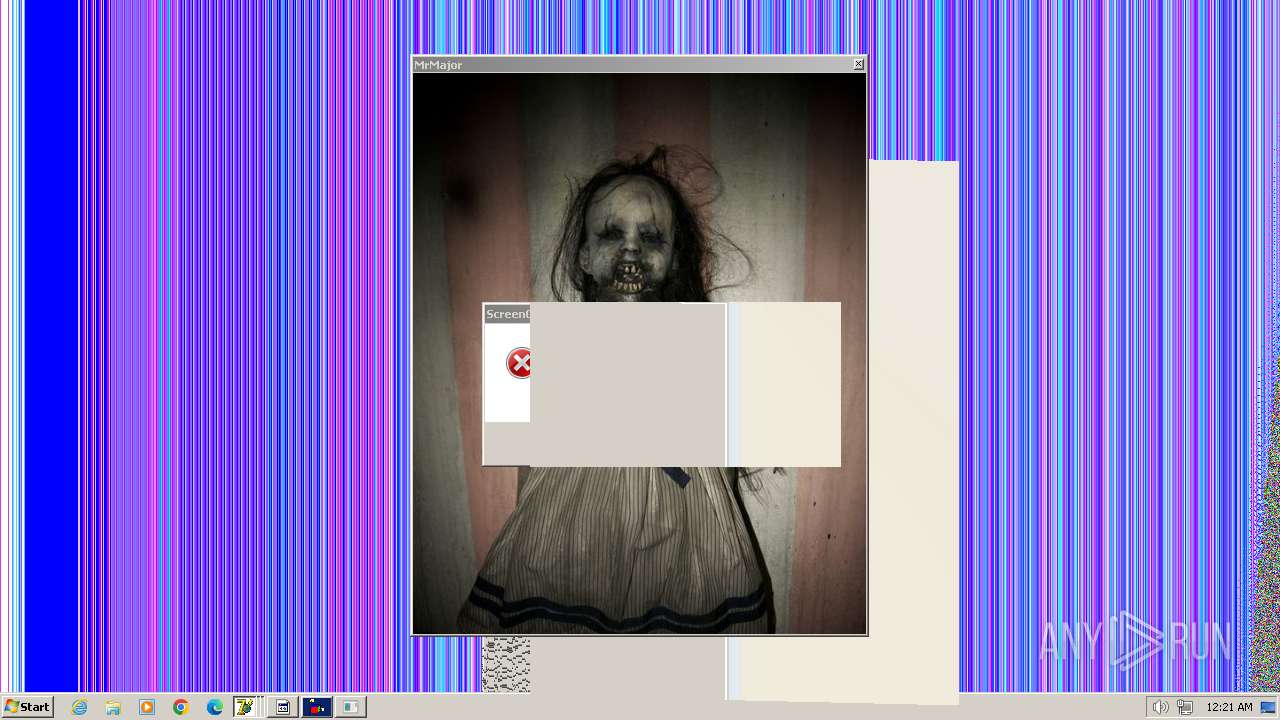
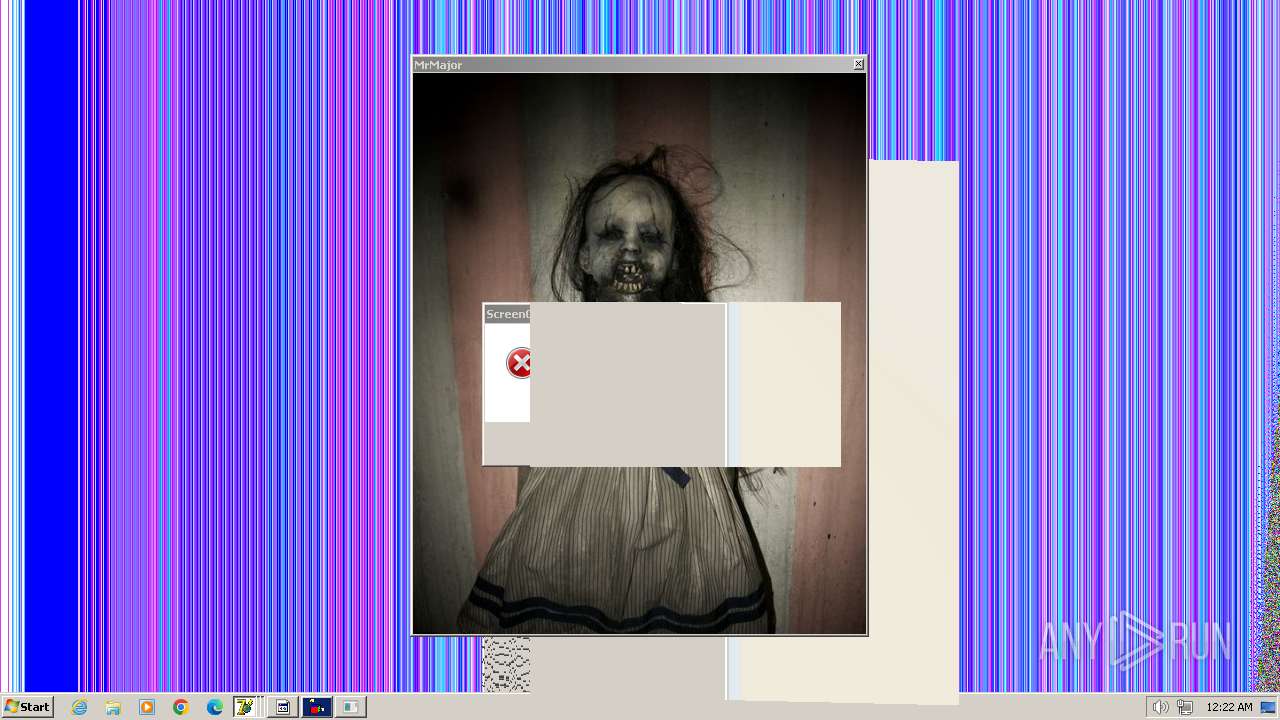
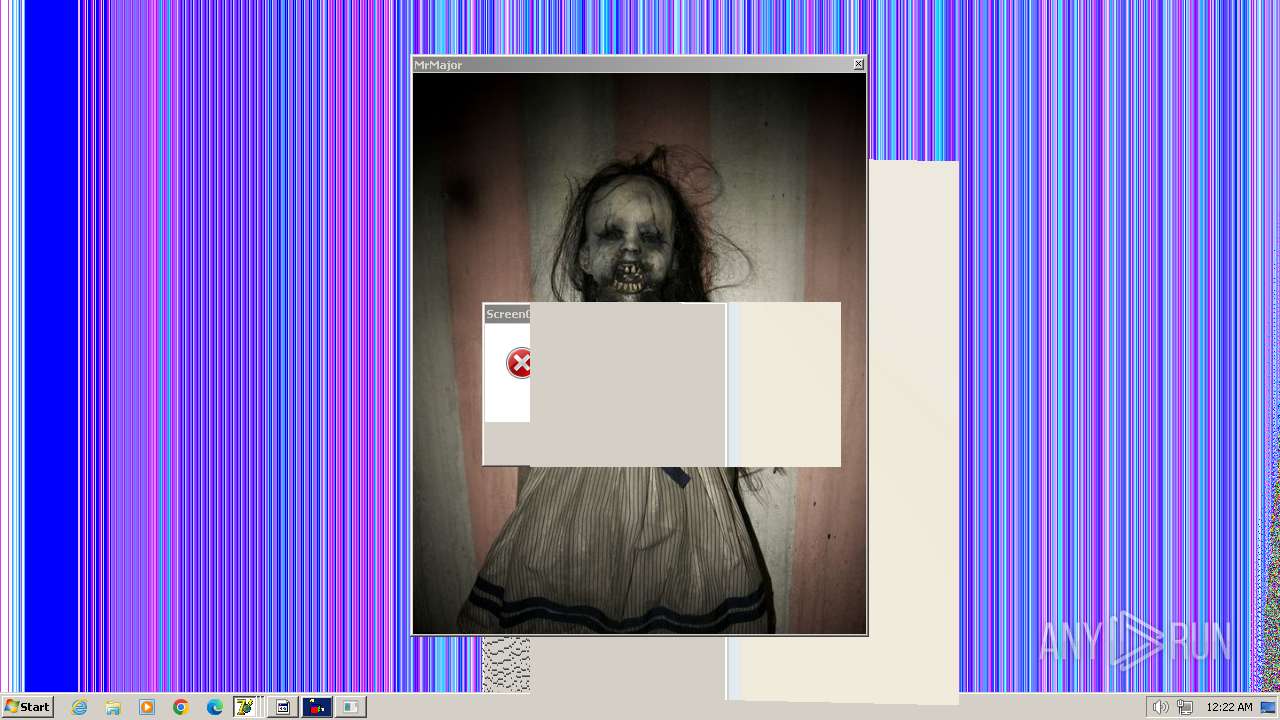
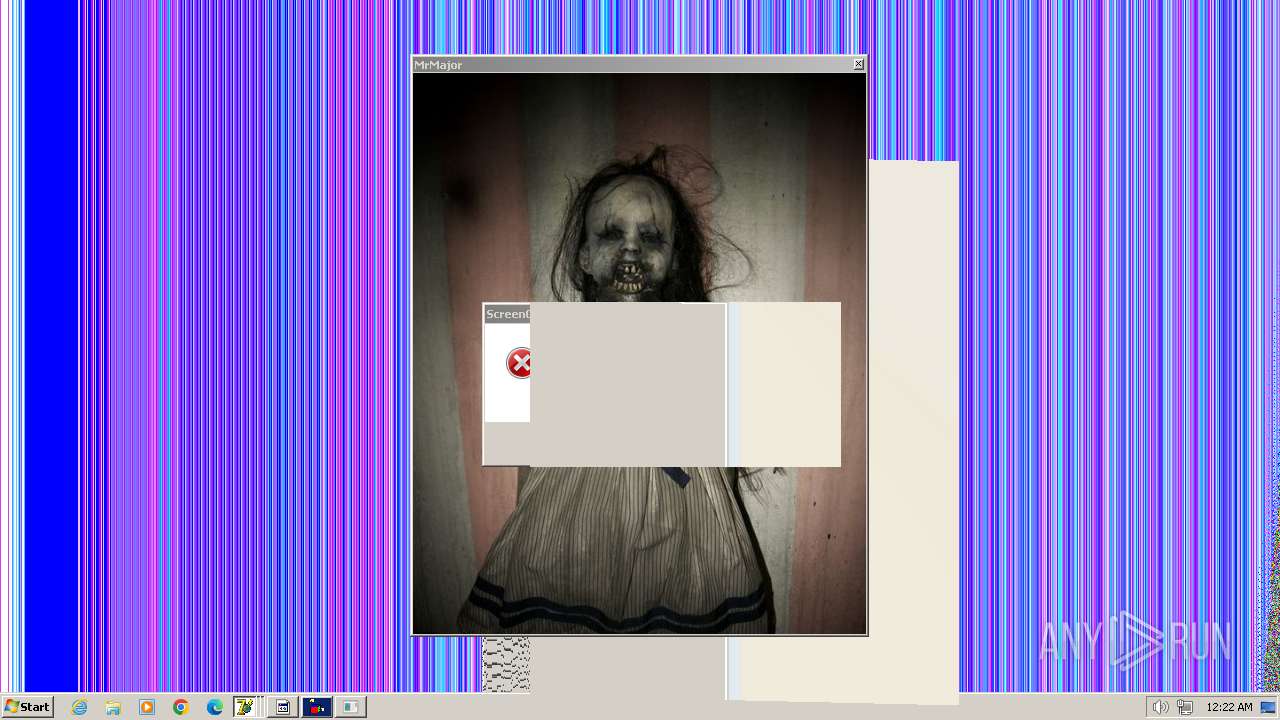
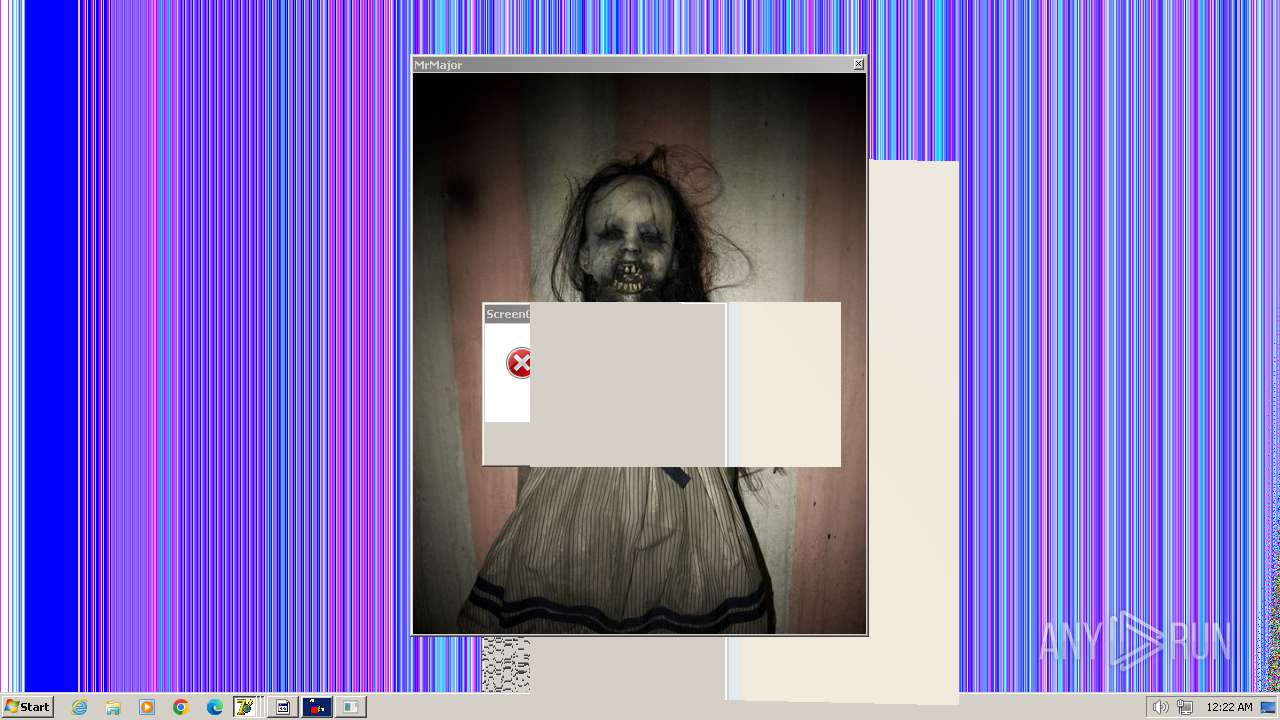
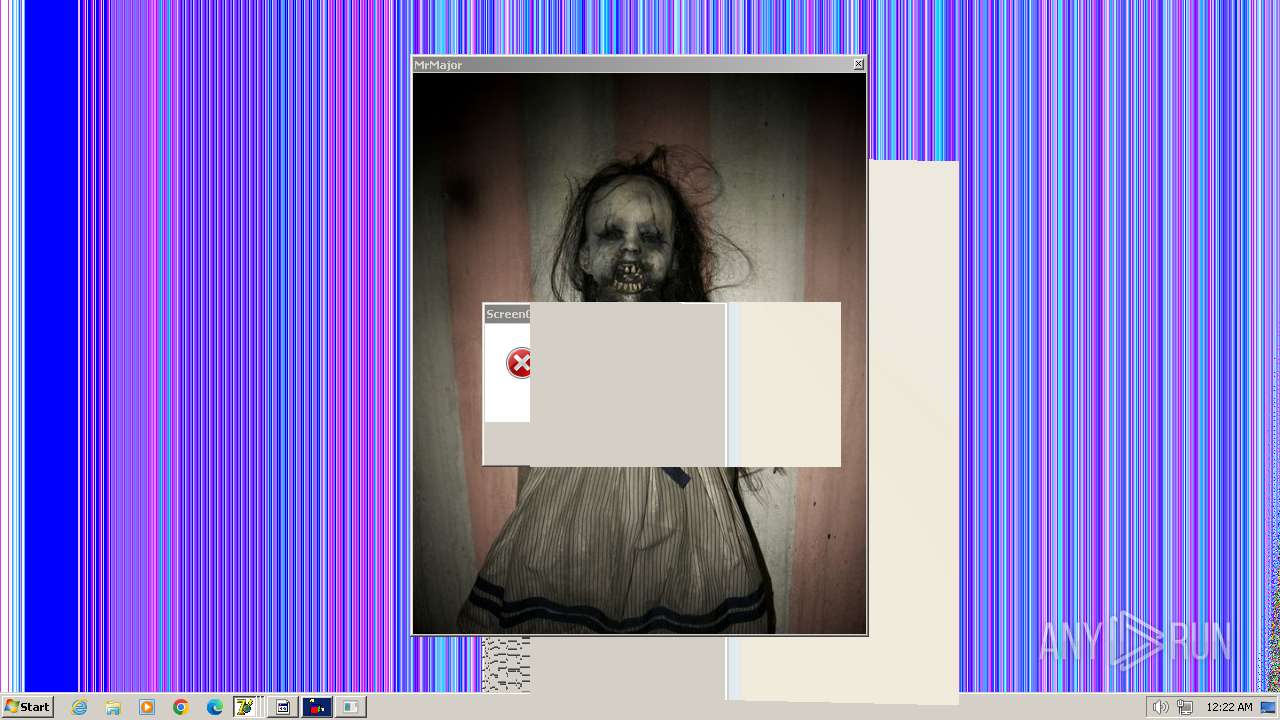
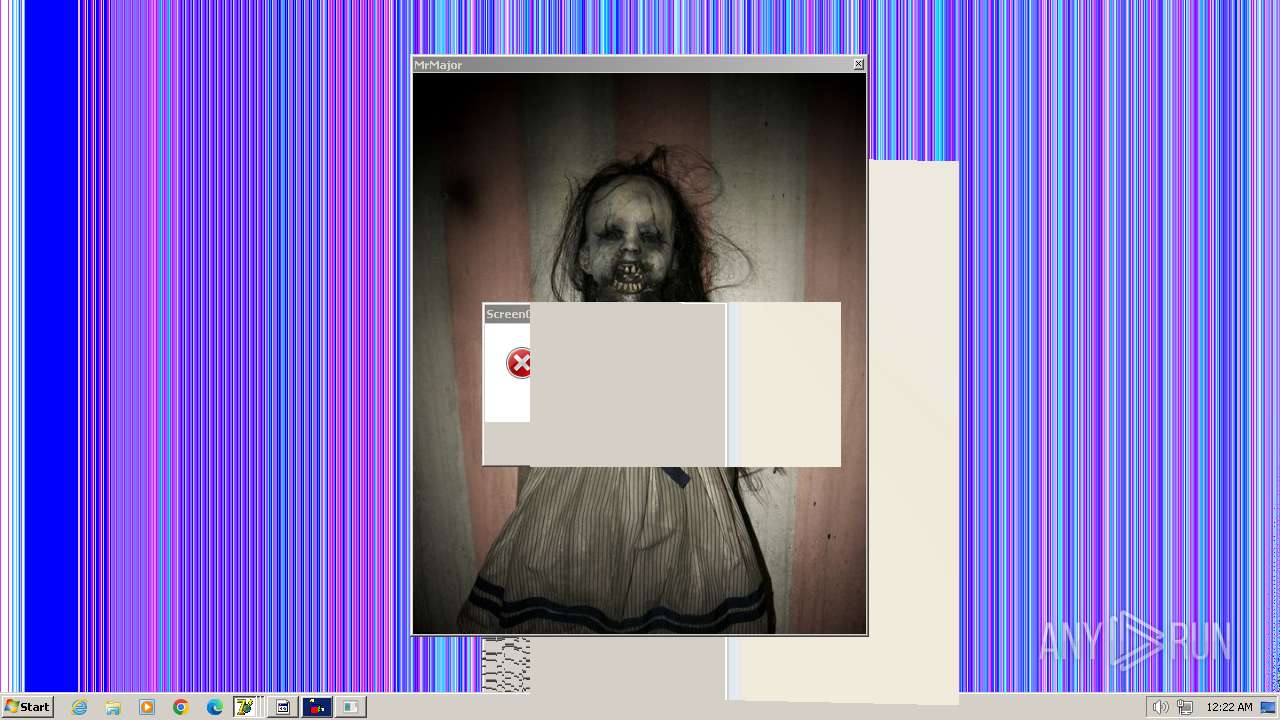
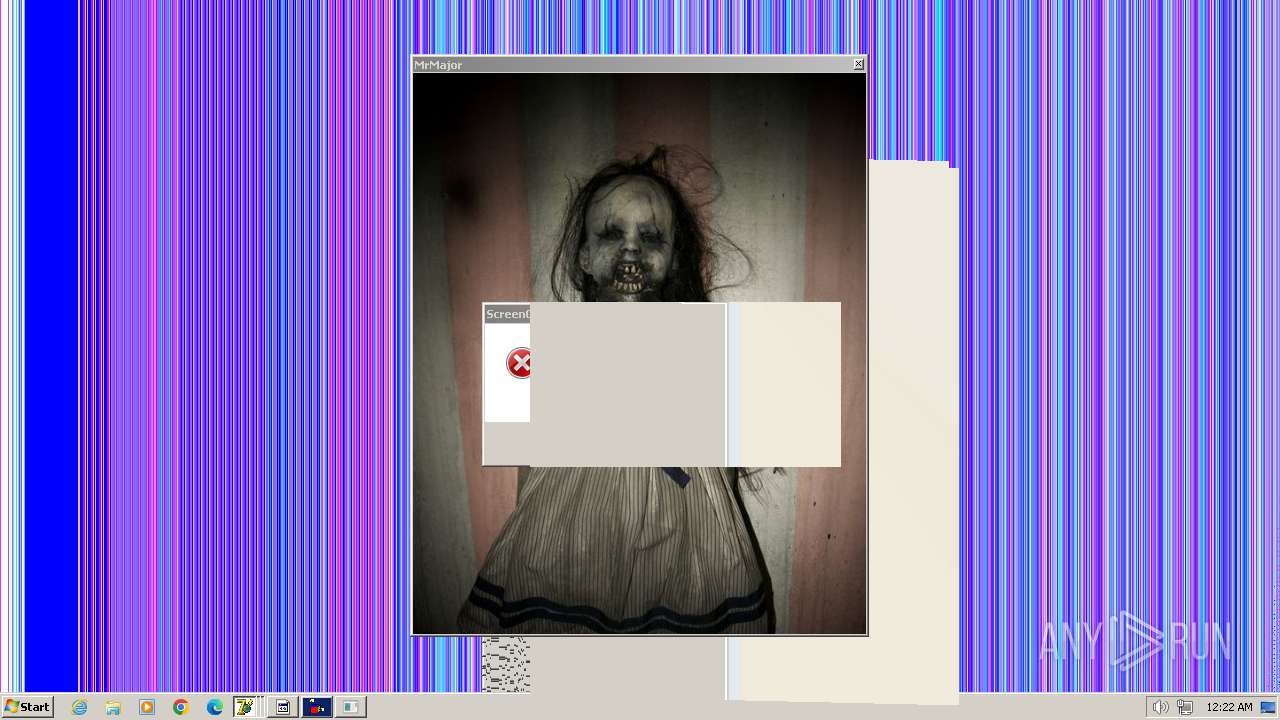
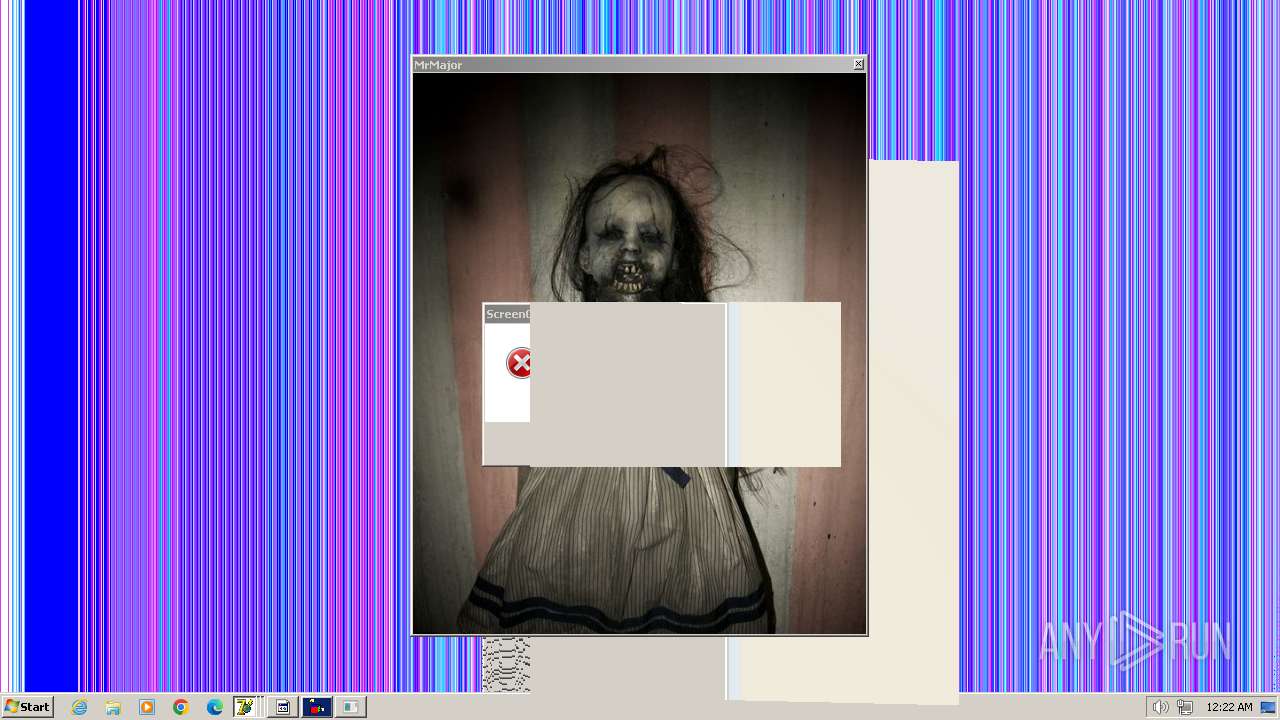
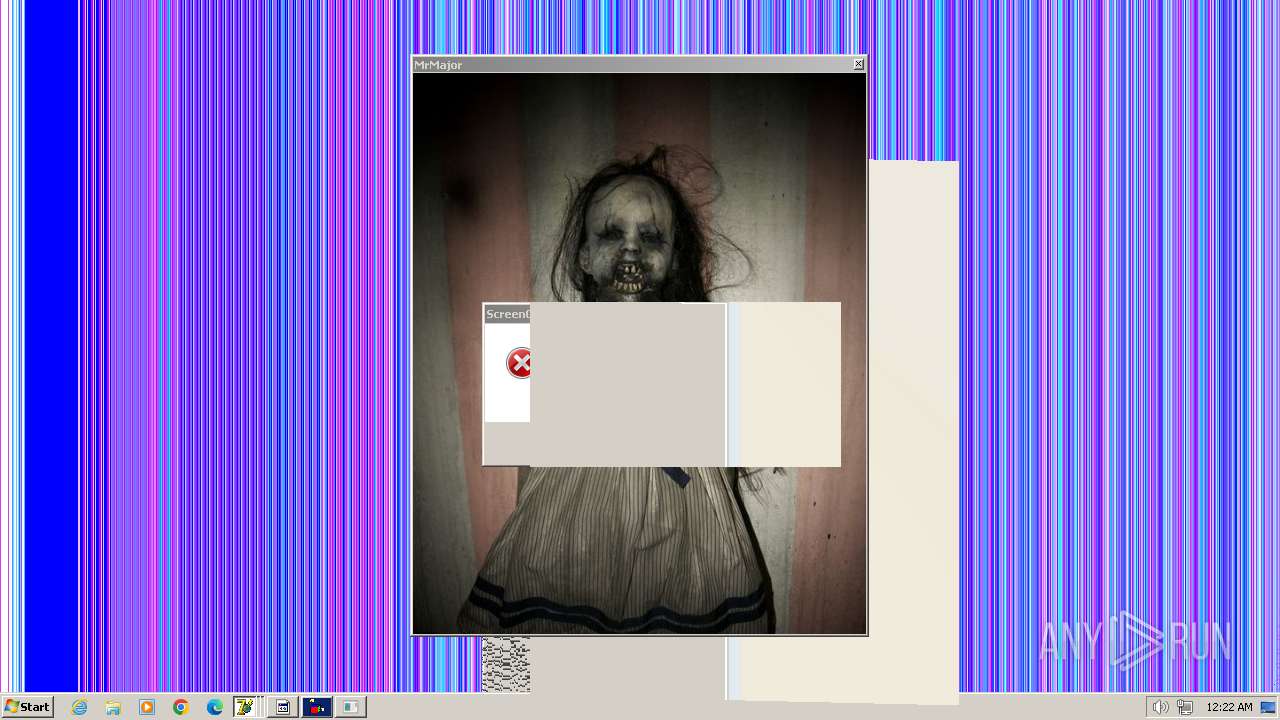
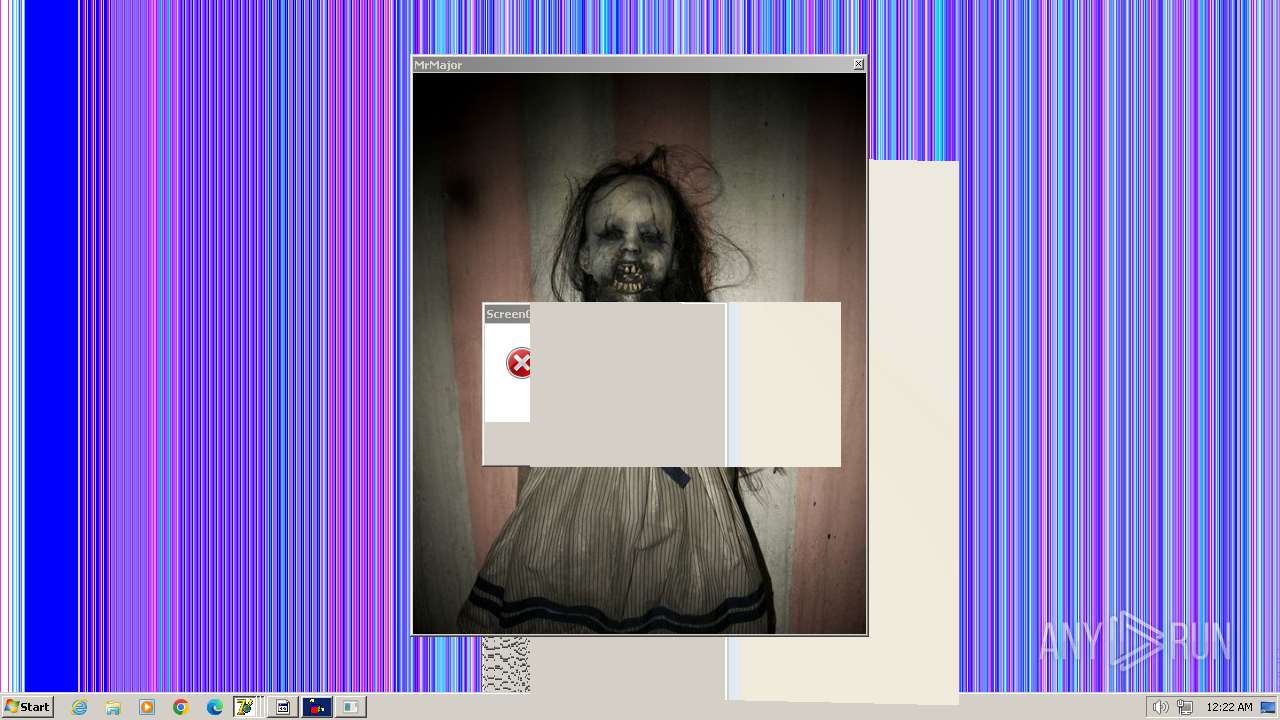
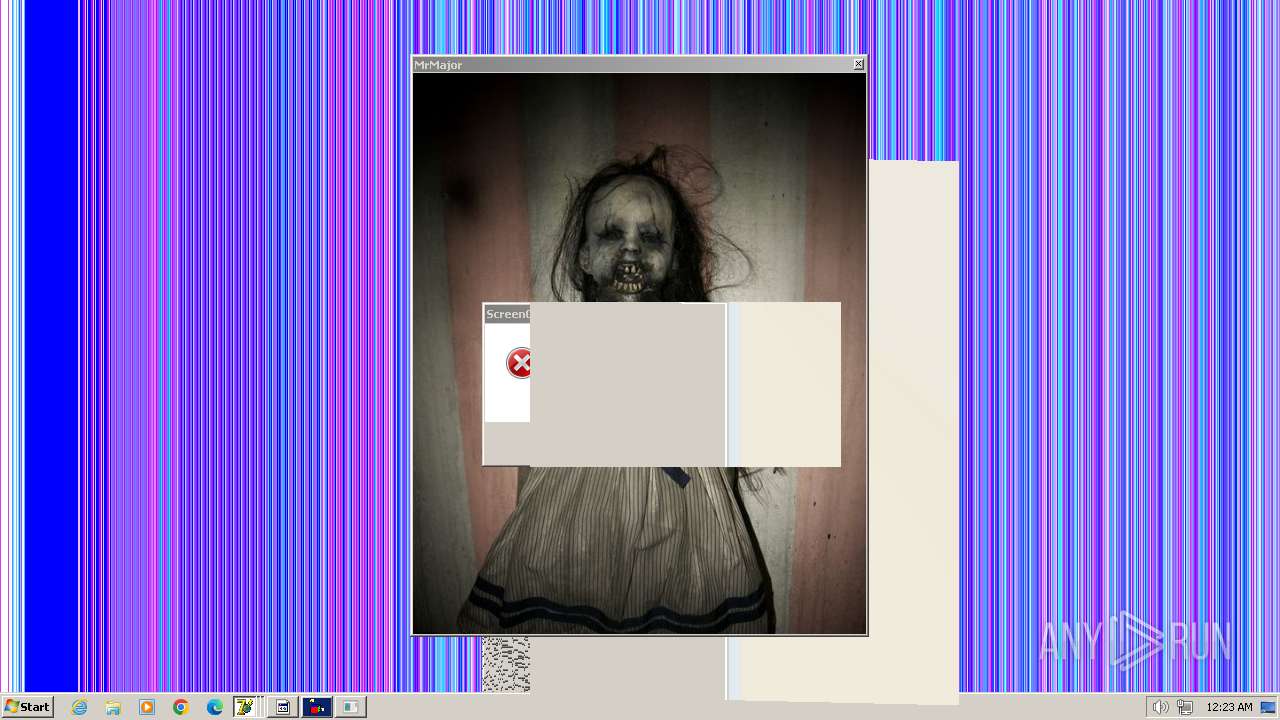
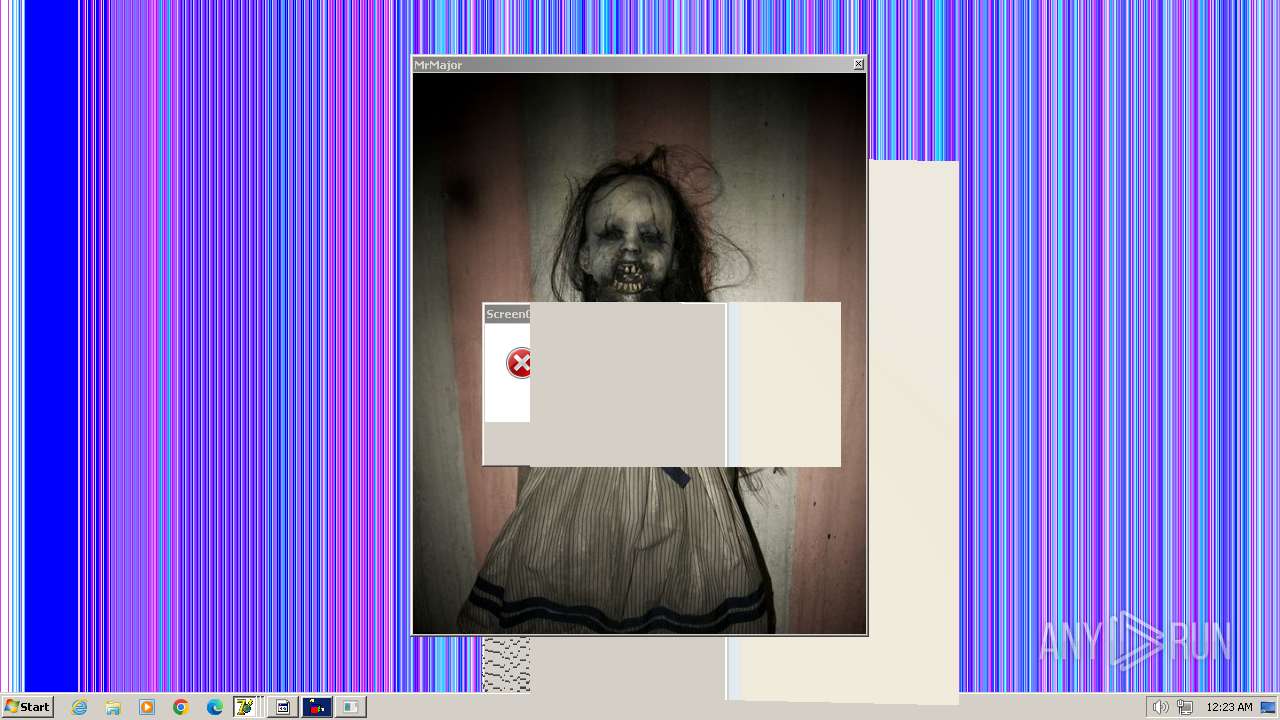
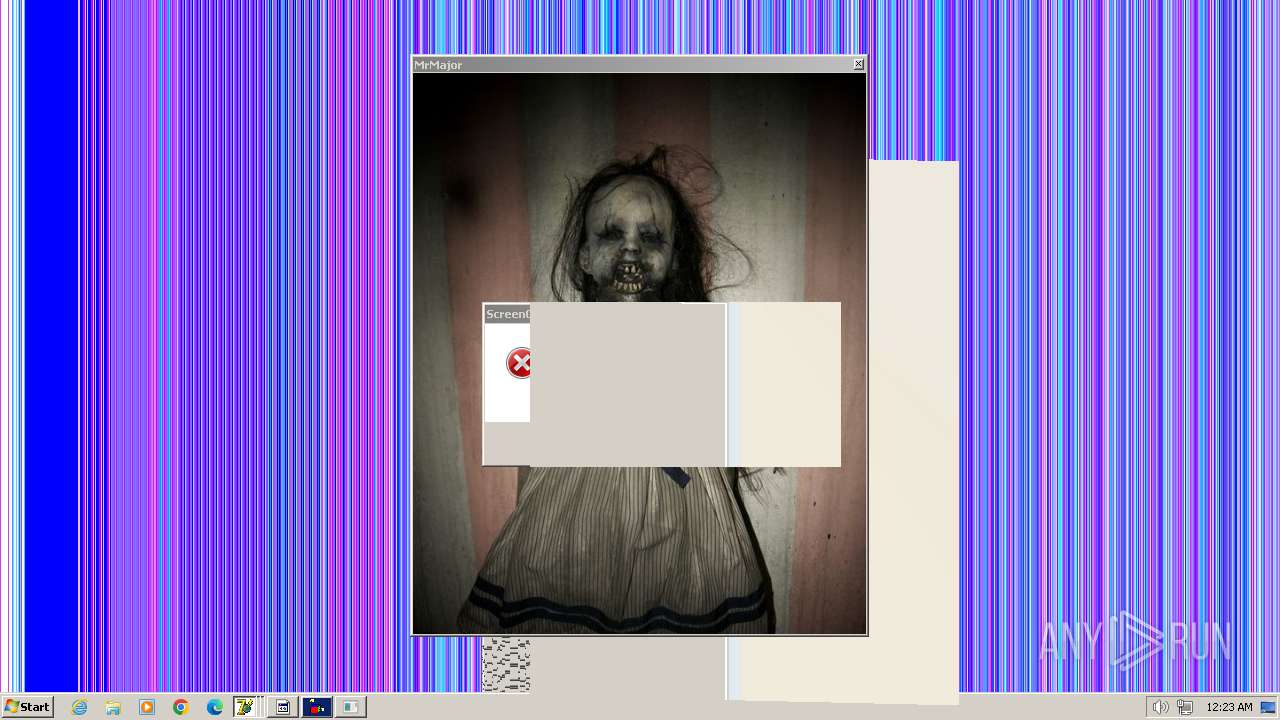
| File name: | HorrorTrojan4.exe |
| Full analysis: | https://app.any.run/tasks/9cb7ff80-1169-433a-834d-f9d957e6e2a0 |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2024, 00:18:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 776C50B8E115FA57E9BD1A52E39D486C |
| SHA1: | EDC9CFC9FF7370F006AEBF6DEB9605F7F859153C |
| SHA256: | DF5716773A8C3E09D24C62B738D33FC40D6B74590F03A269FB40521946CE832F |
| SSDEEP: | 98304:64po9x1PWEN0GpV62sYrx5bCAKP6FPqCYUjLXLaqRDX0jzoLJ+zvVTBLYGr34zVi:P |
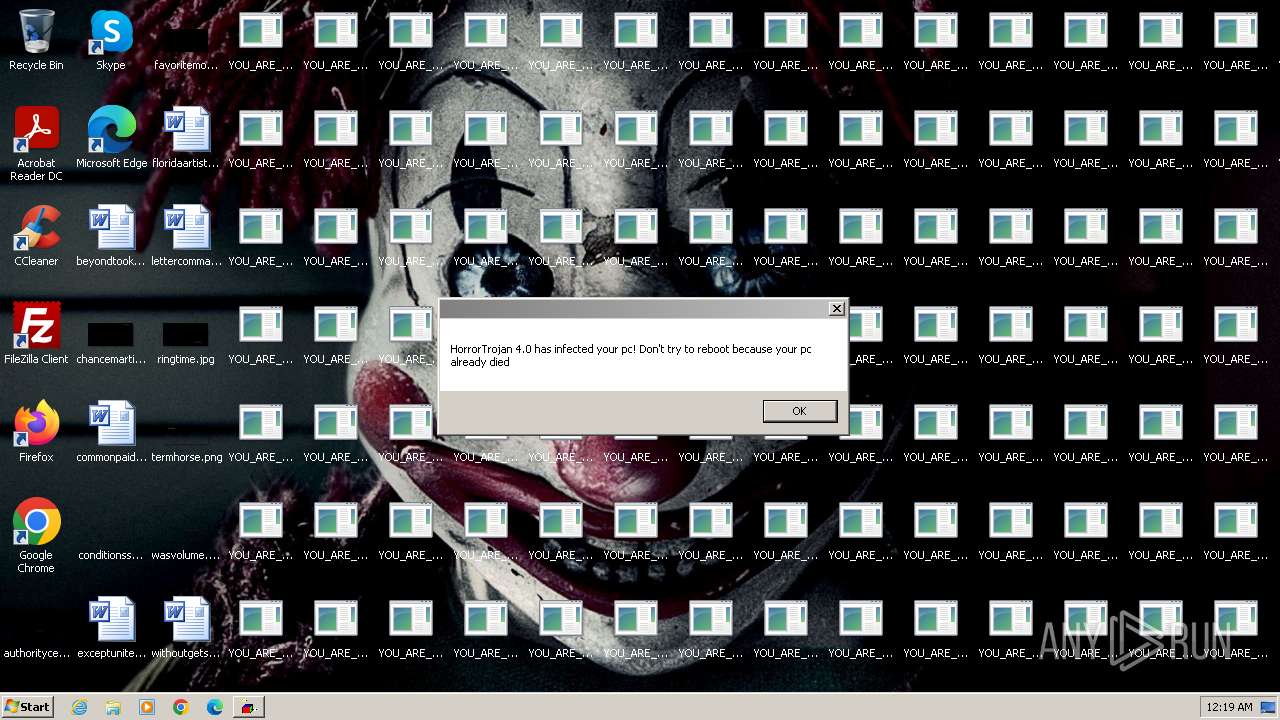
MALICIOUS
Drops the executable file immediately after the start
- HorrorTrojan4.exe (PID: 2848)
- cmd.exe (PID: 3848)
- SystemLoaderPRO.exe (PID: 2156)
Changes the autorun value in the registry
- reg.exe (PID: 3956)
- MBRKill.exe (PID: 2316)
UAC/LUA settings modification
- reg.exe (PID: 3940)
Disables Windows Defender
- reg.exe (PID: 3996)
Deletes shadow copies
- cmd.exe (PID: 3848)
- cmd.exe (PID: 2232)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 3848)
- net.exe (PID: 1576)
SUSPICIOUS
Starts CMD.EXE for commands execution
- HorrorTrojan4.exe (PID: 2848)
- SystemLoaderPRO.exe (PID: 2156)
Executable content was dropped or overwritten
- HorrorTrojan4.exe (PID: 2848)
- cmd.exe (PID: 3848)
- SystemLoaderPRO.exe (PID: 2156)
The process executes VB scripts
- cmd.exe (PID: 3848)
- cmd.exe (PID: 2232)
Executing commands from a ".bat" file
- HorrorTrojan4.exe (PID: 2848)
- SystemLoaderPRO.exe (PID: 2156)
Reads the Internet Settings
- HorrorTrojan4.exe (PID: 2848)
- cmd.exe (PID: 3848)
- WMIC.exe (PID: 2364)
- sipnotify.exe (PID: 1116)
- SystemLoaderPRO.exe (PID: 2156)
- WMIC.exe (PID: 2508)
- cmd.exe (PID: 2232)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3848)
Reads security settings of Internet Explorer
- HorrorTrojan4.exe (PID: 2848)
- SystemLoaderPRO.exe (PID: 2156)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 3848)
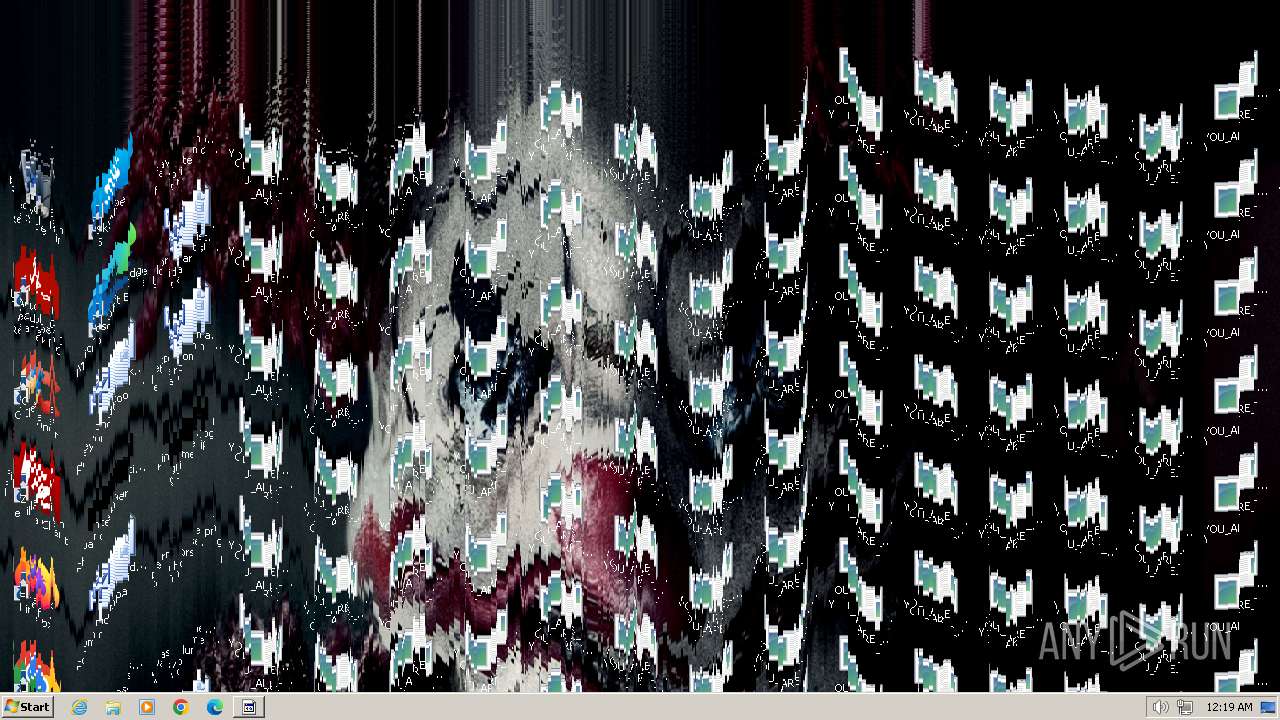
Changes the desktop background image
- reg.exe (PID: 2856)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3848)
- cmd.exe (PID: 2232)
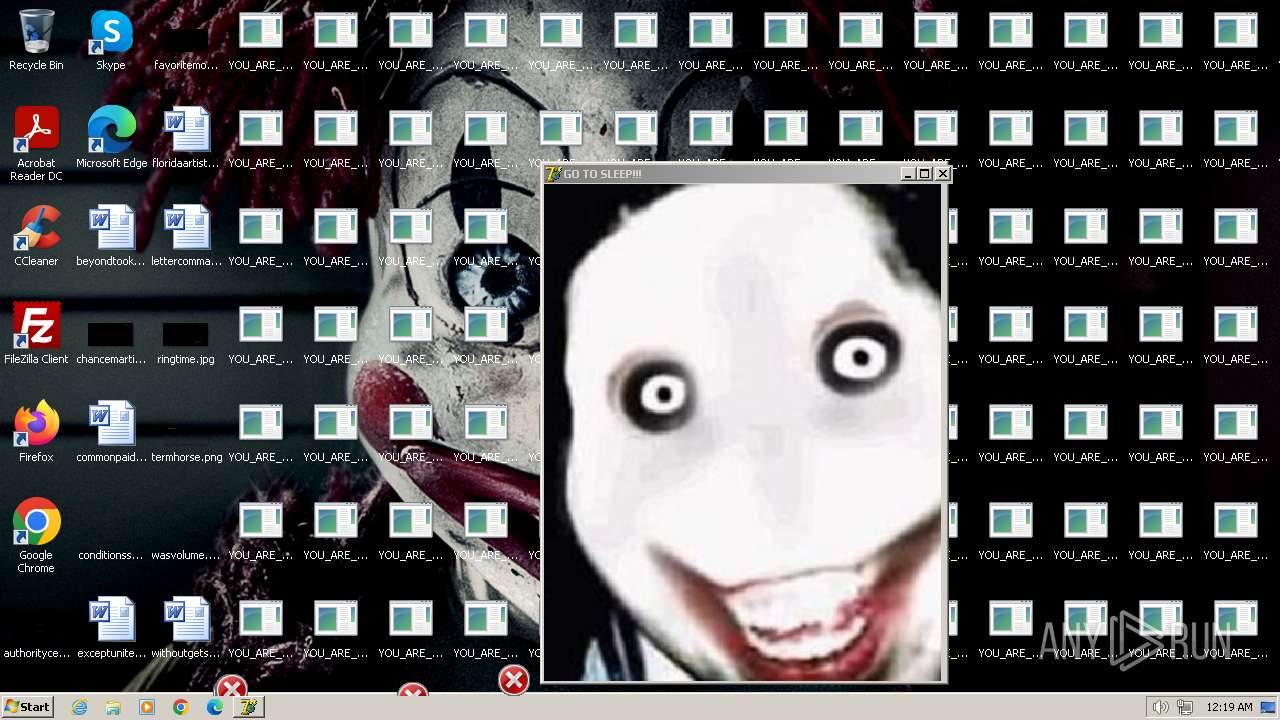
The executable file from the user directory is run by the CMD process
- scream.exe (PID: 1560)
- scream.exe (PID: 1572)
- scream.exe (PID: 3068)
- scream.exe (PID: 2000)
- scream.exe (PID: 240)
- scream.exe (PID: 3912)
- scream.exe (PID: 3308)
- scream.exe (PID: 2904)
- scream.exe (PID: 1112)
- scream.exe (PID: 2432)
- MBRKill.exe (PID: 2316)
- beeper.exe (PID: 2892)
- melter.exe (PID: 2900)
- MouseError.exe (PID: 2988)
- scream.exe (PID: 3080)
- scream.exe (PID: 3088)
- scream.exe (PID: 3072)
- scream.exe (PID: 3064)
- scream.exe (PID: 3096)
- scream.exe (PID: 3104)
- scream.exe (PID: 3112)
- doll.exe (PID: 3168)
- doll.exe (PID: 3160)
- doll.exe (PID: 3176)
- scream.exe (PID: 3120)
- scream.exe (PID: 3128)
- scream.exe (PID: 3136)
- scream.exe (PID: 3144)
- doll.exe (PID: 3152)
- PlgBlt.exe (PID: 3260)
- ScreenGlitches.exe (PID: 3312)
- MouseError.exe (PID: 3380)
- melter.exe (PID: 3428)
Uses WMIC.EXE to obtain data on processes
- cmd.exe (PID: 3848)
- cmd.exe (PID: 2232)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 2232)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3848)
- cmd.exe (PID: 2232)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1512)
- sipnotify.exe (PID: 1116)
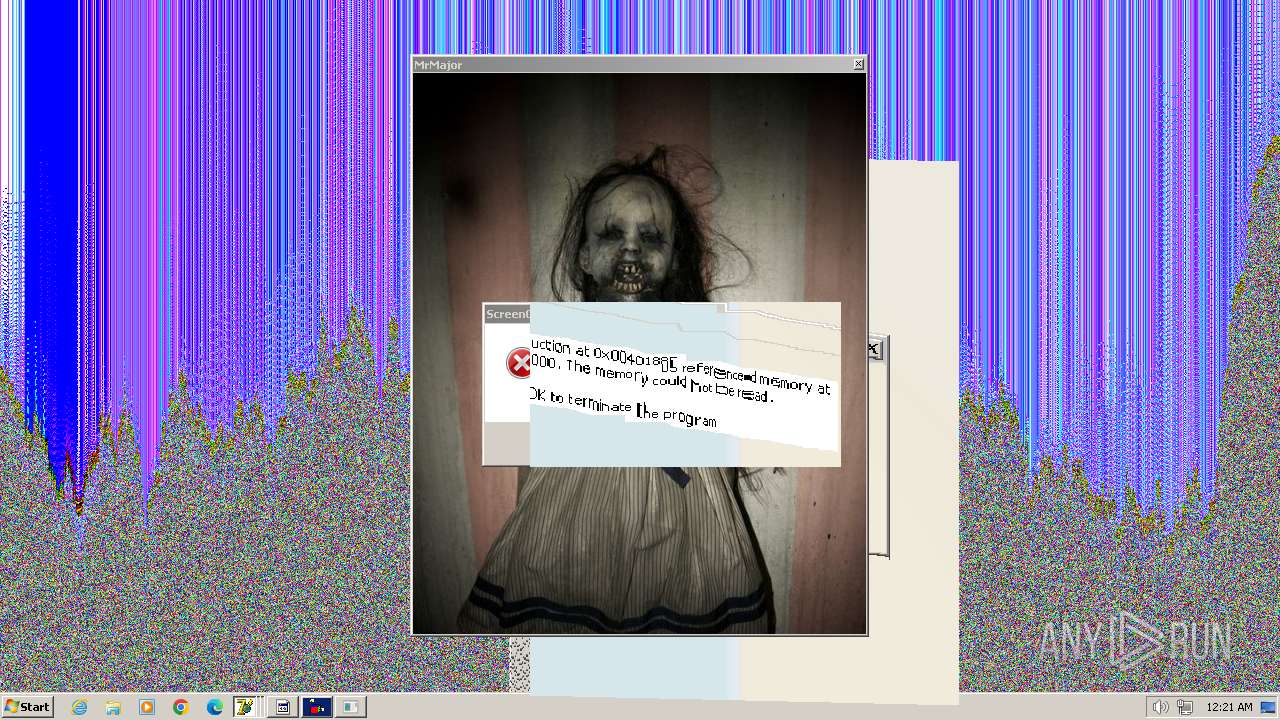
The system shut down or reboot
- cmd.exe (PID: 3848)
Reads settings of System Certificates
- sipnotify.exe (PID: 1116)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2232)
Probably fake Windows Update
- schtasks.exe (PID: 2332)
INFO
Checks supported languages
- HorrorTrojan4.exe (PID: 2848)
- scream.exe (PID: 1560)
- scream.exe (PID: 3068)
- scream.exe (PID: 2000)
- scream.exe (PID: 240)
- scream.exe (PID: 3912)
- scream.exe (PID: 3308)
- scream.exe (PID: 2904)
- scream.exe (PID: 2432)
- scream.exe (PID: 1112)
- IMEKLMG.EXE (PID: 2136)
- scream.exe (PID: 1572)
- IMEKLMG.EXE (PID: 2148)
- SystemLoaderPRO.exe (PID: 2156)
- MBRKill.exe (PID: 2316)
- wmpnscfg.exe (PID: 2748)
- wmpnscfg.exe (PID: 2772)
- melter.exe (PID: 2900)
- MouseError.exe (PID: 2988)
- beeper.exe (PID: 2892)
- scream.exe (PID: 3096)
- scream.exe (PID: 3088)
- scream.exe (PID: 3080)
- scream.exe (PID: 3072)
- scream.exe (PID: 3064)
- scream.exe (PID: 3136)
- doll.exe (PID: 3152)
- doll.exe (PID: 3160)
- doll.exe (PID: 3168)
- scream.exe (PID: 3112)
- scream.exe (PID: 3104)
- scream.exe (PID: 3120)
- scream.exe (PID: 3128)
- scream.exe (PID: 3144)
- doll.exe (PID: 3176)
- PlgBlt.exe (PID: 3260)
- ScreenGlitches.exe (PID: 3312)
- MouseError.exe (PID: 3380)
- melter.exe (PID: 3428)
Reads the computer name
- HorrorTrojan4.exe (PID: 2848)
- IMEKLMG.EXE (PID: 2136)
- IMEKLMG.EXE (PID: 2148)
- SystemLoaderPRO.exe (PID: 2156)
- wmpnscfg.exe (PID: 2748)
- wmpnscfg.exe (PID: 2772)
- beeper.exe (PID: 2892)
- doll.exe (PID: 3168)
- doll.exe (PID: 3176)
- doll.exe (PID: 3160)
- doll.exe (PID: 3152)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3932)
- sipnotify.exe (PID: 1116)
Create files in a temporary directory
- HorrorTrojan4.exe (PID: 2848)
- SystemLoaderPRO.exe (PID: 2156)
Reads the time zone
- net1.exe (PID: 1768)
Manual execution by a user
- SystemLoaderPRO.exe (PID: 2156)
- IMEKLMG.EXE (PID: 2136)
- IMEKLMG.EXE (PID: 2148)
- wmpnscfg.exe (PID: 2748)
- wmpnscfg.exe (PID: 2772)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2148)
- IMEKLMG.EXE (PID: 2136)
Reads the software policy settings
- sipnotify.exe (PID: 1116)
Reads the machine GUID from the registry
- beeper.exe (PID: 2892)
- doll.exe (PID: 3168)
- doll.exe (PID: 3152)
- doll.exe (PID: 3160)
- doll.exe (PID: 3176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:08 13:12:07+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 2727936 |
| InitializedDataSize: | 208896 |
| UninitializedDataSize: | 5091328 |
| EntryPoint: | 0x774e90 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.0.0 |
| ProductVersionNumber: | 4.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | HorrorTrojans |
| FileDescription: | Please Don't run this file |
| FileVersion: | 4,0,0,0 |
| ProductName: | HorrorTrojan 4.0 |
| InternalName: | Horror |
| ProductVersion: | 4,0,0,0 |
| LegalCopyright: | 2021 |
Total processes
175
Monitored processes
84
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\9A0.tmp\1.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 240 | scream.exe | C:\Users\admin\AppData\Local\Temp\9A0.tmp\scream.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1112 | scream.exe | C:\Users\admin\AppData\Local\Temp\9A0.tmp\scream.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 1116 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1512 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1560 | scream.exe | C:\Users\admin\AppData\Local\Temp\9A0.tmp\scream.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1572 | scream.exe | C:\Users\admin\AppData\Local\Temp\9A0.tmp\scream.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 1576 | net user admin /fullname:"YOU ARE VERY DOOMED" | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1740 | takeown /f C:\Windows\system32\taskmgr.exe | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1768 | C:\Windows\system32\net1 user admin /fullname:"YOU ARE VERY DOOMED" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
17 434
Read events
17 329
Write events
67
Delete events
38
Modification events
| (PID) Process: | (2848) HorrorTrojan4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2848) HorrorTrojan4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2848) HorrorTrojan4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2848) HorrorTrojan4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3848) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3848) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3848) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3848) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3500) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (3956) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Windows System Update Service |
Value: C:\SystemLoaderPRO.exe | |||
Executable files
11
Suspicious files
1
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2848 | HorrorTrojan4.exe | C:\Users\admin\AppData\Local\Temp\9A0.tmp\bg.bmp | — | |
MD5:— | SHA256:— | |||
| 3848 | cmd.exe | C:\bg.bmp | — | |
MD5:— | SHA256:— | |||
| 2316 | MBRKill.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 2156 | SystemLoaderPRO.exe | C:\Users\admin\AppData\Local\Temp\4769.tmp\Updates.bat | text | |
MD5:4FCE0582D51ED07E22CE4C5B688A6129 | SHA256:CB90C45D54A8D18B3FACFD87A00BDCAEC7AD3313CCB7C89E046A91DCE3FAE8EE | |||
| 3848 | cmd.exe | C:\SystemLoaderPRO.exe | executable | |
MD5:219032DD6347D5FDBB82647FDFC207A0 | SHA256:C8F4D4891618F8905BA7395640E7124575AA627A7F89ADC66F22E365A1AD48D1 | |||
| 2156 | SystemLoaderPRO.exe | C:\Users\admin\AppData\Local\Temp\4769.tmp\PlgBlt.exe | executable | |
MD5:5D8FF1DD3662AC09E5BFA682FFDB233E | SHA256:7CD320070E23E6582589D83F01F4DA86CE0D1C0FE83D8DF2007886C6EA10CC83 | |||
| 2156 | SystemLoaderPRO.exe | C:\Users\admin\AppData\Local\Temp\4769.tmp\beeper.exe | executable | |
MD5:8D1A9C2E8D53425499F3A1853D2E0910 | SHA256:1D89BD45A36DD300A250292CACF22A7BEFF3CFE0DFDDAB0D7B77C3C260032131 | |||
| 2156 | SystemLoaderPRO.exe | C:\Users\admin\AppData\Local\Temp\4769.tmp\MBRKill.exe | executable | |
MD5:D7D90EA89F241AC9DE787950F9CE3CCF | SHA256:3BB493763CA50288A4644726CCBDB338284C7B42CD16B7BC9BFB5C80063208ED | |||
| 2848 | HorrorTrojan4.exe | C:\Users\admin\AppData\Local\Temp\9A0.tmp\horror4.bat | text | |
MD5:AFDC1968CD160869457D74921ADE999E | SHA256:6DAE624DE9EAD7FCC43795096D1F5C51FF60307AE9BDD6833E7D080D896474E7 | |||
| 2156 | SystemLoaderPRO.exe | C:\Users\admin\AppData\Local\Temp\4769.tmp\doll.exe | executable | |
MD5:450F49426B4519ECAAC8CD04814C03A4 | SHA256:087FCA40E079746B9C1DFAF777D3994C0321EA8F69D08238CDFC02FB109ADD1D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
11
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1116 | sipnotify.exe | HEAD | 200 | 23.7.136.68:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133525163598120000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1124 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1452 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
1116 | sipnotify.exe | 23.7.136.68:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |