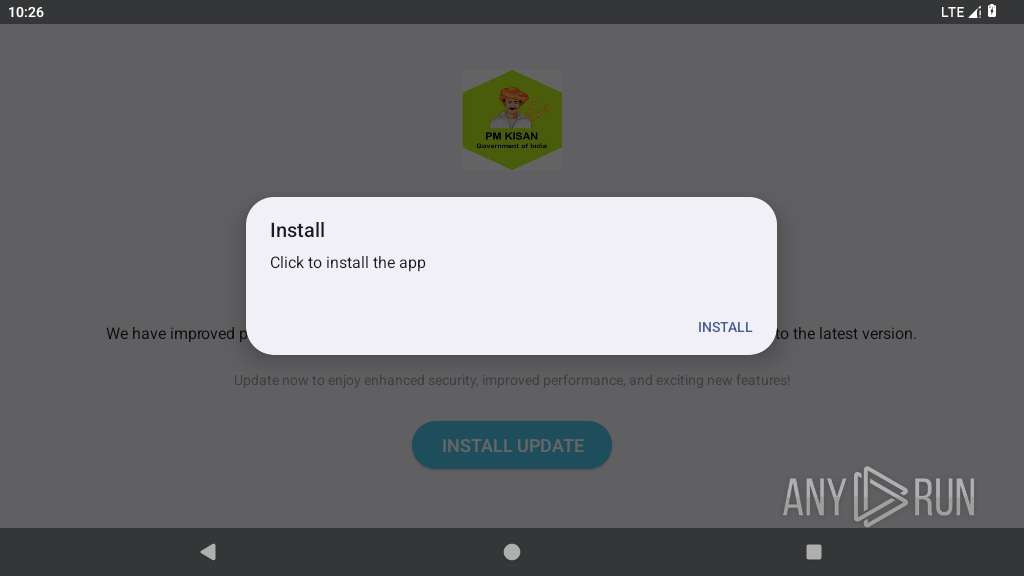
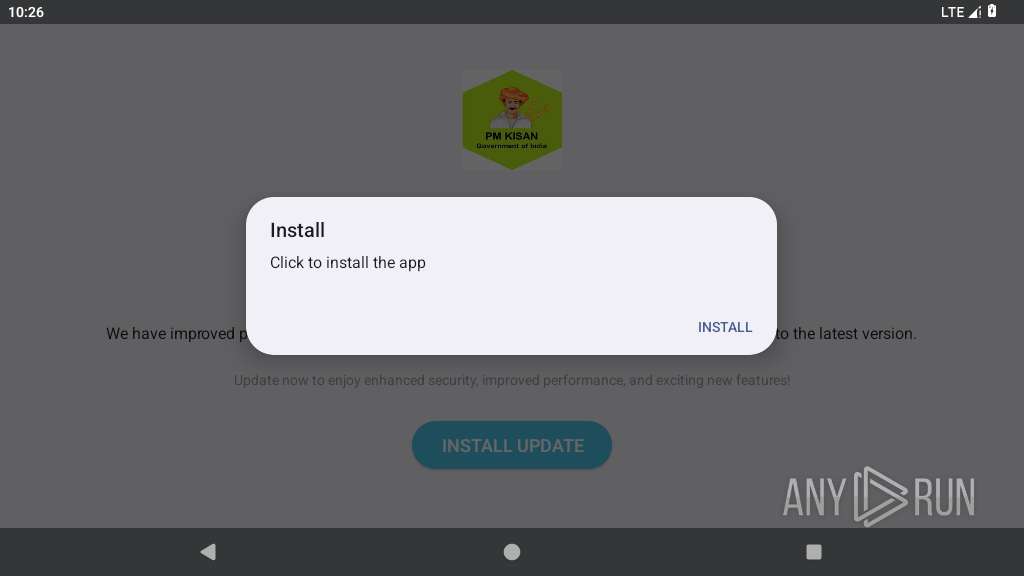
| File name: | PM Kisan 3.apk |
| Full analysis: | https://app.any.run/tasks/b63ddbe3-f9bb-4c5c-ad2f-3bb333d4c022 |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2025, 10:25:12 |
| OS: | Android 14 |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with gradle app-metadata.properties |
| MD5: | BDB615F726E8FD7E961864503182E9C2 |
| SHA1: | 1C46BDA7BD55C85F0C8D1C59C9898AFFEDF6E498 |
| SHA256: | DF2B6DB6D16658ED0AC0AFE6B443AA876414387B773FB16E3B698CC9E4CEB625 |
| SSDEEP: | 98304:C0RSofbb0asKo6ZTiARZvrnYpQ0xQ4SR3qKTwxILiEcCXLQU9c4mgK1UPLzZB5CZ:vXxrjAS3ORyq2l9ylte3A9 |
MALICIOUS
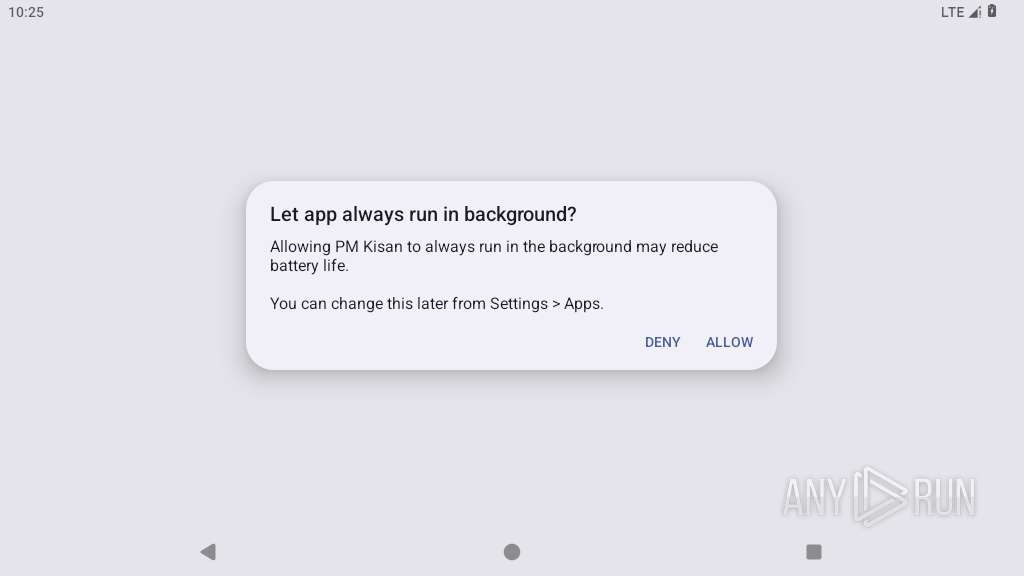
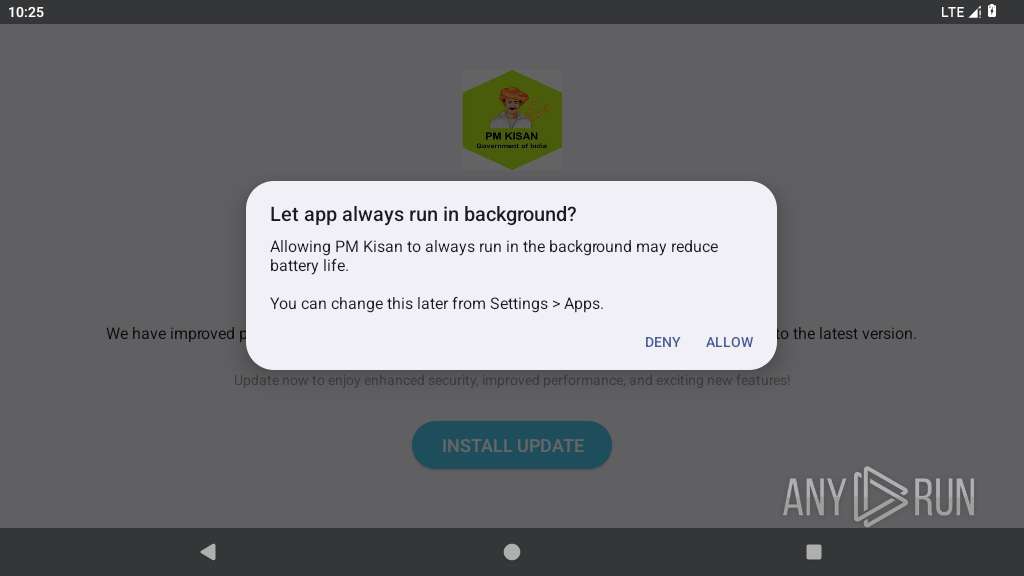
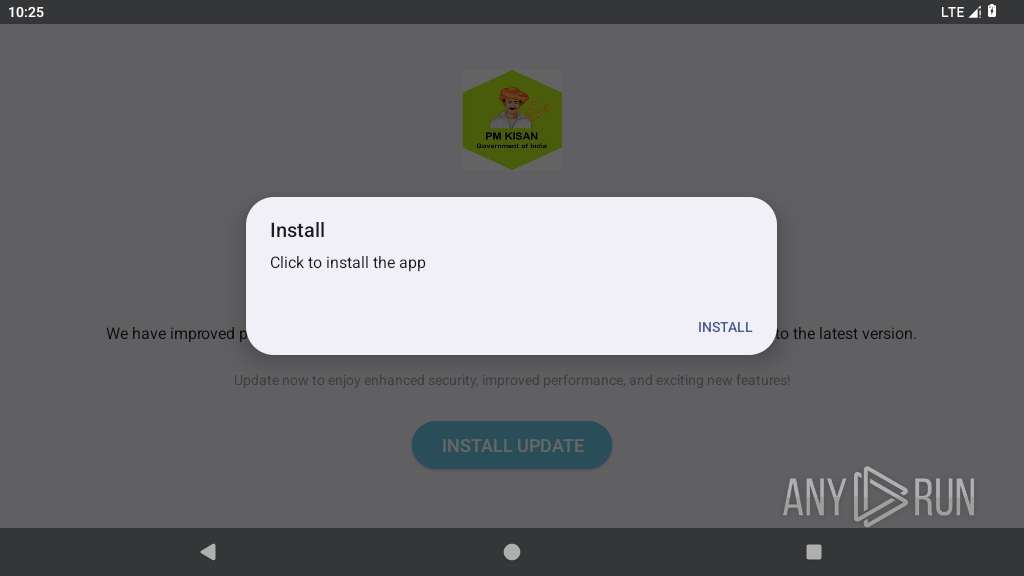
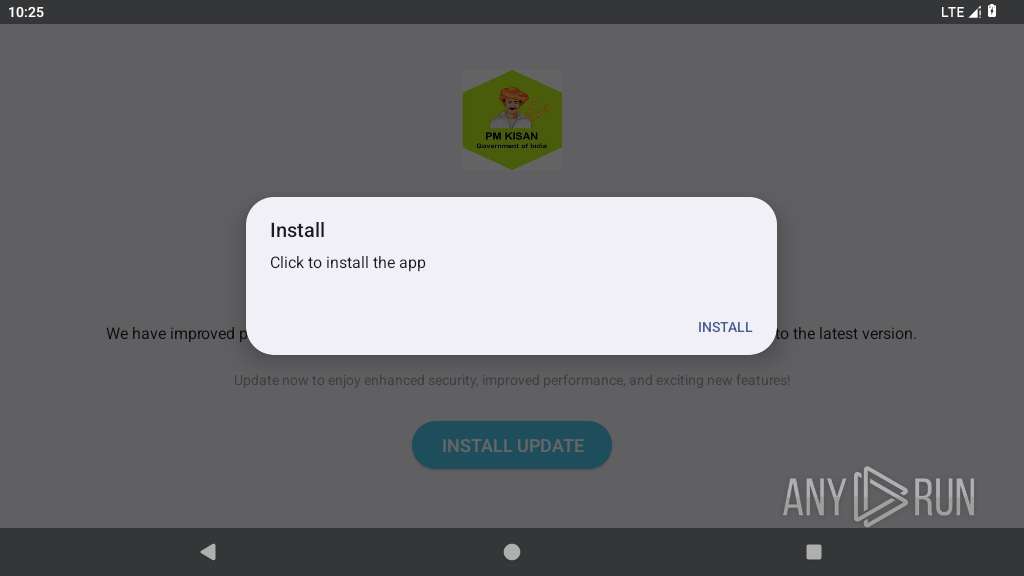
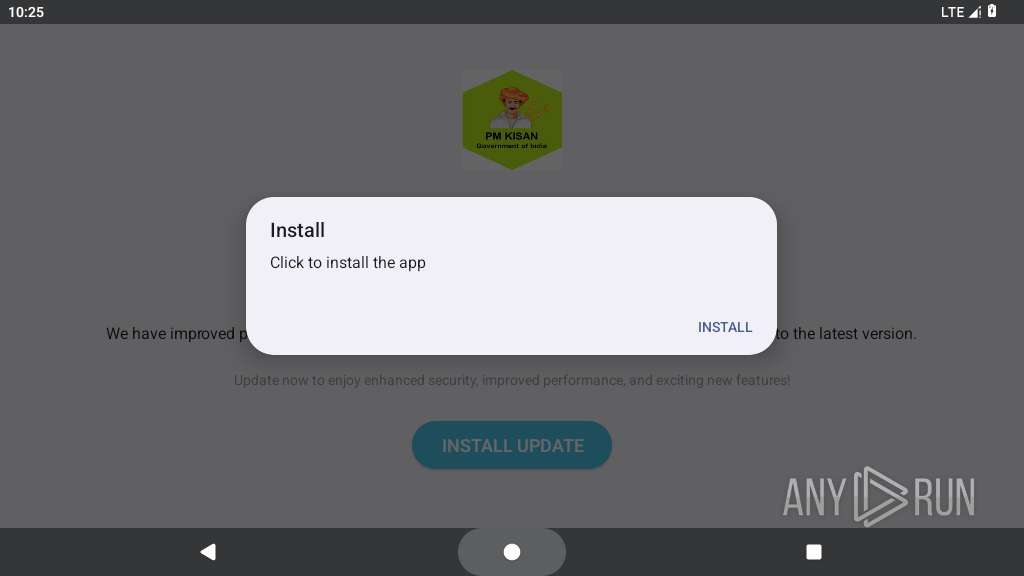
Initiates background APK installation
- app_process64 (PID: 2225)
SUSPICIOUS
Creates a WakeLock to manage power state
- app_process64 (PID: 2225)
Checks if the device's lock screen is showing
- app_process64 (PID: 2225)
Checks exemption from battery optimization
- app_process64 (PID: 2225)
Connects to unusual port
- app_process64 (PID: 2225)
Acquires a wake lock to keep the device awake
- app_process64 (PID: 2225)
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2225)
Uses encryption API functions
- app_process64 (PID: 2225)
INFO
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2225)
Detects device power status
- app_process64 (PID: 2225)
Loads a native library into the application
- app_process64 (PID: 2225)
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2225)
Dynamically loads a class in Java
- app_process64 (PID: 2225)
Dynamically registers broadcast event listeners
- app_process64 (PID: 2225)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .apk | | | Android Package (62.8) |
|---|---|---|
| .jar | | | Java Archive (17.3) |
| .vym | | | VYM Mind Map (14.9) |
| .zip | | | ZIP compressed archive (4.7) |
EXIF
ZIP
| ZipRequiredVersion: | - |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1981:01:01 01:01:02 |
| ZipCRC: | 0xaa2cdc4d |
| ZipCompressedSize: | 52 |
| ZipUncompressedSize: | 56 |
| ZipFileName: | META-INF/com/android/build/gradle/app-metadata.properties |
Total processes
130
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2225 | com.NWilfxj.FxKDr | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2274 | zygote | /system/bin/app_process32 | — | app_process32 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2291 | webview_zygote | /system/bin/app_process32 | — | app_process32 |
User: webview_zygote Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2495 | org.chromium.webview_shell | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2530 | webview_zygote | /system/bin/app_process32 | — | app_process32 |
User: webview_zygote Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
21
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2225 | app_process64 | /data/user/0/com.NWilfxj.FxKDr/shared_prefs/FirebaseHeartBeatW0RFRkFVTFRd+MTo0Njk5NjcxNzYxNjk6YW5kcm9pZDpkNjdkOGQ3NDU0ZDQ0MzlkYmM4Yjc4.xml | xml | |
MD5:— | SHA256:— | |||
| 2225 | app_process64 | /data/user/0/com.NWilfxj.FxKDr/shared_prefs/reporter.xml | xml | |
MD5:— | SHA256:— | |||
| 2225 | app_process64 | /data/user/0/com.NWilfxj.FxKDr/shared_prefs/com.google.firebase.messaging.xml | xml | |
MD5:— | SHA256:— | |||
| 2225 | app_process64 | /data/user/0/com.NWilfxj.FxKDr/shared_prefs/WebViewChromiumPrefs.xml | xml | |
MD5:— | SHA256:— | |||
| 2225 | app_process64 | /data/user/0/com.NWilfxj.FxKDr/app_webview/Default/Local Storage/leveldb/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 2225 | app_process64 | /data/user/0/com.NWilfxj.FxKDr/app_webview/Default/Local Storage/leveldb/000001.dbtmp | text | |
MD5:— | SHA256:— | |||
| 2225 | app_process64 | /data/user/0/com.NWilfxj.FxKDr/app_webview/Default/Local Storage/leveldb/CURRENT | text | |
MD5:— | SHA256:— | |||
| 2225 | app_process64 | /data/user/0/com.NWilfxj.FxKDr/cache/WebView/Default/HTTP Cache/Code Cache/webui_js/index | binary | |
MD5:— | SHA256:— | |||
| 2225 | app_process64 | /data/user/0/com.NWilfxj.FxKDr/cache/WebView/Default/HTTP Cache/Code Cache/js/index | binary | |
MD5:— | SHA256:— | |||
| 2225 | app_process64 | /data/user/0/com.NWilfxj.FxKDr/cache/WebView/Default/HTTP Cache/Code Cache/wasm/index | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
31
DNS requests
8
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 404 | 172.217.18.4:80 | http://www.google.com/gen_204 | unknown | — | — | whitelisted |
834 | app_process64 | GET | 404 | 172.217.18.4:80 | http://www.google.com/gen_204 | unknown | — | — | whitelisted |
834 | app_process64 | GET | 404 | 142.250.186.67:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
834 | app_process64 | GET | 404 | 142.250.186.67:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
834 | app_process64 | GET | 404 | 142.250.186.67:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
834 | app_process64 | GET | 404 | 142.250.186.67:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
834 | app_process64 | GET | 404 | 216.239.32.223:80 | http://play.googleapis.com/generate_204 | unknown | — | — | whitelisted |
834 | app_process64 | GET | 404 | 172.217.18.4:80 | http://www.google.com/gen_204 | unknown | — | — | whitelisted |
834 | app_process64 | GET | 404 | 172.217.18.4:80 | http://www.google.com/gen_204 | unknown | — | — | whitelisted |
834 | app_process64 | GET | 404 | 142.250.186.67:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
443 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 142.250.186.67:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 172.217.18.4:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 172.217.18.4:80 | www.google.com | GOOGLE | US | whitelisted |
2225 | app_process64 | 94.136.186.134:443 | aptabase.uasecurity.org | Clusters GmbH | DE | unknown |
834 | app_process64 | 142.250.186.67:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
834 | app_process64 | 172.217.18.4:443 | www.google.com | GOOGLE | US | whitelisted |
834 | app_process64 | 172.217.18.4:80 | www.google.com | GOOGLE | US | whitelisted |
2225 | app_process64 | 185.200.64.67:8088 | api.uasecurity.org | XTOM | DE | unknown |
568 | app_process64 | 216.239.35.4:123 | time.android.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivitycheck.gstatic.com |
| whitelisted |
www.google.com |
| whitelisted |
google.com |
| whitelisted |
aptabase.uasecurity.org |
| unknown |
api.uasecurity.org |
| unknown |
time.android.com |
| whitelisted |
play.googleapis.com |
| whitelisted |
timeserver.uasecurity.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
834 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |
834 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |
834 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |
834 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |
834 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |