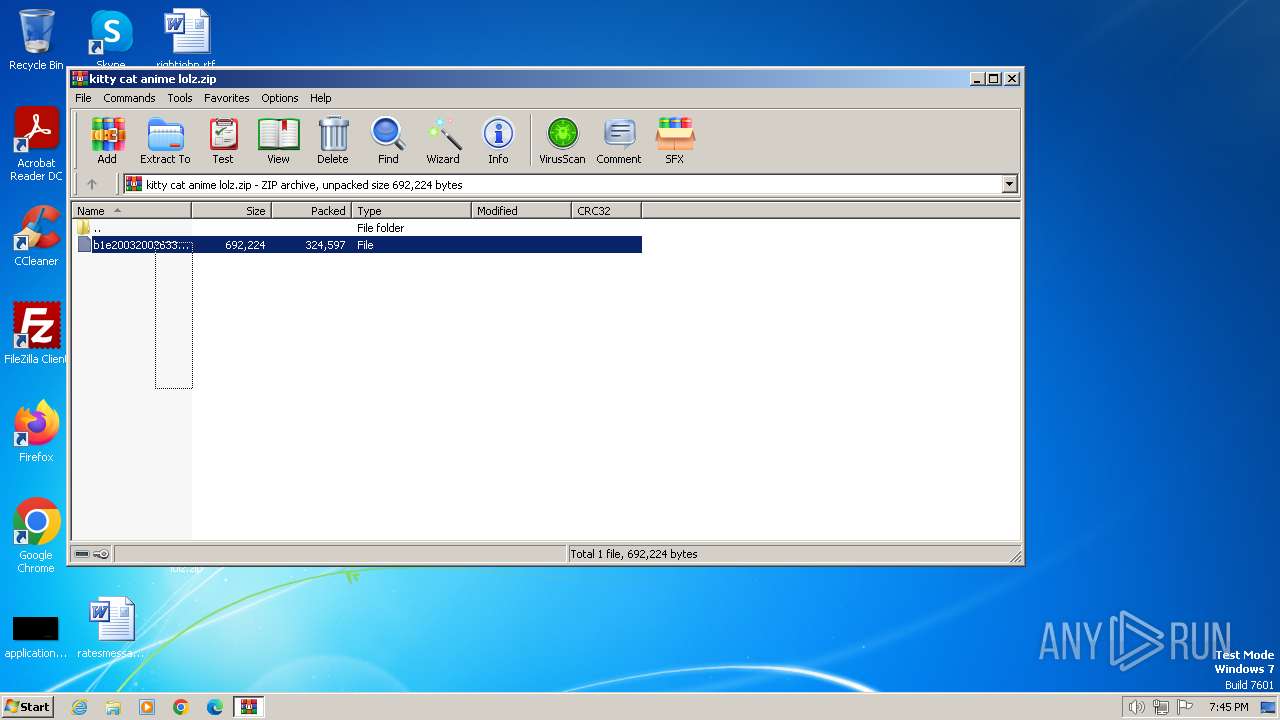
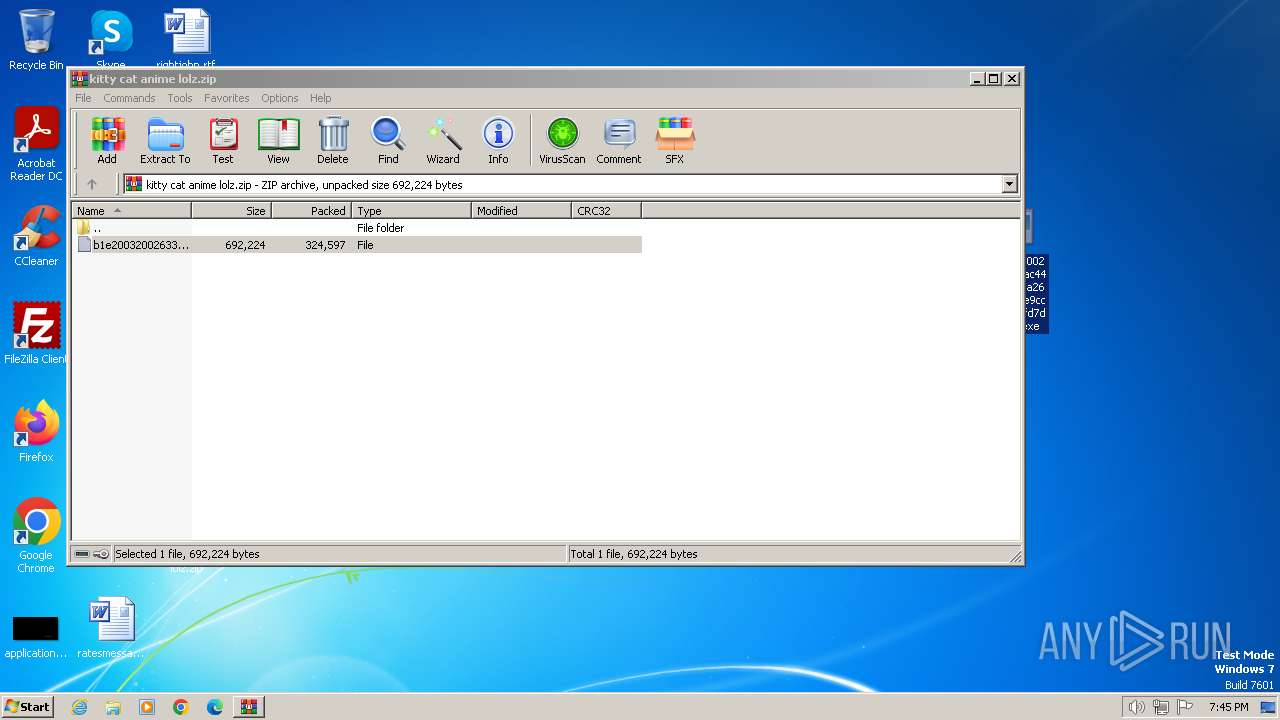
| File name: | kitty cat anime lolz.zip |
| Full analysis: | https://app.any.run/tasks/c618bf6d-fcc5-4028-b503-5bcea1f20ff7 |
| Verdict: | Malicious activity |
| Analysis date: | February 09, 2024, 19:45:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
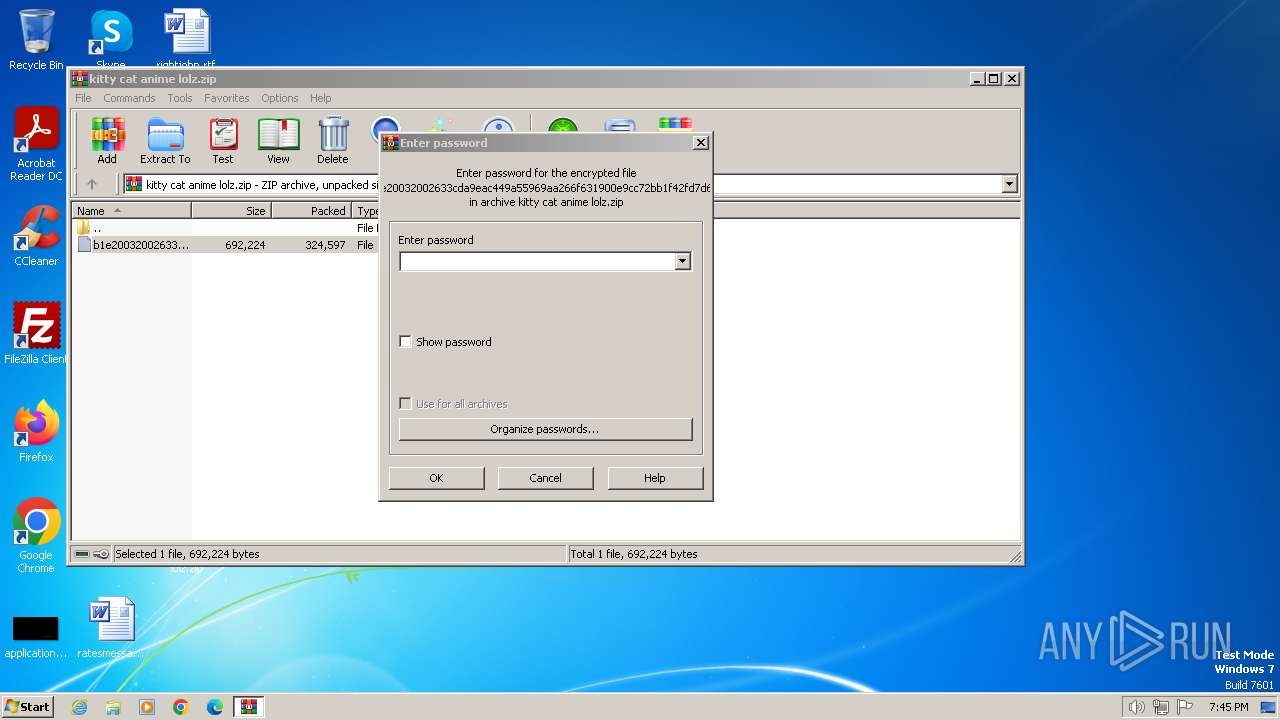
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | 9A97724FA8F13406830EA69C43FC3701 |
| SHA1: | 39E63259A2F79C3D4C0F3DE906E30BDD9CF2F4AE |
| SHA256: | DF1FCE903FB6E08ED70D2A30C850CB3B0A82342D3F743E07871011BF05F69327 |
| SSDEEP: | 12288:2w5+Y6sBcvbdie+dT+PCZ3cipibduI22hnv1cp7j:2w5+3sBObdie+NfsipibF22tv1oj |
MALICIOUS
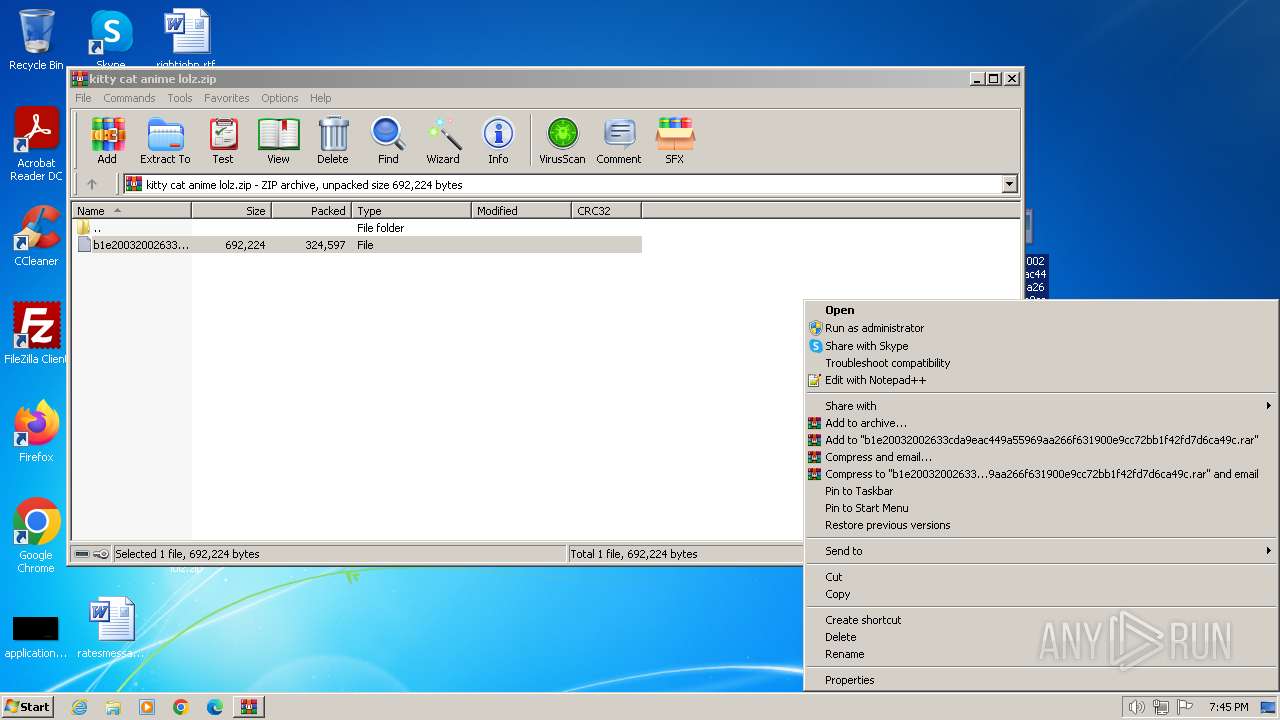
Drops the executable file immediately after the start
- b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe (PID: 2340)
- WinRAR.exe (PID: 3668)
- MSSQLH.exe (PID: 3992)
Disables Windows Defender
- MSSQLH.exe (PID: 3992)
- MSSQLH.exe (PID: 764)
SUSPICIOUS
Process drops legitimate windows executable
- MSSQLH.exe (PID: 3992)
Executable content was dropped or overwritten
- MSSQLH.exe (PID: 3992)
- b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe (PID: 2340)
Suspicious use of NETSH.EXE
- MSSQLH.exe (PID: 3992)
- MSSQLH.exe (PID: 764)
Creates or modifies Windows services
- MSSQLH.exe (PID: 3992)
- netsh.exe (PID: 3028)
- netsh.exe (PID: 2512)
INFO
Reads the computer name
- b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe (PID: 2340)
- MSSQLH.exe (PID: 3992)
- b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe (PID: 2172)
- MSSQLH.exe (PID: 764)
Checks supported languages
- b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe (PID: 2340)
- MSSQLH.exe (PID: 3992)
- b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe (PID: 2172)
- MSSQLH.exe (PID: 764)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3668)
Reads the machine GUID from the registry
- MSSQLH.exe (PID: 3992)
- b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe (PID: 2172)
- b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe (PID: 2340)
- MSSQLH.exe (PID: 764)
Manual execution by a user
- b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe (PID: 2340)
- b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe (PID: 2172)
- MSSQLH.exe (PID: 764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 324597 |
| ZipUncompressedSize: | 692224 |
| ZipFileName: | b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c |
Total processes
94
Monitored processes
27
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | netsh ipsec static add rule name=Rule1 policy=Block filterlist=Filter1 filteraction=FilteraAtion1 | C:\Windows\System32\netsh.exe | — | MSSQLH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | netsh ipsec static add filteraction name=FilteraAtion1 action=block | C:\Windows\System32\netsh.exe | — | MSSQLH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | "C:\Users\admin\Desktop\MSSQLH.exe" | C:\Users\admin\Desktop\MSSQLH.exe | explorer.exe | ||||||||||||
User: admin Company: MSSQL SERVER Integrity Level: HIGH Description: MSSQL SERVER Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 896 | netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=445 protocol=TCP | C:\Windows\System32\netsh.exe | — | MSSQLH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | netsh ipsec static add policy name=Block | C:\Windows\System32\netsh.exe | — | MSSQLH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1368 | netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=445 protocol=UDP | C:\Windows\System32\netsh.exe | — | MSSQLH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=139 protocol=UDP | C:\Windows\System32\netsh.exe | — | MSSQLH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1592 | netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=135 protocol=TCP | C:\Windows\System32\netsh.exe | — | MSSQLH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2152 | netsh ipsec static add filter filterlist=Filter1 srcaddr=any dstaddr=Me dstport=139 protocol=TCP | C:\Windows\System32\netsh.exe | — | MSSQLH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2172 | "C:\Users\admin\Desktop\b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe" | C:\Users\admin\Desktop\b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Windows Integrity Level: MEDIUM Description: Microsoft Windows Run DLL Exit code: 0 Version: 5.2.0.0 Modules
| |||||||||||||||
Total events
17 859
Read events
16 592
Write events
1 241
Delete events
26
Modification events
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\kitty cat anime lolz.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3992 | MSSQLH.exe | C:\Windows\Logs\RunDllExe.dll | executable | |
MD5:87D72272BF8B8F8AFF015802FD3C50D8 | SHA256:7DB290A3C9C0429A1D011C355762633543C1D72E2315A0EECBAF15B946948B1A | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.40643\b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c | executable | |
MD5:5F2FFB3D7233963482EFFFB2BEE94E7B | SHA256:B1E20032002633CDA9EAC449A55969AA266F631900E9CC72BB1F42FD7D6CA49C | |||
| 2340 | b1e20032002633cda9eac449a55969aa266f631900e9cc72bb1f42fd7d6ca49c.exe | C:\Users\admin\Desktop\MSSQLH.exe | executable | |
MD5:F85DA77FCEEEB1E2A6C9BE050CCFF9F5 | SHA256:FFFB018CD8E3C48FE0E343C5763DAD32A5ADA28129BA14DB3F656361D5E44C20 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2120 | svchost.exe | 211.57.200.17:53 | wmi.362-com.com | Korea Telecom | KR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wmi.362-com.com |
| unknown |