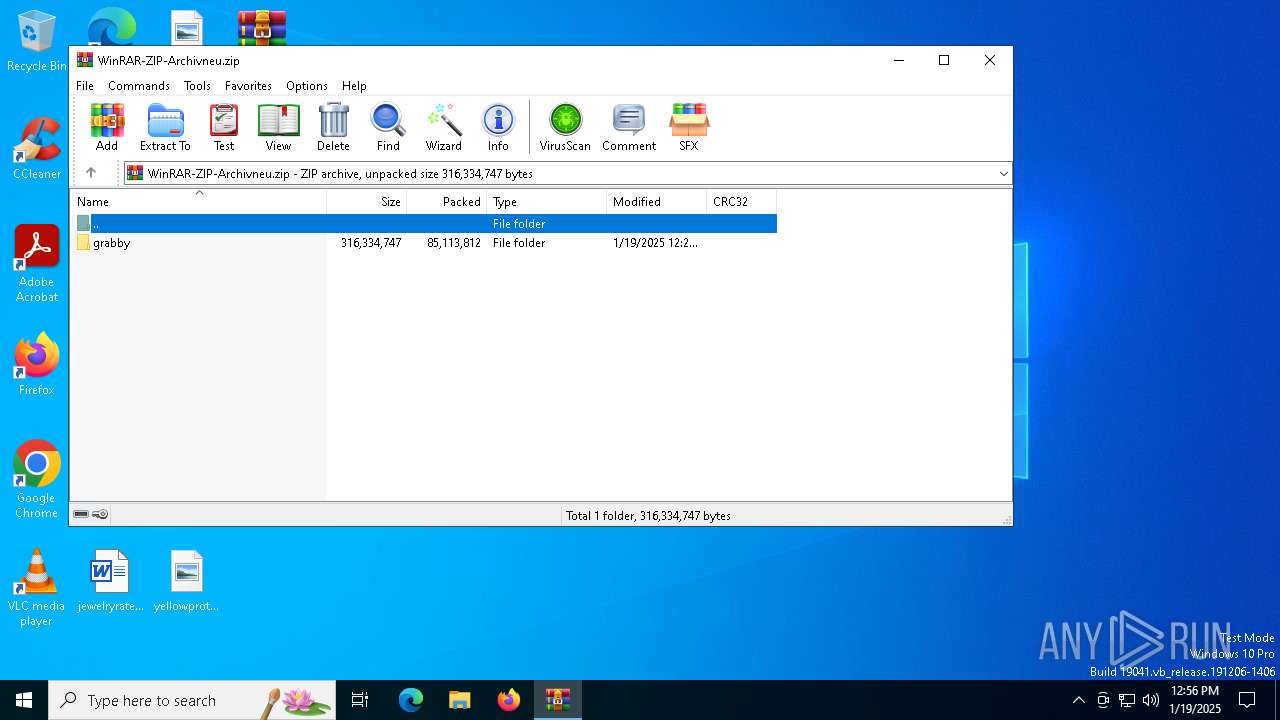
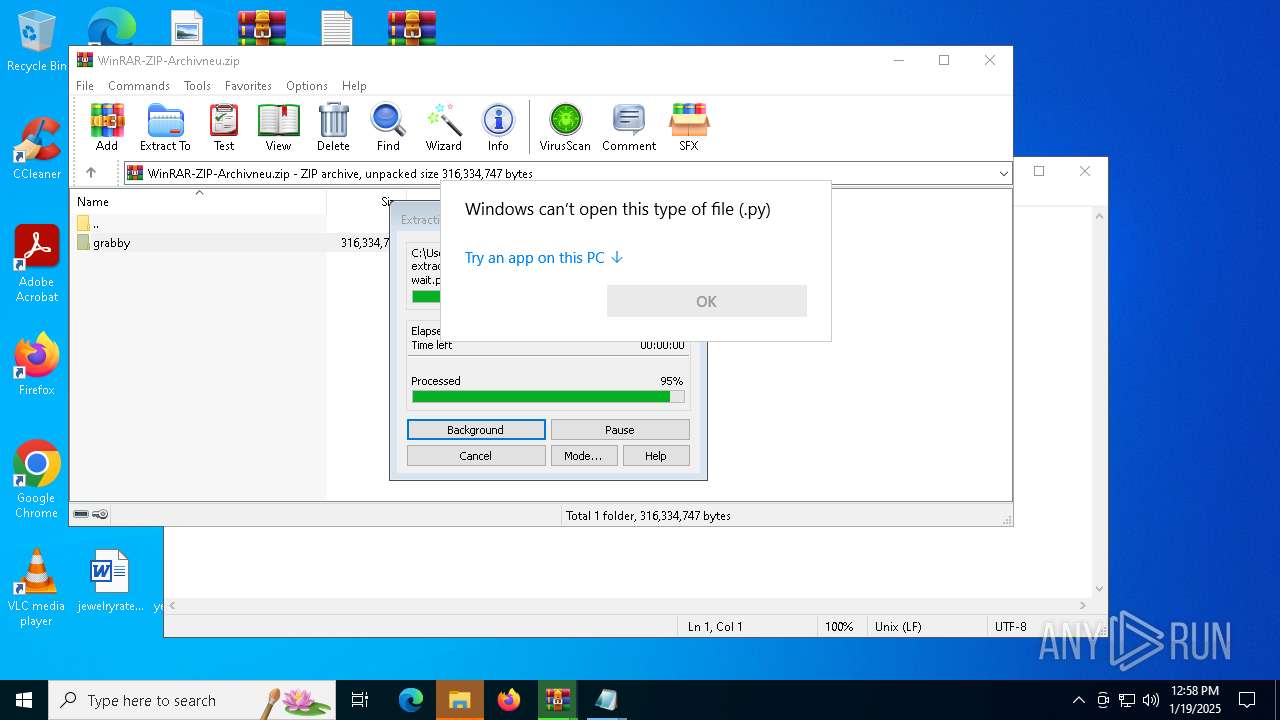
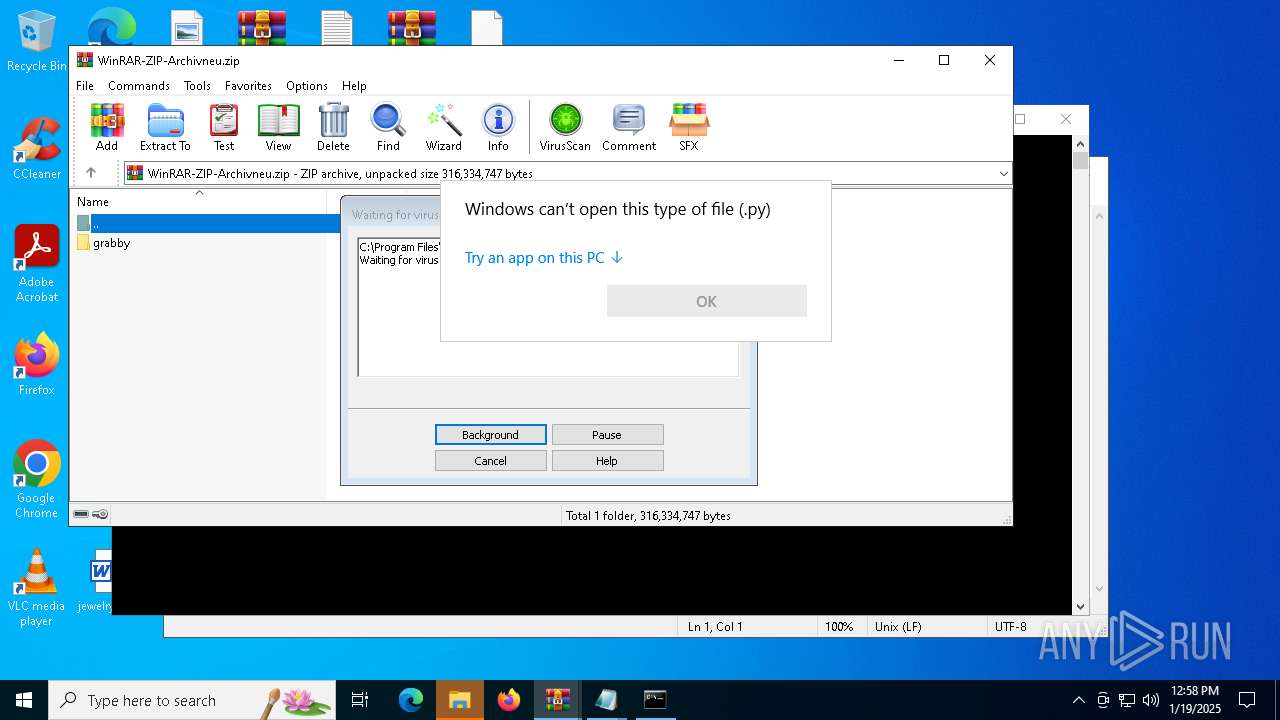
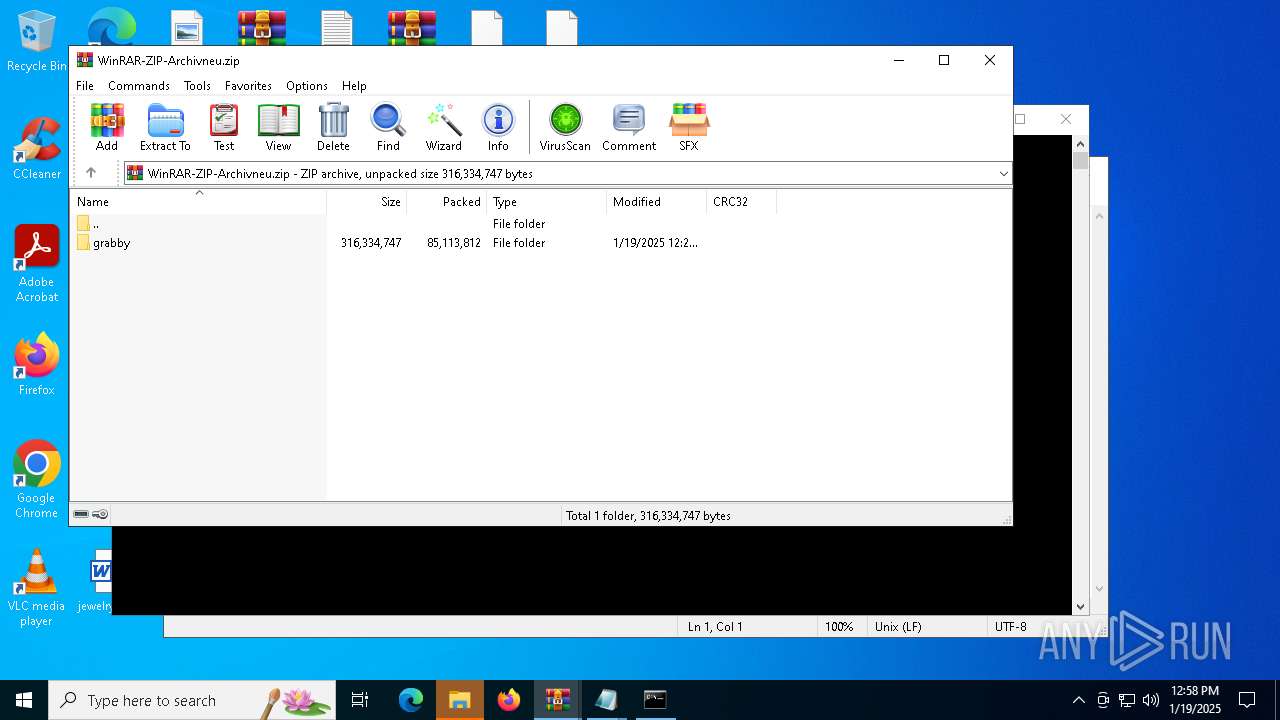
| File name: | WinRAR-ZIP-Archivneu.zip |
| Full analysis: | https://app.any.run/tasks/6aeb7e7d-7914-40a4-a697-258cd903f861 |
| Verdict: | Malicious activity |
| Analysis date: | January 19, 2025, 12:55:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 24C918143D3811191E6B7BC5B9C9CC86 |
| SHA1: | EB1C5CB3F1BD71E3CEE82977621C51C4D5AF1A1F |
| SHA256: | DF1F0189C7A046672553640B179F4E001B0632FD275A83E63A54DC9CCA9206B2 |
| SSDEEP: | 786432:3N0xTgpz5wuoKD6EhE5XnbJwtyzE3ZGe5P/4Yz9Kzp:90Kz5wuo2hE5XnbJwtyzEJG+P/Je |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6728)
- powershell.exe (PID: 6860)
- powershell.exe (PID: 7080)
- powershell.exe (PID: 3840)
SUSPICIOUS
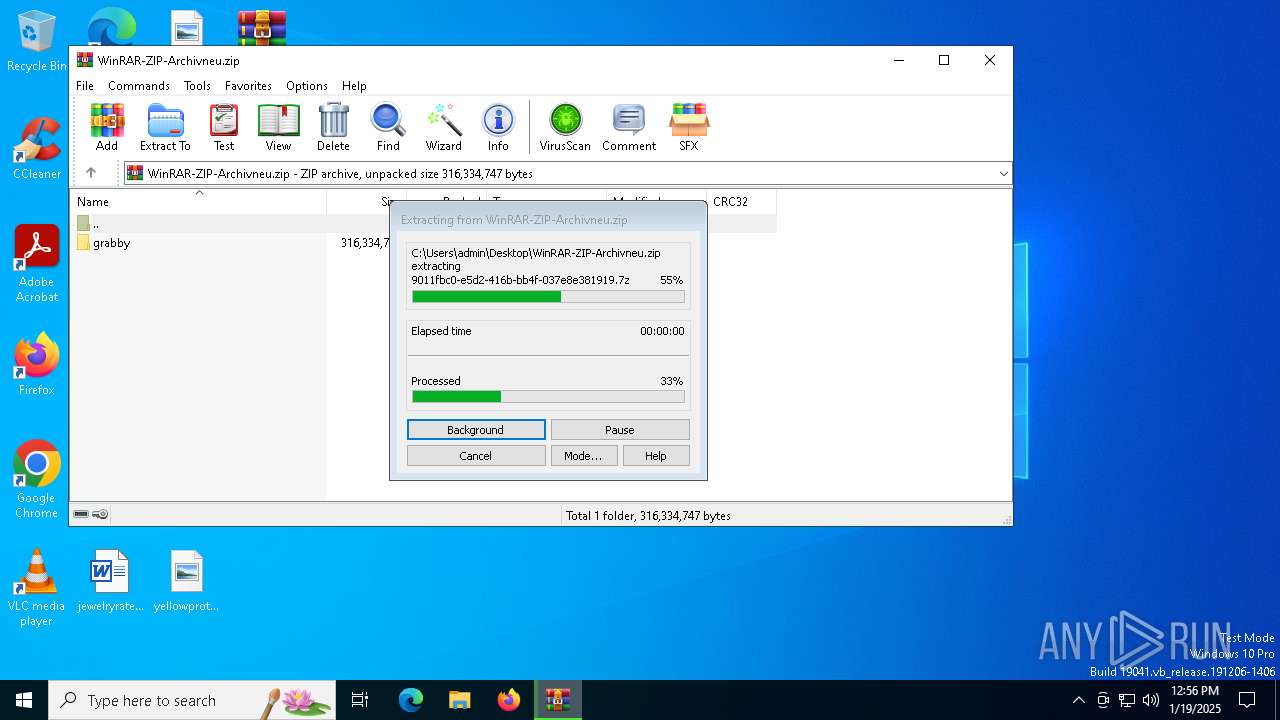
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 6436)
Process drops python dynamic module
- WinRAR.exe (PID: 6436)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6436)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6436)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6436)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6436)
The sample compiled with english language support
- WinRAR.exe (PID: 6436)
The process uses the downloaded file
- WinRAR.exe (PID: 6436)
Manual execution by a user
- powershell.exe (PID: 6728)
- powershell.exe (PID: 7080)
- powershell.exe (PID: 6860)
- powershell.exe (PID: 3840)
- notepad.exe (PID: 3544)
- notepad.exe (PID: 4264)
- notepad.exe (PID: 6012)
- notepad.exe (PID: 4400)
- notepad.exe (PID: 5404)
- WinRAR.exe (PID: 4932)
- WinRAR.exe (PID: 4624)
- notepad.exe (PID: 5920)
- notepad.exe (PID: 4132)
- notepad.exe (PID: 1296)
- OpenWith.exe (PID: 5316)
- OpenWith.exe (PID: 6332)
- notepad.exe (PID: 1804)
- OpenWith.exe (PID: 1140)
- OpenWith.exe (PID: 2424)
- OpenWith.exe (PID: 6244)
- OpenWith.exe (PID: 1468)
- OpenWith.exe (PID: 2428)
- OpenWith.exe (PID: 5268)
- OpenWith.exe (PID: 4360)
- OpenWith.exe (PID: 4612)
Reads security settings of Internet Explorer
- notepad.exe (PID: 3544)
- notepad.exe (PID: 4264)
- notepad.exe (PID: 6012)
- notepad.exe (PID: 4400)
- notepad.exe (PID: 1804)
- notepad.exe (PID: 5404)
- notepad.exe (PID: 4132)
- notepad.exe (PID: 5920)
- notepad.exe (PID: 1296)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5316)
- OpenWith.exe (PID: 5268)
- OpenWith.exe (PID: 2424)
- OpenWith.exe (PID: 6244)
- OpenWith.exe (PID: 6332)
- OpenWith.exe (PID: 2428)
- OpenWith.exe (PID: 1140)
- OpenWith.exe (PID: 1468)
- OpenWith.exe (PID: 4612)
- OpenWith.exe (PID: 4360)
Reads the computer name
- MpCmdRun.exe (PID: 5392)
Create files in a temporary directory
- MpCmdRun.exe (PID: 5392)
Checks supported languages
- MpCmdRun.exe (PID: 5392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:19 13:20:42 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | grabby/ |
Total processes
141
Monitored processes
33
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
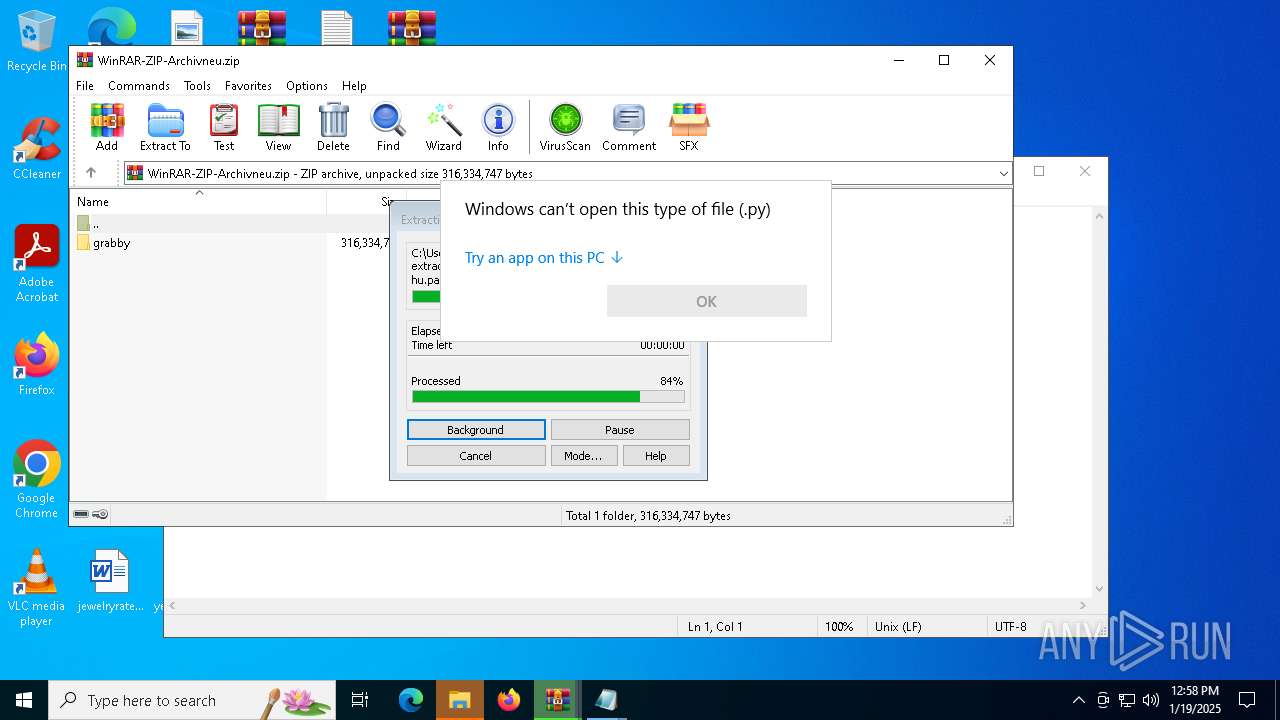
| 1140 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\core.py | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\top_level.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1468 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\cd.py | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\top_level.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6436.32032\Rar$Scan125384.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2424 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\c_lexer.py | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2428 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\blockfeeder.py | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
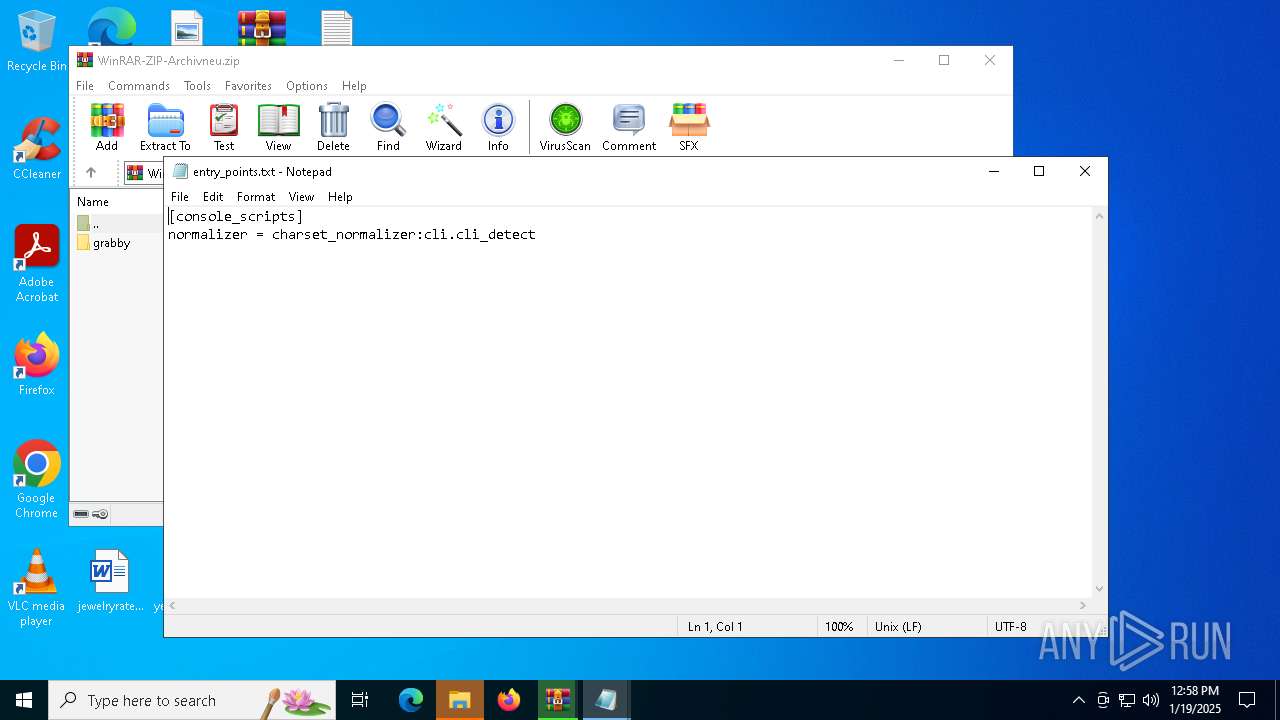
| 3544 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\entry_points.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3840 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\__PSScriptPolicyTest_qujbespe.tiy.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4132 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\LICENSE.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 425
Read events
27 398
Write events
27
Delete events
0
Modification events
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\WinRAR-ZIP-Archivneu.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
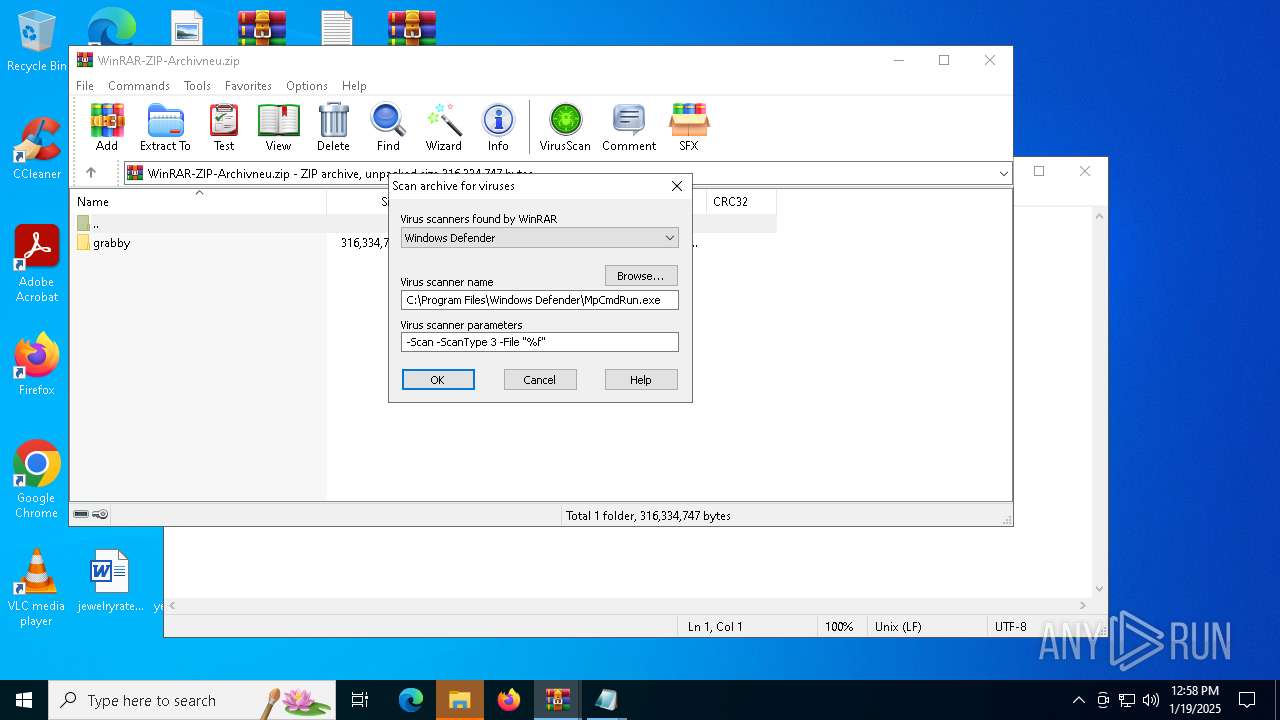
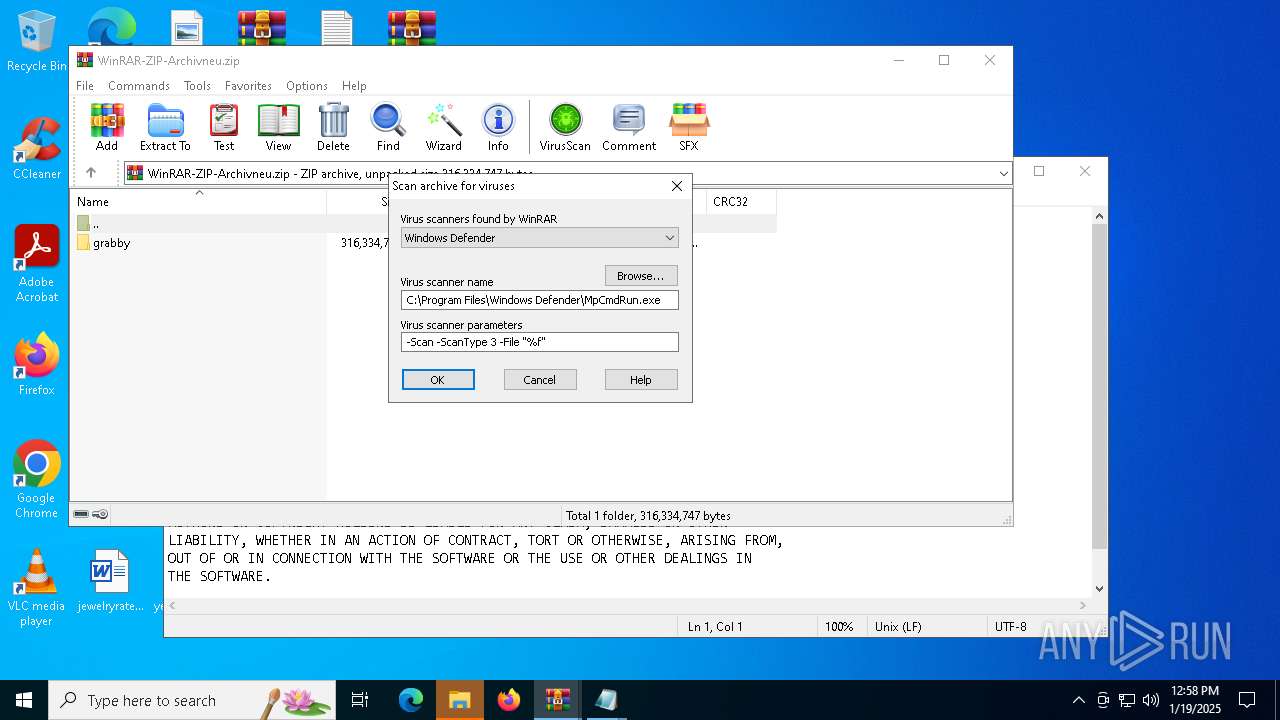
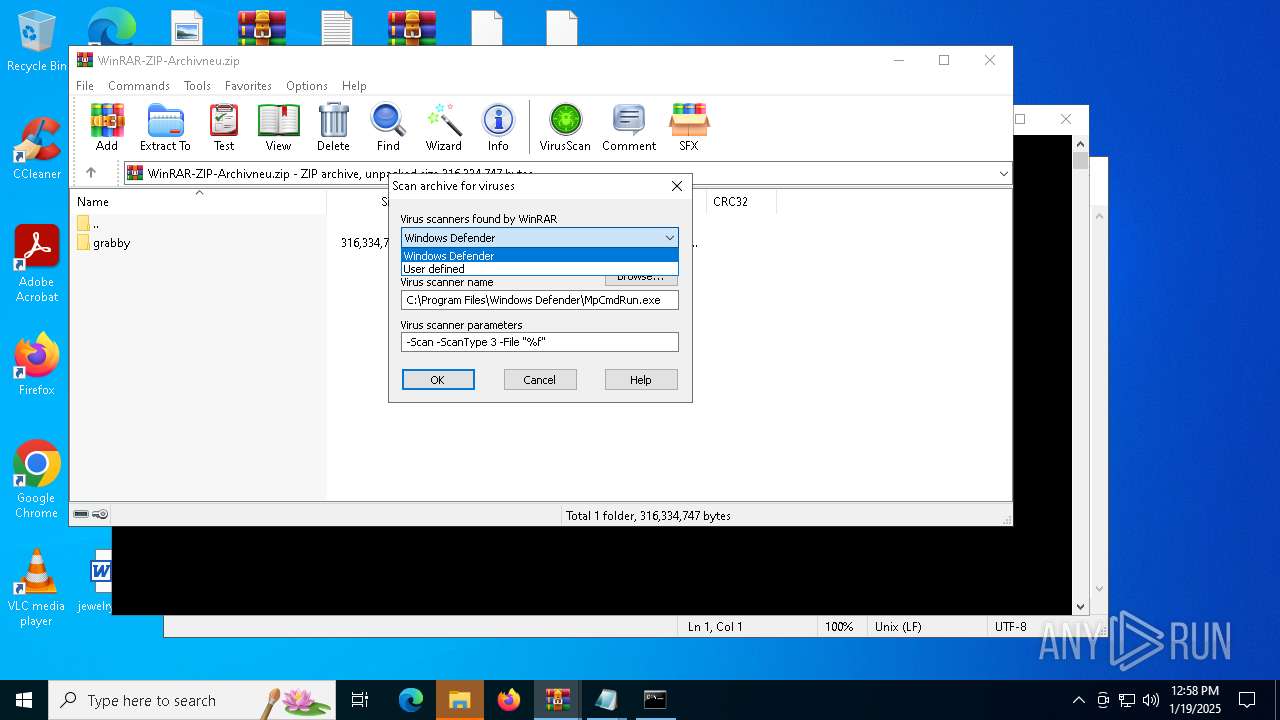
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
| (PID) Process: | (4932) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
25
Suspicious files
191
Text files
293
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
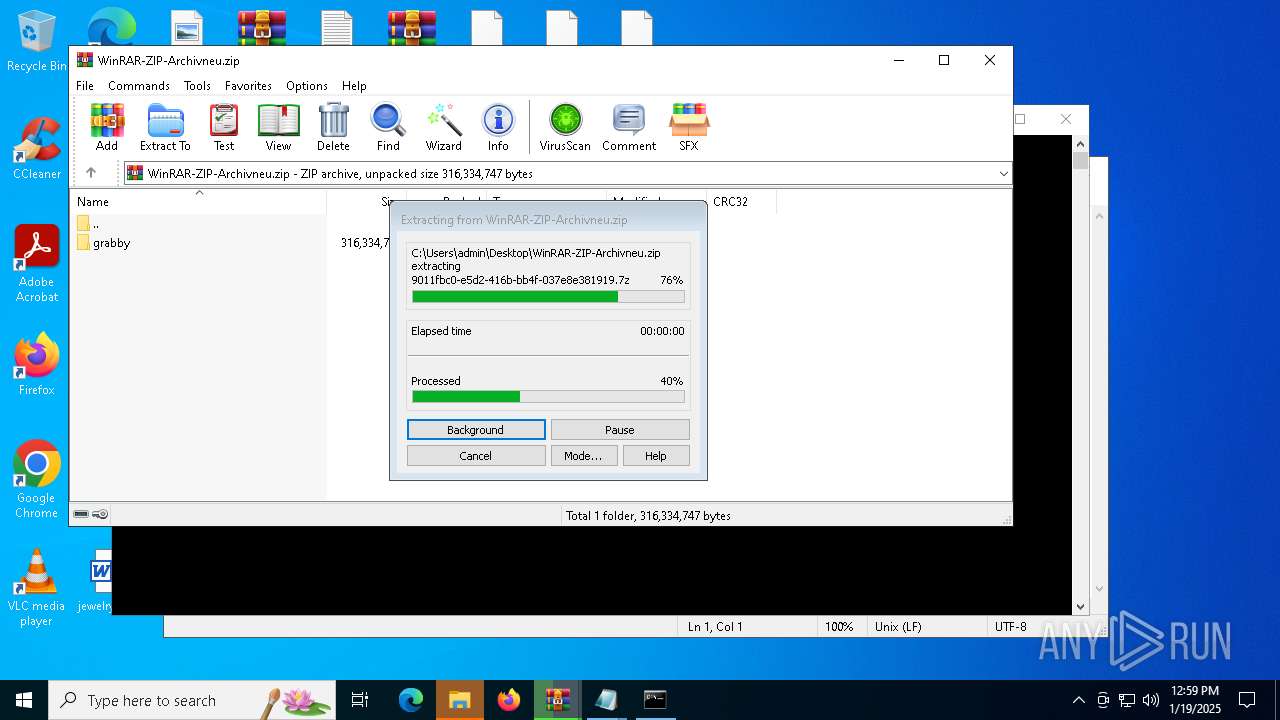
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6436.21645\WinRAR-ZIP-Archivneu.zip\grabby\9011fbc0-e5d2-416b-bb4f-037e8e381919.7z | — | |
MD5:— | SHA256:— | |||
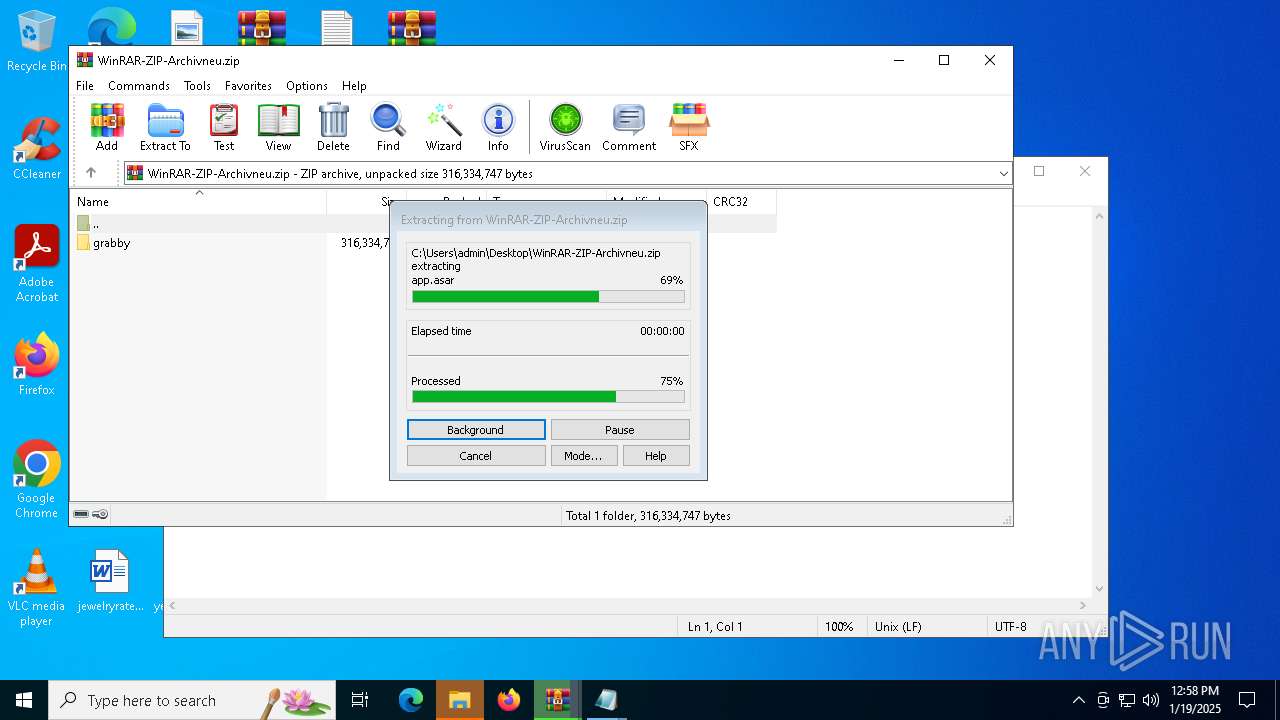
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6436.21645\WinRAR-ZIP-Archivneu.zip\grabby\app.asar | — | |
MD5:— | SHA256:— | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6436.21645\WinRAR-ZIP-Archivneu.zip\grabby\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:5C880ECECE7595AEA41224EDBF5F8BBA | SHA256:31736FECAF227FC906A4146252D5B452D9118E68C3A12C72095969F42724C621 | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6436.21645\WinRAR-ZIP-Archivneu.zip\grabby\api.py | text | |
MD5:AD3E6E647B23B98387FFE0738D965615 | SHA256:FD96FD39AEEDCD5222CD32B016B3E30C463D7A3B66FCE9D2444467003C46B10B | |||
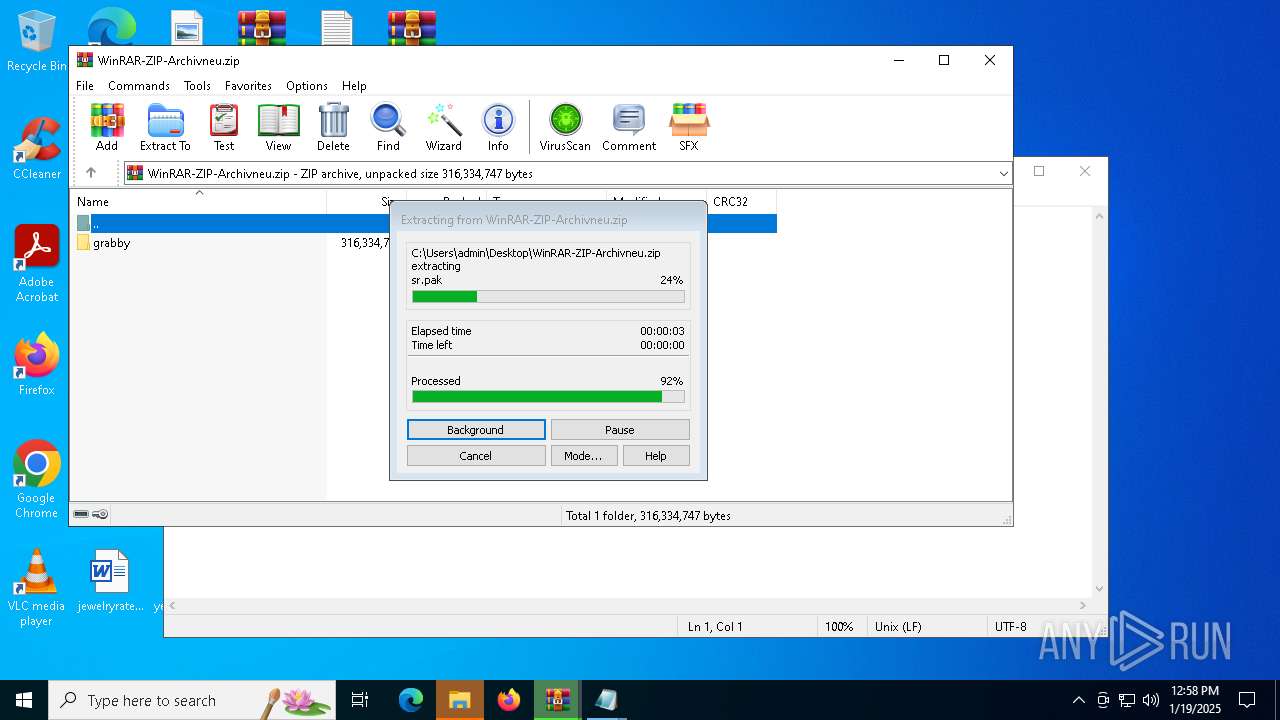
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6436.21645\WinRAR-ZIP-Archivneu.zip\grabby\ar.pak | binary | |
MD5:47A6D10B4112509852D4794229C0A03B | SHA256:857FE3AB766B60A8D82B7B6043137E3A7D9F5CFB8DDD942316452838C67D0495 | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6436.21645\WinRAR-ZIP-Archivneu.zip\grabby\adapters.py | text | |
MD5:55B2F3BB90204EAEA336530AA917B89E | SHA256:28871E72C72A6A6EAB78E097465E03C0FE235FC25C97CB1DE7B7EDD7B291D9C4 | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6436.21645\WinRAR-ZIP-Archivneu.zip\grabby\66b4b51d797e74d7fb7497adc8ddba9194cf006882553f055e16035d | text | |
MD5:678A123DFE98ECDFD3E1007279FFC8EE | SHA256:F2A4744F3E49042EB9FA5846FF90C6E1D708888459717D64EA8D51A7DAEB8AF2 | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6436.21645\WinRAR-ZIP-Archivneu.zip\grabby\Cargo.toml | text | |
MD5:0F101A11E4C8D7D40521FDFC6686AF4A | SHA256:BC409BC4F88DBBE750856E1B693B923F382A6819C18306589C909268941B2140 | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6436.21645\WinRAR-ZIP-Archivneu.zip\grabby\blockfeeder.py | text | |
MD5:F527C7E232EFE70605EACFCF187A1ABE | SHA256:34C550F66D284B4C2866F17130D646BF6C3FC2BF2806203268865782E12E0E44 | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6436.21645\WinRAR-ZIP-Archivneu.zip\grabby\ca.pak | binary | |
MD5:D259469E94F2ADF54380195555154518 | SHA256:F98B7442BEFC285398A5DD6A96740CBA31D2F5AADADD4D5551A05712D693029B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
25
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 2.16.110.121:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.23.227.215:443 | — | Ooredoo Q.S.C. | QA | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2192 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2192 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
5064 | SearchApp.exe | 2.16.110.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |