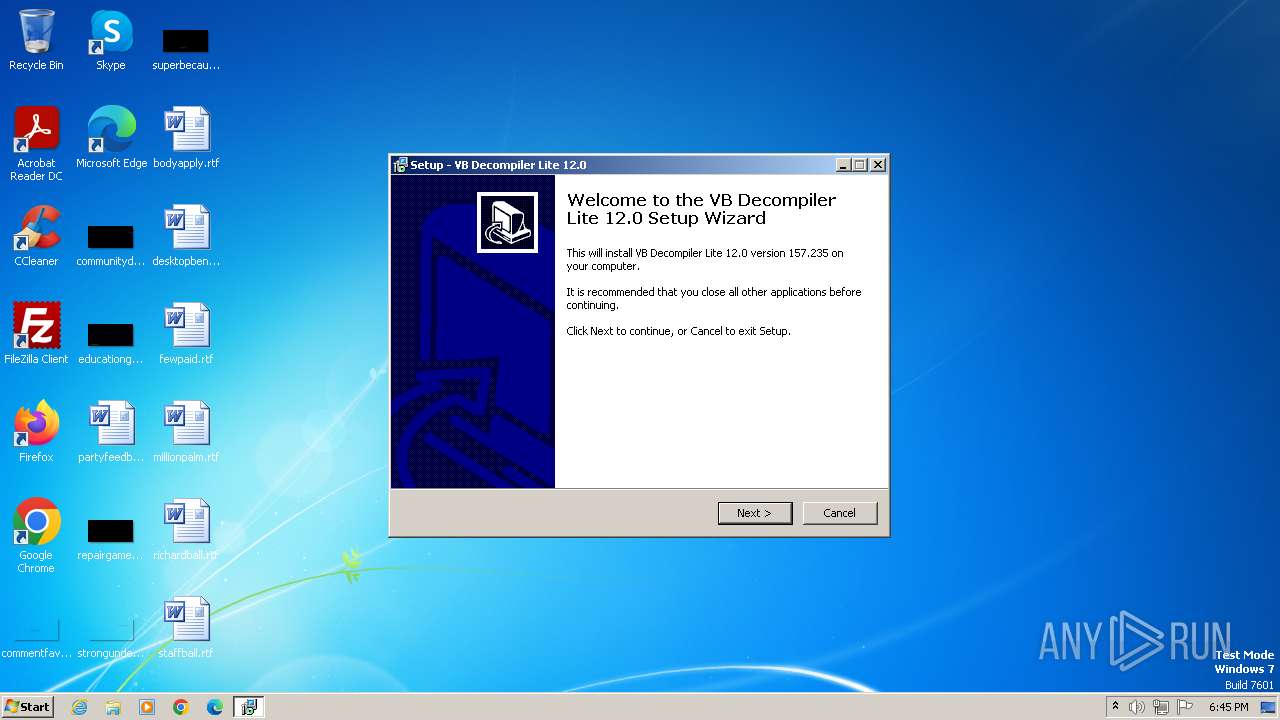
| File name: | VB Decompiler Lite 12.0.exe |
| Full analysis: | https://app.any.run/tasks/7e11344a-8bae-4d8a-97c9-618e90f3dc8c |
| Verdict: | Malicious activity |
| Analysis date: | October 17, 2023, 17:45:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 95C62DCA2255726D342B8C2CCBA42D36 |
| SHA1: | BE8BFBC7BEBB506DB60B0C34710A16A51BF2CF46 |
| SHA256: | DF1E09CA7B5805DA4A7683685B79FAC67D09C25507D07286026E508383D4CD3C |
| SSDEEP: | 24576:6OZE03qYSMXdNkx7CD1IJ9YyZ/hGrEHXlNeUpbi9kNY2ET474EQEFEEjUArDt:6wE06YtdNkx7CD1IJ9YyZ/hGrEHXlNeI |
MALICIOUS
Drops the executable file immediately after the start
- VB Decompiler Lite 12.0.exe (PID: 2060)
- VB Decompiler Lite 12.0.exe (PID: 3908)
- VB Decompiler Lite 12.0.tmp (PID: 316)
- 7za.exe (PID: 1588)
Uses Task Scheduler to run other applications
- sitool.exe (PID: 2668)
Application was dropped or rewritten from another process
- sitool.exe (PID: 2668)
SUSPICIOUS
Reads the Windows owner or organization settings
- VB Decompiler Lite 12.0.tmp (PID: 316)
Drops 7-zip archiver for unpacking
- VB Decompiler Lite 12.0.tmp (PID: 316)
INFO
Create files in a temporary directory
- VB Decompiler Lite 12.0.exe (PID: 3908)
- VB Decompiler Lite 12.0.exe (PID: 2060)
- VB Decompiler Lite 12.0.tmp (PID: 316)
- 7za.exe (PID: 3700)
- 7za.exe (PID: 1588)
- 7za.exe (PID: 3552)
Reads the computer name
- VB Decompiler Lite 12.0.tmp (PID: 3448)
- wmpnscfg.exe (PID: 3828)
- VB Decompiler Lite 12.0.tmp (PID: 316)
- sitool.exe (PID: 2668)
Checks supported languages
- VB Decompiler Lite 12.0.tmp (PID: 3448)
- wmpnscfg.exe (PID: 3828)
- VB Decompiler Lite 12.0.exe (PID: 3908)
- VB Decompiler Lite 12.0.exe (PID: 2060)
- VB Decompiler Lite 12.0.tmp (PID: 316)
- 7za.exe (PID: 3700)
- 7za.exe (PID: 1588)
- 7za.exe (PID: 3552)
- sitool.exe (PID: 2668)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3828)
- sitool.exe (PID: 2668)
Application was dropped or rewritten from another process
- VB Decompiler Lite 12.0.tmp (PID: 3448)
- VB Decompiler Lite 12.0.tmp (PID: 316)
- 7za.exe (PID: 3700)
- 7za.exe (PID: 1588)
- 7za.exe (PID: 3552)
Creates files or folders in the user directory
- VB Decompiler Lite 12.0.tmp (PID: 316)
- sitool.exe (PID: 2668)
Reads the Internet Settings
- explorer.exe (PID: 2864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (45.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (20.9) |
| .exe | | | Win32 Executable (generic) (14.3) |
| .exe | | | Win16/32 Executable Delphi generic (6.6) |
| .exe | | | Generic Win/DOS Executable (6.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:06:14 15:27:46+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 53760 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1181c |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 157.235.0.0 |
| ProductVersionNumber: | 157.235.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | |
| FileVersion: | 157.235 |
| LegalCopyright: | |
| ProductName: | |
| ProductVersion: | 157.235 |
Total processes
58
Monitored processes
14
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Users\admin\AppData\Local\Temp\is-CPB61.tmp\VB Decompiler Lite 12.0.tmp" /SL5="$1001CA,372163,121344,C:\Users\admin\AppData\Local\Temp\VB Decompiler Lite 12.0.exe" /SPAWNWND=$1101BE /NOTIFYWND=$40302 | C:\Users\admin\AppData\Local\Temp\is-CPB61.tmp\VB Decompiler Lite 12.0.tmp | VB Decompiler Lite 12.0.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1588 | "C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\7za.exe" x "C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\form.res" -p"mSR-@sM1tH" | C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\7za.exe | — | VB Decompiler Lite 12.0.tmp | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 4.65 Modules
| |||||||||||||||
| 2060 | "C:\Users\admin\AppData\Local\Temp\VB Decompiler Lite 12.0.exe" /SPAWNWND=$1101BE /NOTIFYWND=$40302 | C:\Users\admin\AppData\Local\Temp\VB Decompiler Lite 12.0.exe | VB Decompiler Lite 12.0.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Exit code: 0 Version: 157.235 Modules
| |||||||||||||||
| 2160 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\VB Decompiler Lite 12.0\license.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2668 | "C:\Users\admin\AppData\Roaming\SysInfoTool\sitool.exe" -cr -tu 4 | C:\Users\admin\AppData\Roaming\SysInfoTool\sitool.exe | — | VB Decompiler Lite 12.0.tmp | |||||||||||
User: admin Integrity Level: HIGH Description: Terminal System Info Exit code: 0 Version: 2.0.226.280 Modules
| |||||||||||||||
| 2864 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2880 | "explorer.exe" "C:\Users\admin\Desktop\VB Decompiler Lite 12.0" | C:\Windows\explorer.exe | — | VB Decompiler Lite 12.0.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3212 | "C:\Windows\system32\schtasks.exe" /Delete /tn "Microsoft\Windows\Windows Error Reporting\TerminalSysInfo" /f | C:\Windows\System32\schtasks.exe | — | sitool.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3448 | "C:\Users\admin\AppData\Local\Temp\is-OF3H7.tmp\VB Decompiler Lite 12.0.tmp" /SL5="$40302,372163,121344,C:\Users\admin\AppData\Local\Temp\VB Decompiler Lite 12.0.exe" | C:\Users\admin\AppData\Local\Temp\is-OF3H7.tmp\VB Decompiler Lite 12.0.tmp | — | VB Decompiler Lite 12.0.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3552 | "C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\7za.exe" x "C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\misc.res" -p"mSR-@sM1tH" | C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\7za.exe | — | VB Decompiler Lite 12.0.tmp | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 4.65 Modules
| |||||||||||||||
Total events
4 085
Read events
3 988
Write events
90
Delete events
7
Modification events
| (PID) Process: | (3828) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{DF147E6A-3263-4800-8594-387D720ECEF3}\{C01382C4-80F3-4280-A0C1-D414DA5DE7AC} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3828) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{DF147E6A-3263-4800-8594-387D720ECEF3} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3828) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{AF2396DE-971E-41CB-9579-5E7196A31577} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2864) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2864) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000000000000200000007000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2864) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\0\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0000000001000000FFFFFFFF | |||
| (PID) Process: | (2864) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2864) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (2864) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2864) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
5
Suspicious files
3
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 316 | VB Decompiler Lite 12.0.tmp | C:\Users\admin\AppData\Local\Temp\{46CB8489-184F-4095-B80D-FE7D732A67A9}\is-PTP81.tmp | — | |
MD5:— | SHA256:— | |||
| 316 | VB Decompiler Lite 12.0.tmp | C:\Users\admin\AppData\Local\Temp\{46CB8489-184F-4095-B80D-FE7D732A67A9}\license.txt | — | |
MD5:— | SHA256:— | |||
| 3552 | 7za.exe | C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\misc.xml | xml | |
MD5:D54DA888E3C5FD5BA749EC296E0C0FD9 | SHA256:EC58F7E5FE7C18248BF4B987DD3D16A8A67508EAE035DF5A25F2643E0E53BEBF | |||
| 316 | VB Decompiler Lite 12.0.tmp | C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\7za.exe | executable | |
MD5:E92604E043F51C604B6D1AC3BCD3A202 | SHA256:FA252E501332B7486A972E7E471CF6915DAA681AF35C6AA102213921093EB2A3 | |||
| 316 | VB Decompiler Lite 12.0.tmp | C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\form.res | compressed | |
MD5:0B1E8774C0FB67B4F6B8573675E55B83 | SHA256:C1FA579DF0D7A4C508DD82BC5632B54A088804B6AD456F6D29C595FB6D33DCF5 | |||
| 316 | VB Decompiler Lite 12.0.tmp | C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\misc.res | compressed | |
MD5:B0DAFE58A3367C5E4DC3E81B80EC9DA7 | SHA256:42F983FB8F67BFF77A4773CB69314AAB7768C9E92878E26D979F9A4827385941 | |||
| 316 | VB Decompiler Lite 12.0.tmp | C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\sub.res | compressed | |
MD5:81EE6029243D6C780CF69BDF17DA7959 | SHA256:BC494BDDAC67892C5817663DE836EC5968F813246A948DC1E163D154800E7AA1 | |||
| 2060 | VB Decompiler Lite 12.0.exe | C:\Users\admin\AppData\Local\Temp\is-CPB61.tmp\VB Decompiler Lite 12.0.tmp | executable | |
MD5:34ACC2BDB45A9C436181426828C4CB49 | SHA256:9C81817ACD4982632D8C7F1DF3898FCA1477577738184265D735F49FC5480F07 | |||
| 3700 | 7za.exe | C:\Users\admin\AppData\Local\Temp\is-78VB4.tmp\sub.xml | xml | |
MD5:C047508A4A1F583B7ED31EC7B0DF9695 | SHA256:CD999BAA036D44D442FE43A541D69F04BA206C58938F3C22EC0F226493C63E35 | |||
| 3908 | VB Decompiler Lite 12.0.exe | C:\Users\admin\AppData\Local\Temp\is-OF3H7.tmp\VB Decompiler Lite 12.0.tmp | executable | |
MD5:34ACC2BDB45A9C436181426828C4CB49 | SHA256:9C81817ACD4982632D8C7F1DF3898FCA1477577738184265D735F49FC5480F07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
5
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
316 | VB Decompiler Lite 12.0.tmp | POST | 200 | 216.58.206.46:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
316 | VB Decompiler Lite 12.0.tmp | GET | 200 | 188.114.96.3:80 | http://avkit.org/home/getchannel | unknown | binary | 1 b | unknown |
316 | VB Decompiler Lite 12.0.tmp | POST | 200 | 216.58.206.46:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
316 | VB Decompiler Lite 12.0.tmp | 216.58.206.46:80 | www.google-analytics.com | GOOGLE | US | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
316 | VB Decompiler Lite 12.0.tmp | 188.114.96.3:80 | avkit.org | CLOUDFLARENET | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google-analytics.com |
| whitelisted |
avkit.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
316 | VB Decompiler Lite 12.0.tmp | Unknown Traffic | ET HUNTING Suspicious Empty User-Agent |