| File name: | LOL.exe |
| Full analysis: | https://app.any.run/tasks/b75c7995-0ebd-46fb-ae3d-f491da740b66 |
| Verdict: | Malicious activity |
| Analysis date: | August 23, 2019, 12:43:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | C59801CEB711CF44A7ACE29DBFA0F9DD |
| SHA1: | BCDB6C2F64F4EB1DFA4F1F1D03F4D7F5F446A792 |
| SHA256: | DF15226975F0E154CEB5D16F19E374C71615ADE38D690A21A79A8E91C3A1E9D4 |
| SSDEEP: | 196608:cof15bpDgFVsDSgB6RdwINzWpXi/q8/7pCPvJioysLdVxujQho:cofryVs36zXKpib/7pi0hizxu+ |
MALICIOUS
Application was dropped or rewritten from another process
- QQPCGameDL.exe (PID: 2508)
- TenioDL.exe (PID: 2764)
Loads dropped or rewritten executable
- QQPCGameDL.exe (PID: 2508)
- TenioDL.exe (PID: 2764)
SUSPICIOUS
Low-level read access rights to disk partition
- QQPCGameDL.exe (PID: 2508)
Executable content was dropped or overwritten
- LOL.exe (PID: 2364)
- TenioDL.exe (PID: 2764)
Creates files in the user directory
- TenioDL.exe (PID: 2764)
- QQPCGameDL.exe (PID: 2508)
Uses ICACLS.EXE to modify access control list
- TenioDL.exe (PID: 2764)
INFO
Dropped object may contain Bitcoin addresses
- LOL.exe (PID: 2364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:09:09 15:23:23+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 25600 |
| InitializedDataSize: | 431104 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x354b |
| OSVersion: | 5 |
| ImageVersion: | 6.1 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 09-Sep-2009 13:23:23 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 09-Sep-2009 13:23:23 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000063A2 | 0x00006400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.48045 |
.rdata | 0x00008000 | 0x000018F2 | 0x00001A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.88829 |
.data | 0x0000A000 | 0x0006669C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.42988 |
.ndata | 0x00071000 | 0x00091000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00102000 | 0x00006EB8 | 0x00007000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.19853 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21649 | 968 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 0 | 3752 | UNKNOWN | English - United States | RT_ICON |
3 | 0 | 2216 | UNKNOWN | English - United States | RT_ICON |
4 | 0 | 1384 | UNKNOWN | English - United States | RT_ICON |
5 | 0 | 1128 | UNKNOWN | English - United States | RT_ICON |
6 | 0 | 744 | UNKNOWN | English - United States | RT_ICON |
7 | 0 | 296 | UNKNOWN | English - United States | RT_ICON |
103 | 2.55309 | 104 | UNKNOWN | English - United States | RT_GROUP_ICON |
111 | 2.9304 | 218 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
42
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2276 | "C:\Windows\System32\icacls.exe" C:\Users\admin\AppData\Roaming\Tencent\Config\ /t /setintegritylevel low | C:\Windows\System32\icacls.exe | — | TenioDL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
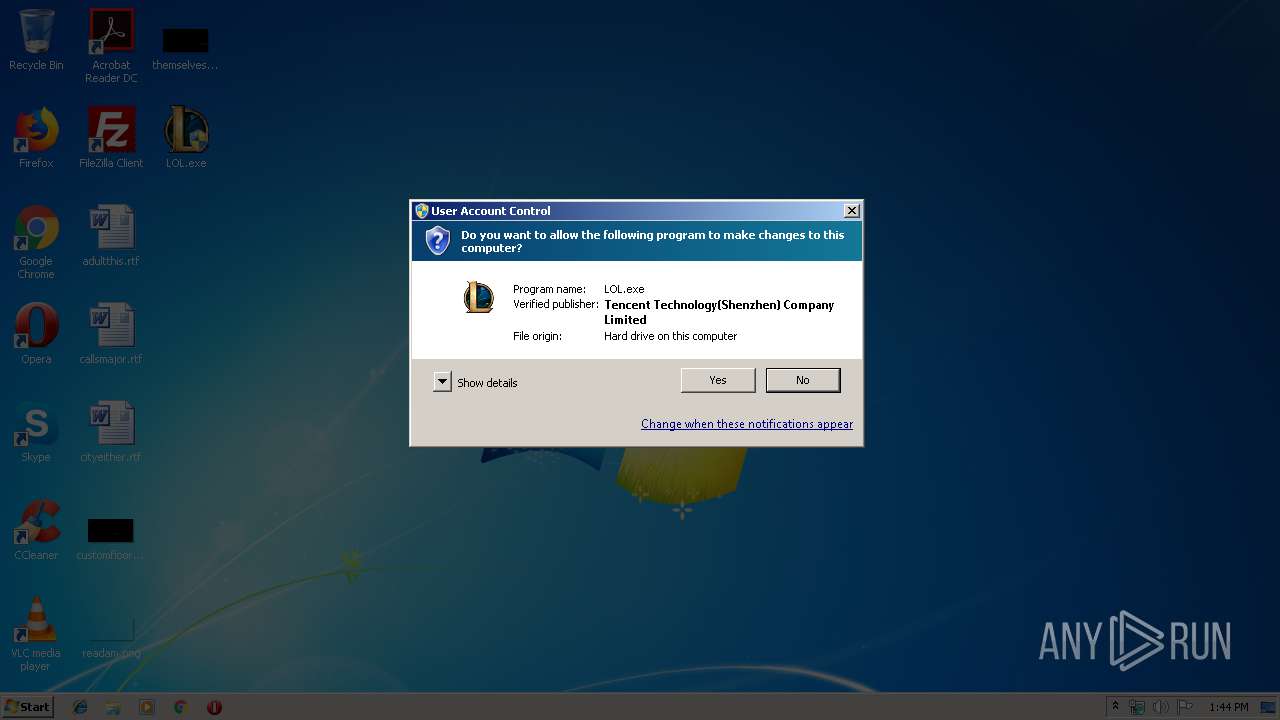
| 2364 | "C:\Users\admin\Desktop\LOL.exe" | C:\Users\admin\Desktop\LOL.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
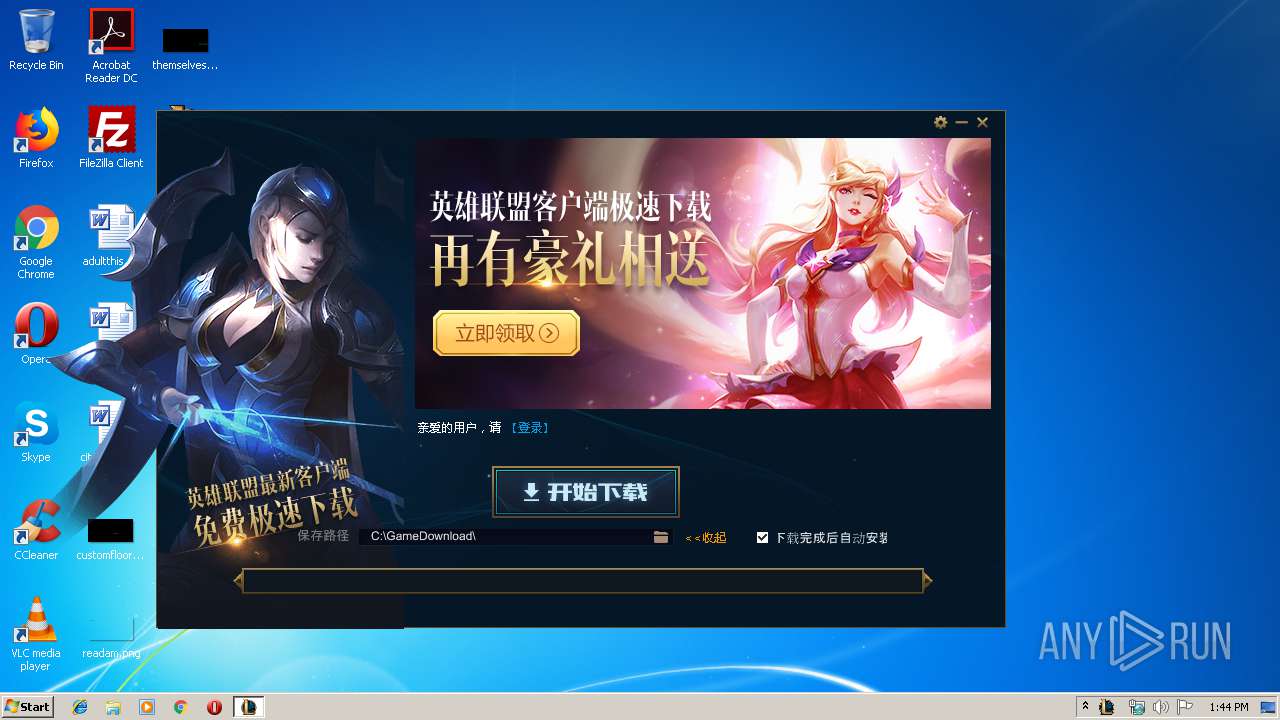
| 2508 | "C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\QQPCGameDL.exe" | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\QQPCGameDL.exe | LOL.exe | ||||||||||||
User: admin Company: TODO: <Company name> Integrity Level: HIGH Description: 腾讯游戏官方下载器 Exit code: 0 Version: 3.2.9.1 Modules
| |||||||||||||||
| 2620 | "C:\Users\admin\Desktop\LOL.exe" | C:\Users\admin\Desktop\LOL.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2764 | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\TenioDL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\TenioDL.exe | QQPCGameDL.exe | ||||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: 腾讯游戏云加速下载引擎(旋风Inside) Exit code: 0 Version: 2, 0, 12, 25 Modules
| |||||||||||||||
Total events
118
Read events
113
Write events
5
Delete events
0
Modification events
| (PID) Process: | (2764) TenioDL.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2764) TenioDL.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2764) TenioDL.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\metnsd\clsid |
| Operation: | write | Name: | SequenceID |
Value: B0270D2822F7BD4493964D8DFE0BB455 | |||
Executable files
24
Suspicious files
13
Text files
8
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2364 | LOL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\QQPCGameDL.exe | executable | |
MD5:— | SHA256:— | |||
| 2364 | LOL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\DuiLib.dll | executable | |
MD5:— | SHA256:— | |||
| 2364 | LOL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\msvcr120.dll | executable | |
MD5:034CCADC1C073E4216E9466B720F9849 | SHA256:86E39B5995AF0E042FCDAA85FE2AEFD7C9DDC7AD65E6327BD5E7058BC3AB615F | |||
| 2364 | LOL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\mfc120u.dll | executable | |
MD5:F4F2A4C459DD3AA22DD3984D13B15746 | SHA256:C2D0E285E2333A9C620BE04A5747881AF0D5615DA32226886E659FF31A9761CC | |||
| 2364 | LOL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\wke.dll | executable | |
MD5:CD3C60A62EE896818E69527B20CFF31A | SHA256:2321F396A0D089C0E7C8AE95160E5EC004C7181BC8951FAFCA2512F95B81F64E | |||
| 2364 | LOL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\msvcr100.dll | executable | |
MD5:0E37FBFA79D349D672456923EC5FBBE3 | SHA256:8793353461826FBD48F25EA8B835BE204B758CE7510DB2AF631B28850355BD18 | |||
| 2364 | LOL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\curllib.dll | executable | |
MD5:45882035D3E92E52B511C497432C0F80 | SHA256:F79808272D03AA7A2E904438F97A63DEE8D0D62FD4ED77709EB80CA3BDBA6510 | |||
| 2364 | LOL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\sqlite3.dll | executable | |
MD5:35B130B0874ABE81E9CC8C9166BF8F17 | SHA256:682A18C2604CE5426B3ED9F47E03FA4FAD2B8906C8739F1C0F6A2F380A4DA96C | |||
| 2364 | LOL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\p2papp.dll | executable | |
MD5:8739E4C38AB297B45C37241189AC5929 | SHA256:3ED87A574FB12089A3793A3FB67EA89F2AE48BCD6D887917D10F3BA182007031 | |||
| 2364 | LOL.exe | C:\Users\admin\AppData\Local\Temp\CommonGameDownloader\132_1564650489_91701\TenioDL.dll | executable | |
MD5:6E4CE3DB3B79A958A0272220E3E1085C | SHA256:CA6FC3BA36A8C7F55EA38E6A25F02202ECA2F49152BE5731EB75724B5B95F21F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
38
DNS requests
25
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2764 | TenioDL.exe | GET | 302 | 203.205.138.72:80 | http://down.qq.com/lol/full/4146/LOL_V4.1.4.6_FULL.exe | CN | — | — | suspicious |
2764 | TenioDL.exe | GET | — | 119.28.164.223:80 | http://119.28.164.223/dlied1.qq.com/lol/full/4146/LOL_V4.1.4.6_FULL.exe?mkey=5d5ff948b9cfadf7&f=0a7c&cip=185.207.139.2&proto=http | CN | — | — | suspicious |
2764 | TenioDL.exe | GET | 302 | 203.205.138.72:80 | http://down.qq.com/lol/full/4146/LOL_V4.1.4.6_FULL.exe | CN | — | — | suspicious |
2764 | TenioDL.exe | GET | 302 | 203.205.138.72:80 | http://down.qq.com/lol/full/4146/LOL_V4.1.4.6_FULL.exe | CN | — | — | suspicious |
2764 | TenioDL.exe | GET | 302 | 203.205.138.72:80 | http://down.qq.com/lol/full/4146/LOL_V4.1.4.6_FULL.exe | CN | — | — | suspicious |
2764 | TenioDL.exe | GET | 302 | 203.205.138.72:80 | http://down.qq.com/lol/full/4146/LOL_V4.1.4.6_FULL.exe | CN | — | — | suspicious |
2764 | TenioDL.exe | GET | — | 203.205.138.72:80 | http://down.qq.com/lol/full/4146/LOL_V4.1.4.6_FULL.7z.001 | CN | — | — | suspicious |
2764 | TenioDL.exe | GET | — | 203.205.138.72:80 | http://down.qq.com/lol/full/4146/LOL_V4.1.4.6_FULL.7z.001 | CN | — | — | suspicious |
2764 | TenioDL.exe | GET | — | 203.205.251.19:80 | http://203.205.251.19/dlied1.qq.com/lol/full/4146/LOL_V4.1.4.6_FULL.7z.001?mkey=5d5ff93ec02a52e5&f=0a7c&cip=192.42.116.16&proto=http | CN | — | — | unknown |
2764 | TenioDL.exe | GET | 302 | 203.205.138.72:80 | http://down.qq.com/lol/full/4146/LOL_V4.1.4.6_FULL.7z.001 | CN | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2764 | TenioDL.exe | 220.249.245.138:8000 | stun.qqlive.qq.com | China Unicom Shenzen network | CN | unknown |
2764 | TenioDL.exe | 101.89.238.160:8443 | ga.gamedl.qq.com | China Telecom (Group) | CN | unknown |
2508 | QQPCGameDL.exe | 125.39.247.36:8000 | p2pupgrade.gamedl.qq.com | CHINA UNICOM China169 Backbone | CN | unknown |
2764 | TenioDL.exe | 220.194.106.125:14309 | config.gamedl.qq.com | CHINA UNICOM China169 Backbone | CN | unknown |
2764 | TenioDL.exe | 125.39.248.41:443 | downloadtpt.gamedl.qq.com | CHINA UNICOM China169 Backbone | CN | unknown |
2764 | TenioDL.exe | 119.28.164.223:80 | — | Tencent Cloud Computing (Beijing) Co., Ltd | CN | suspicious |
2764 | TenioDL.exe | 128.1.102.10:80 | — | Zenlayer Inc | US | unknown |
2764 | TenioDL.exe | 203.205.251.95:80 | — | — | CN | unknown |
2764 | TenioDL.exe | 119.28.164.222:80 | — | Tencent Cloud Computing (Beijing) Co., Ltd | CN | unknown |
2764 | TenioDL.exe | 128.1.102.21:80 | — | Zenlayer Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ied-tqosdl.qq.com |
| unknown |
p2pupgrade.gamedl.qq.com |
| unknown |
s.dc.qq.com |
| unknown |
stat.gamedl.qq.com |
| unknown |
config.gamedl.qq.com |
| whitelisted |
stun.qqlive.qq.com |
| suspicious |
ps2.gamedl.qq.com |
| unknown |
p2pupdate.gamedl.qq.com |
| unknown |
ga.gamedl.qq.com |
| unknown |
downloadtpt.gamedl.qq.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2764 | TenioDL.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag false) |
2764 | TenioDL.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag true change port flag false) |
2764 | TenioDL.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag true) |
Process | Message |
|---|---|
QQPCGameDL.exe | Adapter Num: 1
Adapter Name: {4040CF00-1B3E-486A-B407-FA14C56B6FC0}
Adapter Desc: Intel(R) PRO/1000 MT Network Connection
Adapter Type: 6
Adapter Mac:52-54-00-4A-04-AF
Adapter IP:1 IP:192.168.100.29 Mask:255.255.255.0 Gateway:192.168.100.2
|
QQPCGameDL.exe |
curl_easy_perform start....
|
QQPCGameDL.exe |
curl_easy_perform end....
|
QQPCGameDL.exe |
curl_easy_perform start....
|
QQPCGameDL.exe |
curl_easy_perform end....
|
QQPCGameDL.exe |
curl_easy_perform start....
|
QQPCGameDL.exe |
curl_easy_perform end....
|
QQPCGameDL.exe |
curl_easy_perform start....
|
QQPCGameDL.exe |
curl_easy_perform end....
|
QQPCGameDL.exe |
curl_easy_perform start....
|