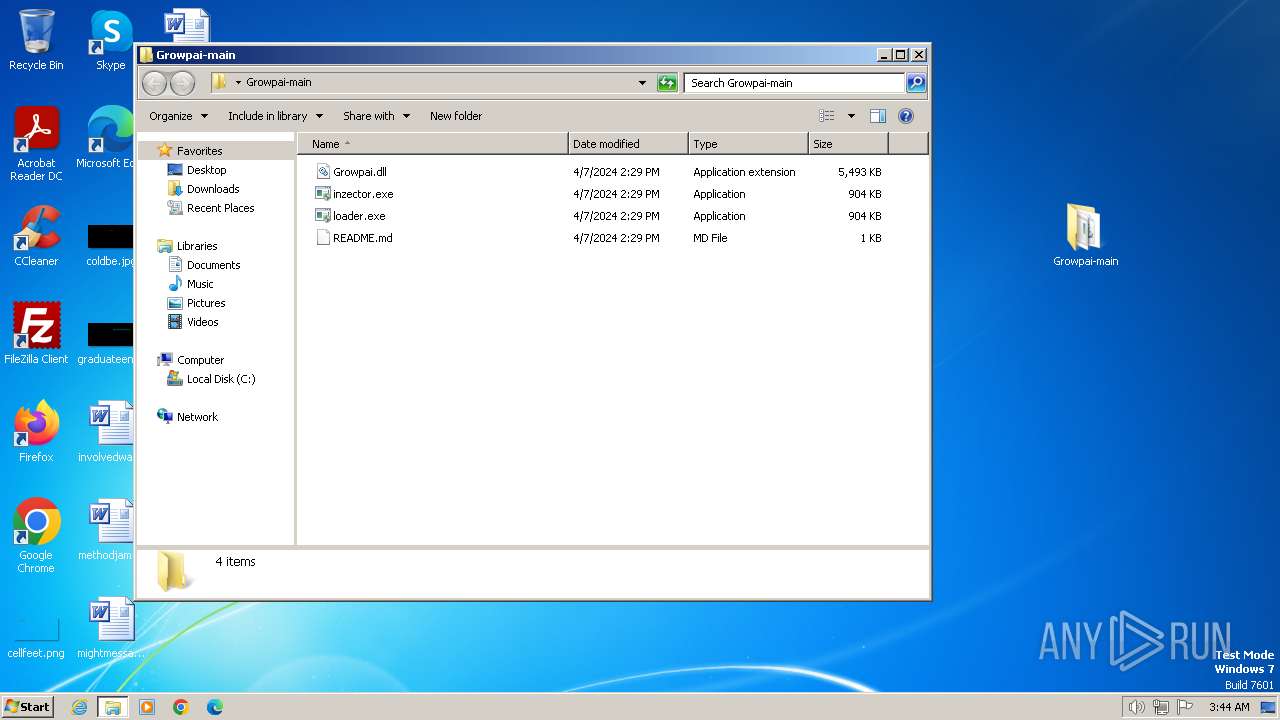
| File name: | Growpai-main.zip |
| Full analysis: | https://app.any.run/tasks/801f9c1f-e2f1-4231-a9cd-b0cd2094def8 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2024, 02:43:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 53AAB8457100F8AA378A3CD6726CFC97 |
| SHA1: | 7B9568D4A84EE0E0CCD6E18C4D696D33482323BF |
| SHA256: | DF06DA6040E8F07007012CD5FB7D554990DFD14C7F559D7F442E271B0EF5A090 |
| SSDEEP: | 98304:0MZHUF8YYDtP12v9T7SjzaRKA9itr8MB1tRJEZvnBSFjjl0LwWS9VhVP4Ef/iyLY:VTV7W4yM49CBrWzWK |
MALICIOUS
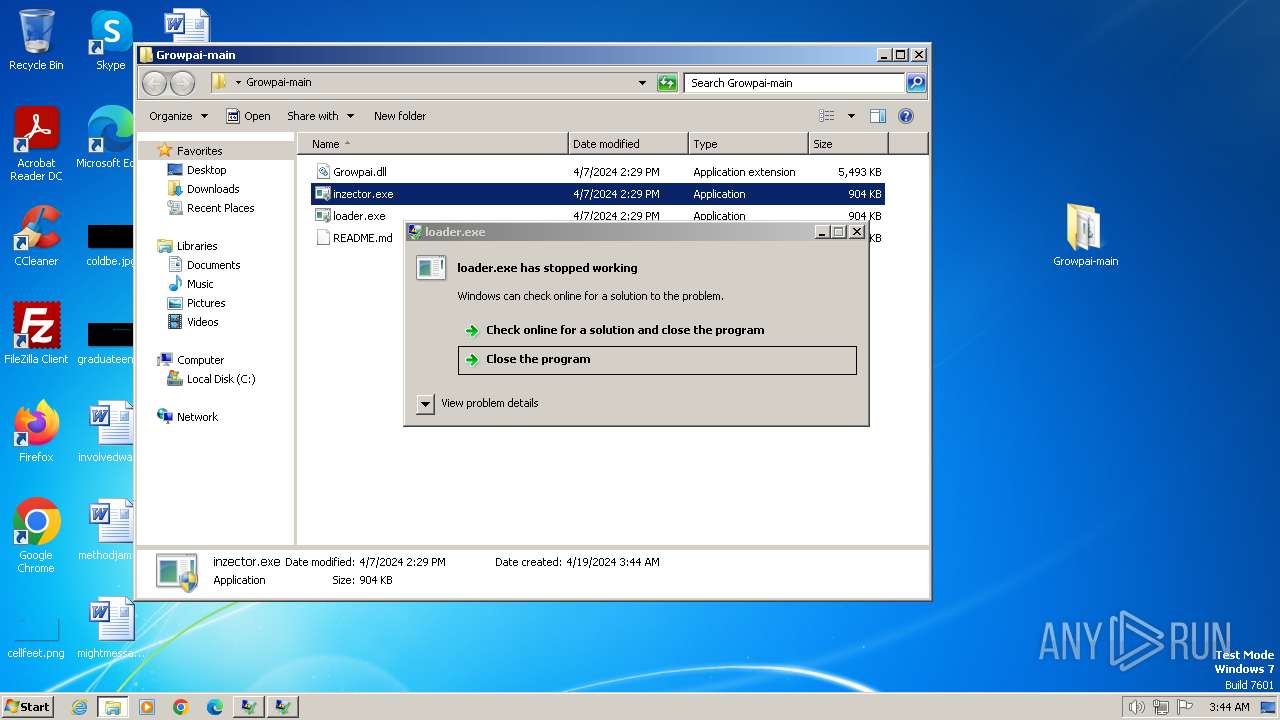
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1288)
- loader.exe (PID: 3044)
- inzector.exe (PID: 1808)
Actions looks like stealing of personal data
- inzector.exe (PID: 1808)
- loader.exe (PID: 3044)
Disables Windows Defender
- inzector.exe (PID: 1808)
- loader.exe (PID: 3044)
SUSPICIOUS
Executable content was dropped or overwritten
- loader.exe (PID: 3044)
- inzector.exe (PID: 1808)
Reads the Internet Settings
- loader.exe (PID: 3044)
- inzector.exe (PID: 1808)
- powershell.exe (PID: 4092)
- powershell.exe (PID: 3692)
Query Microsoft Defender preferences
- loader.exe (PID: 3044)
- inzector.exe (PID: 1808)
Reads settings of System Certificates
- inzector.exe (PID: 1808)
- loader.exe (PID: 3044)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 4092)
- powershell.exe (PID: 3692)
Starts POWERSHELL.EXE for commands execution
- inzector.exe (PID: 1808)
- loader.exe (PID: 3044)
INFO
Reads the computer name
- loader.exe (PID: 3044)
- inzector.exe (PID: 1808)
Checks supported languages
- loader.exe (PID: 3044)
- inzector.exe (PID: 1808)
- dcd.exe (PID: 2724)
- dcd.exe (PID: 3844)
Manual execution by a user
- loader.exe (PID: 3044)
- loader.exe (PID: 1424)
- inzector.exe (PID: 2072)
- inzector.exe (PID: 1808)
Reads Environment values
- loader.exe (PID: 3044)
- inzector.exe (PID: 1808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1288)
Reads the machine GUID from the registry
- loader.exe (PID: 3044)
- inzector.exe (PID: 1808)
Create files in a temporary directory
- loader.exe (PID: 3044)
- inzector.exe (PID: 1808)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4092)
- powershell.exe (PID: 3692)
Reads the software policy settings
- inzector.exe (PID: 1808)
- loader.exe (PID: 3044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:04:07 06:29:56 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Growpai-main/ |
Total processes
52
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1288 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Growpai-main.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1424 | "C:\Users\admin\Desktop\Growpai-main\loader.exe" | C:\Users\admin\Desktop\Growpai-main\loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1808 | "C:\Users\admin\Desktop\Growpai-main\inzector.exe" | C:\Users\admin\Desktop\Growpai-main\inzector.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\Desktop\Growpai-main\inzector.exe" | C:\Users\admin\Desktop\Growpai-main\inzector.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2724 | "C:\Users\admin\AppData\Local\Temp\dcd.exe" -path="" | C:\Users\admin\AppData\Local\Temp\dcd.exe | — | inzector.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3044 | "C:\Users\admin\Desktop\Growpai-main\loader.exe" | C:\Users\admin\Desktop\Growpai-main\loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 3692 | "powershell" Get-MpPreference -verbose | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | inzector.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3844 | "C:\Users\admin\AppData\Local\Temp\dcd.exe" -path="" | C:\Users\admin\AppData\Local\Temp\dcd.exe | — | loader.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4092 | "powershell" Get-MpPreference -verbose | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
17 876
Read events
17 770
Write events
103
Delete events
3
Modification events
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Growpai-main.zip | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
5
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4092 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 1288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1288.45919\Growpai-main\Growpai.dll | executable | |
MD5:4D0D2C76F6299CB909C96393D02FA17E | SHA256:902572D68E1EB8DDC21346501E94BC176962149C390B0F4BDA8317E8E164CB43 | |||
| 1288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1288.45919\Growpai-main\loader.exe | executable | |
MD5:3F1E413B5A4BF4D48C6A80D132C70489 | SHA256:F84AC8ADB94BBB75EFA718DC27221B4197A4033BF78A69D9379306955A02CA54 | |||
| 1288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1288.45919\Growpai-main\README.md | text | |
MD5:724ACB1D47BA7146BFCF81CF54970F2C | SHA256:B9120FCBEC82A55A1EFC24C26D065F9BD2A51212B83A4FBAA47A990F3BF6BB8C | |||
| 1288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1288.45919\Growpai-main\inzector.exe | executable | |
MD5:3F1E413B5A4BF4D48C6A80D132C70489 | SHA256:F84AC8ADB94BBB75EFA718DC27221B4197A4033BF78A69D9379306955A02CA54 | |||
| 1808 | inzector.exe | C:\Users\admin\AppData\Local\Temp\dcd.exe | executable | |
MD5:B5AC46E446CEAD89892628F30A253A06 | SHA256:DEF7AFCB65126C4B04A7CBF08C693F357A707AA99858CAC09A8D5E65F3177669 | |||
| 4092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\elyq4axe.q2g.psm1 | — | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3692 | powershell.exe | C:\Users\admin\AppData\Local\Temp\qhpz1s5g.hxi.ps1 | — | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\brjdr0yb.xxx.ps1 | — | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3692 | powershell.exe | C:\Users\admin\AppData\Local\Temp\puy2tzbi.hlu.psm1 | — | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
10
DNS requests
4
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1808 | inzector.exe | GET | 204 | 172.217.16.206:80 | http://google.com/generate_204 | unknown | — | — | unknown |
3044 | loader.exe | GET | 204 | 142.250.186.110:80 | http://google.com/generate_204 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3044 | loader.exe | 142.250.186.110:80 | google.com | GOOGLE | US | whitelisted |
3044 | loader.exe | 104.21.20.223:443 | eterprx.net | CLOUDFLARENET | — | unknown |
3044 | loader.exe | 172.67.199.29:443 | eternitypr.net | CLOUDFLARENET | US | unknown |
1808 | inzector.exe | 172.217.16.206:80 | google.com | GOOGLE | US | whitelisted |
1808 | inzector.exe | 104.21.20.223:443 | eterprx.net | CLOUDFLARENET | — | unknown |
1808 | inzector.exe | 172.67.199.29:443 | eternitypr.net | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
eterprx.net |
| malicious |
eternitypr.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Eternity Stealer CnC Domain in DNS Lookup (eterprx .net) |
3044 | loader.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Eternity Stealer Domain (eterprx .net in TLS SNI) |
1080 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Eternity Stealer CnC Domain in DNS Lookup (eternitypr .net) |
3044 | loader.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Eternity Stealer Domain (eternitypr .net in TLS SNI) |
1808 | inzector.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Eternity Stealer Domain (eterprx .net in TLS SNI) |
1808 | inzector.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Eternity Stealer Domain (eternitypr .net in TLS SNI) |