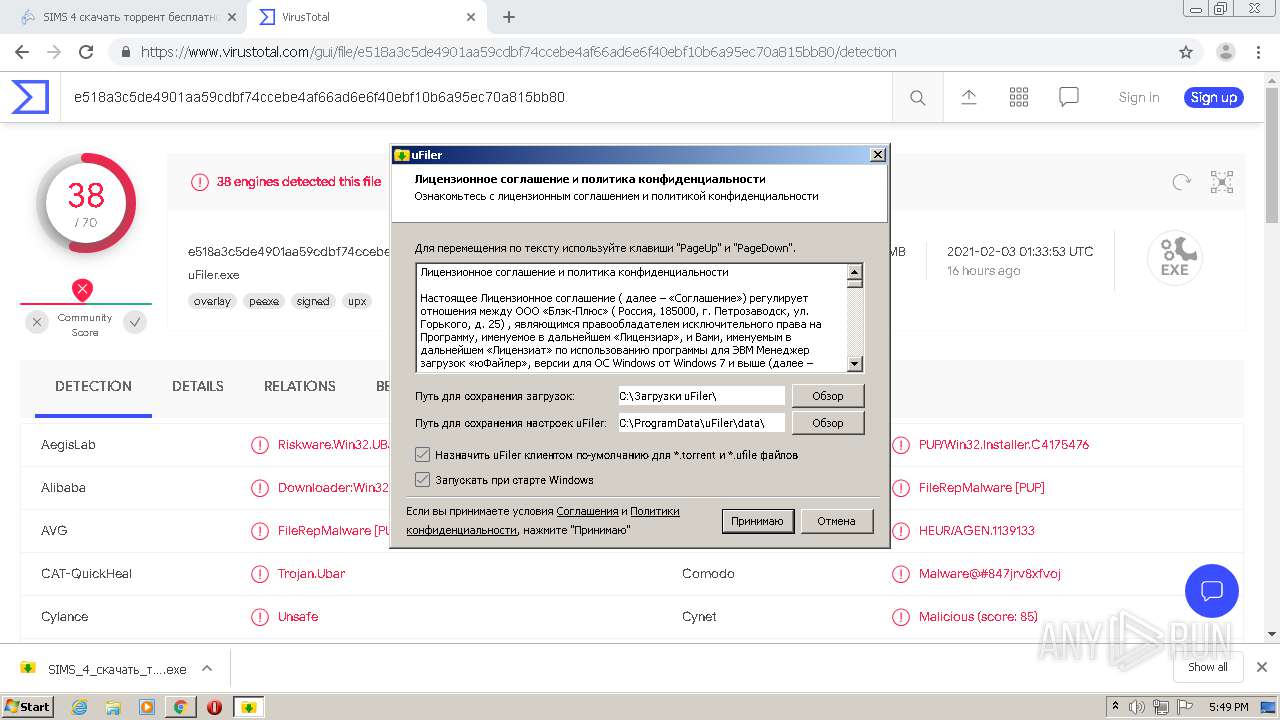
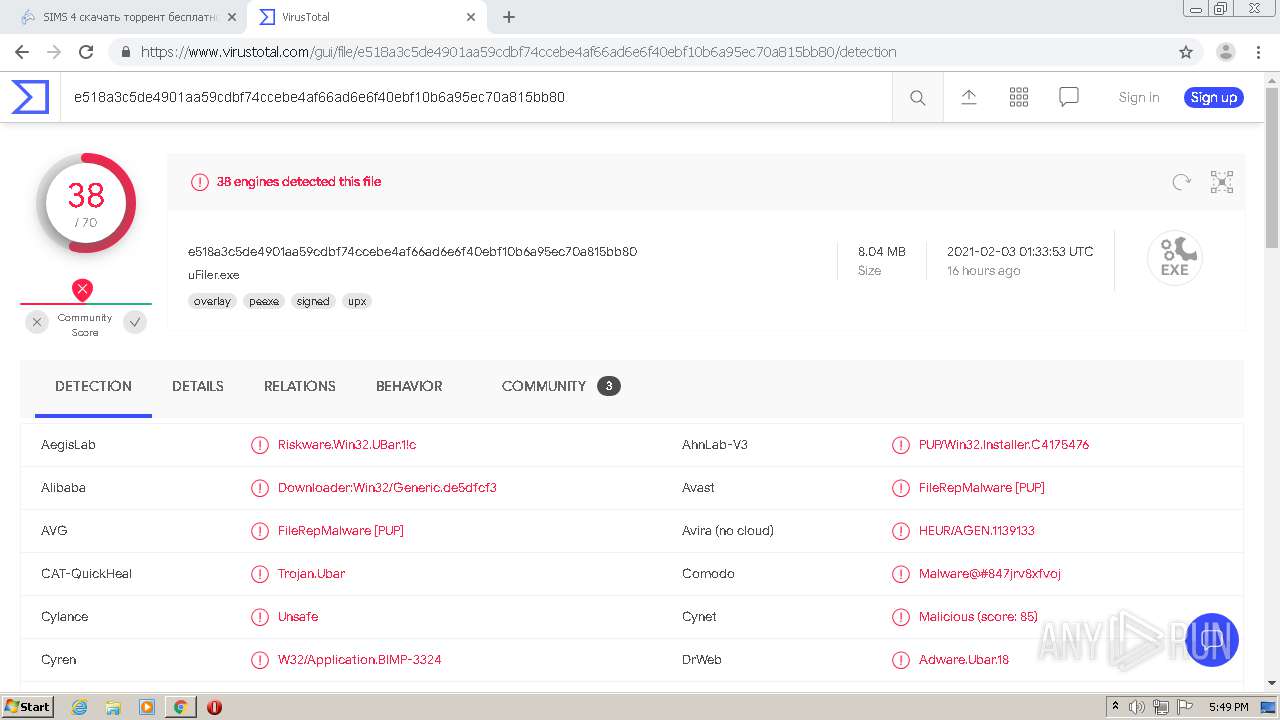
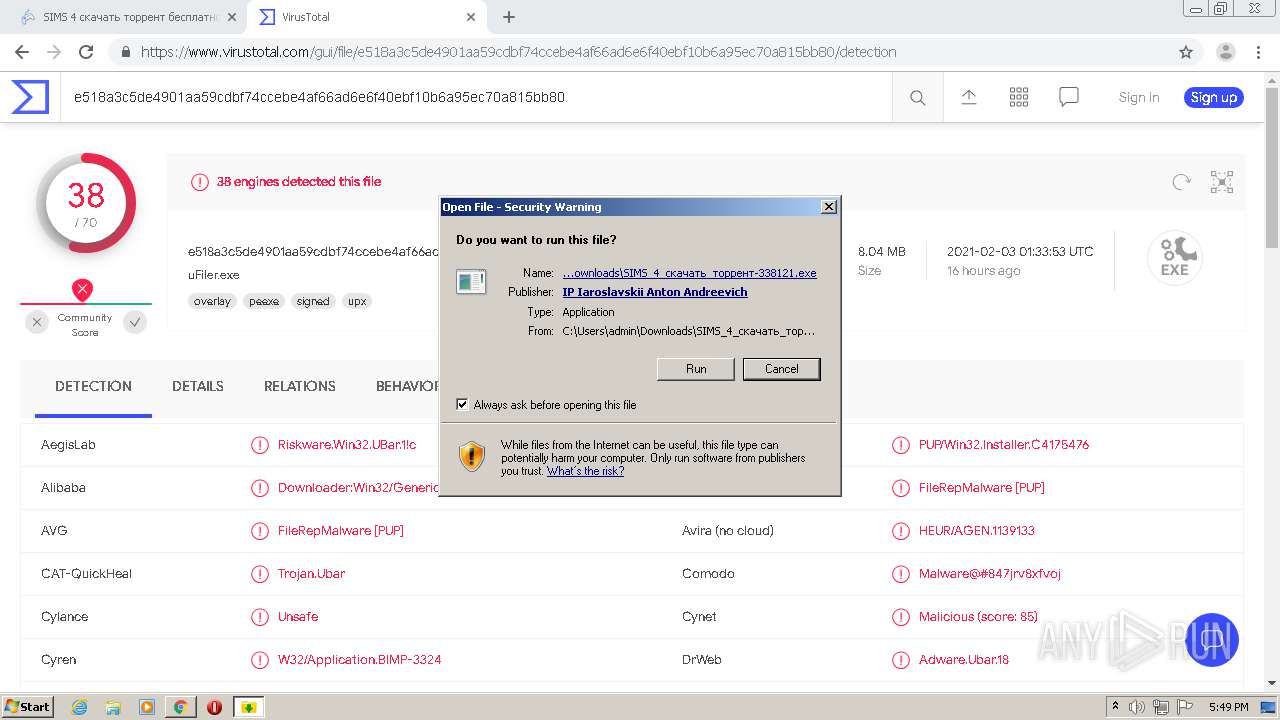
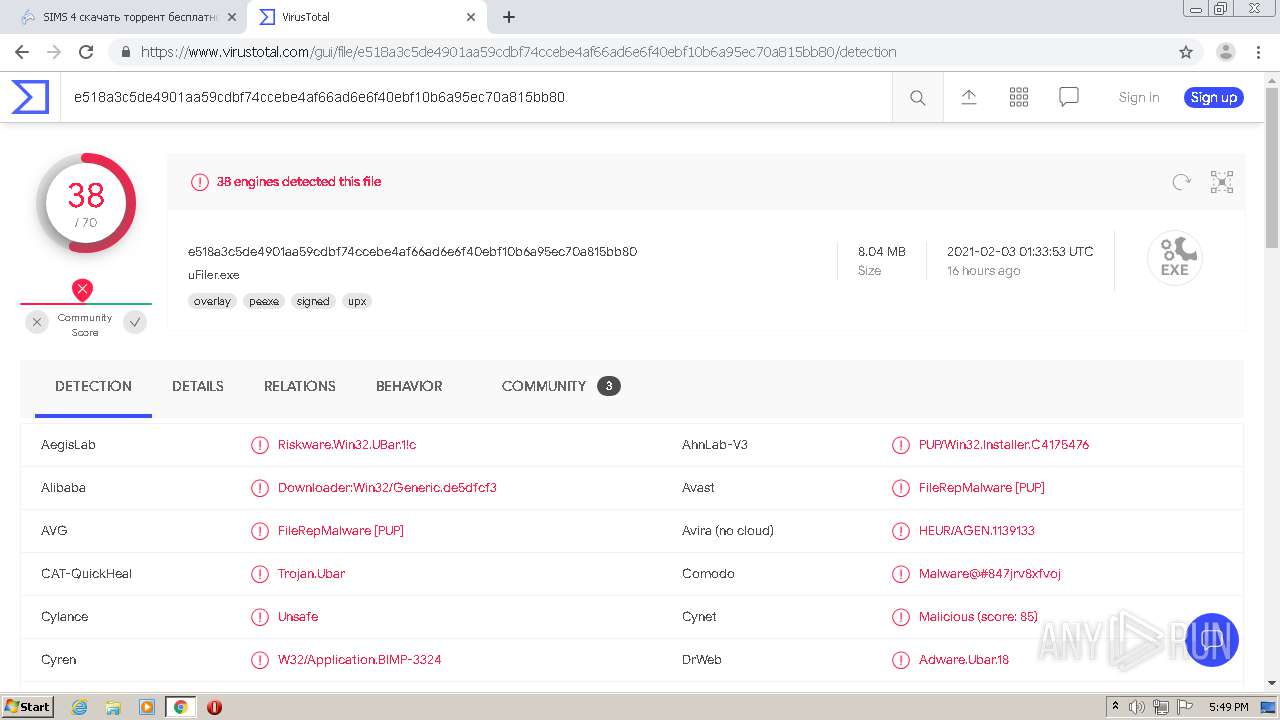
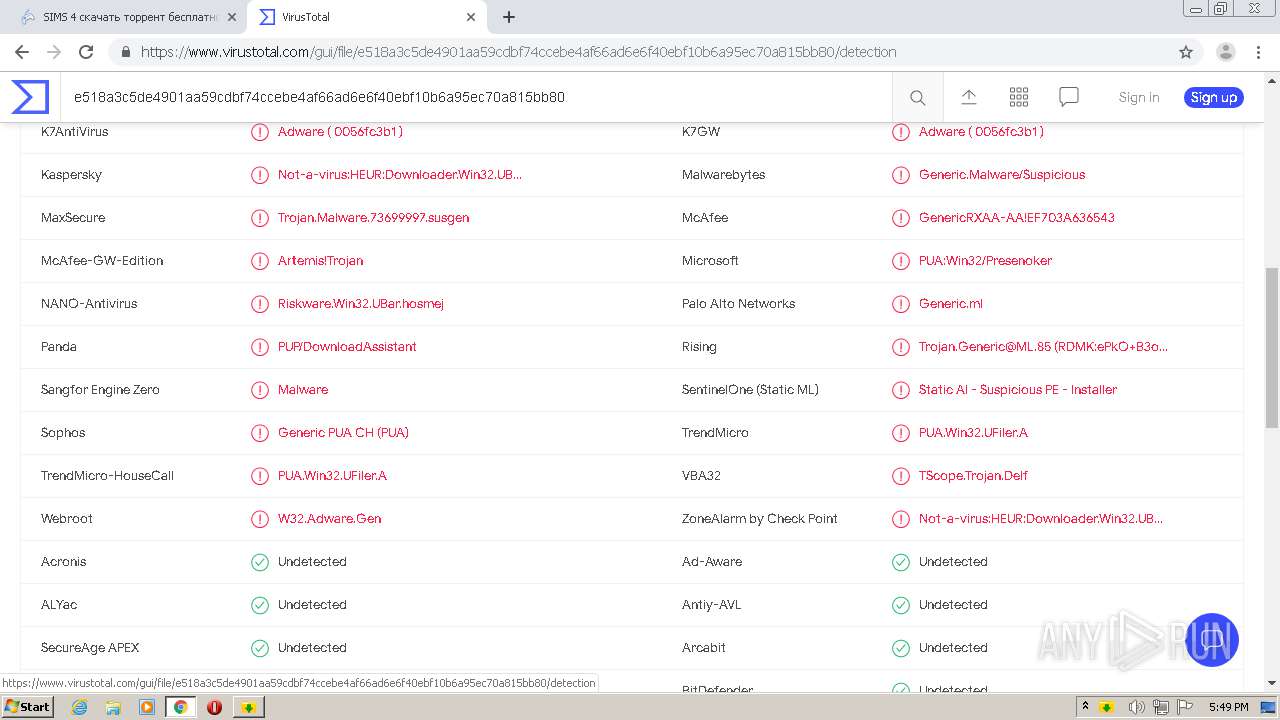
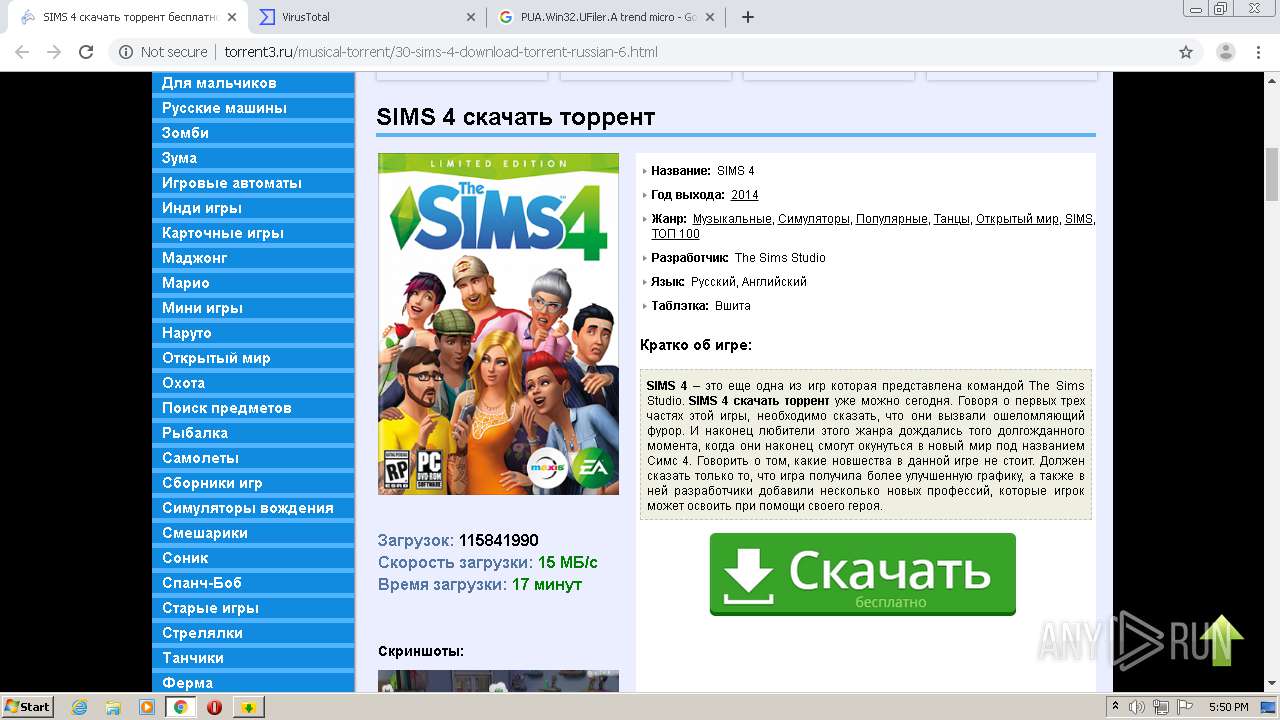
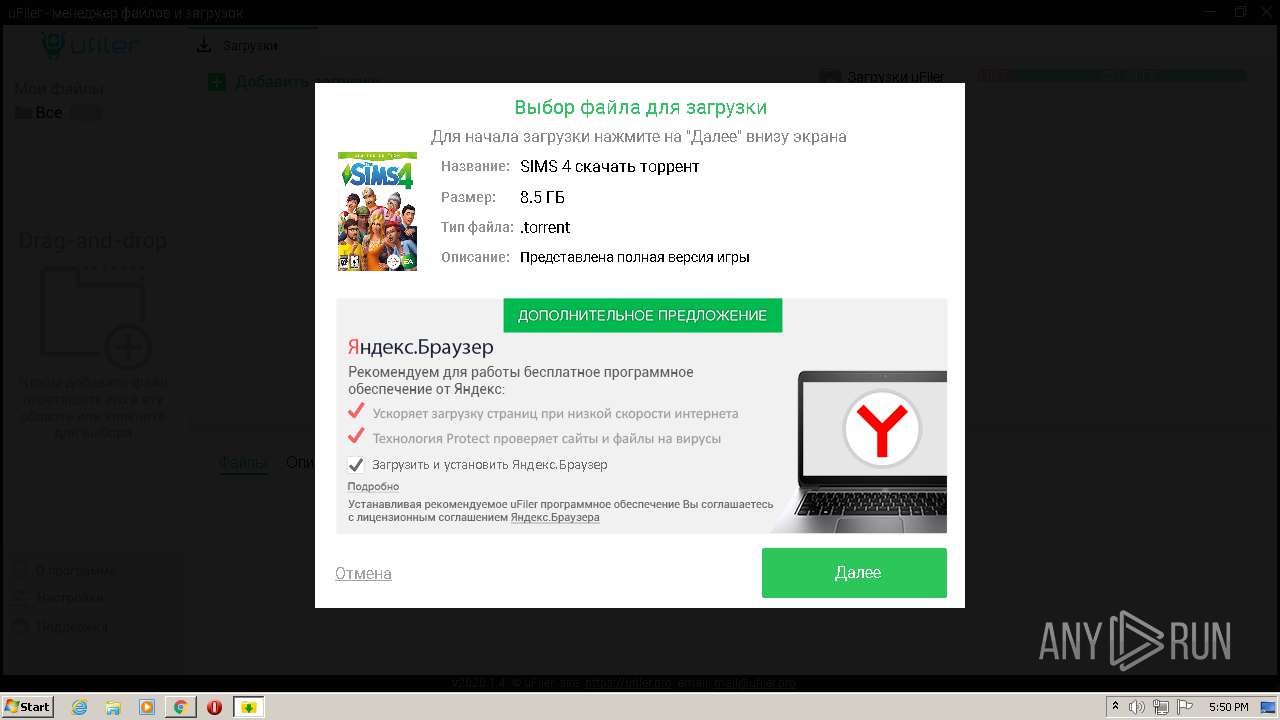
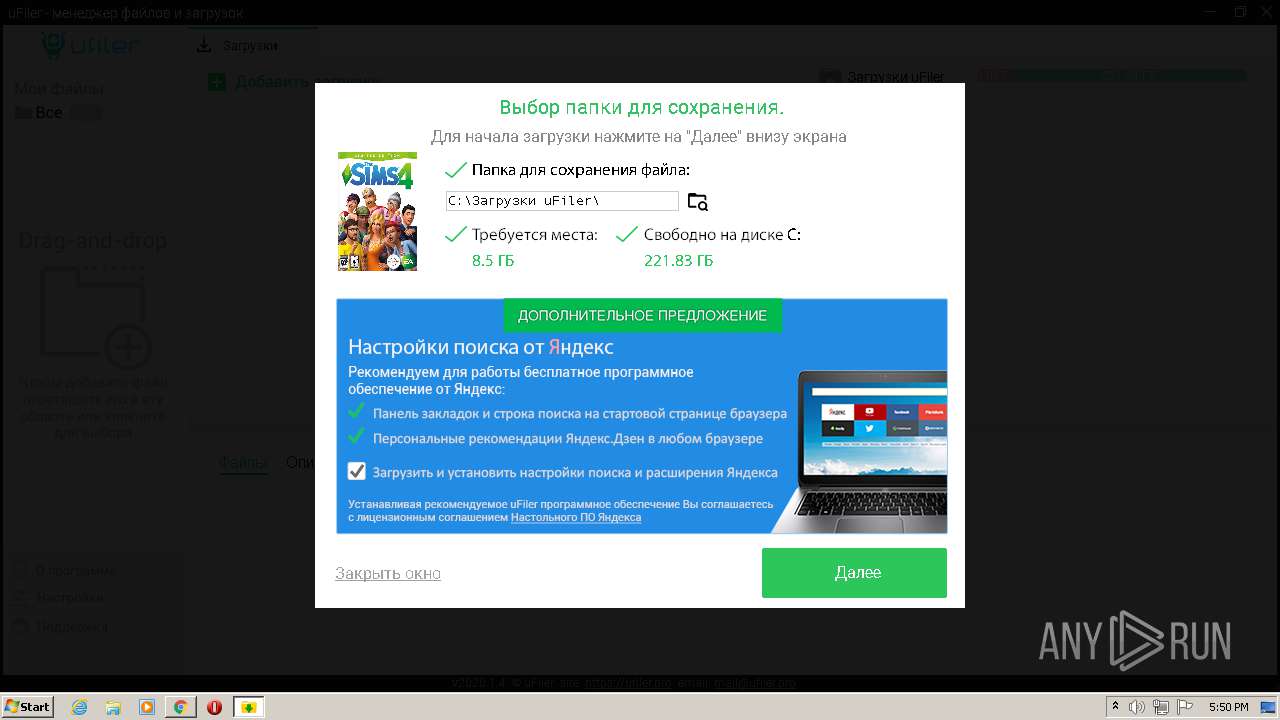
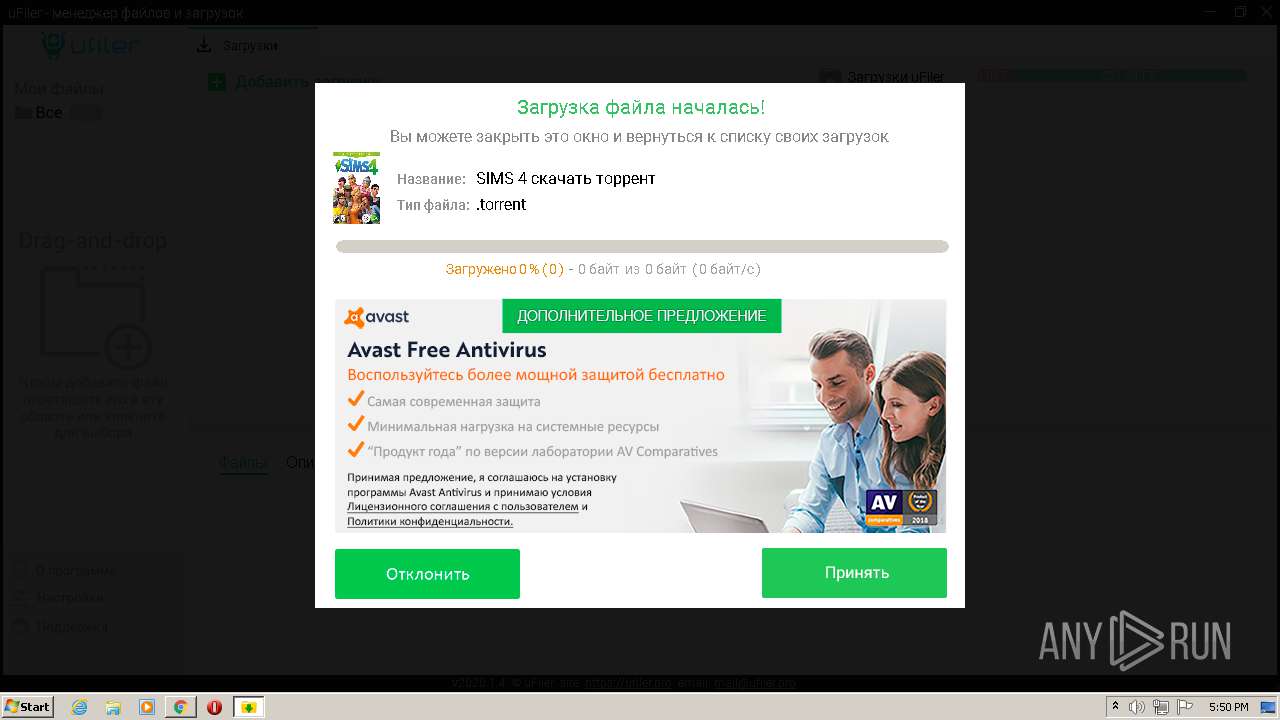
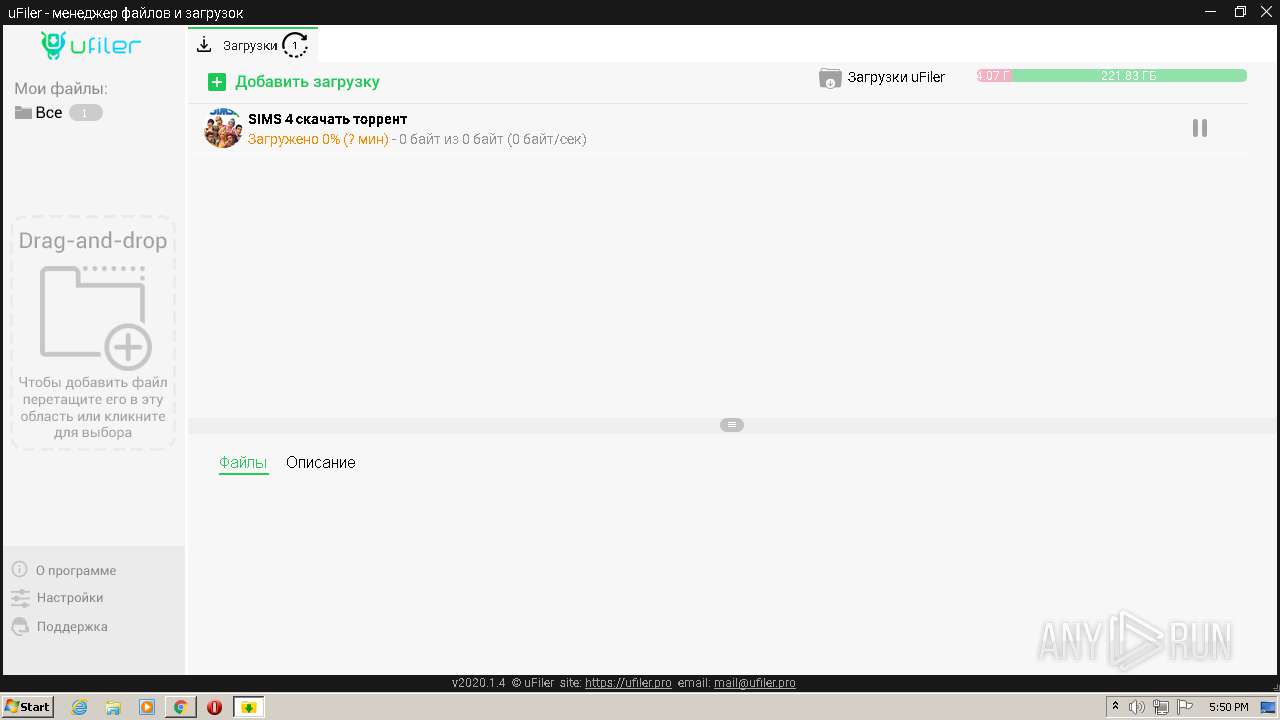
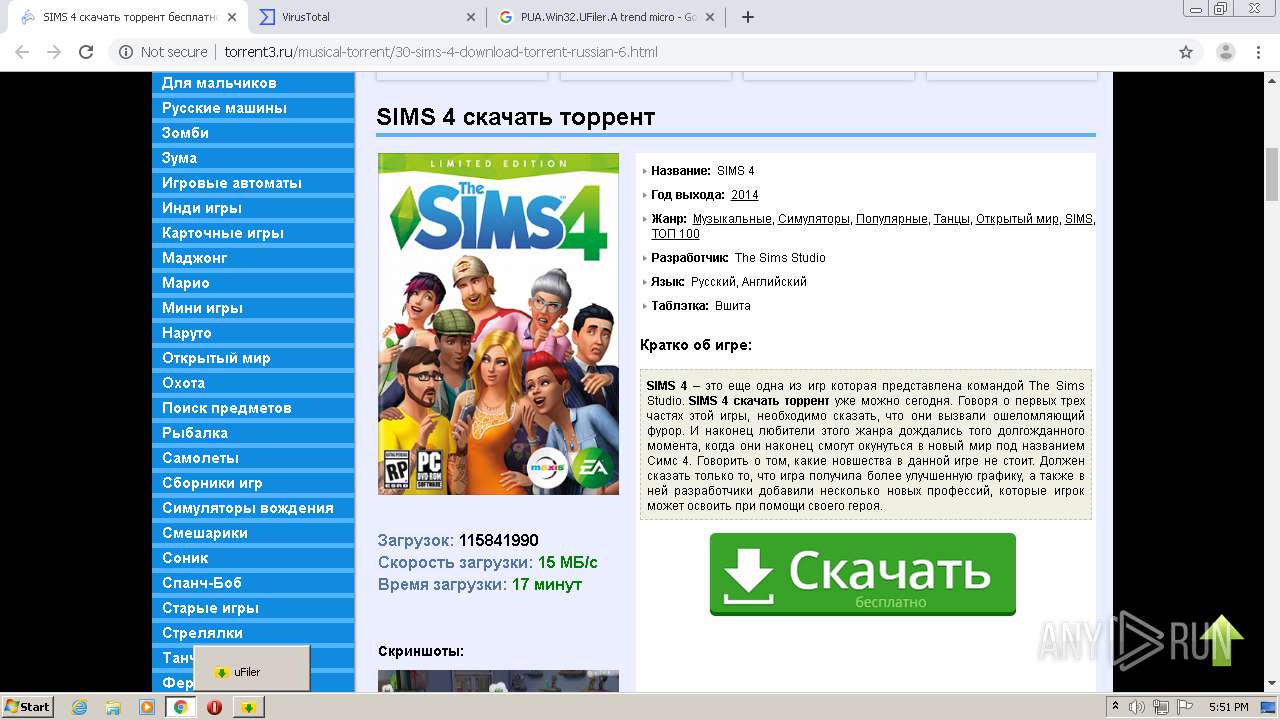
| URL: | http://torrent3.ru/musical-torrent/30-sims-4-download-torrent-russian-6.html |
| Full analysis: | https://app.any.run/tasks/d2951e0a-c62b-4a66-9be6-e07f38900526 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | February 03, 2021, 17:47:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
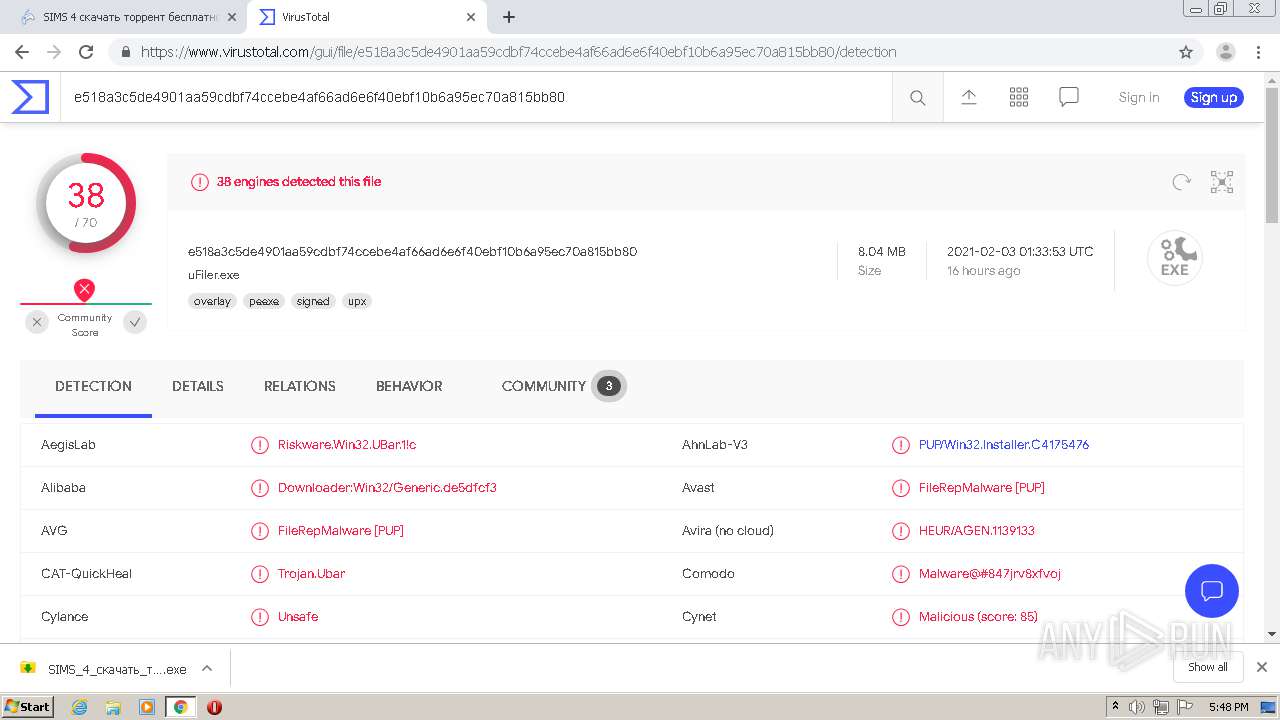
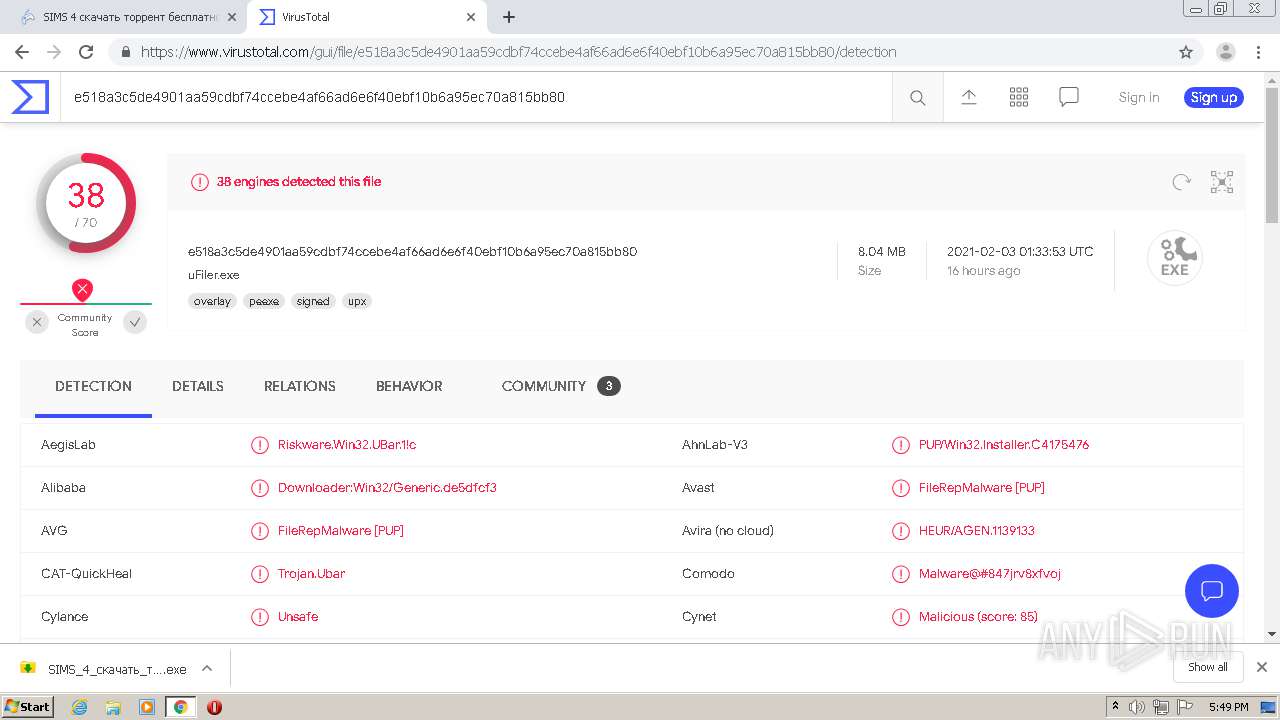
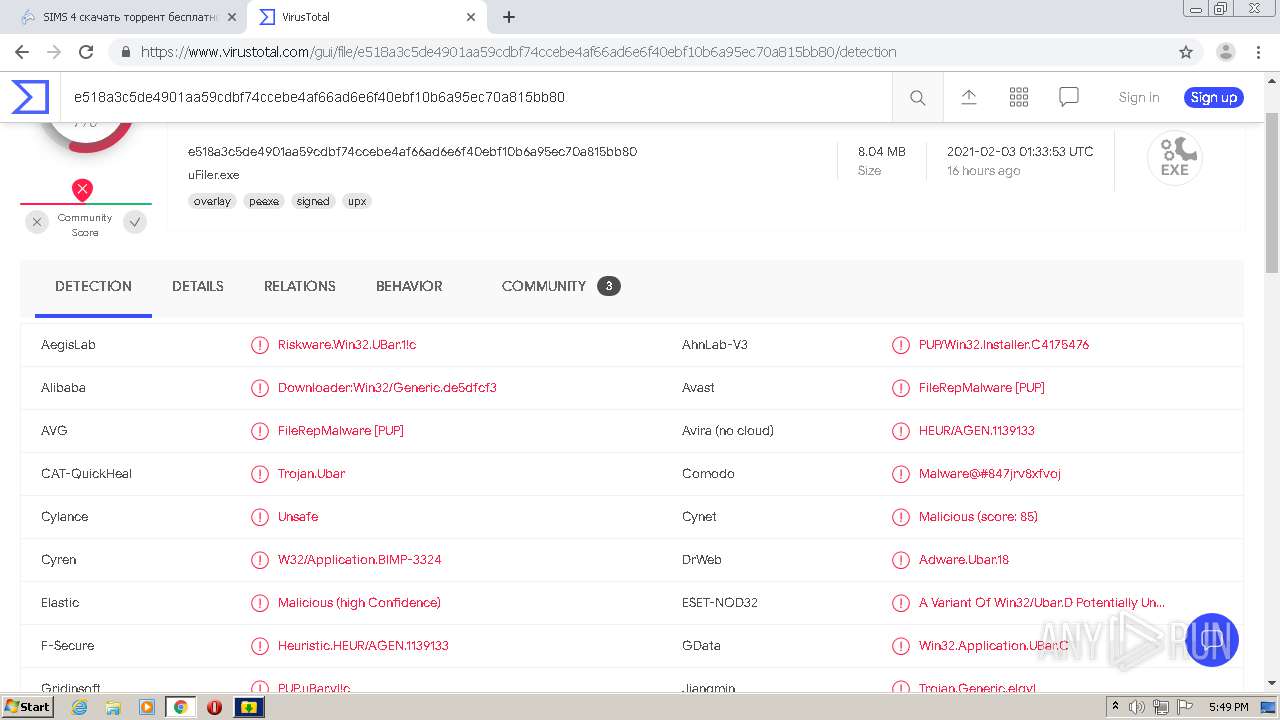
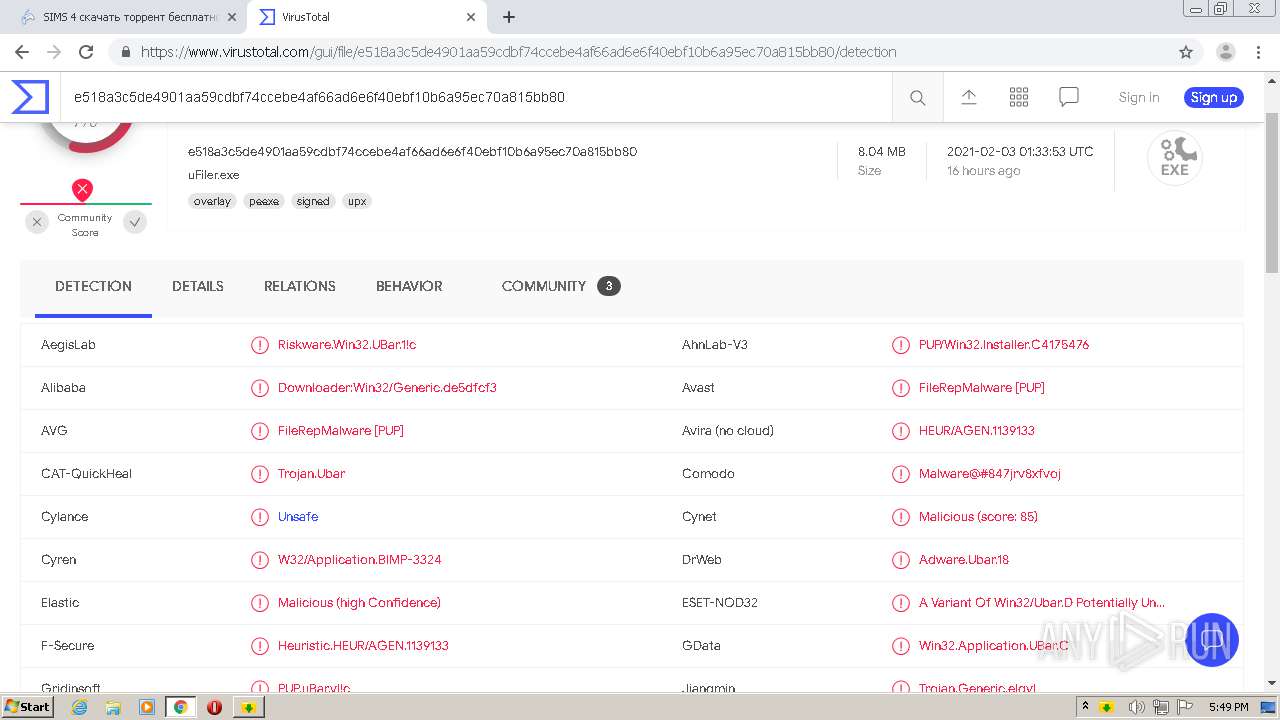
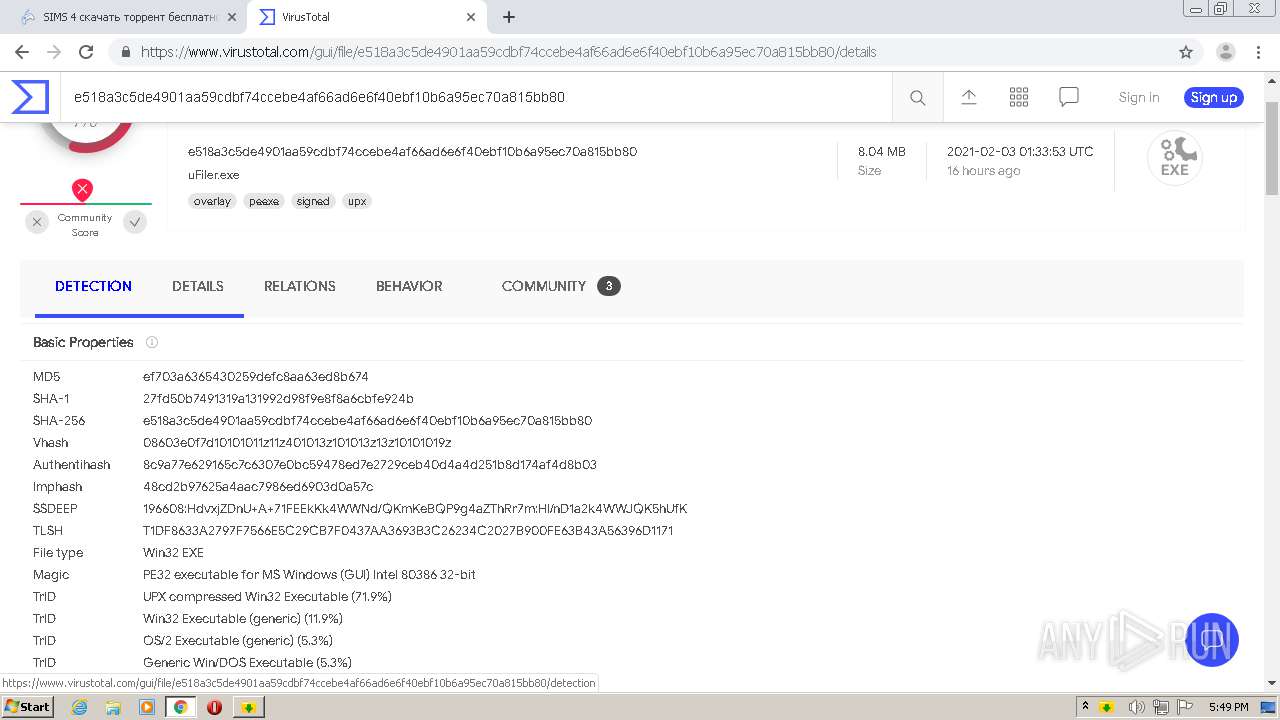
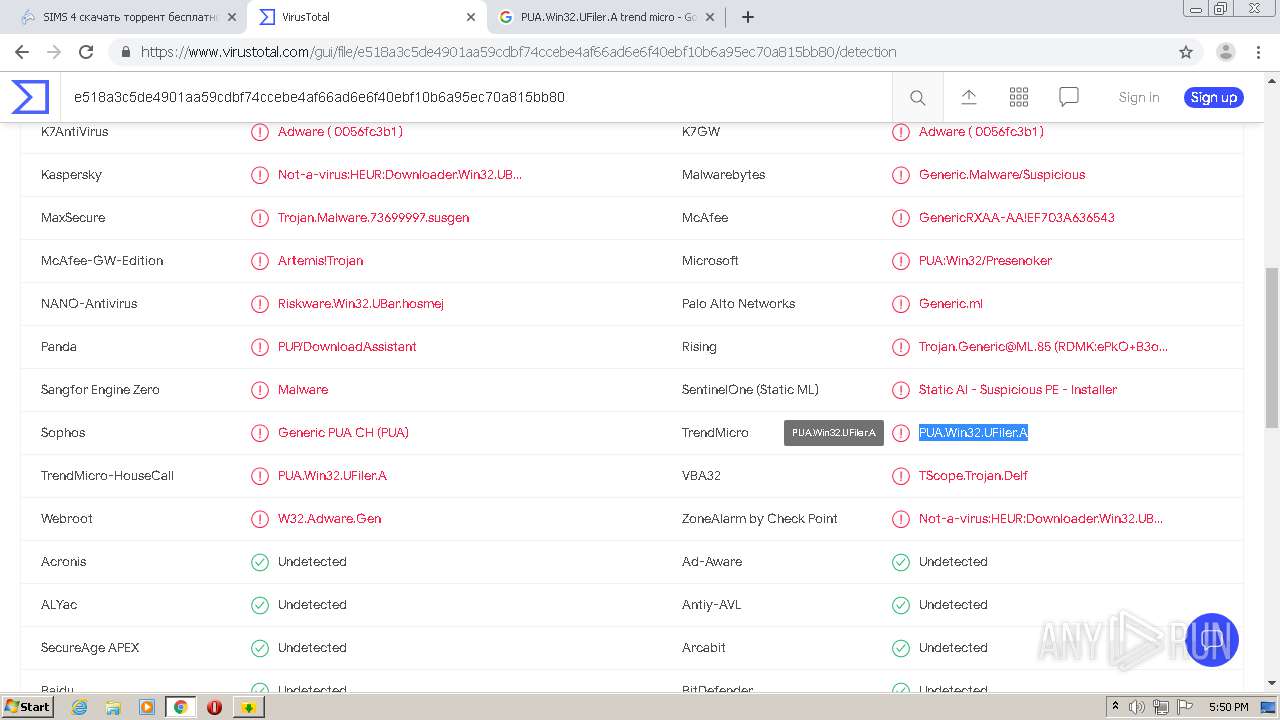
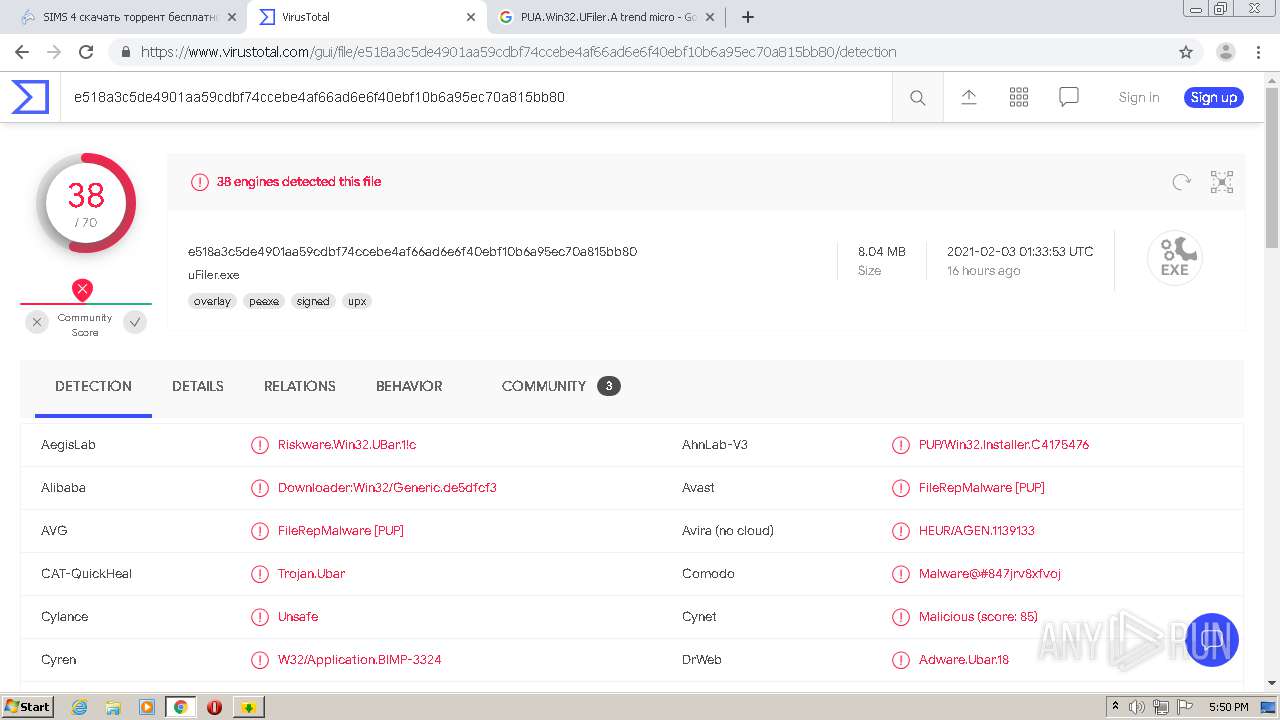
| MD5: | CEB783044B3479E413FA183DDC15A4C2 |
| SHA1: | 783EA9D35A29F0BF7AA1989DCA5526153B1E7ADF |
| SHA256: | DEF61EBB310149BBBBC6B5D8C6236B6ACA0F5BCF6169FD0B54CF518062AF9920 |
| SSDEEP: | 3:N1KKKHeWLX8MGEVXuRKWVIJBKJRKgLRIXQqE/:CKWeMX8weRABWLRqU/ |
MALICIOUS
Application was dropped or rewritten from another process
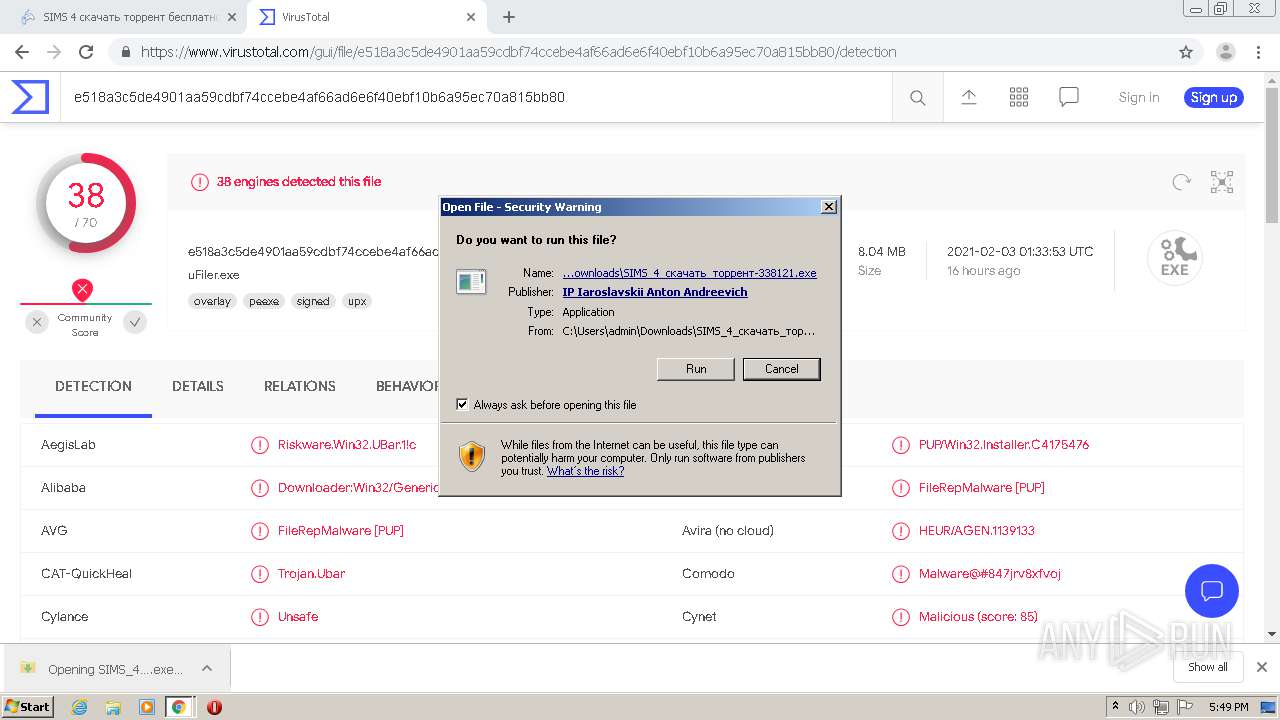
- SIMS_4_скачать_торрент-338121.exe (PID: 3972)
- SIMS_4_скачать_торрент-338121.exe (PID: 3416)
- SIMS_4_скачать_торрент-338121.exe (PID: 3892)
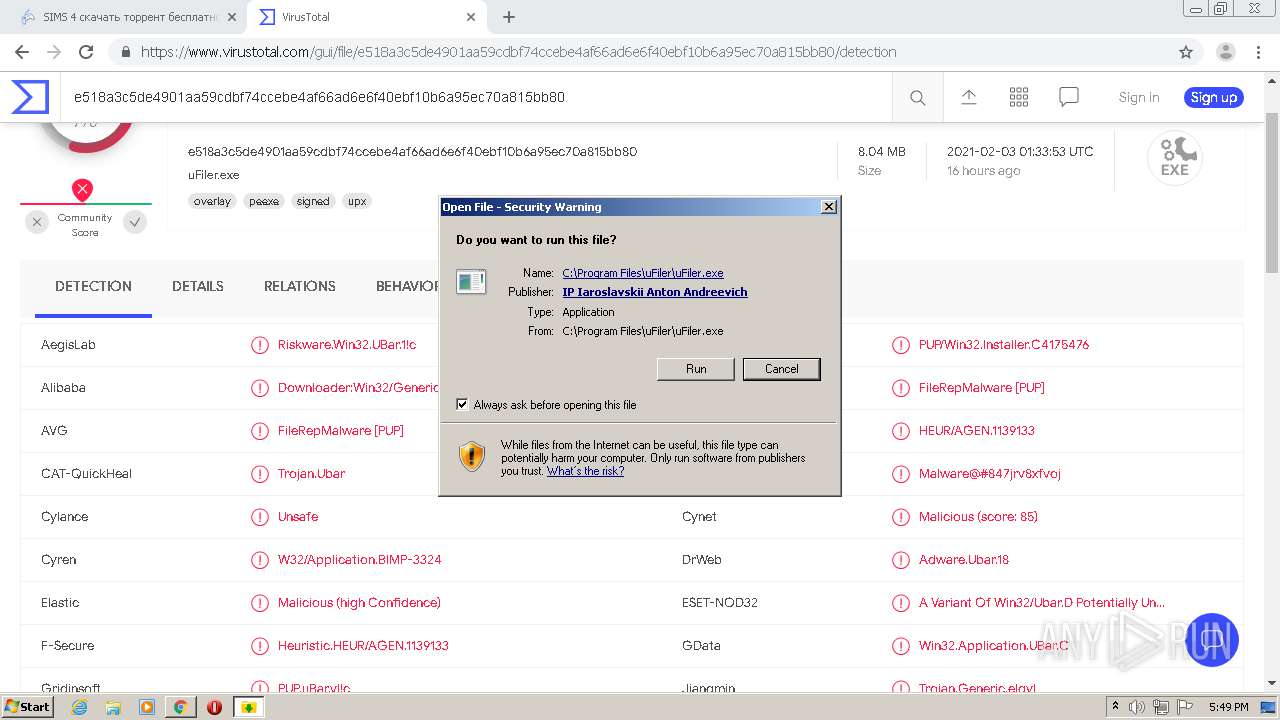
- uFiler.exe (PID: 3772)
- yandex_downloader.exe (PID: 2720)
- avast_free_antivirus_setup_online.exe (PID: 3440)
- YandexPackSetup.exe (PID: 3960)
- yandex_downloader.exe (PID: 2908)
- {021DBF8A-D36A-4466-81F4-3A99643650EF}.exe (PID: 2572)
- seederexe.exe (PID: 4080)
- lite_installer.exe (PID: 3516)
- avast_free_antivirus_setup_online.exe (PID: 3636)
- instup.exe (PID: 3408)
- instup.exe (PID: 3672)
- sbr.exe (PID: 1488)
- Yandex.exe (PID: 3708)
- sender.exe (PID: 1320)
Drops executable file immediately after starts
- SIMS_4_скачать_торрент-338121.exe (PID: 3972)
- MsiExec.exe (PID: 1756)
- Yandex.exe (PID: 3708)
Changes the autorun value in the registry
- SIMS_4_скачать_торрент-338121.exe (PID: 3972)
- instup.exe (PID: 3672)
Loads dropped or rewritten executable
- SIMS_4_скачать_торрент-338121.exe (PID: 3972)
- instup.exe (PID: 3408)
- instup.exe (PID: 3672)
Changes settings of System certificates
- avast_free_antivirus_setup_online.exe (PID: 3440)
- yandex_downloader.exe (PID: 2720)
- avast_free_antivirus_setup_online.exe (PID: 3636)
Steals credentials from Web Browsers
- seederexe.exe (PID: 4080)
Actions looks like stealing of personal data
- lite_installer.exe (PID: 3516)
- seederexe.exe (PID: 4080)
SUSPICIOUS
Creates files in the program directory
- SIMS_4_скачать_торрент-338121.exe (PID: 3972)
- uFiler.exe (PID: 3772)
- avast_free_antivirus_setup_online.exe (PID: 3636)
- instup.exe (PID: 3408)
- instup.exe (PID: 3672)
Application launched itself
- SIMS_4_скачать_торрент-338121.exe (PID: 3416)
- yandex_downloader.exe (PID: 2720)
Creates a directory in Program Files
- SIMS_4_скачать_торрент-338121.exe (PID: 3972)
- instup.exe (PID: 3672)
Executable content was dropped or overwritten
- chrome.exe (PID: 2080)
- SIMS_4_скачать_торрент-338121.exe (PID: 3972)
- uFiler.exe (PID: 3772)
- yandex_downloader.exe (PID: 2720)
- msiexec.exe (PID: 3588)
- MsiExec.exe (PID: 1756)
- lite_installer.exe (PID: 3516)
- avast_free_antivirus_setup_online.exe (PID: 3440)
- avast_free_antivirus_setup_online.exe (PID: 3636)
- instup.exe (PID: 3408)
- Yandex.exe (PID: 3708)
- instup.exe (PID: 3672)
Starts CMD.EXE for commands execution
- SIMS_4_скачать_торрент-338121.exe (PID: 3972)
Changes default file association
- SIMS_4_скачать_торрент-338121.exe (PID: 3972)
Drops a file that was compiled in debug mode
- SIMS_4_скачать_торрент-338121.exe (PID: 3972)
- uFiler.exe (PID: 3772)
- yandex_downloader.exe (PID: 2720)
- msiexec.exe (PID: 3588)
- MsiExec.exe (PID: 1756)
- avast_free_antivirus_setup_online.exe (PID: 3440)
- lite_installer.exe (PID: 3516)
- avast_free_antivirus_setup_online.exe (PID: 3636)
- instup.exe (PID: 3408)
- Yandex.exe (PID: 3708)
- instup.exe (PID: 3672)
Creates a software uninstall entry
- SIMS_4_скачать_торрент-338121.exe (PID: 3416)
- Yandex.exe (PID: 3708)
Starts itself from another location
- SIMS_4_скачать_торрент-338121.exe (PID: 3892)
- instup.exe (PID: 3408)
Low-level read access rights to disk partition
- avast_free_antivirus_setup_online.exe (PID: 3440)
- avast_free_antivirus_setup_online.exe (PID: 3636)
- instup.exe (PID: 3408)
- instup.exe (PID: 3672)
Adds / modifies Windows certificates
- avast_free_antivirus_setup_online.exe (PID: 3440)
- avast_free_antivirus_setup_online.exe (PID: 3636)
Creates files in the Windows directory
- avast_free_antivirus_setup_online.exe (PID: 3440)
- avast_free_antivirus_setup_online.exe (PID: 3636)
- instup.exe (PID: 3408)
- instup.exe (PID: 3672)
Reads Environment values
- MsiExec.exe (PID: 1756)
- instup.exe (PID: 3408)
- instup.exe (PID: 3672)
Creates files in the user directory
- MsiExec.exe (PID: 1756)
- seederexe.exe (PID: 4080)
- Yandex.exe (PID: 3708)
Drops a file with a compile date too recent
- lite_installer.exe (PID: 3516)
Creates or modifies windows services
- instup.exe (PID: 3408)
Removes files from Windows directory
- instup.exe (PID: 3408)
- instup.exe (PID: 3672)
Changes the started page of IE
- seederexe.exe (PID: 4080)
Reads default file associations for system extensions
- Yandex.exe (PID: 3708)
INFO
Application launched itself
- chrome.exe (PID: 2080)
- msiexec.exe (PID: 3588)
- chrome.exe (PID: 2640)
Reads settings of System Certificates
- chrome.exe (PID: 2080)
- {021DBF8A-D36A-4466-81F4-3A99643650EF}.exe (PID: 2572)
- instup.exe (PID: 3408)
- chrome.exe (PID: 4036)
Reads the hosts file
- chrome.exe (PID: 2080)
- chrome.exe (PID: 4036)
- instup.exe (PID: 3408)
- instup.exe (PID: 3672)
Manual execution by user
- {021DBF8A-D36A-4466-81F4-3A99643650EF}.exe (PID: 2572)
Dropped object may contain Bitcoin addresses
- instup.exe (PID: 3672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
102
Monitored processes
56
Malicious processes
15
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,3523806091960015098,9083423500644783406,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4844903575087851069 --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2404 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,3523806091960015098,9083423500644783406,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8492586768432544433 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3576 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1320 | C:\Users\admin\AppData\Local\Temp\2C92BC16-6649-4170-A085-E11F213C94F3\sender.exe --send "/status.xml?clid=2356518-263&uuid=db66ab2d-bb7c-49a7-8d45-ffa5b8429b00&vnt=Windows 7x32&file-no=6%0A10%0A11%0A12%0A13%0A15%0A16%0A17%0A18%0A20%0A21%0A22%0A24%0A25%0A38%0A40%0A42%0A45%0A58%0A61%0A89%0A102%0A103%0A106%0A111%0A121%0A123%0A124%0A125%0A129%0A" | C:\Users\admin\AppData\Local\Temp\2C92BC16-6649-4170-A085-E11F213C94F3\sender.exe | seederexe.exe | ||||||||||||
User: admin Company: Yandex Integrity Level: MEDIUM Description: Yandex Statistics Exit code: 0 Version: 0.0.2.14 Modules
| |||||||||||||||
| 1368 | "C:\Windows\System32\cmd.exe" /с assoc .torrent=SIMS_4_скачать_торрент-338121.torrent | C:\Windows\System32\cmd.exe | — | SIMS_4_скачать_торрент-338121.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1488 | "C:\Windows\Temp\asw.d696da2f1aa0434a\New_140a098a\sbr.exe" 3672 "Avast Antivirus setup" "Avast Antivirus is being installed. Do not shut down your computer!" | C:\Windows\Temp\asw.d696da2f1aa0434a\New_140a098a\sbr.exe | — | instup.exe | |||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: Avast Shutdown blocker Exit code: 0 Version: 20.10.5824.0 Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,3523806091960015098,9083423500644783406,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10073296274979858124 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1628 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1756 | C:\Windows\system32\MsiExec.exe -Embedding 154346CEF886FCB224CFE9A5BADFC151 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1764 | "C:\Windows\System32\cmd.exe" /с ftype SIMS_4_скачать_торрент-338121.ufile="C:\Program Files\uFiler\uFiler.exe""%1" | C:\Windows\System32\cmd.exe | — | SIMS_4_скачать_торрент-338121.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1776 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,3523806091960015098,9083423500644783406,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13026223540315073560 --renderer-client-id=20 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2772 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1840 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1456 --on-initialized-event-handle=316 --parent-handle=320 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
8 854
Read events
4 163
Write events
4 666
Delete events
25
Modification events
| (PID) Process: | (1840) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2080-13256848075686500 |
Value: 259 | |||
| (PID) Process: | (2080) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2080) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2080) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2080) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2080) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2080) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2080) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2080) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2080) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2080-13256848075686500 |
Value: 259 | |||
Executable files
51
Suspicious files
182
Text files
366
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2080 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-601AE1CC-820.pma | — | |
MD5:— | SHA256:— | |||
| 2080 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\03674752-93d7-4b9f-abcf-77d97b1dd16b.tmp | — | |
MD5:— | SHA256:— | |||
| 2080 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2080 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2080 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF12a6e7.TMP | text | |
MD5:— | SHA256:— | |||
| 2080 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
| 2080 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF12a689.TMP | text | |
MD5:— | SHA256:— | |||
| 2080 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF12a6a8.TMP | text | |
MD5:— | SHA256:— | |||
| 2080 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2080 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF12a87d.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
124
TCP/UDP connections
206
DNS requests
127
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4036 | chrome.exe | GET | 301 | 108.177.112.93:80 | http://www.youtube.com/embed/tfi87YVumSM?rel=0&wmode=transparent | US | — | — | whitelisted |
4036 | chrome.exe | GET | 301 | 108.177.112.93:80 | http://www.youtube.com/embed/-8BU5D8auLw?rel=0&wmode=transparent | US | — | — | whitelisted |
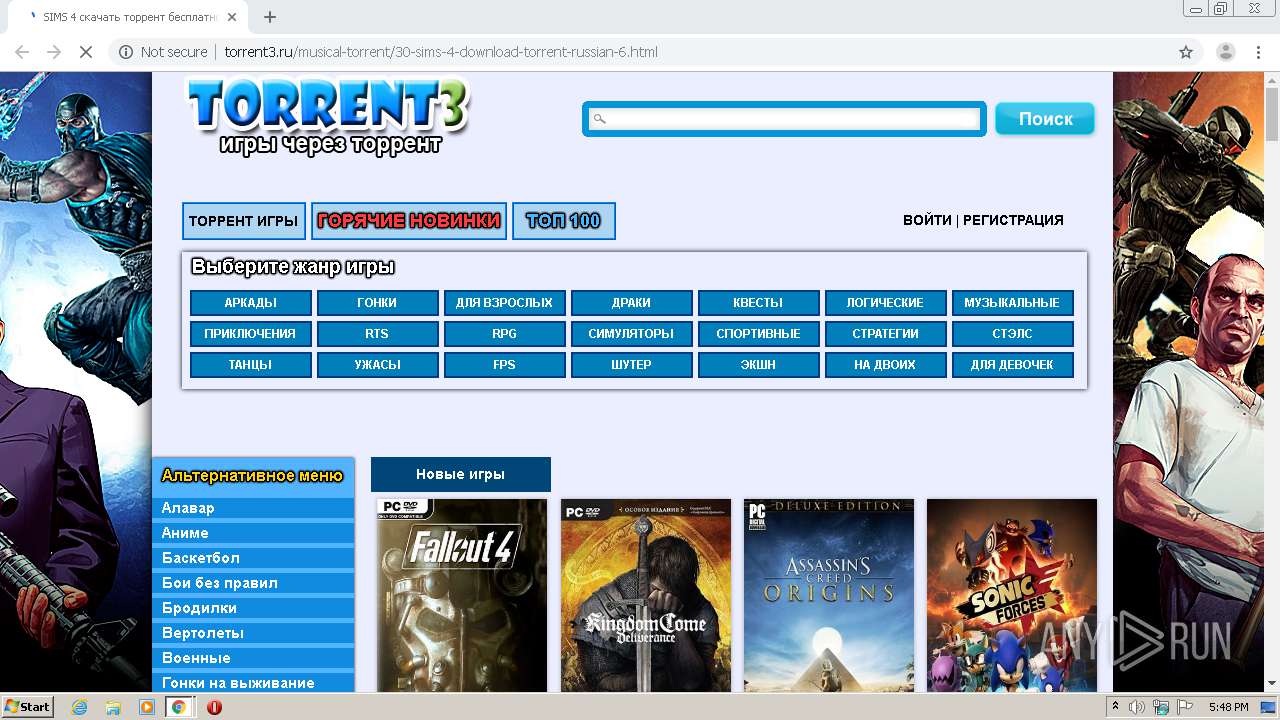
4036 | chrome.exe | GET | 200 | 37.1.204.244:80 | http://torrent3.ru/musical-torrent/30-sims-4-download-torrent-russian-6.html | NL | html | 16.0 Kb | whitelisted |
4036 | chrome.exe | GET | 200 | 37.1.204.244:80 | http://torrent3.ru/engine/classes/min/index.php?f=/templates/torrent3/css/all.css,/templates/torrent3/css/engine.css | NL | text | 9.72 Kb | whitelisted |
4036 | chrome.exe | GET | 200 | 37.1.204.244:80 | http://torrent3.ru/templates/torrent3/images/dlet_bttn_login.gif | NL | image | 541 b | whitelisted |
4036 | chrome.exe | GET | 200 | 37.1.204.244:80 | http://torrent3.ru/uploads/posts/2018-04/1522925705_kingdom-come-deliverance.jpg | NL | image | 33.5 Kb | whitelisted |
4036 | chrome.exe | GET | 200 | 37.1.204.244:80 | http://torrent3.ru/uploads/posts/2017-10/1509463987_assassins-creed-origins.jpg | NL | image | 25.5 Kb | whitelisted |
4036 | chrome.exe | GET | 200 | 37.1.204.244:80 | http://torrent3.ru/uploads/posts/2015-11/1447104514_2777647-l.jpg | NL | image | 36.0 Kb | whitelisted |
4036 | chrome.exe | GET | 200 | 37.1.204.244:80 | http://torrent3.ru/uploads/posts/2015-08/thumbs/1439469090_sims-4-1.jpg | NL | image | 9.27 Kb | whitelisted |
4036 | chrome.exe | GET | 200 | 37.1.204.244:80 | http://torrent3.ru/uploads/posts/2014-09/1409901756_xsk90l020slup2w3ear2z1wjz.png | NL | image | 294 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4036 | chrome.exe | 37.1.204.244:80 | torrent3.ru | Serverius Holding B.V. | NL | suspicious |
4036 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
4036 | chrome.exe | 108.177.112.93:80 | www.youtube.com | Google Inc. | US | unknown |
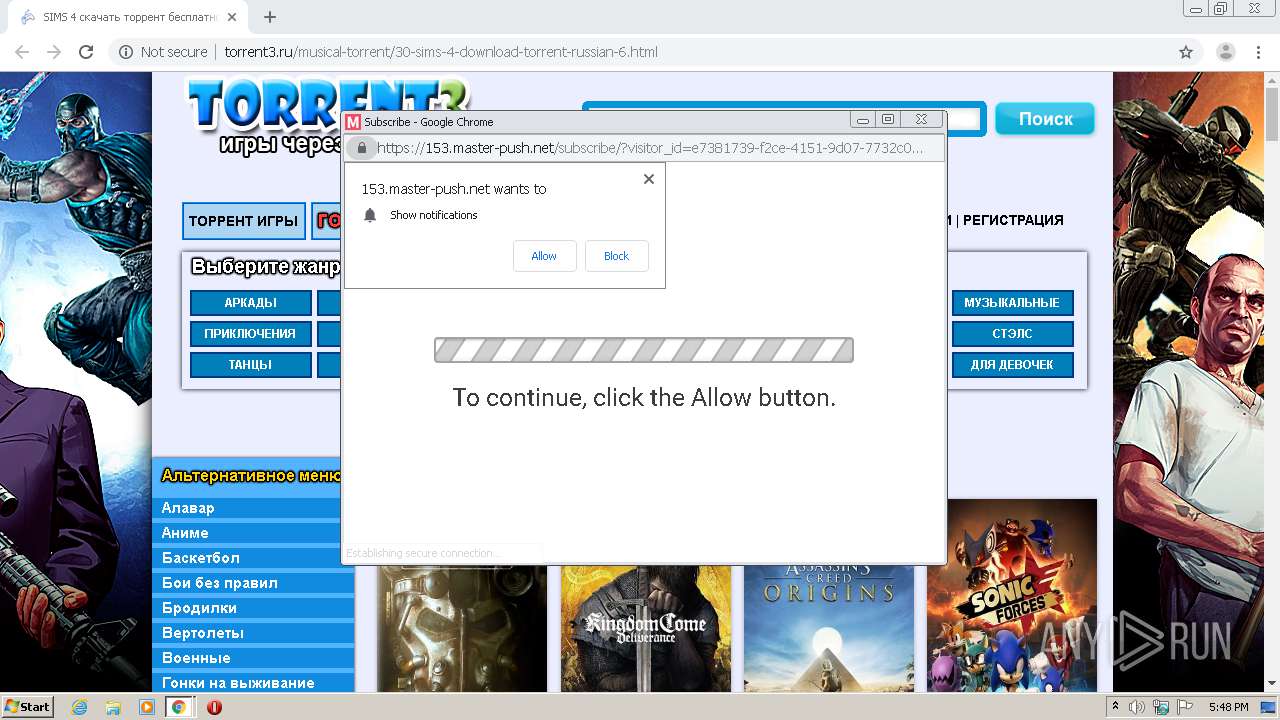
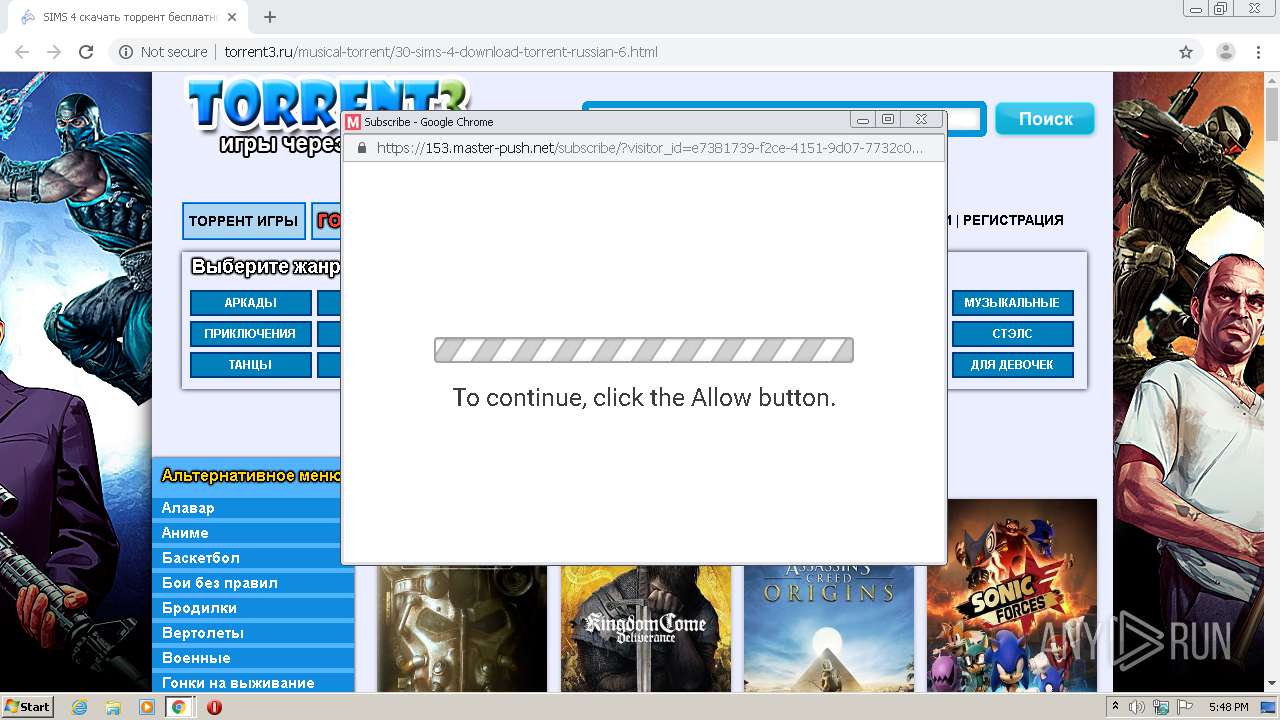
4036 | chrome.exe | 88.208.46.53:443 | master-push.net | DataWeb Global Group B.V. | NL | unknown |
4036 | chrome.exe | 31.220.27.134:80 | uuidksinc.net | — | NL | suspicious |
4036 | chrome.exe | 142.250.74.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
4036 | chrome.exe | 88.208.46.33:443 | master-push.net | DataWeb Global Group B.V. | NL | unknown |
4036 | chrome.exe | 142.250.186.130:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
4036 | chrome.exe | 172.217.23.134:443 | static.doubleclick.net | Google Inc. | US | whitelisted |
4036 | chrome.exe | 172.217.16.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
torrent3.ru |
| whitelisted |
accounts.google.com |
| shared |
www.youtube.com |
| whitelisted |
sub2.bubblesmedia.ru |
| unknown |
ufiler-pro.ru |
| malicious |
counter.yadro.ru |
| whitelisted |
master-push.net |
| whitelisted |
clients1.google.com |
| whitelisted |
www.liveinternet.ru |
| whitelisted |
uuidksinc.net |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
3772 | uFiler.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.cloud Domain |
3772 | uFiler.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.cloud Domain |
3772 | uFiler.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.cloud Domain |
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
3772 | uFiler.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.cloud Domain |
3772 | uFiler.exe | Potential Corporate Privacy Violation | ET P2P possible torrent download |
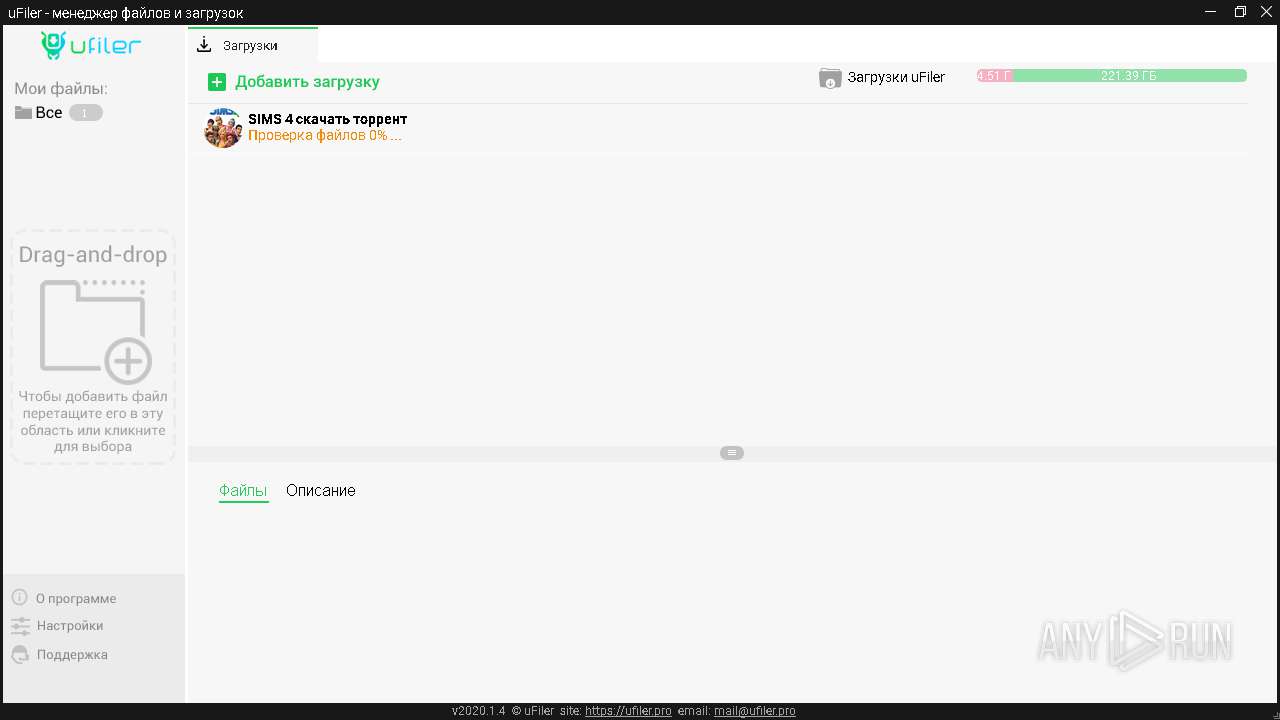
3772 | uFiler.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent - Torrent File Downloaded |
3772 | uFiler.exe | Potential Corporate Privacy Violation | ET P2P possible torrent download |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
YandexPackSetup.exe | IsAlreadyRun() In
|
YandexPackSetup.exe | IsAlreadyRun() Out : ret (BOOL) = 0
|
YandexPackSetup.exe | IsMSISrvFree() In |
YandexPackSetup.exe | IsMSISrvFree() : OpenMutex() err ret = 2
|
YandexPackSetup.exe | IsMSISrvFree() Out ret = 1
|
YandexPackSetup.exe | GetLoggedCreds_WTSSessionInfo(): szUserName = admin, szDomain = USER-PC, dwSessionId = 1
|
YandexPackSetup.exe | GetSidFromEnumSess(): LsaGetLogonSessionData(0) err = 5
|
YandexPackSetup.exe | GetSidFromEnumSess(): ProfileImagePath(1) = C:\Users\admin
|
YandexPackSetup.exe | GetSidFromEnumSess(): LsaEnumerateLogonSessions() lpszSid = S-1-5-21-1302019708-1500728564-335382590-1000
|
YandexPackSetup.exe | GetLoggedCreds_WTSSessionInfo(): szUserName = admin, szDomain = USER-PC, dwSessionId = 1
|