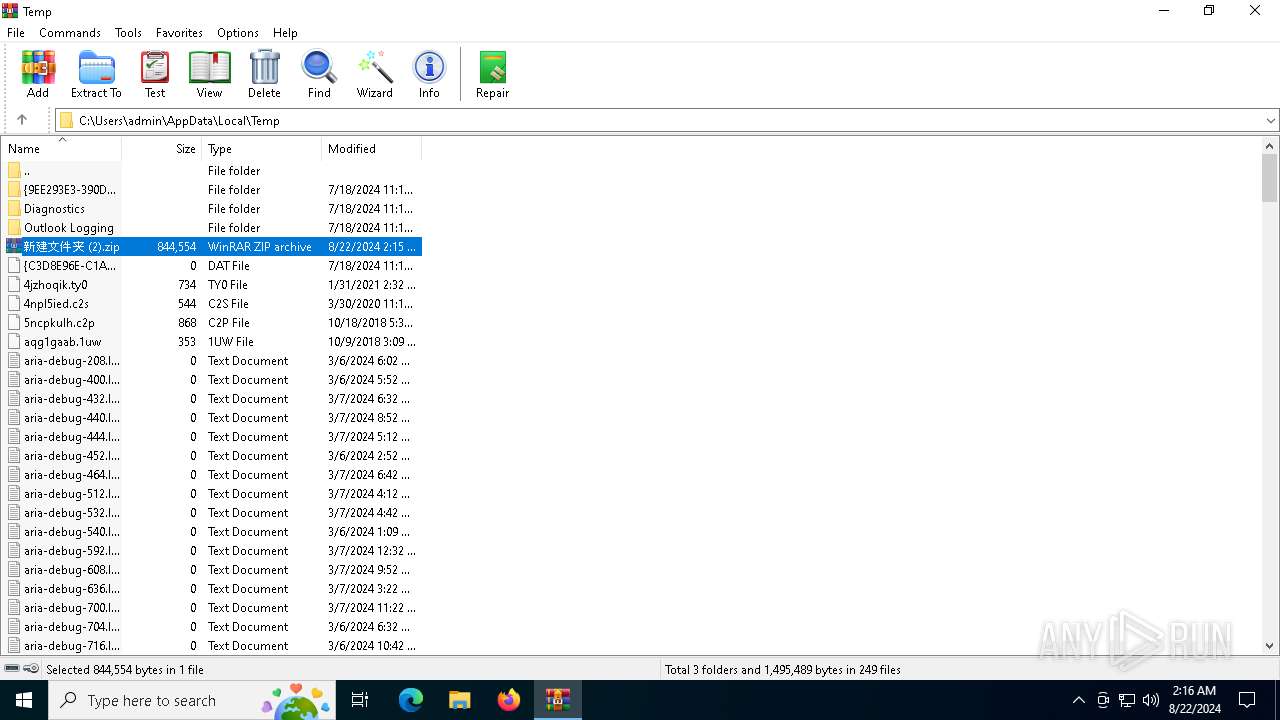
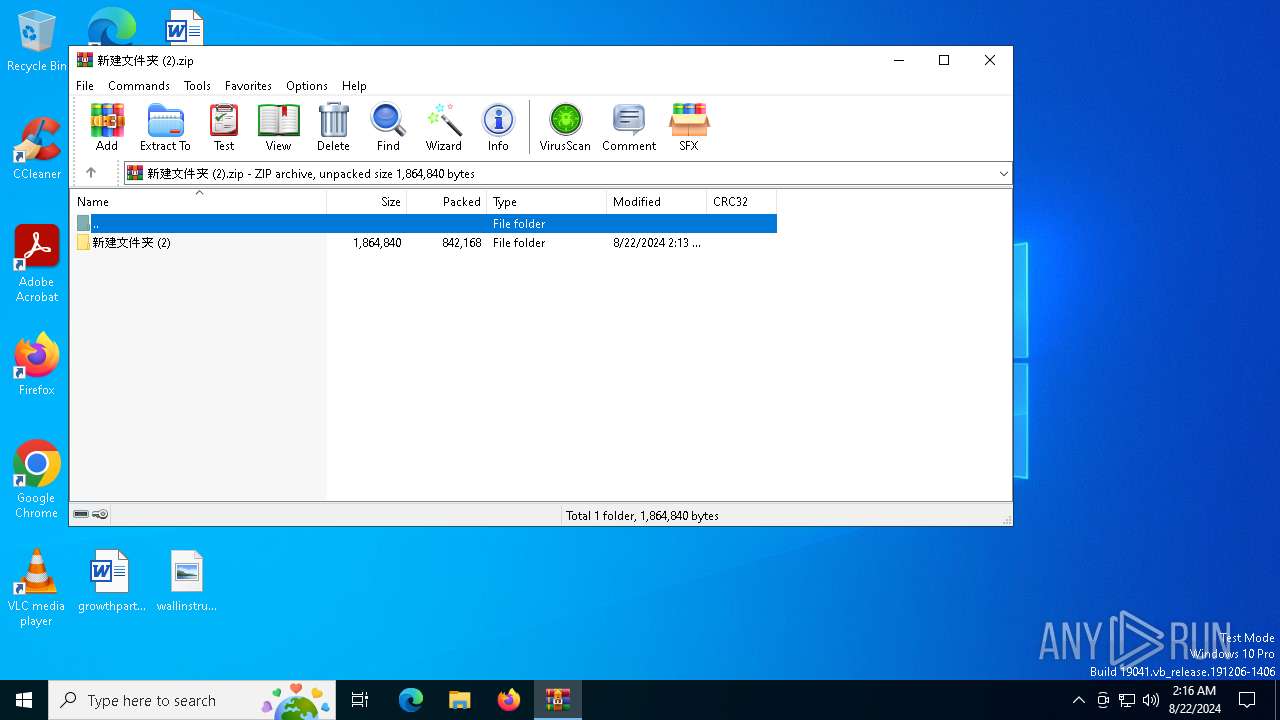
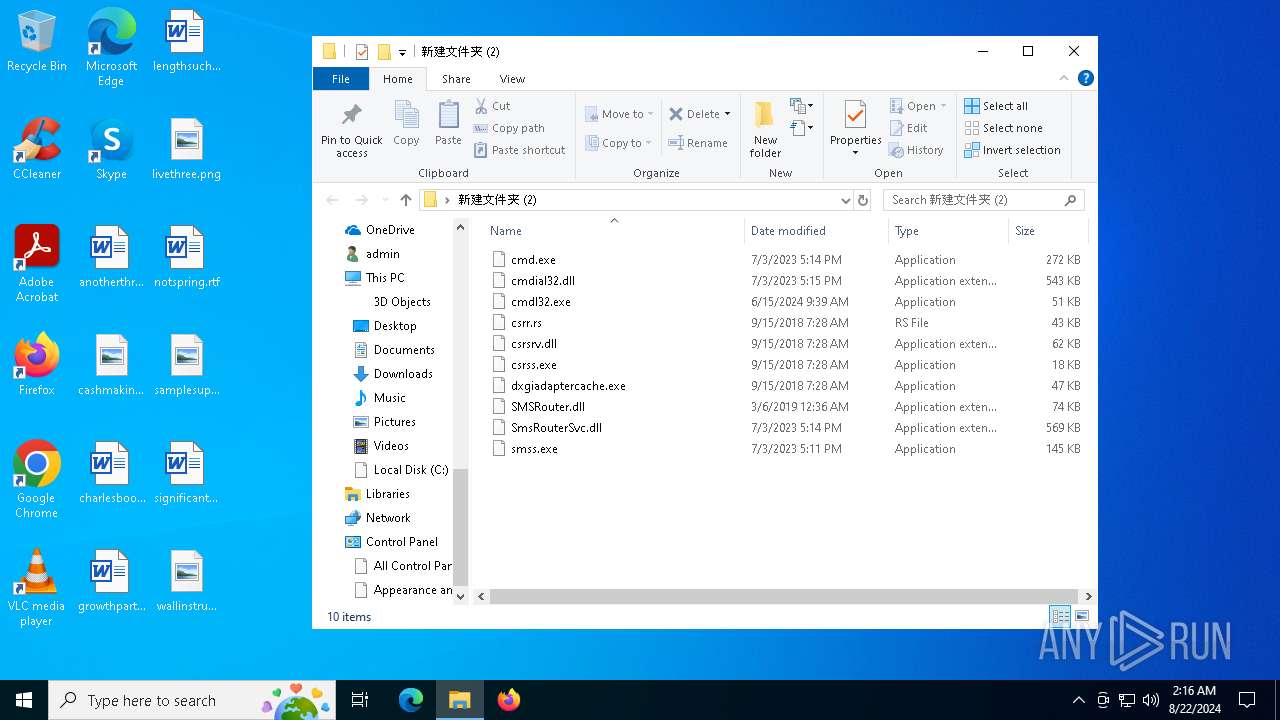
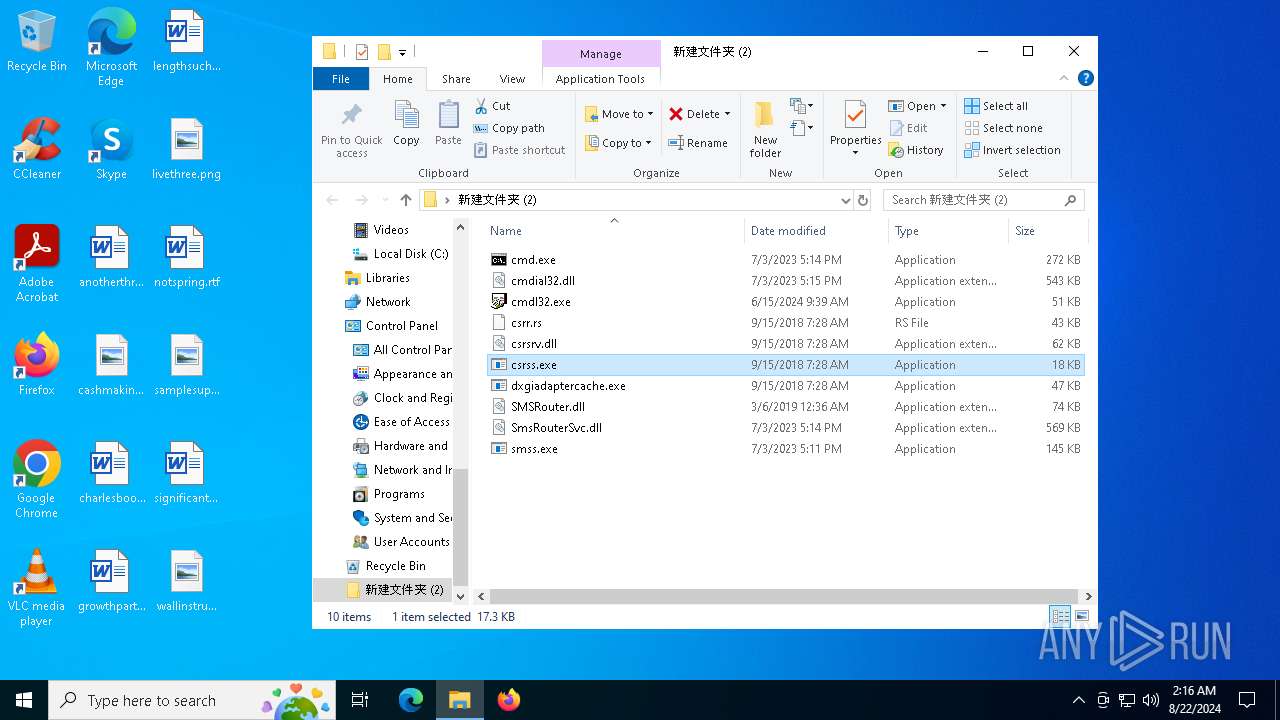
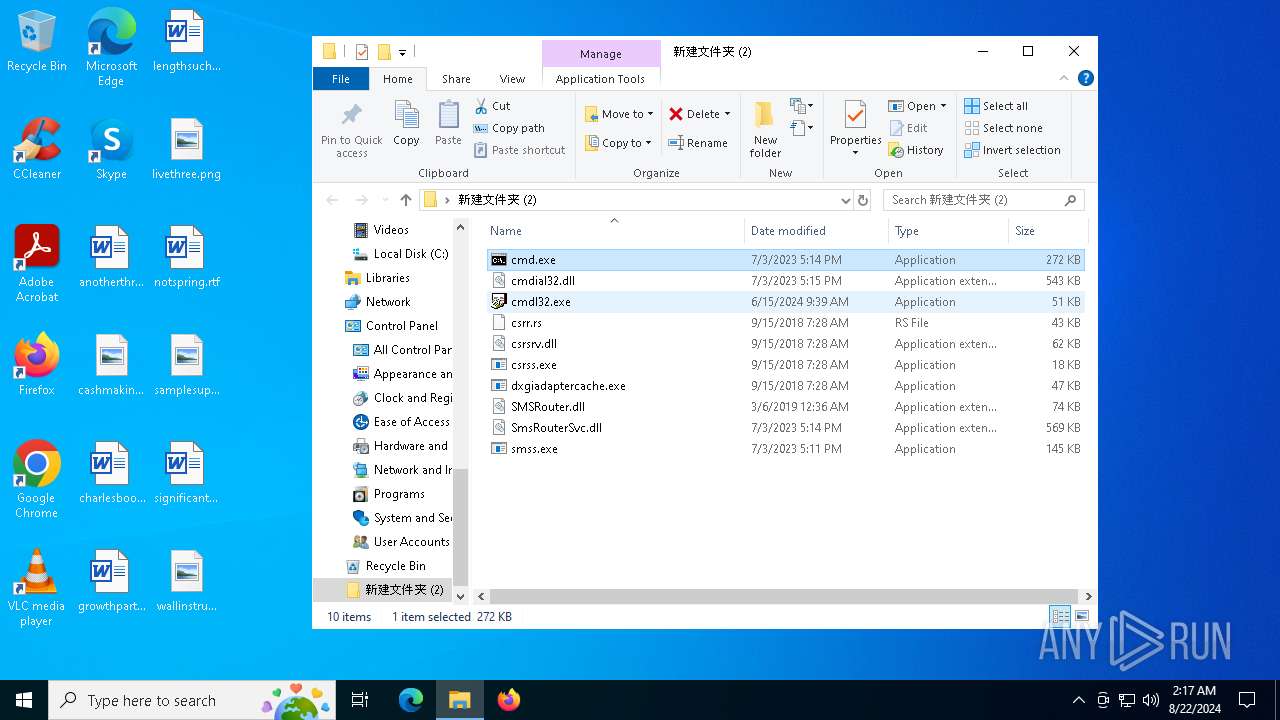
| File name: | 新建文件夹 (2).zip |
| Full analysis: | https://app.any.run/tasks/ecb19765-1e9d-40a8-8491-fad51ecbebb1 |
| Verdict: | Malicious activity |
| Analysis date: | August 22, 2024, 02:15:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | FB825E11BA174697A42B361C2E732468 |
| SHA1: | 295EBE78188C6ABA2C4D19F9B91EC2BD0A5703FC |
| SHA256: | DEF4BEF4426F36D14104233C2B0848259C14C952E010C0456E9B5A8DBC0D82A8 |
| SSDEEP: | 24576:U6S421YTTrnC0k4VcbUK0xUtmDgPM2rmNv0Og1uCFx2ZqJ+CEEpFZg6MkD/5pnAp:UTPYTTrnC0k42bUK0xUtmDgPM2rmNv04 |
MALICIOUS
No malicious indicators.SUSPICIOUS
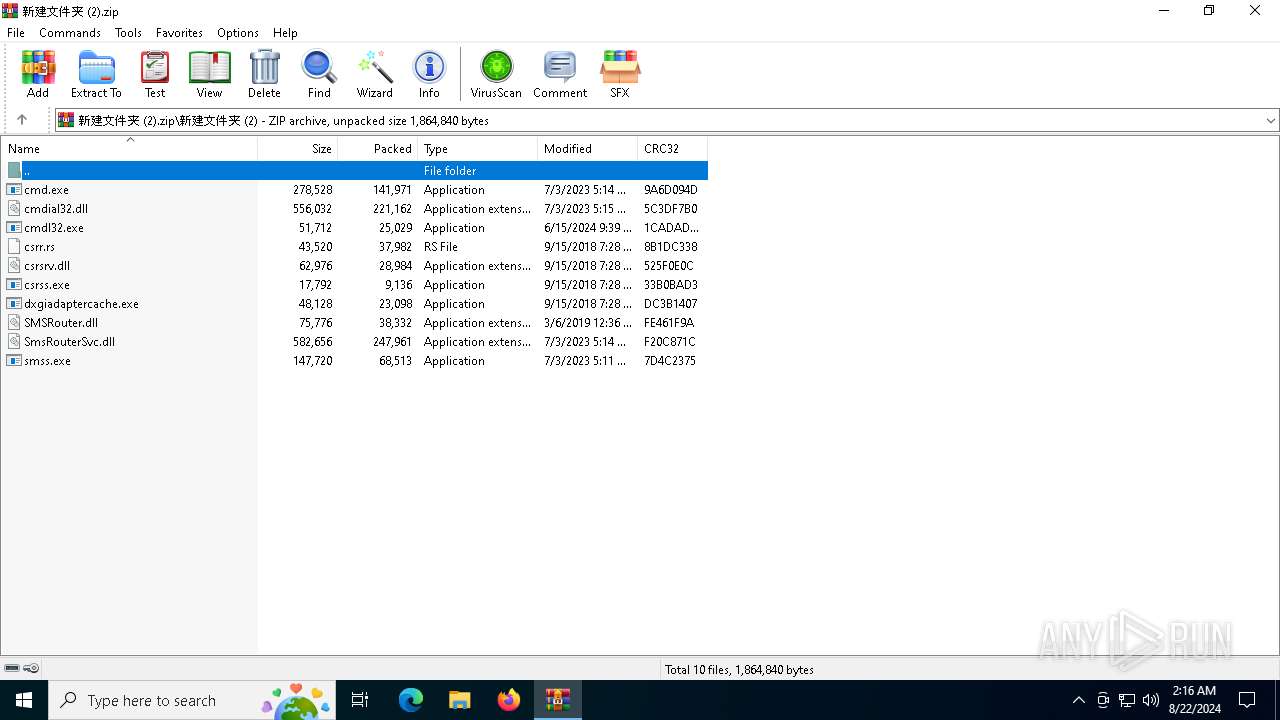
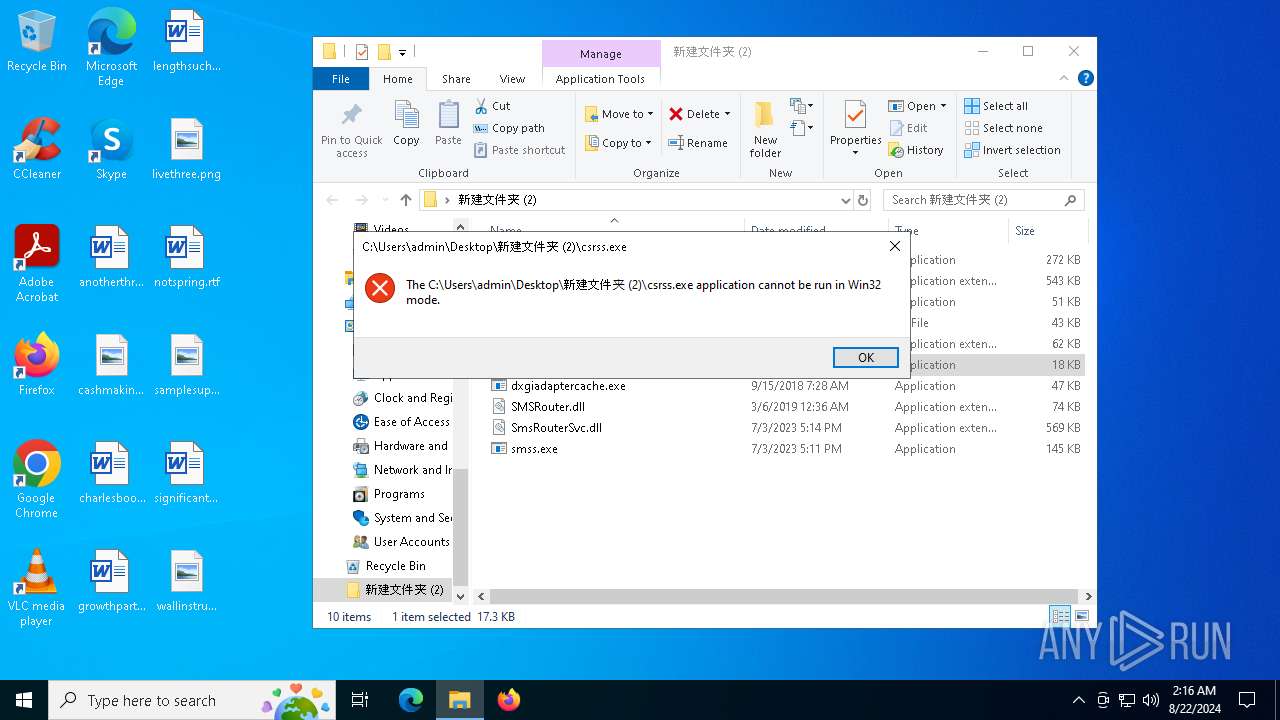
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6556)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6556)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6556)
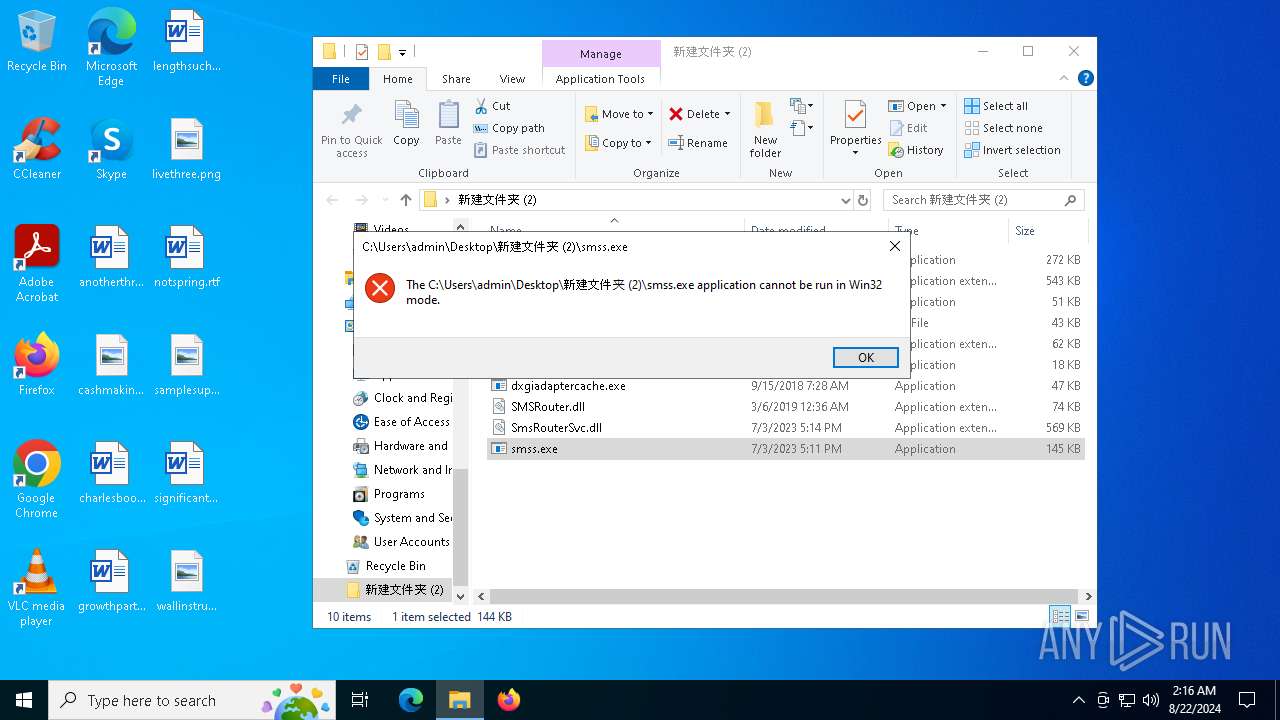
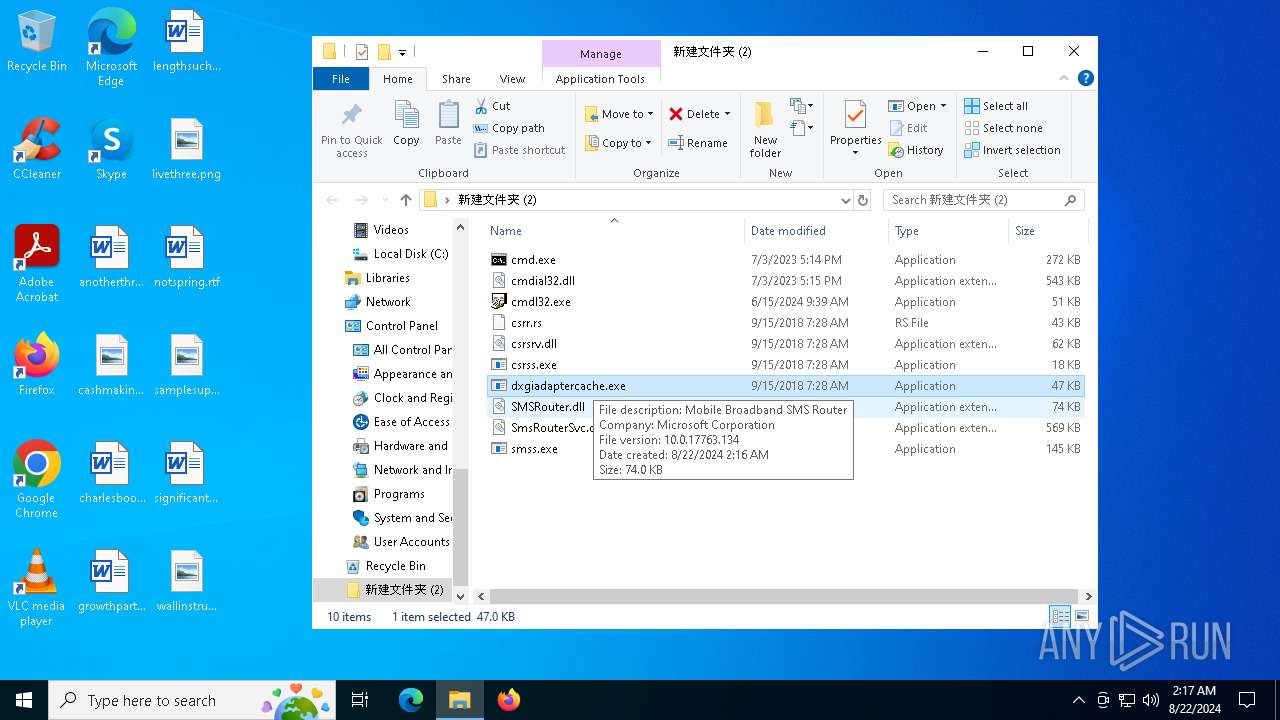
Starts a Microsoft application from unusual location
- dxgiadaptercache.exe (PID: 6280)
- smss.exe (PID: 6212)
- csrss.exe (PID: 6264)
- cmd.exe (PID: 6848)
- dxgiadaptercache.exe (PID: 6976)
INFO
Manual execution by a user
- csrss.exe (PID: 6264)
- dxgiadaptercache.exe (PID: 6280)
- smss.exe (PID: 6212)
- cmd.exe (PID: 6848)
- dxgiadaptercache.exe (PID: 6976)
Checks supported languages
- dxgiadaptercache.exe (PID: 6280)
- cmd.exe (PID: 6848)
- dxgiadaptercache.exe (PID: 6976)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2024:08:22 10:13:26 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | 新建文件夹 (2)/ |
Total processes
144
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2384 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6212 | "C:\Users\admin\Desktop\新建文件夹 (2)\smss.exe" | C:\Users\admin\Desktop\新建文件夹 (2)\smss.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Session Manager Exit code: 0 Version: 10.0.17763.1911 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6264 | "C:\Users\admin\Desktop\新建文件夹 (2)\csrss.exe" | C:\Users\admin\Desktop\新建文件夹 (2)\csrss.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Client Server Runtime Process Exit code: 0 Version: 10.0.17763.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6280 | "C:\Users\admin\Desktop\新建文件夹 (2)\dxgiadaptercache.exe" | C:\Users\admin\Desktop\新建文件夹 (2)\dxgiadaptercache.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DXGI Adapter Cache Exit code: 2147942405 Version: 10.0.17763.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6556 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\新建文件夹 (2).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6848 | "C:\Users\admin\Desktop\新建文件夹 (2)\cmd.exe" | C:\Users\admin\Desktop\新建文件夹 (2)\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.17763.1697 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6976 | "C:\Users\admin\Desktop\新建文件夹 (2)\dxgiadaptercache.exe" | C:\Users\admin\Desktop\新建文件夹 (2)\dxgiadaptercache.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DXGI Adapter Cache Exit code: 2147942405 Version: 10.0.17763.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 092
Read events
11 062
Write events
30
Delete events
0
Modification events
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\新建文件夹 (2).zip | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
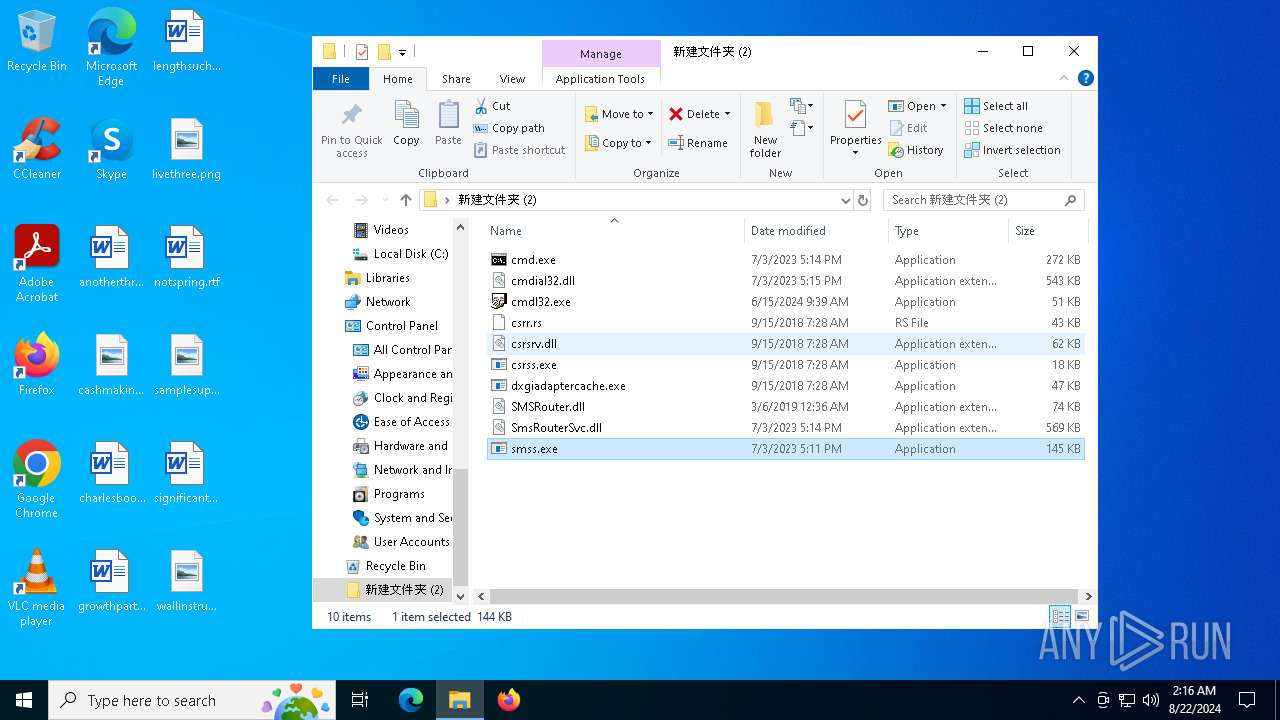
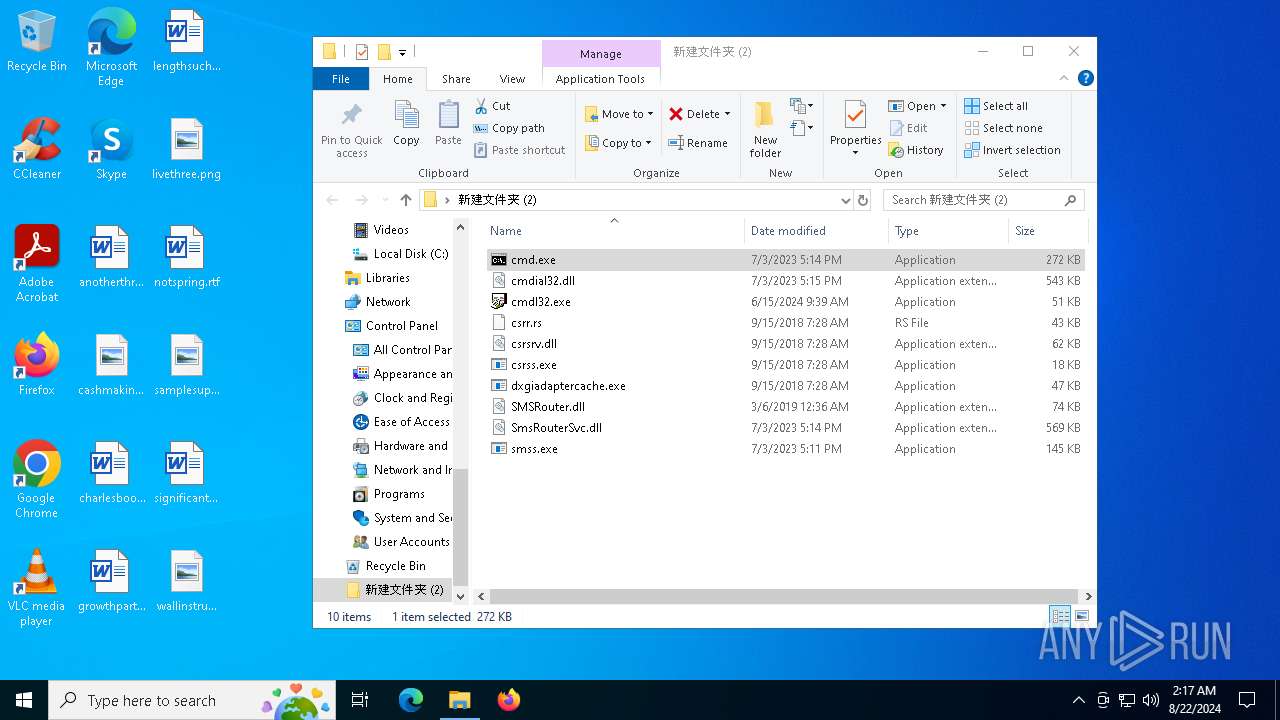
Executable files
10
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.28885\新建文件夹 (2)\cmdial32.dll | executable | |
MD5:199C06DDBAD82C3F90F3211A24B3BE4C | SHA256:E6404240CBB8640160ACA56D4362369523AC7A4437FA7DB5CB499C2A89B5992D | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.28885\新建文件夹 (2)\SMSRouter.dll | executable | |
MD5:B145D0B0CF2DB0707C316A0C7ACC9D94 | SHA256:5D97BBE785183FEDDF1A5D166B8C8C86E8C86A408F93DAD86F3E7AC2DB8FAEC2 | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.28885\新建文件夹 (2)\cmdl32.exe | executable | |
MD5:0C3DEAA35C81BA14B2AF07B5D376F3A7 | SHA256:CF47E27D2BE05D9AD97B609B88E31B80492090A125EC787E22A505A4E19F4030 | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.28885\新建文件夹 (2)\dxgiadaptercache.exe | executable | |
MD5:CEA17E28EFF3B2EED6B49B5DDCC7327F | SHA256:BA598EFD9D9C4449DEAC83F78CEC893AA127F31767902D6DD69A157B65450240 | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.28885\新建文件夹 (2)\csrss.exe | executable | |
MD5:7D64128BC1EECE41196858897596EBC8 | SHA256:FB40ED0FFA6BC795923A941DAB6B7D6B43583D0F152A6DF4D8953D2C1A0CB417 | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.28885\新建文件夹 (2)\SmsRouterSvc.dll | executable | |
MD5:44824A7022A219DFAB068BDDA4DC755C | SHA256:07B752D096D7DC78B55001E00E5723951B56364AABF1C5B95805E57374DEF578 | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.28885\新建文件夹 (2)\smss.exe | executable | |
MD5:D509E4899A815B97E7E118D8BA56C2DB | SHA256:FAC9407ADDEE9DEB1D07CAE8F11E13CB5F4B99CFD87894A52747524C212E1C28 | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.28885\新建文件夹 (2)\csrr.rs | executable | |
MD5:A50FC35BAC7C2E755A7F434E603125BB | SHA256:FE40D5000C08DF820360CDD399983AA828588585B167AB42F6719257EB2A9585 | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.28885\新建文件夹 (2)\csrsrv.dll | executable | |
MD5:D5AE22FDFB0549BCA4676F171D1972F1 | SHA256:4F315302DBA388E4C4643F09F12333C7DAEB9BCE64DCFCBABF4D57E2643D90E1 | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6556.28885\新建文件夹 (2)\cmd.exe | executable | |
MD5:911D039E71583A07320B32BDE22F8E22 | SHA256:BC866CFCDDA37E24DC2634DC282C7A0E6F55209DA17A8FA105B07414C0E7C527 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
34
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5372 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6952 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1920 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2468 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3916 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3840 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3916 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5372 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5372 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |