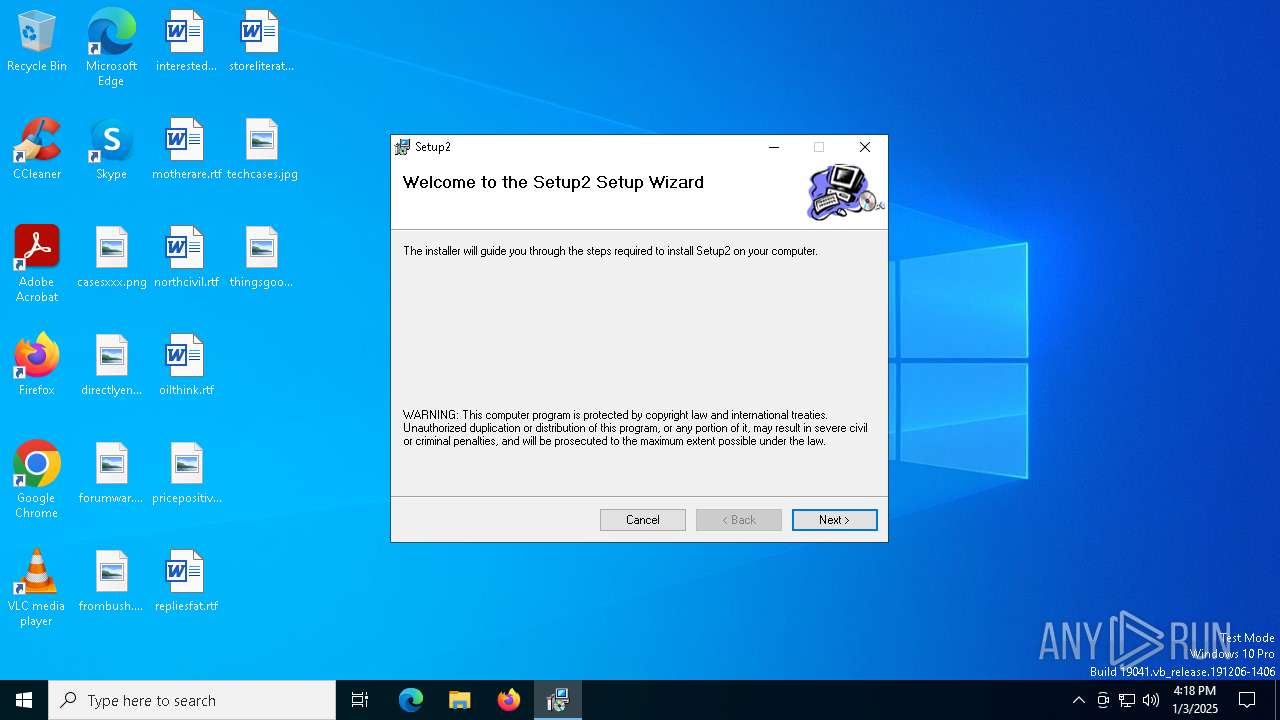
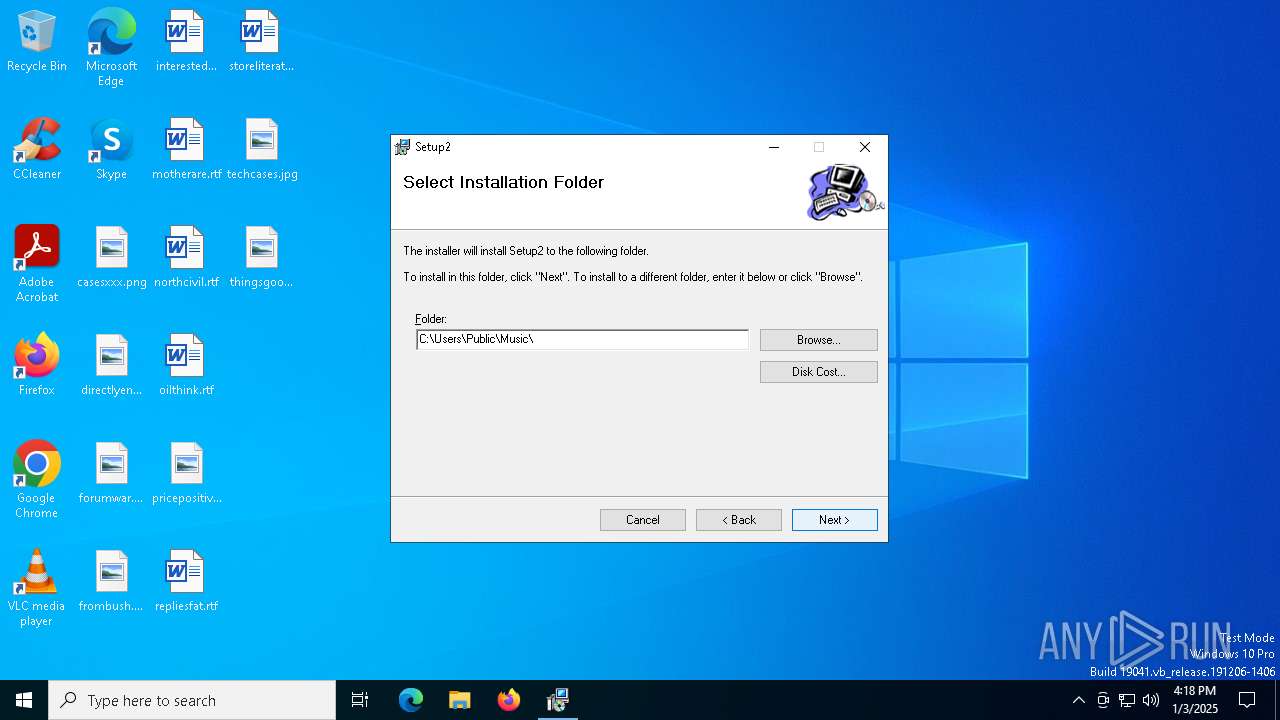
| File name: | deef940da19f6baca00002f28ee02998269ac036b0d277132402cd4bb086f093.msi |
| Full analysis: | https://app.any.run/tasks/1796606c-b13e-40d8-adaf-690038e20d1d |
| Verdict: | Malicious activity |
| Analysis date: | January 03, 2025, 16:18:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Create Time/Date: Mon Jun 21 07:00:00 1999, Name of Creating Application: Windows Installer, Code page: 1252, Last Printed: Mon Jun 3 18:16:22 2024, Title: Setup2, Author: Microsoft, Template: Intel;1033, Last Saved By: Asterix, Revision Number: {346216D6-FC2D-4B10-AF3A-E3FFCBE2B3C3}, Last Saved Time/Date: Mon Jun 3 18:17:41 2024, Number of Pages: 200, Number of Words: 10, Security: 0 |
| MD5: | 47F1B324EAB7E1DA2CA116F62B7C2D05 |
| SHA1: | 1D35C95616D2D9187B735B039DB7D4D71FF7DAF2 |
| SHA256: | DEEF940DA19F6BACA00002F28EE02998269AC036B0D277132402CD4BB086F093 |
| SSDEEP: | 98304:qBvwwznn8+aM3rmFEqPqzeRFf0CZbuk8GO9AoJqDgOo0n7IgtuVw9UdHGdhe95Z6:A+EwtS3V2ty+E |
MALICIOUS
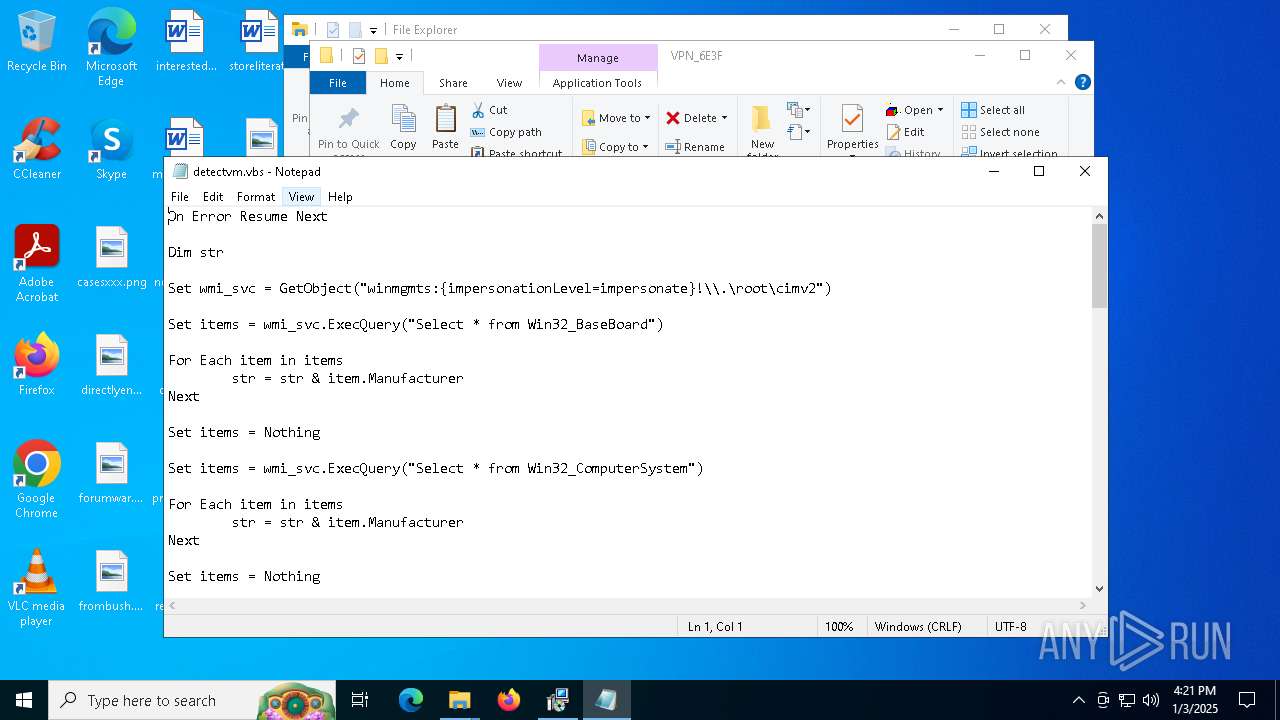
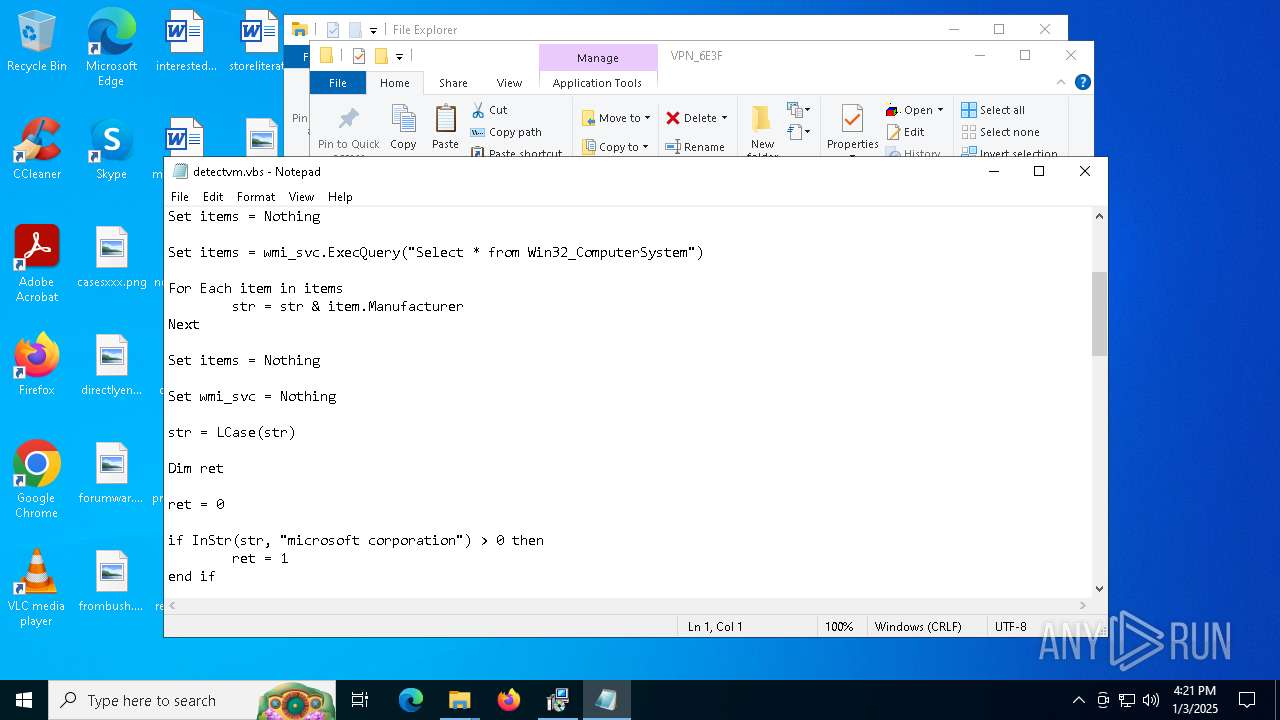
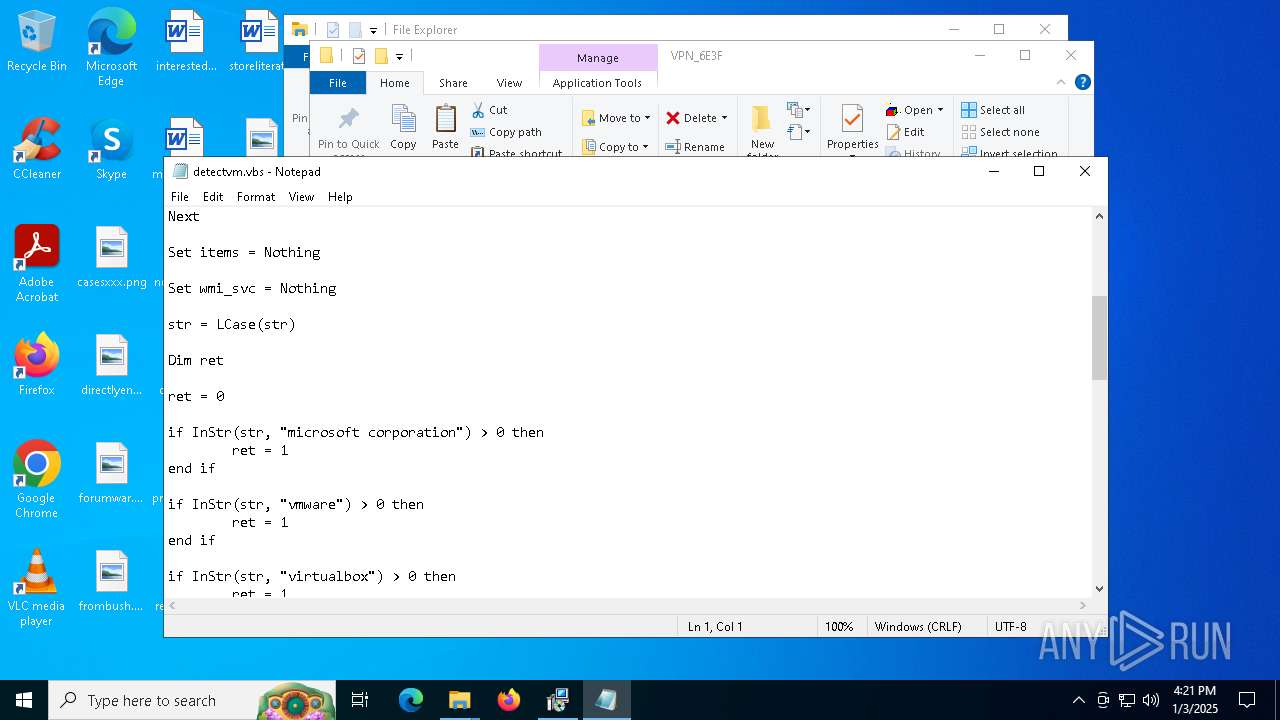
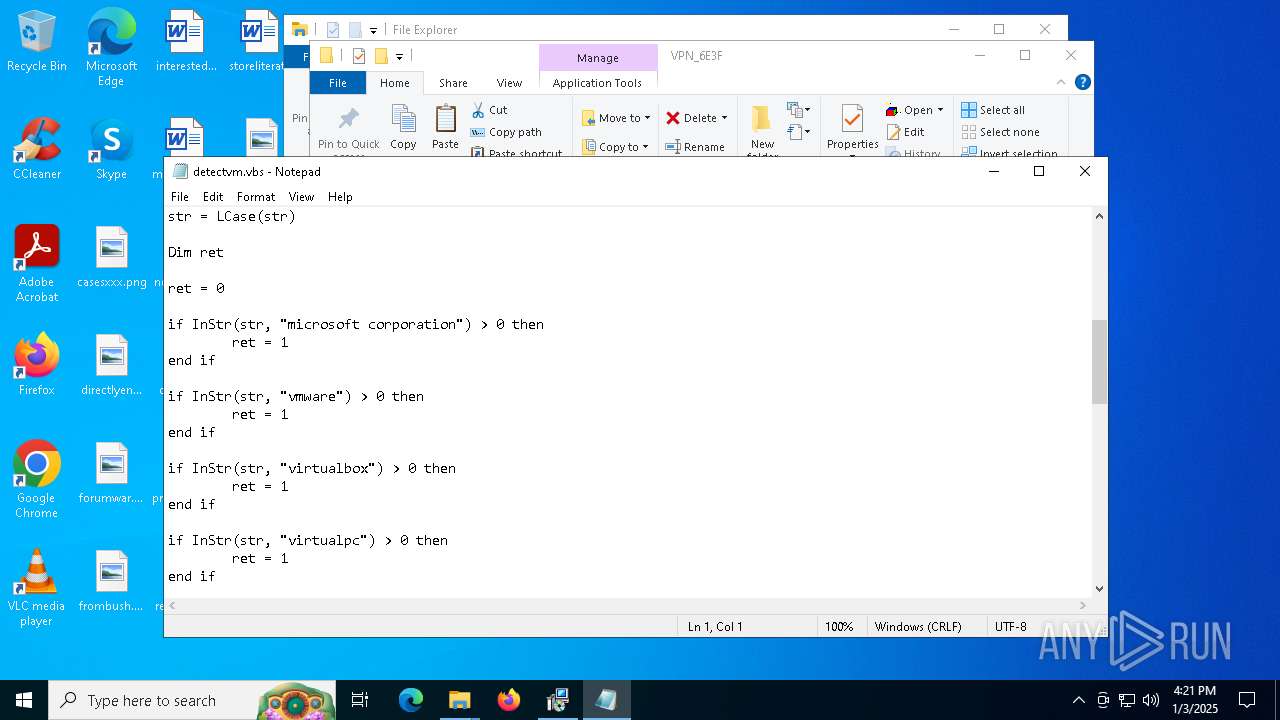
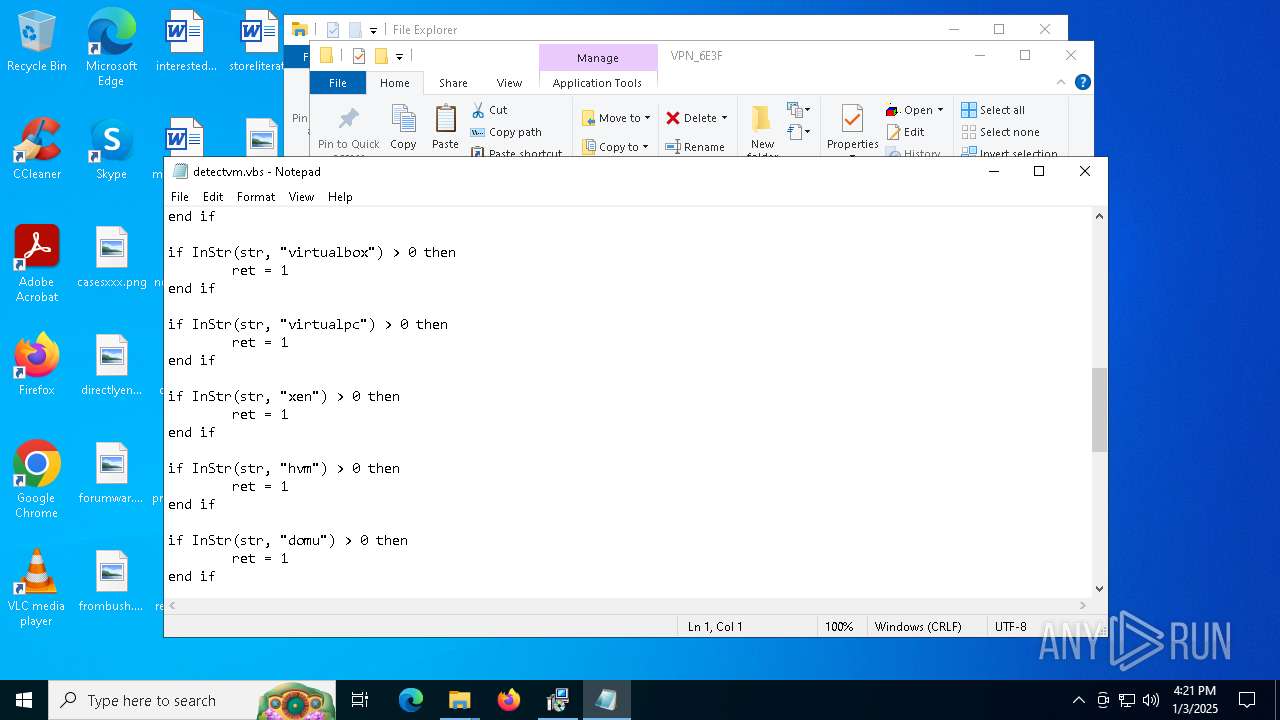
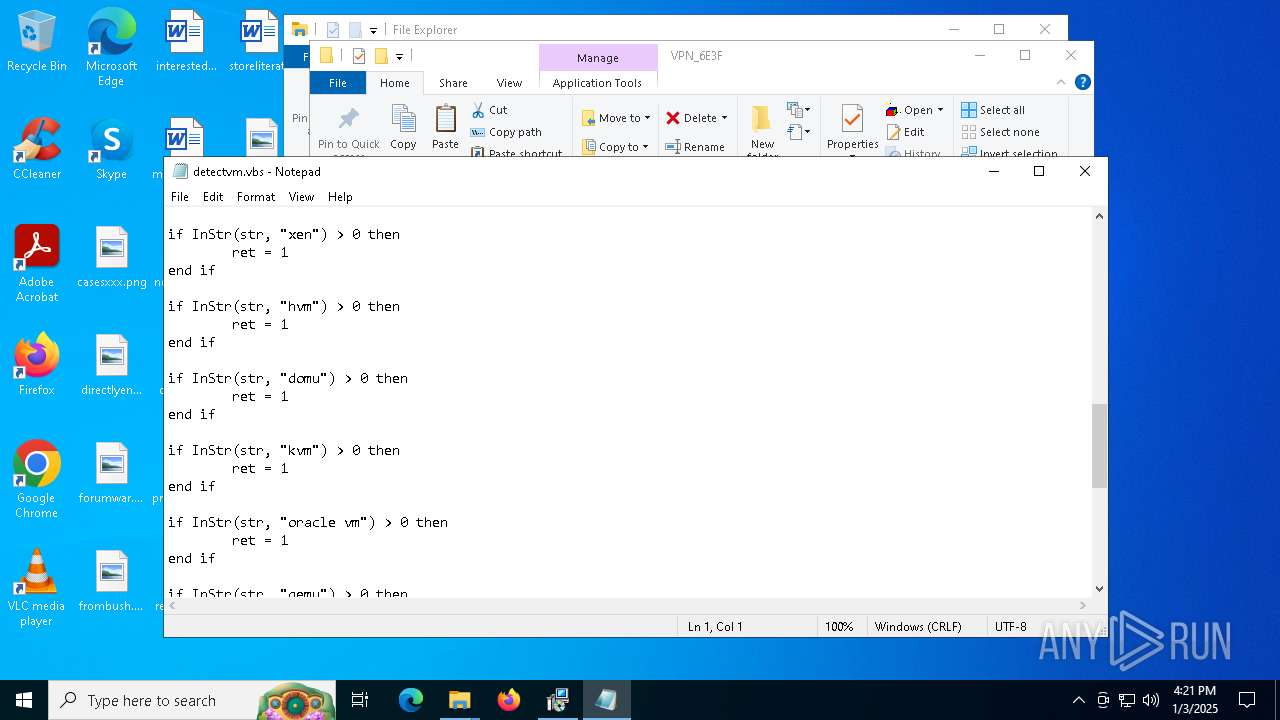
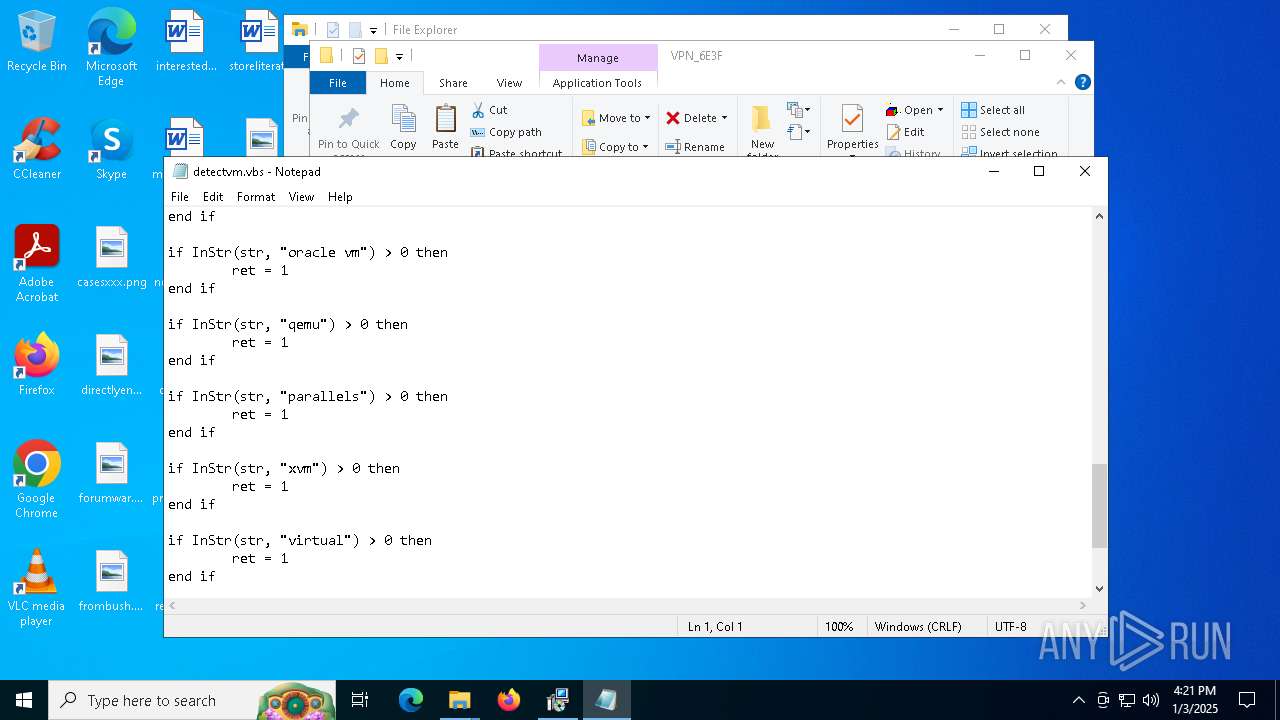
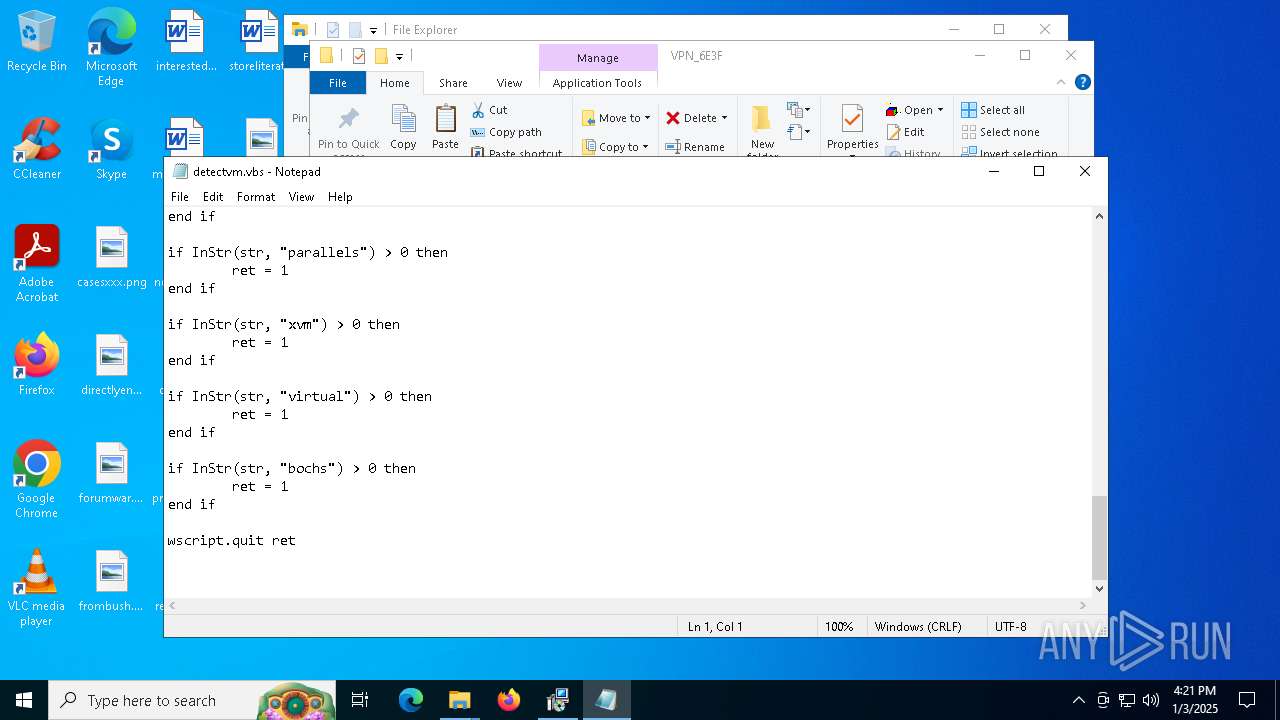
Accesses name of a computer manufacturer via WMI (SCRIPT)
- cscript.exe (PID: 4388)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6920)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6368)
Process drops legitimate windows executable
- msiexec.exe (PID: 6368)
- nwsvc.exe (PID: 1156)
The process creates files with name similar to system file names
- msiexec.exe (PID: 6368)
Starts a Microsoft application from unusual location
- nwsvc.exe (PID: 1156)
Likely accesses (executes) a file from the Public directory
- nwsvc.exe (PID: 1156)
Executable content was dropped or overwritten
- nwsvc.exe (PID: 1156)
The process executes VB scripts
- nwsvc.exe (PID: 1156)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 4388)
There is functionality for enable RDP (YARA)
- nwsvc.exe (PID: 1156)
INFO
Manages system restore points
- SrTasks.exe (PID: 6424)
Checks supported languages
- SearchApp.exe (PID: 5064)
- msiexec.exe (PID: 6368)
- nwsvc.exe (PID: 1156)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6368)
The sample compiled with english language support
- msiexec.exe (PID: 6368)
- nwsvc.exe (PID: 1156)
Reads the computer name
- nwsvc.exe (PID: 1156)
Reads the machine GUID from the registry
- nwsvc.exe (PID: 1156)
- SearchApp.exe (PID: 5064)
Reads Environment values
- nwsvc.exe (PID: 1156)
Reads security settings of Internet Explorer
- cscript.exe (PID: 4388)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
Manual execution by a user
- notepad.exe (PID: 396)
- notepad.exe (PID: 5340)
Reads the software policy settings
- SearchApp.exe (PID: 5064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| CodePage: | Windows Latin 1 (Western European) |
| LastPrinted: | 2024:06:03 18:16:22 |
| Title: | Setup2 |
| Subject: | - |
| Author: | Microsoft |
| Keywords: | - |
| Comments: | - |
| Template: | Intel;1033 |
| LastModifiedBy: | Asterix |
| RevisionNumber: | {346216D6-FC2D-4B10-AF3A-E3FFCBE2B3C3} |
| ModifyDate: | 2024:06:03 18:17:41 |
| Pages: | 200 |
| Words: | 10 |
| Security: | None |
Total processes
137
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | "C:\WINDOWS\System32\Notepad.exe" C:\Users\admin\Desktop\detectvm.vbs | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "C:\Users\Public\Music\nwsvc.exe" /usermode | C:\Users\Public\Music\nwsvc.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Access Service Version: 6.1.7600.16385 Modules
| |||||||||||||||
| 4388 | C:\WINDOWS\system32\cscript.exe "C:\Users\admin\AppData\Local\Temp\VPN_6E3F\detectvm.vbs" | C:\Windows\System32\cscript.exe | — | nwsvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4824 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5340 | "C:\WINDOWS\system32\notepad.exe" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5576 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6276 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\deef940da19f6baca00002f28ee02998269ac036b0d277132402cd4bb086f093.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6368 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6424 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 699
Read events
10 399
Write events
287
Delete events
13
Modification events
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\ConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0049006E007000750074005F007B00380033003200620036003800640032002D0037006600650032002D0034006500370031002D0061003300610064002D003200360031003600360062003600350036006500630036007D000000631BD027FB5DDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0041007000700073005F007B00610030003200350036006600340032002D0062006200300037002D0034003000620034002D0039003400390035002D006200300030003300390036003800380039006500380035007D000000631BD027FB5DDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LastConstraintIndexBuildCompleted |
Value: 743AD027FB5DDB01631BD027FB5DDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Input_{832b68d2-7fe2-4e71-a3ad-26166b656ec6} | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{a0256f42-bb07-40b4-9495-b00396889e85} | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | IndexedLanguage |
Value: en-US | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppIndexer |
| Operation: | write | Name: | LatestCacheFileName |
Value: 410070007000430061006300680065003100330033003800300033003900340037003100350034003200370030003000360031002E007400780074000000631BD027FB5DDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppIndexer |
| Operation: | write | Name: | InstalledWin32AppsRevision |
Value: 7B00340046003200330031003700450030002D0034003600460033002D0034003300300042002D0039003500360034002D003500330043003700410041003000340039003300370035007D000000787ED227FB5DDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 929 | |||
Executable files
4
Suspicious files
59
Text files
196
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6368 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6368 | msiexec.exe | C:\Windows\Installer\13bd58.msi | — | |
MD5:— | SHA256:— | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{a0256f42-bb07-40b4-9495-b00396889e85}\0.1.filtertrie.intermediate.txt | text | |
MD5:34BD1DFB9F72CF4F86E6DF6DA0A9E49A | SHA256:8E1E6A3D56796A245D0C7B0849548932FEE803BBDB03F6E289495830E017F14C | |||
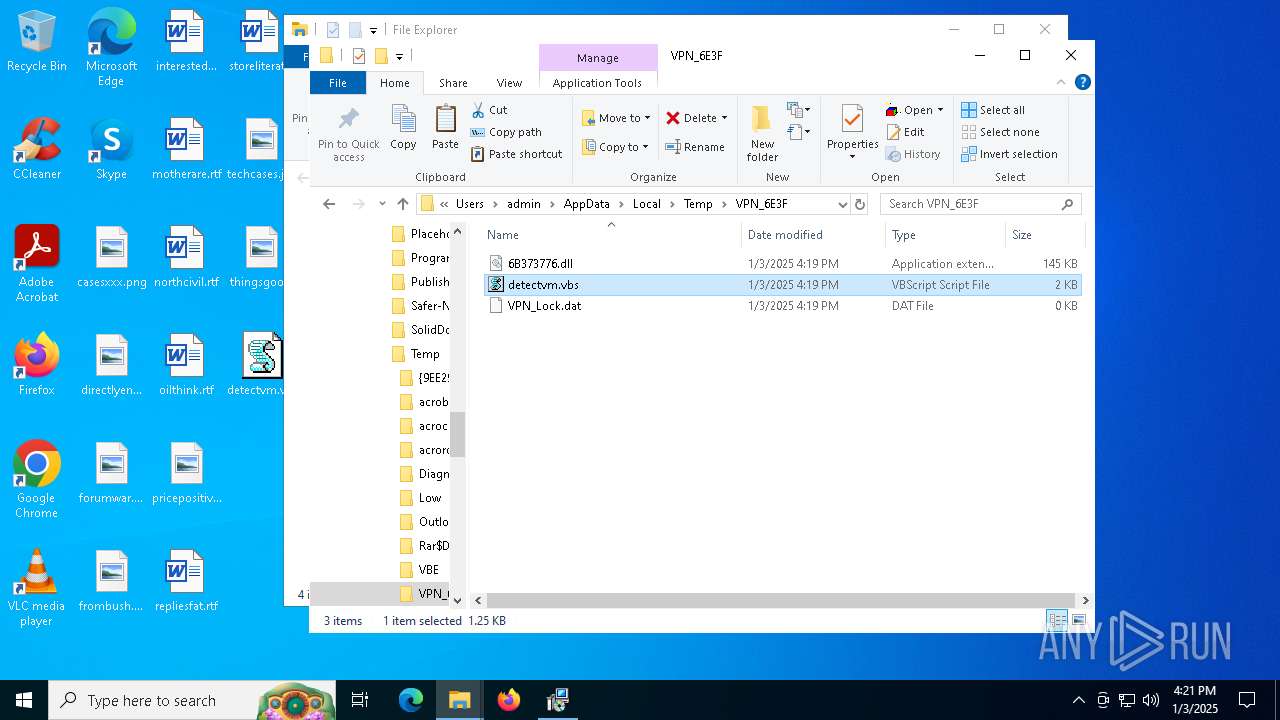
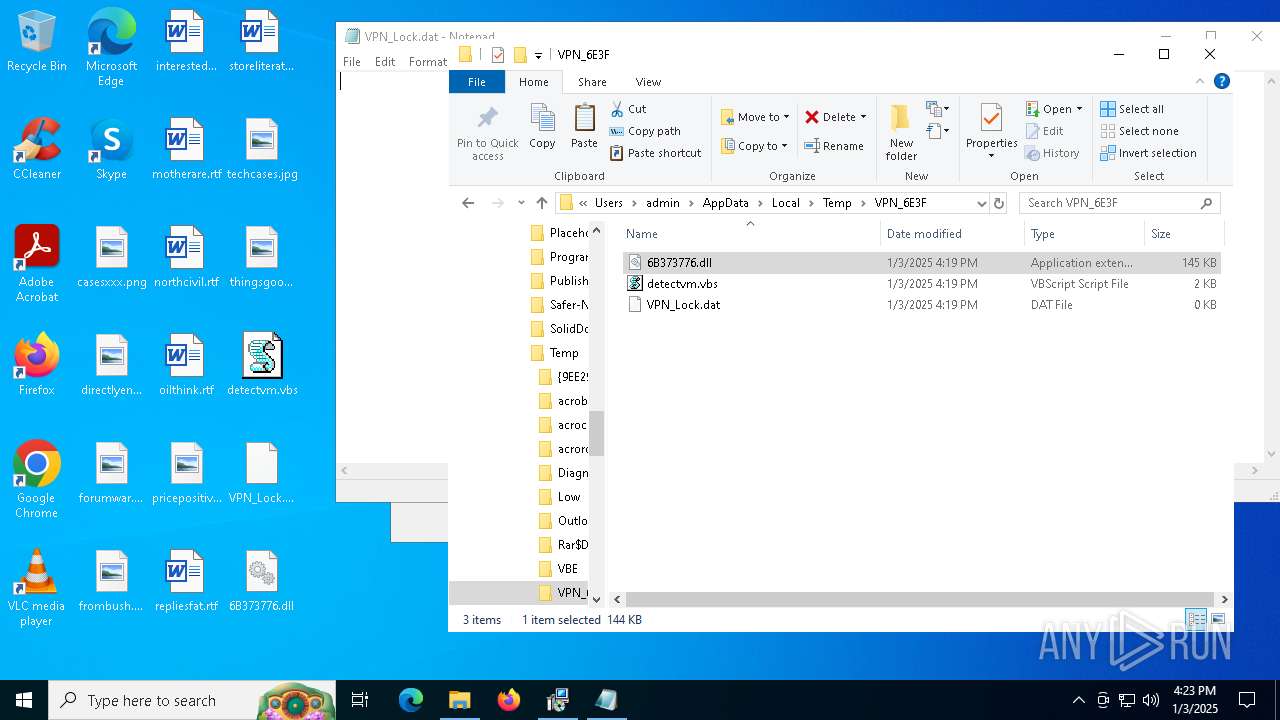
| 6368 | msiexec.exe | C:\Users\Public\Music\nwsvb.exe | executable | |
MD5:A3FD2D29D6DC9BE3625AE87BF1EA5B78 | SHA256:C7D731AFC4303DC898D65F9E2FDDF282C659D2517FE7A448778CBBE7759B17C2 | |||
| 6368 | msiexec.exe | C:\Users\Public\Music\hamcore\languages.txt | text | |
MD5:331C37929CC46B4C9853D4018BE2F676 | SHA256:C35287198BBF4C4643AB31C29B55F3471885A649B6B1F99D8885FA07C2021396 | |||
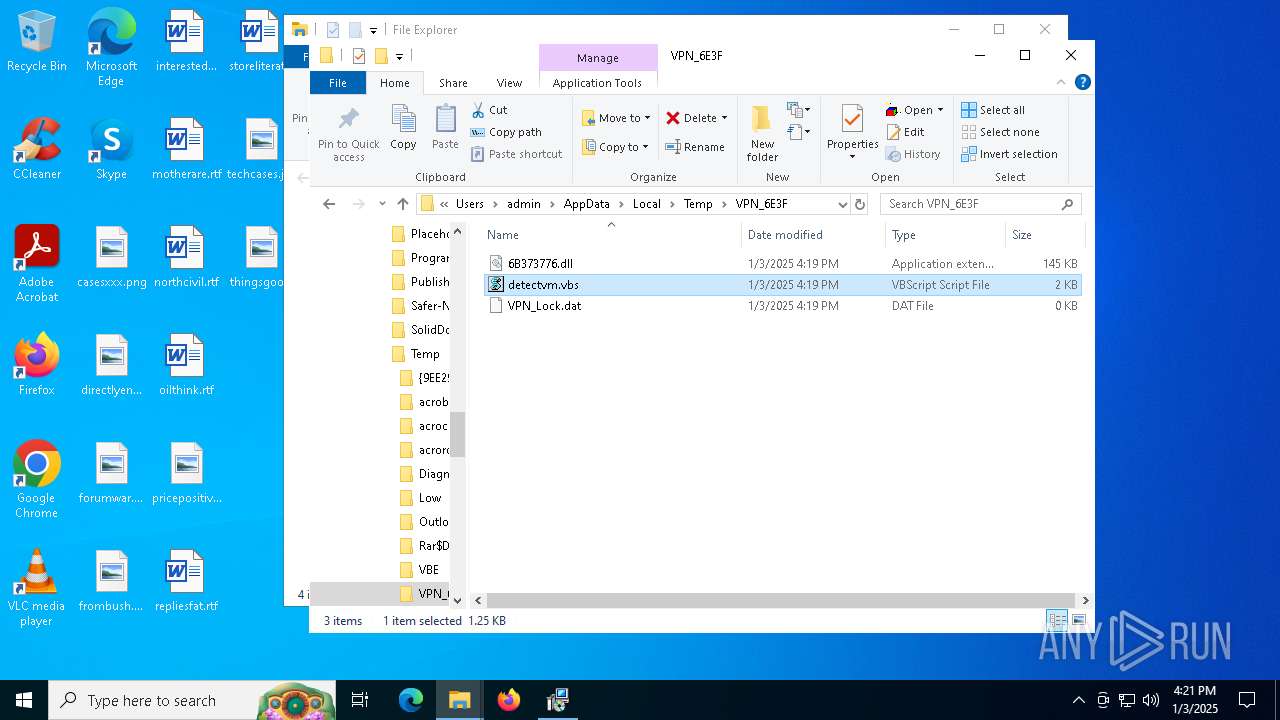
| 1156 | nwsvc.exe | C:\Users\admin\AppData\Local\Temp\.unicode_cache_93c424cf.dat | binary | |
MD5:32B7661D7274E3E9D813DE2E618BF58F | SHA256:341DDFF044EBF8A513C915F08BBAC5ED5CA49F2C976D643C797D0537F56AE226 | |||
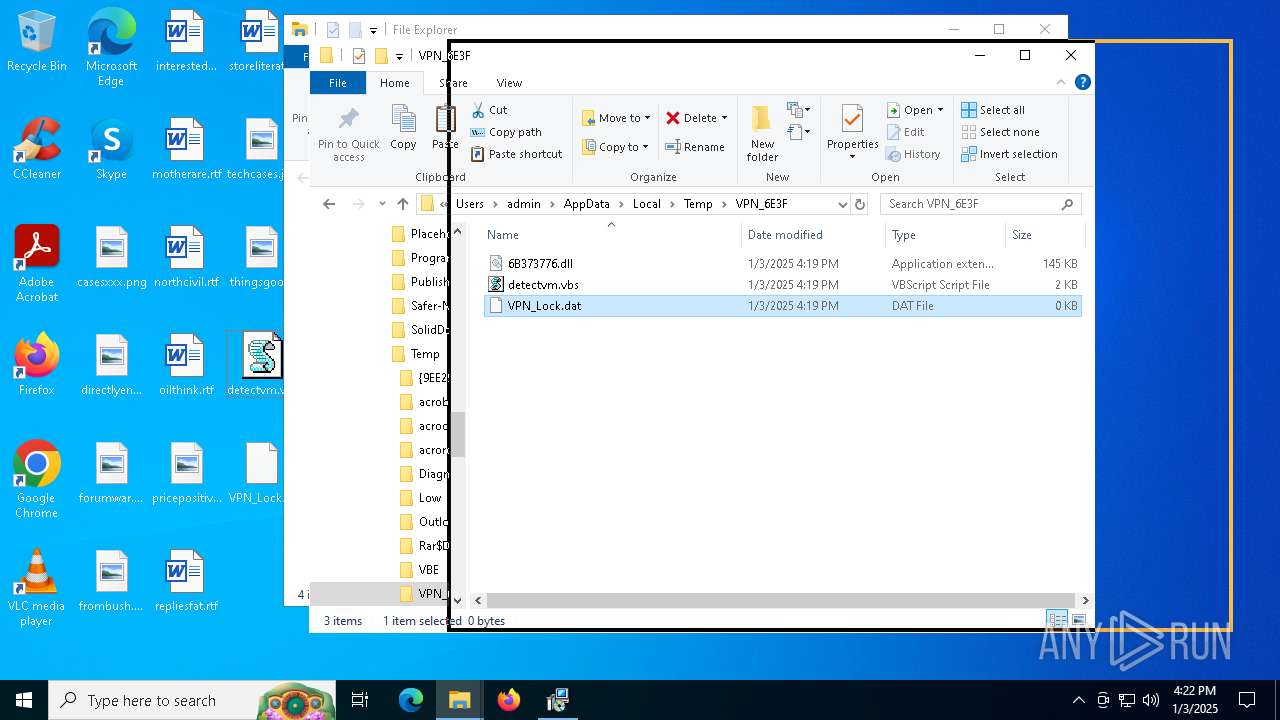
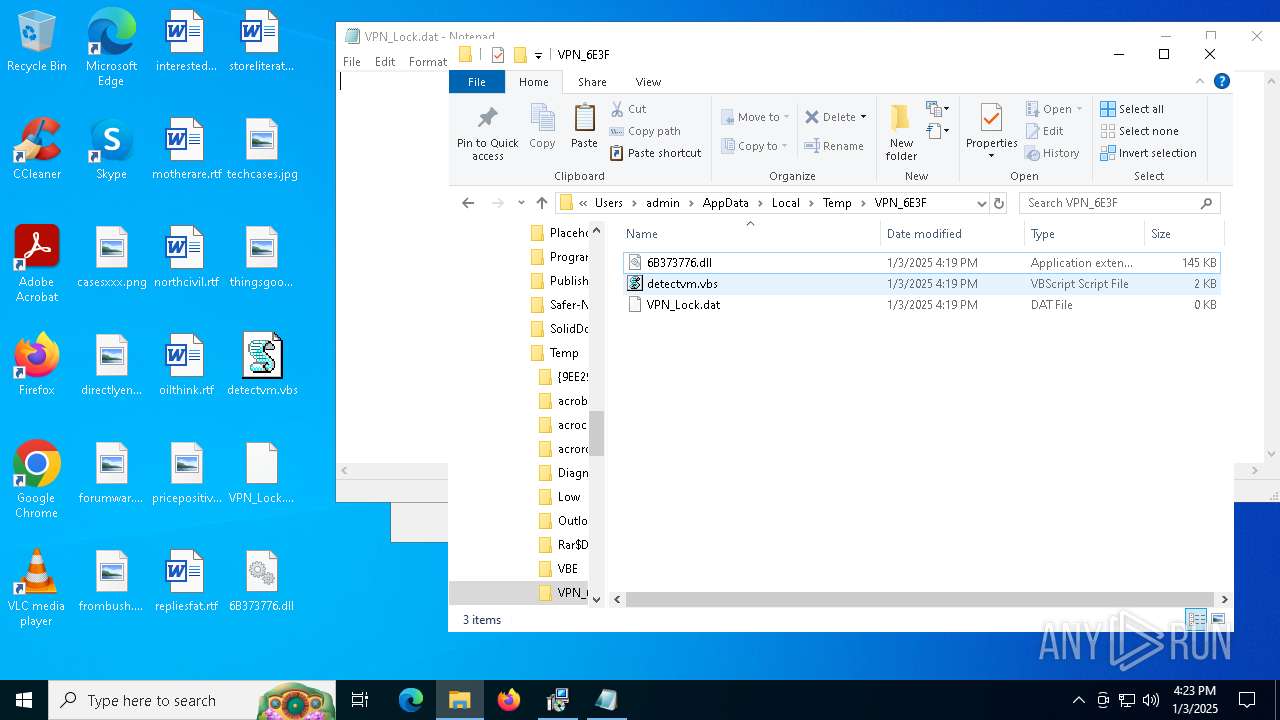
| 1156 | nwsvc.exe | C:\Users\admin\AppData\Local\Temp\VPN_6E3F\6B373776.dll | executable | |
MD5:4196CCFA6E7185D76B59410665418C43 | SHA256:3CB88ADE46905A41239D23958B1CD877E6FBE1E83CE78E3FF7A65E639F1A77BA | |||
| 6368 | msiexec.exe | C:\Windows\Temp\~DF1D5AF186BD78DF1F.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6368 | msiexec.exe | C:\Users\Public\Music\nw.bat | text | |
MD5:00A8EF0B5F1CDB995DA375DD2F3141C8 | SHA256:C63F030993944C3789EE3DBB44A75BB292B15BA50240F27E709B614E92B62030 | |||
| 6368 | msiexec.exe | C:\Users\Public\Music\nwsvc.exe | executable | |
MD5:71630300BD04A8C07844844FE9A33568 | SHA256:A203D0849E09D676428A998CE69B3B9C5662FA566856619A62707C12B9E15663 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
63
DNS requests
102
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5004 | svchost.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3732 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1920 | SIHClient.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1920 | SIHClient.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1156 | nwsvc.exe | POST | 200 | 103.41.63.66:80 | http://x4.xd.open.servers.ddns.softether-network.net/ddns/ddns.aspx?v=4758416074676061695 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.164.112:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
5004 | svchost.exe | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
— | — | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
1176 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| unknown |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |