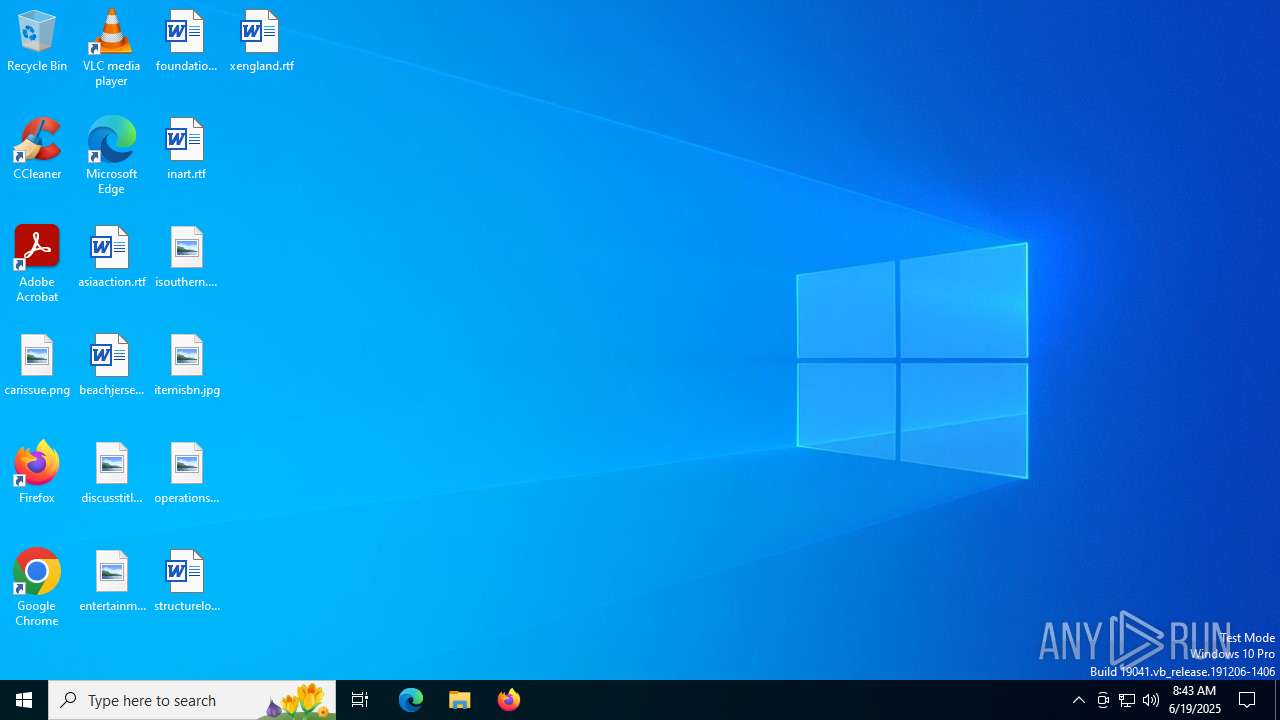
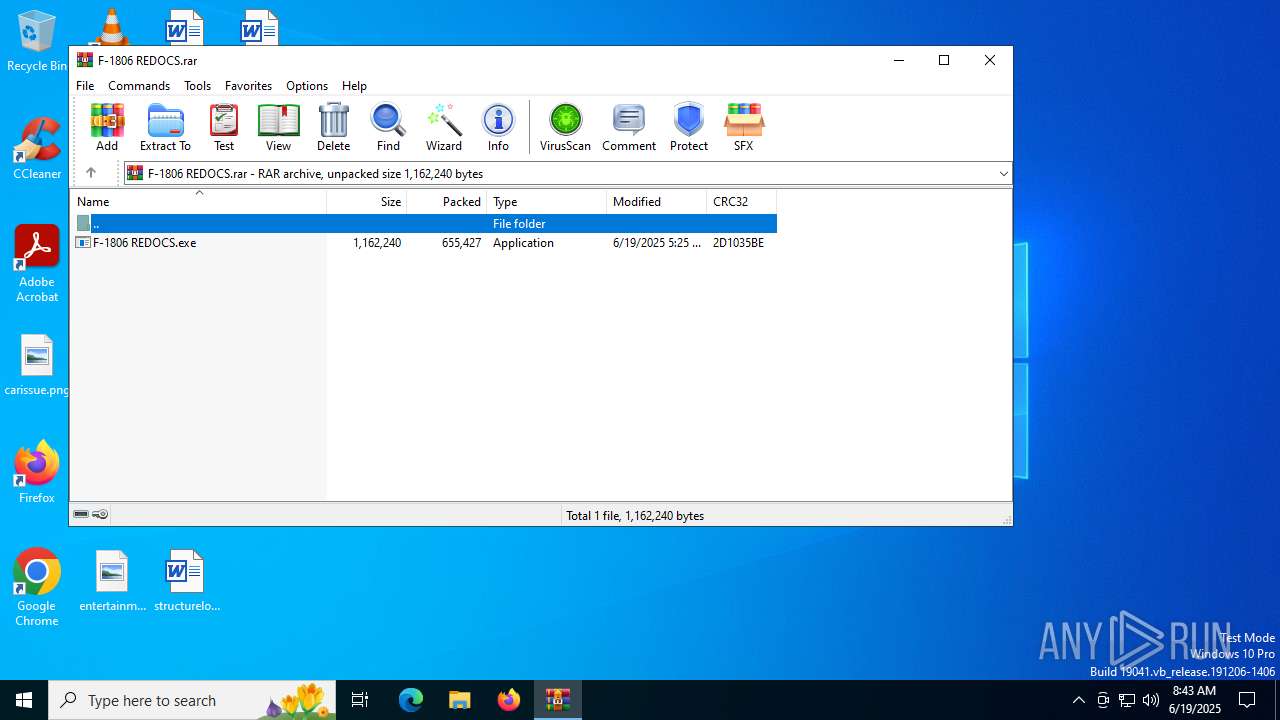
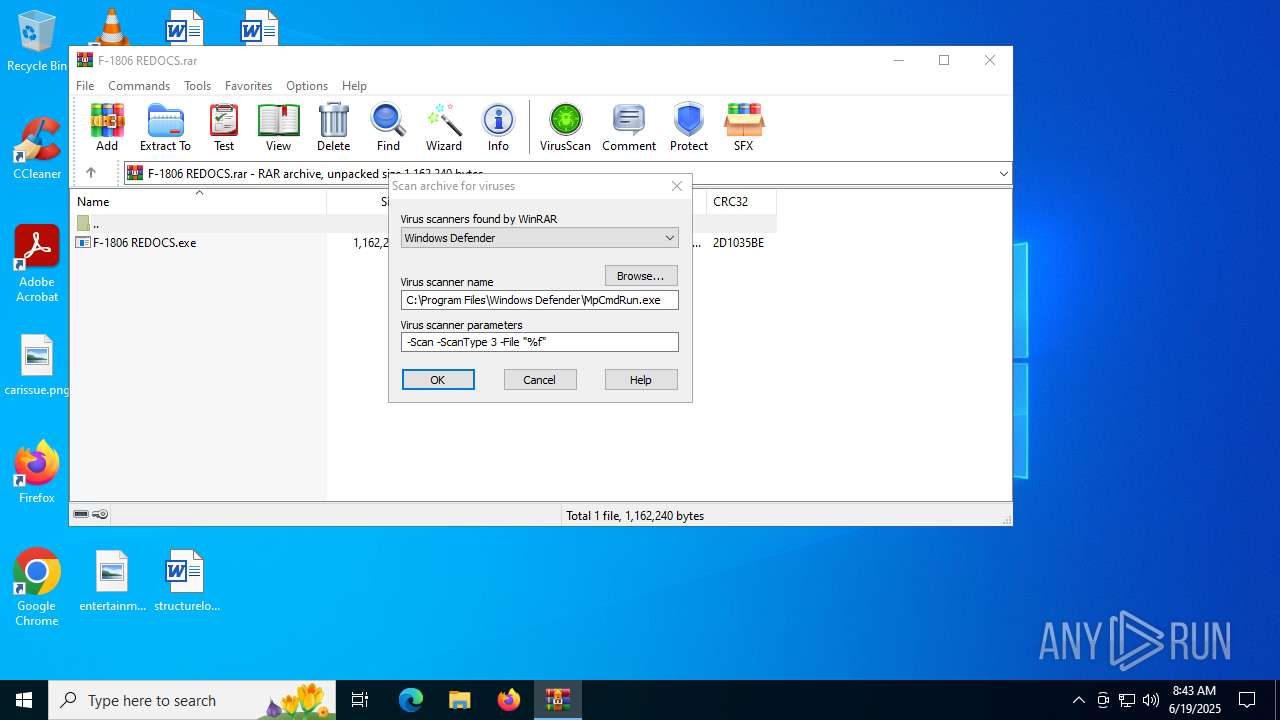
| File name: | F-1806 REDOCS.rar |
| Full analysis: | https://app.any.run/tasks/0a5de9dd-ea41-478e-a83f-d44c3234e6f4 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2025, 08:43:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 764C3B7D47B9B4F4E4E7B8A836FF5906 |
| SHA1: | 0C1E0740D28FD2A54C2F46F8BB1E3D23BB837FAC |
| SHA256: | DEEB5EF4894414D22E52814BE18398D0EDCA3597EF0FC38F49E9073FFF75639C |
| SSDEEP: | 24576:NIr3CcKFxe/pEUVdZYPjKWSLBEx4i+HRZiK8XlhRjaiupvZqMHWKHbzf1aLQc:NIr3Ccexe/p3VdZYPjKWSLs4i+HRZiKC |
MALICIOUS
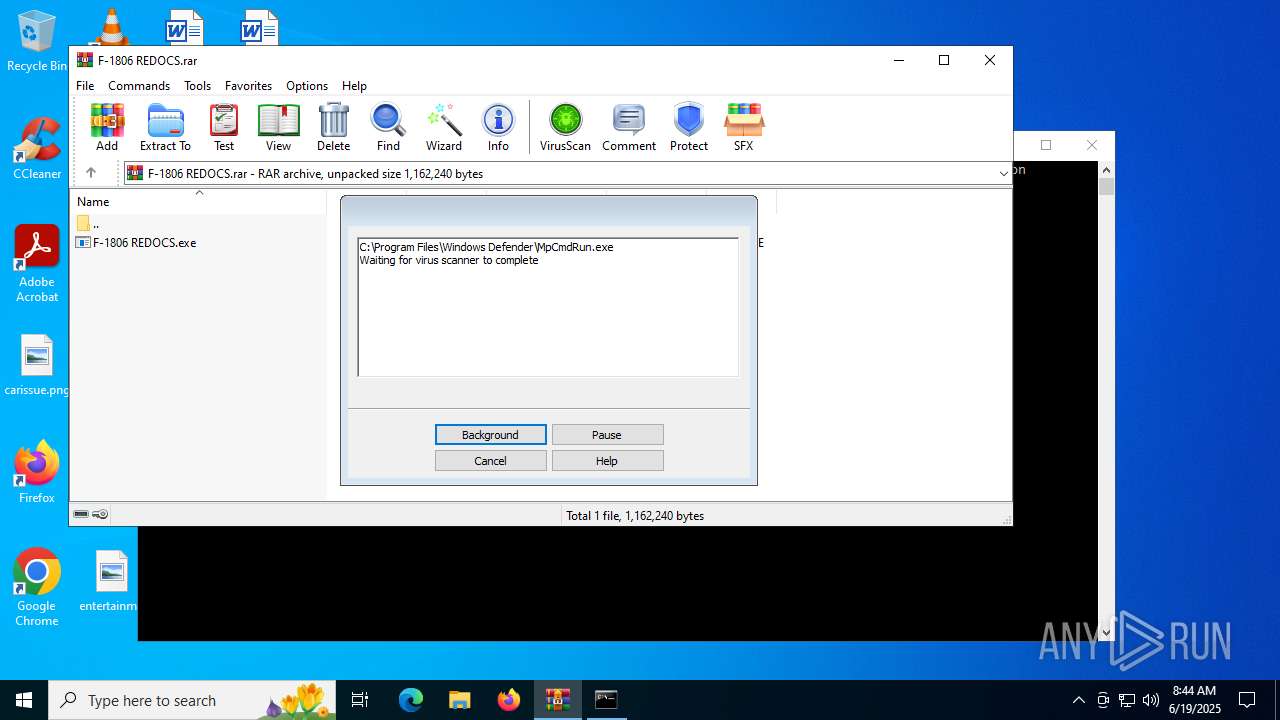
Generic archive extractor
- WinRAR.exe (PID: 6640)
SUSPICIOUS
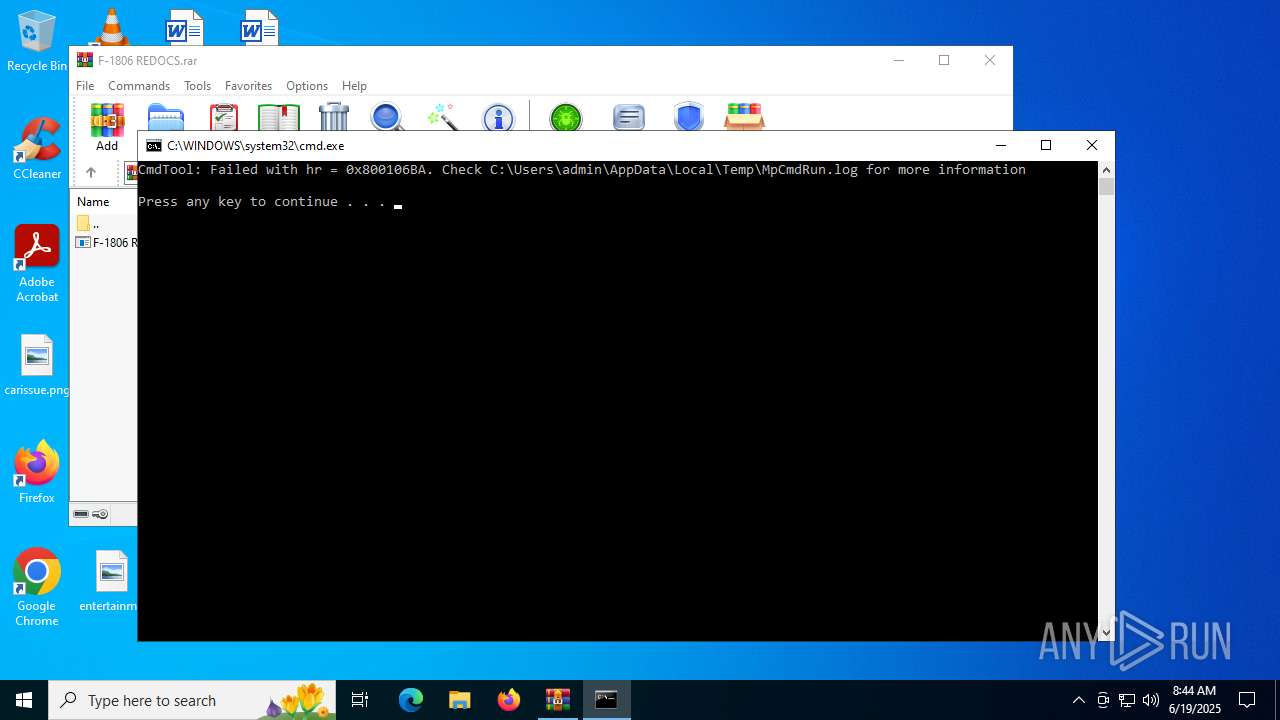
Executes application which crashes
- F-1806 REDOCS.exe (PID: 2648)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6640)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6640)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6640)
INFO
Manual execution by a user
- F-1806 REDOCS.exe (PID: 2648)
Reads mouse settings
- F-1806 REDOCS.exe (PID: 2648)
Checks supported languages
- F-1806 REDOCS.exe (PID: 2648)
- MpCmdRun.exe (PID: 4196)
Create files in a temporary directory
- F-1806 REDOCS.exe (PID: 2648)
- MpCmdRun.exe (PID: 4196)
Checks proxy server information
- WerFault.exe (PID: 6224)
Creates files or folders in the user directory
- WerFault.exe (PID: 6224)
Reads the software policy settings
- WerFault.exe (PID: 6224)
- slui.exe (PID: 3876)
The sample compiled with english language support
- WinRAR.exe (PID: 6640)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6640)
Reads the computer name
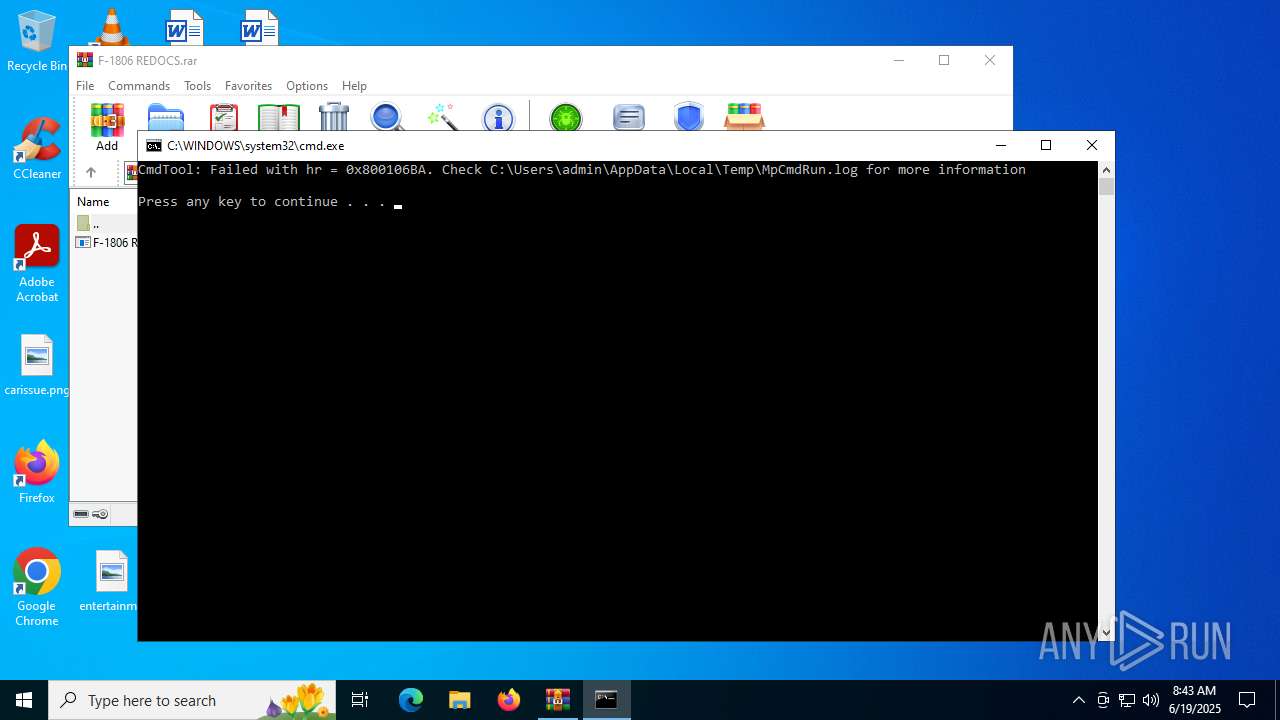
- MpCmdRun.exe (PID: 4196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 655427 |
| UncompressedSize: | 1162240 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | F-1806 REDOCS.exe |
Total processes
147
Monitored processes
8
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2536 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6640.43431\Rar$Scan17577.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2648 | "C:\Users\admin\Desktop\F-1806 REDOCS.exe" | C:\Users\admin\Desktop\F-1806 REDOCS.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 3876 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4196 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6640.43431" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6224 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 2648 -s 720 | C:\Windows\SysWOW64\WerFault.exe | F-1806 REDOCS.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\F-1806 REDOCS.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6980 | "C:\Users\admin\Desktop\F-1806 REDOCS.exe" | C:\Windows\SysWOW64\svchost.exe | — | F-1806 REDOCS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 7076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 619
Read events
5 610
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\F-1806 REDOCS.rar | |||
| (PID) Process: | (6640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
1
Suspicious files
5
Text files
5
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_F-1806 REDOCS.ex_bffc230d783a7ac1fedff95425aed4d8f66f660_10ba2b00_abd78b6f-98f2-4b4a-99e8-eb8ec6aa73a7\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER64F3.tmp.dmp | dmp | |
MD5:E9FB05BE980A9C0954B1C27856C665EA | SHA256:3234F1A463A0780D19802489B7FB9CAB0832F2A2EECCA5EF2CBFE534791ECC3D | |||
| 2648 | F-1806 REDOCS.exe | C:\Users\admin\AppData\Local\Temp\aut60CE.tmp | binary | |
MD5:AA173FBE63B6C43786B197A5FA051904 | SHA256:24EED0EC4B9CD426AF4CC9D6DC0603C73927A015E45B218FEE3A81DE2A59B085 | |||
| 6224 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:6333F3F5D1CA5A747B369783146EA92F | SHA256:42293351BC6389F2E74804900647A9C56D05E52DD987122CF4925E47125F4CD0 | |||
| 6224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER65E0.tmp.xml | xml | |
MD5:B98FEFECE3B9D8559295083535E0495A | SHA256:29BEBEE4F6D77F6EB125BC546A4DB39A03D1470CFD45B10C335C917EE6DFCF56 | |||
| 6640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6640.43431\Rar$Scan17577.bat | text | |
MD5:33B99ACD68BBA68DBAD76B6A510CD541 | SHA256:82CFA4A6BB0186982FE516ED4F33A820496E541C76B962512A0916F8988E7D4A | |||
| 6224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER65C0.tmp.WERInternalMetadata.xml | xml | |
MD5:948C9489F02E7DF18D74FF1C94101335 | SHA256:3FD6050AB59A6F6C88DEBB5EC1182F6A50621BE3D7487AB75FE04940BE6FA032 | |||
| 2648 | F-1806 REDOCS.exe | C:\Users\admin\AppData\Local\Temp\indivisibility | binary | |
MD5:AA173FBE63B6C43786B197A5FA051904 | SHA256:24EED0EC4B9CD426AF4CC9D6DC0603C73927A015E45B218FEE3A81DE2A59B085 | |||
| 6224 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:5B63C0144C61100C949E65C9B4C7B790 | SHA256:51E7A9D4403161514027724D012C19E4717FD92CC87B31049944A37B40228B8E | |||
| 6640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6640.43431\F-1806 REDOCS.rar\F-1806 REDOCS.exe | executable | |
MD5:AC68216CA71382D4626AA7131E482115 | SHA256:37C433692490D7CDED8C8BD3A0F8BC0CC688294A3D3116E859FA9E28483D5041 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
30
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6224 | WerFault.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6224 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2668 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3752 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3752 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1508 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6224 | WerFault.exe | 20.42.65.92:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6224 | WerFault.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
6224 | WerFault.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2668 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |