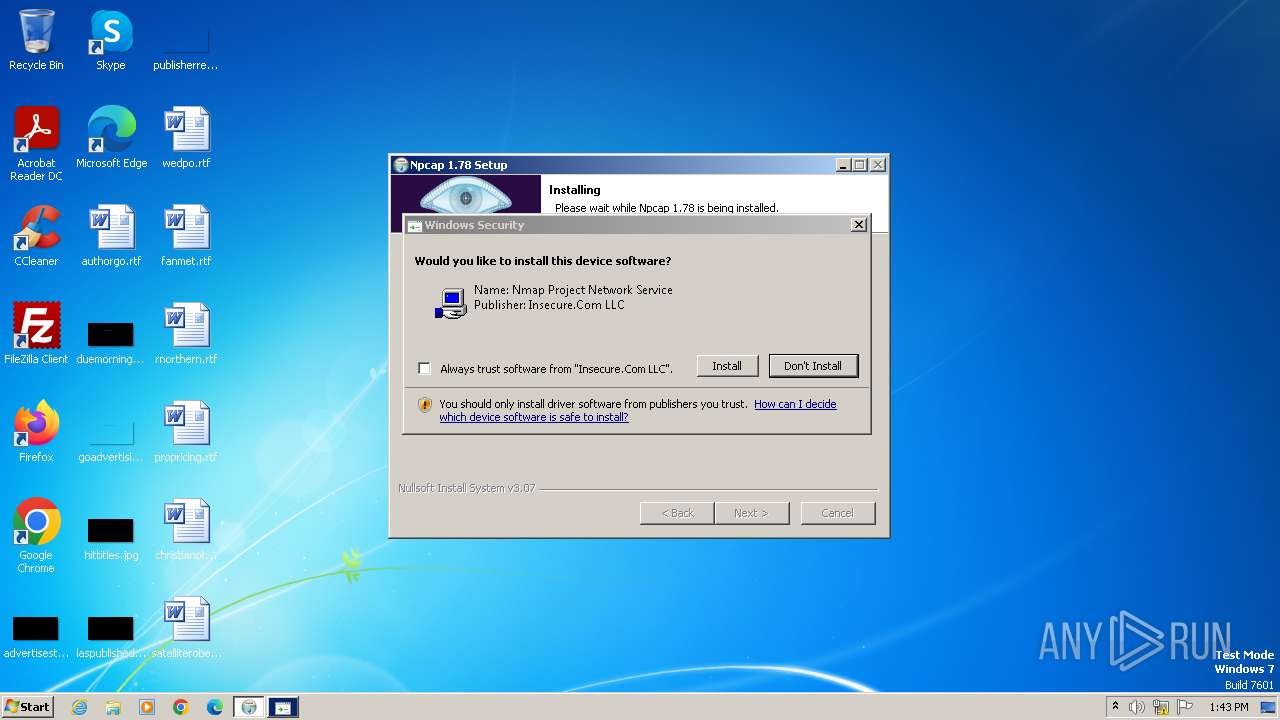
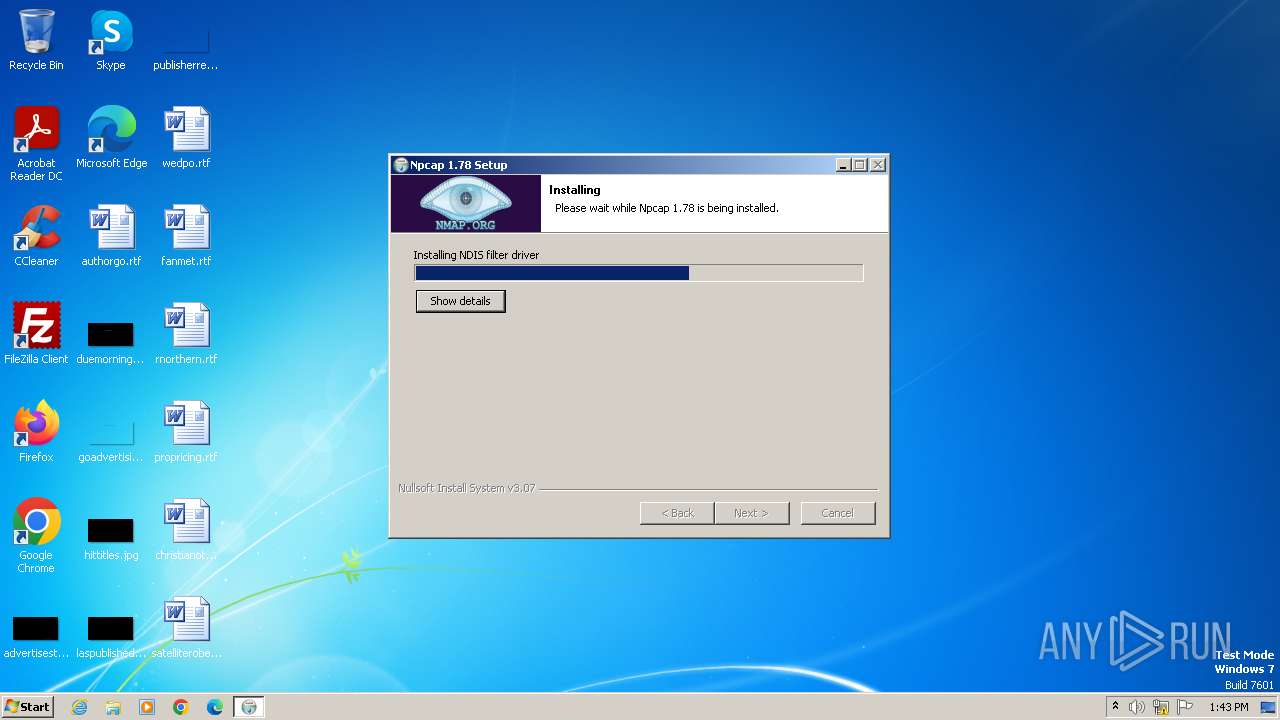
| File name: | npcap-1.78.exe |
| Full analysis: | https://app.any.run/tasks/7e660d7a-0e73-4745-8878-43a15254631c |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2023, 13:42:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 1B7DFFF4E1F16785D5E800C193301BD7 |
| SHA1: | E1EE172EE36999DAA3CFB2A0406FD8950038CEFE |
| SHA256: | DEEB39AE22A44EA2698C4A58732E621BC45B84686A444C405491FEF946898D90 |
| SSDEEP: | 49152:Y4tBS1uAo57BdQimf8QqbTz4VBCX1PbpJ0tSeSYf43gTc+XEr1bF+oLj9In0ffsM:YOcWnz4VBClPbEoeHTc+g1h+gGn0ffsM |
MALICIOUS
Drops the executable file immediately after the start
- npcap-1.78.exe (PID: 3576)
- NPFInstall.exe (PID: 2624)
- drvinst.exe (PID: 2528)
Run PowerShell with an invisible window
- powershell.exe (PID: 3980)
- powershell.exe (PID: 3536)
- powershell.exe (PID: 908)
- powershell.exe (PID: 1892)
- powershell.exe (PID: 2828)
Creates a writable file the system directory
- drvinst.exe (PID: 2528)
- NPFInstall.exe (PID: 2624)
- npcap-1.78.exe (PID: 3576)
Uses Task Scheduler to run other applications
- nsCD88.tmp (PID: 3324)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- npcap-1.78.exe (PID: 3576)
The process creates files with name similar to system file names
- npcap-1.78.exe (PID: 3576)
Starts application with an unusual extension
- npcap-1.78.exe (PID: 3576)
Starts CMD.EXE for commands execution
- ns7065.tmp (PID: 3584)
Uses WMIC.EXE to obtain quick Fix Engineering (patches) data
- cmd.exe (PID: 3444)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3444)
Reads the Internet Settings
- WMIC.exe (PID: 3556)
Starts POWERSHELL.EXE for commands execution
- ns91F9.tmp (PID: 4008)
- ns942C.tmp (PID: 4044)
- ns9808.tmp (PID: 2196)
- ns99CE.tmp (PID: 1508)
- nsCBD2.tmp (PID: 3120)
Powershell version downgrade attack
- powershell.exe (PID: 3980)
- powershell.exe (PID: 3536)
- powershell.exe (PID: 1892)
- powershell.exe (PID: 908)
- powershell.exe (PID: 2828)
The process hide an interactive prompt from the user
- ns91F9.tmp (PID: 4008)
- ns942C.tmp (PID: 4044)
- ns9808.tmp (PID: 2196)
- ns99CE.tmp (PID: 1508)
- nsCBD2.tmp (PID: 3120)
The process bypasses the loading of PowerShell profile settings
- ns91F9.tmp (PID: 4008)
- ns942C.tmp (PID: 4044)
- ns9808.tmp (PID: 2196)
- ns99CE.tmp (PID: 1508)
- nsCBD2.tmp (PID: 3120)
Executes as Windows Service
- VSSVC.exe (PID: 448)
Drops a system driver (possible attempt to evade defenses)
- NPFInstall.exe (PID: 2624)
- drvinst.exe (PID: 2528)
Creates files in the driver directory
- drvinst.exe (PID: 2528)
- NPFInstall.exe (PID: 2624)
Checks Windows Trust Settings
- drvinst.exe (PID: 2528)
- NPFInstall.exe (PID: 2624)
Reads settings of System Certificates
- rundll32.exe (PID: 2080)
- NPFInstall.exe (PID: 2624)
Reads security settings of Internet Explorer
- NPFInstall.exe (PID: 2624)
Creates or modifies Windows services
- npcap-1.78.exe (PID: 3576)
INFO
Checks supported languages
- npcap-1.78.exe (PID: 3576)
- ns7065.tmp (PID: 3584)
- ns8FE5.tmp (PID: 3728)
- NPFInstall.exe (PID: 3724)
- ns91F9.tmp (PID: 4008)
- ns942C.tmp (PID: 4044)
- ns972B.tmp (PID: 3684)
- ns9799.tmp (PID: 3672)
- ns99CE.tmp (PID: 1508)
- ns9D3A.tmp (PID: 1856)
- ns9DB8.tmp (PID: 1232)
- ns9E26.tmp (PID: 684)
- ns9EA4.tmp (PID: 2336)
- NPFInstall.exe (PID: 2316)
- ns9F90.tmp (PID: 1928)
- NPFInstall.exe (PID: 328)
- nsA06B.tmp (PID: 2688)
- NPFInstall.exe (PID: 2624)
- ns9808.tmp (PID: 2196)
- drvinst.exe (PID: 2528)
- nsCBD2.tmp (PID: 3120)
- nsCD88.tmp (PID: 3324)
Reads the computer name
- npcap-1.78.exe (PID: 3576)
- NPFInstall.exe (PID: 3724)
- NPFInstall.exe (PID: 328)
- NPFInstall.exe (PID: 2624)
- drvinst.exe (PID: 2528)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3436)
- NPFInstall.exe (PID: 2624)
- drvinst.exe (PID: 2528)
Creates files in the program directory
- npcap-1.78.exe (PID: 3576)
- NPFInstall.exe (PID: 3724)
Create files in a temporary directory
- npcap-1.78.exe (PID: 3576)
- NPFInstall.exe (PID: 2624)
Reads Environment values
- npcap-1.78.exe (PID: 3576)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 2080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:07:25 00:40:31+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 28160 |
| InitializedDataSize: | 152576 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3a59 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.1.78.1018 |
| ProductVersionNumber: | 5.1.78.1018 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Npcap 1.78 installer |
| FileVersion: | 1.78 |
| LegalCopyright: | Copyright (c) 2023, Insecure.Com LLC. All rights reserved. |
| ProductName: | Npcap |
| ProductVersion: | 1.78 |
Total processes
100
Monitored processes
41
Malicious processes
15
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | certutil.exe -addstore -f "TrustedPublisher" "C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\signing.p7b" | C:\Windows\System32\certutil.exe | — | ns9E26.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
| 328 | "C:\Program Files\Npcap\NPFInstall.exe" -n -iw | C:\Program Files\Npcap\NPFInstall.exe | — | ns9F90.tmp | |||||||||||
User: admin Company: Insecure.Com LLC. Integrity Level: HIGH Description: A LWF & WFP driver installation tool Exit code: 0 Version: 1.78 Modules
| |||||||||||||||
| 448 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | "C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\ns9E26.tmp" certutil.exe -addstore -f "TrustedPublisher" "C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\signing.p7b" | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\ns9E26.tmp | — | npcap-1.78.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 908 | powershell.exe -NoProfile -WindowStyle Hidden -NonInteractive -Command "Get-ChildItem Cert:\LocalMachine\Root | Where-Object {$_.Thumbprint -eq '5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25'} | Sort-Object -Descending -Property FriendlyName | Select-Object -Skip 1 | Remove-Item" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | ns9808.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | SCHTASKS.EXE /Create /F /RU SYSTEM /SC ONSTART /TN npcapwatchdog /TR "'C:\Program Files\Npcap\CheckStatus.bat'" /NP | C:\Windows\System32\schtasks.exe | — | nsCD88.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | "C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\ns9DB8.tmp" certutil.exe -addstore -f "Root" "C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25.sst" | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\ns9DB8.tmp | — | npcap-1.78.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 2148086027 Modules
| |||||||||||||||
| 1508 | "C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\ns99CE.tmp" powershell.exe -NoProfile -WindowStyle Hidden -NonInteractive -Command "If (Get-ChildItem Cert:\LocalMachine\Root\5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25){certutil.exe -verifystore 'Root' '5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25';If($LASTEXITCODE -ne 0){Remove-Item Cert:\LocalMachine\Root\5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25}}" | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\ns99CE.tmp | — | npcap-1.78.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1856 | "C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\ns9D3A.tmp" certutil.exe -verifystore "Root" "5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25" | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\ns9D3A.tmp | — | npcap-1.78.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 2148073489 Modules
| |||||||||||||||
| 1880 | certutil.exe -addstore -f "Root" "C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\5fb7ee0633e259dbad0c4c9ae6d38f1a61c7dc25.sst" | C:\Windows\System32\certutil.exe | — | ns9DB8.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 2148086027 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
Total events
43 918
Read events
43 489
Write events
424
Delete events
5
Modification events
| (PID) Process: | (3436) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{D7C1E68E-B10B-4535-A09E-400BBE9CEFB4}\{857FCC3A-01A8-40B5-BF87-E3A324CC6E41} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3436) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{D7C1E68E-B10B-4535-A09E-400BBE9CEFB4} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3436) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{CF6B7DA6-DD6D-4944-A393-9639369FCADE} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3980) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3536) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4032) certutil.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (908) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1892) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2164) certutil.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (284) certutil.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
39
Suspicious files
44
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3576 | npcap-1.78.exe | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\options.ini | text | |
MD5:13A70D1FB5473932B6BECACCE3256EB8 | SHA256:6FB874CA5489CE28232F3451467A3E39047ECED5670830F813E5DEFA6A80D8F7 | |||
| 3576 | npcap-1.78.exe | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\InstallOptions.dll | executable | |
MD5:170C17AC80215D0A377B42557252AE10 | SHA256:61EA114D9D0CD1E884535095AA3527A6C28DF55A4ECEE733C8C398F50B84CC3D | |||
| 3576 | npcap-1.78.exe | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\ns7065.tmp | executable | |
MD5:F9E61A25016DCB49867477C1E71A704E | SHA256:274E53DC8C5DDC273A6F5683B71B882EF8917029E2EAF6C8DBEE0C62D999225D | |||
| 3576 | npcap-1.78.exe | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\nsExec.dll | executable | |
MD5:F9E61A25016DCB49867477C1E71A704E | SHA256:274E53DC8C5DDC273A6F5683B71B882EF8917029E2EAF6C8DBEE0C62D999225D | |||
| 3576 | npcap-1.78.exe | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\final.ini | text | |
MD5:5FAA58B0398F6C4442D5CFBC616B4531 | SHA256:4AF865B65FDBA7BB5C874F3D67BFDCE7EEAD2459A572E0681A6C067568AF4902 | |||
| 3576 | npcap-1.78.exe | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\ns8FE5.tmp | executable | |
MD5:F9E61A25016DCB49867477C1E71A704E | SHA256:274E53DC8C5DDC273A6F5683B71B882EF8917029E2EAF6C8DBEE0C62D999225D | |||
| 3576 | npcap-1.78.exe | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\modern-header.bmp | image | |
MD5:B514F98A3DF2F23FB0FDF170FA772F5C | SHA256:F22D49EEC7926CDE60DAD056A3A9FA844327F759F38E76BAD4C3119A57E37888 | |||
| 3576 | npcap-1.78.exe | C:\Users\admin\AppData\Local\Temp\nsx7045.tmp\NPFInstall.exe | executable | |
MD5:EFBAA811FF9A2AE814ED2A897CBF2E03 | SHA256:A6DD4A41CCDF8EF97F5E04B204DB3BB3F2FF397C336E2A375A1E72E75A5C49DD | |||
| 3576 | npcap-1.78.exe | C:\Program Files\Npcap\DiagReport.ps1 | text | |
MD5:0B4DF7D19ADE75BEE930D54BE31AC09C | SHA256:27EB36CB165C6EDD2F55B72A6856E4BF32AE2FA6CADFFCD267F5DF96EEA0B011 | |||
| 3576 | npcap-1.78.exe | C:\Program Files\Npcap\DiagReport.bat | text | |
MD5:B82606A6AFB3777D62E35E8D9850FAED | SHA256:0843361F05255E3970ED955171C20003238756C57137FEF9AC19D29FBD49F9F6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |