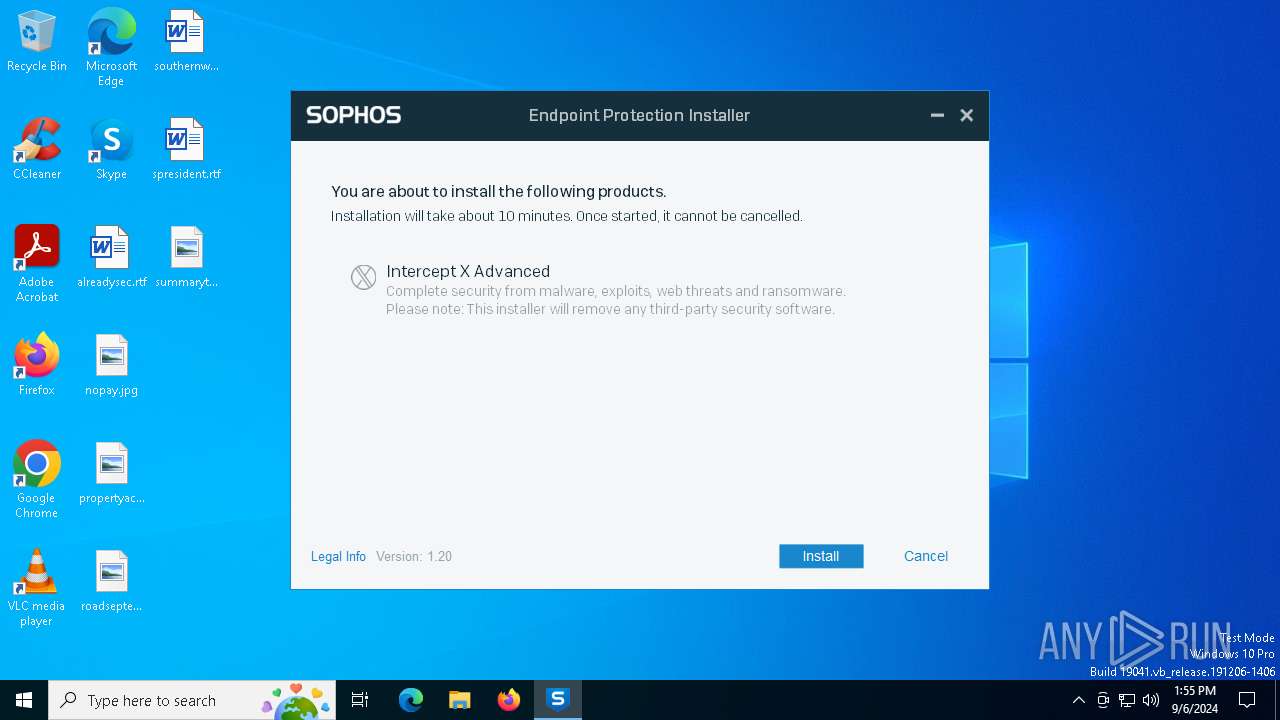
| File name: | SophosSetup.exe |
| Full analysis: | https://app.any.run/tasks/09bcb5e1-9a01-4c79-a48d-0fc5bbd58a69 |
| Verdict: | Malicious activity |
| Analysis date: | September 06, 2024, 13:54:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C10EBC0C140364FB2EBBD405E665ACFA |
| SHA1: | A50B7BCE933668D301709948771B7B64AB5FAEB2 |
| SHA256: | DEE4A68F432AC4E7C130C03FFAC7A9938205A319B778B20F2BC161EE69417C0E |
| SSDEEP: | 98304:yjTEXtYji6TMN6lxcCtL0QeEd1TQFkXmAay7o6UwQsXUN7GEbTMNnn:qcs |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- SophosHealth.exe (PID: 5084)
Changes the autorun value in the registry
- su-setup64.exe (PID: 2768)
MIMIKATZ has been detected (YARA)
- SophosFileScanner.exe (PID: 4392)
SUSPICIOUS
Checks Windows Trust Settings
- Setup.exe (PID: 5000)
- SophosSetup_Stage2.exe (PID: 1432)
- su-setup64.exe (PID: 2016)
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 6612)
- SSPService.exe (PID: 4528)
- su-setup64.exe (PID: 2684)
- McsAgent.exe (PID: 4444)
- su-setup64.exe (PID: 3844)
- SophosSSEValidator.exe (PID: 5544)
- su-setup64.exe (PID: 7000)
- SophosFSVerify.exe (PID: 3352)
- su-setup32.exe (PID: 6196)
- su-setup64.exe (PID: 2768)
- Sophos UI.exe (PID: 3036)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- SophosSMEValidator.exe (PID: 6416)
- SophosSMEValidator.exe (PID: 1452)
- SophosSMEValidator.exe (PID: 4092)
- SophosFileScanner.exe (PID: 4392)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6180)
- SophosNtpService.exe (PID: 5988)
- SophosFileScanner.exe (PID: 6984)
- su-setup64.exe (PID: 6056)
Reads security settings of Internet Explorer
- Setup.exe (PID: 5000)
- SophosSetup_Stage2.exe (PID: 1432)
- su-setup64.exe (PID: 2016)
- su-setup64.exe (PID: 6612)
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 2684)
- su-setup64.exe (PID: 3844)
- SophosSSEValidator.exe (PID: 5544)
- su-setup64.exe (PID: 7000)
- SophosFSVerify.exe (PID: 3352)
- SophosFileScanner.exe (PID: 4392)
- su-setup32.exe (PID: 6196)
- su-setup64.exe (PID: 2768)
- Sophos UI.exe (PID: 3036)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- SophosSMEValidator.exe (PID: 6416)
- SophosSMEValidator.exe (PID: 1452)
- SophosSMEValidator.exe (PID: 4092)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 6180)
- SophosNtpService.exe (PID: 5988)
- SophosFileScanner.exe (PID: 6984)
- su-setup64.exe (PID: 5732)
The process verifies whether the antivirus software is installed
- SophosSetup_Stage2.exe (PID: 1432)
- su-setup64.exe (PID: 2016)
- su-setup64.exe (PID: 6656)
- Setup.exe (PID: 5000)
- su-setup64.exe (PID: 6612)
- SEDService.exe (PID: 3908)
- SSPService.exe (PID: 4528)
- SophosSSEValidator.exe (PID: 5544)
- su-setup64.exe (PID: 7000)
- su-setup64.exe (PID: 3844)
- SophosFSVerify.exe (PID: 3352)
- SophosFileScanner.exe (PID: 4392)
- su-setup32.exe (PID: 6196)
- su-setup64.exe (PID: 2684)
- su-setup64.exe (PID: 2768)
- Sophos UI.exe (PID: 3036)
- su-setup64.exe (PID: 1552)
- SophosACSenabledTest.exe (PID: 3568)
- SophosSMEValidator.exe (PID: 6416)
- SophosSMEValidator.exe (PID: 1452)
- SophosSMEValidator.exe (PID: 4092)
- su-setup64.exe (PID: 2524)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 6180)
- wevtutil.exe (PID: 5144)
- SophosFS.exe (PID: 6508)
- SophosFileScanner.exe (PID: 6984)
Executable content was dropped or overwritten
- Setup.exe (PID: 5000)
- SophosSetup_Stage2.exe (PID: 1432)
- SophosSetup.exe (PID: 4980)
- AVRemoveW_.exe (PID: 7116)
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 6612)
- su-setup64.exe (PID: 2684)
- su-setup64.exe (PID: 3844)
- su-setup64.exe (PID: 7000)
- su-setup32.exe (PID: 6196)
- su-setup64.exe (PID: 2768)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6180)
- su-setup64.exe (PID: 6056)
Process drops legitimate windows executable
- SophosSetup_Stage2.exe (PID: 1432)
- su-setup64.exe (PID: 2768)
- su-setup64.exe (PID: 2524)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 6180)
Drops a system driver (possible attempt to evade defenses)
- SophosSetup_Stage2.exe (PID: 1432)
- su-setup64.exe (PID: 6612)
- su-setup64.exe (PID: 6180)
Process drops python dynamic module
- SophosSetup_Stage2.exe (PID: 1432)
The process drops C-runtime libraries
- SophosSetup_Stage2.exe (PID: 1432)
- su-setup64.exe (PID: 6180)
Loads Python modules
- AVRemoveW_.exe (PID: 7116)
Starts CMD.EXE for commands execution
- AVRemoveW_.exe (PID: 7116)
Searches for installed software
- AVRemoveW_.exe (PID: 7116)
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 2684)
- su-setup64.exe (PID: 3844)
- su-setup64.exe (PID: 7000)
- su-setup32.exe (PID: 6196)
- su-setup64.exe (PID: 2768)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6180)
Creates a software uninstall entry
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 6612)
- su-setup64.exe (PID: 2684)
- su-setup64.exe (PID: 3844)
- su-setup64.exe (PID: 7000)
- su-setup32.exe (PID: 6196)
- su-setup64.exe (PID: 2768)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6180)
Creates or modifies Windows services
- su-setup64.exe (PID: 6612)
- SEDService.exe (PID: 3908)
- SSPService.exe (PID: 4528)
Creates files in the driver directory
- su-setup64.exe (PID: 6612)
- su-setup64.exe (PID: 6180)
Executes as Windows Service
- SEDService.exe (PID: 3908)
- SSPService.exe (PID: 4528)
- McsAgent.exe (PID: 4444)
- McsClient.exe (PID: 6192)
- SophosFS.exe (PID: 6508)
- SophosHealth.exe (PID: 5084)
- SophosNtpService.exe (PID: 5988)
Application launched itself
- SophosFileScanner.exe (PID: 1440)
- SophosFileScanner.exe (PID: 6016)
Creates/Modifies COM task schedule object
- su-setup64.exe (PID: 2768)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 6180)
Found regular expressions for crypto-addresses (YARA)
- SophosFileScanner.exe (PID: 4392)
There is functionality for communication over UDP network (YARA)
- SophosFileScanner.exe (PID: 4392)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- su-setup64.exe (PID: 6180)
INFO
Checks supported languages
- SophosSetup.exe (PID: 4980)
- SophosSetup_Stage2.exe (PID: 1432)
- Setup.exe (PID: 5000)
- su-setup64.exe (PID: 2016)
- AVRemoveW.exe (PID: 788)
- AVRemoveW_.exe (PID: 7116)
- SubmitTelem.exe (PID: 6160)
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 6612)
- SEDService.exe (PID: 3908)
- SSPService.exe (PID: 4528)
- su-setup64.exe (PID: 2684)
- McsAgent.exe (PID: 4444)
- McsClient.exe (PID: 6192)
- su-setup64.exe (PID: 3844)
- SophosSSEValidator.exe (PID: 5544)
- su-setup64.exe (PID: 7000)
- SophosFSVerify.exe (PID: 3352)
- SophosFileScanner.exe (PID: 1440)
- SophosFS.exe (PID: 6508)
- SophosFileScanner.exe (PID: 4392)
- su-setup32.exe (PID: 6196)
- SophosHealth.exe (PID: 5084)
- Sophos UI.exe (PID: 3036)
- su-setup64.exe (PID: 1552)
- SophosACSenabledTest.exe (PID: 3568)
- su-setup64.exe (PID: 2524)
- SophosSMEValidator.exe (PID: 6416)
- SophosSMEValidator.exe (PID: 4092)
- SophosSMEValidator.exe (PID: 1452)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 2768)
- su-setup64.exe (PID: 6180)
- SophosNtpService.exe (PID: 5988)
- SophosFileScanner.exe (PID: 6016)
- SophosFileScanner.exe (PID: 6984)
- su-setup64.exe (PID: 5732)
Create files in a temporary directory
- SophosSetup.exe (PID: 4980)
- su-setup64.exe (PID: 2016)
- AVRemoveW_.exe (PID: 7116)
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 6612)
- su-setup64.exe (PID: 2684)
- su-setup64.exe (PID: 3844)
- SophosSSEValidator.exe (PID: 5544)
- su-setup64.exe (PID: 7000)
- su-setup32.exe (PID: 6196)
- su-setup64.exe (PID: 2768)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- SophosSMEValidator.exe (PID: 6416)
- SophosSMEValidator.exe (PID: 1452)
- SophosSMEValidator.exe (PID: 4092)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6180)
Reads product name
- Setup.exe (PID: 5000)
- SophosSetup_Stage2.exe (PID: 1432)
- su-setup64.exe (PID: 2016)
- AVRemoveW.exe (PID: 788)
- AVRemoveW_.exe (PID: 7116)
- SubmitTelem.exe (PID: 6160)
- su-setup64.exe (PID: 6612)
- su-setup64.exe (PID: 2684)
- su-setup64.exe (PID: 6656)
- McsAgent.exe (PID: 4444)
- McsClient.exe (PID: 6192)
- su-setup64.exe (PID: 3844)
- su-setup64.exe (PID: 7000)
- SophosFS.exe (PID: 6508)
- SophosHealth.exe (PID: 5084)
- su-setup64.exe (PID: 2768)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- su-setup64.exe (PID: 6056)
- su-setup32.exe (PID: 6196)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6180)
- SophosNtpService.exe (PID: 5988)
Reads Environment values
- Setup.exe (PID: 5000)
- SophosSetup_Stage2.exe (PID: 1432)
- su-setup64.exe (PID: 2016)
- AVRemoveW.exe (PID: 788)
- AVRemoveW_.exe (PID: 7116)
- SubmitTelem.exe (PID: 6160)
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 6612)
- su-setup64.exe (PID: 2684)
- McsAgent.exe (PID: 4444)
- McsClient.exe (PID: 6192)
- su-setup64.exe (PID: 3844)
- su-setup64.exe (PID: 7000)
- SophosFS.exe (PID: 6508)
- su-setup32.exe (PID: 6196)
- SophosHealth.exe (PID: 5084)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 2768)
- su-setup64.exe (PID: 6180)
- SophosNtpService.exe (PID: 5988)
Reads the software policy settings
- Setup.exe (PID: 5000)
- SophosSetup_Stage2.exe (PID: 1432)
- su-setup64.exe (PID: 2016)
- SubmitTelem.exe (PID: 6160)
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 6612)
- su-setup64.exe (PID: 2684)
- McsClient.exe (PID: 6192)
- McsAgent.exe (PID: 4444)
- su-setup64.exe (PID: 3844)
- SophosSSEValidator.exe (PID: 5544)
- su-setup64.exe (PID: 7000)
- SophosFSVerify.exe (PID: 3352)
- SSPService.exe (PID: 4528)
- SophosFileScanner.exe (PID: 4392)
- su-setup32.exe (PID: 6196)
- su-setup64.exe (PID: 2768)
- Sophos UI.exe (PID: 3036)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- SophosSMEValidator.exe (PID: 6416)
- SophosSMEValidator.exe (PID: 1452)
- su-setup64.exe (PID: 6056)
- SophosSMEValidator.exe (PID: 4092)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6180)
- SophosNtpService.exe (PID: 5988)
- SophosFileScanner.exe (PID: 6984)
Reads the computer name
- SophosSetup_Stage2.exe (PID: 1432)
- Setup.exe (PID: 5000)
- AVRemoveW_.exe (PID: 7116)
- SubmitTelem.exe (PID: 6160)
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 2016)
- SEDService.exe (PID: 3908)
- SSPService.exe (PID: 4528)
- su-setup64.exe (PID: 2684)
- su-setup64.exe (PID: 6612)
- McsAgent.exe (PID: 4444)
- McsClient.exe (PID: 6192)
- su-setup64.exe (PID: 3844)
- su-setup64.exe (PID: 7000)
- SophosFS.exe (PID: 6508)
- SophosFileScanner.exe (PID: 1440)
- SophosFileScanner.exe (PID: 4392)
- su-setup32.exe (PID: 6196)
- SophosHealth.exe (PID: 5084)
- su-setup64.exe (PID: 2768)
- Sophos UI.exe (PID: 3036)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6180)
- SophosFileScanner.exe (PID: 6016)
- SophosNtpService.exe (PID: 5988)
Reads the machine GUID from the registry
- SophosSetup_Stage2.exe (PID: 1432)
- su-setup64.exe (PID: 2016)
- Setup.exe (PID: 5000)
- AVRemoveW.exe (PID: 788)
- AVRemoveW_.exe (PID: 7116)
- su-setup64.exe (PID: 6656)
- SubmitTelem.exe (PID: 6160)
- su-setup64.exe (PID: 6612)
- SSPService.exe (PID: 4528)
- McsAgent.exe (PID: 4444)
- su-setup64.exe (PID: 3844)
- McsClient.exe (PID: 6192)
- SophosSSEValidator.exe (PID: 5544)
- su-setup64.exe (PID: 7000)
- SophosFSVerify.exe (PID: 3352)
- su-setup64.exe (PID: 2684)
- SophosFileScanner.exe (PID: 4392)
- su-setup32.exe (PID: 6196)
- su-setup64.exe (PID: 2768)
- Sophos UI.exe (PID: 3036)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- SophosSMEValidator.exe (PID: 6416)
- SophosSMEValidator.exe (PID: 1452)
- SophosSMEValidator.exe (PID: 4092)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6180)
- SophosNtpService.exe (PID: 5988)
- SophosFileScanner.exe (PID: 6984)
Creates files in the program directory
- SophosSetup_Stage2.exe (PID: 1432)
- Setup.exe (PID: 5000)
- su-setup64.exe (PID: 6656)
- su-setup64.exe (PID: 6612)
- SEDService.exe (PID: 3908)
- su-setup64.exe (PID: 2684)
- McsAgent.exe (PID: 4444)
- McsClient.exe (PID: 6192)
- su-setup64.exe (PID: 3844)
- SSPService.exe (PID: 4528)
- su-setup64.exe (PID: 7000)
- SophosFS.exe (PID: 6508)
- SophosFileScanner.exe (PID: 1440)
- su-setup32.exe (PID: 6196)
- SophosHealth.exe (PID: 5084)
- su-setup64.exe (PID: 2768)
- su-setup64.exe (PID: 1552)
- su-setup64.exe (PID: 2524)
- su-setup64.exe (PID: 6056)
- su-setup64.exe (PID: 5732)
- su-setup64.exe (PID: 6180)
- SophosNtpService.exe (PID: 5988)
- SophosFileScanner.exe (PID: 6016)
Checks operating system version
- AVRemoveW_.exe (PID: 7116)
Sends debugging messages
- McsAgent.exe (PID: 4444)
Manual execution by a user
- Sophos UI.exe (PID: 3036)
The process uses the downloaded file
- Sophos UI.exe (PID: 3036)
Creates files or folders in the user directory
- Sophos UI.exe (PID: 3036)
Checks proxy server information
- Sophos UI.exe (PID: 3036)
Potential remote process memory writing (Base64 Encoded 'WriteProcessMemory')
- SophosFileScanner.exe (PID: 4392)
Potential remote process memory interaction (Base64 Encoded 'VirtualAllocEx')
- SophosFileScanner.exe (PID: 4392)
UPX packer has been detected
- SophosFileScanner.exe (PID: 4392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:09:28 10:25:25+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 222720 |
| InitializedDataSize: | 1691136 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x18b30 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.19.68.0 |
| ProductVersionNumber: | 1.19.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| Comments: | 97effa424f4e21045f696c40951b8920511ef4b4 |
| CompanyName: | Sophos Limited |
| FileDescription: | Sophos Setup |
| FileVersion: | 1.19.68.0 |
| InternalName: | SophosSetup.exe |
| LegalCopyright: | Copyright 1989-2023 Sophos Limited. All rights reserved. |
| OriginalFileName: | SophosSetup.exe |
| ProductName: | Sophos Setup |
| ProductVersion: | 1.19 |
Total processes
188
Monitored processes
57
Malicious processes
28
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | su-setup64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | su-setup64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 788 | avremovew.exe -f | C:\ProgramData\Sophos\AutoUpdate\Cache\decoded\crt\crt\AVRemoveW.exe | — | su-setup64.exe | |||||||||||
User: admin Company: Sophos Limited Integrity Level: HIGH Description: Sophos Third-Party Security Software Removal Launcher Exit code: 10 Version: 2.24.0.48 Modules
| |||||||||||||||
| 1232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | su-setup64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1432 | "C:\Program Files (x86)\Sophos\CloudInstaller\SophosSetup_Stage2.exe" --mgmtserver="mcs2-cloudstation-us-west-2.prod.hydra.sophos.com" --telemserver="t1.sophosupd.com" --diagserver="installer1.sophosupd.com" --logfile="C:\ProgramData\Sophos\CloudInstaller\Logs\SophosCloudInstaller_20240906_135450.log" --parentpid="5000" --products="all" --customertoken="fe1fb507-068d-45ff-a609-416ef2f963a7" --pipewritehandle="1732" --mcscustomerid="7abd7a54-7a0b-f42a-5a5d-8ffcfea83c5f" | C:\Program Files (x86)\Sophos\CloudInstaller\SophosSetup_Stage2.exe | Setup.exe | ||||||||||||
User: admin Company: Sophos Limited Integrity Level: HIGH Description: Sophos Setup Version: 1.20.627.0 Modules
| |||||||||||||||
| 1440 | "C:\Program Files\Sophos\Sophos File Scanner\SophosFileScanner.exe" --host --engine-path "C:\Program Files\Sophos\Sophos Standalone Engine\engine1\engine\17256311603169423" --data-path "C:\Program Files\Sophos\Sophos Standalone Engine\engine1\data\17256311603169423" --process-registry-key "SOFTWARE\Sophos\Sophos File Scanner\Scanner" --log-level 3 --log-request 3 --log-scan-summaries 3 --memory-scan-send-integer-properties-to-ssp --scan-dispatcher-config-path "C:\ProgramData\Sophos\Sophos File Scanner\Drop\scan_dispatcher_config_17256311706577977.json" | C:\Program Files\Sophos\Sophos File Scanner\SophosFileScanner.exe | — | SophosFS.exe | |||||||||||
User: LOCAL SERVICE Company: Sophos Limited Integrity Level: SYSTEM Description: Sophos File Scanner Version: 1.12.0.419 Modules
| |||||||||||||||
| 1452 | "C:\ProgramData\Sophos\AutoUpdate\Cache\decoded\sme64\SophosSMEValidator.exe" "C:\Program Files\Sophos\Sophos ML Engine\ML1\scan\17256311794159709" | C:\ProgramData\Sophos\AutoUpdate\Cache\decoded\sme64\SophosSMEValidator.exe | — | su-setup64.exe | |||||||||||
User: admin Company: Sophos Limited Integrity Level: HIGH Description: Sophos ML Engine validator tool Exit code: 0 Version: 1.9.0.154 Modules
| |||||||||||||||
| 1552 | "C:\Program Files (x86)\Sophos\CloudInstaller\su-setup64.exe" --quiet | C:\Program Files (x86)\Sophos\CloudInstaller\su-setup64.exe | SophosSetup_Stage2.exe | ||||||||||||
User: admin Company: Sophos Limited Integrity Level: HIGH Description: Sophos Update 64-bit Setup Runner Exit code: 0 Version: 6.17.985 Modules
| |||||||||||||||
| 2016 | "C:\Program Files (x86)\Sophos\CloudInstaller\su-setup64.exe" --quiet | C:\Program Files (x86)\Sophos\CloudInstaller\su-setup64.exe | — | SophosSetup_Stage2.exe | |||||||||||
User: admin Company: Sophos Limited Integrity Level: HIGH Description: Sophos Update 64-bit Setup Runner Exit code: 0 Version: 6.17.985 Modules
| |||||||||||||||
| 2224 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
132 631
Read events
130 378
Write events
2 190
Delete events
63
Modification events
| (PID) Process: | (1432) SophosSetup_Stage2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Sophos Endpoint Defense\TamperProtection\Components\INSTALLER |
| Operation: | write | Name: | IntegrityPath |
Value: C:\Program Files (x86)\Sophos\CloudInstaller\integrity.dat | |||
| (PID) Process: | (1432) SophosSetup_Stage2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Sophos Endpoint Defense\TamperProtection\Components\INSTALLER |
| Operation: | delete value | Name: | IntegrityDat |
Value: | |||
| (PID) Process: | (1432) SophosSetup_Stage2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Sophos Endpoint Defense\TamperProtection\Components\INSTALLER |
| Operation: | write | Name: | Enable |
Value: 1 | |||
| (PID) Process: | (1432) SophosSetup_Stage2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Sophos\Health\CloudInstaller |
| Operation: | write | Name: | IsInstalling |
Value: 1 | |||
| (PID) Process: | (1432) SophosSetup_Stage2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Sophos\AutoUpdate\UpdateStatus |
| Operation: | write | Name: | BlockUpdates |
Value: 1 | |||
| (PID) Process: | (1432) SophosSetup_Stage2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Sophos\AutoUpdate\UpdateStatus |
| Operation: | delete value | Name: | LastSyncedTime |
Value: | |||
| (PID) Process: | (1432) SophosSetup_Stage2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Sophos\AutoUpdate |
| Operation: | write | Name: | InstallIncomplete |
Value: 1 | |||
| (PID) Process: | (1432) SophosSetup_Stage2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\Authority\20240906135852737617 |
| Operation: | write | Name: | deviceId |
Value: bd654f96-e7fa-4b20-ae86-4f0d3a2d670f | |||
| (PID) Process: | (1432) SophosSetup_Stage2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\Authority\20240906135852737617 |
| Operation: | write | Name: | registration_token |
Value: a5ac962cc8b9ef00248f03a82a1d795c9ea3c0c2b0a9b8b1da378ed33df2a2dd | |||
| (PID) Process: | (1432) SophosSetup_Stage2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Sophos\Management\Policy\Authority\20240906135852737617 |
| Operation: | write | Name: | tenantId |
Value: a7dba745-a7b0-4fa2-a5d5-f8cfef8ac3f5 | |||
Executable files
835
Suspicious files
1 013
Text files
563
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4980 | SophosSetup.exe | C:\Users\admin\AppData\Local\Temp\SophosSetup-1312736932\Setup.exe | executable | |
MD5:B1F1713363836FED82DECB69491D43EF | SHA256:4DC3519F3730EB371CDA898A7C654EC53BD776EF75B7A7DC011F006D526469A5 | |||
| 5000 | Setup.exe | C:\Program Files (x86)\Sophos\CloudInstaller\extract_cache\SophosSetup_Stage2.exe | executable | |
MD5:6DBD0BF768ED7B5A5E44A4F464B15217 | SHA256:04E1E91E63BE94ACBD09112A6A243EFBB9B4E74460DD9DA02857038EFF85F699 | |||
| 5000 | Setup.exe | C:\Program Files (x86)\Sophos\CloudInstaller\extract_cache\Management Certs\sophosca1.crl | binary | |
MD5:48AD0FBB2E473628CA6FBE5F40C1B335 | SHA256:3484FE4376803D32C56BA6A850D330651BE49E4B69E4DE901B2100A80C25D9B9 | |||
| 5000 | Setup.exe | C:\Program Files (x86)\Sophos\CloudInstaller\extract_cache\manifest.dat | text | |
MD5:ADD8231F11AA4A797916BC642E1B9E94 | SHA256:389B4639DFD5C5D9EE169A586B532C184DF7EAA0597E05C1F77452D54A33A792 | |||
| 5000 | Setup.exe | C:\Program Files (x86)\Sophos\CloudInstaller\extract_cache\integrity.dat | text | |
MD5:D84CDD1D0AA7AF11461FD904A2F8C361 | SHA256:955918CA902367F9AE06828CC12344A9B953E5F06CD28E9E90BCB874CEDEB556 | |||
| 5000 | Setup.exe | C:\ProgramData\Sophos\CloudInstaller\Logs\SophosCloudInstaller_20240906_135450.log | text | |
MD5:851D7409C68228DD3FD790F7AFEB5232 | SHA256:33DA4DAADB329FAEAEC8F208C12D058604B92E19C160AFE8D3BEDE30557D872A | |||
| 5000 | Setup.exe | C:\Program Files (x86)\Sophos\CloudInstaller\extract_cache\SDDS3.dll | executable | |
MD5:1EC8B54B89D8545B6CAC00D9AC39EF5E | SHA256:2B0597513F71360AAC78F047C75A16C7693BBC50925587777D001A924849A9FD | |||
| 5000 | Setup.exe | C:\Program Files (x86)\Sophos\CloudInstaller\extract_cache\Management Certs\sophosca2.crl | der | |
MD5:4512CDDF97293CA04BAFF2337DA700B6 | SHA256:DE2C59C12A1774610B6C0952ADE122028F892DC14BC6B568A44B2220897320D7 | |||
| 5000 | Setup.exe | C:\Program Files (x86)\Sophos\CloudInstaller\extract_cache\Management Certs\sophosca2.crt | binary | |
MD5:450B9D35C9A0B33F80D9E8FAA29A260A | SHA256:92E6CCBE80F31DB683E4C331B599EFC91E593365AF8895504A9360C087060D44 | |||
| 5000 | Setup.exe | C:\Program Files (x86)\Sophos\CloudInstaller\extract_cache\Management Certs\sophosca4.crt | binary | |
MD5:150C183892DE69BDCBEA89E8F59AC9DA | SHA256:4D44A6BA0CE8FC3771C6BC95D385AAA944AABDCD2D908D87EF5CA20418BF5D90 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
44
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2248 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3036 | Sophos UI.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
3036 | Sophos UI.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6208 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1496 | SIHClient.exe | GET | 200 | 72.246.169.155:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1496 | SIHClient.exe | GET | 200 | 72.246.169.155:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3036 | Sophos UI.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAnKajHVVe7kGFMvSuSsOMs%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6160 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2248 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5000 | Setup.exe | 44.233.234.86:443 | dzr-api-amzn-us-west-2-fa88.api-upe.p.hmr.sophos.com | AMAZON-02 | US | suspicious |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5000 | Setup.exe | 88.221.125.144:443 | downloads.sophos.com | AKAMAI-AS | DE | suspicious |
6208 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6208 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1432 | SophosSetup_Stage2.exe | 54.218.59.181:443 | mcs2-cloudstation-us-west-2.prod.hydra.sophos.com | AMAZON-02 | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
dzr-api-amzn-us-west-2-fa88.api-upe.p.hmr.sophos.com |
| unknown |
client.wns.windows.com |
| whitelisted |
downloads.sophos.com |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
mcs2-cloudstation-us-west-2.prod.hydra.sophos.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
McsAgent.exe | CorcAdapter entering DllMain
|
McsAgent.exe | CorcAdapter attaching process
|
McsAgent.exe | CorcAdapter leaving DllMain
|
McsAgent.exe | CoreEndpointAdapter entering DllMain
|
McsAgent.exe | CoreEndpointAdapter attaching process
|
McsAgent.exe | CoreEndpointAdapter leaving DllMain
|
McsAgent.exe | CorcAdapter entering DllMain
|
McsAgent.exe | CorcAdapter attaching thread
|
McsAgent.exe | CorcAdapter leaving DllMain
|
McsAgent.exe | CoreEndpointAdapter entering DllMain
|