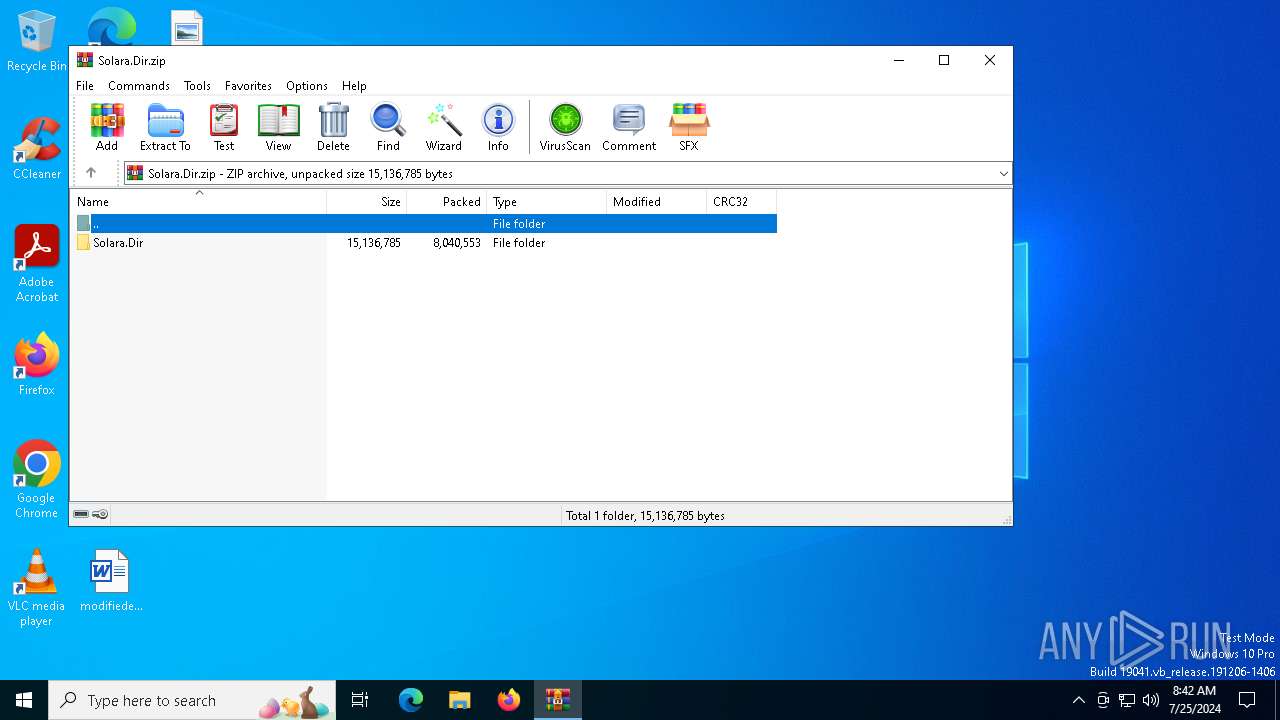
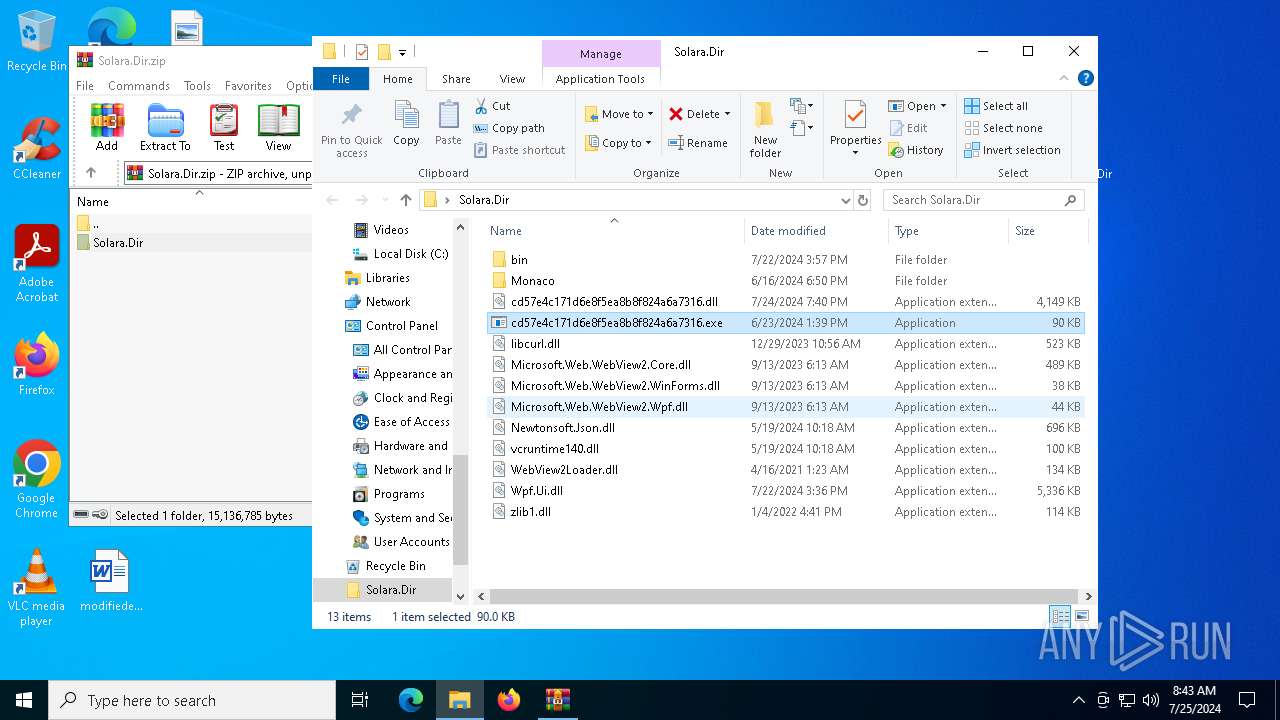
| download: | /quivings/Solara/raw/main/Files/Solara.Dir.zip |
| Full analysis: | https://app.any.run/tasks/4eee18d1-78cc-4a16-9eae-7cdaf0991579 |
| Verdict: | Malicious activity |
| Analysis date: | July 25, 2024, 08:42:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 9BD9AA90323438A6CBADE4596D16C5AA |
| SHA1: | AF3E64847DB76B914B7037EE6B14CD1F989F9706 |
| SHA256: | DEAC87399F24746CAE8CB22ED13B0BF87B505D7F47FE298C04AC7E780A670BE5 |
| SSDEEP: | 98304:7LslEynX9VIYkSSKXYYaJKvyZYBkpdCBLTrEwUlf/scQsGzrNySepwxnPK0qyZ/q:L2LC+6MJh3UPB |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4052)
Reads security settings of Internet Explorer
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
Reads the BIOS version
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
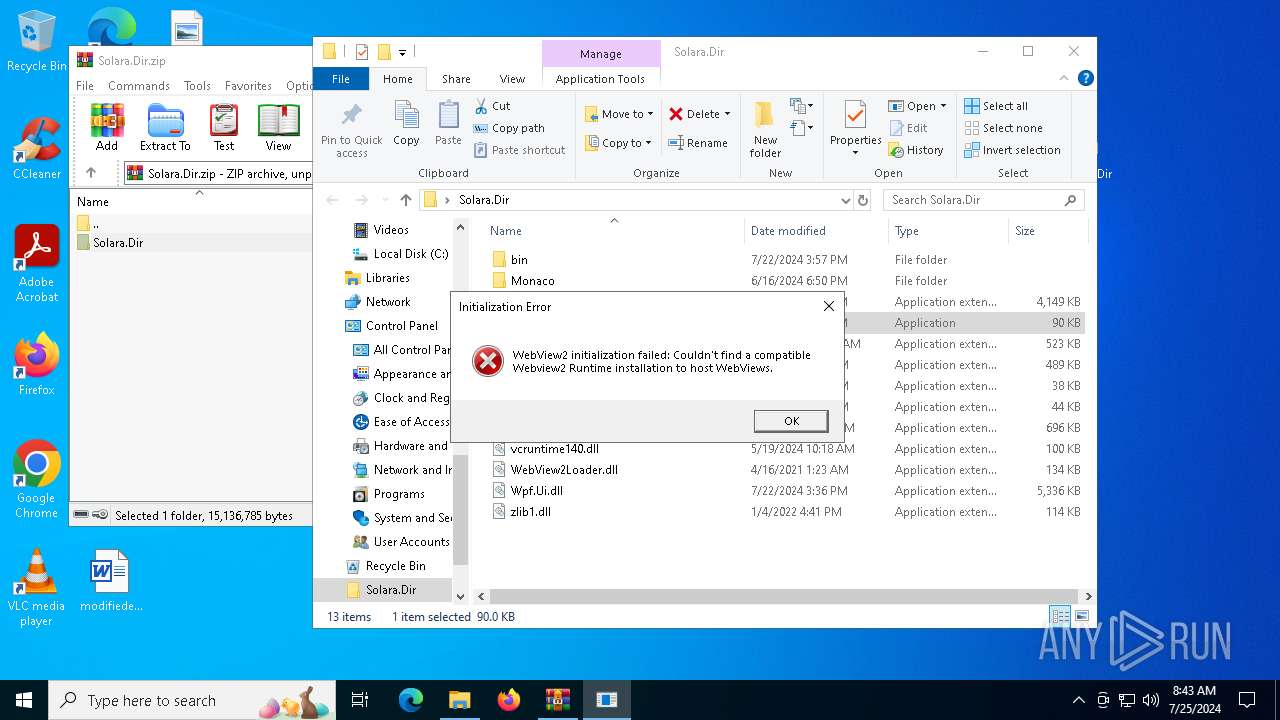
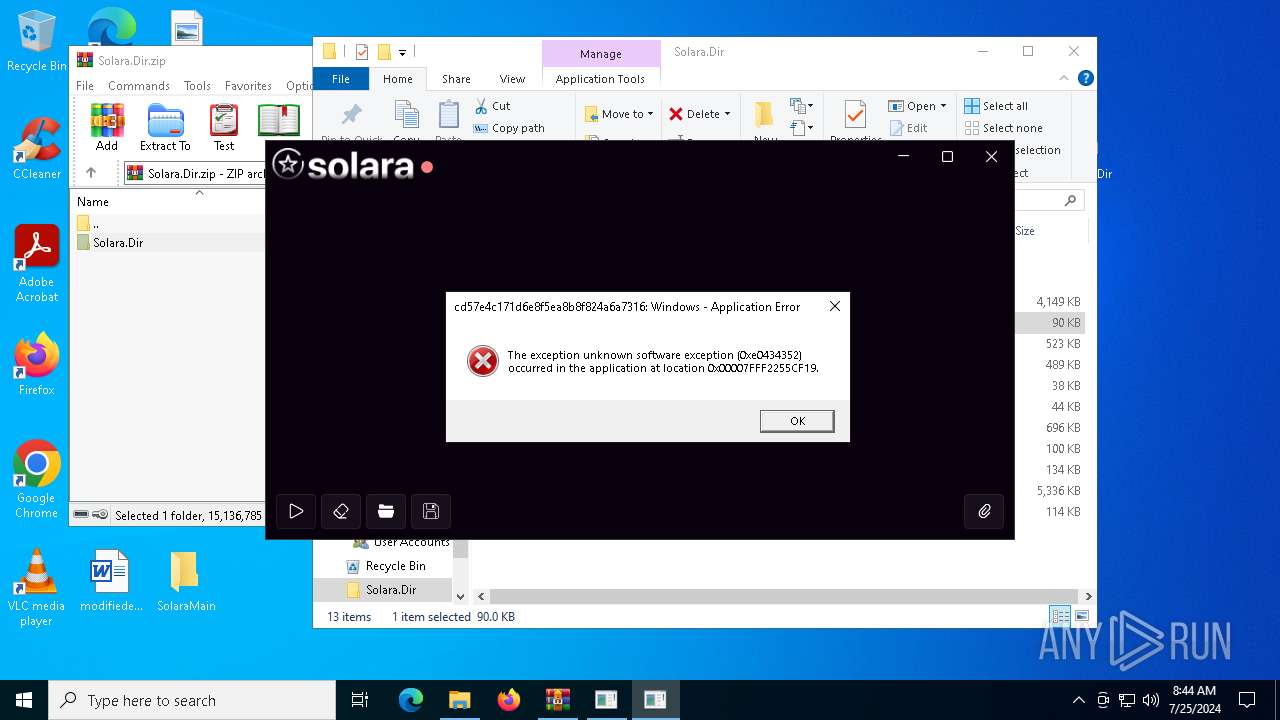
Executes application which crashes
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 3008)
INFO
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 4052)
Disables trace logs
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 3008)
Checks supported languages
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 3008)
Manual execution by a user
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 3008)
Reads Environment values
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 3008)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4052)
Checks proxy server information
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
- slui.exe (PID: 4028)
- WerFault.exe (PID: 5740)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 3008)
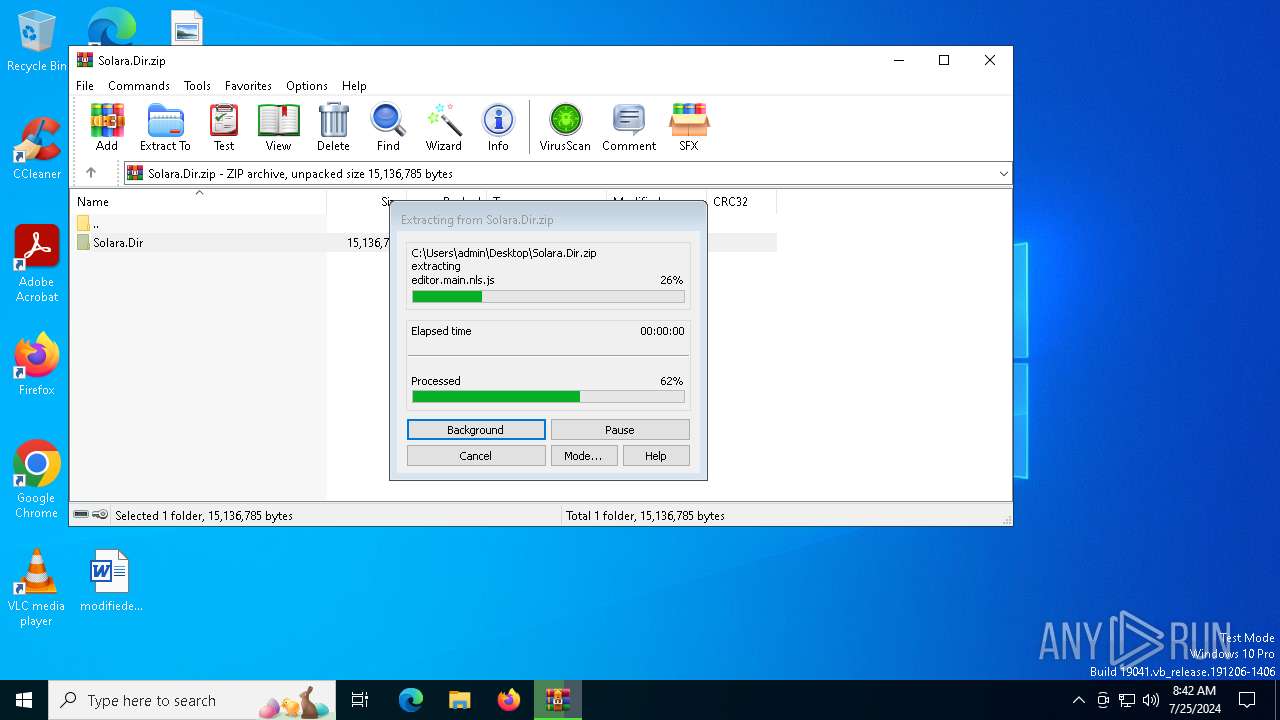
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4052)
Reads the machine GUID from the registry
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 3008)
Reads the software policy settings
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
- slui.exe (PID: 4028)
- WerFault.exe (PID: 5740)
Reads the computer name
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 3008)
Create files in a temporary directory
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
Themida protector has been detected
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 6636)
Creates files or folders in the user directory
- WerFault.exe (PID: 5740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:07:22 15:57:44 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
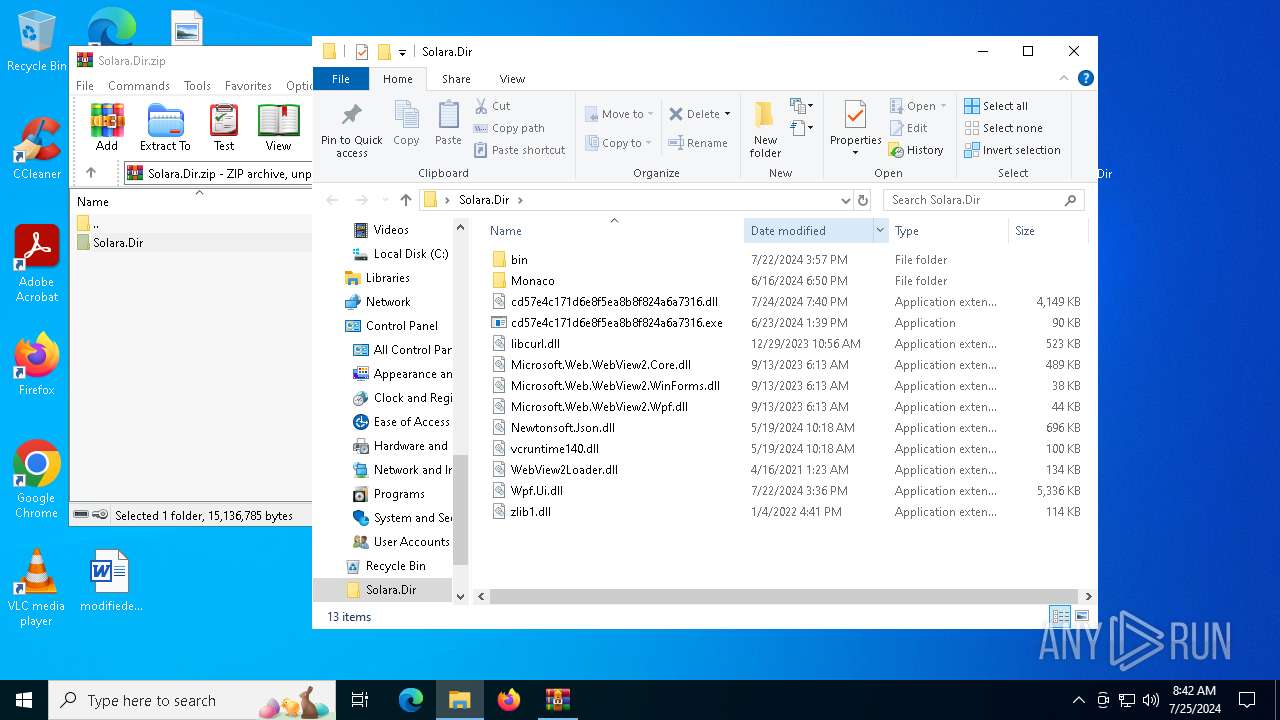
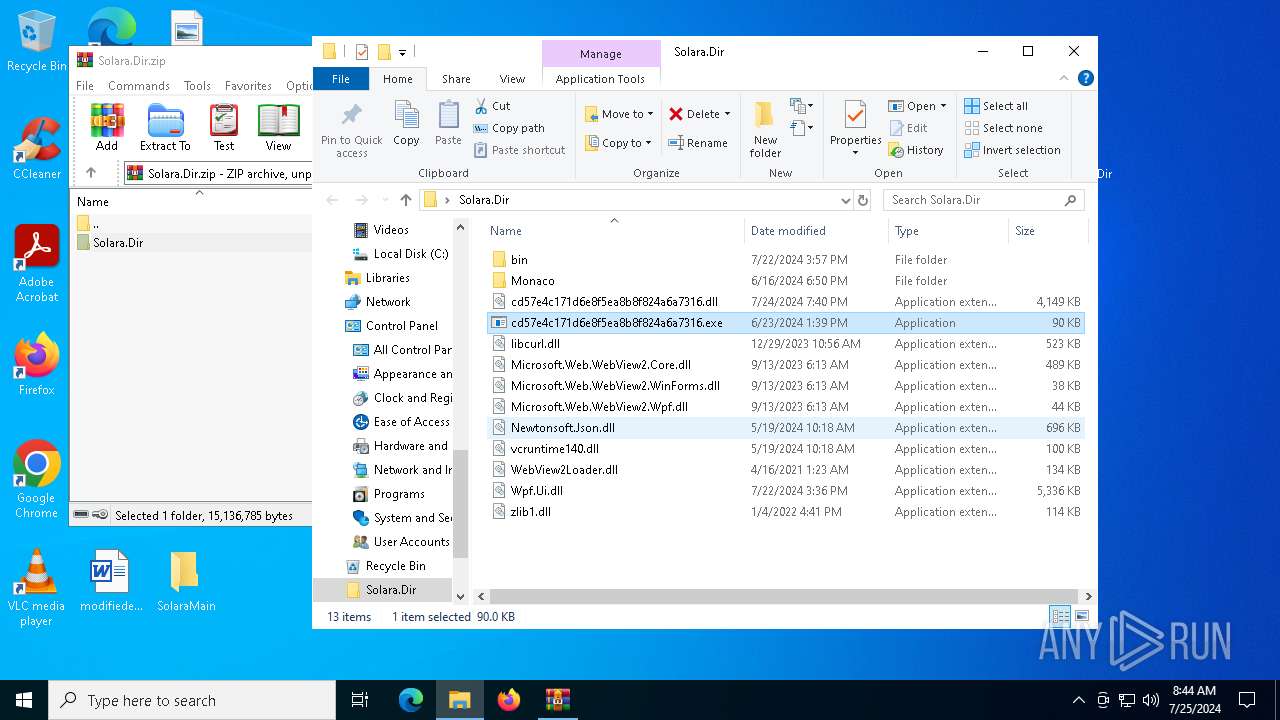
| ZipFileName: | Solara.Dir/bin/ |
Total processes
145
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
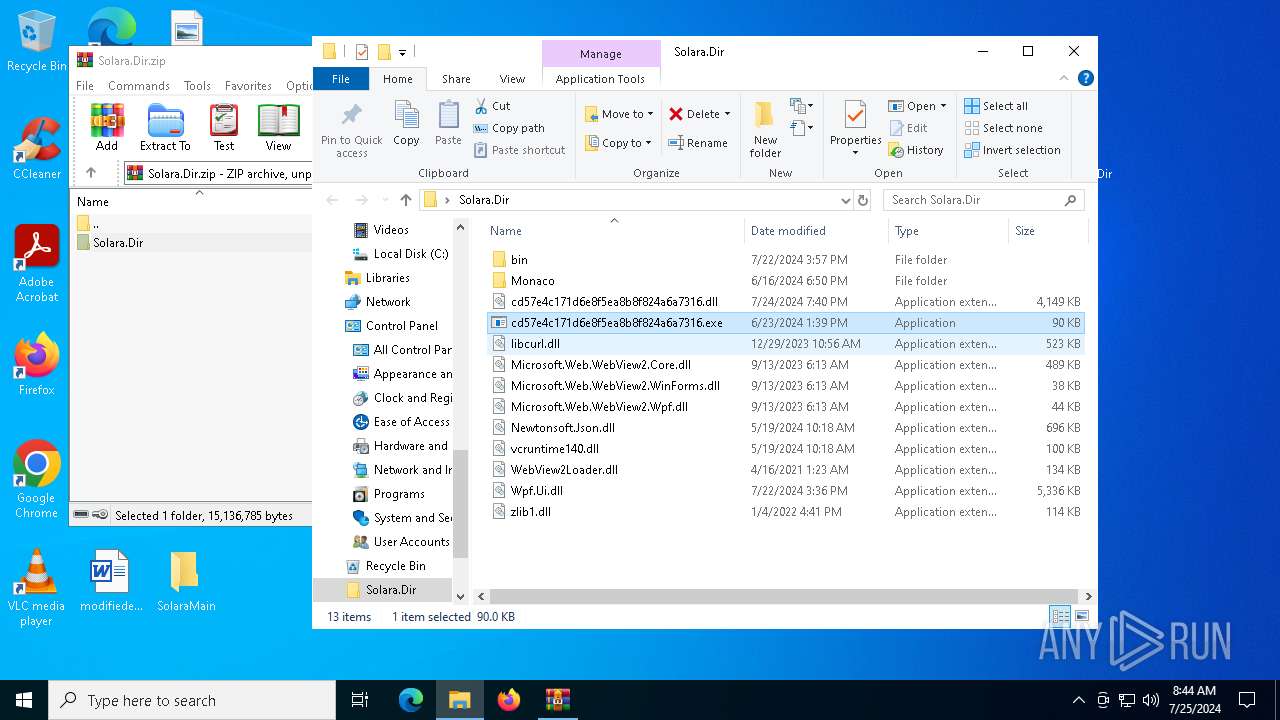
| 3008 | "C:\Users\admin\Desktop\Solara.Dir\cd57e4c171d6e8f5ea8b8f824a6a7316.exe" | C:\Users\admin\Desktop\Solara.Dir\cd57e4c171d6e8f5ea8b8f824a6a7316.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WpfApp1 Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4028 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4052 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Solara.Dir.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4584 | C:\WINDOWS\system32\WerFault.exe -u -p 6636 -s 2596 | C:\Windows\System32\WerFault.exe | — | cd57e4c171d6e8f5ea8b8f824a6a7316.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 2147942405 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5200 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5740 | C:\WINDOWS\system32\WerFault.exe -u -p 3008 -s 1812 | C:\Windows\System32\WerFault.exe | cd57e4c171d6e8f5ea8b8f824a6a7316.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6636 | "C:\Users\admin\Desktop\Solara.Dir\cd57e4c171d6e8f5ea8b8f824a6a7316.exe" | C:\Users\admin\Desktop\Solara.Dir\cd57e4c171d6e8f5ea8b8f824a6a7316.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WpfApp1 Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
9 788
Read events
9 766
Write events
22
Delete events
0
Modification events
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Solara.Dir.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6636) cd57e4c171d6e8f5ea8b8f824a6a7316.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\cd57e4c171d6e8f5ea8b8f824a6a7316_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6636) cd57e4c171d6e8f5ea8b8f824a6a7316.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\cd57e4c171d6e8f5ea8b8f824a6a7316_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
11
Suspicious files
170
Text files
19
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.28464\Solara.Dir\cd57e4c171d6e8f5ea8b8f824a6a7316.dll | executable | |
MD5:A9F04DA45768D32D110BCC28E8EEC17B | SHA256:0FE02773D86518849BBC8EC1964F642B2B5C75249056C8600E43815E39FB18D5 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.28464\Solara.Dir\Microsoft.Web.WebView2.WinForms.dll | executable | |
MD5:4CF94FFA50FD9BDC0BB93CCEAEDE0629 | SHA256:50B2E46C99076F6FA9C33E0A98F0FE3A2809A7C647BB509066E58F4C7685D7E6 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.28464\Solara.Dir\cd57e4c171d6e8f5ea8b8f824a6a7316.exe | executable | |
MD5:D84E7F79F4F0D7074802D2D6E6F3579E | SHA256:DCFC2B4FA3185DF415855EC54395D9C36612F68100D046D8C69659DA01F7D227 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.28464\Solara.Dir\bin\version.txt | text | |
MD5:73CDF608D1EE898D0B5EF68F1869A851 | SHA256:853A9A75B07E44C4A4117630D67A4C1EB7CED7B45C72BB6C13CAF2CA2AB338ED | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.28464\Solara.Dir\Microsoft.Web.WebView2.Wpf.dll | executable | |
MD5:34EC990ED346EC6A4F14841B12280C20 | SHA256:1E987B22CD011E4396A0805C73539586B67DF172DF75E3DDED16A77D31850409 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.28464\Solara.Dir\Monaco\fileaccess\node_modules\array-flatten\array-flatten.js | binary | |
MD5:4B17FA06C54846B686B8B799E9DD253A | SHA256:766CA145B6D25E3D60F352A716E8FA1876BCDF362C0767C360CF24F335BC281E | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.28464\Solara.Dir\Monaco\fileaccess\node_modules\accepts\package.json | binary | |
MD5:32A15D6909FCAE63E52D8664593D32D5 | SHA256:E5716D5D939DB08C5C28EC6AE86ED67BE5320F91089E2673FCA1C5B876E57AA3 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.28464\Solara.Dir\Monaco\fileaccess\node_modules\body-parser\lib\types\json.js | text | |
MD5:6B036408F968978BF9668496DB9953BA | SHA256:44F8B529333004E2AAFF6DB3A1DBE7068F1AC5FA1173E9634686A78C2262AF35 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.28464\Solara.Dir\Monaco\fileaccess\node_modules\body-parser\package.json | binary | |
MD5:826BD4315438573BA1A6D88AE2A2AA65 | SHA256:0FD31AD69FDCF1E2A94530F9DB9C93E96709B690393A14711643123F678EE956 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.28464\Solara.Dir\Monaco\fileaccess\node_modules\body-parser\lib\read.js | binary | |
MD5:C148BB38C59CE266E271C96AB1F2D192 | SHA256:1E9E274755366C39AE70E8B9A7A42FC12219566E67EFAF9B7EBC2A8B337F5B6B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
54
DNS requests
24
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
5664 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7164 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6132 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3108 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4204 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3108 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6636 | cd57e4c171d6e8f5ea8b8f824a6a7316.exe | 128.116.44.4:443 | clientsettings.roblox.com | ROBLOX-PRODUCTION | US | malicious |
6636 | cd57e4c171d6e8f5ea8b8f824a6a7316.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
clientsettings.roblox.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2284 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |