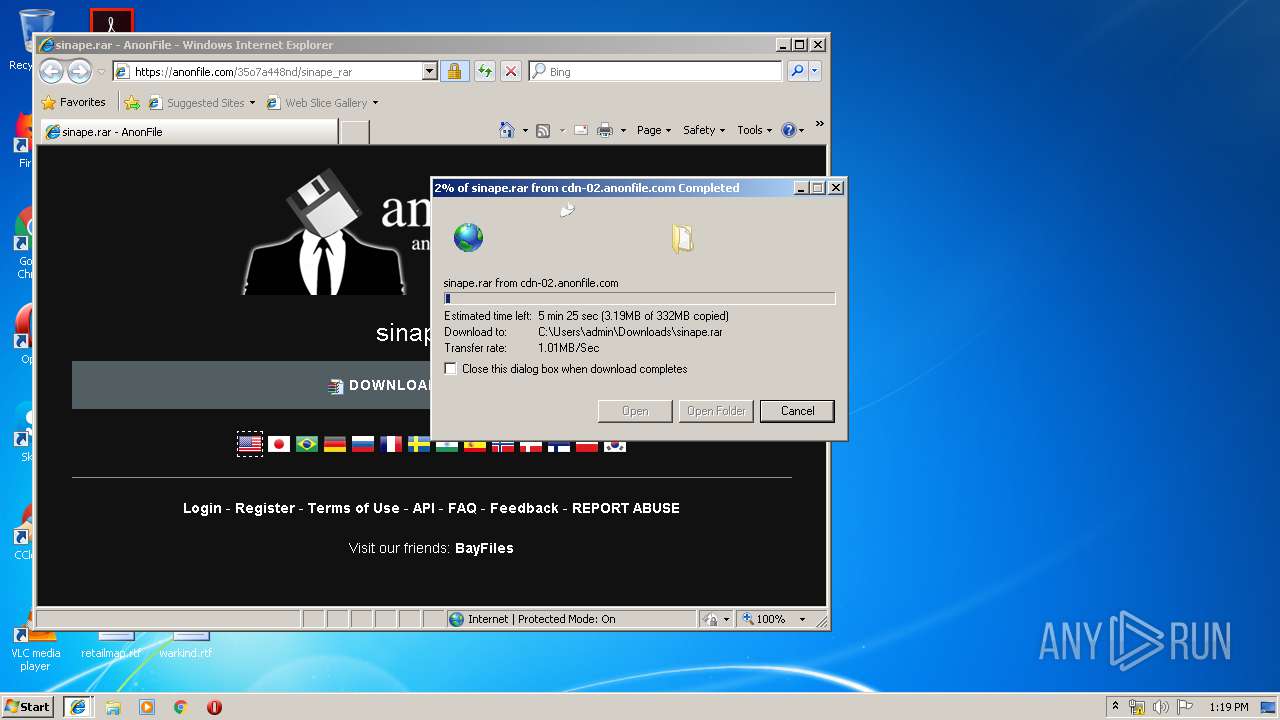
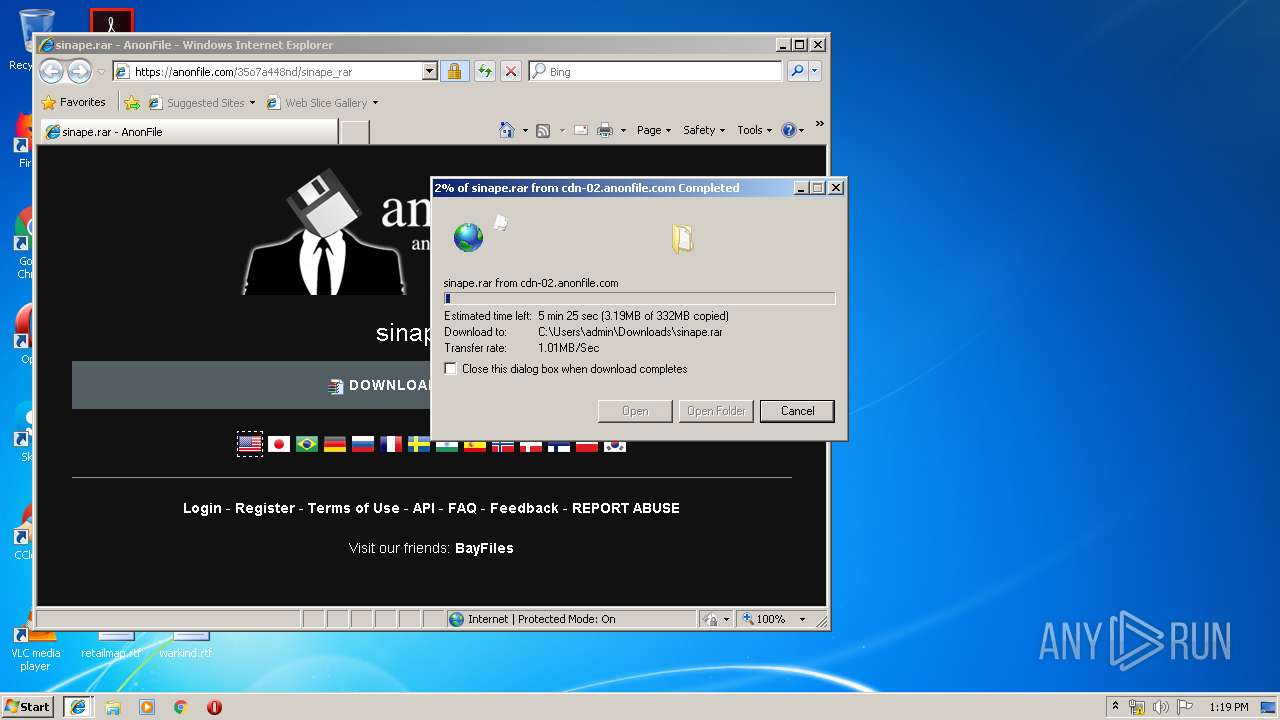
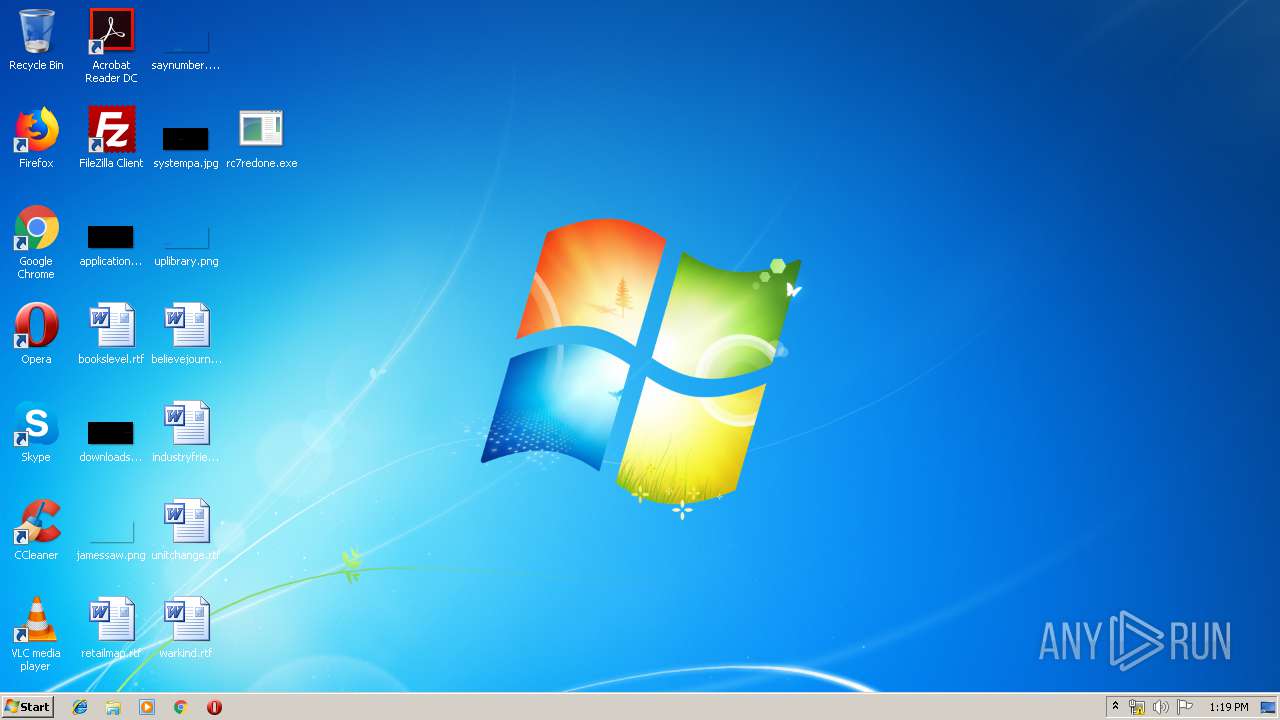
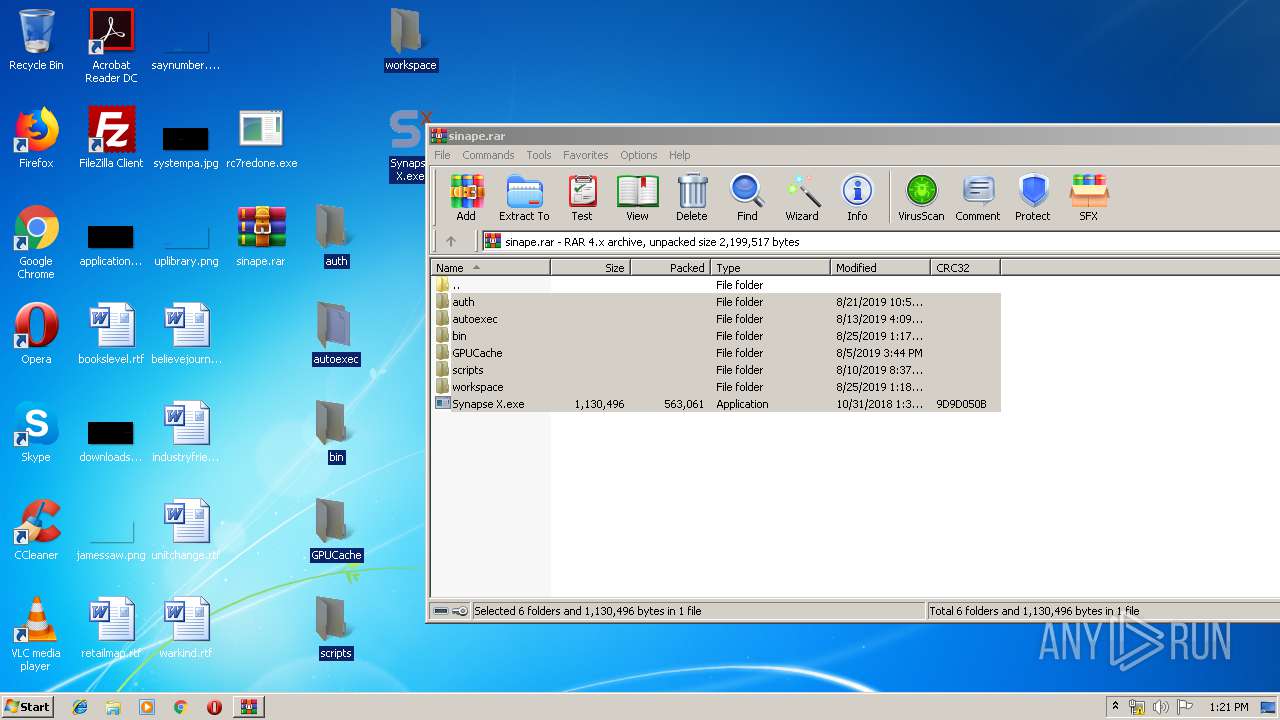
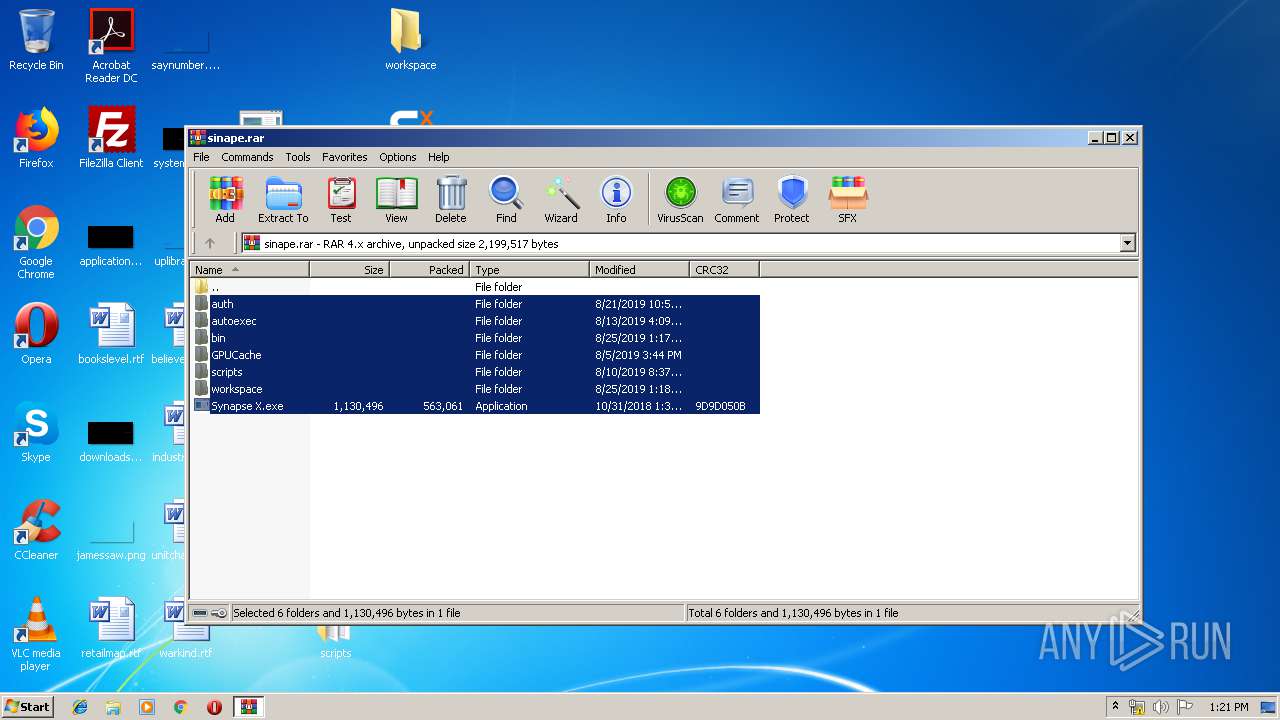
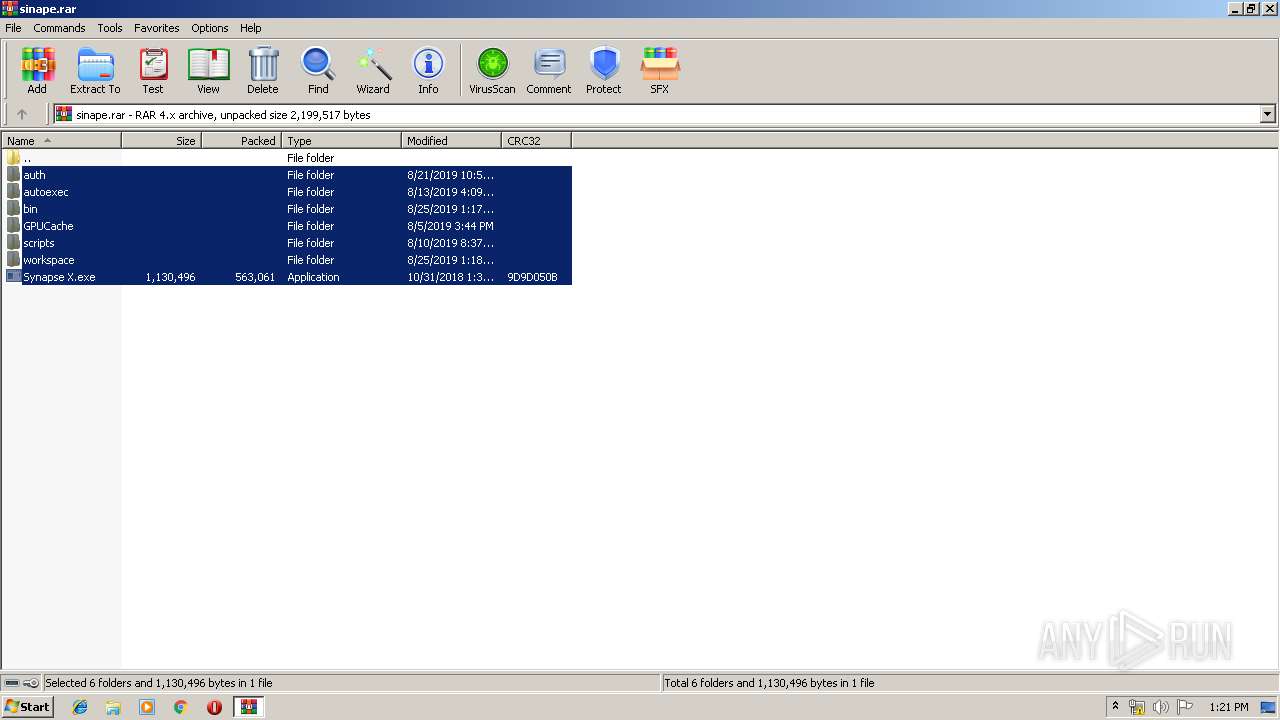
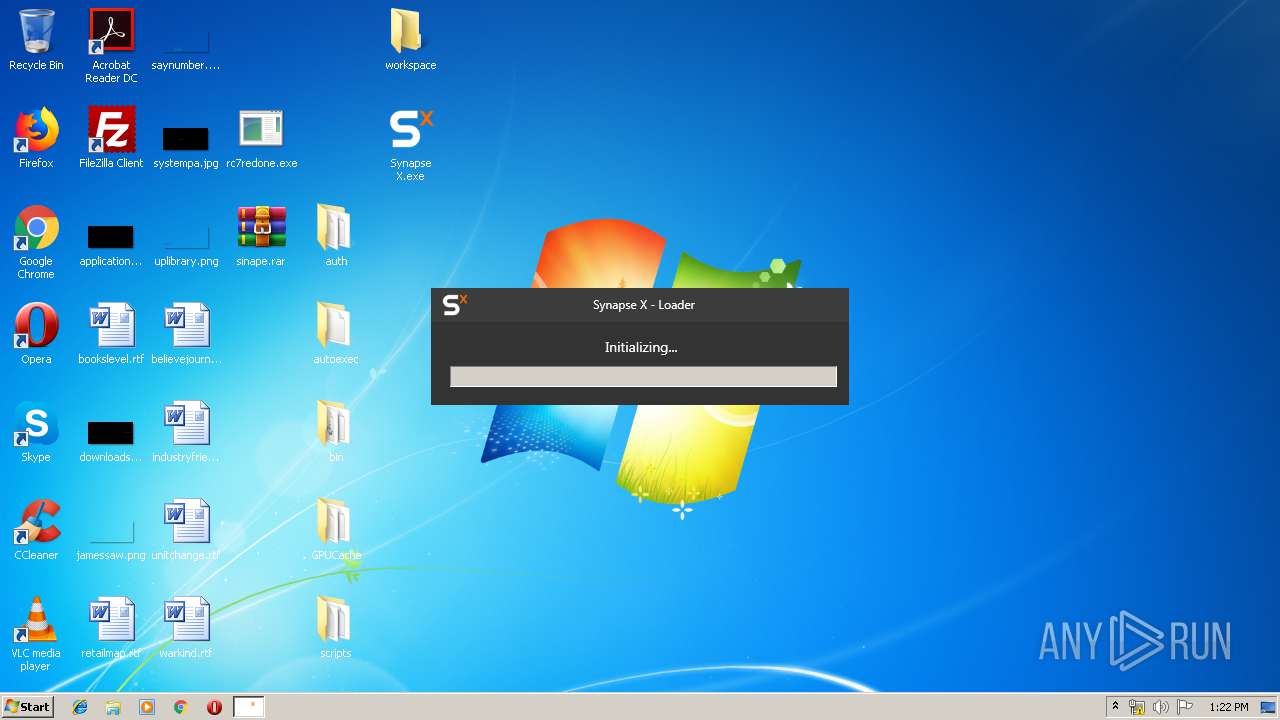
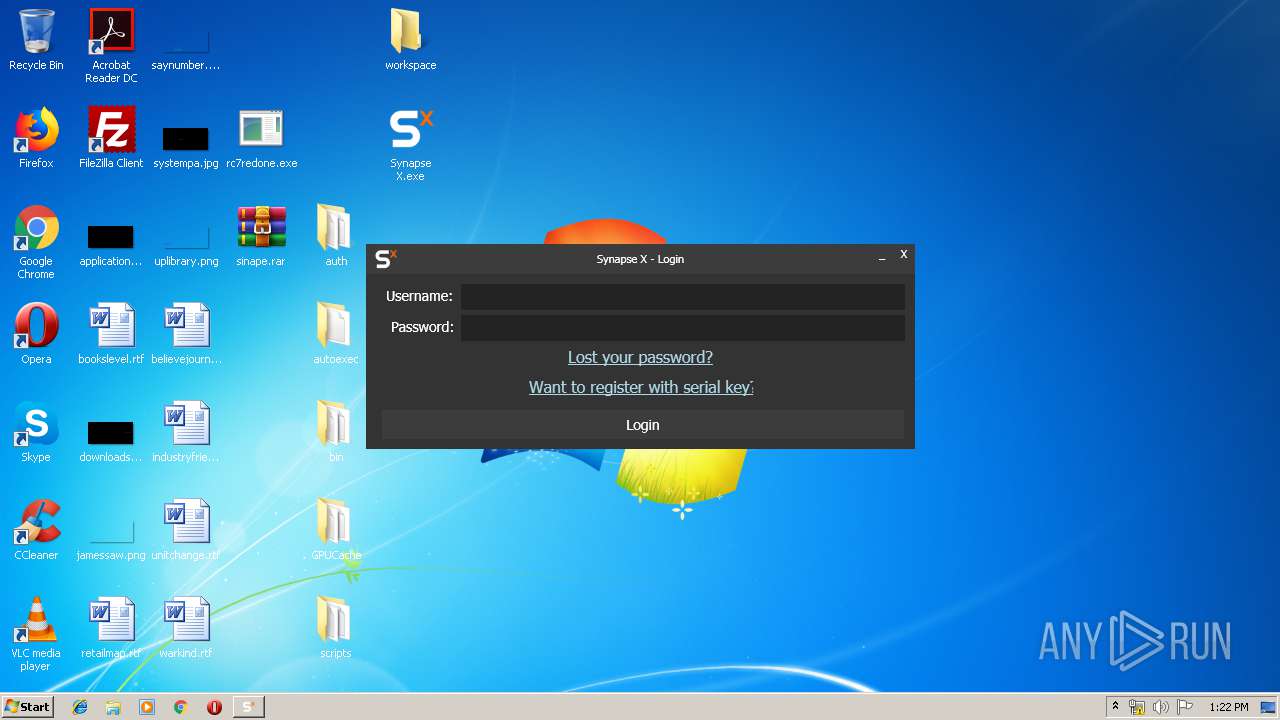
| download: | rc7redone.exe |
| Full analysis: | https://app.any.run/tasks/86248556-094c-4d9d-b3e0-d6422b02df06 |
| Verdict: | Malicious activity |
| Analysis date: | August 25, 2019, 12:17:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 66A2244A5BECC91366D927006D5C2967 |
| SHA1: | 05AE7F9E6D81AF1B9B0BB3834BC8B20C8DE6C4B1 |
| SHA256: | DEA04AE20524D1F51505011B6C2E2D56321D986D26D2A1CD5BB34FDEA78B62E9 |
| SSDEEP: | 3072:mOxN8/IiSA6zxXhx+Gvp+GVZ5IyPPPTVBCWmk0hhhhhhhhhhhhhhhhhhhhhhhh2Y:mOxXjvpxZ/PPPTVBjteH |
MALICIOUS
Application was dropped or rewritten from another process
- Synapse X.exe (PID: 3120)
- C7FB8689DFEAC65B.bin (PID: 2756)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2408)
- C7FB8689DFEAC65B.bin (PID: 2756)
SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1764)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2460)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3604)
- Synapse X.exe (PID: 3120)
Starts application with an unusual extension
- Synapse X.exe (PID: 3120)
Reads the BIOS version
- C7FB8689DFEAC65B.bin (PID: 2756)
Reads Environment values
- C7FB8689DFEAC65B.bin (PID: 2756)
INFO
Manual execution by user
- explorer.exe (PID: 3704)
- iexplore.exe (PID: 3148)
- iexplore.exe (PID: 3648)
- WinRAR.exe (PID: 3604)
- rc7redone.exe (PID: 2176)
- explorer.exe (PID: 2636)
- rc7redone.exe (PID: 1348)
- Synapse X.exe (PID: 3120)
Changes internet zones settings
- iexplore.exe (PID: 3148)
- iexplore.exe (PID: 3648)
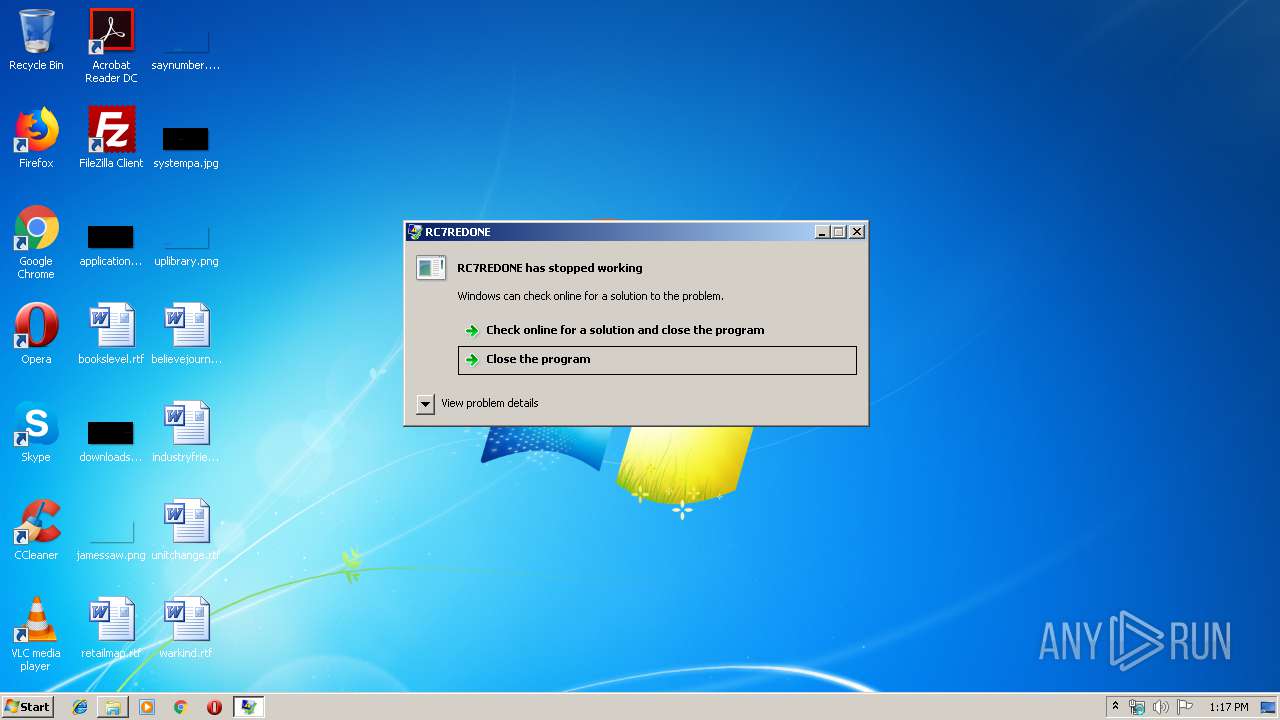
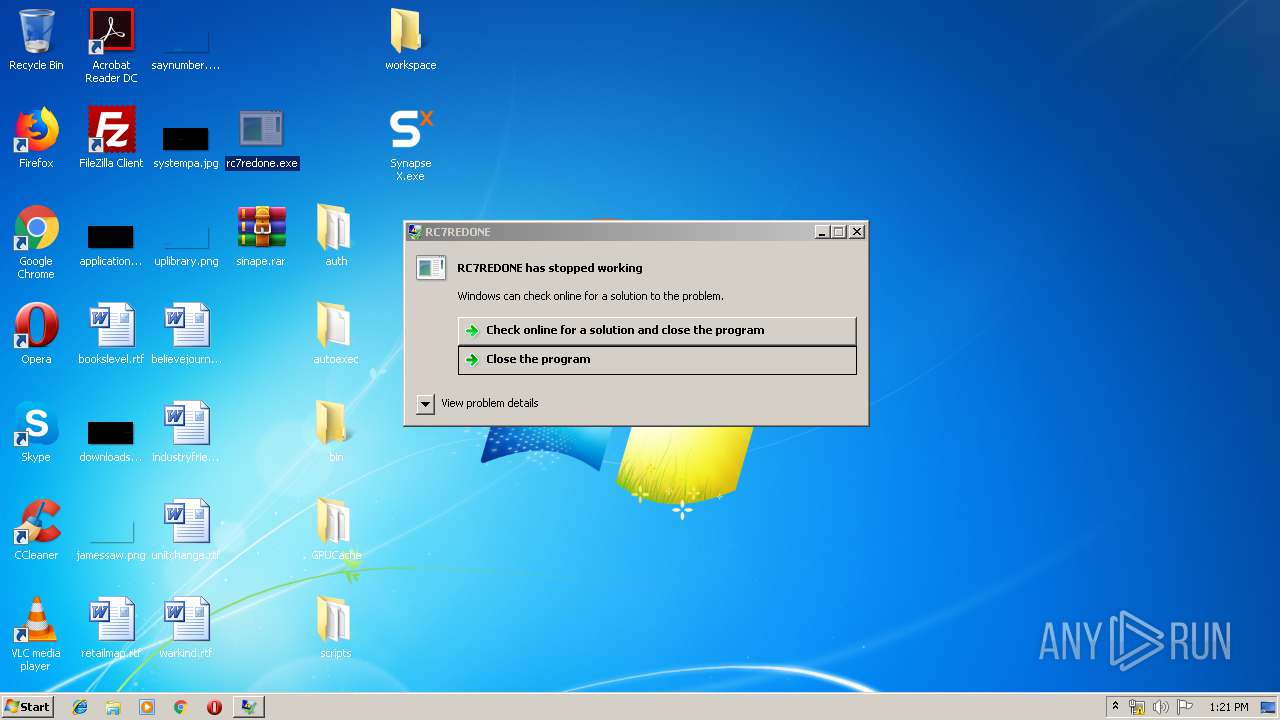
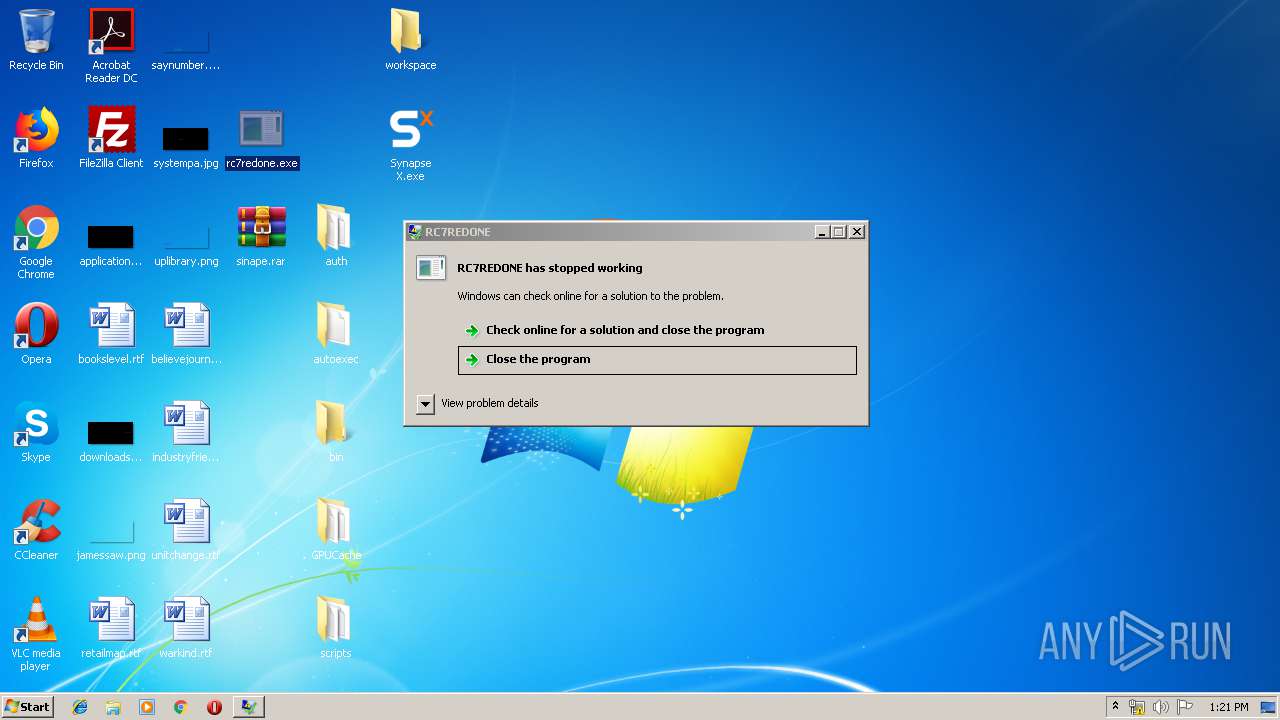
Application was crashed
- rc7redone.exe (PID: 3524)
- rc7redone.exe (PID: 2176)
- rc7redone.exe (PID: 1348)
Creates files in the user directory
- iexplore.exe (PID: 3904)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1764)
- iexplore.exe (PID: 3940)
- iexplore.exe (PID: 3148)
- iexplore.exe (PID: 3648)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2460)
Reads internet explorer settings
- iexplore.exe (PID: 3940)
- iexplore.exe (PID: 3904)
Reads Internet Cache Settings
- iexplore.exe (PID: 3940)
- iexplore.exe (PID: 3904)
Application launched itself
- iexplore.exe (PID: 3148)
Changes settings of System certificates
- iexplore.exe (PID: 3148)
- iexplore.exe (PID: 3648)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 3148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2076:04:11 21:01:08+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 651776 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa10b2 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | RC7REDONE |
| FileVersion: | 1.0.0.0 |
| InternalName: | RC7REDONE.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | - |
| OriginalFileName: | RC7REDONE.exe |
| ProductName: | RC7REDONE |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Mar-1940 12:32:52 |
| Debug artifacts: |
|
| Comments: | - |
| CompanyName: | - |
| FileDescription: | RC7REDONE |
| FileVersion: | 1.0.0.0 |
| InternalName: | RC7REDONE.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | - |
| OriginalFilename: | RC7REDONE.exe |
| ProductName: | RC7REDONE |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 06-Mar-1940 12:32:52 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x0009F0B8 | 0x0009F200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.39945 |
.rsrc | 0x000A2000 | 0x000005AC | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.12466 |
.reloc | 0x000A4000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
61
Monitored processes
15
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1348 | "C:\Users\admin\Desktop\rc7redone.exe" | C:\Users\admin\Desktop\rc7redone.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RC7REDONE Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1764 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 2176 | "C:\Users\admin\Desktop\rc7redone.exe" | C:\Users\admin\Desktop\rc7redone.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RC7REDONE Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2408 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2460 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 2636 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | "bin\C7FB8689DFEAC65B.bin" | C:\Users\admin\Desktop\bin\C7FB8689DFEAC65B.bin | Synapse X.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Synapse UI WPF Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3120 | "C:\Users\admin\Desktop\Synapse X.exe" | C:\Users\admin\Desktop\Synapse X.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Synapse Bootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3148 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3524 | "C:\Users\admin\AppData\Local\Temp\rc7redone.exe" | C:\Users\admin\AppData\Local\Temp\rc7redone.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RC7REDONE Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
3 360
Read events
2 784
Write events
555
Delete events
21
Modification events
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {6BFB1D6F-C732-11E9-B86F-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070800000019000C00120013006603 | |||
Executable files
3
Suspicious files
23
Text files
62
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3940 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\AOT4S2Y0\sinape_rar[1].txt | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 3940 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\AOT4S2Y0\sinape_rar[1].htm | html | |
MD5:— | SHA256:— | |||
| 3940 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3940 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\K7S9DBCX\anonfile[1].css | text | |
MD5:— | SHA256:— | |||
| 3940 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5EHYKEPF\shermore_info[1] | text | |
MD5:— | SHA256:— | |||
| 3940 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\TL9Y5UHD\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 3940 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\K7S9DBCX\js[1] | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
62
DNS requests
21
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3940 | iexplore.exe | GET | 200 | 2.16.106.186:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 56.6 Kb | whitelisted |
3940 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.6 Kb | whitelisted |
3148 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3940 | iexplore.exe | GET | 200 | 13.224.197.157:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
3904 | iexplore.exe | GET | 301 | 194.32.146.60:80 | http://anonfile.com/s3pcac45n7 | unknown | html | 178 b | whitelisted |
3940 | iexplore.exe | GET | 200 | 13.224.197.19:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
3940 | iexplore.exe | GET | 301 | 194.32.146.60:80 | http://anonfile.com/35o7a448nd/sinape_rar | unknown | html | 178 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3148 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3940 | iexplore.exe | 194.32.146.60:80 | anonfile.com | — | — | unknown |
3940 | iexplore.exe | 194.32.146.60:443 | anonfile.com | — | — | unknown |
3940 | iexplore.exe | 151.101.2.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
3940 | iexplore.exe | 104.18.39.148:443 | shermore.info | Cloudflare Inc | US | shared |
3940 | iexplore.exe | 23.111.8.154:443 | oss.maxcdn.com | netDNA | US | unknown |
3940 | iexplore.exe | 172.217.18.104:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3940 | iexplore.exe | 13.224.197.19:80 | x.ss2.us | — | US | unknown |
3940 | iexplore.exe | 172.217.16.174:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3940 | iexplore.exe | 13.224.197.18:443 | d3ud741uvs727m.cloudfront.net | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
anonfile.com |
| whitelisted |
vjs.zencdn.net |
| whitelisted |
oss.maxcdn.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
d3ud741uvs727m.cloudfront.net |
| whitelisted |
shermore.info |
| whitelisted |
www.google-analytics.com |
| whitelisted |
rappenedstoric.info |
| unknown |
x.ss2.us |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |