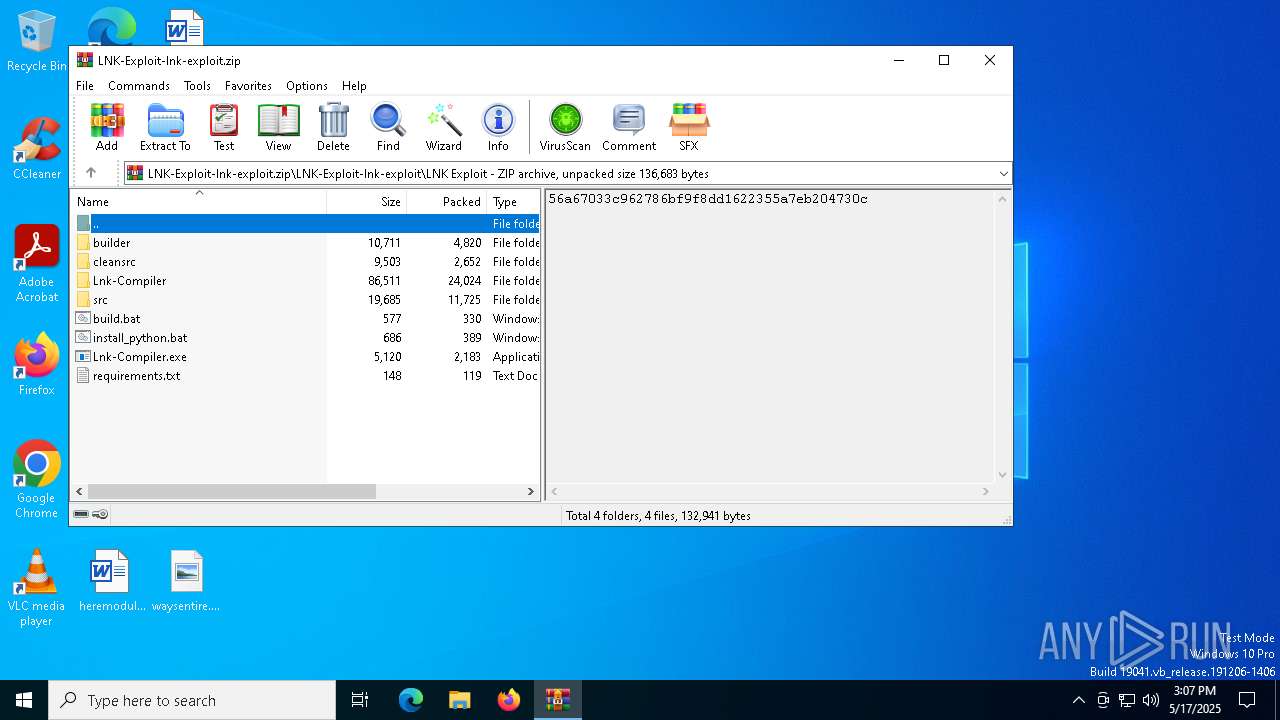
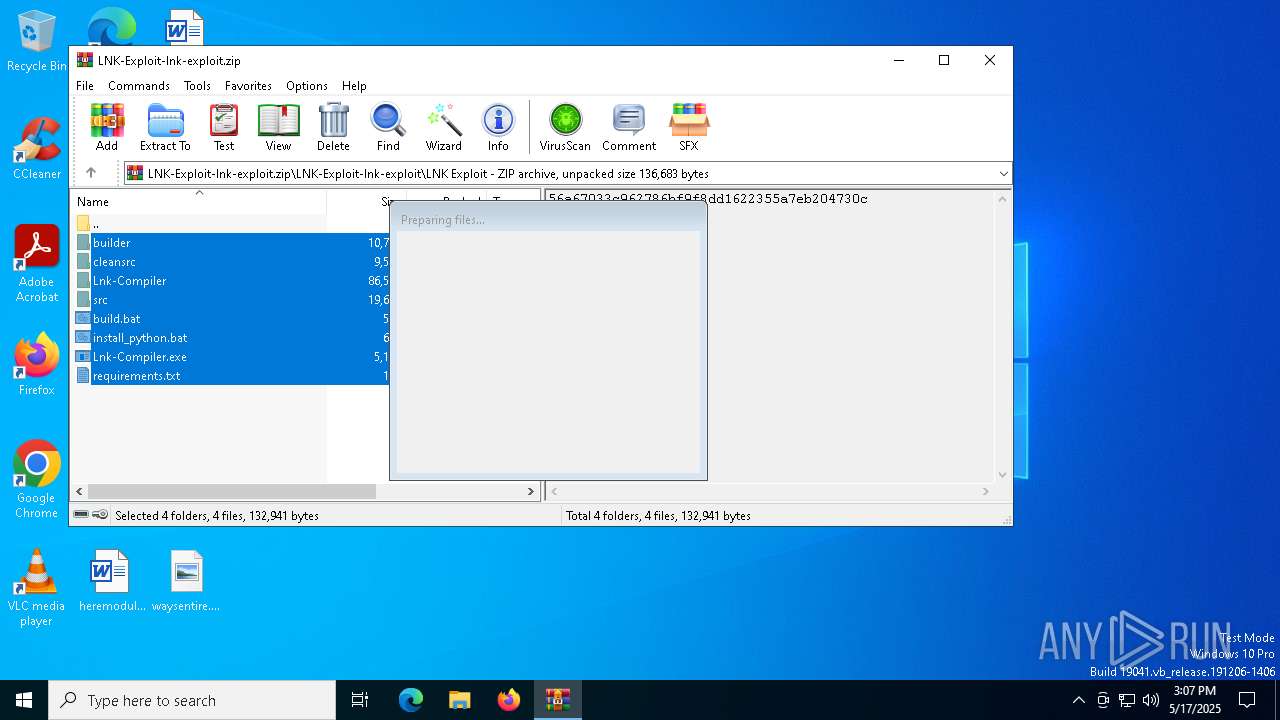
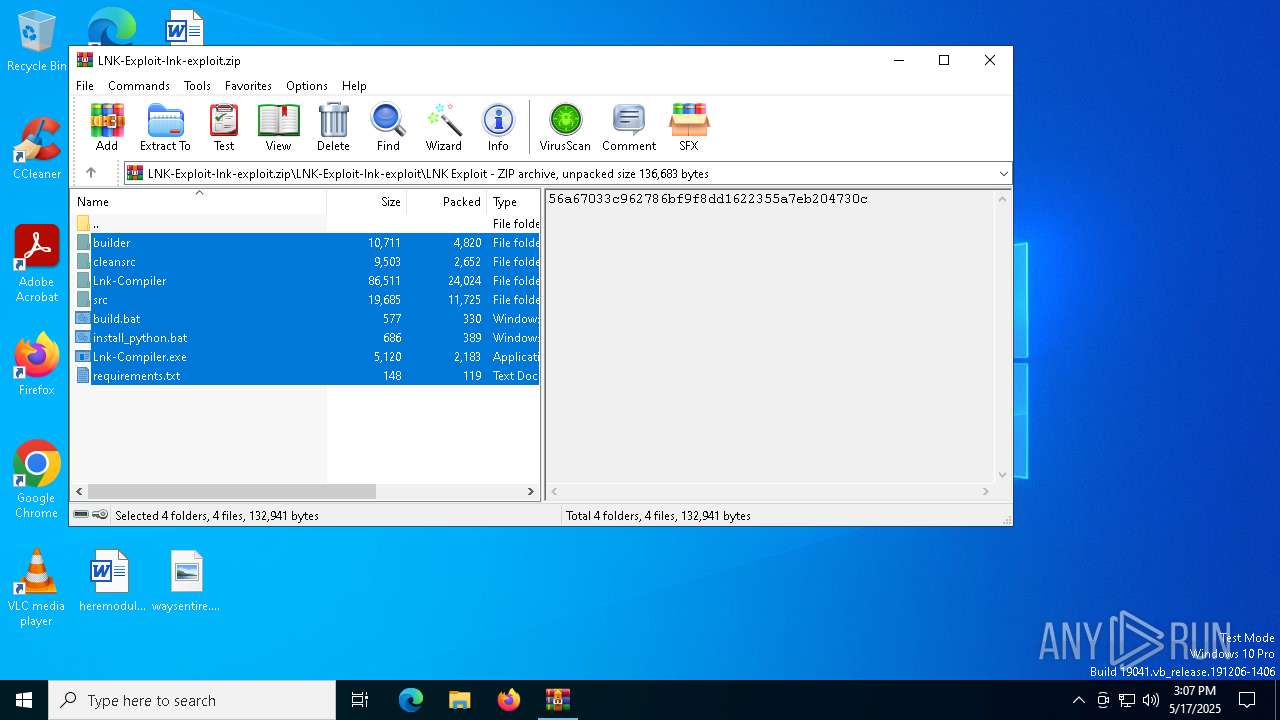
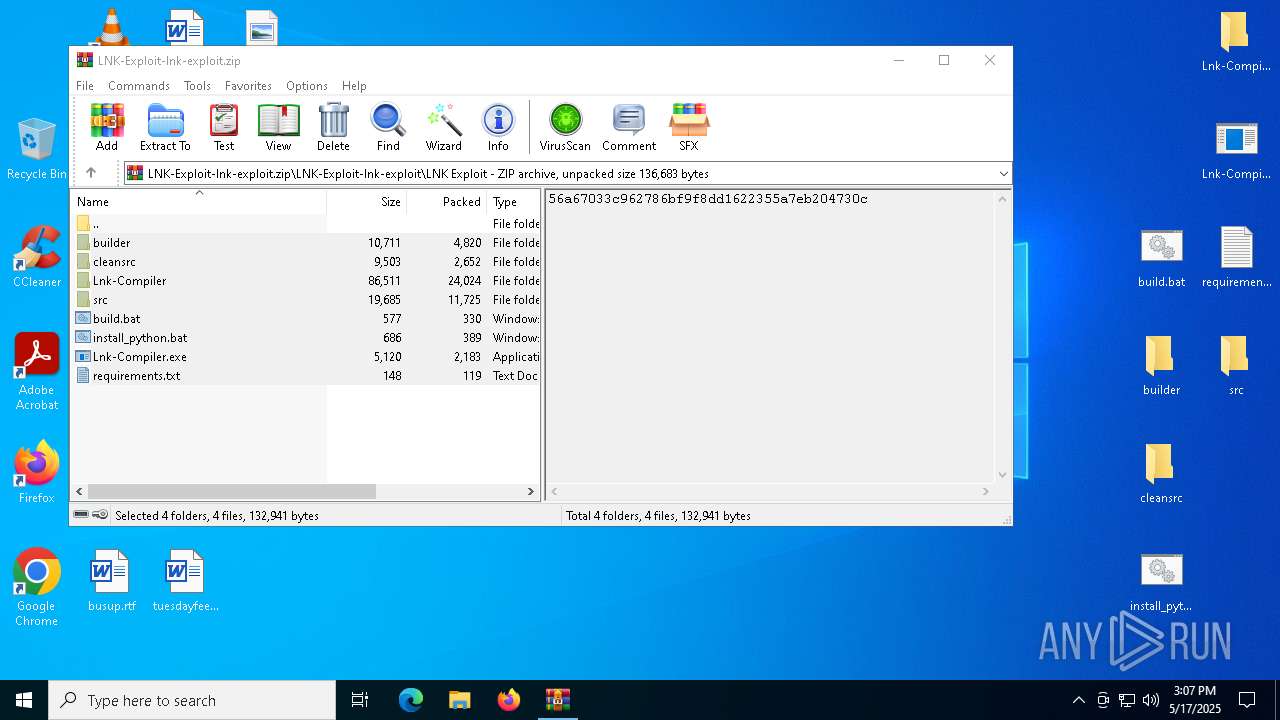
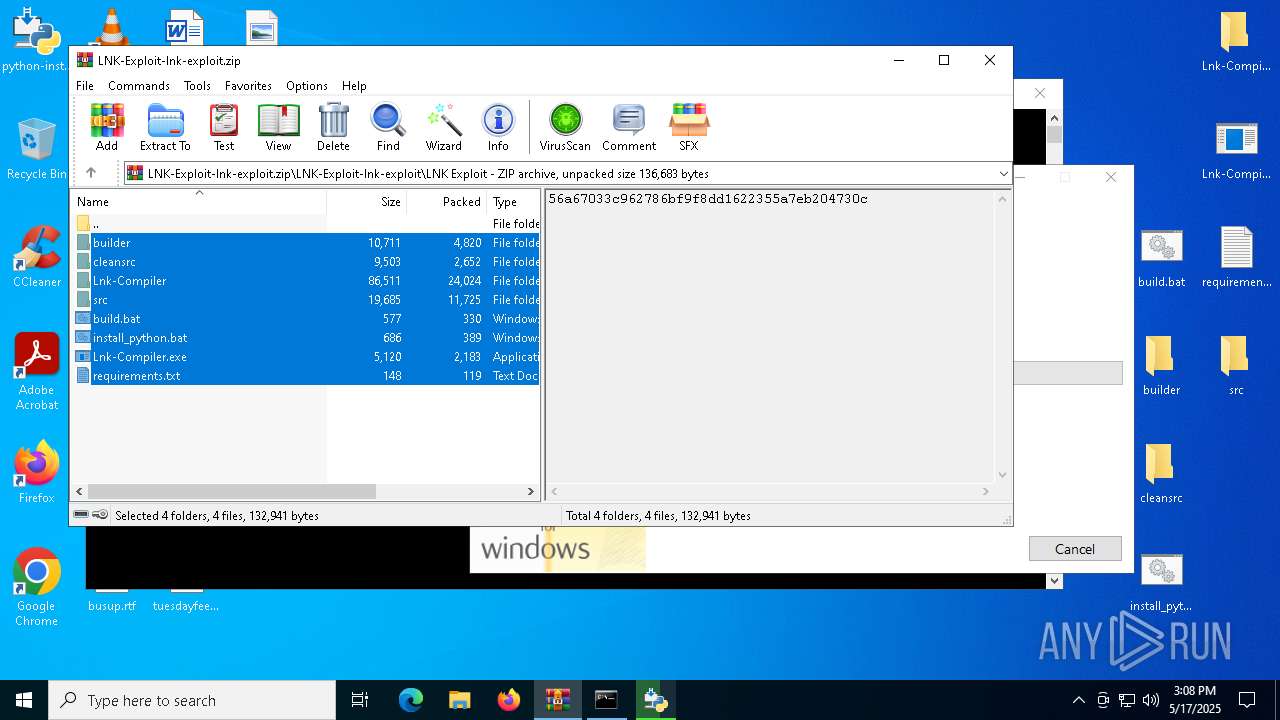
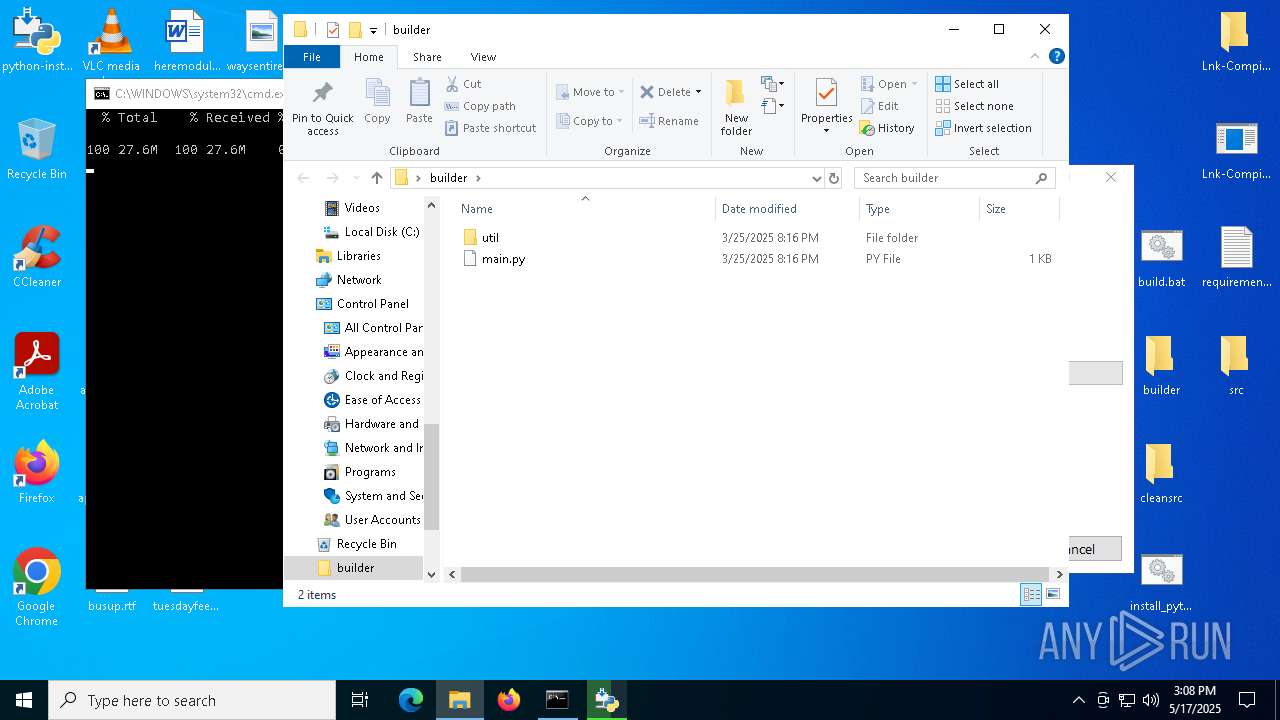
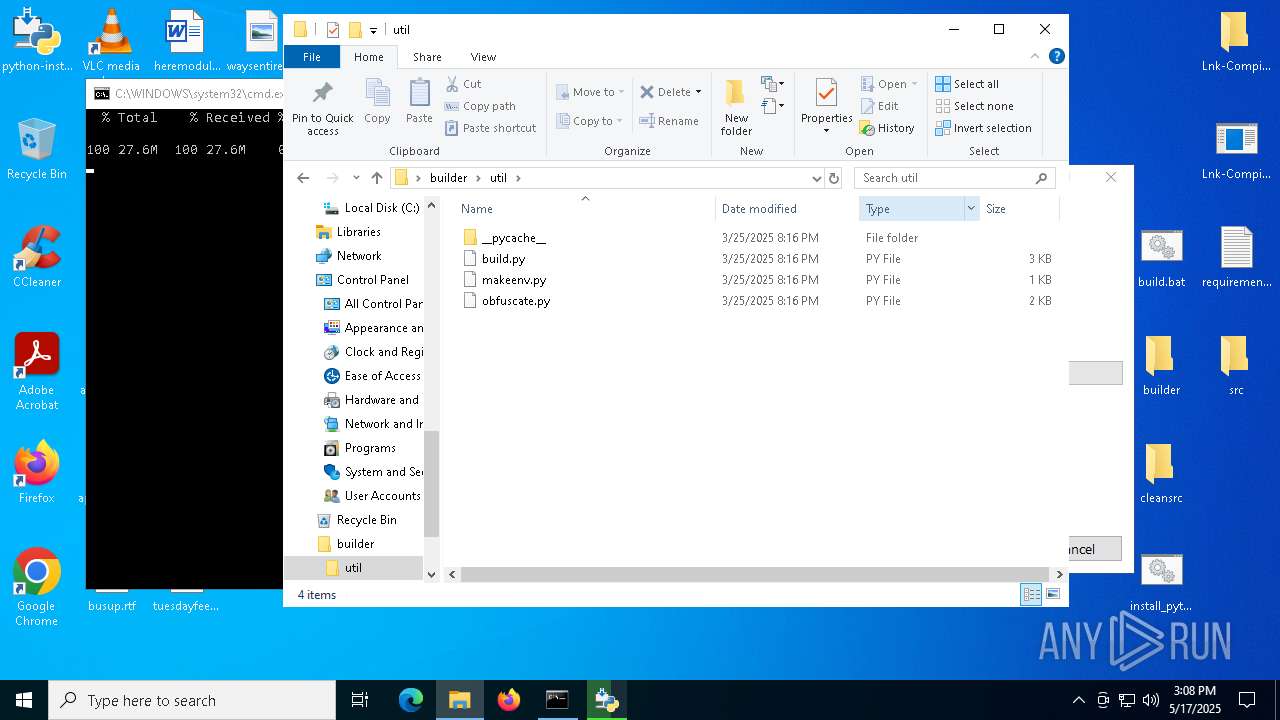
| File name: | LNK-Exploit-lnk-exploit.zip |
| Full analysis: | https://app.any.run/tasks/0ff6db5b-ad11-4edd-aac3-826026d66217 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 15:07:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | BAF3FCB25DB30C8CA0C0BFDF693B5015 |
| SHA1: | BB255FB4FC890EE836F99F2D94F8A9F1D99B62D7 |
| SHA256: | DE941C0AECFA34BE1F2F0C99F18952C7A8D828465A6095F78BA9B86680270A03 |
| SSDEEP: | 768:hvic9vPbFc9vP4fdebNnDKhDkxFc9vP3fsQyiHwOVno56Z+NXjD1t3GDMfVb+zzJ:hvN9L+9IlNx9nBjHHVo55jDX3GIVOJ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7464)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 7940)
- python.exe (PID: 7772)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7940)
- Lnk-Compiler.exe (PID: 7220)
- Lnk-Compiler.exe (PID: 7724)
- python.exe (PID: 7672)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 8004)
Reads the date of Windows installation
- Lnk-Compiler.exe (PID: 7220)
Reads security settings of Internet Explorer
- Lnk-Compiler.exe (PID: 7220)
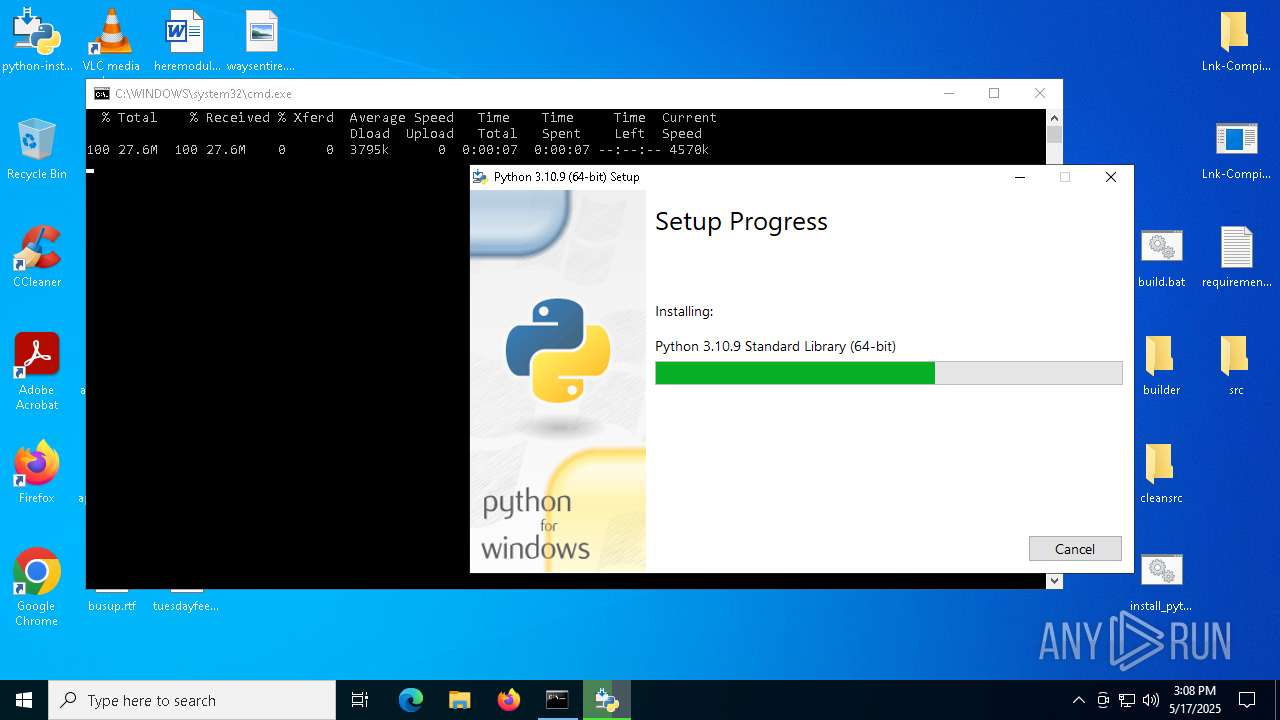
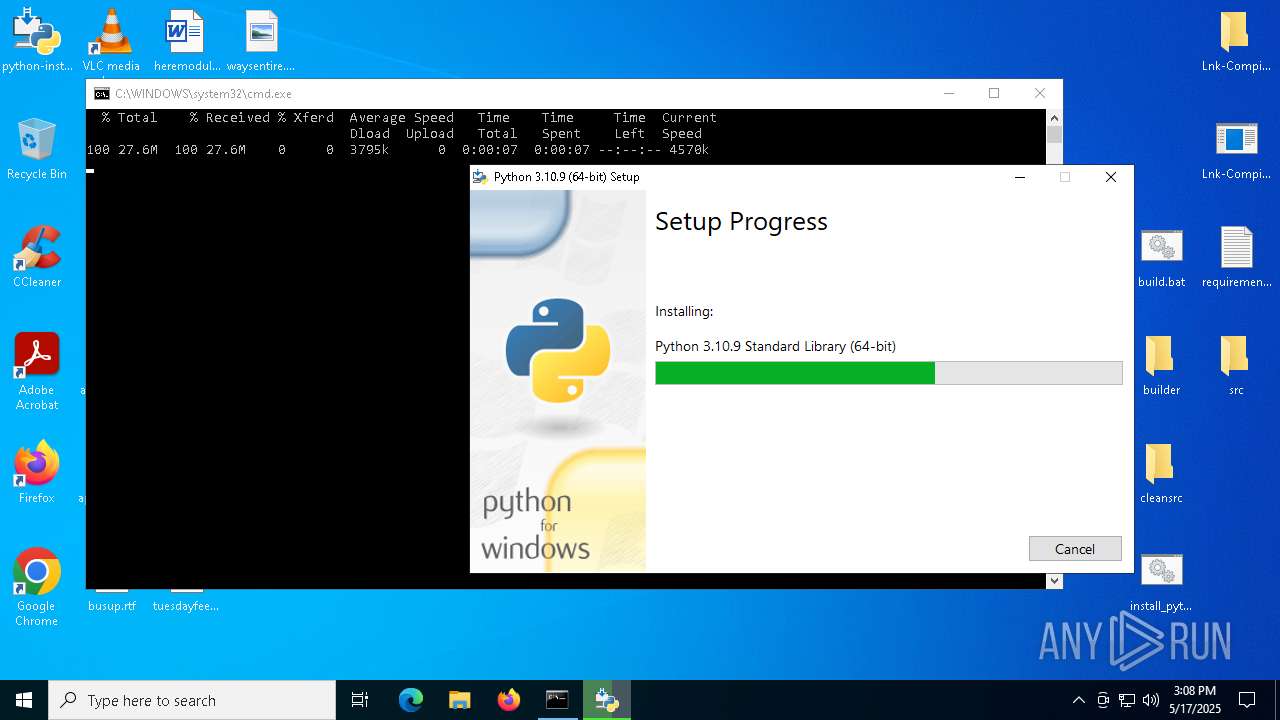
- python-installer.exe (PID: 6040)
Executable content was dropped or overwritten
- python-installer.exe (PID: 4620)
- python-installer.exe (PID: 6040)
- python-3.10.9-amd64.exe (PID: 7584)
- python.exe (PID: 7672)
Executing commands from a ".bat" file
- Lnk-Compiler.exe (PID: 7220)
- Lnk-Compiler.exe (PID: 7724)
Searches for installed software
- dllhost.exe (PID: 7872)
- python-installer.exe (PID: 6040)
Starts itself from another location
- python-installer.exe (PID: 6040)
Executes as Windows Service
- VSSVC.exe (PID: 7888)
Process drops legitimate windows executable
- msiexec.exe (PID: 7356)
- python-installer.exe (PID: 6040)
The process drops C-runtime libraries
- msiexec.exe (PID: 7356)
- python-installer.exe (PID: 6040)
There is functionality for taking screenshot (YARA)
- python-installer.exe (PID: 6040)
Process drops python dynamic module
- msiexec.exe (PID: 7356)
INFO
Disables trace logs
- powershell.exe (PID: 8020)
Reads the computer name
- curl.exe (PID: 7252)
- Lnk-Compiler.exe (PID: 7220)
- Lnk-Compiler.exe (PID: 5436)
- python-installer.exe (PID: 6040)
- python-3.10.9-amd64.exe (PID: 7584)
Manual execution by a user
- cmd.exe (PID: 7368)
- cmd.exe (PID: 7940)
- Lnk-Compiler.exe (PID: 7220)
- Lnk-Compiler.exe (PID: 5436)
- Lnk-Compiler.exe (PID: 7724)
- Lnk-Compiler.exe (PID: 5260)
Checks proxy server information
- powershell.exe (PID: 8020)
Starts MODE.COM to configure console settings
- mode.com (PID: 2320)
- mode.com (PID: 5720)
- mode.com (PID: 920)
Execution of CURL command
- cmd.exe (PID: 7940)
Checks supported languages
- curl.exe (PID: 7252)
- mode.com (PID: 2320)
- Lnk-Compiler.exe (PID: 7220)
- python-installer.exe (PID: 4620)
- mode.com (PID: 5720)
- Lnk-Compiler.exe (PID: 5436)
- python-installer.exe (PID: 6040)
- python-3.10.9-amd64.exe (PID: 7584)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7464)
- msiexec.exe (PID: 7356)
Create files in a temporary directory
- Lnk-Compiler.exe (PID: 7220)
- python-installer.exe (PID: 4620)
- python-installer.exe (PID: 6040)
Process checks computer location settings
- Lnk-Compiler.exe (PID: 7220)
- python-installer.exe (PID: 6040)
The sample compiled with english language support
- python-installer.exe (PID: 4620)
- python-installer.exe (PID: 6040)
- msiexec.exe (PID: 7356)
- python.exe (PID: 7672)
Manages system restore points
- SrTasks.exe (PID: 7284)
Python executable
- python.exe (PID: 7672)
- python.exe (PID: 7772)
Checks operating system version
- python.exe (PID: 7672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:25 13:16:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | LNK-Exploit-lnk-exploit/ |
Total processes
179
Monitored processes
40
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | mode con: cols=100 lines=30 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Lnk-Compiler.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | C:\Windows\syswow64\MsiExec.exe -Embedding 82B9F0B17345782904959CA5D133D707 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | mode con: cols=100 lines=30 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4620 | python-installer.exe /quiet /passive InstallAllUsers=0 PrependPath=1 Include_test=0 Include_pip=1 Include_doc=0 | C:\Users\admin\Desktop\python-installer.exe | cmd.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.10.9 (64-bit) Version: 3.10.9150.0 Modules
| |||||||||||||||
| 4812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4844 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Lnk-Compiler.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\build.bat" " | C:\Windows\System32\cmd.exe | — | Lnk-Compiler.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 255 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
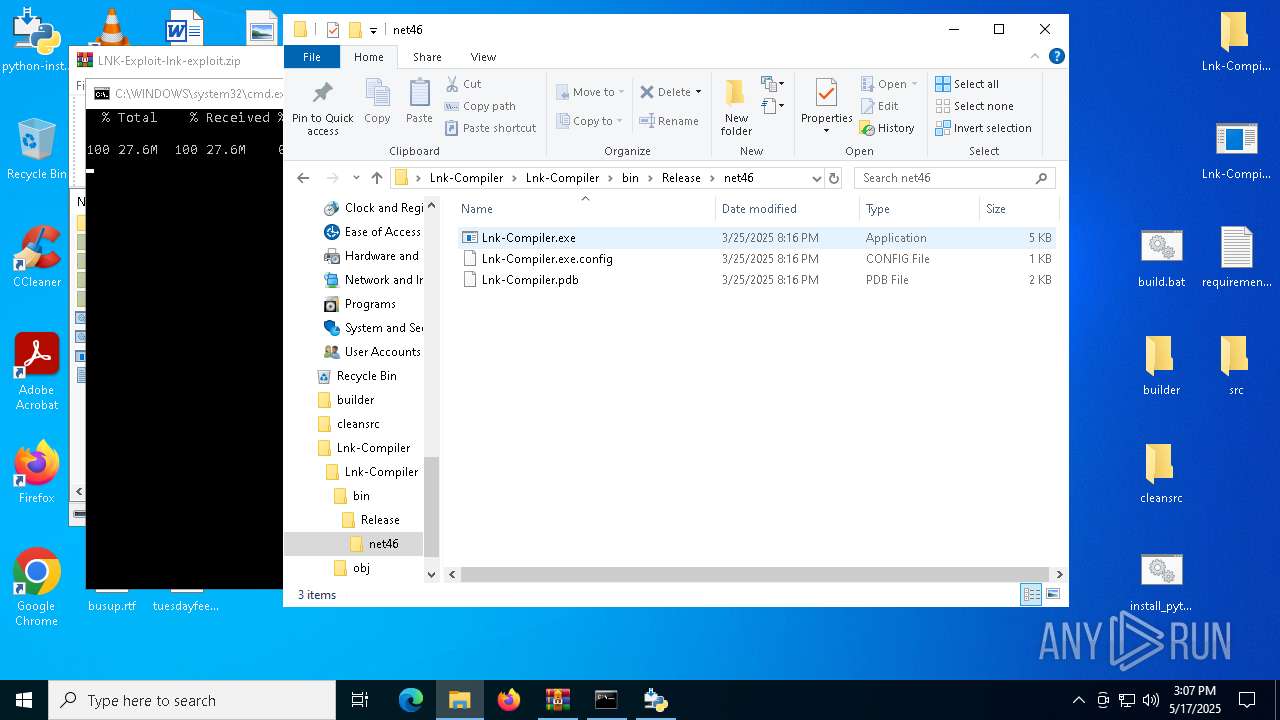
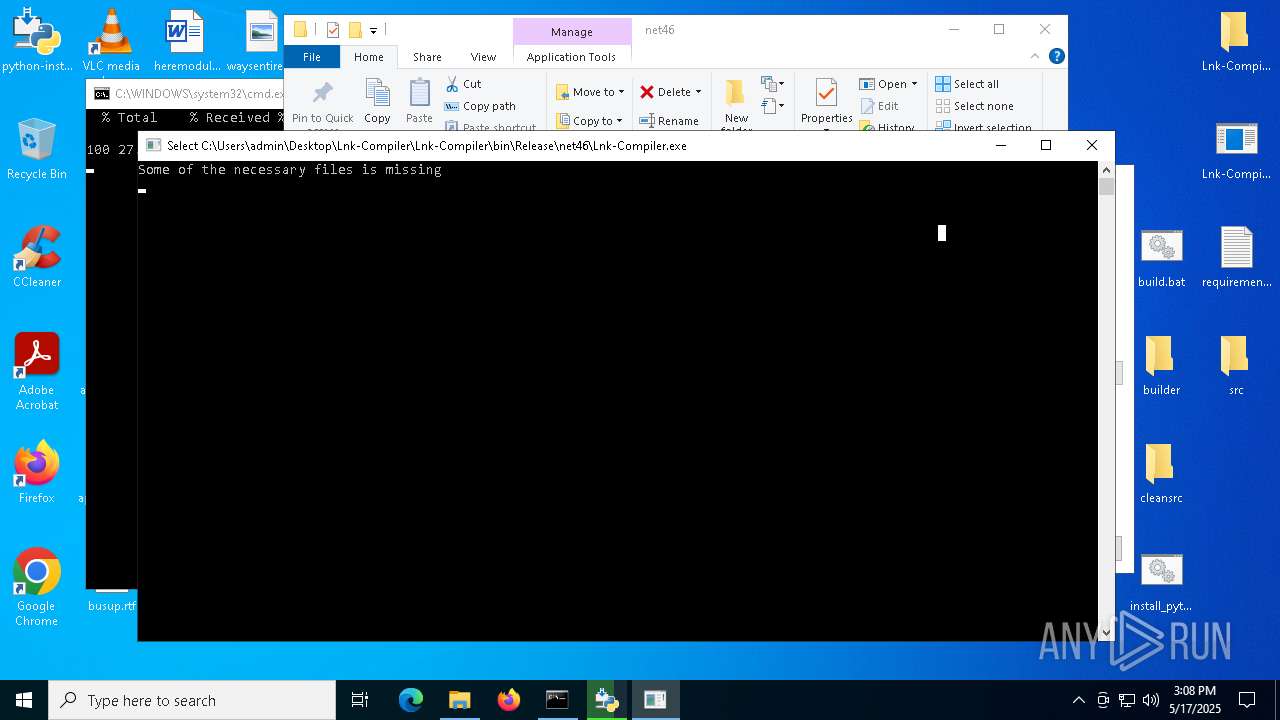
| 5260 | "C:\Users\admin\Desktop\Lnk-Compiler\Lnk-Compiler\bin\Release\net46\Lnk-Compiler.exe" | C:\Users\admin\Desktop\Lnk-Compiler\Lnk-Compiler\bin\Release\net46\Lnk-Compiler.exe | — | explorer.exe | |||||||||||
User: admin Company: Lnk-Compiler Integrity Level: MEDIUM Description: Lnk-Compiler Exit code: 3221225786 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
44 669
Read events
40 896
Write events
3 680
Delete events
93
Modification events
| (PID) Process: | (7464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\LNK-Exploit-lnk-exploit.zip | |||
| (PID) Process: | (7464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7584) python-3.10.9-amd64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000001F577D6F3DC7DB01A01D0000301E0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7872) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000001F577D6F3DC7DB01C01E0000681E0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
102
Suspicious files
1 549
Text files
3 279
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7464.25148\LNK-Exploit-lnk-exploit\LNK Exploit\Lnk-Compiler\Lnk-Compiler\Lnk-Compiler.csproj | text | |
MD5:8D02E22D3DF5FB2A4F580DC2D7C19CF1 | SHA256:9BE13073B360839EC832EE4A5741BB3BF3173B39CB4D2CBE367205CBAD2700EF | |||
| 7464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7464.25148\LNK-Exploit-lnk-exploit\LNK Exploit\Lnk-Compiler.exe | executable | |
MD5:59CE608D78C2C62C39A6E2861BAC1056 | SHA256:4F520880D042652EC96BE5C750E493D094BB8DBE24795DE9539B907A76FDE65B | |||
| 7464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7464.25148\LNK-Exploit-lnk-exploit\LNK Exploit\Lnk-Compiler\Lnk-Compiler\bin\Release\net46\Lnk-Compiler.exe | executable | |
MD5:59CE608D78C2C62C39A6E2861BAC1056 | SHA256:4F520880D042652EC96BE5C750E493D094BB8DBE24795DE9539B907A76FDE65B | |||
| 7464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7464.25148\LNK-Exploit-lnk-exploit\LNK Exploit\Lnk-Compiler\Lnk-Compiler\bin\Release\net46\Lnk-Compiler.pdb | binary | |
MD5:1D55068D2BB721B1880039F259CFF679 | SHA256:0EDE0914AB77584554F70677B3ED3BC73636643F29CB3219CEA470A8ACBFFC69 | |||
| 7464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7464.25148\LNK-Exploit-lnk-exploit\LNK Exploit\Lnk-Compiler\Lnk-Compiler\Program.cs | text | |
MD5:FF4822B478FBC29423E222EAB59E5A64 | SHA256:08675FB4B70912EC067B328D0A551376DE6444E1D6C3BB5EB46775D67C33EA77 | |||
| 7464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7464.25148\LNK-Exploit-lnk-exploit\LNK Exploit\Lnk-Compiler\Lnk-Compiler\obj\Debug\net46\Lnk-Compiler.AssemblyInfo.cs | text | |
MD5:E1C24C9FB7E71EA6C498E3D699DE16D0 | SHA256:1E766332273215D0BF31730C828FEF2A1F46DDF597F33414CC63AD0D2CE0C443 | |||
| 7464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7464.25148\LNK-Exploit-lnk-exploit\LNK Exploit\Lnk-Compiler\Lnk-Compiler\obj\Lnk-Compiler.csproj.nuget.g.targets | xml | |
MD5:0F5E12BEBFA254B10A8A11B3DB59AF5B | SHA256:2733621945C1FEE935293318104429A558CBACF2EEAA93642118D413BF5908FF | |||
| 7464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7464.25148\LNK-Exploit-lnk-exploit\LNK Exploit\Lnk-Compiler\Lnk-Compiler\obj\Millenium-Compiler.csproj.nuget.g.props | xml | |
MD5:53AD69BED95A5000B9ADDA33491869FF | SHA256:CE3F580C4BC8CA483C459CD914CA51FA1BBF7889EC0ADFF071F9490FD5106188 | |||
| 7464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7464.25148\LNK-Exploit-lnk-exploit\LNK Exploit\Lnk-Compiler\Lnk-Compiler\obj\Lnk-Compiler.csproj.nuget.dgspec.json | binary | |
MD5:83607D7CF6FDFF1F4885B13BF1E02F27 | SHA256:C82F9A3BA0D075E880F3BEB020B463DD3F927275E06416426A3F3B8FC3FC56DF | |||
| 7464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7464.25148\LNK-Exploit-lnk-exploit\LNK Exploit\Lnk-Compiler\Lnk-Compiler\obj\Debug\net46\Lnk-Compiler.GeneratedMSBuildEditorConfig.editorconfig | text | |
MD5:025E27AFFD84D3EC8099506DD23FF48C | SHA256:BB596A8F48919800075B00F611F7ED3C6645CF58D850D0957D35611154A6EF42 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
39
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 151.101.2.133:80 | http://ocsp2.globalsign.com/rootr3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEQCCFEE7BXGhpoEKjlIOBXTx | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7356 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
7356 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
7356 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAcfFBuLMA0l8xTrIwzQ0d0%3D | unknown | — | — | whitelisted |
7936 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.python.org |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |