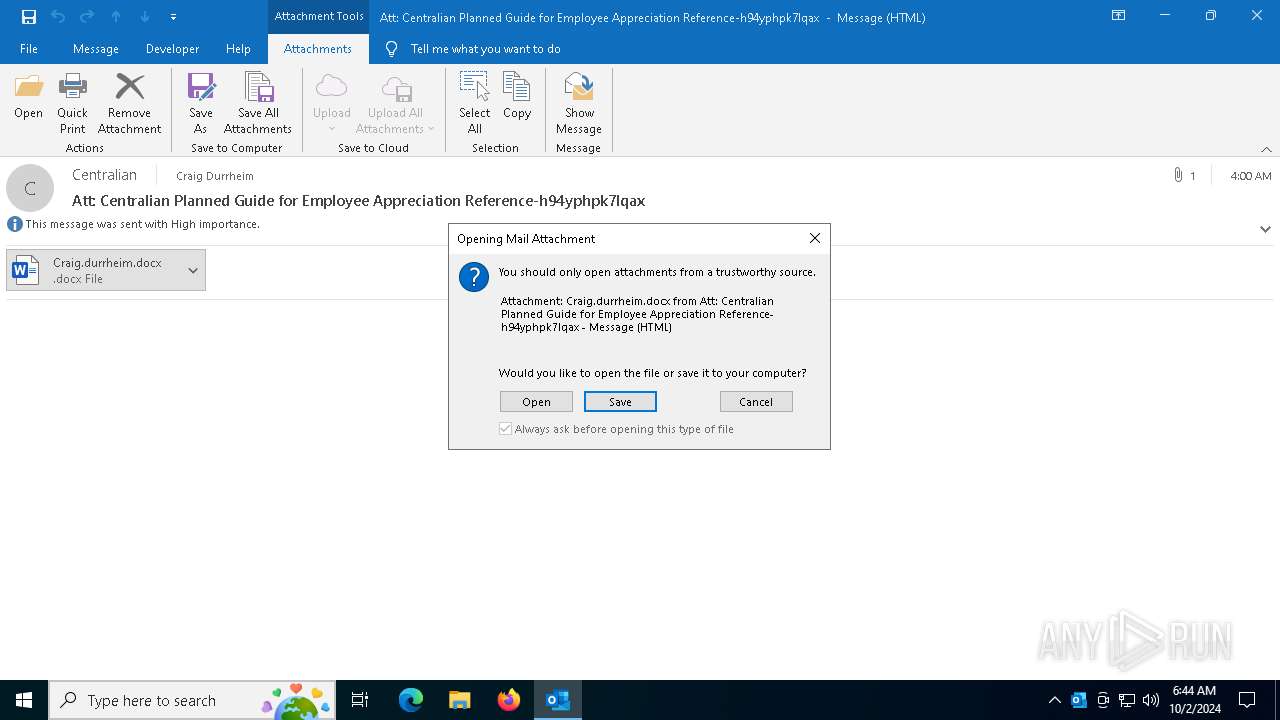
| File name: | Att Centralian Planned Guide for Employee Appreciation Reference-h94yphpk7lqax.msg.7z |
| Full analysis: | https://app.any.run/tasks/12cf880e-2c3c-4732-8a6d-000159a33ce5 |
| Verdict: | Malicious activity |
| Analysis date: | October 02, 2024, 06:43:44 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | AF5C4A53AA759AAD5E76935C3E2FD01D |
| SHA1: | 55CB537FDDA90D926679C1D84541582438593DB7 |
| SHA256: | DE75B07BA653C8E74FD8B70ED881AF939A8B8B757006746A33FC88623F465143 |
| SSDEEP: | 1536:eLIzgL+ZZqMyR0c6jP95I/lSf4o8r5CqNzUO+ziig7HsaGzE:lk0lT95eeR6Cq5UO+zi37b |
MALICIOUS
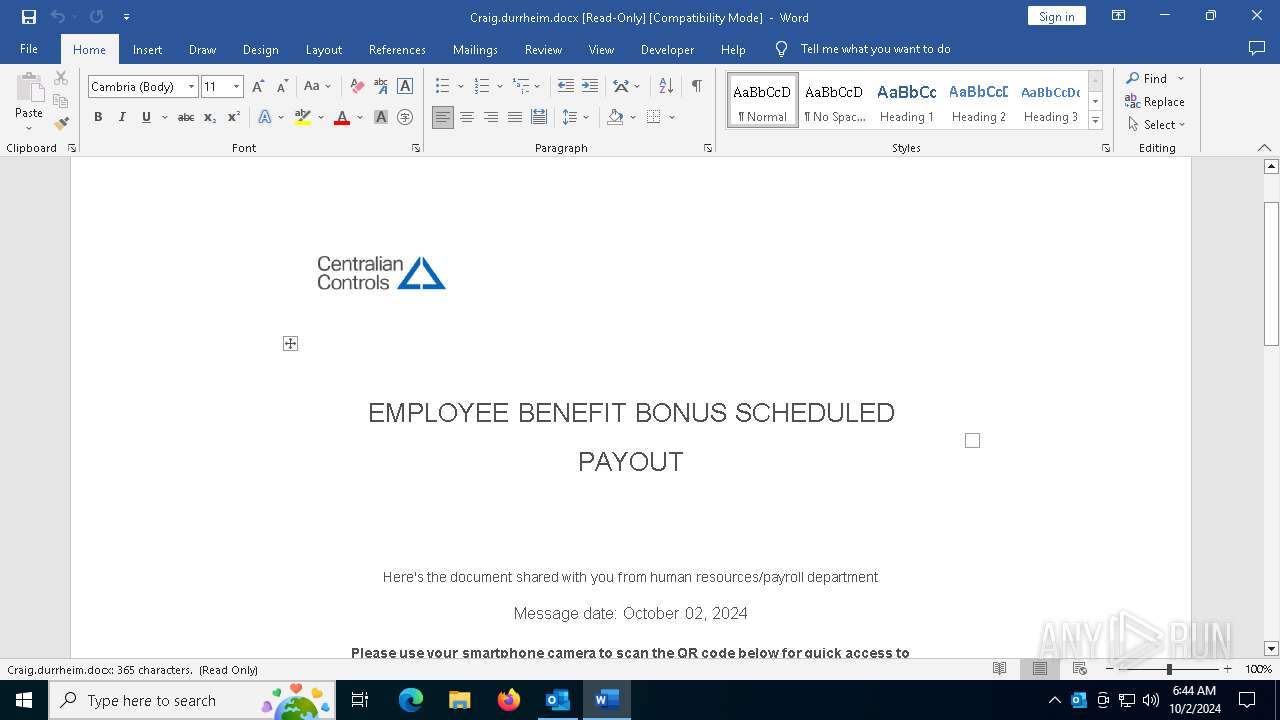
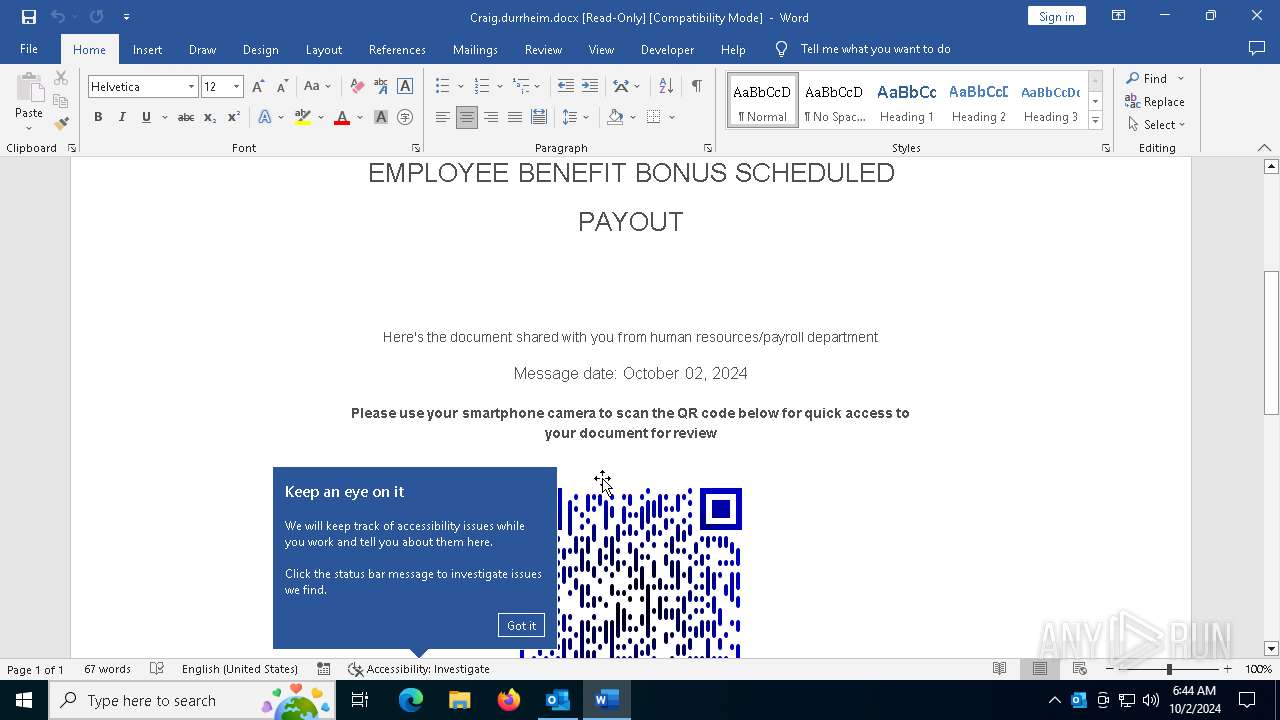
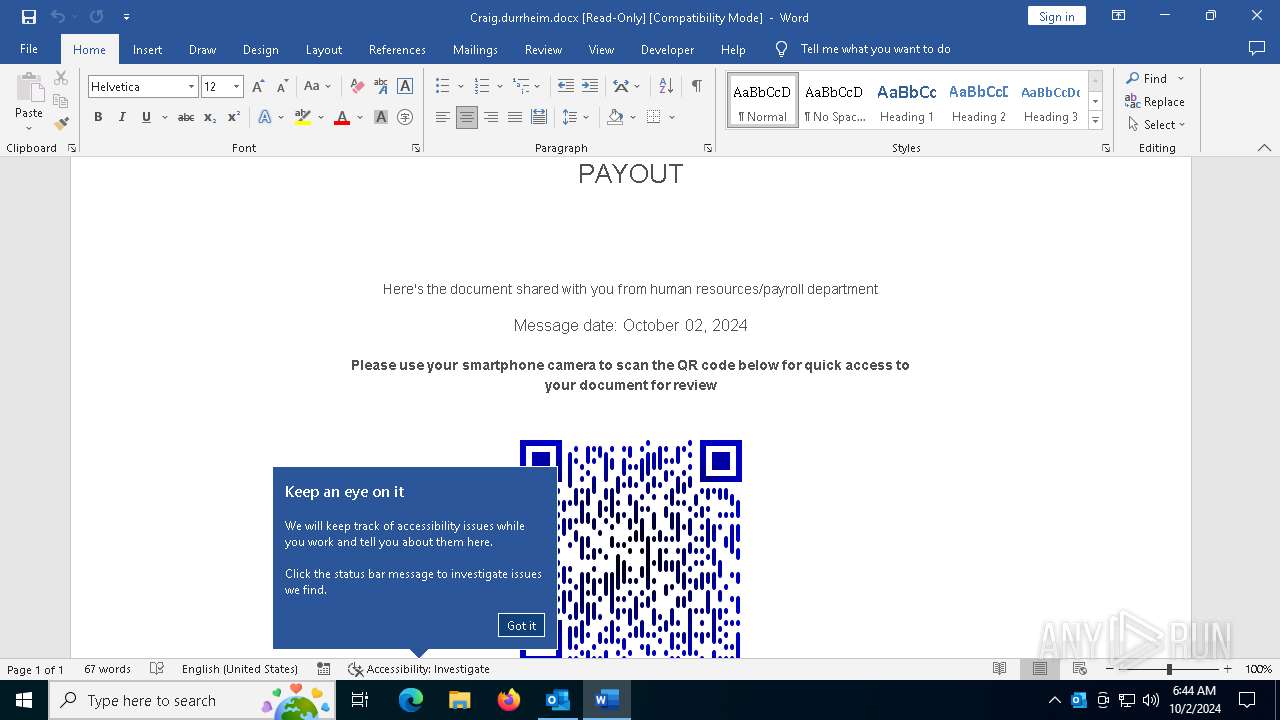
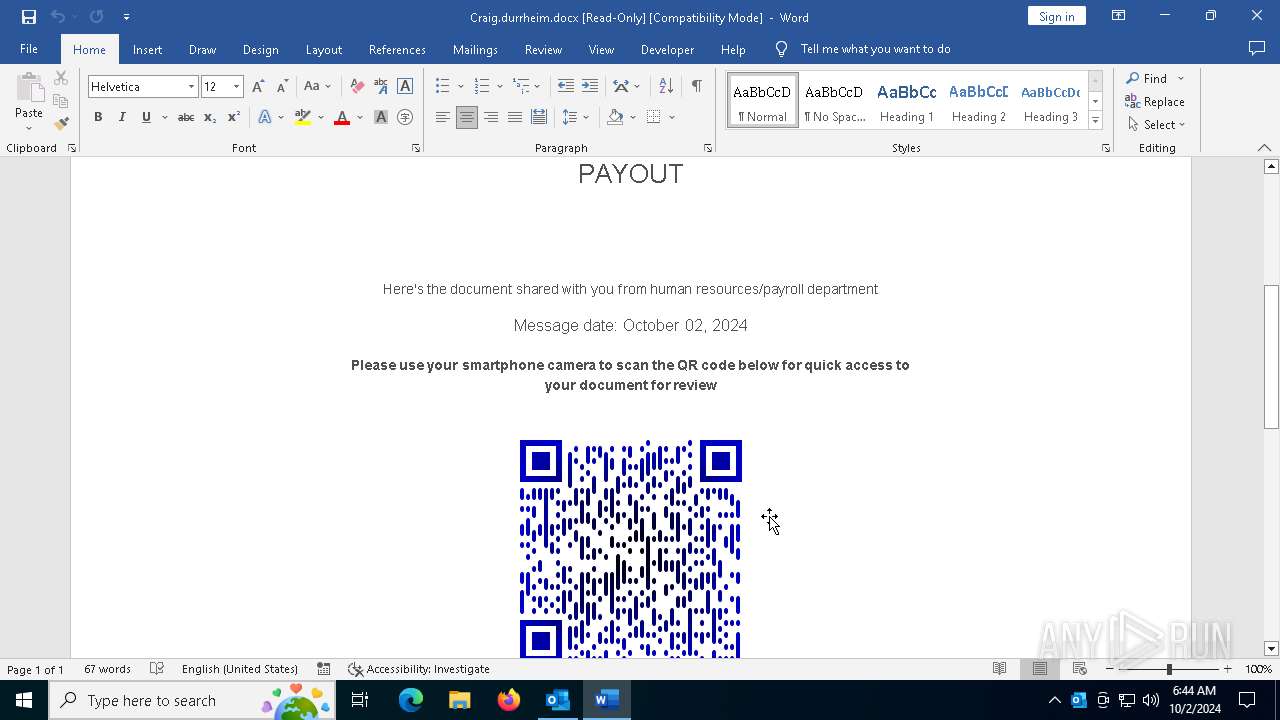
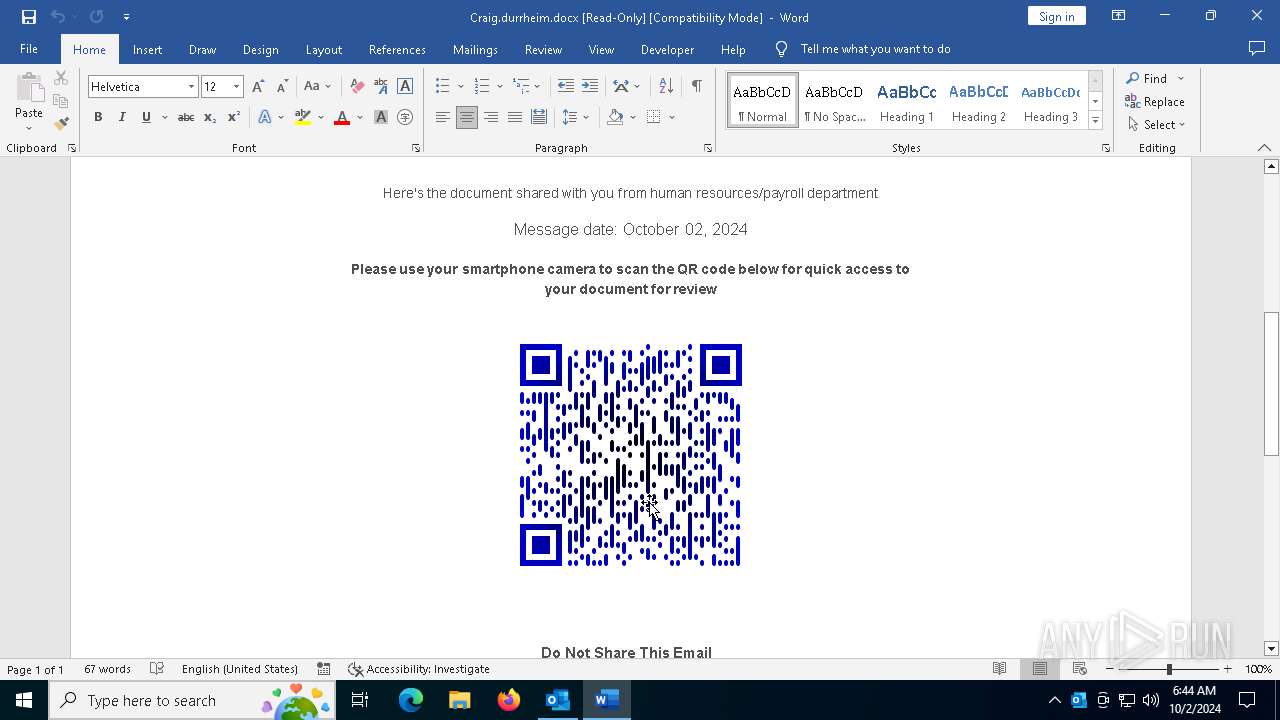
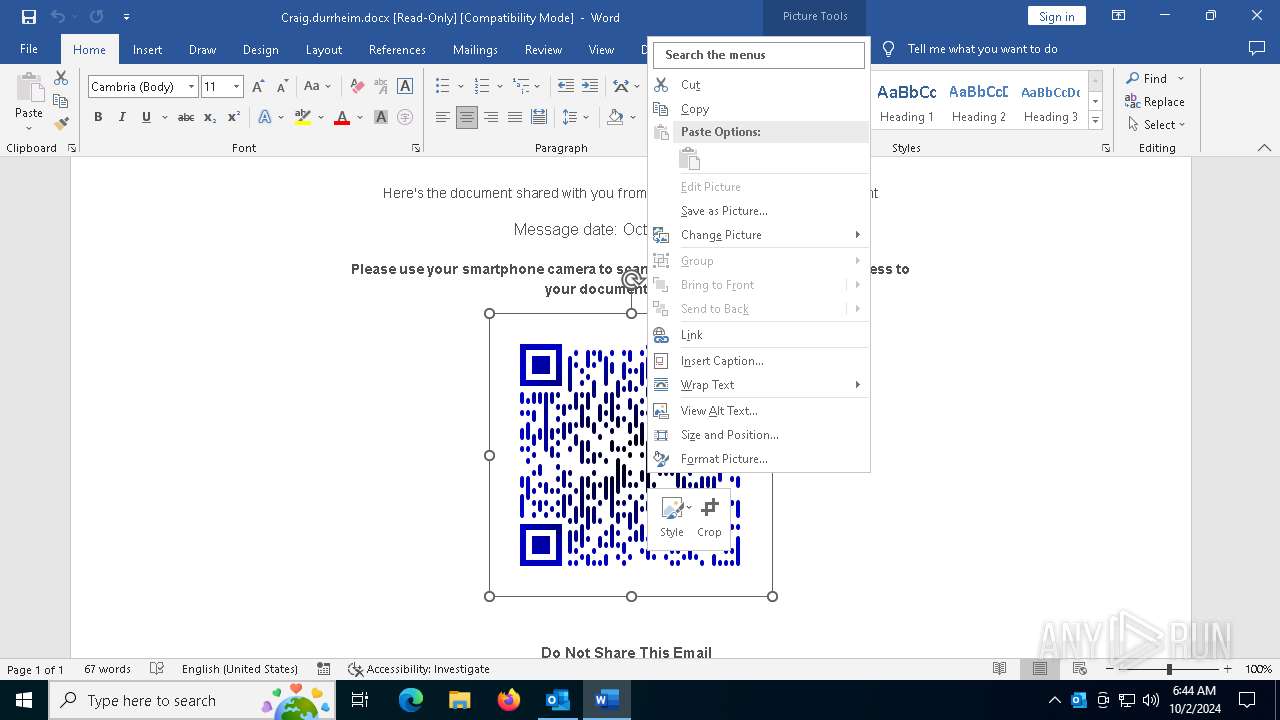
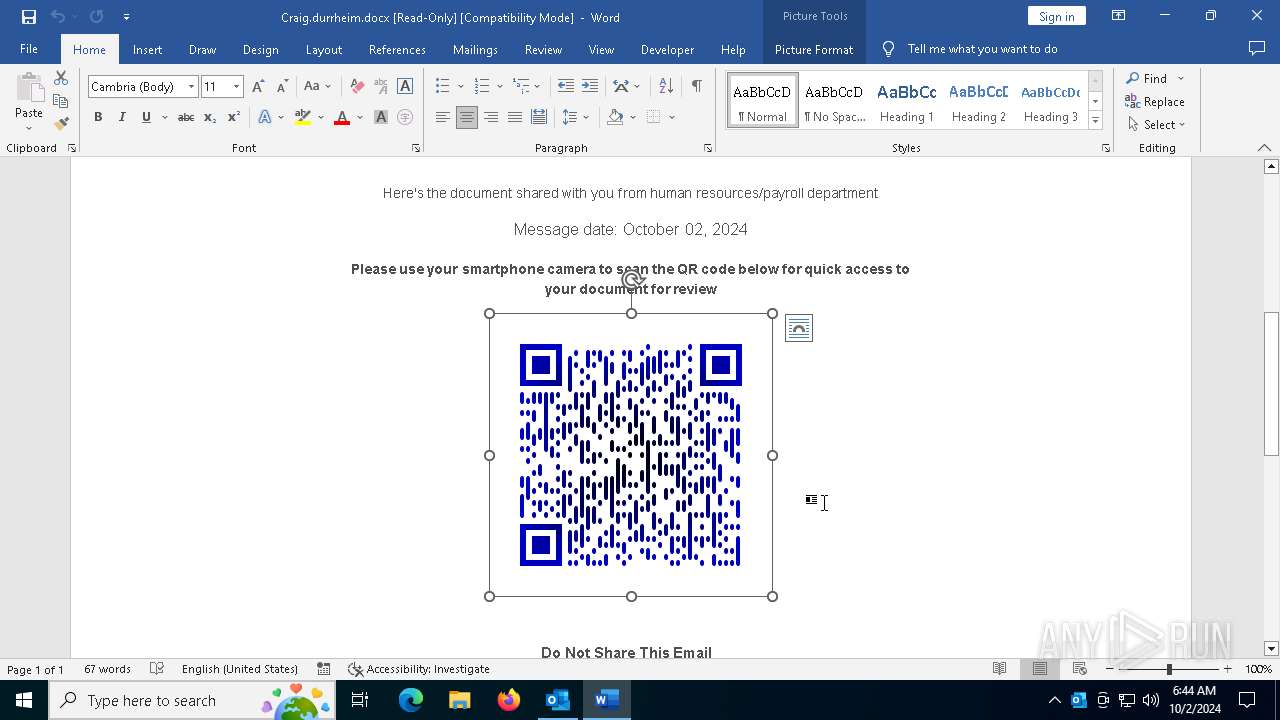
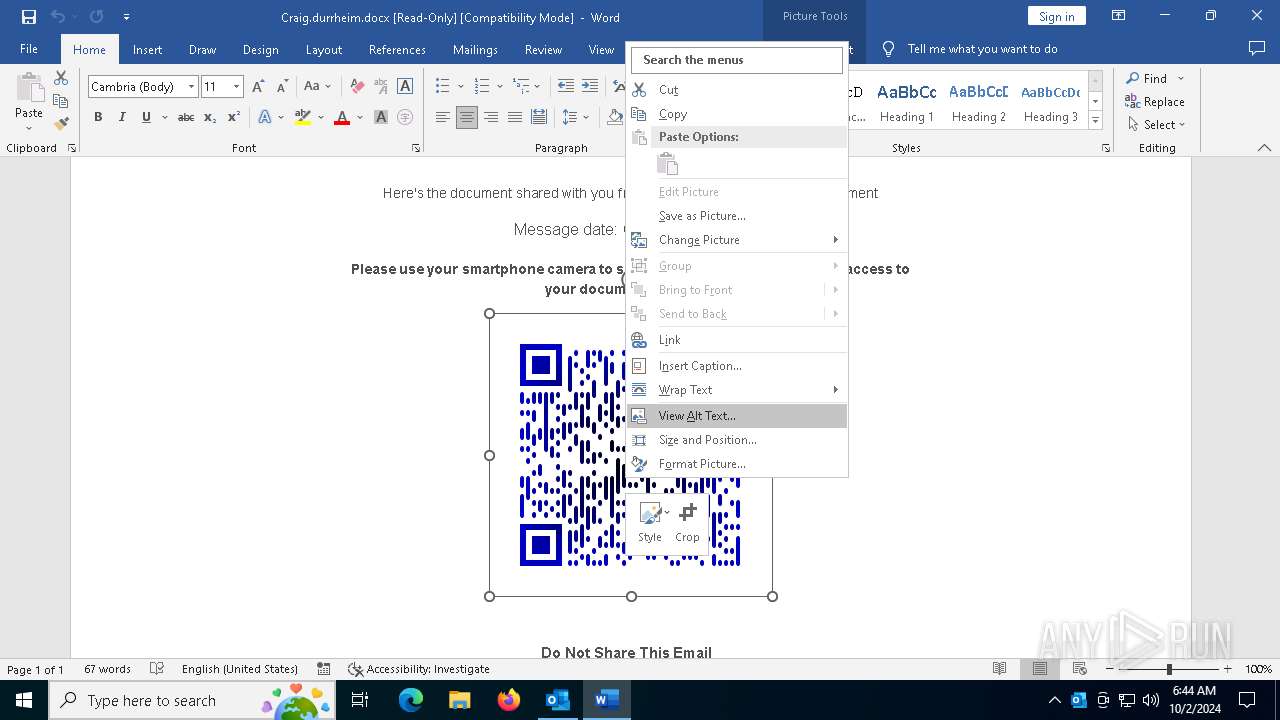
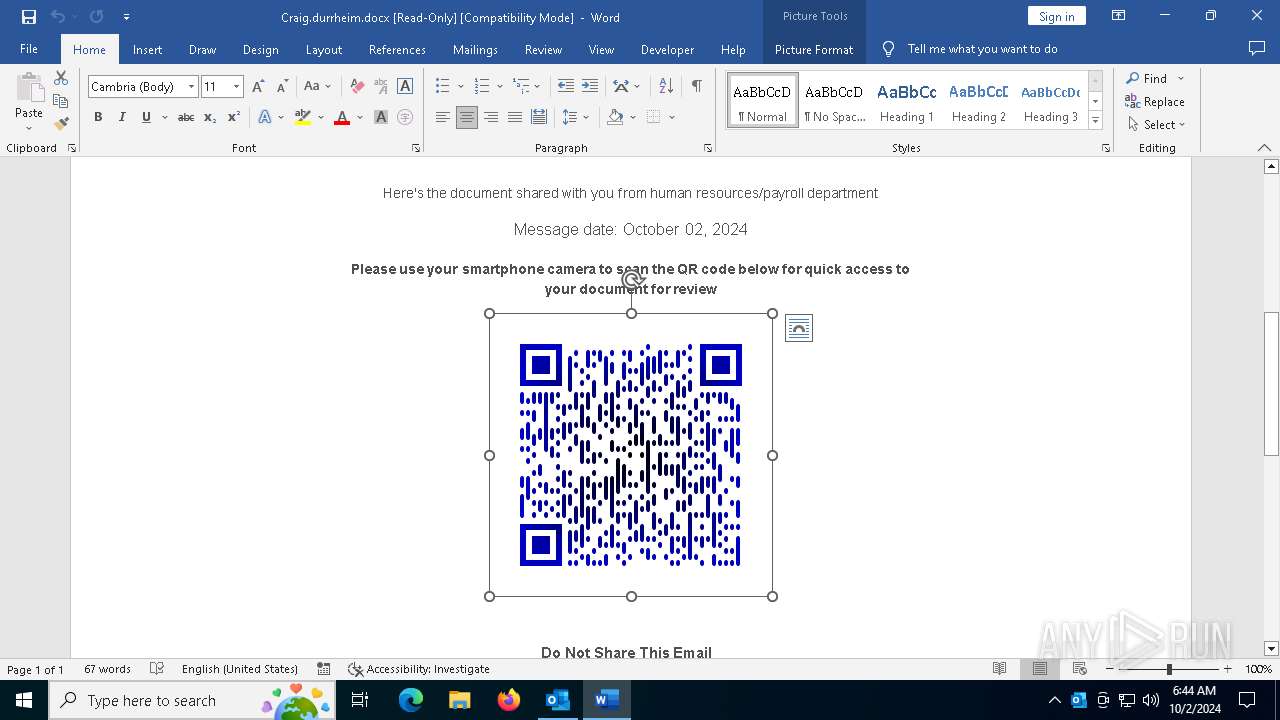
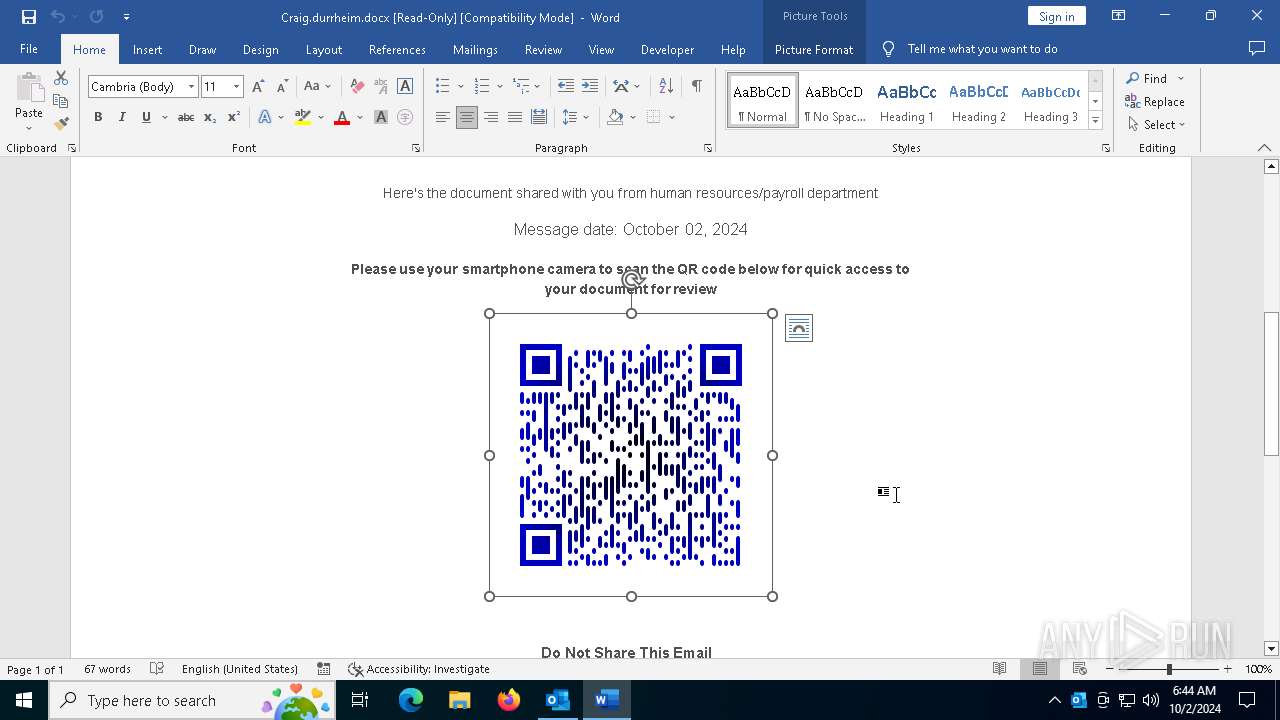
QR code contains URL with email
- WinRAR.exe (PID: 1184)
SUSPICIOUS
QR code with Mixed Case Domain (Potential Phishing)
- WinRAR.exe (PID: 1184)
INFO
Manual execution by a user
- OUTLOOK.EXE (PID: 6572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
137
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1184 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Att Centralian Planned Guide for Employee Appreciation Reference-h94yphpk7lqax.msg.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2608 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "05D9033E-B8D6-43E4-9E34-7850CDBF329C" "8AD380F4-F5DE-43BB-A3EE-60FAE52632E9" "6948" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 4424 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "C11AF2AF-58EC-4012-B680-026CDB710AB1" "99B51D9A-FF2F-4612-8C3F-E208A7DE961D" "6572" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
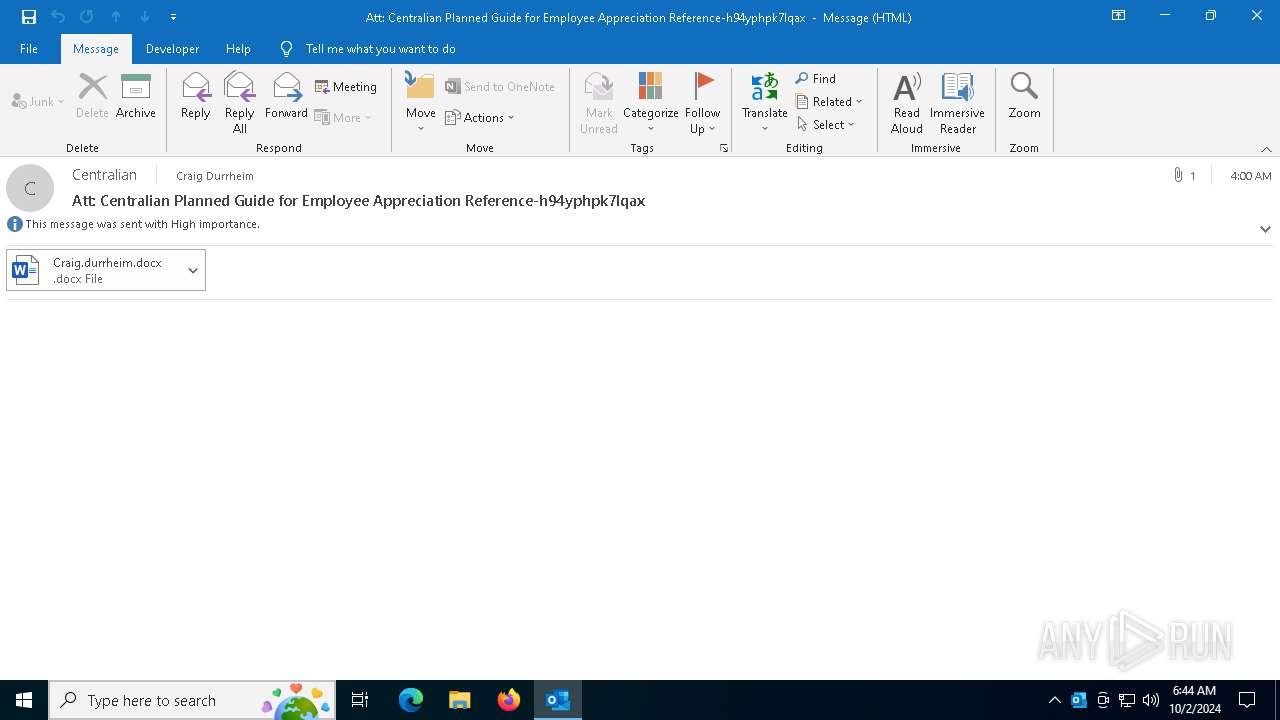
| 6572 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\Desktop\Att Centralian Planned Guide for Employee Appreciation Reference-h94yphpk7lqax.msg" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6948 | "C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\7OJ7MWAI\Craig.durrheim.docx" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
25 447
Read events
23 939
Write events
1 349
Delete events
159
Modification events
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Att Centralian Planned Guide for Employee Appreciation Reference-h94yphpk7lqax.msg.7z | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
24
Suspicious files
122
Text files
28
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6572 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6572 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:68EE1D143B11D52F95C087C6BE862A8C | SHA256:1099F7C549BF215A9289E2B890D0F7C66B05D7318924A907CADBC67094E505F8 | |||
| 6572 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:2DCF489239AF96769DBE5562403C3BB0 | SHA256:E62BB04ADE200D8CE25AD4B0BFE790A3EF5FE6BDB34DF1C7862E82072D7E8012 | |||
| 6572 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:3DB0C0C5FA01D862603AB9DD01ACB4E1 | SHA256:73506D288991B4EB4D2803A4090D77051B8AF702CEF9923EC52D6D45FF7FE411 | |||
| 6572 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\7OJ7MWAI\Craig.durrheim (002).docx | document | |
MD5:2BBC68145139D6AB446C274A956D4B23 | SHA256:F28B455B3D531252AE800B523158EF6B4EBA3F93483E589CFC340C218106F971 | |||
| 6572 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | der | |
MD5:00CD62D1C71F7CEBC93821164F916E82 | SHA256:B320F01682D14A9614DA0691AEE664C132ABEDF6E666189B3E53CA58E2247AFB | |||
| 6572 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:3E5E42CA78641FBA96E486E2EA970749 | SHA256:9DD54D9249C91E251185C3B5F5E12FEFF24FBDD8C1B7D45B04A5D838F6798480 | |||
| 6572 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\7OJ7MWAI\Craig.durrheim.docx:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 6572 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6572 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:024F3742EF91B839F28042F201705025 | SHA256:CE7DBD7C3FFFBDB6F628327486A23951003ABEF17FC5D762CB33FA340623CBD6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
94
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1308 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5476 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6572 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
3276 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5476 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6572 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6948 | WINWORD.EXE | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
6948 | WINWORD.EXE | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
6948 | WINWORD.EXE | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2356 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2356 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1308 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1308 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|