| URL: | http://x.bidswitch.net |
| Full analysis: | https://app.any.run/tasks/ab633cbb-8c81-471e-b941-aeb8307c666d |
| Verdict: | Malicious activity |
| Analysis date: | March 05, 2019, 20:14:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 41090CE9179F422F15AC98BC1595C11C |
| SHA1: | A9B1CA5C24C07D997A53DD99EE999EBB7DD22D72 |
| SHA256: | DE6A427795CF3D2F9EA16DD499188BF89FD5B23831F46621A2DBA1E48DC6C5C8 |
| SSDEEP: | 3:N1KGLgmRp:CGLdp |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads internet explorer settings
- iexplore.exe (PID: 3460)
Reads settings of System Certificates
- iexplore.exe (PID: 2944)
Application launched itself
- iexplore.exe (PID: 2944)
Reads Internet Cache Settings
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 2944)
Changes internet zones settings
- iexplore.exe (PID: 2944)
Creates files in the user directory
- iexplore.exe (PID: 3460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
33
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2944 | "C:\Program Files\Internet Explorer\iexplore.exe" http://x.bidswitch.net | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3460 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2944 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
509
Read events
420
Write events
86
Delete events
3
Modification events
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {5215DE05-3F83-11E9-BAD8-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30703000200050014000E002F005802 | |||
Executable files
0
Suspicious files
1
Text files
42
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bing[2].txt | — | |
MD5:— | SHA256:— | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\search[1].txt | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012019030520190306\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bing[1].txt | text | |
MD5:— | SHA256:— | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@www.bing[1].txt | text | |
MD5:— | SHA256:— | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\search[1].htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3460 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/fd/ls/l?IG=068412DF7AD44A98A94880844ADDF490&CID=081C71295B55634433947C3F5A9F6283&Type=Event.CPT&DATA={"pp":{"S":"L","FC":42,"BC":339,"SE":-1,"TC":-1,"H":386,"BP":542,"CT":557,"IL":3},"ad":[-1,-1,1260,560,1260,498,0]}&P=SERP&DA=DUB02 | US | image | 5.73 Kb | whitelisted |
3460 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rb/6m/cj,nj/f28dadef/aea7e831.js?bu=AckF | US | text | 174 b | whitelisted |
3460 | iexplore.exe | GET | 404 | 18.153.11.8:80 | http://x.bidswitch.net/ | US | text | 9 b | shared |
3460 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/5f/2s/cj,nj/bab57e12/ea8fe300.js | US | text | 2.75 Kb | whitelisted |
3460 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/6q/4T/cj,nj/347afee2/33036ea1.js | US | text | 1.77 Kb | whitelisted |
3460 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rms/BingCore.Bundle/cj,nj/3e6a7d75/9a358300.js?bu=rms+answers+Shared+BingCore%24ClientInstV2%24DuplicateXlsDefaultConfig*BingCore%24ClientInstV2%24SharedLocalStorageConfigDefault*BingCore%24shared*BingCore%24env.override*Empty*BingCore%24event.custom.fix*BingCore%24event.native*BingCore%24onHTML*BingCore%24dom*BingCore%24cookies*BingCore%24rmsajax*BingCore%24ClientInstV2%24LogUploadCapFeatureDisabled*BingCore%24ClientInstV2%24ClientInstConfigSeparateOfflineQueue*BingCore%24clientinst*BingCore%24replay*BingCore%24Animation*BingCore%24fadeAnimation*BingCore%24framework | US | text | 4.95 Kb | whitelisted |
3460 | iexplore.exe | GET | 200 | 204.79.197.222:80 | http://fcdc3b1a91e66e5df6c878f75616341a.clo.footprintdns.com/apc/trans.gif | US | image | 43 b | suspicious |
3460 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/Passport.aspx?popup=1 | US | html | 230 b | whitelisted |
3460 | iexplore.exe | GET | 200 | 70.37.73.37:80 | http://1fa667bda83a9911283190c4de9cd6ea.clo.footprintdns.com/apc/trans.gif | US | image | 43 b | whitelisted |
3460 | iexplore.exe | GET | 200 | 204.79.197.222:80 | http://4dfce1839cd9bb497c7845aa89ef994b.clo.footprintdns.com/apc/trans.gif | US | image | 43 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2944 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3460 | iexplore.exe | 18.153.11.8:80 | x.bidswitch.net | — | US | unknown |
2944 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3460 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3460 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3460 | iexplore.exe | 204.79.197.222:80 | fcdc3b1a91e66e5df6c878f75616341a.clo.footprintdns.com | Microsoft Corporation | US | whitelisted |
3460 | iexplore.exe | 65.55.163.90:443 | login.live.com | Microsoft Corporation | US | unknown |
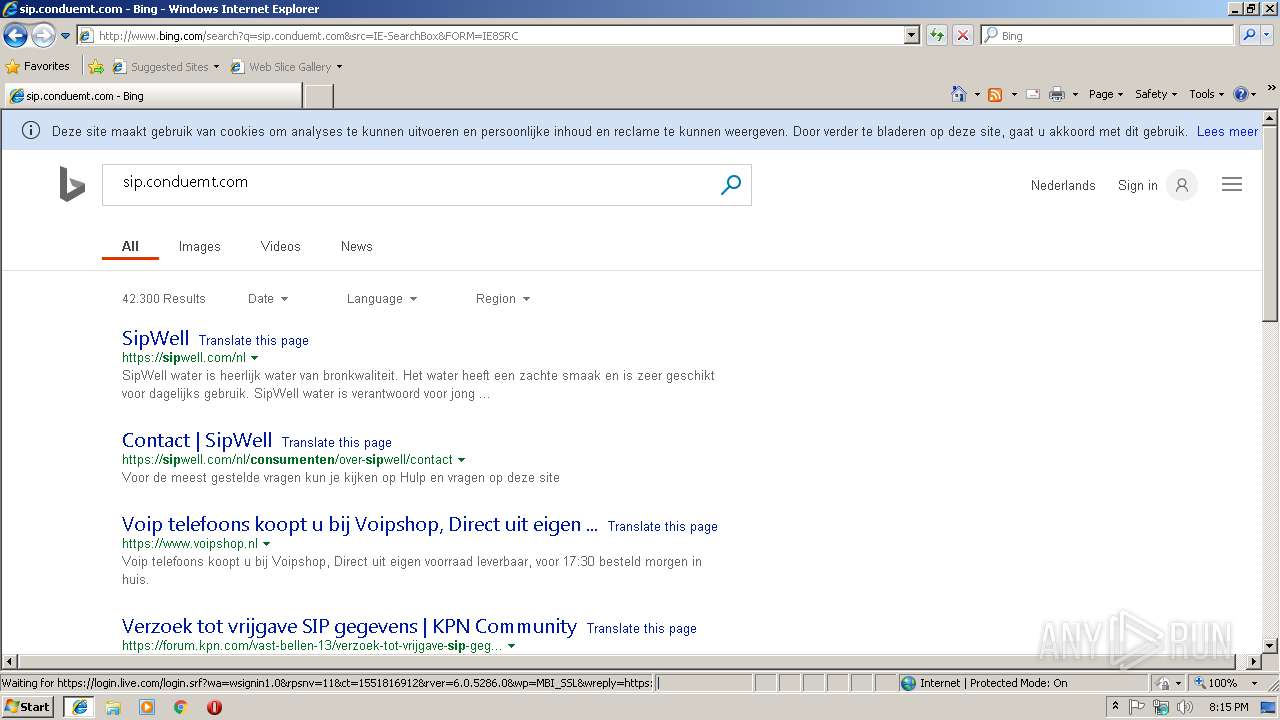
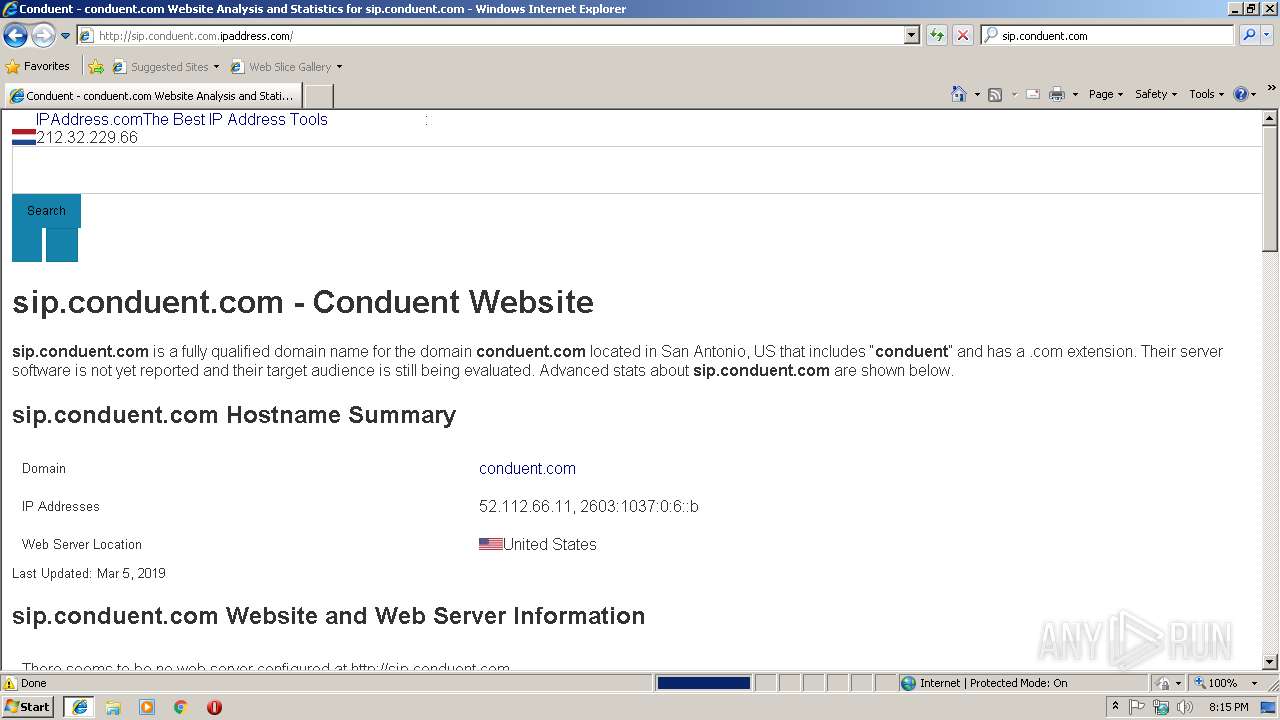
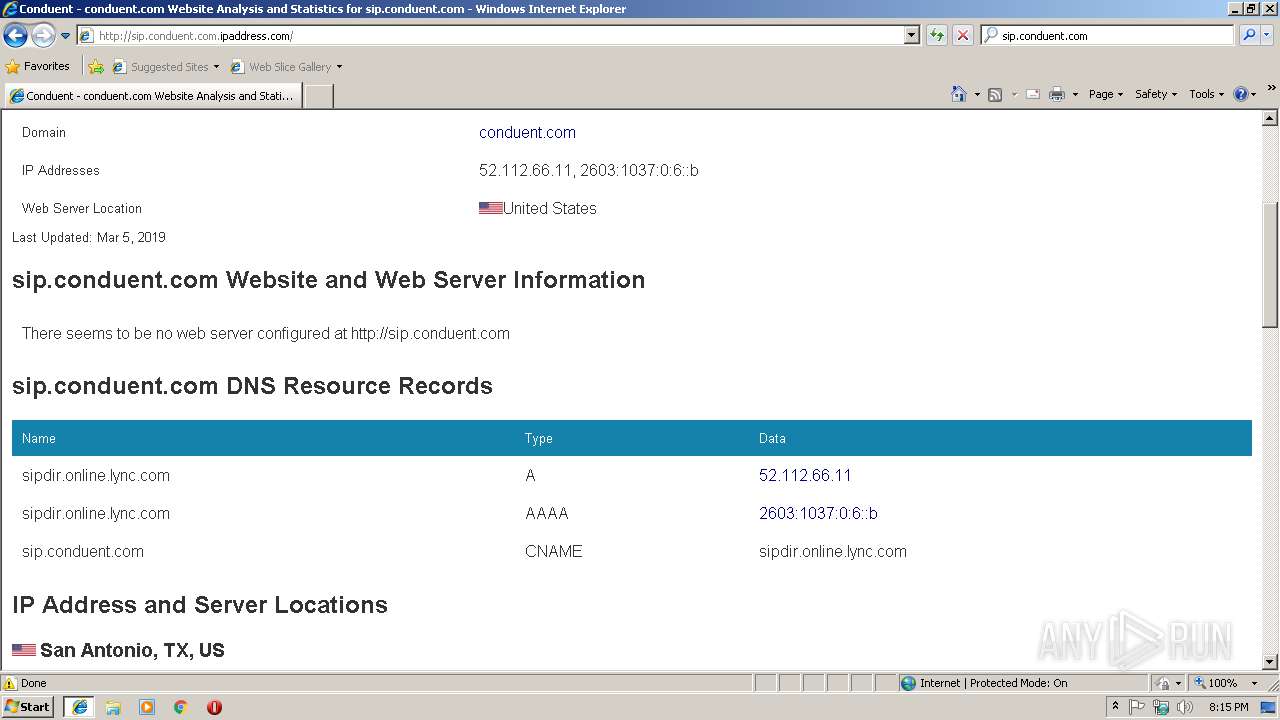
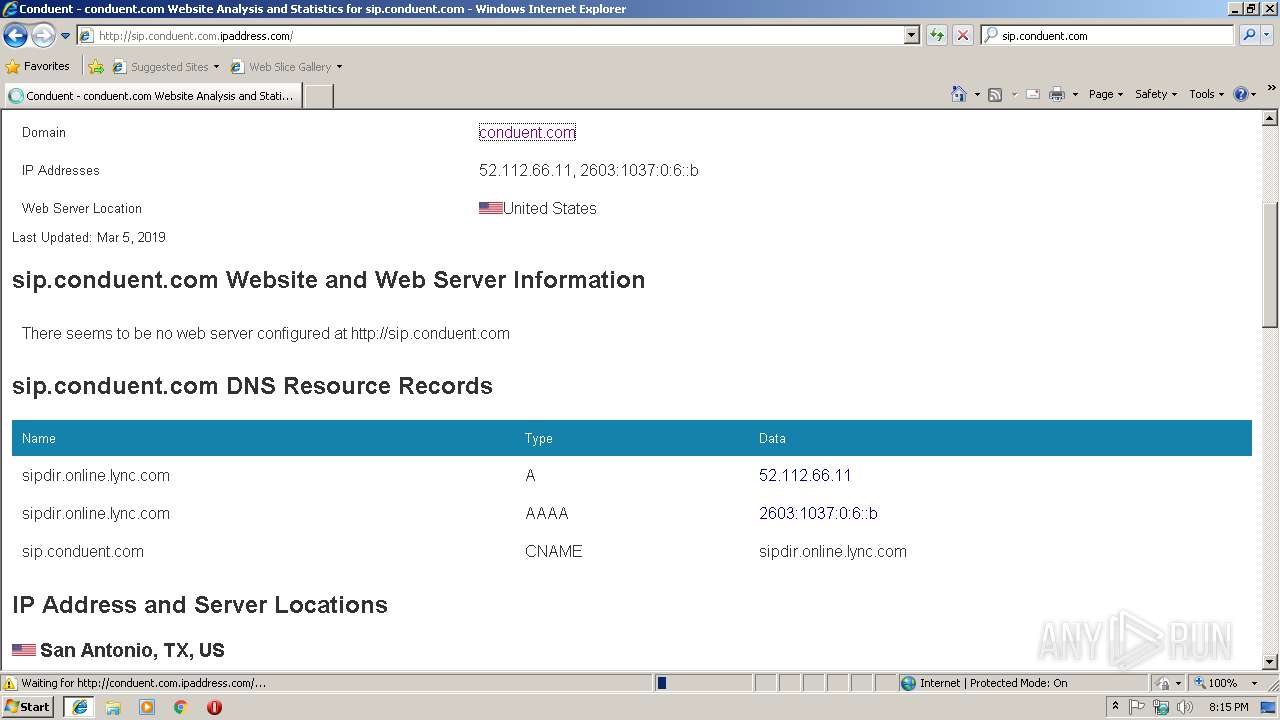
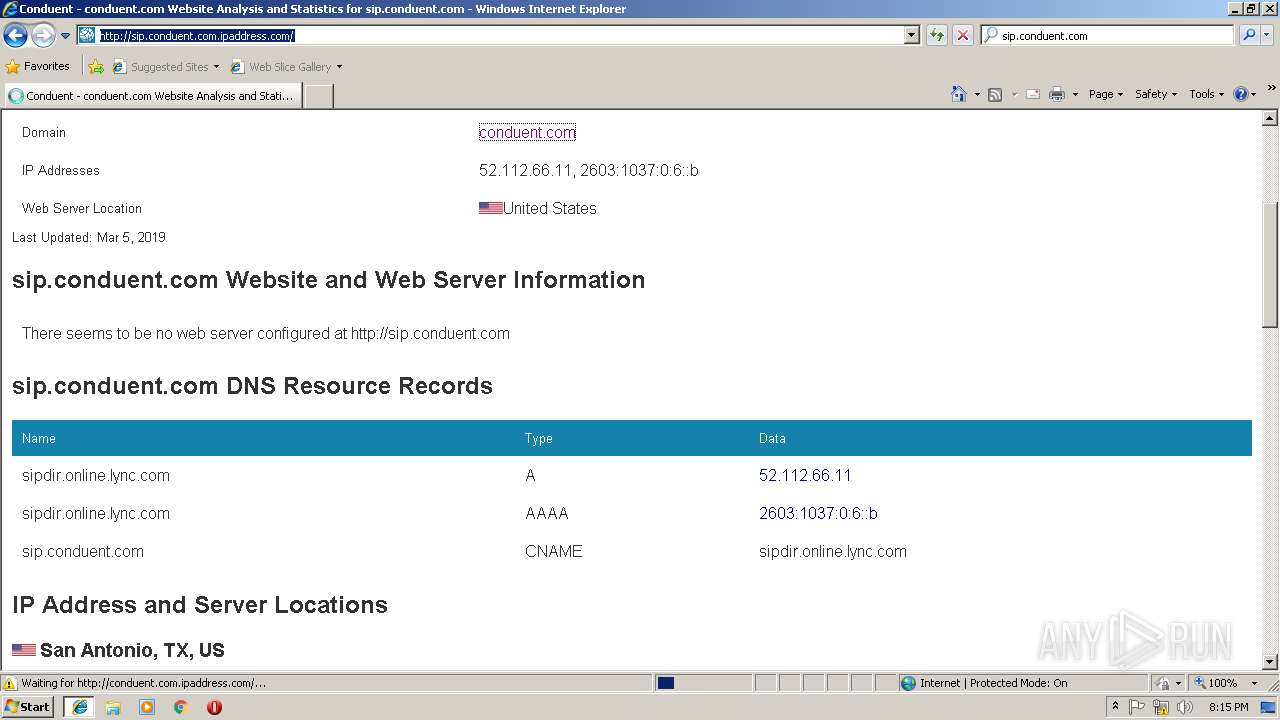
3460 | iexplore.exe | 209.126.119.176:80 | sip.conduent.com.ipaddress.com | server4you Inc. | US | malicious |
3460 | iexplore.exe | 209.126.119.176:443 | sip.conduent.com.ipaddress.com | server4you Inc. | US | malicious |
3460 | iexplore.exe | 62.138.6.165:443 | wh.ip-adress.com | Host Europe GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
x.bidswitch.net |
| shared |
www.bing.com |
| whitelisted |
sip.conduemt.com |
| unknown |
login.live.com |
| whitelisted |
fcdc3b1a91e66e5df6c878f75616341a.clo.footprintdns.com |
| suspicious |
1fa667bda83a9911283190c4de9cd6ea.clo.footprintdns.com |
| unknown |
4dfce1839cd9bb497c7845aa89ef994b.clo.footprintdns.com |
| suspicious |
fp.msedge.net |
| whitelisted |
a4.bing.com |
| whitelisted |
sip.conduent.com.ipaddress.com |
| malicious |