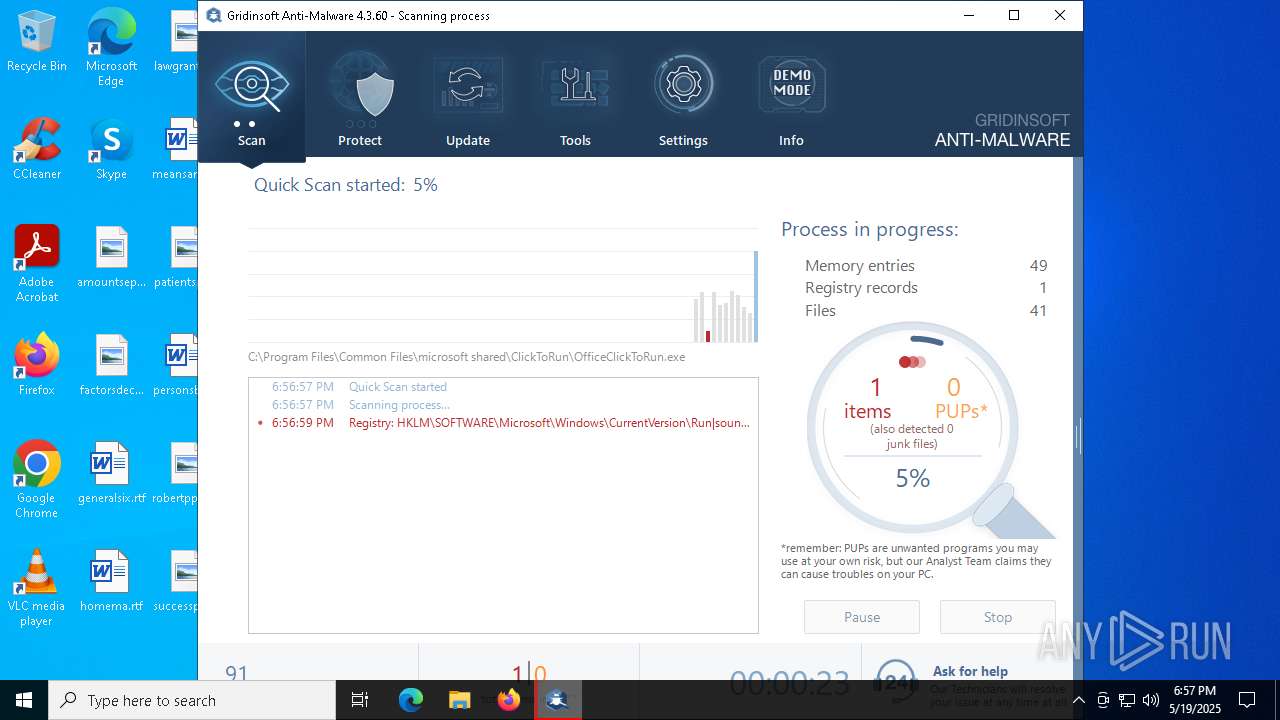
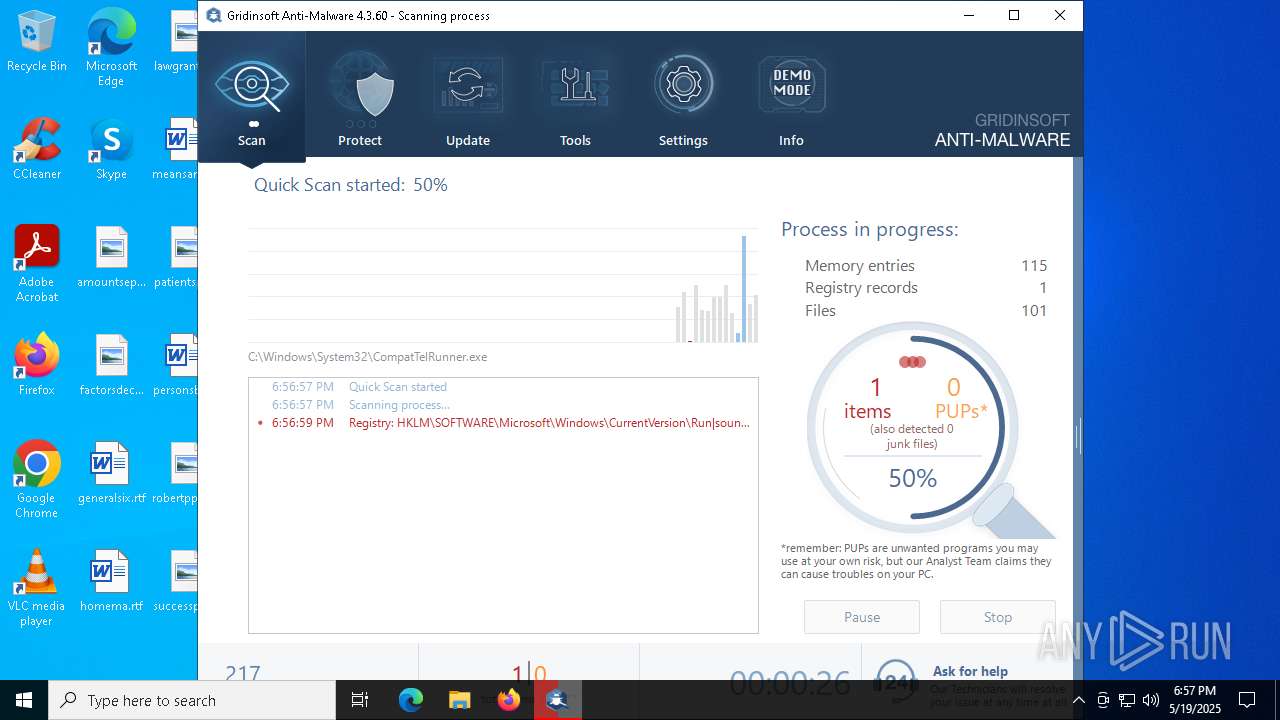
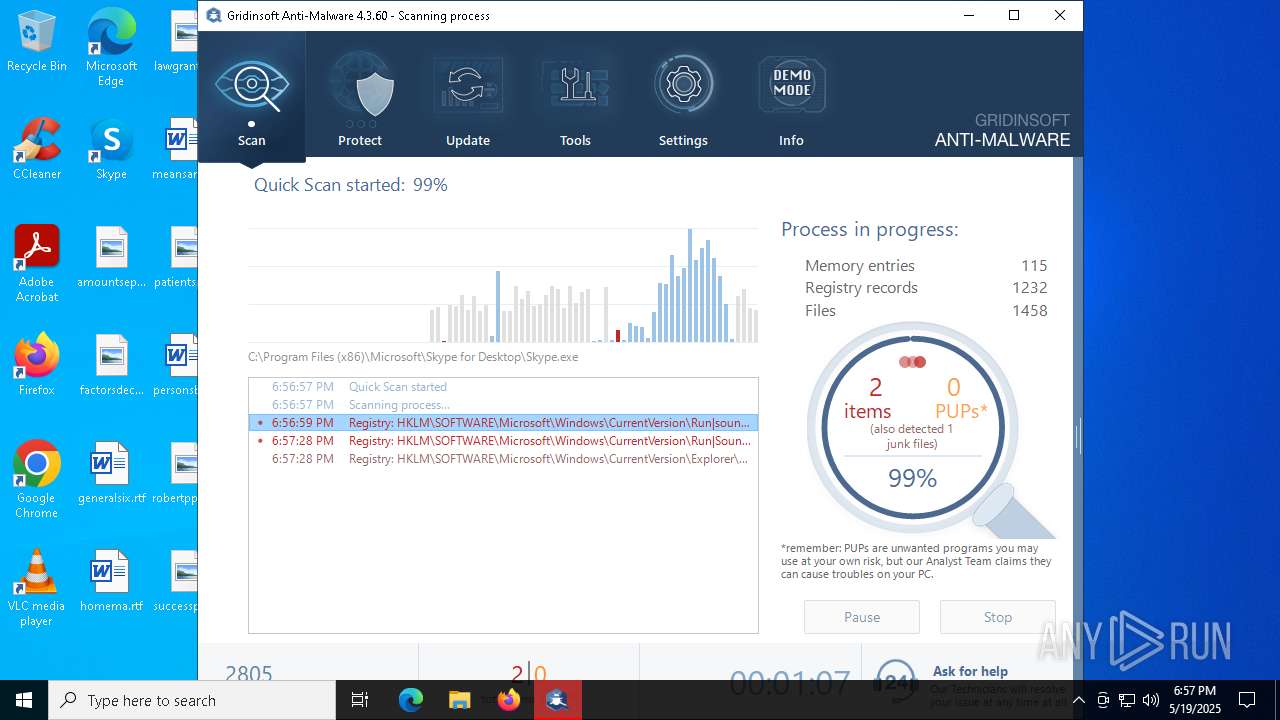
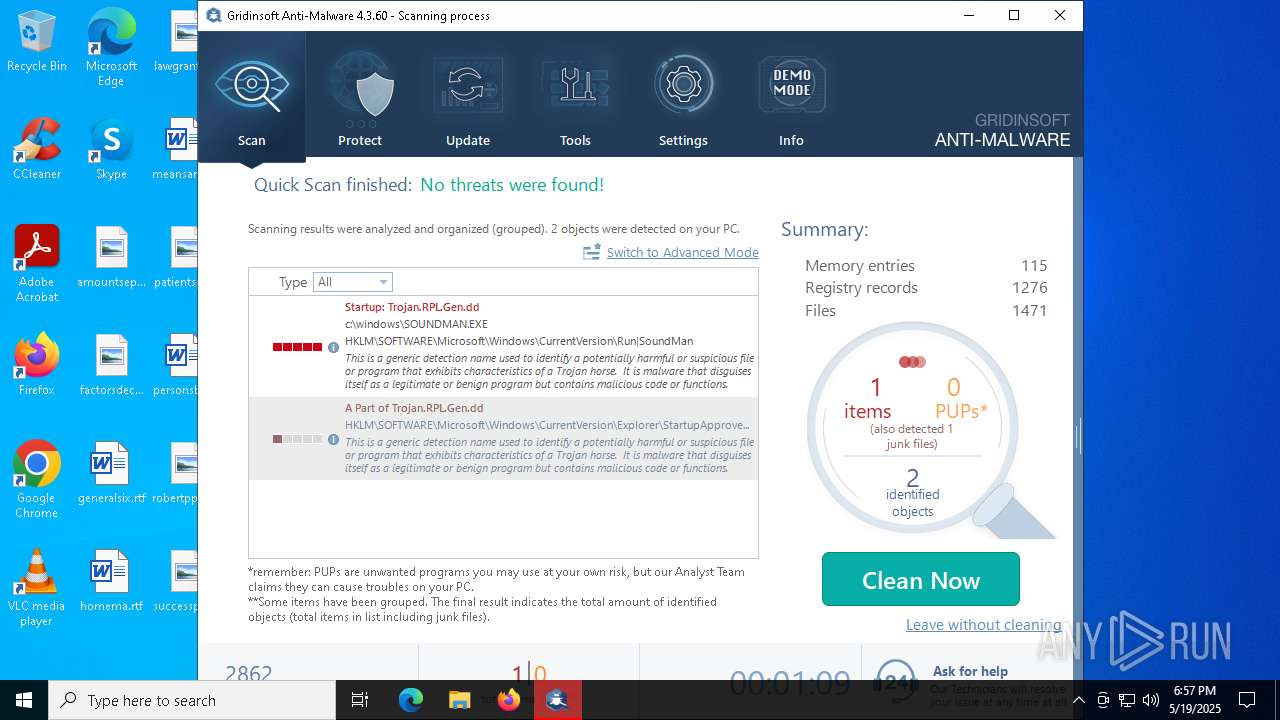
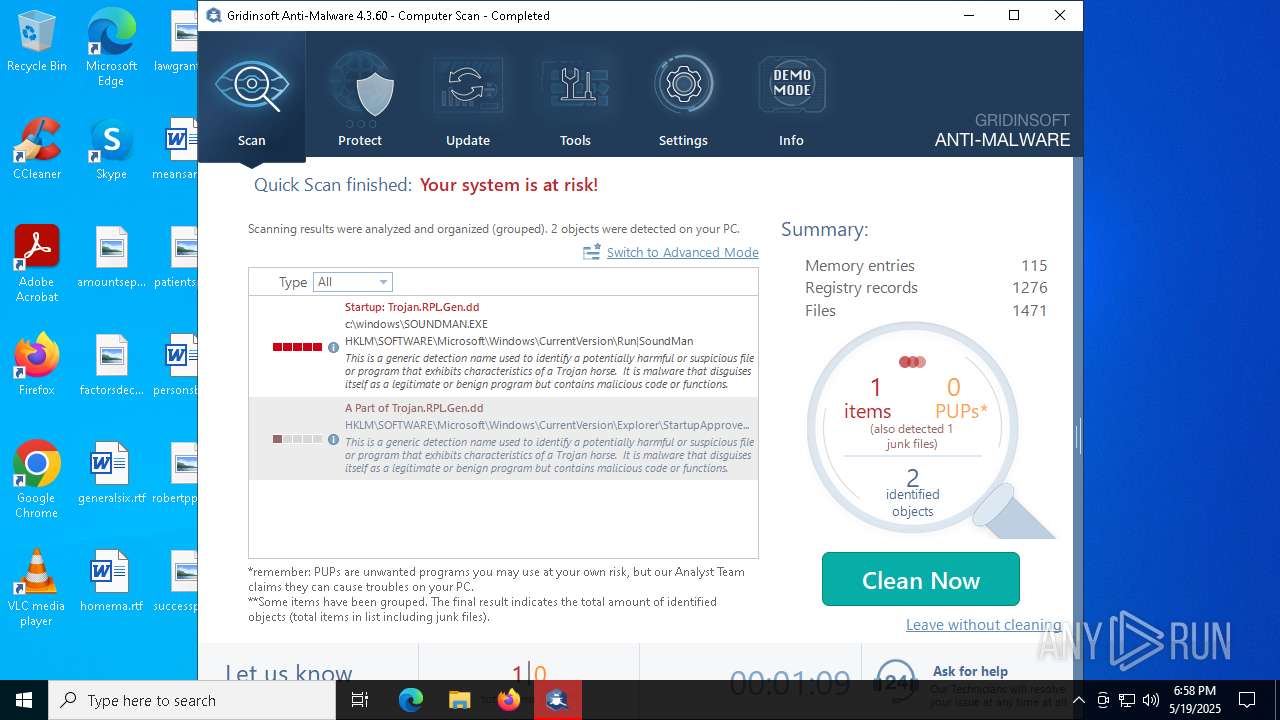
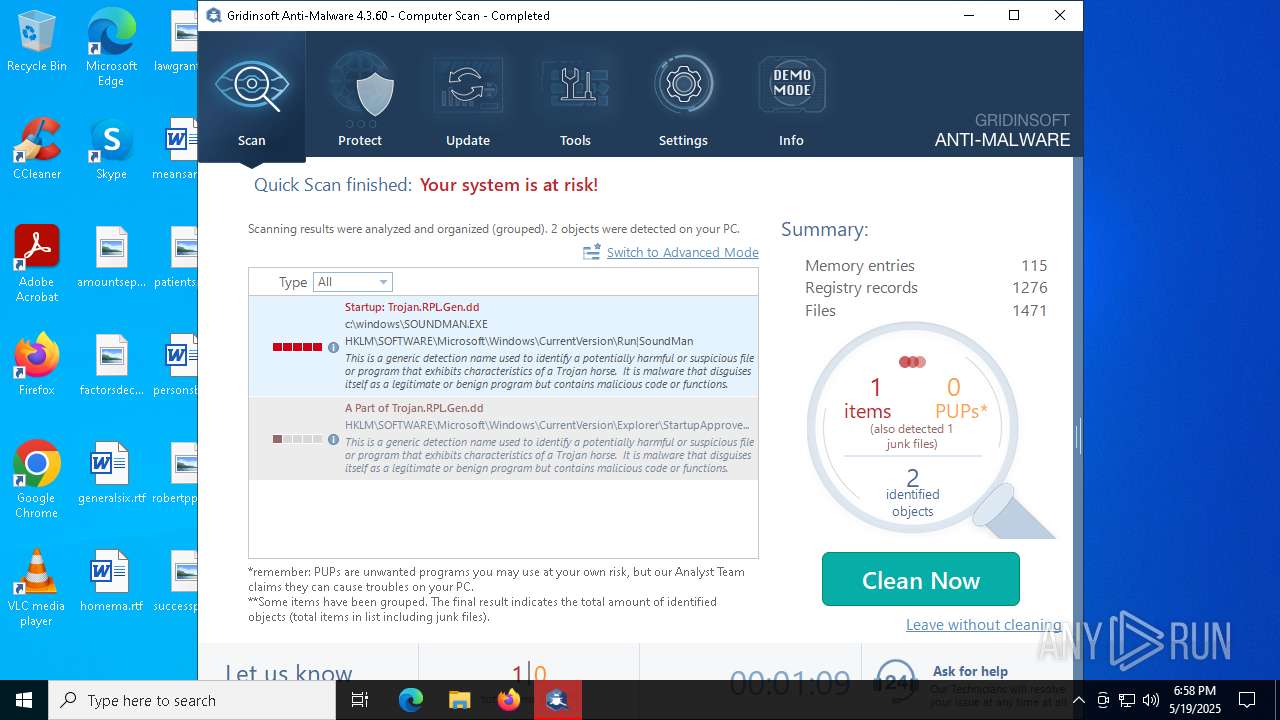
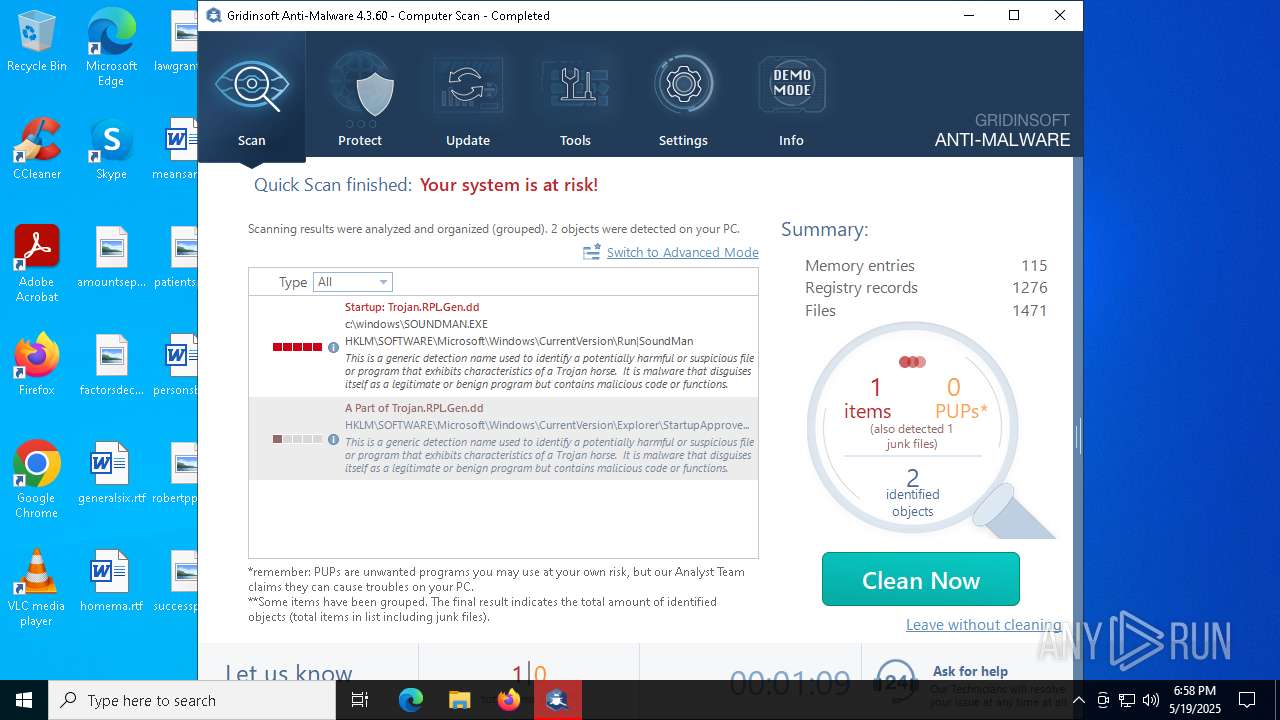
| File name: | setup-antimalware-1024.exe |
| Full analysis: | https://app.any.run/tasks/ad352044-5d3e-45e1-8909-365feaa0f2b9 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | May 19, 2025, 18:55:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | D4BC14D79ADB65D8A03C1043F0C2FF07 |
| SHA1: | D454154FE8241EECF2A53F658AAEED805D25FECC |
| SHA256: | DE3E7309A038212864C3F1D717E29CBC3528390F1A8A99B5AEE924F1FDDC2508 |
| SSDEEP: | 24576:n9HmIVL1Tvp/MdafdwXCK0W8R/XJe0oYbdVRcTjCPJrIklTG0Z:RmIVXCafdjJDM0oYbTRejCxrIklTG0Z |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- DEJ2EXhm.DOr (PID: 4776)
Bypass execution policy to execute commands
- powershell.exe (PID: 7508)
Changes Windows Defender settings
- DEJ2EXhm.DOr (PID: 4776)
Actions looks like stealing of personal data
- gsam.exe (PID: 5344)
- gsam.exe (PID: 7084)
Steals credentials from Web Browsers
- gsam.exe (PID: 5344)
- gsam.exe (PID: 7084)
Changes the autorun value in the registry
- rundll32.exe (PID: 2616)
- rundll32.exe (PID: 6132)
- rundll32.exe (PID: 7876)
Changes powershell execution policy (Bypass)
- DEJ2EXhm.DOr (PID: 4776)
DCRAT has been detected (YARA)
- gsam.exe (PID: 7084)
SUSPICIOUS
Starts application with an unusual extension
- setup-antimalware-1024.exe (PID: 7536)
Reads security settings of Internet Explorer
- setup-antimalware-1024.exe (PID: 7536)
- gsam.exe (PID: 7084)
Malware-specific behavior (creating "System.dll" in Temp)
- DEJ2EXhm.DOr (PID: 4776)
Drops 7-zip archiver for unpacking
- DEJ2EXhm.DOr (PID: 4776)
Executable content was dropped or overwritten
- DEJ2EXhm.DOr (PID: 4776)
- rundll32.exe (PID: 6132)
- drvinst.exe (PID: 7788)
- rundll32.exe (PID: 7876)
The process creates files with name similar to system file names
- DEJ2EXhm.DOr (PID: 4776)
Starts POWERSHELL.EXE for commands execution
- DEJ2EXhm.DOr (PID: 4776)
Process drops legitimate windows executable
- DEJ2EXhm.DOr (PID: 4776)
Drops a system driver (possible attempt to evade defenses)
- DEJ2EXhm.DOr (PID: 4776)
- rundll32.exe (PID: 6132)
- drvinst.exe (PID: 7788)
- rundll32.exe (PID: 7876)
The process bypasses the loading of PowerShell profile settings
- DEJ2EXhm.DOr (PID: 4776)
There is functionality for taking screenshot (YARA)
- DEJ2EXhm.DOr (PID: 4776)
- gsam.exe (PID: 7084)
Creates a software uninstall entry
- DEJ2EXhm.DOr (PID: 4776)
The process verifies whether the antivirus software is installed
- gsam.exe (PID: 5344)
- gsam.exe (PID: 7084)
Uses RUNDLL32.EXE to load library
- DEJ2EXhm.DOr (PID: 4776)
Process drops SQLite DLL files
- DEJ2EXhm.DOr (PID: 4776)
Creates files in the driver directory
- drvinst.exe (PID: 7788)
Creates or modifies Windows services
- drvinst.exe (PID: 7772)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 7940)
Connects to unusual port
- gsam.exe (PID: 7084)
Found regular expressions for crypto-addresses (YARA)
- gsam.exe (PID: 7084)
INFO
The sample compiled with english language support
- setup-antimalware-1024.exe (PID: 7536)
- DEJ2EXhm.DOr (PID: 4776)
- rundll32.exe (PID: 6132)
- drvinst.exe (PID: 7788)
- rundll32.exe (PID: 7876)
Reads the computer name
- setup-antimalware-1024.exe (PID: 7536)
- DEJ2EXhm.DOr (PID: 4776)
- gsam.exe (PID: 5344)
- drvinst.exe (PID: 7772)
- drvinst.exe (PID: 7788)
- gsam.exe (PID: 7084)
Checks proxy server information
- setup-antimalware-1024.exe (PID: 7536)
- gsam.exe (PID: 7084)
Checks supported languages
- setup-antimalware-1024.exe (PID: 7536)
- DEJ2EXhm.DOr (PID: 4776)
- gsam.exe (PID: 5344)
- drvinst.exe (PID: 7788)
- drvinst.exe (PID: 7772)
- gsam.exe (PID: 7084)
Reads the machine GUID from the registry
- setup-antimalware-1024.exe (PID: 7536)
- drvinst.exe (PID: 7788)
- gsam.exe (PID: 7084)
Creates files or folders in the user directory
- setup-antimalware-1024.exe (PID: 7536)
- gsam.exe (PID: 7084)
UPX packer has been detected
- setup-antimalware-1024.exe (PID: 7536)
Create files in a temporary directory
- DEJ2EXhm.DOr (PID: 4776)
- setup-antimalware-1024.exe (PID: 7536)
- rundll32.exe (PID: 6132)
Reads the software policy settings
- setup-antimalware-1024.exe (PID: 7536)
- slui.exe (PID: 7616)
- drvinst.exe (PID: 7788)
- gsam.exe (PID: 7084)
Compiled with Borland Delphi (YARA)
- setup-antimalware-1024.exe (PID: 7536)
- DEJ2EXhm.DOr (PID: 4776)
- gsam.exe (PID: 7084)
- slui.exe (PID: 5800)
Reads CPU info
- setup-antimalware-1024.exe (PID: 7536)
- gsam.exe (PID: 7084)
Creates files in the program directory
- DEJ2EXhm.DOr (PID: 4776)
- gsam.exe (PID: 5344)
- gsam.exe (PID: 7084)
Reads Environment values
- gsam.exe (PID: 5344)
- gsam.exe (PID: 7084)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7508)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7508)
Reads security settings of Internet Explorer
- runonce.exe (PID: 7568)
- runonce.exe (PID: 7704)
- runonce.exe (PID: 5548)
Reads the time zone
- runonce.exe (PID: 7568)
- runonce.exe (PID: 7704)
- runonce.exe (PID: 5548)
Creates files in the driver directory
- rundll32.exe (PID: 7876)
Process checks computer location settings
- gsam.exe (PID: 7084)
- setup-antimalware-1024.exe (PID: 7536)
Reads product name
- gsam.exe (PID: 7084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (38.2) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (37.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.2) |
| .exe | | | Win32 Executable (generic) (6.3) |
| .exe | | | Win16/32 Executable Delphi generic (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:07:19 19:33:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 831488 |
| InitializedDataSize: | 61440 |
| UninitializedDataSize: | 1548288 |
| EntryPoint: | 0x2450f0 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.1.0.88 |
| ProductVersionNumber: | 4.1.0.88 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Gridinsoft® Anti-Malware Web Installer |
| ProductVersion: | 4.1.0 |
| CompanyName: | Gridinsoft LLC |
| LegalCopyright: | © Gridinsoft LLC, 2022 |
| LegalTrademarks: | Gridinsoft® |
| InternalName: | AntiMalwareInstaller |
| OriginalFileName: | AntiMalwareInstaller.exe |
| FileVersion: | 4.1.0.88 |
| FileDescription: | Anti-Malware Web Installer |
Total processes
160
Monitored processes
24
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1244 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | C:\WINDOWS\system32\RUNDLL32.EXE SETUPAPI.DLL,InstallHinfSection DefaultUninstall 128 C:\Program Files\GridinSoft Anti-Malware\Driver\GSDriver.inf | C:\Windows\System32\rundll32.exe | DEJ2EXhm.DOr | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | C:\Users\admin\AppData\Local\Temp\DEJ2EXhm.DOr /S /I /D=C:\Program Files\GridinSoft Anti-Malware\ | C:\Users\admin\AppData\Local\Temp\DEJ2EXhm.DOr | setup-antimalware-1024.exe | ||||||||||||
User: admin Company: Gridinsoft LLC Integrity Level: HIGH Description: GridinSoft Anti-Malware 4.3.60 Setup Exit code: 0 Version: 4.3.60.5852 Modules
| |||||||||||||||
| 5344 | "C:\Program Files\GridinSoft Anti-Malware\gsam.exe" -add-shortcut | C:\Program Files\GridinSoft Anti-Malware\gsam.exe | DEJ2EXhm.DOr | ||||||||||||
User: admin Company: Gridinsoft LLC Integrity Level: HIGH Description: Anti-Malware (64-bit) Exit code: 0 Version: 4.3.60.5852 Modules
| |||||||||||||||
| 5548 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5800 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6132 | C:\WINDOWS\system32\RUNDLL32.EXE SETUPAPI.DLL,InstallHinfSection DefaultInstall 132 C:\Program Files\GridinSoft Anti-Malware\Driver\GSDriver.inf | C:\Windows\System32\rundll32.exe | DEJ2EXhm.DOr | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7084 | "C:\Program Files\GridinSoft Anti-Malware\gsam.exe" | C:\Program Files\GridinSoft Anti-Malware\gsam.exe | setup-antimalware-1024.exe | ||||||||||||
User: admin Company: Gridinsoft LLC Integrity Level: HIGH Description: Anti-Malware (64-bit) Version: 4.3.60.5852 Modules
| |||||||||||||||
| 7368 | "C:\WINDOWS\system32\regsvr32.exe" /s /u "C:\Program Files\GridinSoft Anti-Malware\shellext.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | DEJ2EXhm.DOr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7440 | "C:\Users\admin\Desktop\setup-antimalware-1024.exe" | C:\Users\admin\Desktop\setup-antimalware-1024.exe | — | explorer.exe | |||||||||||
User: admin Company: Gridinsoft LLC Integrity Level: MEDIUM Description: Anti-Malware Web Installer Exit code: 3221226540 Version: 4.1.0.88 Modules
| |||||||||||||||
Total events
67 340
Read events
67 212
Write events
120
Delete events
8
Modification events
| (PID) Process: | (7536) setup-antimalware-1024.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7536) setup-antimalware-1024.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7536) setup-antimalware-1024.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7536) setup-antimalware-1024.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\GridinSoft\Anti-Malware |
| Operation: | write | Name: | InstallerFileName |
Value: setup-antimalware-1024.exe | |||
| (PID) Process: | (7568) runonce.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | GrpConv |
Value: grpconv -o | |||
| (PID) Process: | (6132) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (4776) DEJ2EXhm.DOr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\GridinSoft Anti-Malware |
| Operation: | write | Name: | DisplayVersion |
Value: 4.3.60 | |||
| (PID) Process: | (4776) DEJ2EXhm.DOr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\GridinSoft Anti-Malware |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\GridinSoft Anti-Malware\uninst.exe | |||
| (PID) Process: | (4776) DEJ2EXhm.DOr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\GridinSoft Anti-Malware |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\GridinSoft Anti-Malware | |||
| (PID) Process: | (4776) DEJ2EXhm.DOr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\GridinSoft Anti-Malware |
| Operation: | write | Name: | DisplayName |
Value: GridinSoft Anti-Malware | |||
Executable files
49
Suspicious files
289
Text files
65
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7536 | setup-antimalware-1024.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\gsam-4.3.60.5852-setup[1].exe | — | |
MD5:— | SHA256:— | |||
| 7536 | setup-antimalware-1024.exe | C:\Users\admin\AppData\Local\Temp\DEJ2EXhm.DOr | — | |
MD5:— | SHA256:— | |||
| 4776 | DEJ2EXhm.DOr | C:\Program Files\GridinSoft Anti-Malware\gsam.exe | executable | |
MD5:E510F9713227AF9E7DE668F4A563297A | SHA256:2DACCC181D3D1EA3DC87C302C3DB2EAEFABA4E1D050C501684C538A76827DADF | |||
| 4776 | DEJ2EXhm.DOr | C:\Program Files\GridinSoft Anti-Malware\gsInetSecurity.dll | executable | |
MD5:0C32B8440CF3F7F335142AA0FC41CFB1 | SHA256:C9A469F258E529C8974AA315886B4E7543C981C6D2BEB92B6B3CEFCB87CB7F67 | |||
| 4776 | DEJ2EXhm.DOr | C:\Program Files\GridinSoft Anti-Malware\uninst.exe | executable | |
MD5:AC0FEB2F35412B74E564043C59B55ED7 | SHA256:35CA46C6BC8FCFF9FA567498B80392EE8C54E6856F1AFE5637EB06D57CAC0B1E | |||
| 4776 | DEJ2EXhm.DOr | C:\Program Files\GridinSoft Anti-Malware\shellext.dll | executable | |
MD5:86B25FDE5B216C9671F8D55F25253D9E | SHA256:5D8335270E22AD9B0250940631F08C3411D0575869C23CCCED819809E76CFEB0 | |||
| 4776 | DEJ2EXhm.DOr | C:\Program Files\GridinSoft Anti-Malware\7z.dll | executable | |
MD5:5BCB868237730591D761B7C85DC83495 | SHA256:36B179985D8DFA5CB6068AFE032568ED19513B16B578B32FCD9EC29F71C41F6D | |||
| 4776 | DEJ2EXhm.DOr | C:\Program Files\GridinSoft Anti-Malware\libmem.dll | executable | |
MD5:A91AD44260CB64A971E60EA210D0F9D6 | SHA256:8193EF3964CA00C84811AA5BAF0CEC652E8C89EAAEEADFC5763B2B7922F8EF7F | |||
| 4776 | DEJ2EXhm.DOr | C:\Program Files\GridinSoft Anti-Malware\pFilters.dll | executable | |
MD5:61E33977A8DECDFCA372F9AAFEC7F334 | SHA256:D27EEB8628B99E66D3C27FDF52C457AEA03F01E23E6C8ED632B847B99B17D936 | |||
| 4776 | DEJ2EXhm.DOr | C:\Program Files\GridinSoft Anti-Malware\offreg.dll | executable | |
MD5:1EAB65173F446A3E116556CE53C7717D | SHA256:54CE76E23156BDB9873014F9DA22C023339EE3F1E5A3B7D70C1A9E1016865A50 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
80
DNS requests
39
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7536 | setup-antimalware-1024.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.188:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7536 | setup-antimalware-1024.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
1276 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7084 | gsam.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7084 | gsam.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
1276 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7084 | gsam.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAxzMedPflRKIhs2702zVHA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.188:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7536 | setup-antimalware-1024.exe | 142.93.183.102:443 | bind.gridinsoft.com | DIGITALOCEAN-ASN | US | suspicious |
7536 | setup-antimalware-1024.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
bind.gridinsoft.com |
| unknown |
x1.c.lencr.org |
| whitelisted |
8a82d43e7382eb560508-db1e9047be4d687c9233d1b7230c4dbc.ssl.cf2.rackcdn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |