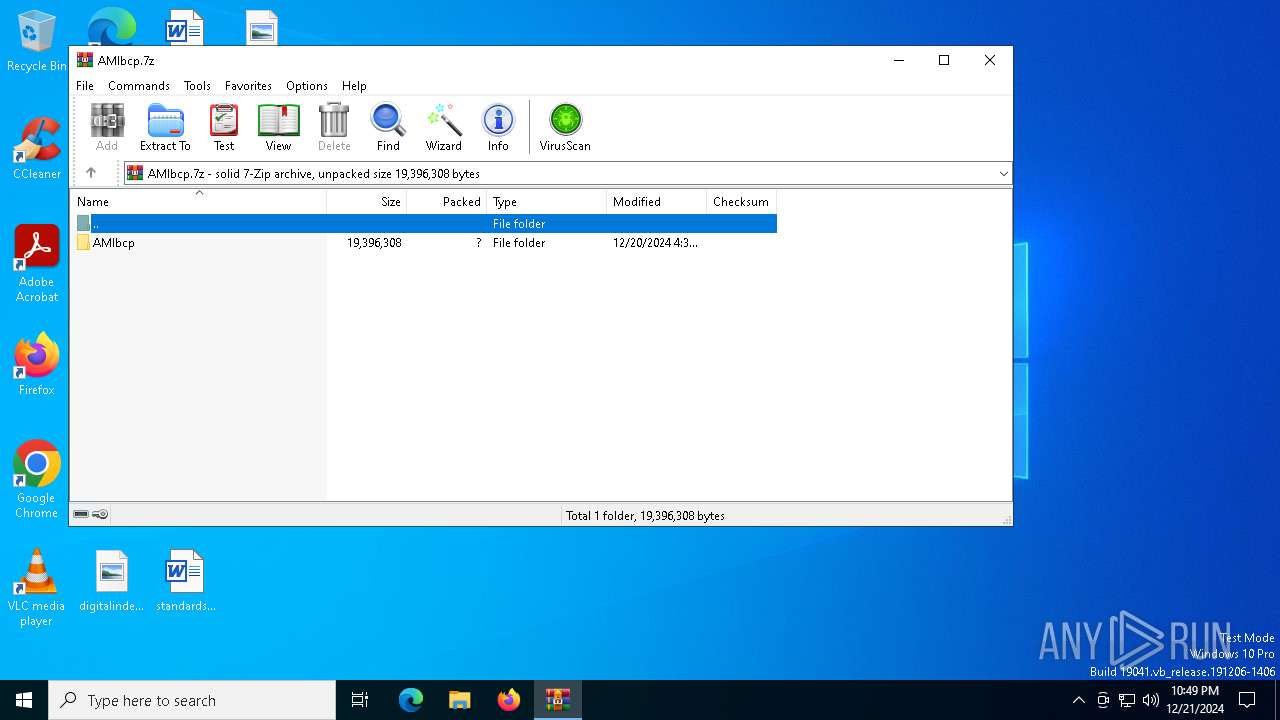
| File name: | AMlbcp.7z |
| Full analysis: | https://app.any.run/tasks/45f4ae12-61a6-45f9-83ee-8cdd6f033565 |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2024, 22:49:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.3 |
| MD5: | 108FEEBA23B1676D1A59D5BF8287D9B8 |
| SHA1: | 81EC2B6D812EF164B3A7EBFD9B45E9B5AC7AA687 |
| SHA256: | DE29FEDA86A248D55C534DAC7FDA67F56359AC1DD2CBD064E5CD4AC17A0ECEE3 |
| SSDEEP: | 98304:OewA+b3My+x07yZHFx+p0+4n/PBQr3rjjq2O1dOqVN3TFP++W1O86YSfiiUvGYXa:eCvNkSPwkw+zC8hDYz4XzD0KDQO5 |
MALICIOUS
Executing a file with an untrusted certificate
- AMlbcp.exe (PID: 6148)
- AMlbcp.exe (PID: 5988)
- AMlbcp.exe (PID: 2940)
SUSPICIOUS
Reads security settings of Internet Explorer
- AMlbcp.exe (PID: 5988)
- AMlbcp.exe (PID: 6148)
Reads the Windows owner or organization settings
- AMlbcp.exe (PID: 5988)
- AMlbcp.exe (PID: 2940)
Application launched itself
- AMlbcp.exe (PID: 6148)
- AMlbcp.exe (PID: 5988)
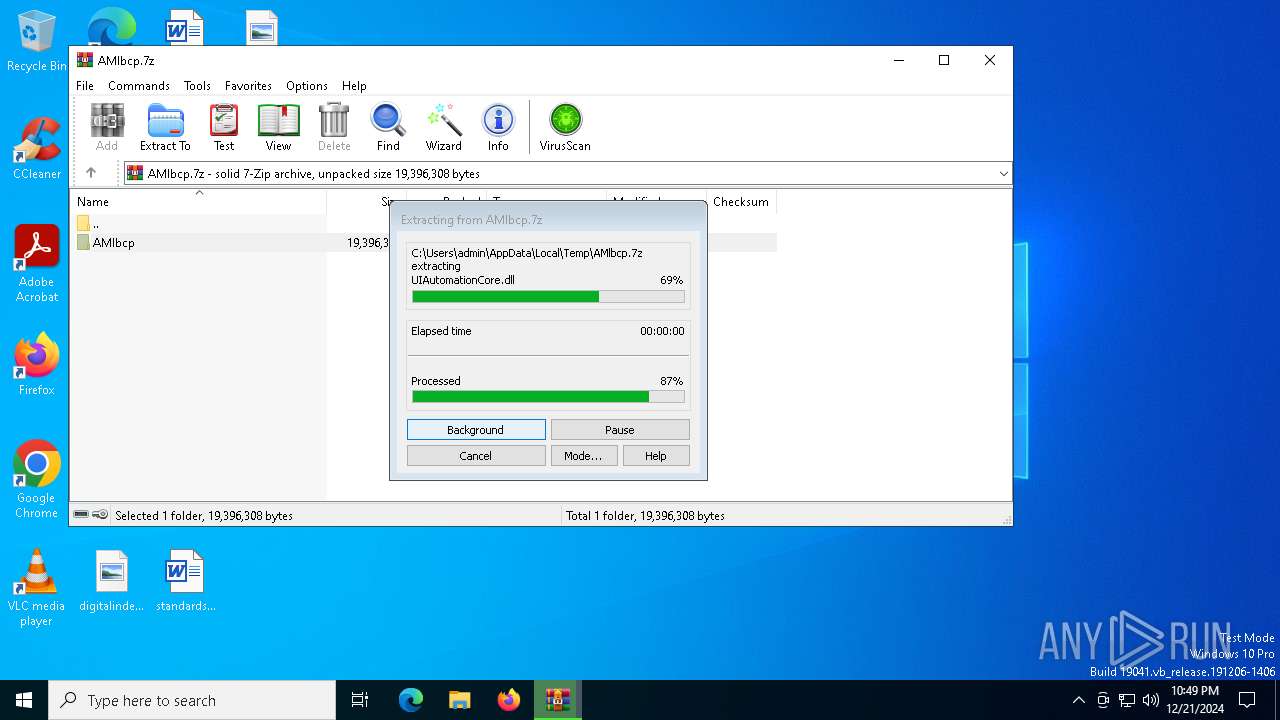
Executable content was dropped or overwritten
- AMlbcp.exe (PID: 5988)
- AMlbcp.exe (PID: 2940)
- hv.exe (PID: 4996)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6752)
- AMlbcp.exe (PID: 2940)
Starts itself from another location
- hv.exe (PID: 4996)
Starts CMD.EXE for commands execution
- hv.exe (PID: 6612)
INFO
Create files in a temporary directory
- AMlbcp.exe (PID: 5988)
- AMlbcp.exe (PID: 2940)
- hv.exe (PID: 4996)
- hv.exe (PID: 6612)
Reads the computer name
- AMlbcp.exe (PID: 5988)
- AMlbcp.exe (PID: 6148)
- AMlbcp.exe (PID: 2940)
- AMI.exe (PID: 5300)
- hv.exe (PID: 4996)
- hv.exe (PID: 6612)
Process checks computer location settings
- AMlbcp.exe (PID: 5988)
- AMlbcp.exe (PID: 6148)
The process uses the downloaded file
- AMlbcp.exe (PID: 5988)
- WinRAR.exe (PID: 6752)
Checks supported languages
- AMlbcp.exe (PID: 5988)
- AMlbcp.exe (PID: 6148)
- AMlbcp.exe (PID: 2940)
- AMI.exe (PID: 5300)
- hv.exe (PID: 4996)
- hv.exe (PID: 6612)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6752)
The sample compiled with english language support
- WinRAR.exe (PID: 6752)
- AMlbcp.exe (PID: 2940)
- hv.exe (PID: 4996)
Manual execution by a user
- AMlbcp.exe (PID: 6148)
- hv.exe (PID: 4996)
Creates files or folders in the user directory
- AMlbcp.exe (PID: 2940)
- hv.exe (PID: 4996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (gen) (100) |
|---|
EXIF
ZIP
| FileVersion: | 7z v0.03 |
|---|---|
| ModifyDate: | 2016:05:02 10:33:33+00:00 |
| ArchivedFileName: | AMlbcp/AMlbcp-0.bin |
Total processes
138
Monitored processes
11
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2040 | C:\WINDOWS\SysWOW64\explorer.exe | C:\Windows\SysWOW64\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2408 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2940 | "C:\Users\admin\Desktop\AMlbcp\AMlbcp.exe" /VERYSILENT | C:\Users\admin\Desktop\AMlbcp\AMlbcp.exe | AMlbcp.exe | ||||||||||||
User: admin Company: Guru3d Integrity Level: HIGH Description: BIOS configuration AMl Version: 5.0.2.31 Modules
| |||||||||||||||
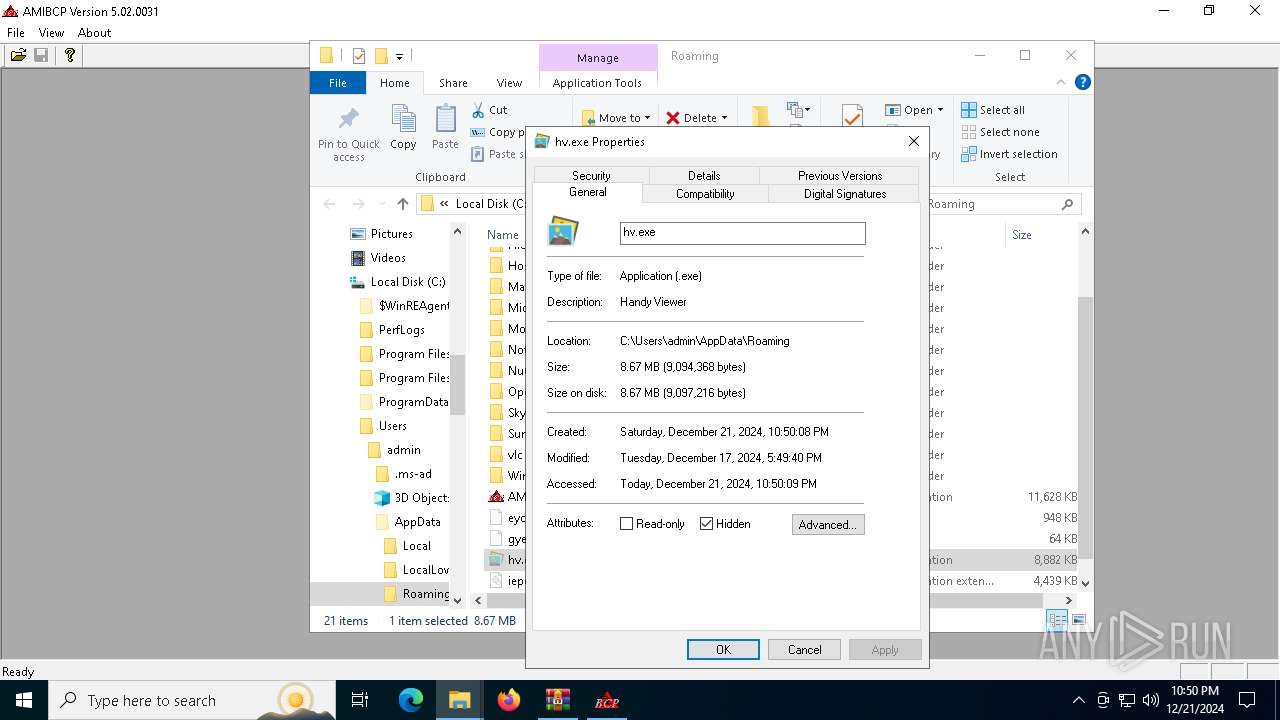
| 4996 | "C:\Users\admin\AppData\Roaming\hv.exe" | C:\Users\admin\AppData\Roaming\hv.exe | explorer.exe | ||||||||||||
User: admin Company: Handy Software Integrity Level: MEDIUM Description: Handy Viewer Exit code: 0 Version: 2.2.0.0 Modules
| |||||||||||||||
| 5300 | "C:\Users\admin\AppData\Roaming\AMI.exe" | C:\Users\admin\AppData\Roaming\AMI.exe | — | AMlbcp.exe | |||||||||||
User: admin Integrity Level: HIGH Description: AMIBCP MFC Application Version: 5, 2, 0, 31 Modules
| |||||||||||||||
| 5988 | "C:\Users\admin\Desktop\AMlbcp\AMlbcp.exe" /SPAWNWND=$20230 /NOTIFYWND=$20230 | C:\Users\admin\Desktop\AMlbcp\AMlbcp.exe | AMlbcp.exe | ||||||||||||
User: admin Company: Guru3d Integrity Level: HIGH Description: BIOS configuration AMl Exit code: 1 Version: 5.0.2.31 Modules
| |||||||||||||||
| 6148 | "C:\Users\admin\Desktop\AMlbcp\AMlbcp.exe" | C:\Users\admin\Desktop\AMlbcp\AMlbcp.exe | — | explorer.exe | |||||||||||
User: admin Company: Guru3d Integrity Level: MEDIUM Description: BIOS configuration AMl Exit code: 1 Version: 5.0.2.31 Modules
| |||||||||||||||
| 6224 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | hv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6612 | C:\Users\admin\AppData\Roaming\HostSecurity_gdev2\hv.exe | C:\Users\admin\AppData\Roaming\HostSecurity_gdev2\hv.exe | — | hv.exe | |||||||||||
User: admin Company: Handy Software Integrity Level: MEDIUM Description: Handy Viewer Exit code: 1 Version: 2.2.0.0 Modules
| |||||||||||||||
| 6752 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\AMlbcp.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 641
Read events
2 633
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AMlbcp.7z | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
17
Suspicious files
12
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6752.20811\AMlbcp\AMlbcp-1.bin | — | |
MD5:— | SHA256:— | |||
| 6752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6752.20811\AMlbcp\UIAutomationCore.dll | executable | |
MD5:DC75D3ECEC2EA1096B3B5FE626ED5425 | SHA256:71122857E62D0EDE3D8371E397B69753CC38BCC580566454E582E0B9DF87C901 | |||
| 6752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6752.20811\AMlbcp\AMlbcp.exe | executable | |
MD5:DECC9D6A173EBBFC097B0A45F733768F | SHA256:14B3666B19C2E1F362C2232A3CB63B592EAFAD367AA63DED49D9A961791C03D5 | |||
| 6752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6752.20811\AMlbcp\UiaManager.dll | executable | |
MD5:EB175F92DF5D04348AEA7123901E1E6F | SHA256:869811E1A2395275FDF762B3A43334B2ED8C9D4C265DE7BE4B3076C60DDDB7BC | |||
| 5988 | AMlbcp.exe | C:\Users\admin\AppData\Local\Temp\is-8AHFB.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6752.20811\AMlbcp\AMlbcp-0.bin | binary | |
MD5:F784952E037CCC4904448BBC9DBBEEC2 | SHA256:040AC6E0E841FF01A3EB05EFBF81116ABDE72E0A188A64F884A96A64C3B404B4 | |||
| 5988 | AMlbcp.exe | C:\Users\admin\AppData\Local\Temp\is-8AHFB.tmp\_isetup\_isdecmp.dll | executable | |
MD5:C6AE924AD02500284F7E4EFA11FA7CFC | SHA256:31D04C1E4BFDFA34704C142FA98F80C0A3076E4B312D6ADA57C4BE9D9C7DCF26 | |||
| 2940 | AMlbcp.exe | C:\Users\admin\AppData\Roaming\AMI.exe | executable | |
MD5:C15E0801502A6AD896476E64B93D6924 | SHA256:C7ADE67FE0E8F4C22F73CE3168FF6E718086F1EDA83CCE4C065B4FE49BD5AD99 | |||
| 2940 | AMlbcp.exe | C:\Users\admin\AppData\Local\Temp\is-IPGAK.tmp\_isetup\_isdecmp.dll | executable | |
MD5:C6AE924AD02500284F7E4EFA11FA7CFC | SHA256:31D04C1E4BFDFA34704C142FA98F80C0A3076E4B312D6ADA57C4BE9D9C7DCF26 | |||
| 2940 | AMlbcp.exe | C:\Users\admin\AppData\Roaming\gyea | binary | |
MD5:D54F765DAD19FF116DC3972AA5C24AD3 | SHA256:24AD7C2C72AF176BAD3CB4B41E46BC58851745E9C747B24F322EDDFDD3725FB3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
39
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.21.20.133:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7036 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7036 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.21.20.133:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.21.110.139:443 | www.bing.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |