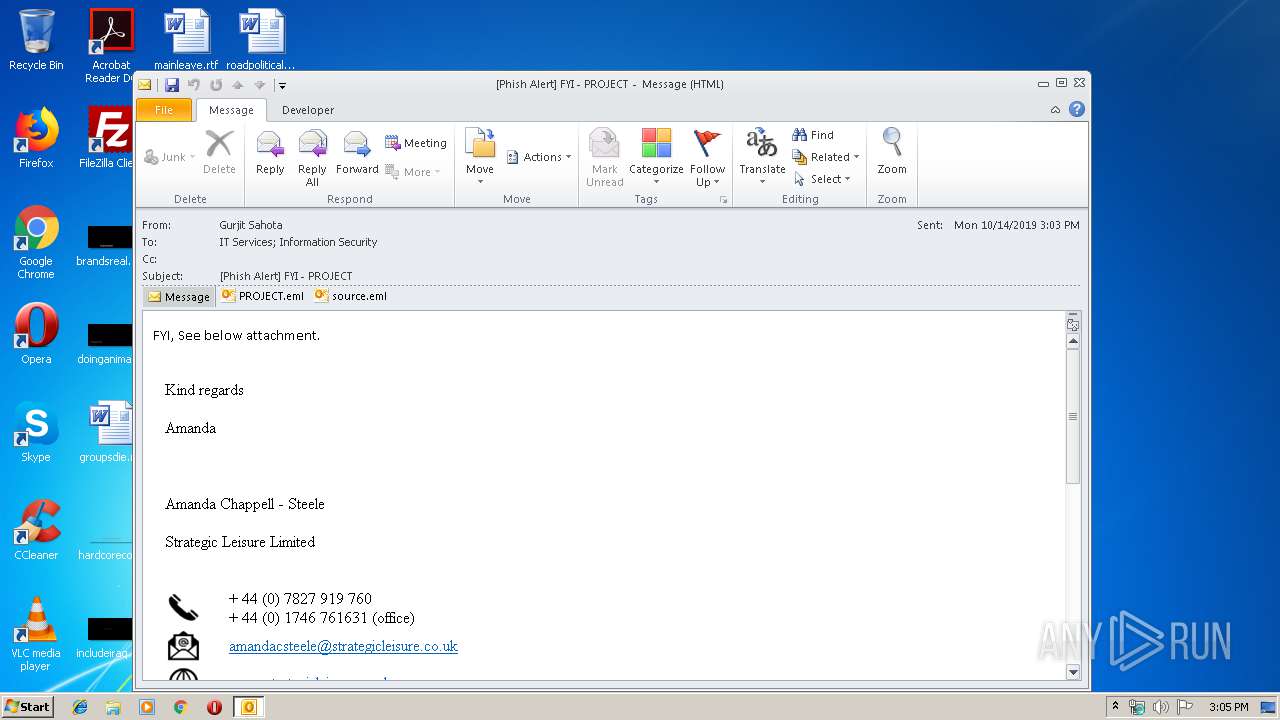
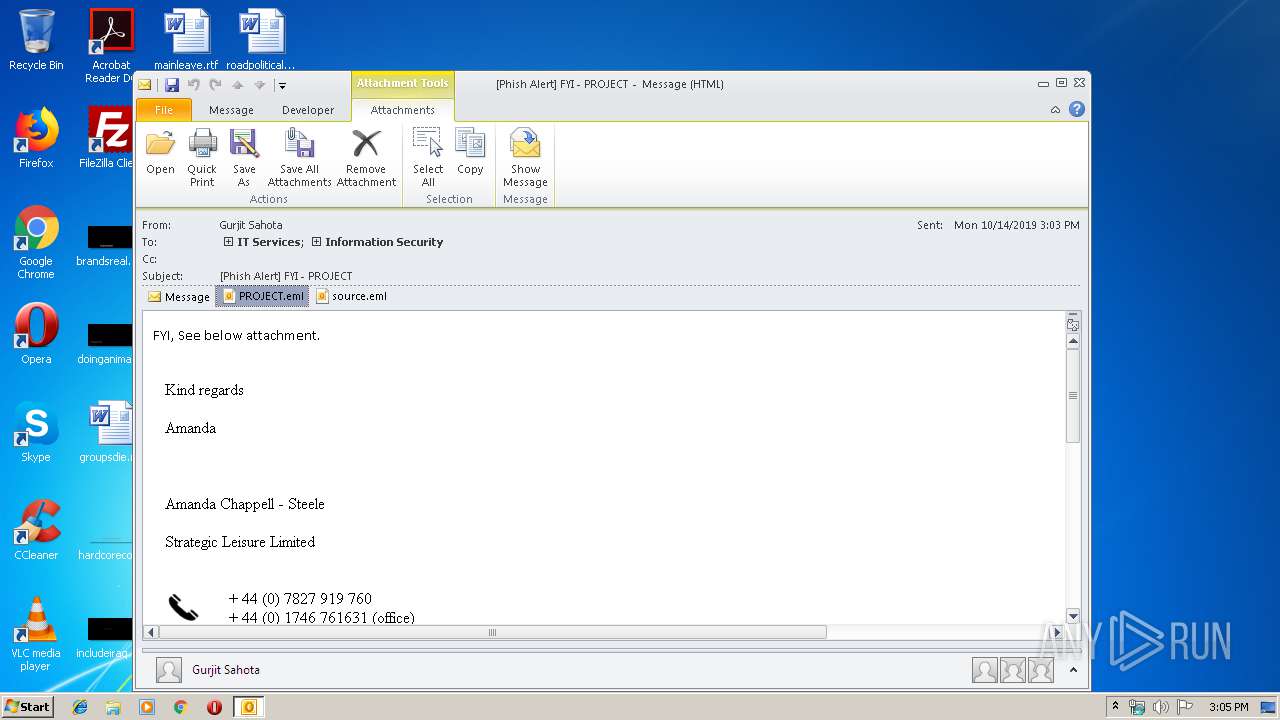
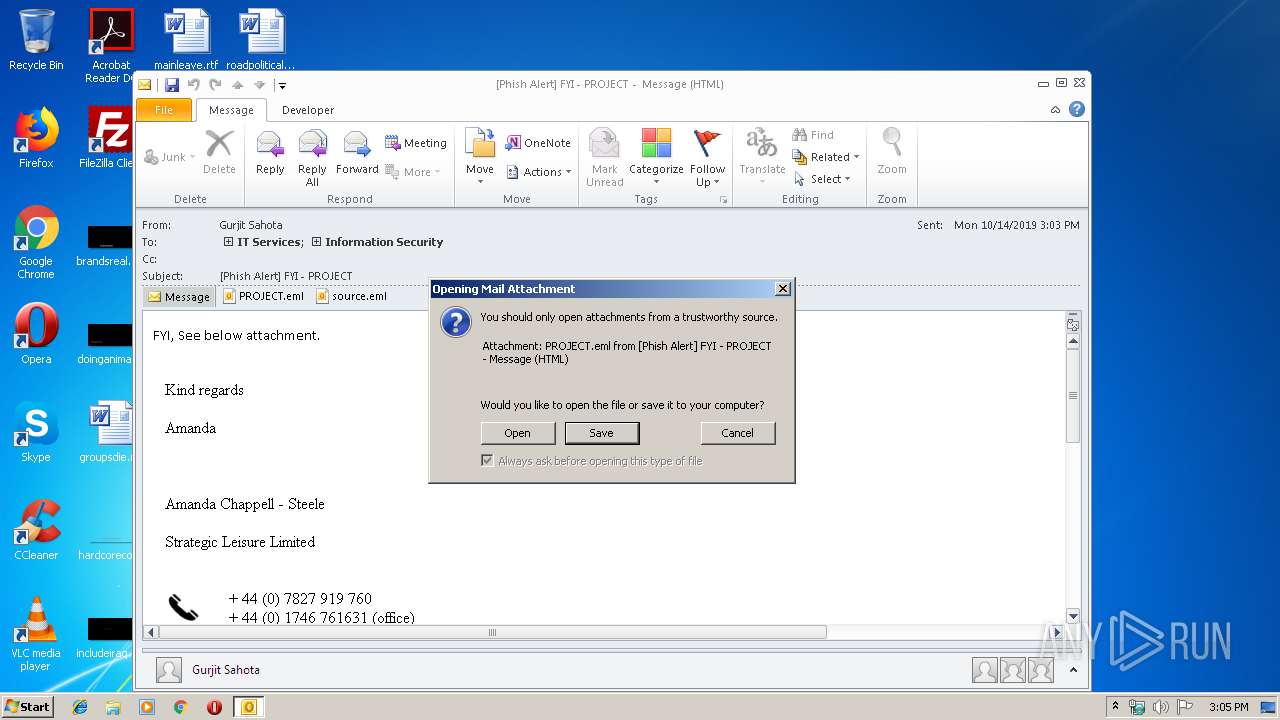
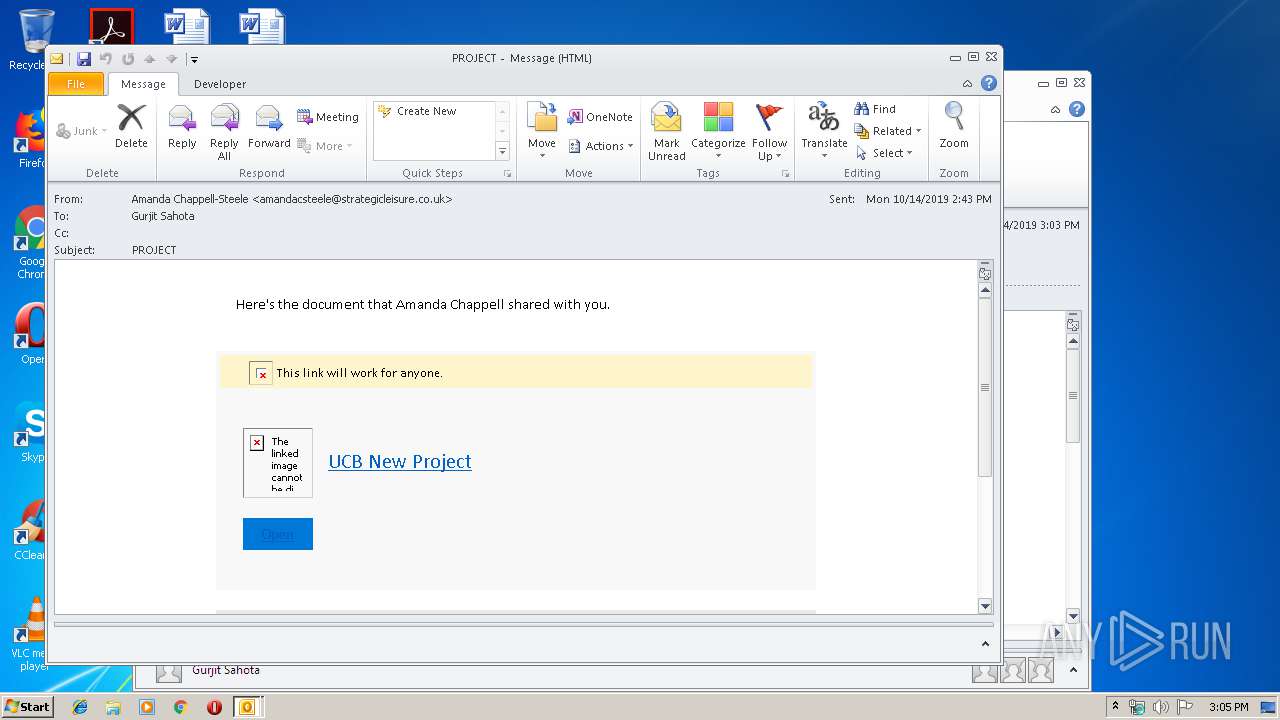
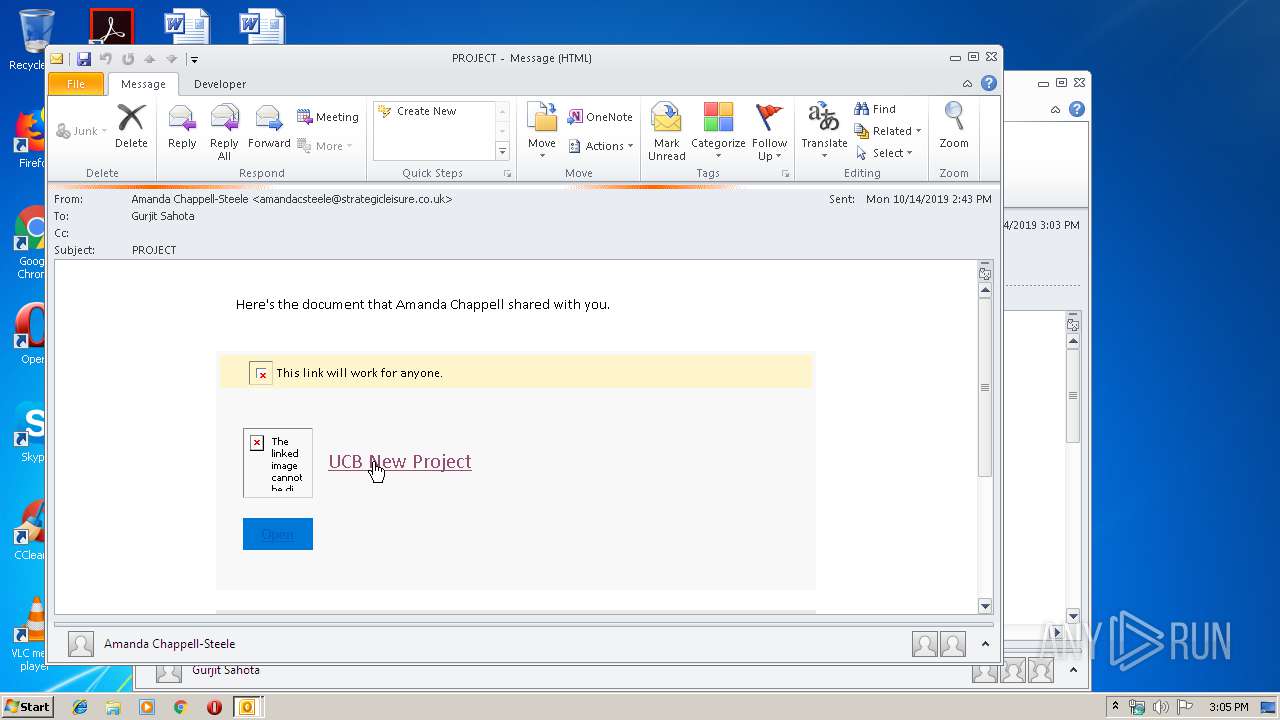
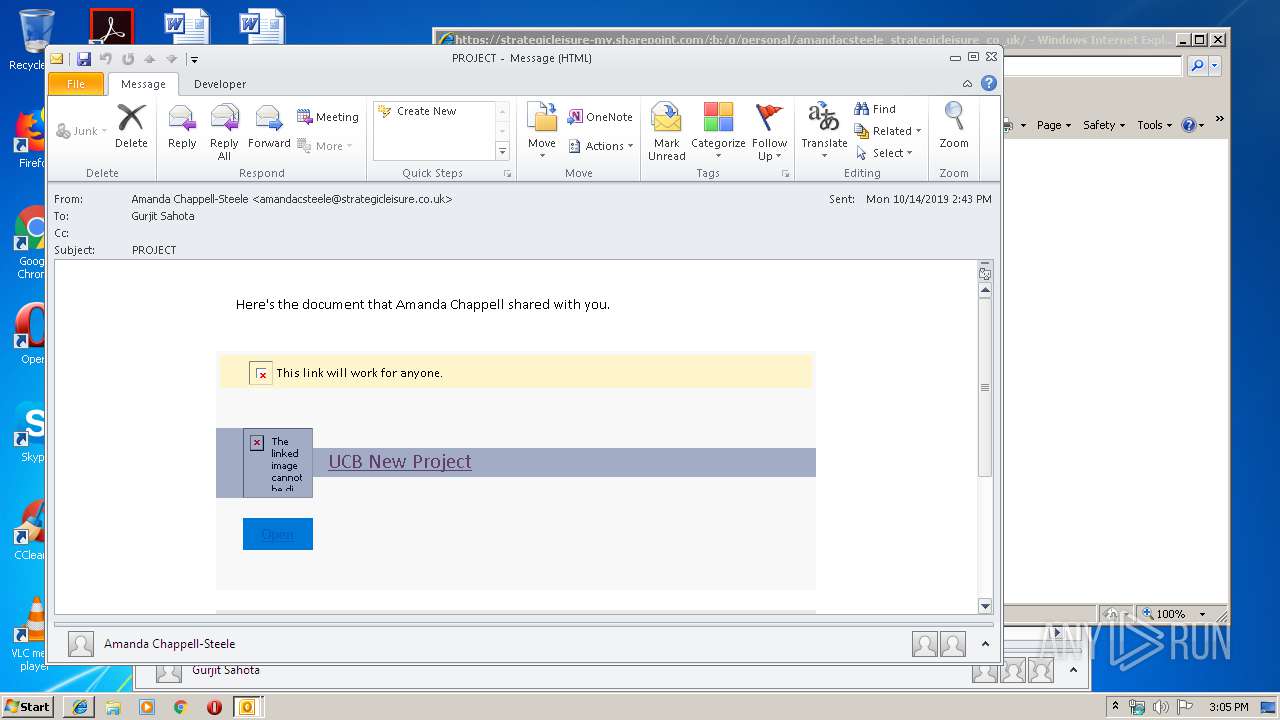
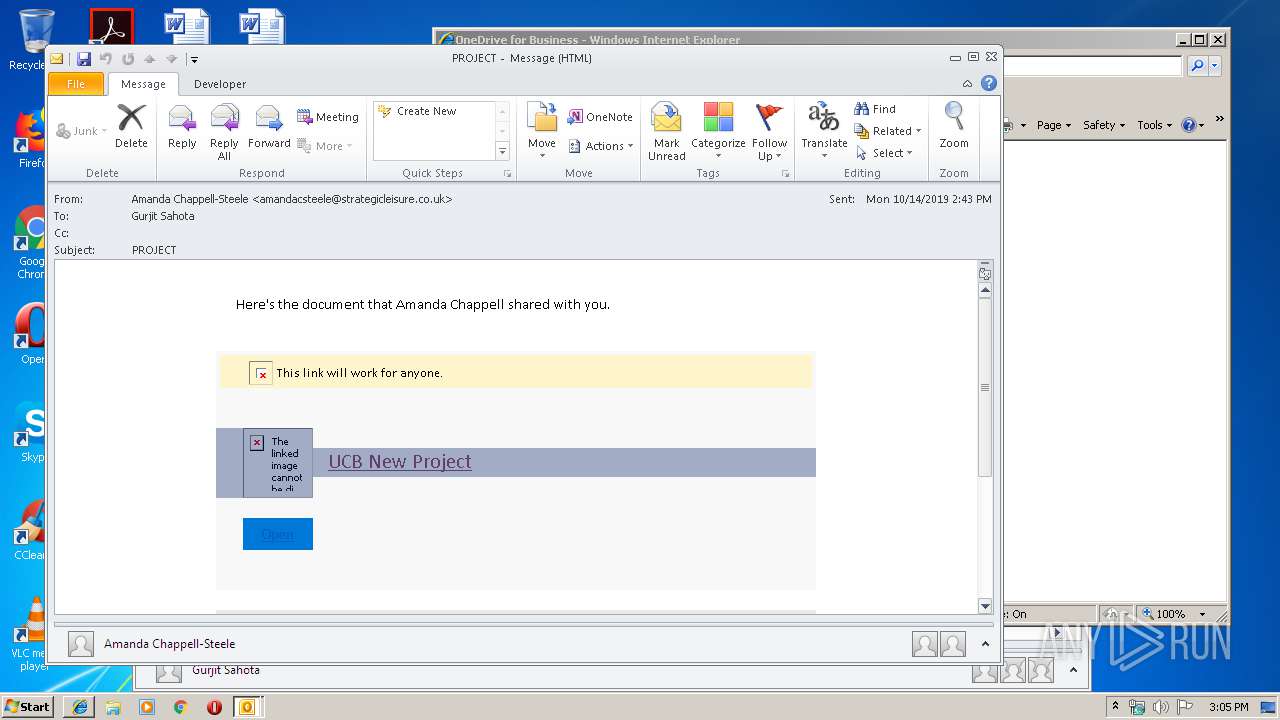
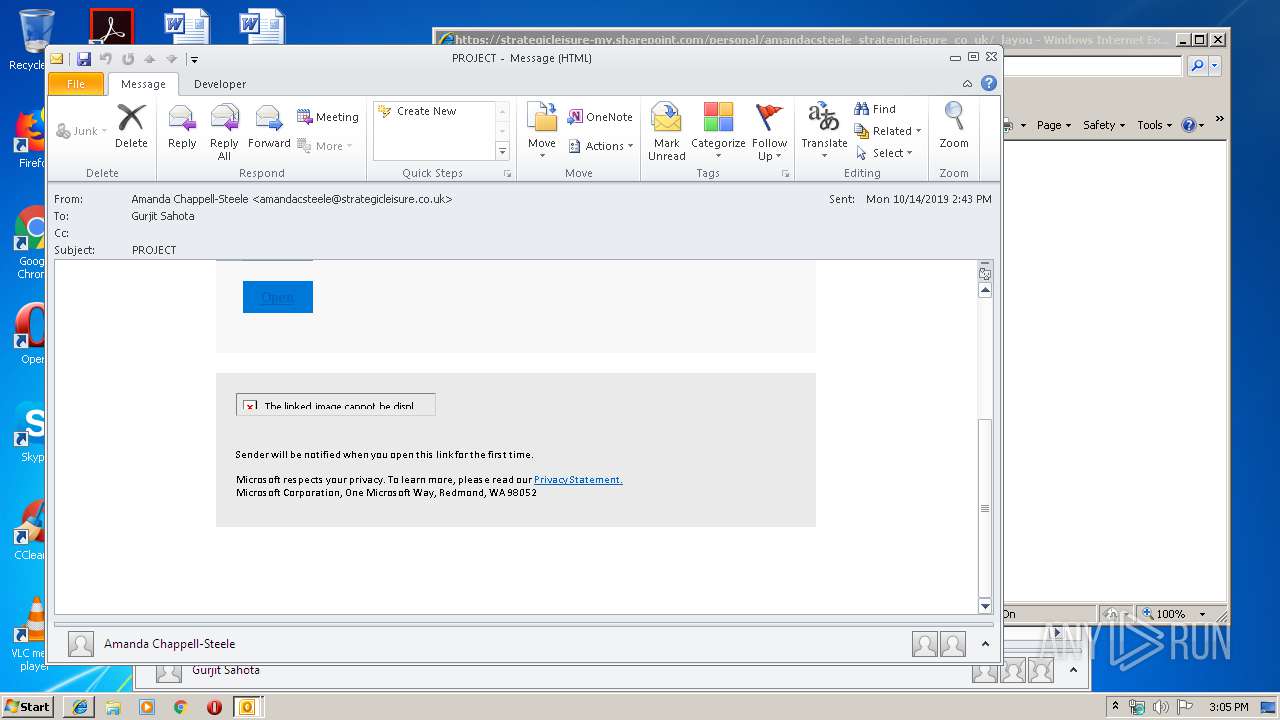
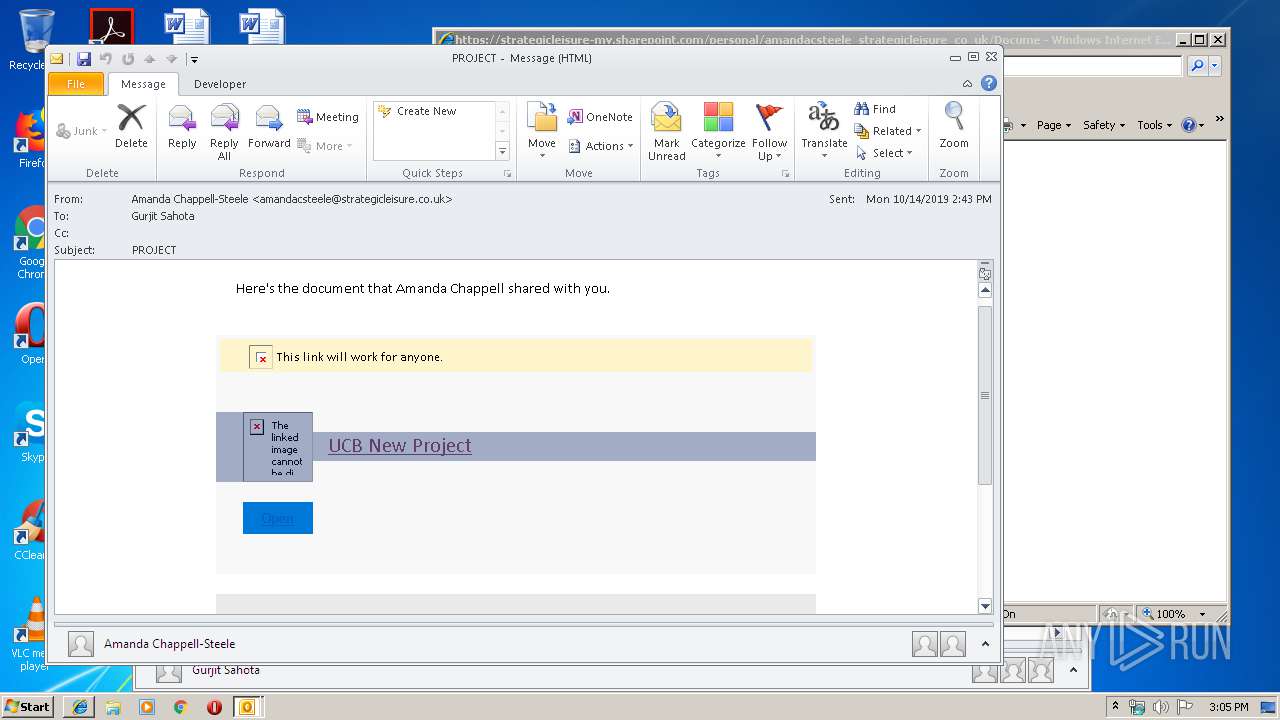
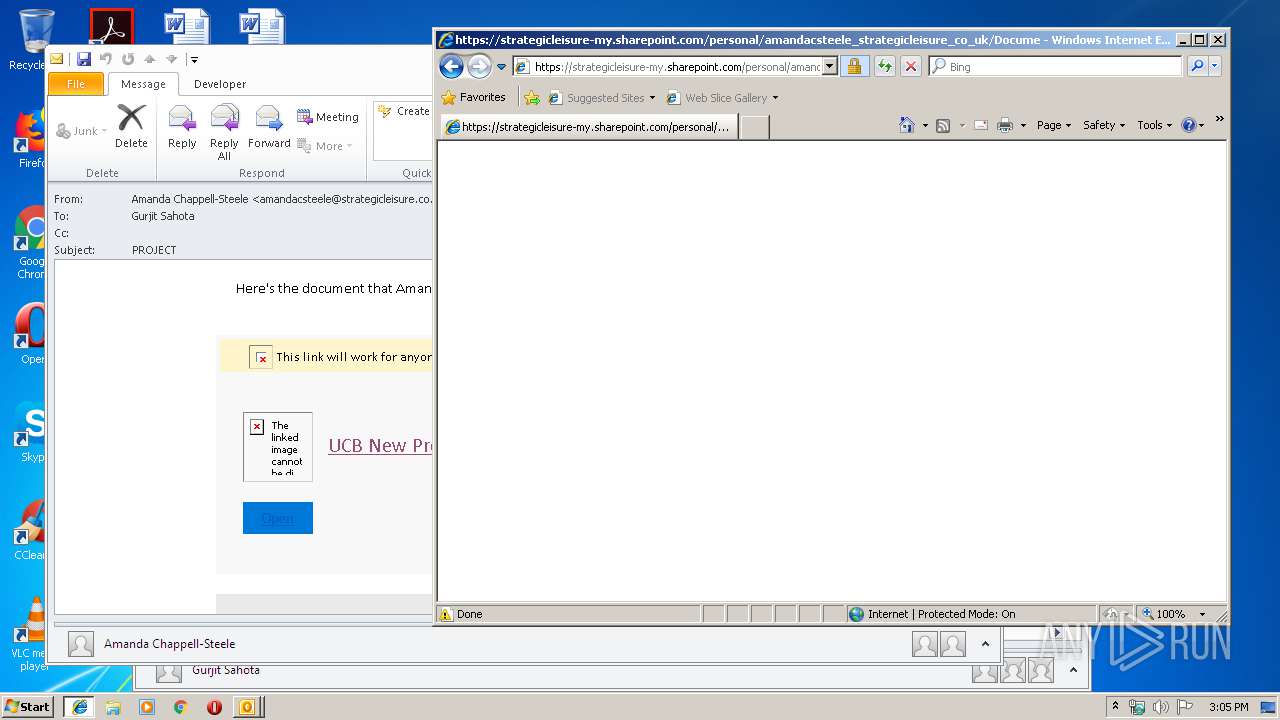
| File name: | Phish Alert FYI - PROJECT.msg |
| Full analysis: | https://app.any.run/tasks/0c5c36ce-3cc2-4846-9c45-9aee98e3ee23 |
| Verdict: | Malicious activity |
| Analysis date: | October 14, 2019, 14:04:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 9B196518DBDBA4CED222D239A043DC52 |
| SHA1: | 28D41070F491ED9847E58AEF5626BC58C15FD19E |
| SHA256: | DE05A94A72D2B5BA2D5BBF10A43899FACACC66D6E251AAC29DFA29C60D6456B1 |
| SSDEEP: | 3072:KyUKdWbvT1sH227IzUYecvGdqfnXGZZhep1ADep1AKT1sH227IzU3qfnXG0mxM8Q:VdWedLD+nj9wEdDxP |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 1584)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 1584)
Creates files in the user directory
- OUTLOOK.EXE (PID: 1584)
Starts itself from another location
- OUTLOOK.EXE (PID: 1584)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 1584)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2916)
- OUTLOOK.EXE (PID: 1584)
Changes internet zones settings
- iexplore.exe (PID: 2884)
Application launched itself
- iexplore.exe (PID: 2884)
- chrome.exe (PID: 2588)
Reads internet explorer settings
- iexplore.exe (PID: 2700)
Creates files in the user directory
- iexplore.exe (PID: 2700)
Reads Internet Cache Settings
- iexplore.exe (PID: 2700)
- iexplore.exe (PID: 2884)
Manual execution by user
- chrome.exe (PID: 2588)
Reads the hosts file
- chrome.exe (PID: 2588)
- chrome.exe (PID: 788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (50.8) |
|---|---|---|
| .oft | | | Outlook Form Template (29.7) |
| .doc | | | Microsoft Word document (old ver.) (13.6) |
Total processes
53
Monitored processes
17
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,14002843400145535165,1921639629102073157,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=4199519663876459961 --mojo-platform-channel-handle=1636 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,14002843400145535165,1921639629102073157,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15680575683658070929 --mojo-platform-channel-handle=3372 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Phish Alert FYI - PROJECT.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,14002843400145535165,1921639629102073157,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9154691347190935473 --mojo-platform-channel-handle=2728 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,14002843400145535165,1921639629102073157,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11476849097739764950 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2440 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2140 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,14002843400145535165,1921639629102073157,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2848240286600692996 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3212 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2264 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6fe1a9d0,0x6fe1a9e0,0x6fe1a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,14002843400145535165,1921639629102073157,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7620719429502591750 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2452 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2700 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2884 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 907
Read events
1 836
Write events
1 045
Delete events
26
Modification events
| (PID) Process: | (1584) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1584) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1584) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1584) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1584) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1584) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1584) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1584) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1584) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330512052 | |||
| (PID) Process: | (1584) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
0
Suspicious files
13
Text files
90
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1584 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRB07E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1584 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\MYI6SUKL\PROJECT (2).eml\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2916 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRDF2F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1584 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1584 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\44604C1C.dat | image | |
MD5:— | SHA256:— | |||
| 1584 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\45F3056D.dat | image | |
MD5:— | SHA256:— | |||
| 1584 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7E532703.dat | image | |
MD5:— | SHA256:— | |||
| 1584 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\E925B48A.dat | image | |
MD5:— | SHA256:— | |||
| 2884 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1584 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5B0F2D28.dat | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
37
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1584 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2884 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1584 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2884 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 13.107.136.9:443 | strategicleisure-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
— | — | 104.96.95.205:443 | static.sharepointonline.com | Akamai Technologies, Inc. | NL | unknown |
2700 | iexplore.exe | 104.96.95.205:443 | static.sharepointonline.com | Akamai Technologies, Inc. | NL | unknown |
2884 | iexplore.exe | 13.107.136.9:443 | strategicleisure-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
2700 | iexplore.exe | 13.107.136.9:443 | strategicleisure-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
788 | chrome.exe | 172.217.23.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
788 | chrome.exe | 13.107.136.9:443 | strategicleisure-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
788 | chrome.exe | 172.217.16.131:443 | www.google.com.ua | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
strategicleisure-my.sharepoint.com |
| suspicious |
www.bing.com |
| whitelisted |
static.sharepointonline.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.google.com |
| malicious |