| File name: | windows-commands |
| Full analysis: | https://app.any.run/tasks/c07bd3e1-260d-4af8-8655-4752a55b985a |
| Verdict: | Malicious activity |
| Analysis date: | March 10, 2021, 15:45:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines, with CRLF, LF line terminators |
| MD5: | E7EB39D1116F64BC1F18DC5DD1DB1B2E |
| SHA1: | 9887F69EAEFE86F7880CF5F726B8FAF7604A4B6C |
| SHA256: | DDD2069EC3876C5CFE9A2737D7FF63337E68D85FCA86C9164BEA0AA2791DF80E |
| SSDEEP: | 1536:mooQH0uX/szyehSFIrL7Z6H5vhx/sGhx/C:msRvhe0FIrL7Z05A3 |
MALICIOUS
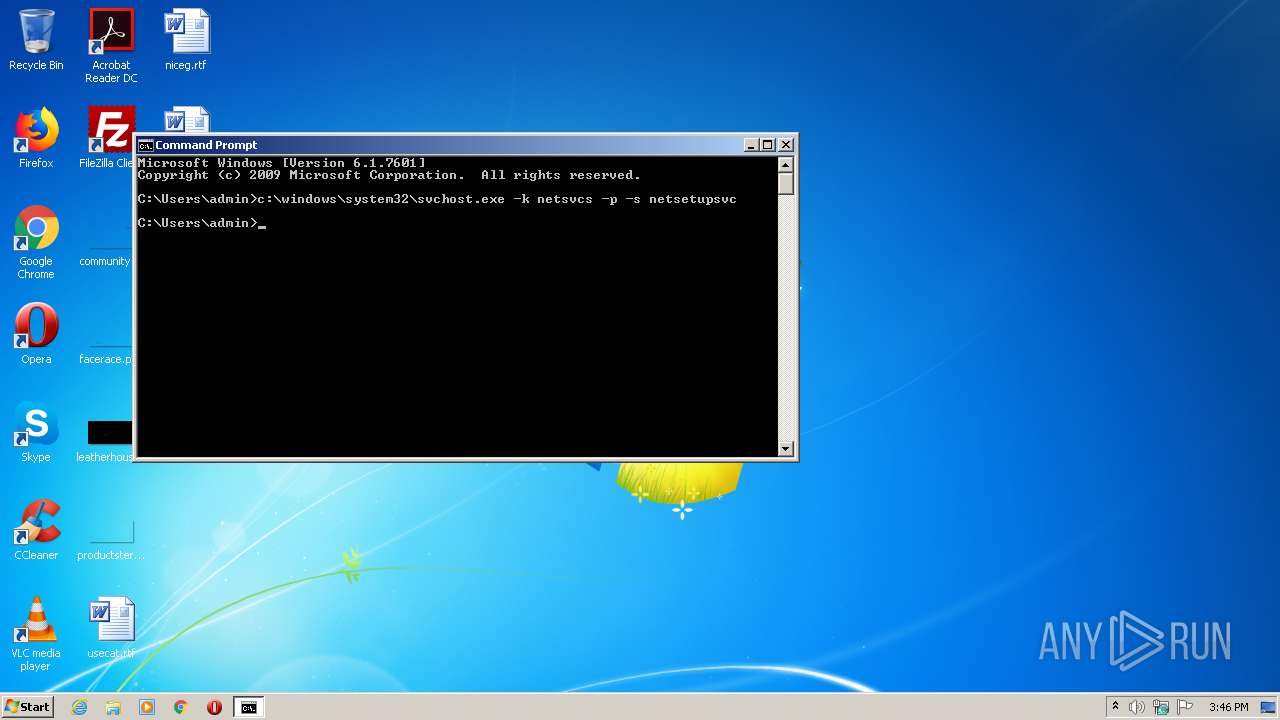
Uses SVCHOST.EXE for hidden code execution
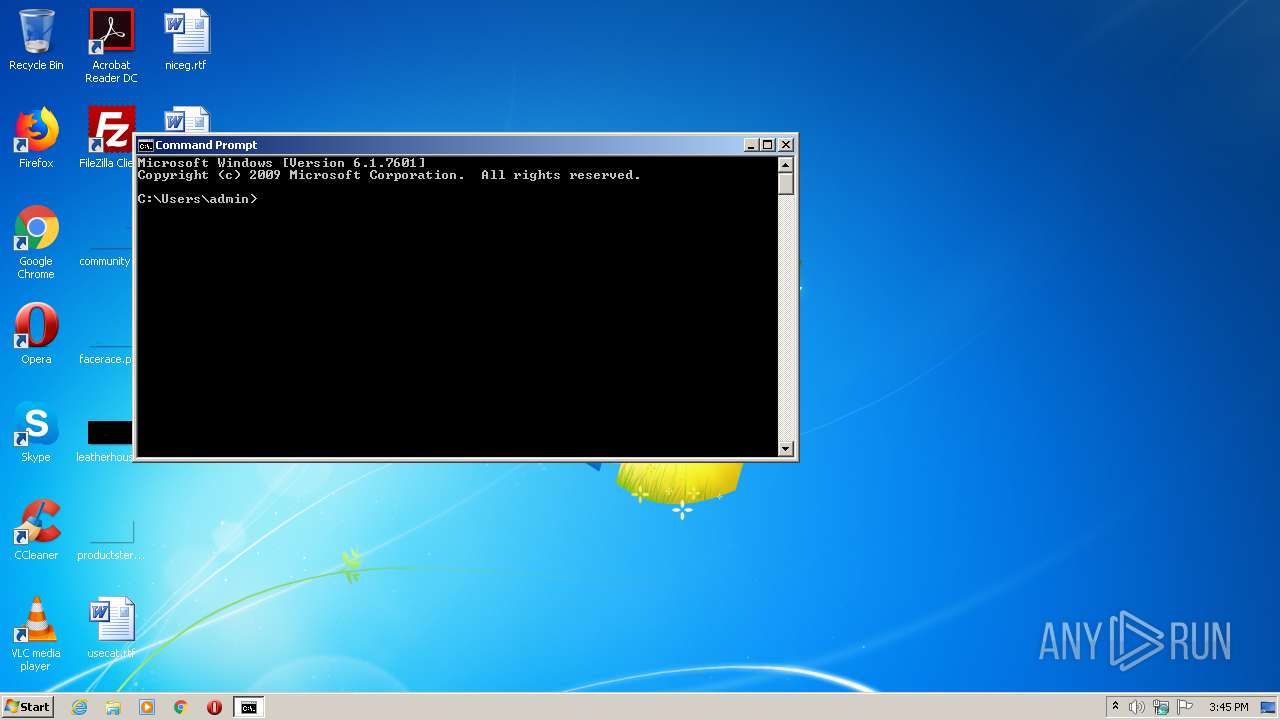
- cmd.exe (PID: 2532)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by user
- cmd.exe (PID: 2532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| viewport: | width=device-width, initial-scale=1.0 |
|---|---|
| twitterCard: | summary |
| twitterSite: | @docsmsft |
| colorScheme: | light dark |
| Author: | JasonGerend |
| breadcrumb_path: | /windows-server/breadcrumbs/toc.json |
| depot_name: | MSDN.WindowsServerDocs-pr |
| Description: | Reference |
| document_id: | 6d382ca0-6538-5e1d-3e83-e31c9ab6a911 |
| document_version_independent_id: | 11eff296-6158-f89a-4941-8735529183e9 |
| gitcommit: | https://github.com/MicrosoftDocs/windowsserverdocs-pr/blob/68e512d7a026babde93ec35ded2e8ae2b4b6b4b1/WindowsServerDocs/administration/windows-commands/windows-commands.md |
| locale: | en-us |
| manager: | dongill |
| msAssetid: | c703d07c-8227-4e86-94a6-8ef390f94cdc |
| msAuthor: | jgerend |
| msDate: | 06/29/2020 |
| msProd: | windows-server |
| msTechnology: | windows-commands |
| msTopic: | reference |
| original_content_git_url: | https://github.com/MicrosoftDocs/windowsserverdocs-pr/blob/live/WindowsServerDocs/administration/windows-commands/windows-commands.md |
| searchMs_docsetname: | WindowsServerDocs-pr |
| searchMs_product: | MSDN |
| searchMs_sitename: | Docs |
| site_name: | Docs |
| updated_at: | 2020-10-16 10:32 PM |
| page_type: | conceptual |
| toc_rel: | toc.json |
| pdf_url_template: | https://docs.microsoft.com/pdfstore/en-us/MSDN.WindowsServerDocs-pr/{branchName}{pdfName} |
| word_count: | 1746 |
| Title: | Windows commands | Microsoft Docs |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2020 | "C:\windows\system32\svchost.exe" -k netsvcs -p -s netsetupsvc | C:\windows\system32\svchost.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2140 | c:\windows\system32\svchost.exe -k netsvcs -p -s netsetupsvc | c:\windows\system32\svchost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2532 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
8
Read events
8
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report