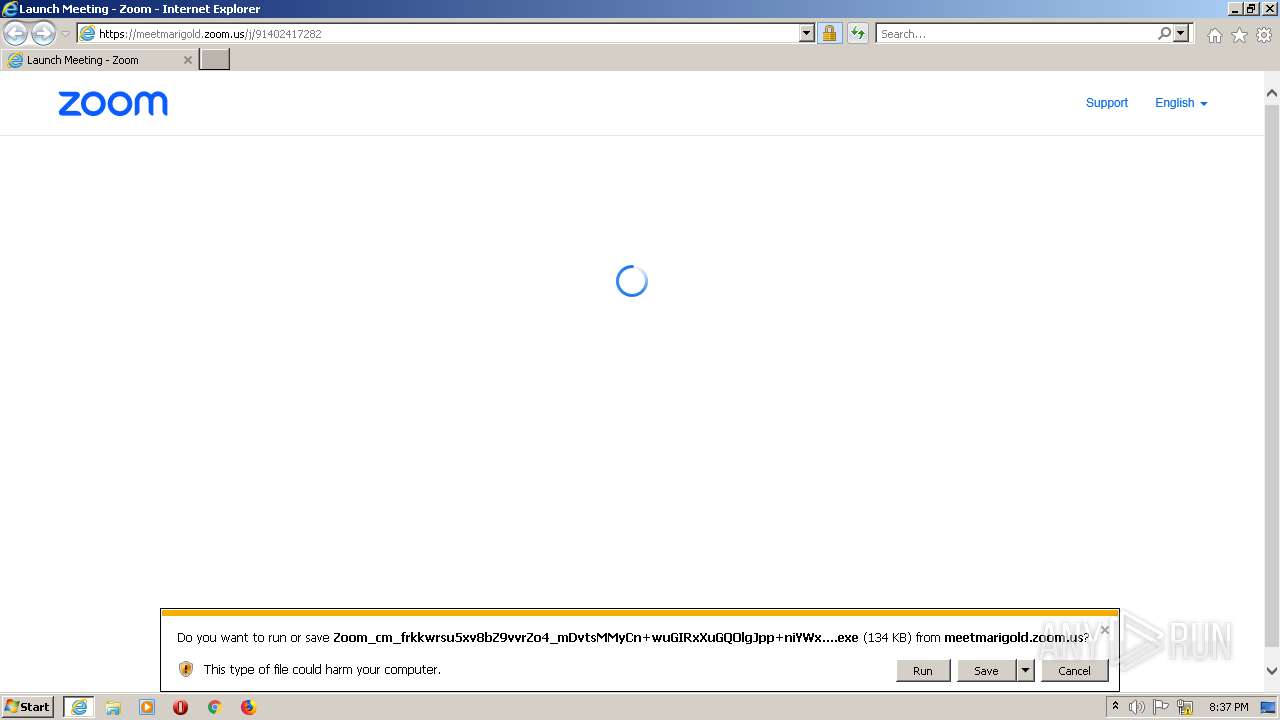
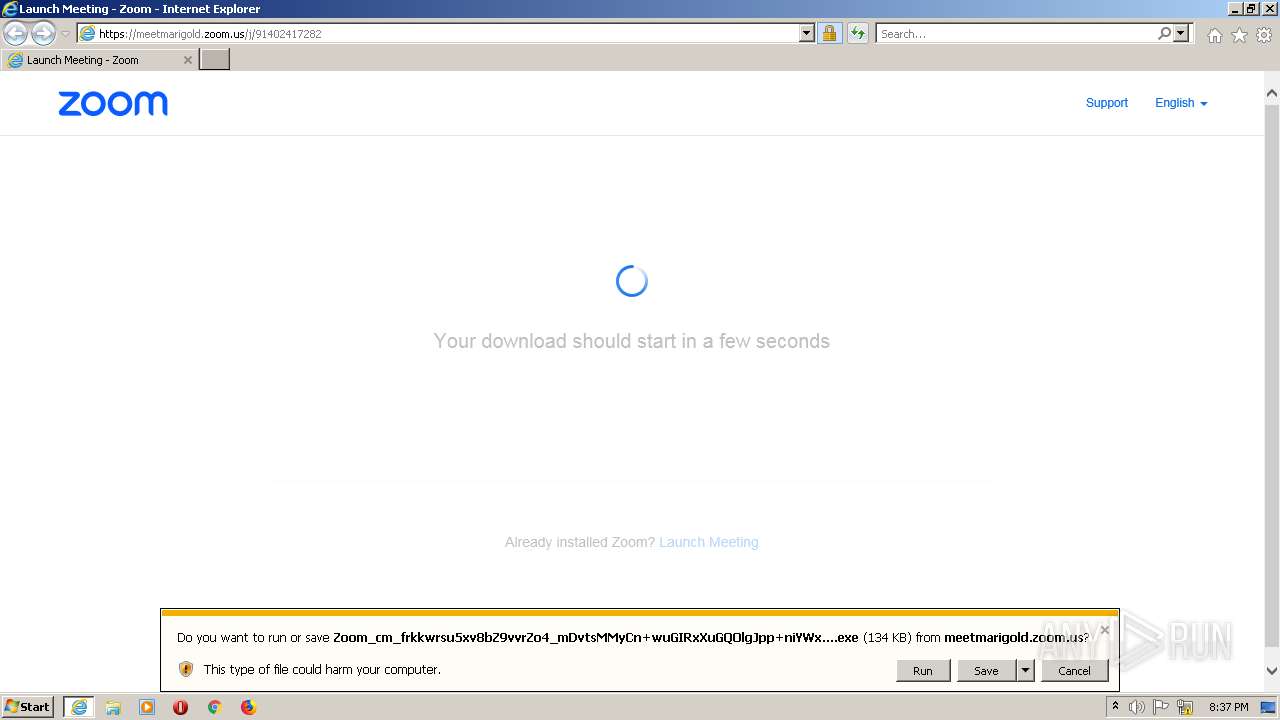
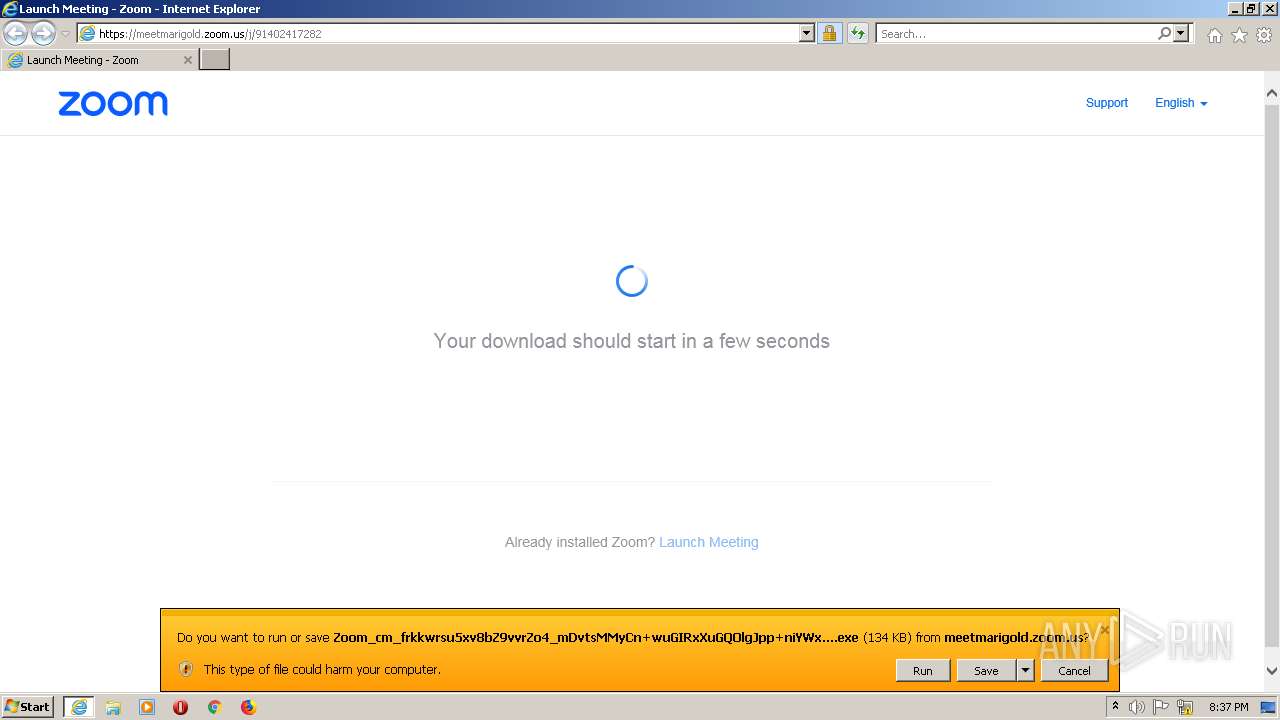
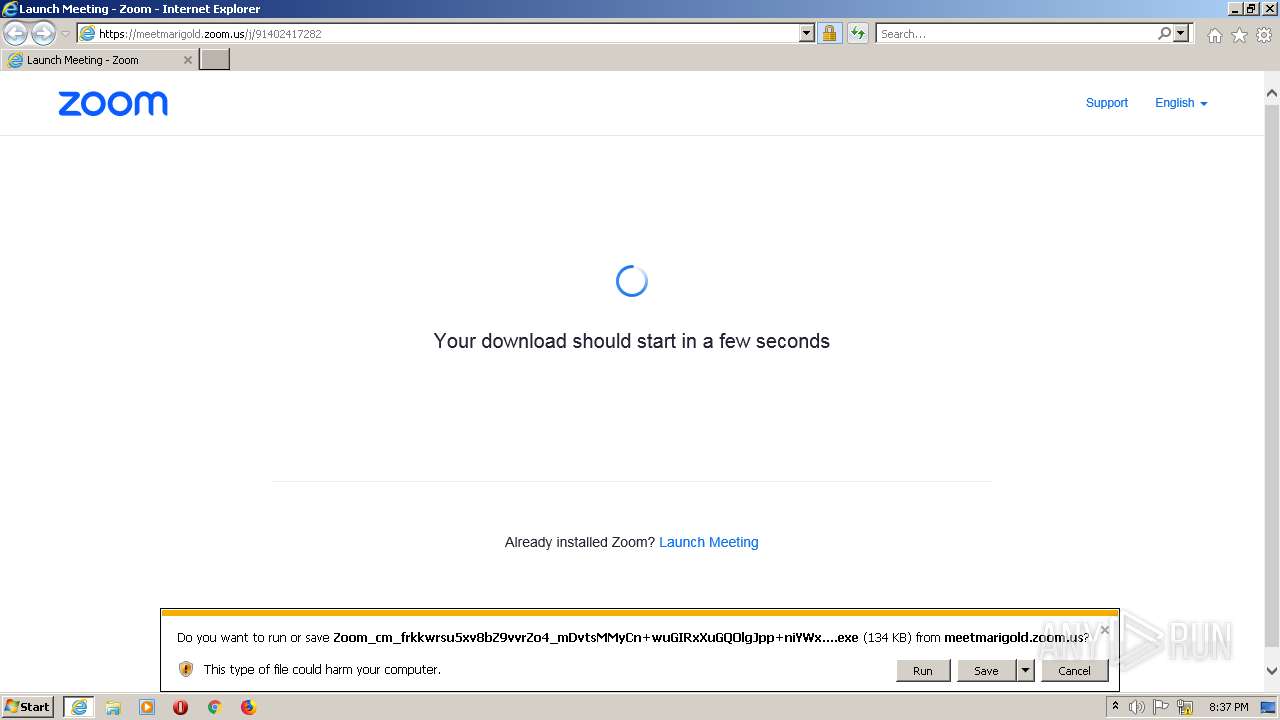
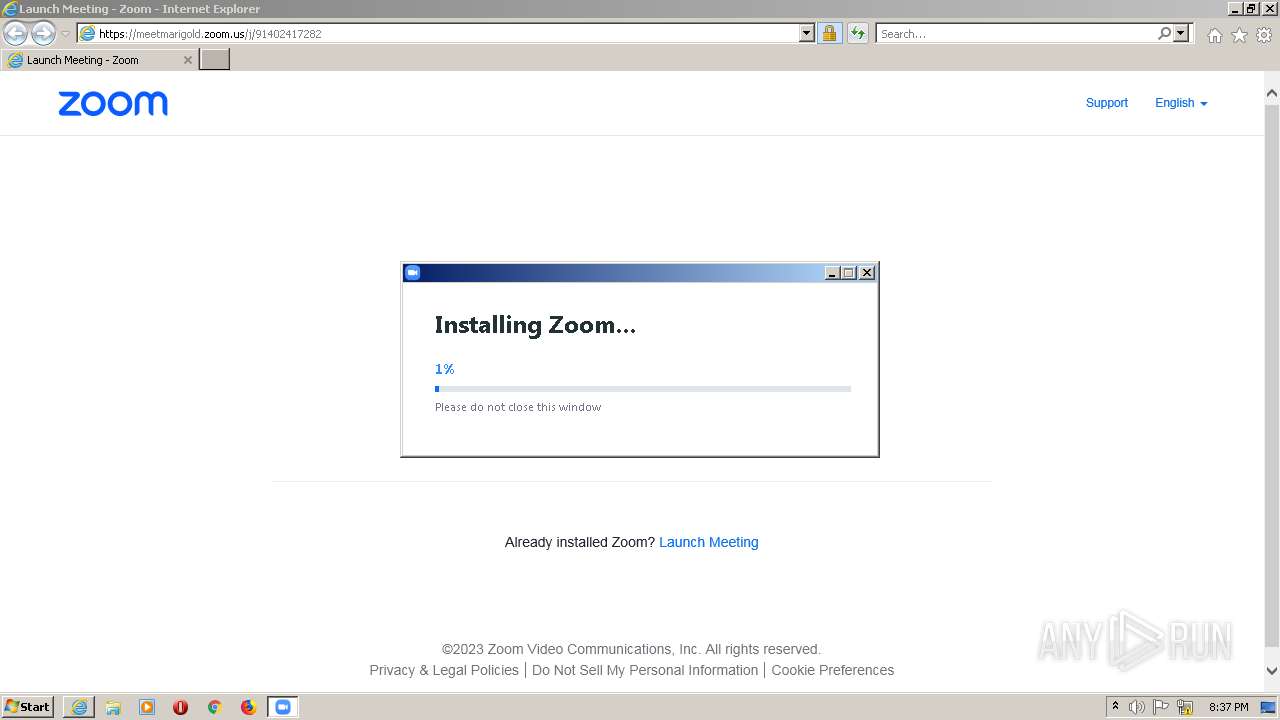
| URL: | https://meetmarigold.zoom.us/j/91402417282 |
| Full analysis: | https://app.any.run/tasks/6bba3c59-a15b-4e9b-836f-f686c7408444 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2023, 20:37:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MD5: | D6EEC338FEFE3774C086E39A2CD3F0E0 |
| SHA1: | 65249406F0790F3BADFD7D8E8E18EE086A151381 |
| SHA256: | DDCD8859A051354B48B3729A3F535F8E82CCF3F01EE4C95C89FB62E52592993F |
| SSDEEP: | 3:N8YYp3NiLXdX:2YgijdX |
MALICIOUS
Application was dropped or rewritten from another process
- Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_.exe (PID: 2768)
SUSPICIOUS
Reads the Internet Settings
- Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_.exe (PID: 2768)
INFO
Create files in a temporary directory
- iexplore.exe (PID: 1732)
Executable content was dropped or overwritten
- iexplore.exe (PID: 1752)
- iexplore.exe (PID: 1732)
The process uses the downloaded file
- iexplore.exe (PID: 1732)
Creates files or folders in the user directory
- Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_.exe (PID: 2768)
Reads the computer name
- Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_.exe (PID: 2768)
Checks proxy server information
- Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_.exe (PID: 2768)
Checks supported languages
- Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_.exe (PID: 2768)
The process checks LSA protection
- Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_.exe (PID: 2768)
Reads the machine GUID from the registry
- Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_.exe (PID: 2768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
30
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1732 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://meetmarigold.zoom.us/j/91402417282" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1752 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:1732 CREDAT:267521 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2768 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2U1WPAC\Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2U1WPAC\Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_.exe | iexplore.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 5,10,3,4851 Modules
| |||||||||||||||
Total events
9 668
Read events
9 450
Write events
218
Delete events
0
Modification events
| (PID) Process: | (1732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 3 | |||
| (PID) Process: | (1732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 659226608 | |||
| (PID) Process: | (1732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30902802 | |||
| (PID) Process: | (1732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 959230748 | |||
| (PID) Process: | (1732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30902802 | |||
| (PID) Process: | (1732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000008B000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
6
Suspicious files
8
Text files
58
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1752 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\7GF3MDB8.txt | text | |
MD5:— | SHA256:— | |||
| 1752 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\5Z1826EE.txt | text | |
MD5:— | SHA256:— | |||
| 1752 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\A80DPWVW.txt | text | |
MD5:— | SHA256:— | |||
| 1752 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\38B5GPAW.txt | text | |
MD5:— | SHA256:— | |||
| 1752 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\ADNKYPOE.txt | text | |
MD5:— | SHA256:— | |||
| 1752 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\UJFUX3OG\91402417282[1].htm | html | |
MD5:— | SHA256:— | |||
| 1752 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YQPEPCE1\Zoom_cm_frkkwrsu5xv8bZ9vvrZo4_mDvtsMMyCn+wuGIRxXuGQOlgJpp+niYWx9mPW@DuhKnhdTL6GaXfuj_kd46be2e3a15876bd_[1].exe | executable | |
MD5:— | SHA256:— | |||
| 1752 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\XF1V03J7.txt | text | |
MD5:— | SHA256:— | |||
| 1752 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\SLRNP3YJ.txt | text | |
MD5:— | SHA256:— | |||
| 1752 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\UJFUX3OG\lres[1].js | text | |
MD5:A824BB853A5E62D2E62EE1ECFE219292 | SHA256:CFCCA75DD367EE46D359CE8DB5584A2179E8FF742E328882DC54CBD67D1AB73E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
32
DNS requests
17
Threats
21
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1752 | iexplore.exe | 170.114.52.2:443 | meetmarigold.zoom.us | — | US | suspicious |
— | — | 34.98.108.207:443 | cdn.solvvy.com | GOOGLE | US | unknown |
— | — | 18.66.147.60:443 | static.ada.support | AMAZON-02 | US | suspicious |
— | — | 18.66.130.242:443 | st3.zoom.us | AMAZON-02 | US | unknown |
1752 | iexplore.exe | 18.66.130.242:443 | st3.zoom.us | AMAZON-02 | US | unknown |
— | — | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1752 | iexplore.exe | 104.19.187.97:443 | cdn.cookielaw.org | CLOUDFLARENET | — | whitelisted |
— | — | 54.227.249.145:443 | log-gateway.zoom.us | AMAZON-AES | US | unknown |
1732 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1752 | iexplore.exe | 172.64.144.98:443 | geolocation.onetrust.com | CLOUDFLARENET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
meetmarigold.zoom.us |
| suspicious |
static.ada.support |
| whitelisted |
cdn.solvvy.com |
| shared |
st3.zoom.us |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
st1.zoom.us |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
log-gateway.zoom.us |
| unknown |
cdn.cookielaw.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1752 | iexplore.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Tofsee |
1752 | iexplore.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Tofsee |
1752 | iexplore.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Tofsee |
1752 | iexplore.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Tofsee |
1752 | iexplore.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Tofsee |
1752 | iexplore.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Tofsee |
1752 | iexplore.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Tofsee |
1752 | iexplore.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Tofsee |
1732 | iexplore.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Tofsee |
1732 | iexplore.exe | Unknown Traffic | ET JA3 Hash - [Abuse.ch] Possible Tofsee |