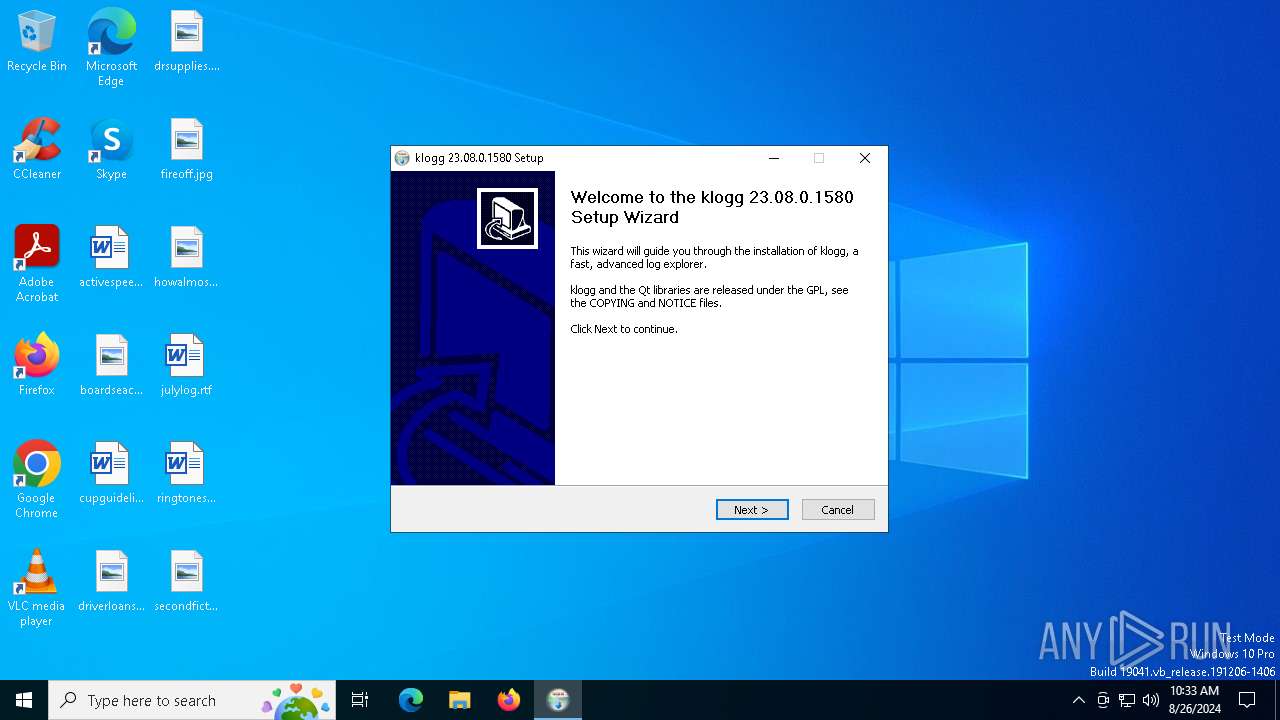
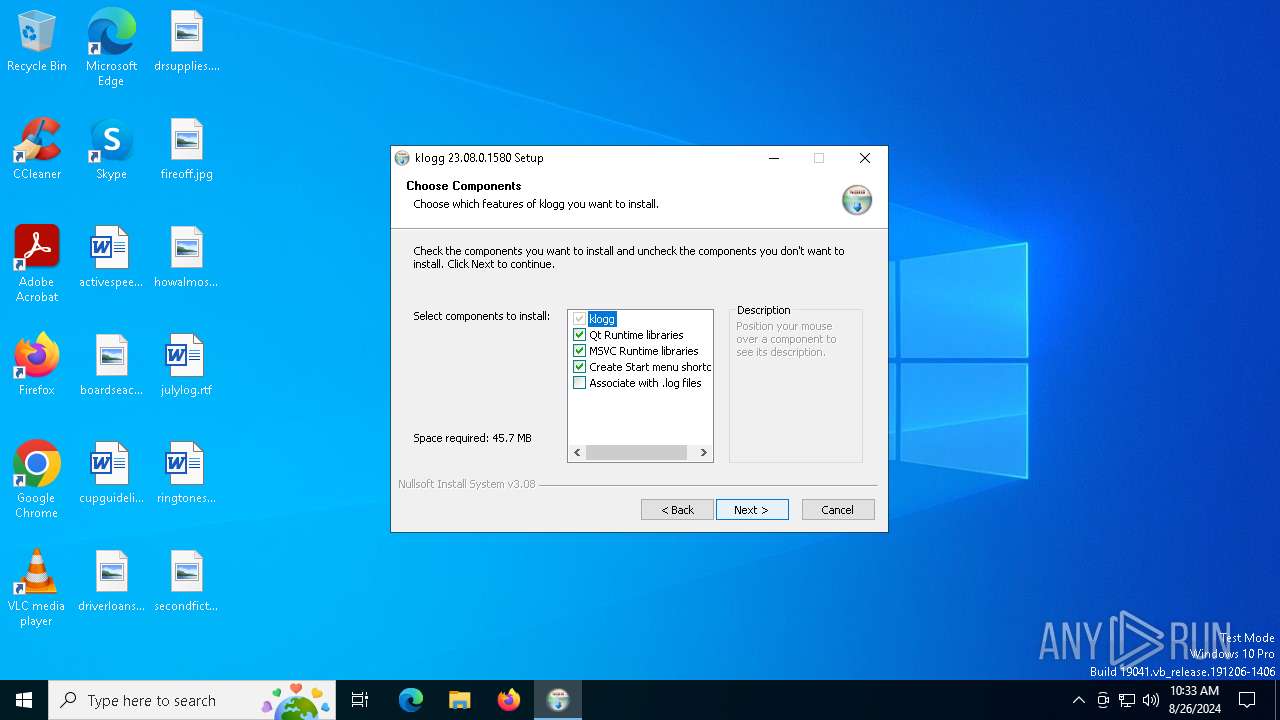
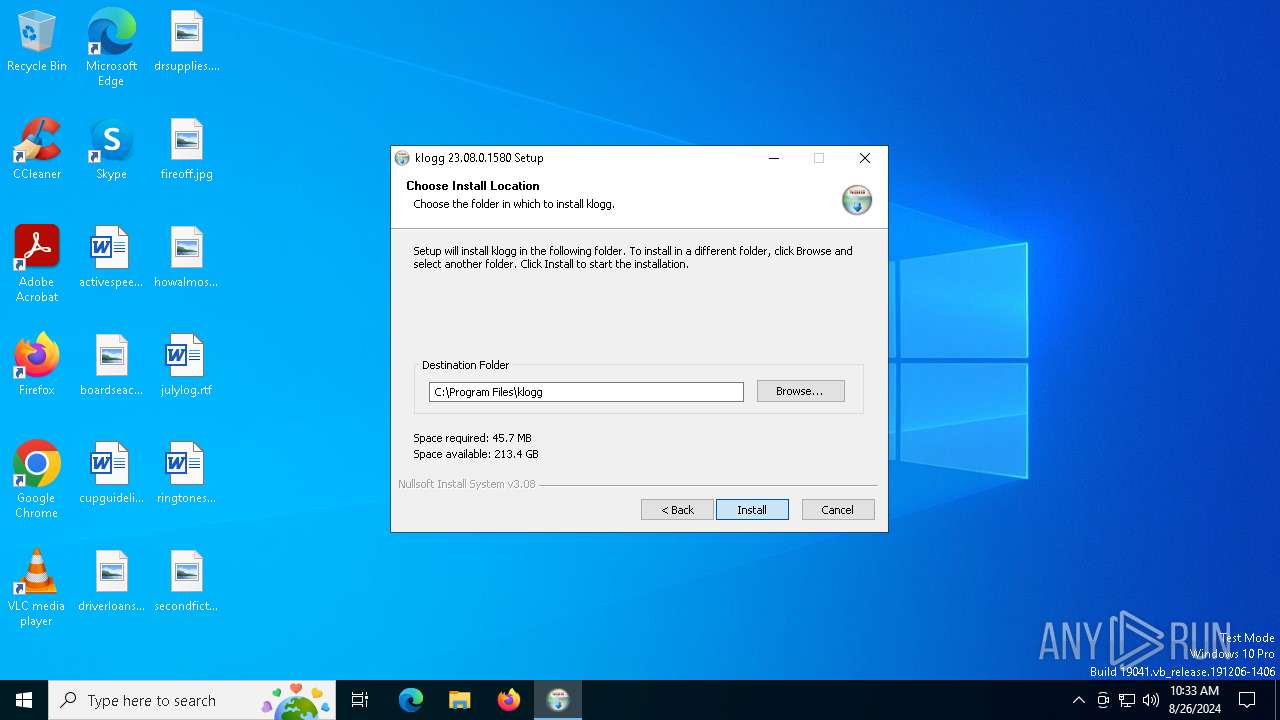
| File name: | klogg-23.08.0.1580-x64-Qt6-setup.exe |
| Full analysis: | https://app.any.run/tasks/9163b422-90e2-440a-9454-a67944b78301 |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 10:32:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 70F9CD4B769116C048C87B36E5CB7D43 |
| SHA1: | 32B3F4F8C6A3A7EF7947C7A425BC1FF5934EA02E |
| SHA256: | DDB0BC4B34012912DB953A5F98122CA72C0A060D2D9CF1111EEAACD4D9790700 |
| SSDEEP: | 98304:HJ8JFWk3jKO70htg7RN+DbClxChtrg4zOlhCdZl9tcI2lcfY+XOH2zpKIwe5uxO6:H964hj8YHCHCtaCmhE1fMD |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
Executable content was dropped or overwritten
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
The process creates files with name similar to system file names
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
Malware-specific behavior (creating "System.dll" in Temp)
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
Creates a software uninstall entry
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
Process drops legitimate windows executable
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
The process drops C-runtime libraries
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
INFO
Create files in a temporary directory
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
- klogg.exe (PID: 5988)
Creates files in the program directory
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
Reads the computer name
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
- klogg.exe (PID: 5988)
Creates files or folders in the user directory
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
- klogg.exe (PID: 5988)
Manual execution by a user
- klogg.exe (PID: 5988)
Checks supported languages
- klogg-23.08.0.1580-x64-Qt6-setup.exe (PID: 6744)
- klogg.exe (PID: 5988)
- klogg_crashpad_handler.exe (PID: 6168)
Reads the machine GUID from the registry
- klogg.exe (PID: 5988)
Reads Environment values
- klogg.exe (PID: 5988)
Process checks computer location settings
- klogg.exe (PID: 5988)
Reads the time zone
- klogg.exe (PID: 5988)
Checks proxy server information
- klogg.exe (PID: 5988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:56:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3640 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
132
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2700 | "C:\Users\admin\AppData\Local\Temp\klogg-23.08.0.1580-x64-Qt6-setup.exe" | C:\Users\admin\AppData\Local\Temp\klogg-23.08.0.1580-x64-Qt6-setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5988 | "C:\Program Files\klogg\klogg.exe" | C:\Program Files\klogg\klogg.exe | — | explorer.exe | |||||||||||
User: admin Company: Anton Filimonov Integrity Level: MEDIUM Description: klogg log viewer Exit code: 0 Version: 23.08.0.1580 Modules
| |||||||||||||||
| 6168 | "C:\Program Files\klogg\klogg_crashpad_handler.exe" --no-rate-limit --database=C:\Users\admin\AppData\Roaming\klogg\klogg_dump --metrics-dir=C:\Users\admin\AppData\Roaming\klogg\klogg_dump --url=https://o453796.ingest.sentry.io:443/api/5442855/minidump/?sentry_client=sentry.native/0.6.5&sentry_key=aad3b270e5ba4ec2915eb5caf6e6d929 --attachment=C:\Users\admin\AppData\Roaming\klogg\klogg_dump\d1aeff41-389b-4685-3aa1-3709e0528969.run\__sentry-event --attachment=C:\Users\admin\AppData\Roaming\klogg\klogg_dump\d1aeff41-389b-4685-3aa1-3709e0528969.run\__sentry-breadcrumb1 --attachment=C:\Users\admin\AppData\Roaming\klogg\klogg_dump\d1aeff41-389b-4685-3aa1-3709e0528969.run\__sentry-breadcrumb2 --initial-client-data=0x4e4,0x4e8,0x4ec,0x4e0,0x4f0,0x7ff7a8b83ce8,0x7ff7a8b83d08,0x7ff7a8b83d20 | C:\Program Files\klogg\klogg_crashpad_handler.exe | — | klogg.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6744 | "C:\Users\admin\AppData\Local\Temp\klogg-23.08.0.1580-x64-Qt6-setup.exe" | C:\Users\admin\AppData\Local\Temp\klogg-23.08.0.1580-x64-Qt6-setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
3 885
Read events
3 878
Write events
7
Delete events
0
Modification events
| (PID) Process: | (6744) klogg-23.08.0.1580-x64-Qt6-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\klogg.exe\shell\open |
| Operation: | write | Name: | Klogg log viewer |
Value: klogg | |||
| (PID) Process: | (6744) klogg-23.08.0.1580-x64-Qt6-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\klogg |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\klogg\Uninstall.exe" | |||
| (PID) Process: | (6744) klogg-23.08.0.1580-x64-Qt6-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\klogg |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\klogg | |||
| (PID) Process: | (6744) klogg-23.08.0.1580-x64-Qt6-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\klogg |
| Operation: | write | Name: | DisplayName |
Value: klogg | |||
| (PID) Process: | (6744) klogg-23.08.0.1580-x64-Qt6-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\klogg |
| Operation: | write | Name: | DisplayVersion |
Value: 23.08.0.1580 | |||
| (PID) Process: | (6744) klogg-23.08.0.1580-x64-Qt6-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\klogg |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (6744) klogg-23.08.0.1580-x64-Qt6-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\klogg |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
Executable files
26
Suspicious files
3
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6744 | klogg-23.08.0.1580-x64-Qt6-setup.exe | C:\Program Files\klogg\COPYING | text | |
MD5:3C34AFDC3ADF82D2448F12715A255122 | SHA256:0B383D5A63DA644F628D99C33976EA6487ED89AAA59F0B3257992DEAC1171E6B | |||
| 6744 | klogg-23.08.0.1580-x64-Qt6-setup.exe | C:\Program Files\klogg\tbb12.dll | executable | |
MD5:6F36FB0C5F8F6D50142B345BC690D072 | SHA256:8FA88B6401FF730B27B7D46FBC5BC4FF22721BE732B1FAFC8A8F1F9CD7DE4407 | |||
| 6744 | klogg-23.08.0.1580-x64-Qt6-setup.exe | C:\Users\admin\AppData\Local\Temp\nsiAC96.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 6744 | klogg-23.08.0.1580-x64-Qt6-setup.exe | C:\Program Files\klogg\DOCUMENTATION.md | text | |
MD5:1142579EDC9BF0A5B558105667E08067 | SHA256:92B3EE7F4B1B1A3FD0362C45D8E55D9AF4799731B5DA5818A3F0E8D78EFA3938 | |||
| 6744 | klogg-23.08.0.1580-x64-Qt6-setup.exe | C:\Users\admin\AppData\Local\Temp\nsiAC96.tmp\nsDialogs.dll | executable | |
MD5:6C3F8C94D0727894D706940A8A980543 | SHA256:56B96ADD1978B1ABBA286F7F8982B0EFBE007D4A48B3DED6A4D408E01D753FE2 | |||
| 6744 | klogg-23.08.0.1580-x64-Qt6-setup.exe | C:\Program Files\klogg\klogg_crashpad_handler.exe | executable | |
MD5:0085F03062157E8FF4291DF91DC1CB34 | SHA256:D6B685868AA09CD6C23893A1D62E07212843B656BF2810448ADBBAEE95444854 | |||
| 6744 | klogg-23.08.0.1580-x64-Qt6-setup.exe | C:\Program Files\klogg\klogg_minidump_dump.exe | executable | |
MD5:84DB7C760E658196B015ED9D88979DEA | SHA256:C8D1B3597F91A5D0E7368E447F233A01819EF562AADB7FF8DDA33D41BED4456F | |||
| 6744 | klogg-23.08.0.1580-x64-Qt6-setup.exe | C:\Program Files\klogg\NOTICE | text | |
MD5:A26F075381AFC30CB3D8EAFDB0AC5323 | SHA256:B47635506E821FB82D67F764C65BFDA59FD9CDBC5A8EA6FC28375763862CC9DB | |||
| 6744 | klogg-23.08.0.1580-x64-Qt6-setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\SendTo\klogg.lnk | binary | |
MD5:6818B850DC0D4477C2EF0B6131E2C7AE | SHA256:3B585121FFDDD5AA8900F552AC1C6C3B4E78E39318D4C3796B23C65EC43B0359 | |||
| 6744 | klogg-23.08.0.1580-x64-Qt6-setup.exe | C:\Program Files\klogg\Qt6Core.dll | executable | |
MD5:970DF5D767E87C18EBED28381B0F4ADC | SHA256:238B6DAD34D40EB3E1C4999ECD224BE2EF0FFF3CC7B2587D6B4D9DD260EFFA49 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
42
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2660 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3276 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3276 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
6876 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6776 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6876 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 20.7.2.167:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2660 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2660 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3276 | SIHClient.exe | 52.165.165.26:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3276 | SIHClient.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |