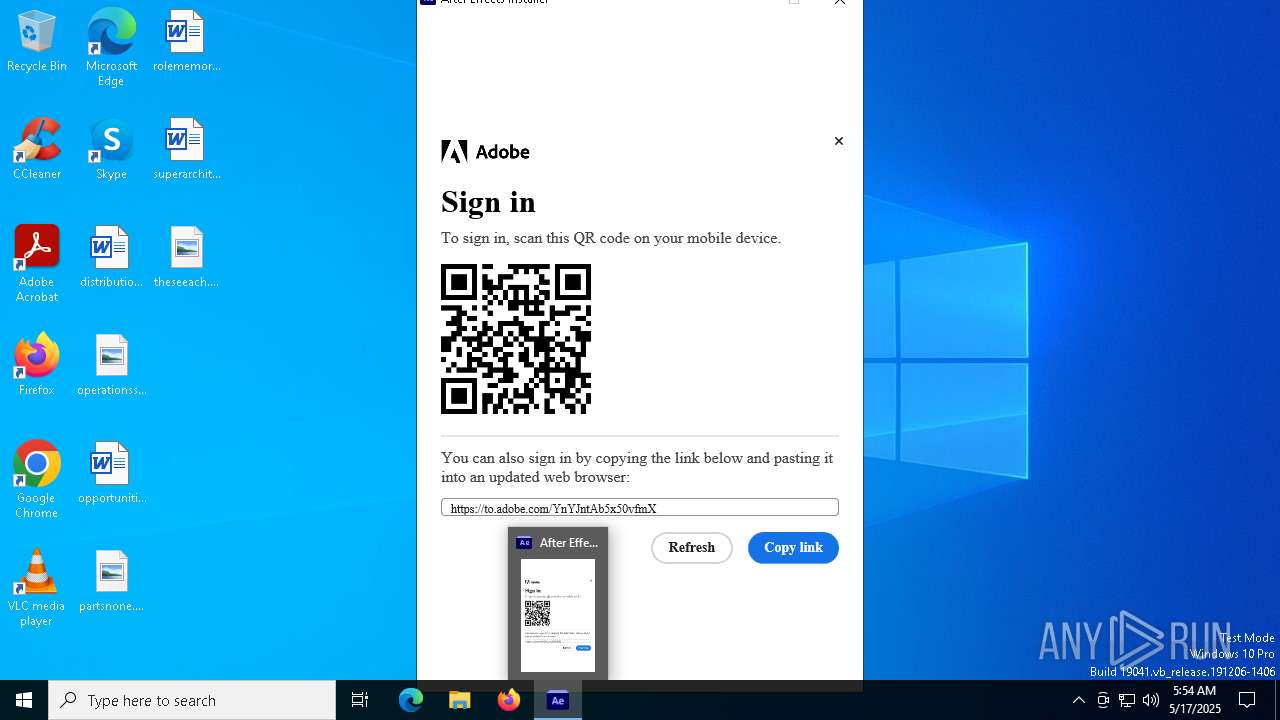
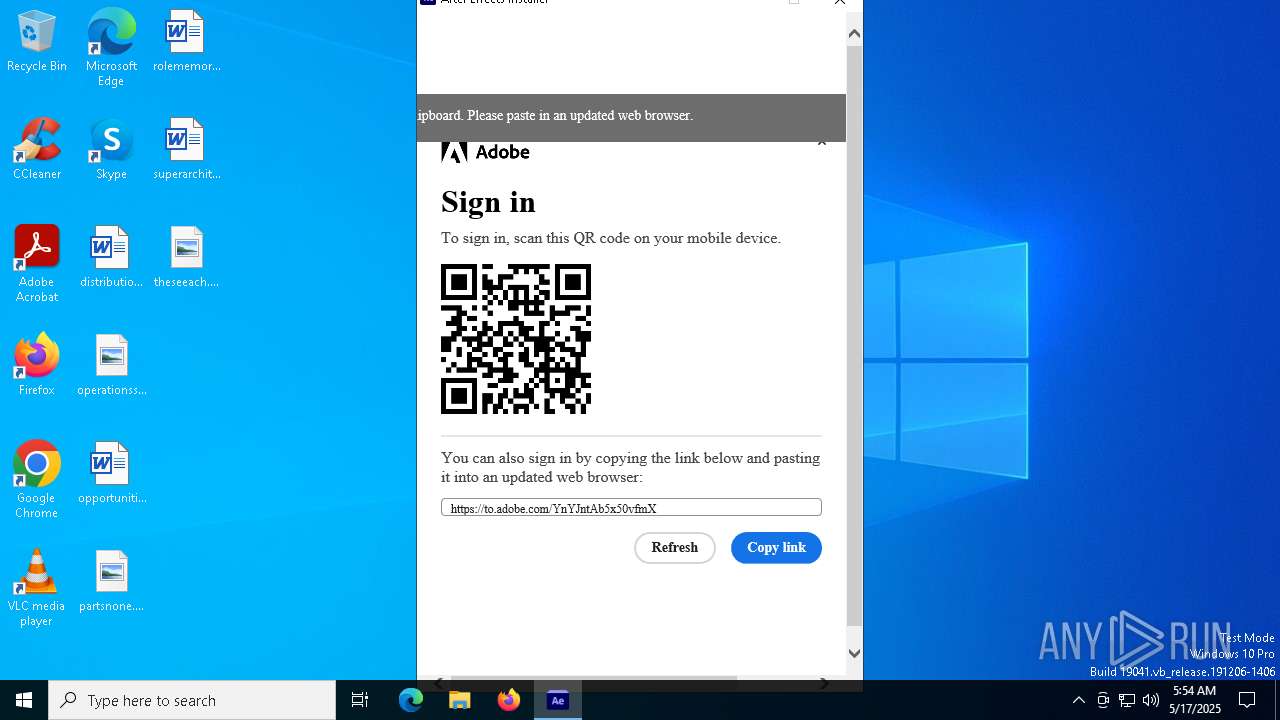
| File name: | After_Effects_Set-Up.exe |
| Full analysis: | https://app.any.run/tasks/30cd9ac3-acc5-412a-81b0-106d6c04a740 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 05:53:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | FA1BEBA48EF8C786B2A4F38ADC3B4483 |
| SHA1: | 19745869810CD99CAC44709BD42C2B0E25FEC622 |
| SHA256: | DDAF989461BAA7EEB0D9787A2A072722ABC3F51E53B1B607AB1BA7B16F49F378 |
| SSDEEP: | 98304:ehrrrAZbJJcNChltm1kO0U2qcJtWYhcU91jTJ7bWu7Cw28/H/EDOjdmRFva3opuq:7Qn3xQj3s |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- After_Effects_Set-Up.exe (PID: 4620)
Reads Microsoft Outlook installation path
- After_Effects_Set-Up.exe (PID: 4620)
Reads Internet Explorer settings
- After_Effects_Set-Up.exe (PID: 4620)
Reads security settings of Internet Explorer
- After_Effects_Set-Up.exe (PID: 4620)
INFO
Reads the computer name
- After_Effects_Set-Up.exe (PID: 4620)
- After_Effects_Set-Up.exe (PID: 5548)
Create files in a temporary directory
- After_Effects_Set-Up.exe (PID: 4620)
The sample compiled with english language support
- After_Effects_Set-Up.exe (PID: 4620)
Creates files or folders in the user directory
- After_Effects_Set-Up.exe (PID: 4620)
Checks supported languages
- After_Effects_Set-Up.exe (PID: 4620)
- After_Effects_Set-Up.exe (PID: 5548)
Process checks computer location settings
- After_Effects_Set-Up.exe (PID: 4620)
Reads the software policy settings
- After_Effects_Set-Up.exe (PID: 5548)
- After_Effects_Set-Up.exe (PID: 4620)
Checks proxy server information
- After_Effects_Set-Up.exe (PID: 5548)
- After_Effects_Set-Up.exe (PID: 4620)
Process checks whether UAC notifications are on
- After_Effects_Set-Up.exe (PID: 4620)
Reads the machine GUID from the registry
- After_Effects_Set-Up.exe (PID: 4620)
UPX packer has been detected
- After_Effects_Set-Up.exe (PID: 4620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:10:30 03:14:41+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.23 |
| CodeSize: | 2072576 |
| InitializedDataSize: | 45056 |
| UninitializedDataSize: | 3284992 |
| EntryPoint: | 0x51cb70 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.3.5.13 |
| ProductVersionNumber: | 5.3.5.13 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Adobe Inc. |
| FileDescription: | Adobe Installer |
| FileVersion: | 5.3.5.13 |
| InternalName: | Adobe Installer |
| LegalCopyright: | © 2015-2020 Adobe. All rights reserved. |
| OriginalFileName: | Adobe Installer |
| ProductName: | Adobe Installer |
| ProductVersion: | 5.3.5.13 |
Total processes
131
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4620 | "C:\Users\admin\AppData\Local\Temp\After_Effects_Set-Up.exe" | C:\Users\admin\AppData\Local\Temp\After_Effects_Set-Up.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Installer Version: 5.3.5.13 Modules
| |||||||||||||||
| 5548 | "C:\Users\admin\AppData\Local\Temp\After_Effects_Set-Up.exe" --pipename={8C059D23-F29A-4DDB-9A9E-66418B98C259} --pid=4620 --locale=en_US | C:\Users\admin\AppData\Local\Temp\After_Effects_Set-Up.exe | After_Effects_Set-Up.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: HIGH Description: Adobe Installer Version: 5.3.5.13 Modules
| |||||||||||||||
| 7336 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7368 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 906
Read events
5 903
Write events
3
Delete events
0
Modification events
| (PID) Process: | (4620) After_Effects_Set-Up.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4620) After_Effects_Set-Up.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4620) After_Effects_Set-Up.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
31
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4620 | After_Effects_Set-Up.exe | C:\Users\admin\AppData\Local\Adobe\OOBE\temp_ins_lbs_wid | text | |
MD5:F520D7FCCCA75C97778AD7DCAA1F5D8F | SHA256:43EE2F6FAF793D32E8C4499E68E84D4C36827BDB46A0587781C929BC173AD39F | |||
| 4620 | After_Effects_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\{427F24F9-3934-40F9-A3BC-98B3A180B36E}\main.html | html | |
MD5:A501355E23582CBC6C8C2835FE076F52 | SHA256:4BE92DEE71936C52319D441434992895818586ACAB859000341AF74D0175AB54 | |||
| 4620 | After_Effects_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\CreativeCloud\ACC\WAM.log | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 4620 | After_Effects_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\{427F24F9-3934-40F9-A3BC-98B3A180B36E}\js\main.js | binary | |
MD5:A2ECC3BBA3A5033720DD046CC6CF64D3 | SHA256:FC1BBA3A598AF6605A402AD2552CD8D7605E51A019AF119F25F30DFBD67E63C0 | |||
| 4620 | After_Effects_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\{427F24F9-3934-40F9-A3BC-98B3A180B36E}\lib\IE8\angular.min.js | binary | |
MD5:2064E68A3817059E5560DD83C5419422 | SHA256:98126704568532E8B3FB771CE6F5F44AE6A24FBF53D61CD7792E23A75971ABC6 | |||
| 4620 | After_Effects_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\{427F24F9-3934-40F9-A3BC-98B3A180B36E}\lib\jquery.min.js | binary | |
MD5:9AC39DC31635A363E377EDA0F6FBE03F | SHA256:9A2723C21FB1B7DFF0E2AA5DC6BE24A9670220A17AE21F70FDBC602D1F8ACD38 | |||
| 4620 | After_Effects_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\{427F24F9-3934-40F9-A3BC-98B3A180B36E}\js\utils.js | binary | |
MD5:11671543588B007E7BE2AF6C784CB8AC | SHA256:BC354F2E25FE40AE21745C51B06D8F34643E238EE67FB94F5CD59C9B56AC17F5 | |||
| 4620 | After_Effects_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\{427F24F9-3934-40F9-A3BC-98B3A180B36E}\js\overlayController.js | binary | |
MD5:B610650C4D826B14C225CFBECA89B8C1 | SHA256:79D00458B49A02ACEE141B53DCF026AA1302AB6B48A745B57E1215BD3B20501C | |||
| 4620 | After_Effects_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\{427F24F9-3934-40F9-A3BC-98B3A180B36E}\lib\IE8\jquery.min.js | binary | |
MD5:E1288116312E4728F98923C79B034B67 | SHA256:BA6EDA7945AB8D7E57B34CC5A3DD292FA2E4C60A5CED79236ECF1A9E0F0C2D32 | |||
| 4620 | After_Effects_Set-Up.exe | C:\Users\admin\AppData\Local\Temp\{427F24F9-3934-40F9-A3BC-98B3A180B36E}\lib\jquery.custom-scrollbar.min.js | binary | |
MD5:AB3ADF4AFF09A1C562A29DB05795C8AB | SHA256:D05E193674C6FC31DE0503CBC0B152600F22689AD7AD72ADB35FCC7C25D4B01B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
43
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4620 | After_Effects_Set-Up.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | unknown | — | — | whitelisted |
4620 | After_Effects_Set-Up.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEALg45daKT25OnNobTFoqPw%3D | unknown | — | — | whitelisted |
4620 | After_Effects_Set-Up.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEQCA5WrF4j1Lr8MOJXyXArf%2F | unknown | — | — | whitelisted |
4620 | After_Effects_Set-Up.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
7908 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7908 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4620 | After_Effects_Set-Up.exe | 52.26.37.169:443 | na1e-acc.services.adobe.com | AMAZON-02 | US | whitelisted |
4620 | After_Effects_Set-Up.exe | 54.195.71.107:443 | cc-api-data.adobe.io | AMAZON-02 | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5548 | After_Effects_Set-Up.exe | 54.195.71.107:443 | cc-api-data.adobe.io | AMAZON-02 | IE | whitelisted |
4620 | After_Effects_Set-Up.exe | 162.159.140.165:443 | ims-prod07.adobelogin.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
na1e-acc.services.adobe.com |
| whitelisted |
cc-api-data.adobe.io |
| whitelisted |
client.wns.windows.com |
| whitelisted |
cdn-ffc.oobesaas.adobe.com |
| whitelisted |
ims-prod07.adobelogin.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |