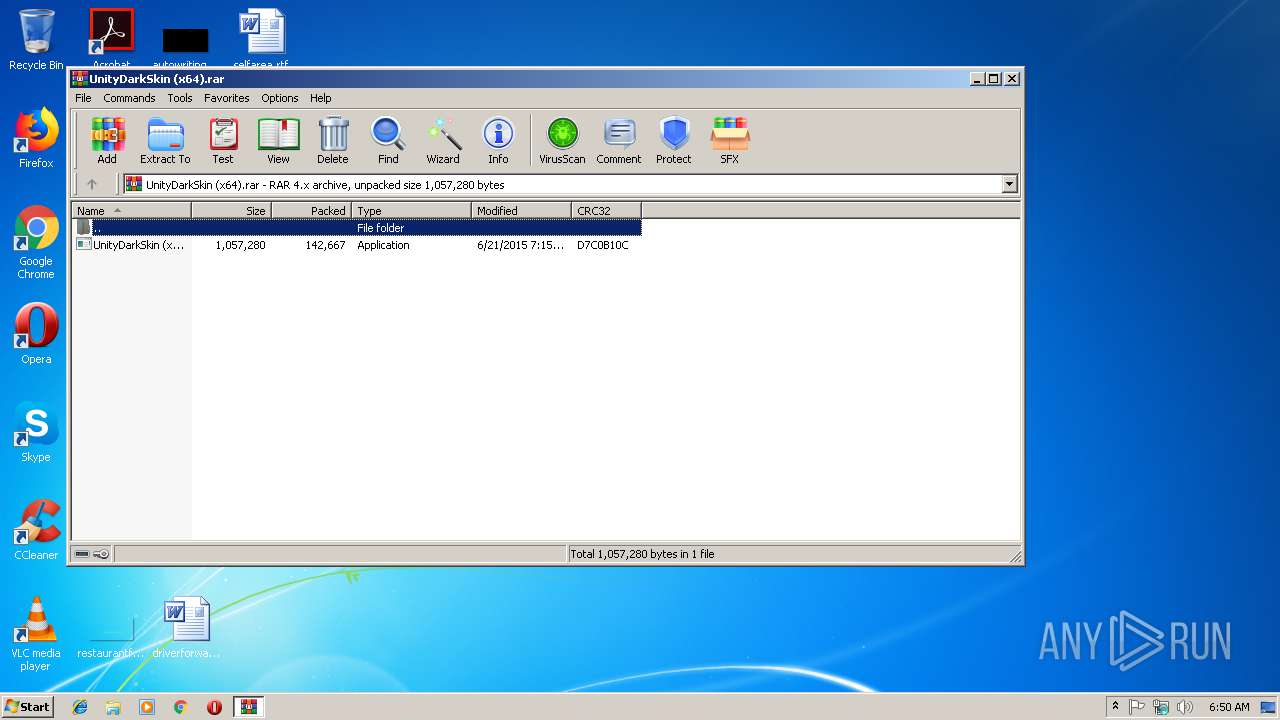
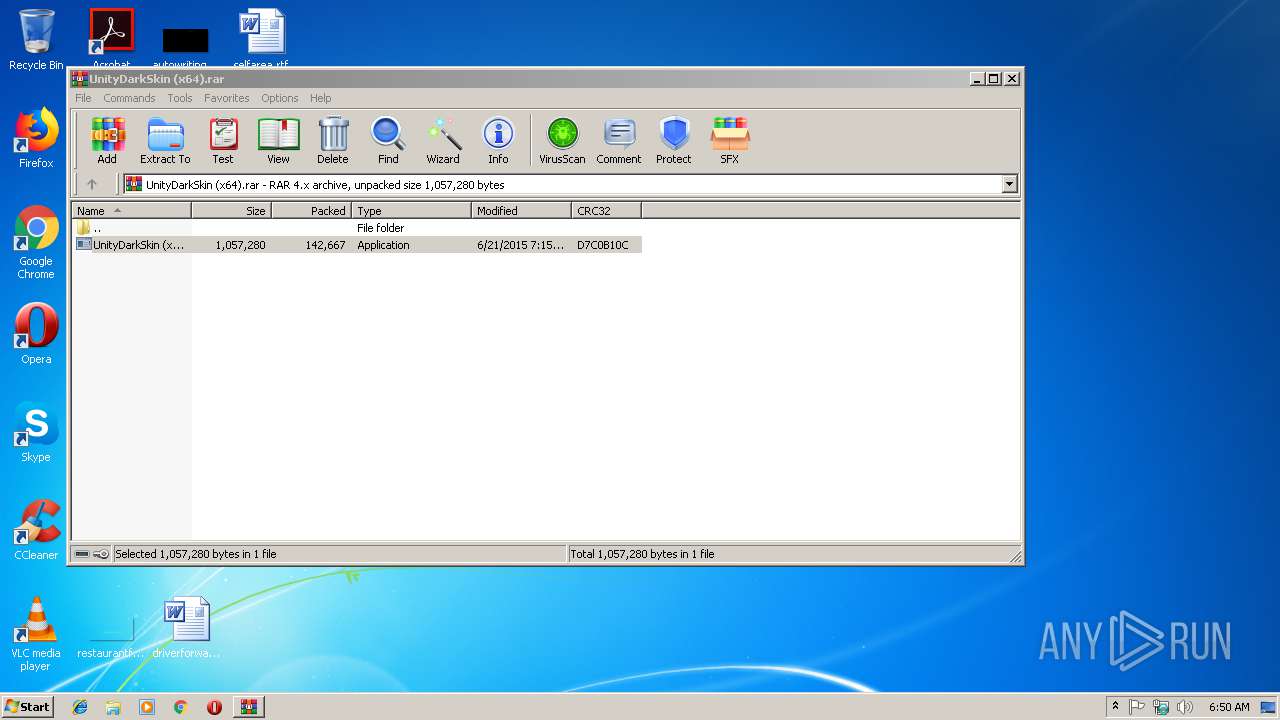
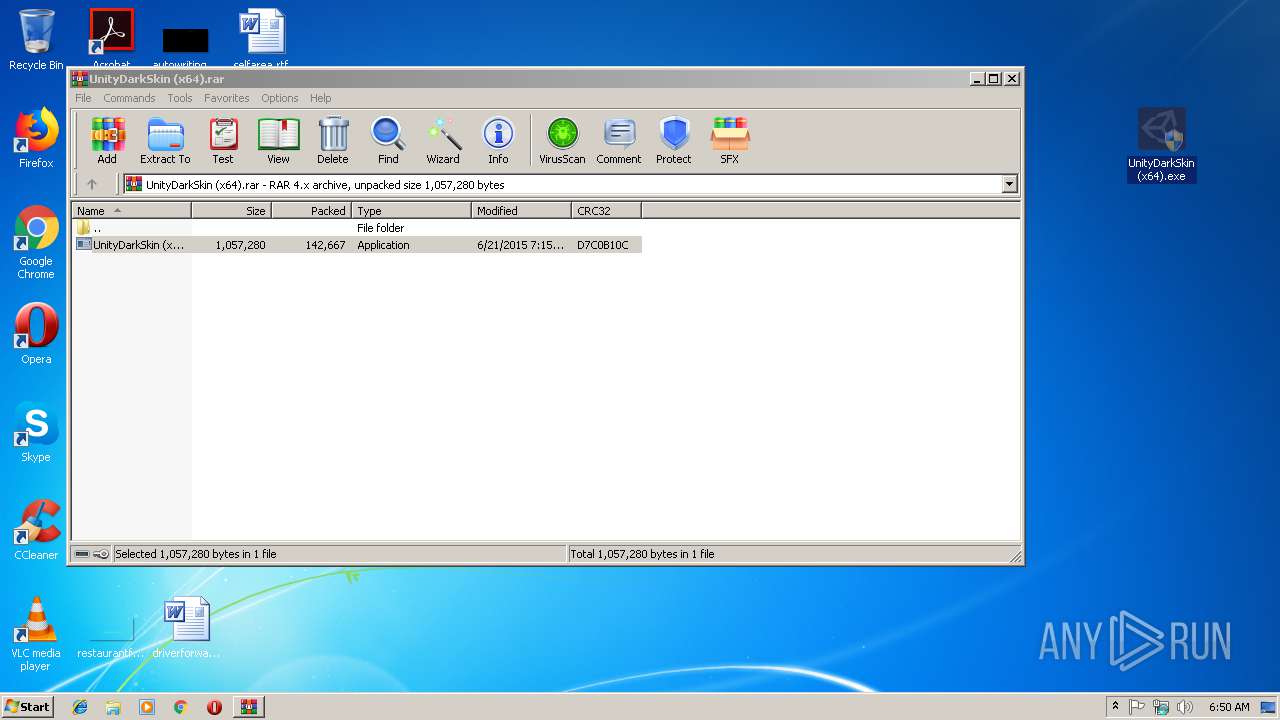
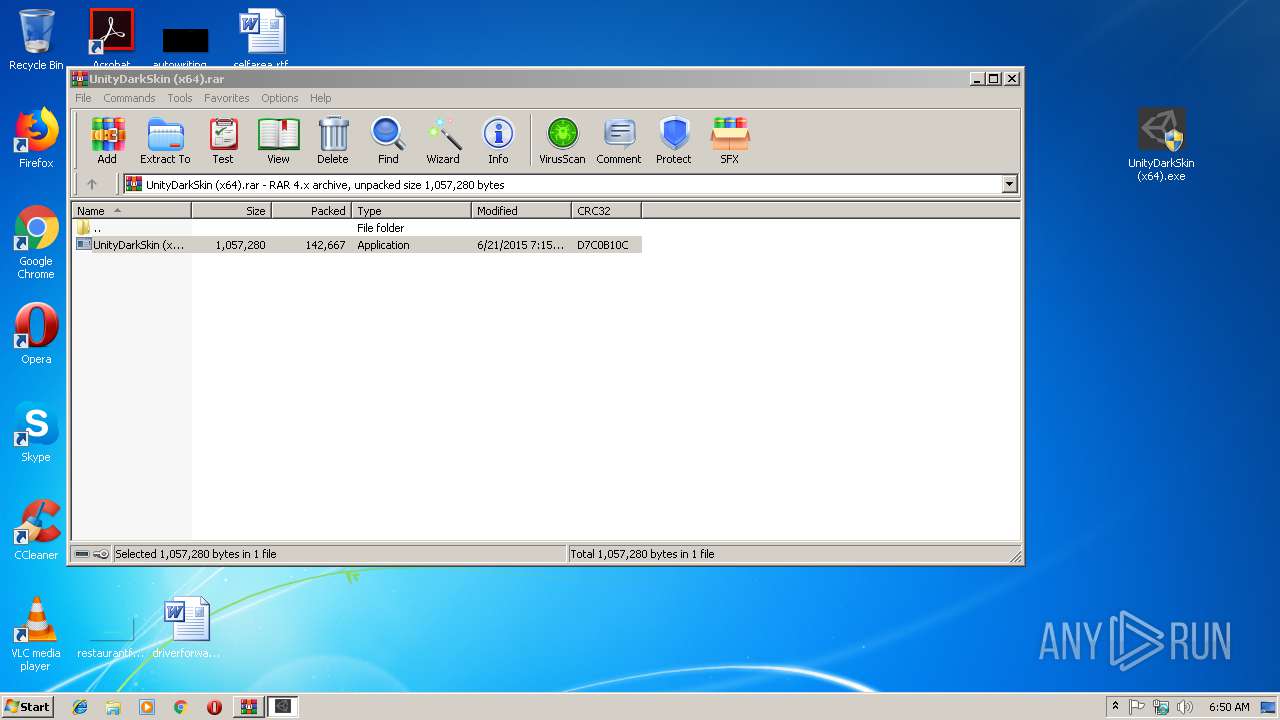
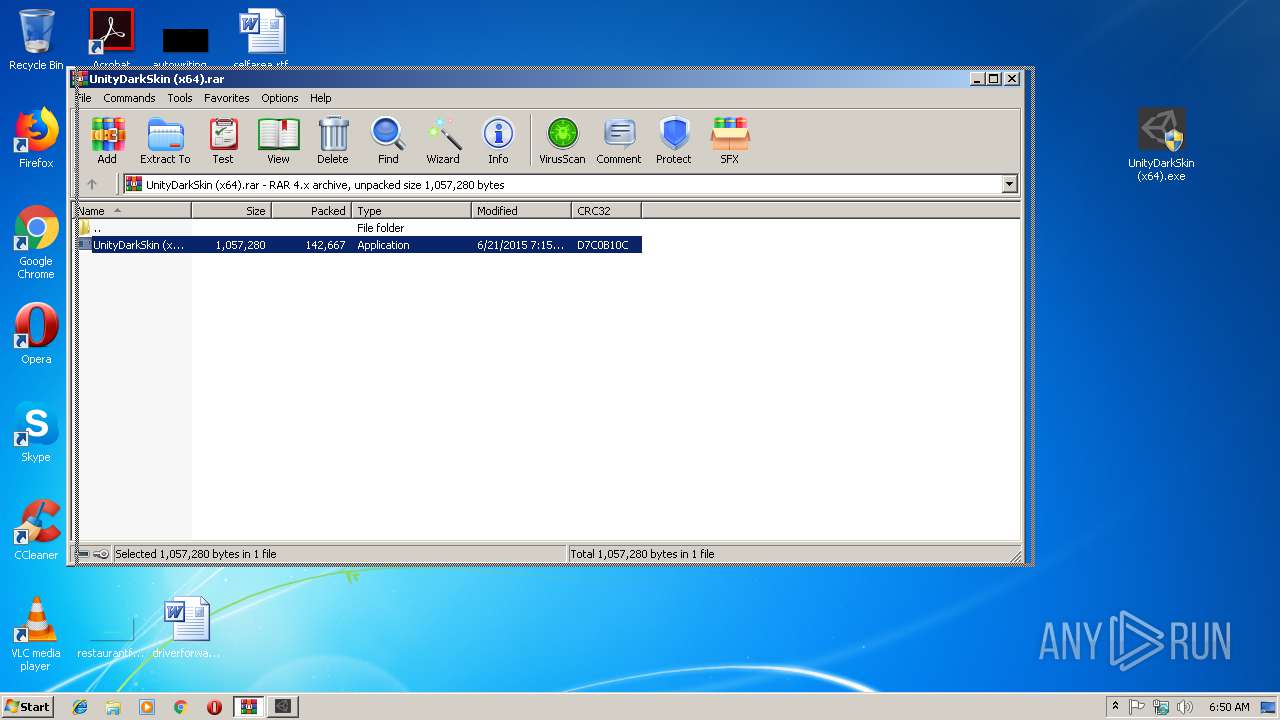
| File name: | UnityDarkSkin (x64).rar |
| Full analysis: | https://app.any.run/tasks/2f73551c-7f94-47fc-8688-ed59be1b54bf |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 06:49:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 64E5295F2DCDCE033F0E4A305C08F133 |
| SHA1: | 2A944DA49285C9EE670E67DD5D402F8E8F8DBA8F |
| SHA256: | DD7C1CE056DDC6110BCC734A5B965A63CBCD3511EE834DE4905338939C75E9BB |
| SSDEEP: | 3072:ofnDY+K0H7Y/z8brR4ypB9LhDCaUhhUXhlFqUD9WJ2eZ7ud6Yg+/91KSeG:r0HM/W4gLhD+hhuhlFP8G6A3eG |
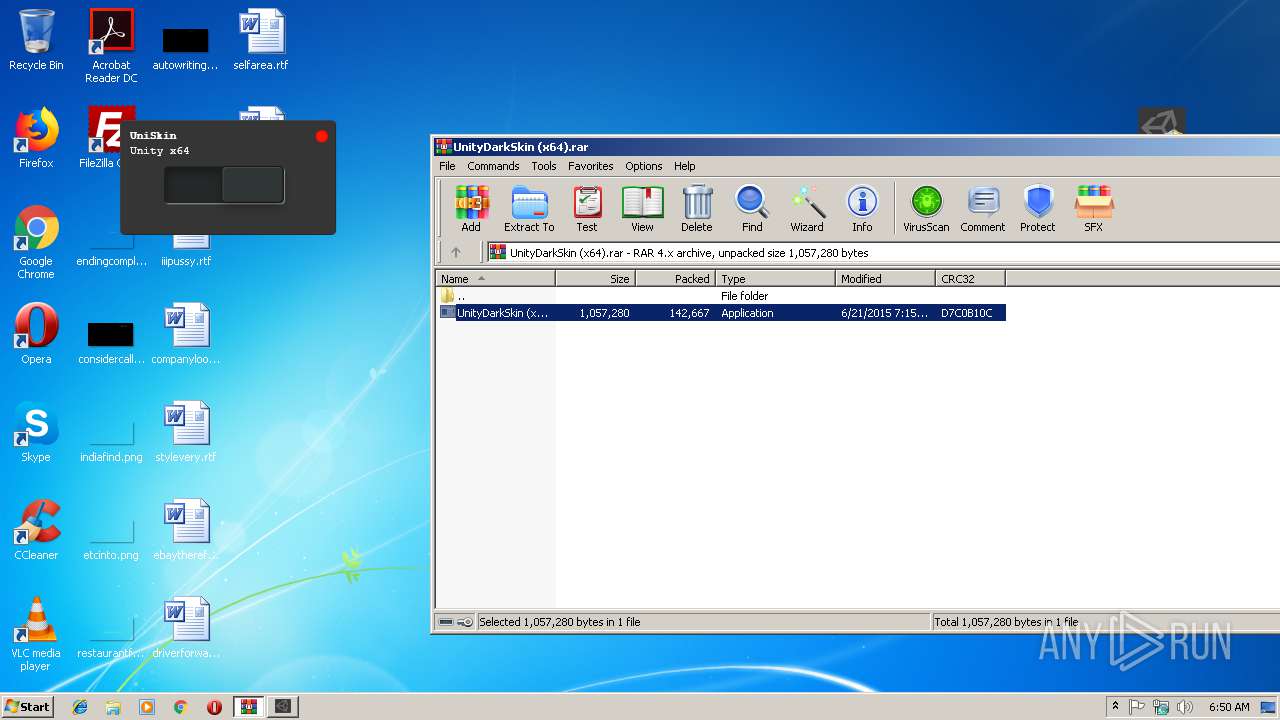
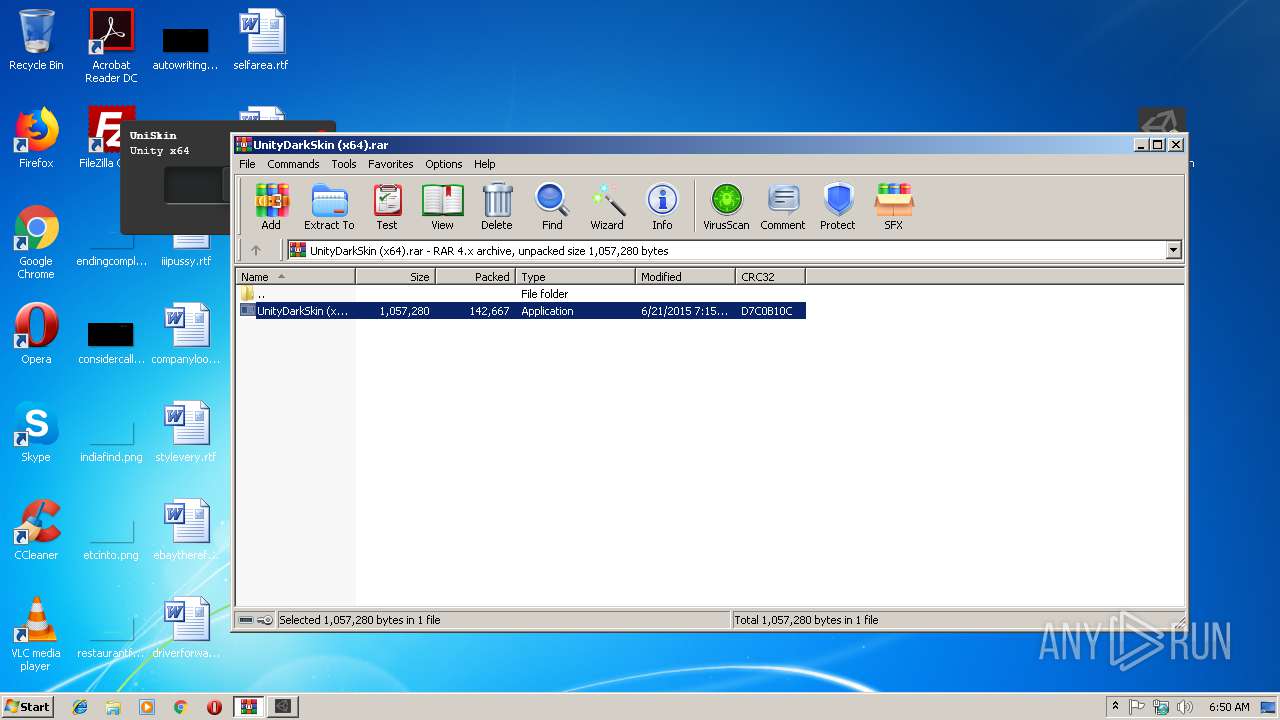
MALICIOUS
Application was dropped or rewritten from another process
- UnityDarkSkin (x64).exe (PID: 2332)
SUSPICIOUS
No suspicious indicators.INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3220)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 142716 |
|---|---|
| UncompressedSize: | 1057280 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2015:06:21 19:15:04 |
| PackingMethod: | Normal |
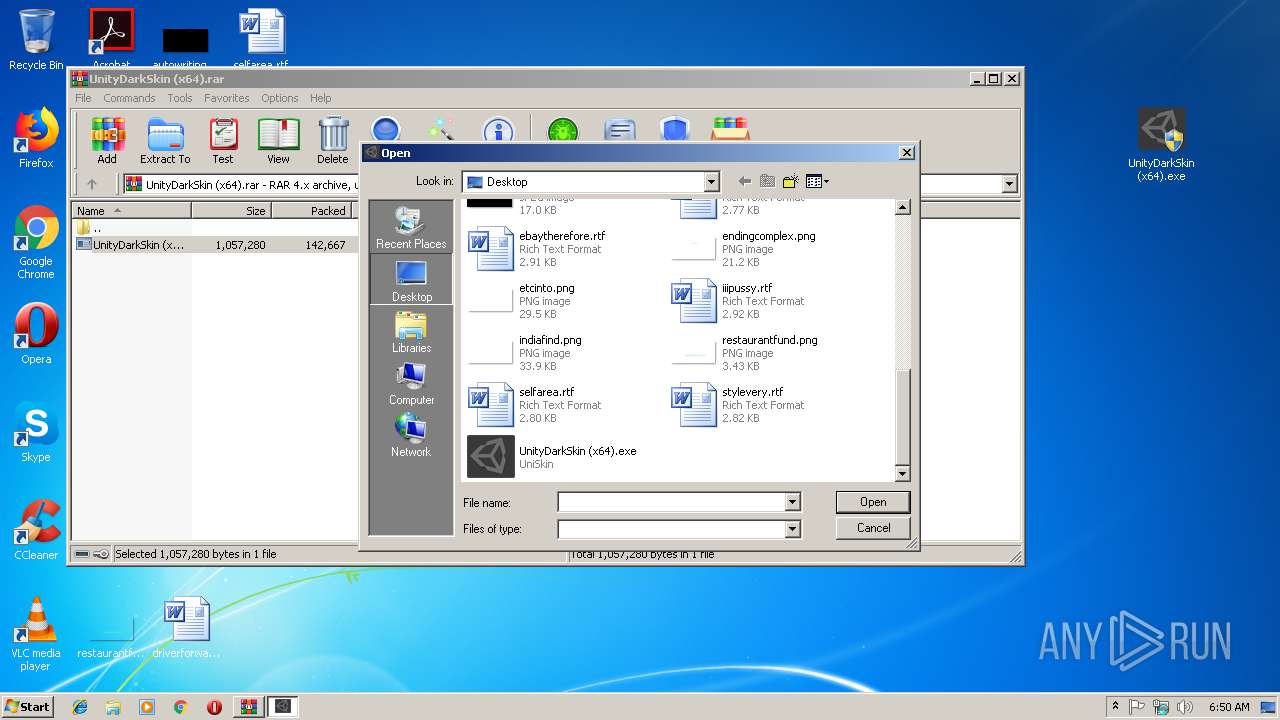
| ArchivedFileName: | UnityDarkSkin (x64).exe |
Total processes
41
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2268 | C:\Windows\Microsoft.Net\Framework\v3.0\WPF\PresentationFontCache.exe | C:\Windows\Microsoft.Net\Framework\v3.0\WPF\PresentationFontCache.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: PresentationFontCache.exe Exit code: 0 Version: 3.0.6920.4902 built by: NetFXw7 Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\Desktop\UnityDarkSkin (x64).exe" | C:\Users\admin\Desktop\UnityDarkSkin (x64).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: UniSkin Exit code: 0 Version: 0.1 Modules
| |||||||||||||||
| 2828 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\UnityDarkSkin (x64).rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3104 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3220 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\driverforward.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 238
Read events
1 140
Write events
86
Delete events
12
Modification events
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\UnityDarkSkin (x64).rar | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2332) UnityDarkSkin (x64).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: UnityDarkSkin (x64).exe | |||
| (PID) Process: | (2332) UnityDarkSkin (x64).exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
0
Text files
3
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2828.1680\UnityDarkSkin (x64).exe | — | |
MD5:— | SHA256:— | |||
| 3220 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3048.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3220 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{237EF8FC-51E2-436C-B8B9-EBD8DEAB8EA0}.tmp | — | |
MD5:— | SHA256:— | |||
| 3220 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{A410F765-1823-4D30-A36D-2A8D34FF6373}.tmp | — | |
MD5:— | SHA256:— | |||
| 2332 | UnityDarkSkin (x64).exe | C:\Users\admin\Desktop\stylevery.rtf | text | |
MD5:— | SHA256:— | |||
| 3220 | WINWORD.EXE | C:\Users\admin\Desktop\~$iverforward.rtf | pgc | |
MD5:— | SHA256:— | |||
| 3220 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 3220 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3220 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\driverforward.rtf.LNK | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report