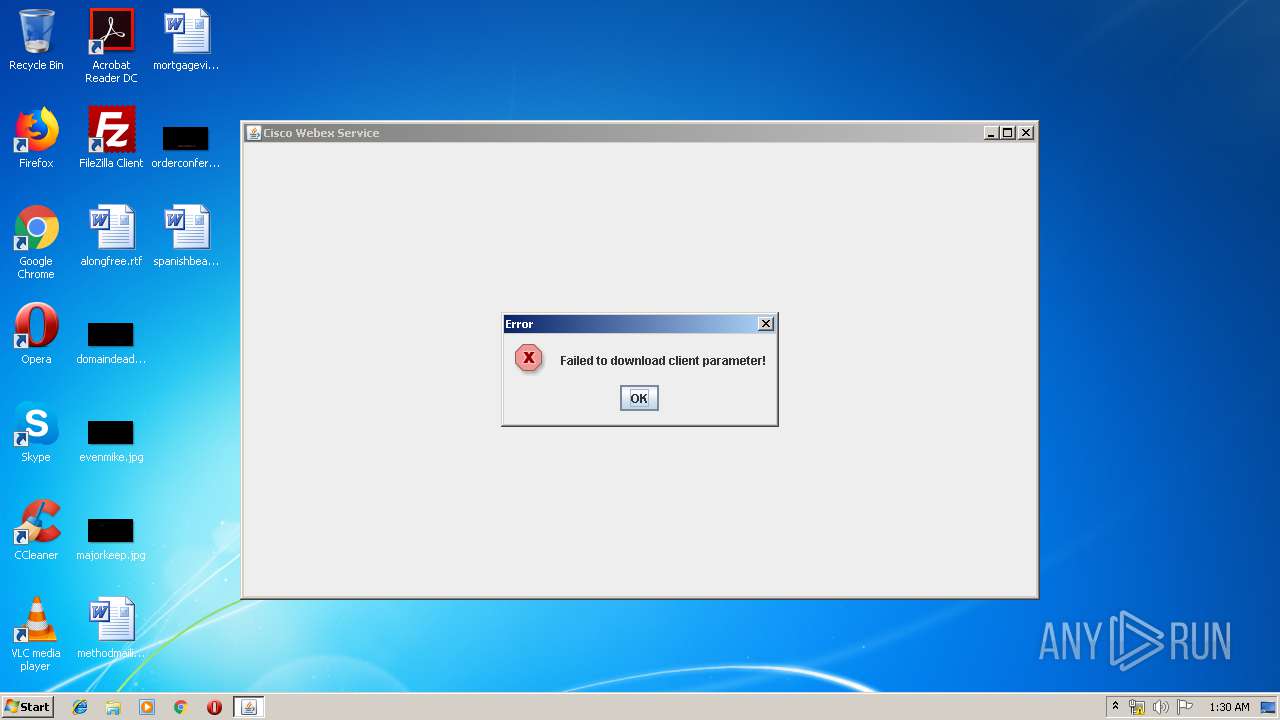
| File name: | CiscoWebExServlet (1) |
| Full analysis: | https://app.any.run/tasks/7d301656-7299-4feb-acce-14f8ac4f8555 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2019, 00:29:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, ASCII text, with very long lines, with no line terminators |
| MD5: | 6E9067B91644A2DA3DD14B68EEE49148 |
| SHA1: | B3340C4E262670A362EE63A5B2BB68883C3FFF05 |
| SHA256: | DD72D6F89F3281ECA34DAB728AE207457788030462A018E0C34640CB184F175A |
| SSDEEP: | 24:2dzPZiaVHDGwylfPAZ8bZ9DVpwl0gDtprrJm:czPkSHuu8zVpwl0Up0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- javaws.exe (PID: 3852)
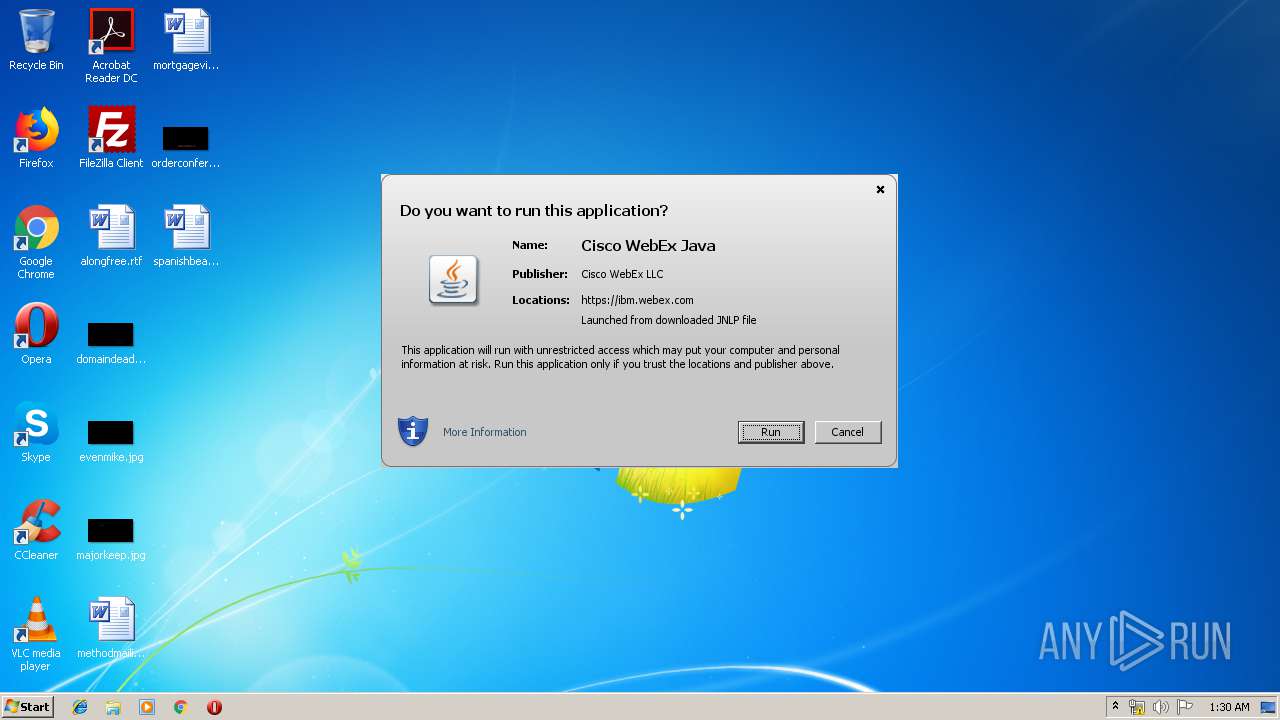
Executes JAVA applets
- javaws.exe (PID: 3852)
Creates files in the user directory
- jp2launcher.exe (PID: 2132)
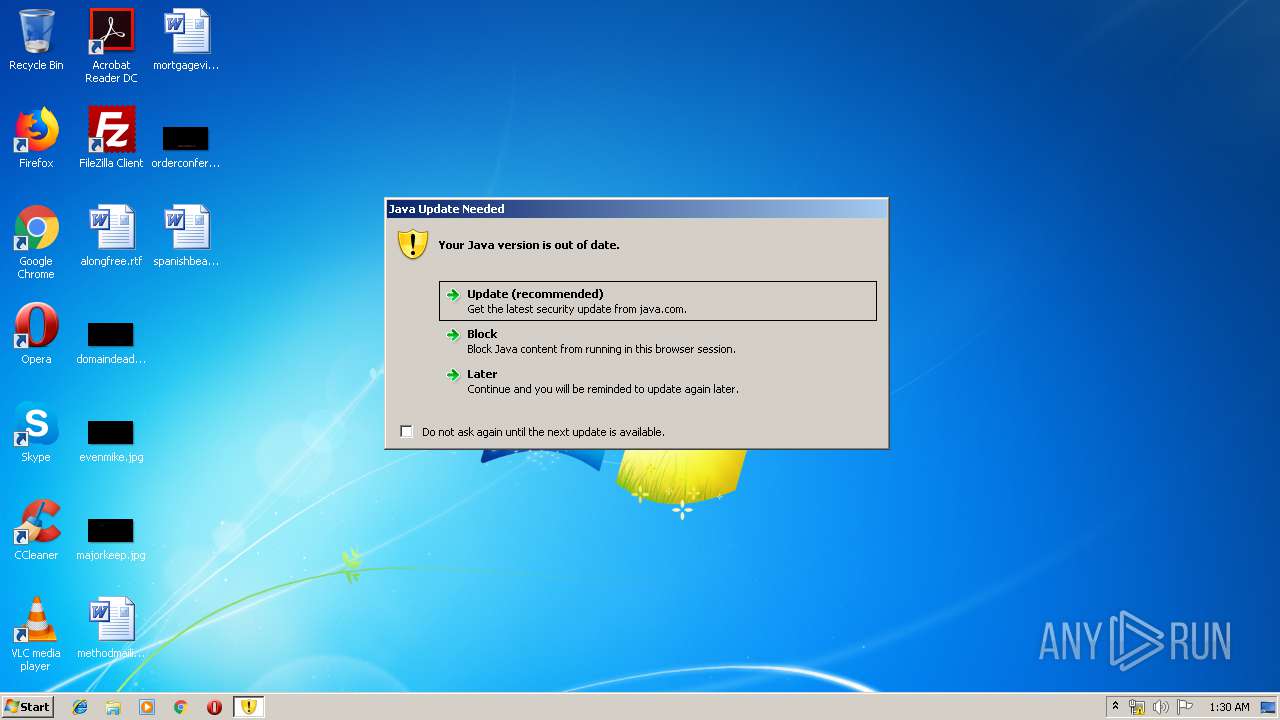
Check for Java to be installed
- javaws.exe (PID: 3852)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jnlp | | | Java Web Start application descriptor (88.3) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (11.6) |
EXIF
XMP
| JnlpSpec: | 7.0+ |
|---|---|
| JnlpCodebase: | https://ibm.webex.com/client/T33L/javaclient/training/ |
| JnlpInformationTitle: | WebEx Java-client |
| JnlpInformationVendor: | Cisco System, Inc. |
| JnlpInformationOffline-allowed: | - |
| JnlpUpdateCheck: | always |
| JnlpUpdatePolicy: | always |
| JnlpSecurityAll-permissions: | - |
| JnlpResourcesJ2seVersion: | 1.7+ |
| JnlpResourcesJ2seHref: | http://java.sun.com/products/autodl/j2se |
| JnlpResourcesJarHref: | atdwnld.jar |
| JnlpResourcesJarMain: | |
| JnlpApplication-descMain-class: | JDownload |
| JnlpApplication-descArgument: | aHR0cHM6Ly9pYm0ud2ViZXguY29tL2libS9qbWZfd2ViLnBocD9BVD1UQyZjb25maWQ9MTIxODg5NjY4NDIyNzA3MjE2JnVpZD01NDA1MzUyNzcmZmxhZz0wfDAmam5scD0xJmVtYWM9U0RKVFN3QUFBQVFWYjVVdklUUEhULXFyZHBqek9QTUxRTHQxYlFEQlY1R3B0bi1zblhJT0lBMg== |
Total processes
39
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2132 | "C:\Program Files\Java\jre1.8.0_92\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_92" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfOTJcbGliXGRlcGxveS5qYXIALURqYXZhLnNlY3VyaXR5LnBvbGljeT1maWxlOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF85MlxsaWJcc2VjdXJpdHlcamF2YXdzLnBvbGljeQAtRHRydXN0UHJveHk9dHJ1ZQAtWHZlcmlmeTpyZW1vdGUALURqbmxweC5ob21lPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF85MlxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURqbmxweC5vcmlnRmlsZW5hbWVBcmc9QzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wXENpc2NvV2ViRXhTZXJ2bGV0ICgxKS5qbmxwAC1Eam5scHgucmVtb3ZlPXRydWUALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF85MlxsaWJcamF2YXdzLmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfOTJcbGliXGRlcGxveS5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzkyXGxpYlxwbHVnaW4uamFyAC1Eam5scHguc3BsYXNocG9ydD00OTI4OQAtRGpubHB4Lmp2bT1DOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfOTJcYmluXGphdmF3LmV4ZQ== -ma QzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wXGphdmF3czI= | C:\Program Files\Java\jre1.8.0_92\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.92.2.14 Modules
| |||||||||||||||
| 2224 | JavaWSSplashScreen -splash 49287 "C:\Program Files\Java\jre1.8.0_92\lib\deploy\splash.gif" | C:\Program Files\Java\jre1.8.0_92\bin\javaws.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.92.2.14 Modules
| |||||||||||||||
| 2728 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_9\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.11.92.2" "later" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 3476 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_9\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.suppression.11.92.2" "false" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 3760 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_9\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.92.2" "1563409815" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 3852 | "C:\Program Files\Java\jre1.8.0_92\bin\javaws.exe" "C:\Users\admin\AppData\Local\Temp\CiscoWebExServlet (1).jnlp" | C:\Program Files\Java\jre1.8.0_92\bin\javaws.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.92.2.14 Modules
| |||||||||||||||
Total events
187
Read events
93
Write events
85
Delete events
9
Modification events
| (PID) Process: | (2728) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2728) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.modified.timestamp |
Value: 1535457890299 | |||
| (PID) Process: | (2728) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.roaming.profile |
Value: false | |||
| (PID) Process: | (2728) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.version |
Value: 8 | |||
| (PID) Process: | (2728) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expired.version |
Value: 11.92.2 | |||
| (PID) Process: | (2728) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.browser.path |
Value: C:\Program Files\Internet Explorer\iexplore.exe | |||
| (PID) Process: | (2728) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.expiration.decision.11.92.2 |
Value: later | |||
| (PID) Process: | (3760) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3760) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.modified.timestamp |
Value: 1563409815046 | |||
| (PID) Process: | (3760) javaw.exe | Key: | HKEY_CURRENT_USER\Software\AppDataLow\Software\JavaSoft\DeploymentProperties |
| Operation: | write | Name: | deployment.roaming.profile |
Value: false | |||
Executable files
1
Suspicious files
2
Text files
23
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2132 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\26\1e4433da-3b5c8cd8-temp | — | |
MD5:— | SHA256:— | |||
| 2132 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\63\615a51ff-77016488-temp | — | |
MD5:— | SHA256:— | |||
| 3852 | javaws.exe | C:\Users\admin\AppData\Local\Temp\javaws2 | xml | |
MD5:— | SHA256:— | |||
| 3476 | javaw.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:— | SHA256:— | |||
| 3476 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2132 | jp2launcher.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2132 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:— | SHA256:— | |||
| 2132 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\cache\6.0\26\1e4433da-3b5c8cd8 | xml | |
MD5:— | SHA256:— | |||
| 3476 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
| 3760 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
5
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2132 | jp2launcher.exe | POST | 200 | 35.158.10.169:80 | http://ocsp.quovadisglobal.com/ | DE | der | 1.78 Kb | whitelisted |
2132 | jp2launcher.exe | POST | 200 | 23.37.43.27:80 | http://sv.symcd.com/ | NL | der | 1.57 Kb | shared |
2132 | jp2launcher.exe | POST | 200 | 35.158.10.169:80 | http://ocsp.quovadisglobal.com/ | DE | der | 1.80 Kb | whitelisted |
2132 | jp2launcher.exe | POST | 200 | 23.37.43.27:80 | http://s2.symcb.com/ | NL | der | 1.71 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2132 | jp2launcher.exe | 35.158.10.169:80 | ocsp.quovadisglobal.com | Amazon.com, Inc. | DE | whitelisted |
2132 | jp2launcher.exe | 66.114.168.199:443 | ibm.webex.com | Cisco Webex LLC | US | unknown |
2132 | jp2launcher.exe | 23.37.43.27:80 | s2.symcb.com | Akamai Technologies, Inc. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ibm.webex.com |
| unknown |
ocsp.quovadisglobal.com |
| whitelisted |
s2.symcb.com |
| whitelisted |
sv.symcd.com |
| shared |