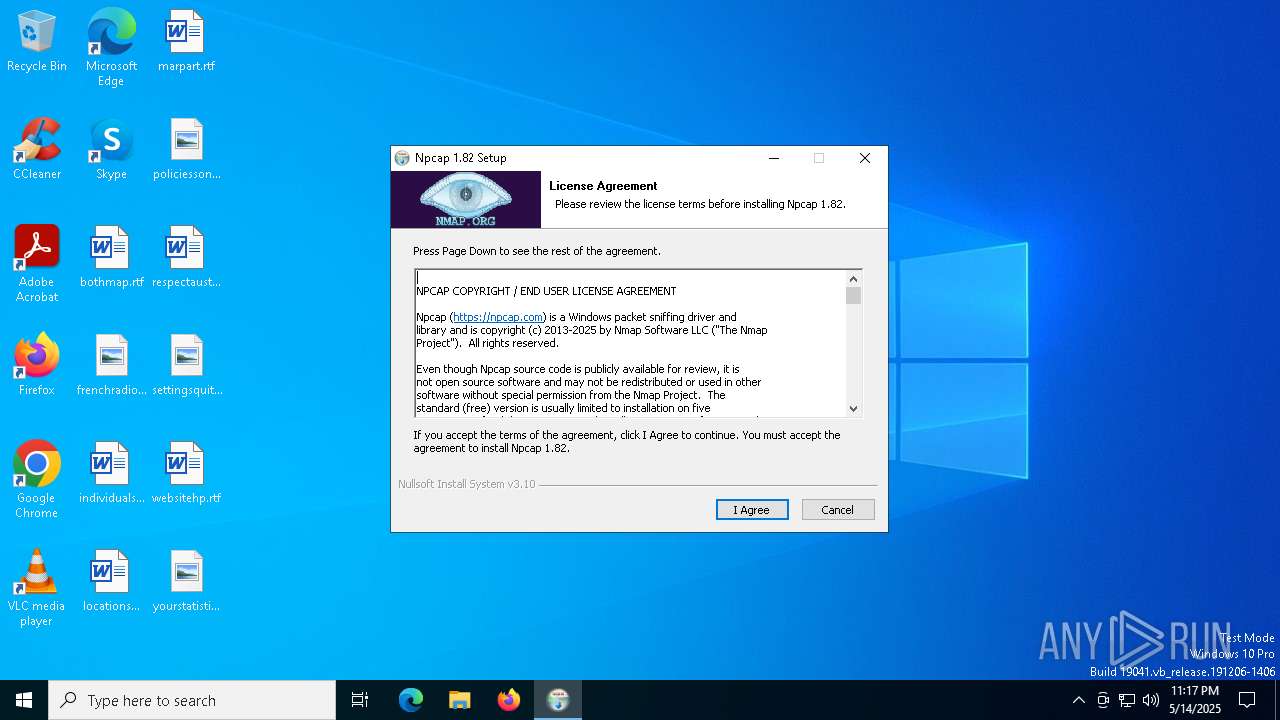
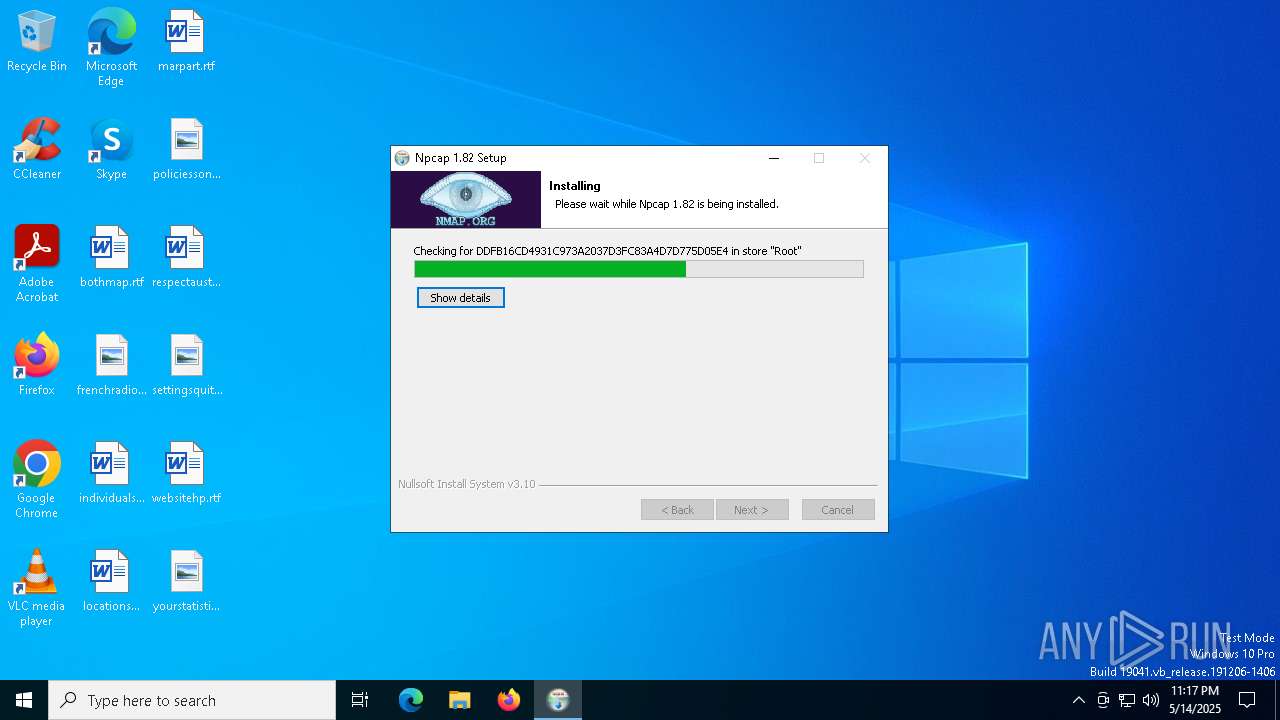
| File name: | npcap-1.82.exe |
| Full analysis: | https://app.any.run/tasks/8941e221-0421-438b-9dac-b96139f46ff8 |
| Verdict: | Malicious activity |
| Analysis date: | May 14, 2025, 23:17:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | BFFB330A7E60C1F6B73DC10A8E7B9C34 |
| SHA1: | AB87F720019E63A4C04628C79112FBCDA6D485D9 |
| SHA256: | DD6A26F07E90FE8308F06B09AF0EAFA188F4FF0A1A184E5ADFA35E37467C705D |
| SSDEEP: | 49152:oTc2+n7LNsFtpZps7BLeILgob7lyKCyuphXM8IOpaxEsn5UZrT5jJWn29PYwdq5P:oTc2+l7BLfgW4fp5rnsyB5jJWn29u5cM |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 7748)
- powershell.exe (PID: 7972)
- powershell.exe (PID: 7400)
- powershell.exe (PID: 7420)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- npcap-1.82.exe (PID: 7188)
The process creates files with name similar to system file names
- npcap-1.82.exe (PID: 7188)
The process hide an interactive prompt from the user
- npcap-1.82.exe (PID: 7188)
Creates a software uninstall entry
- npcap-1.82.exe (PID: 7188)
Starts POWERSHELL.EXE for commands execution
- npcap-1.82.exe (PID: 7188)
Executable content was dropped or overwritten
- npcap-1.82.exe (PID: 7188)
- drvinst.exe (PID: 7152)
- NPFInstall.exe (PID: 7248)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 7748)
- powershell.exe (PID: 7972)
Drops a system driver (possible attempt to evade defenses)
- npcap-1.82.exe (PID: 7188)
- drvinst.exe (PID: 7152)
- NPFInstall.exe (PID: 7248)
The process bypasses the loading of PowerShell profile settings
- npcap-1.82.exe (PID: 7188)
Removes files via Powershell
- powershell.exe (PID: 7972)
Adds/modifies Windows certificates
- certutil.exe (PID: 4652)
- certutil.exe (PID: 5380)
- certutil.exe (PID: 680)
Creates files in the driver directory
- drvinst.exe (PID: 7152)
- NPFInstall.exe (PID: 7248)
Creates or modifies Windows services
- npcap-1.82.exe (PID: 7188)
INFO
The sample compiled with english language support
- npcap-1.82.exe (PID: 7188)
Creates files in the program directory
- npcap-1.82.exe (PID: 7188)
- NPFInstall.exe (PID: 7680)
Reads the computer name
- NPFInstall.exe (PID: 7680)
- npcap-1.82.exe (PID: 7188)
- drvinst.exe (PID: 7152)
- NPFInstall.exe (PID: 7248)
Create files in a temporary directory
- npcap-1.82.exe (PID: 7188)
- NPFInstall.exe (PID: 7248)
Checks supported languages
- SearchApp.exe (PID: 2924)
- npcap-1.82.exe (PID: 7188)
- NPFInstall.exe (PID: 7680)
- NPFInstall.exe (PID: 1164)
- NPFInstall.exe (PID: 7248)
- drvinst.exe (PID: 7152)
- NPFInstall.exe (PID: 1168)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 7756)
- conhost.exe (PID: 5216)
- conhost.exe (PID: 7980)
- conhost.exe (PID: 8152)
- conhost.exe (PID: 5556)
- conhost.exe (PID: 5008)
- conhost.exe (PID: 1184)
- conhost.exe (PID: 5772)
- conhost.exe (PID: 7588)
- conhost.exe (PID: 4620)
- conhost.exe (PID: 7240)
- powershell.exe (PID: 7420)
- conhost.exe (PID: 7500)
Reads security settings of Internet Explorer
- pnputil.exe (PID: 5800)
Reads the software policy settings
- pnputil.exe (PID: 5800)
- drvinst.exe (PID: 7152)
- SearchApp.exe (PID: 2924)
Reads the machine GUID from the registry
- drvinst.exe (PID: 7152)
- SearchApp.exe (PID: 2924)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7420)
Process checks computer location settings
- SearchApp.exe (PID: 2924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:56:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 28672 |
| InitializedDataSize: | 150528 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3ae9 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.1.82.418 |
| ProductVersionNumber: | 5.1.82.418 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Npcap 1.82 installer |
| FileVersion: | 1.82 |
| LegalCopyright: | Copyright (c) 2025, Nmap Software LLC. All rights reserved. |
| ProductName: | Npcap |
| ProductVersion: | 1.82 |
Total processes
170
Monitored processes
35
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Users\admin\AppData\Local\Temp\npcap-1.82.exe" | C:\Users\admin\AppData\Local\Temp\npcap-1.82.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Npcap 1.82 installer Exit code: 3221226540 Version: 1.82 Modules
| |||||||||||||||
| 680 | certutil.exe -addstore -f "AddressBook" "C:\Users\admin\AppData\Local\Temp\nsfB75D.tmp\digi-ts-2023.p7b" | C:\Windows\SysWOW64\certutil.exe | — | npcap-1.82.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\Program Files\Npcap\NPFInstall.exe" -n -c | C:\Program Files\Npcap\NPFInstall.exe | — | npcap-1.82.exe | |||||||||||
User: admin Company: Nmap Software LLC Integrity Level: HIGH Description: A LWF & WFP driver installation tool Exit code: 0 Version: 1.82 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Npcap\NPFInstall.exe" -n -iw | C:\Program Files\Npcap\NPFInstall.exe | — | npcap-1.82.exe | |||||||||||
User: admin Company: Nmap Software LLC Integrity Level: HIGH Description: A LWF & WFP driver installation tool Exit code: 0 Version: 1.82 Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NPFInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2924 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | C:\WINDOWS\System32\rundll32.exe shell32.dll,SHCreateLocalServerRunDll {c82192ee-6cb5-4bc0-9ef0-fb818773790a} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4228 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NPFInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4652 | certutil.exe -addstore -f "Root" "C:\Users\admin\AppData\Local\Temp\nsfB75D.tmp\DDFB16CD4931C973A2037D3FC83A4D7D775D05E4.sst" | C:\Windows\SysWOW64\certutil.exe | — | npcap-1.82.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 533
Read events
36 389
Write events
136
Delete events
8
Modification events
| (PID) Process: | (2924) SearchApp.exe | Key: | \REGISTRY\A\{919c907a-b14a-1c2d-b076-c1402ff6e70c}\LocalState\ConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0049006E007000750074005F007B00380033003200620036003800640032002D0037006600650032002D0034006500370031002D0061003300610064002D003200360031003600360062003600350036006500630036007D000000E5A3A65326C5DB01 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | \REGISTRY\A\{919c907a-b14a-1c2d-b076-c1402ff6e70c}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0041007000700073005F007B00300063006300310030003400660034002D0032006600360031002D0034006500330066002D0038006200340064002D003700640033003500660030003600650038003200380037007D000000E5A3A65326C5DB01 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | \REGISTRY\A\{919c907a-b14a-1c2d-b076-c1402ff6e70c}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LastConstraintIndexBuildCompleted |
Value: 08FEA75326C5DB01E5A3A65326C5DB01 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Input_{832b68d2-7fe2-4e71-a3ad-26166b656ec6} | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{0cc104f4-2f61-4e3f-8b4d-7d35f06e8287} | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | IndexedLanguage |
Value: en-US | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | \REGISTRY\A\{919c907a-b14a-1c2d-b076-c1402ff6e70c}\LocalState\AppIndexer |
| Operation: | write | Name: | LatestCacheFileName |
Value: 410070007000430061006300680065003100330033003900310037003300380032003200370039003100310031003500310032002E007400780074000000E5A3A65326C5DB01 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | \REGISTRY\A\{919c907a-b14a-1c2d-b076-c1402ff6e70c}\LocalState\AppIndexer |
| Operation: | write | Name: | InstalledWin32AppsRevision |
Value: 7B00420035003500370031004200310030002D0030003400350030002D0034004400340046002D0038004600370043002D004600360036004200360043004500370045004300450039007D000000E5A3A65326C5DB01 | |||
| (PID) Process: | (7188) npcap-1.82.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\NpcapInst |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\Npcap\uninstall.exe" | |||
Executable files
32
Suspicious files
65
Text files
195
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7188 | npcap-1.82.exe | C:\Users\admin\AppData\Local\Temp\nsfB75D.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
| 7188 | npcap-1.82.exe | C:\Program Files\Npcap\FixInstall.bat | text | |
MD5:3DCB581D39D9349A906368B77A4CEDFA | SHA256:C6158E40BDFD88E892EE6C4DA3A16A037EDF2CC77DC008CBD8FBEB44C643DDDA | |||
| 7188 | npcap-1.82.exe | C:\Program Files\Npcap\Uninstall.exe | executable | |
MD5:34BC2AFC9E120B714BA33D9CCAE4486D | SHA256:F96955290B60B5DD8F638881569EB4C10E92875EC411CE442AA87684C11A52BC | |||
| 7188 | npcap-1.82.exe | C:\Windows\SysWOW64\WlanHelper.exe | executable | |
MD5:ED825ED561CD25E337089B54AE14A7FC | SHA256:46C7FACF22C7CCF283C567DEA7EA7C788EC04BB7657F6785F45F700E5AD1B275 | |||
| 7680 | NPFInstall.exe | C:\Program Files\Npcap\NPFInstall.log | text | |
MD5:ECAA88F7FA0BF610A5A26CF545DCD3AA | SHA256:F1945CD6C19E56B3C1C78943EF5EC18116907A4CA1EFC40A57D48AB1DB7ADFC5 | |||
| 7188 | npcap-1.82.exe | C:\Windows\SysWOW64\NpcapHelper.exe | executable | |
MD5:47258C996A2204CEC8CCD707CC224A82 | SHA256:BEA8C0296AAF6A4C52E4DDDFDF20391FA20F3960A6FD31E3CC0AC7ADE587815A | |||
| 7188 | npcap-1.82.exe | C:\Windows\SysWOW64\wpcap.dll | executable | |
MD5:1ED9759377A8793E61AF36871AD3A427 | SHA256:7CE11E1FA06E3EF9F17372CFCBAD908AE3D8D75C8FB1C1FEAB53E827ECA6E301 | |||
| 7188 | npcap-1.82.exe | C:\Windows\SysWOW64\Packet.dll | executable | |
MD5:63D360B2D8C212086FAF4A8DA206AD2C | SHA256:4CA13DD9D582BCDB16A268FDA7C3940E85CB32E39357F98177BD578CC6D9953D | |||
| 7188 | npcap-1.82.exe | C:\Users\admin\AppData\Local\Temp\nsfB75D.tmp\InstallOptions.dll | executable | |
MD5:D1EEFB07ABC2577DFB92EB2E95A975E4 | SHA256:89DD7D646278D8BFC41D5446BDC348B9A9AFAA832ABF02C1396272BB7AC7262A | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{0cc104f4-2f61-4e3f-8b4d-7d35f06e8287}\0.1.filtertrie.intermediate.txt | text | |
MD5:34BD1DFB9F72CF4F86E6DF6DA0A9E49A | SHA256:8E1E6A3D56796A245D0C7B0849548932FEE803BBDB03F6E289495830E017F14C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4464 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4464 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4464 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |