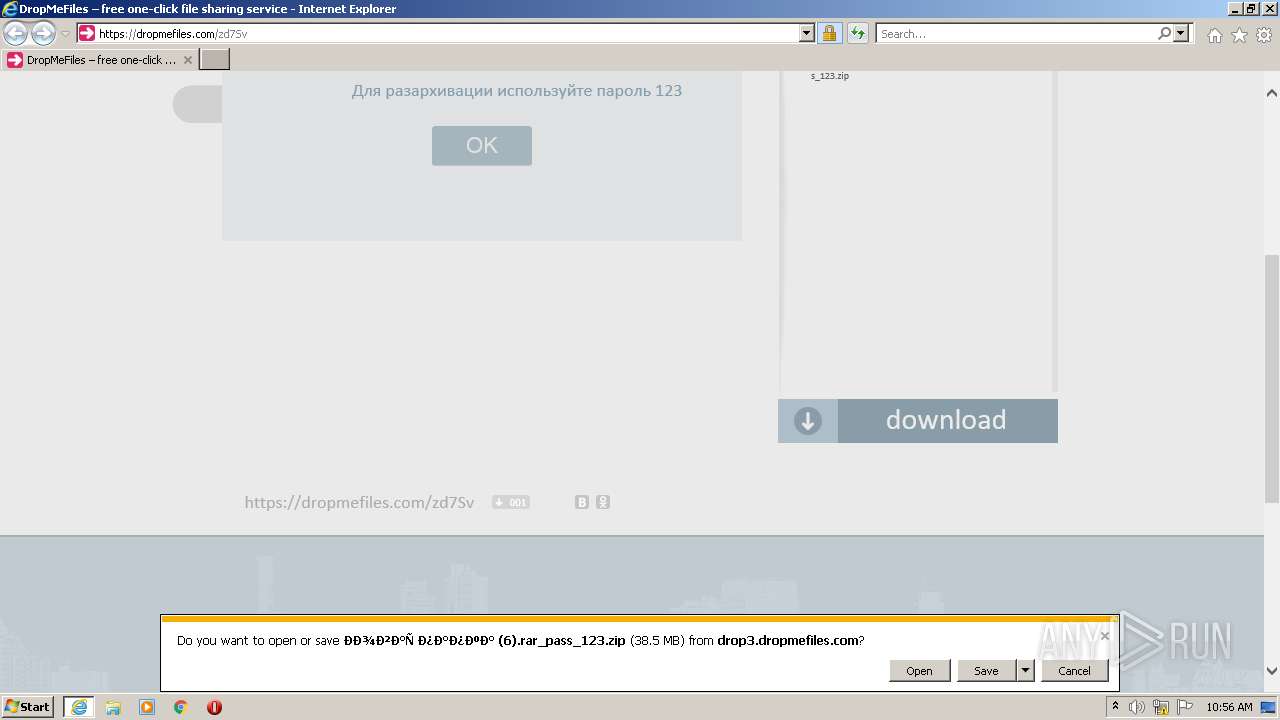
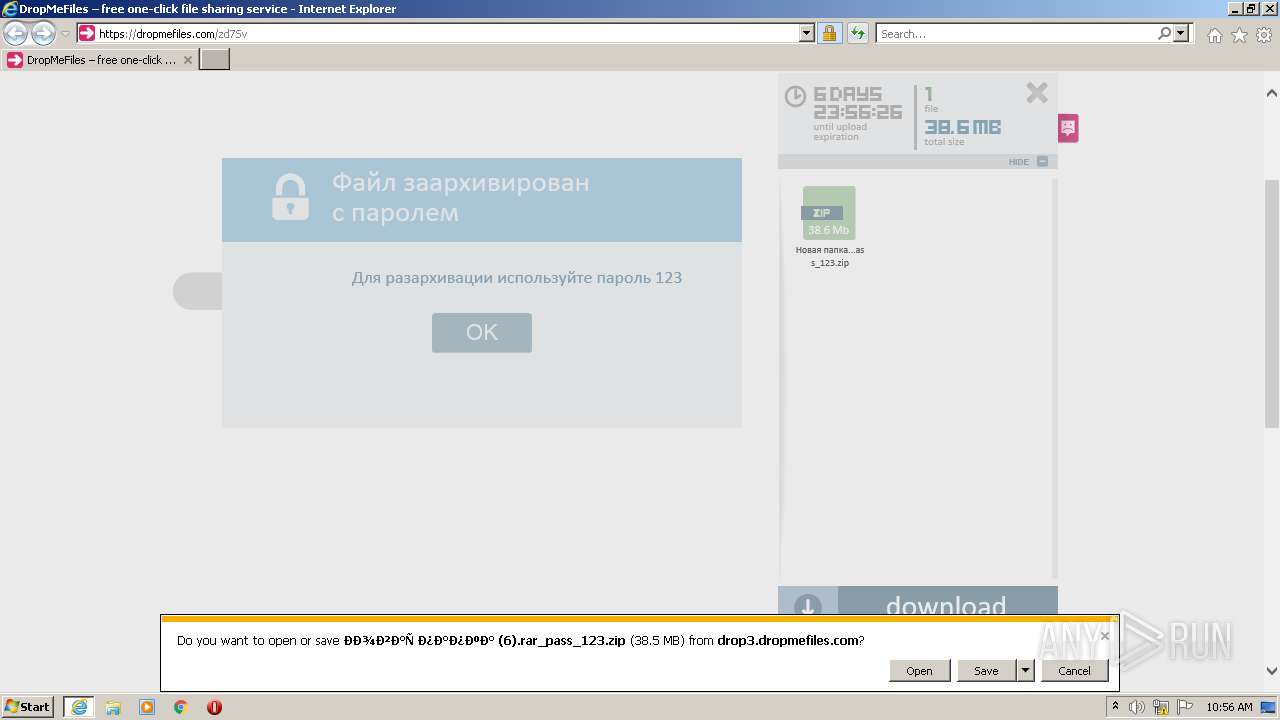
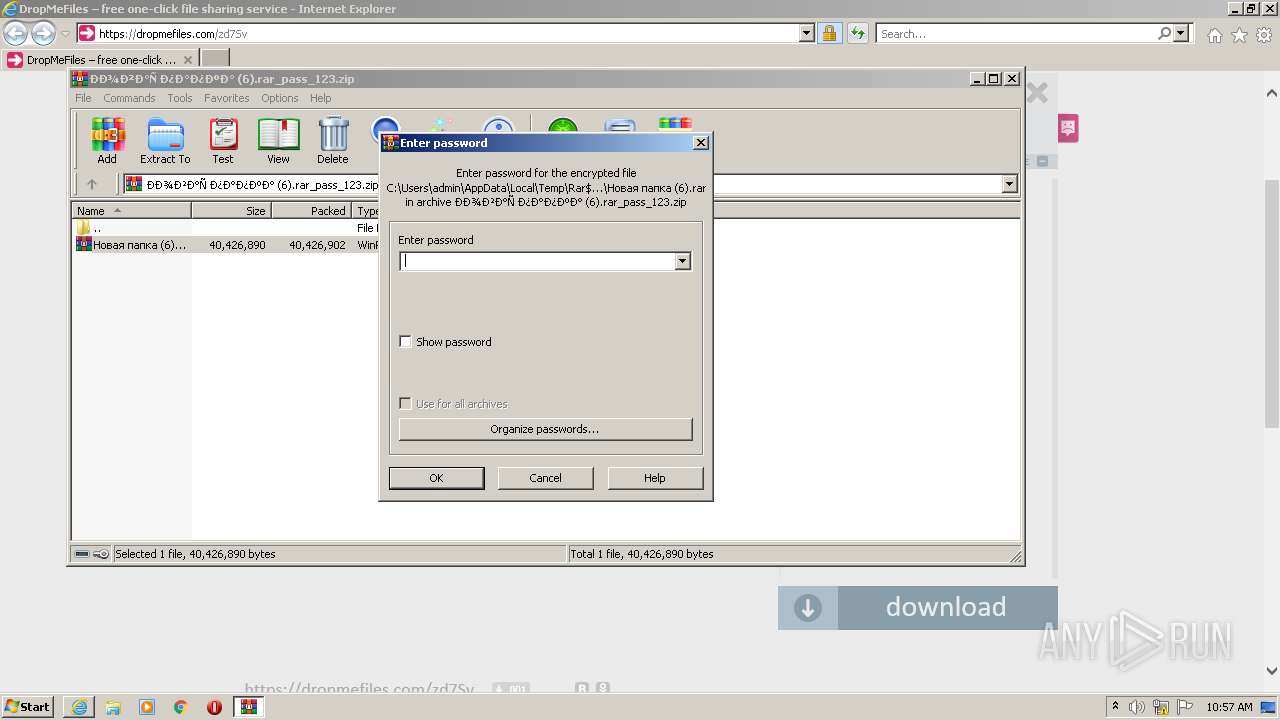
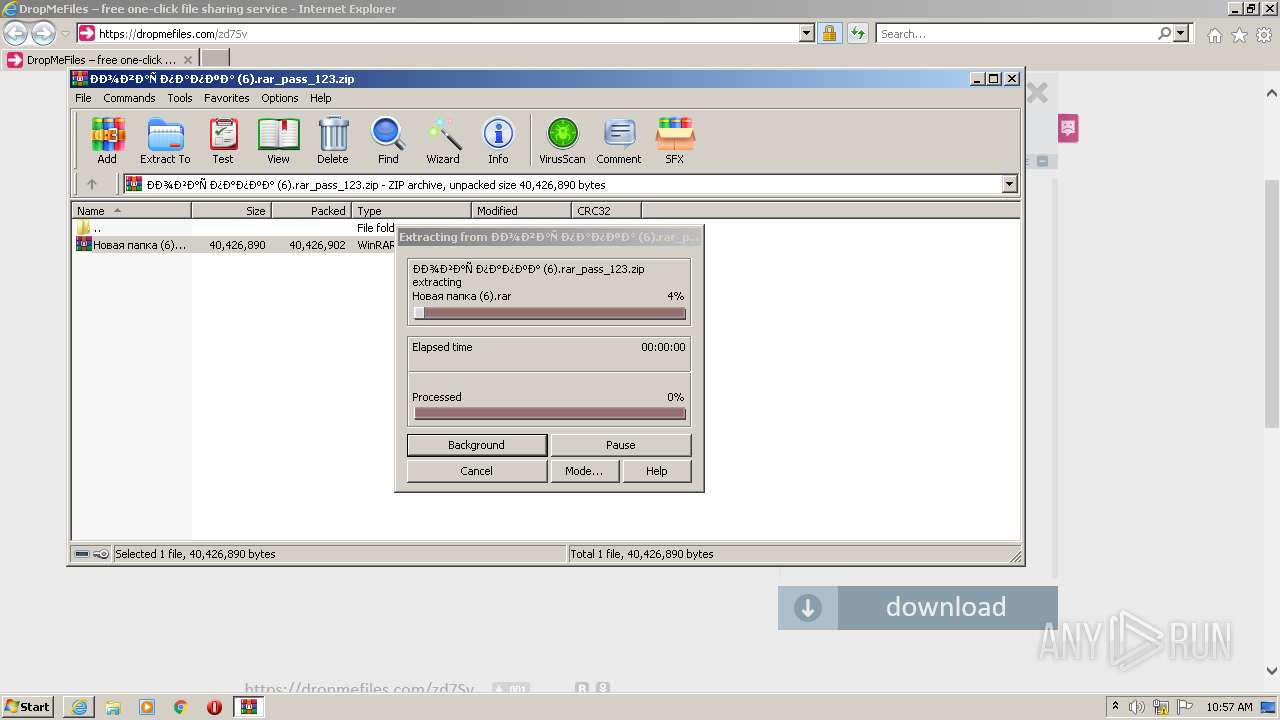
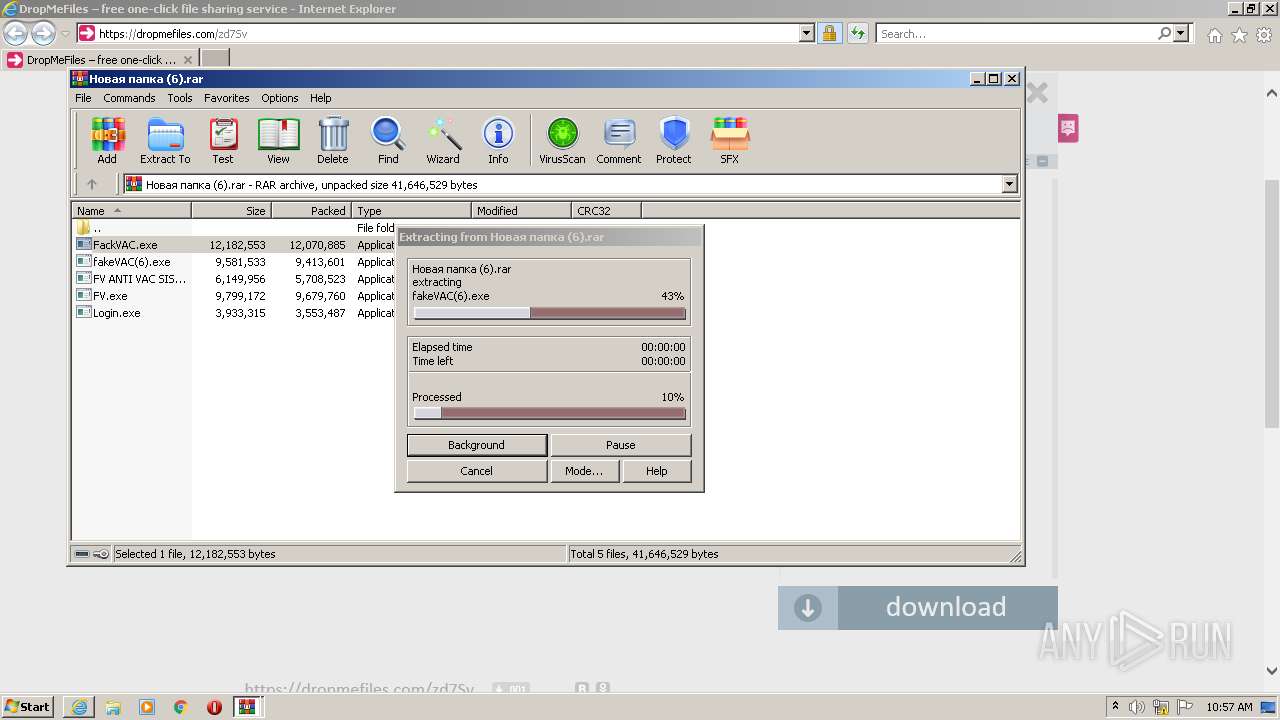
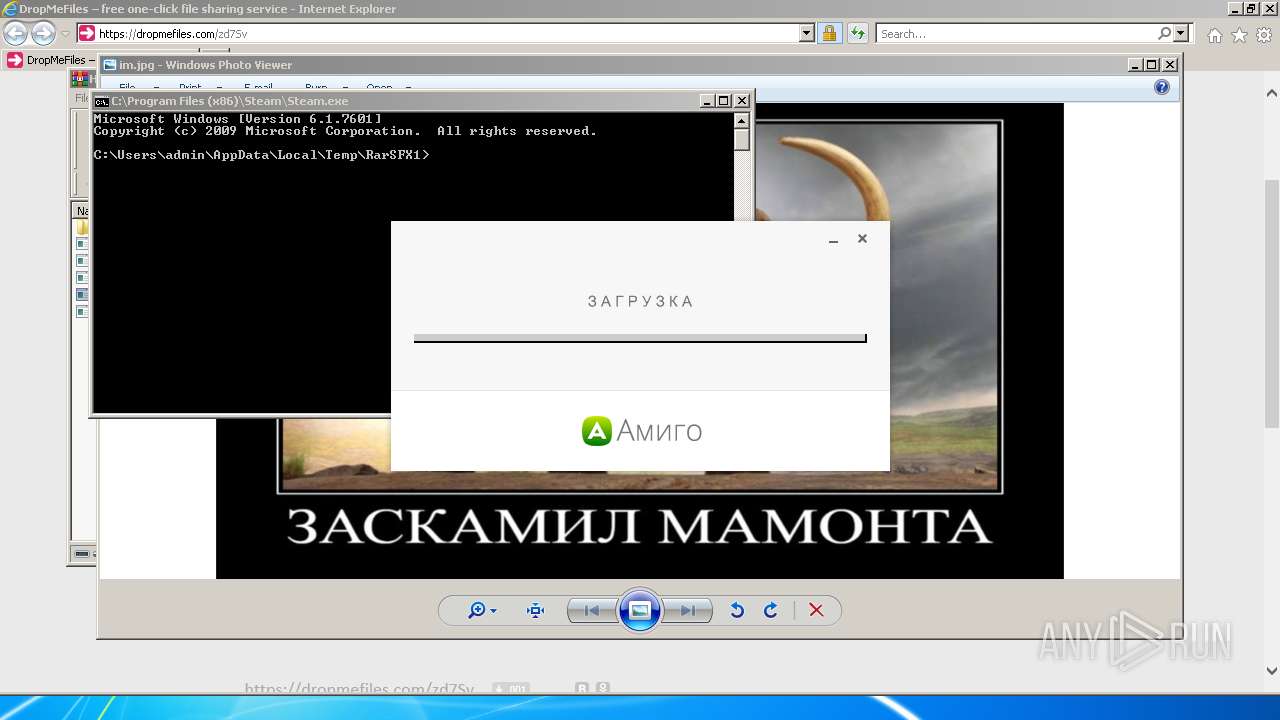
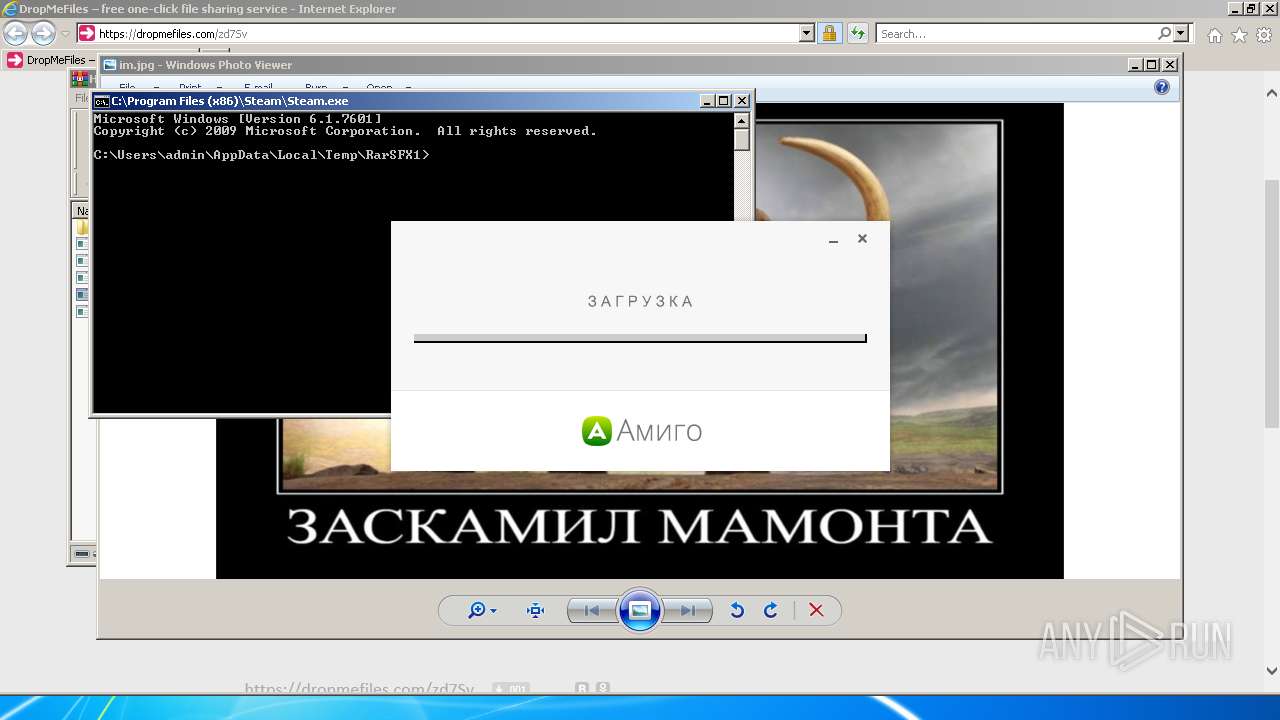
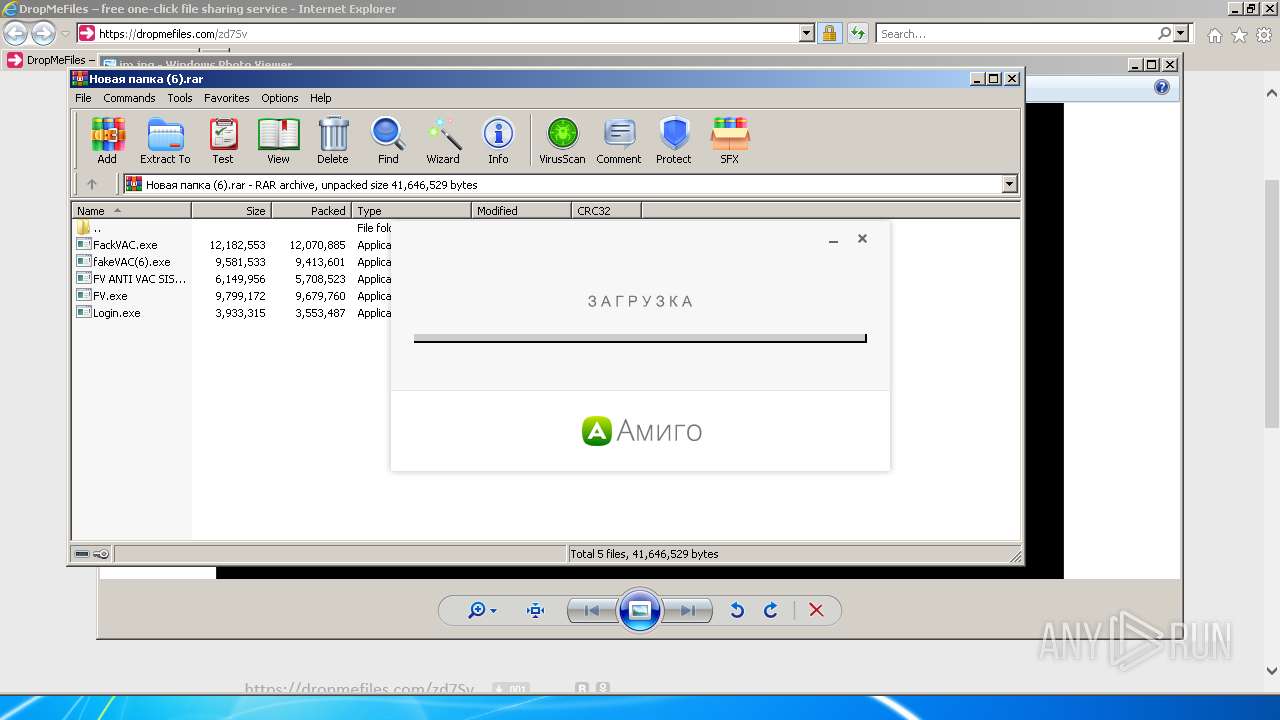
| URL: | https://dropmefiles.com/zd7Sv |
| Full analysis: | https://app.any.run/tasks/d48648ce-5d0d-4d0a-b201-c5d6e59bbbc2 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2022, 09:55:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | DBDE2303C742EBB194654327460CE999 |
| SHA1: | FBA0B30D75D82A8C7DCF182EC8AC0221C65B85D0 |
| SHA256: | DD67589EA0EC2FD83FF2B17D15FF95295F67E470F99BDE27465E7C4FE9C6E744 |
| SSDEEP: | 3:N8PKV9DNEb:2oDN8 |
MALICIOUS
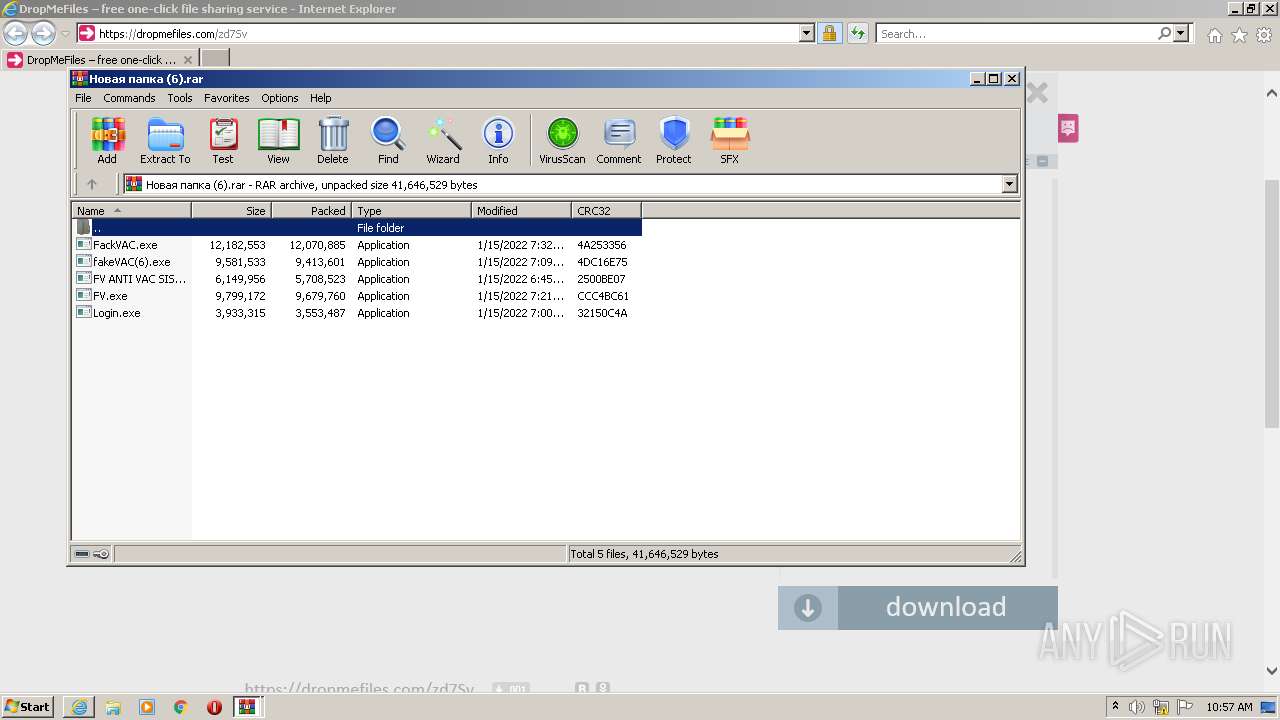
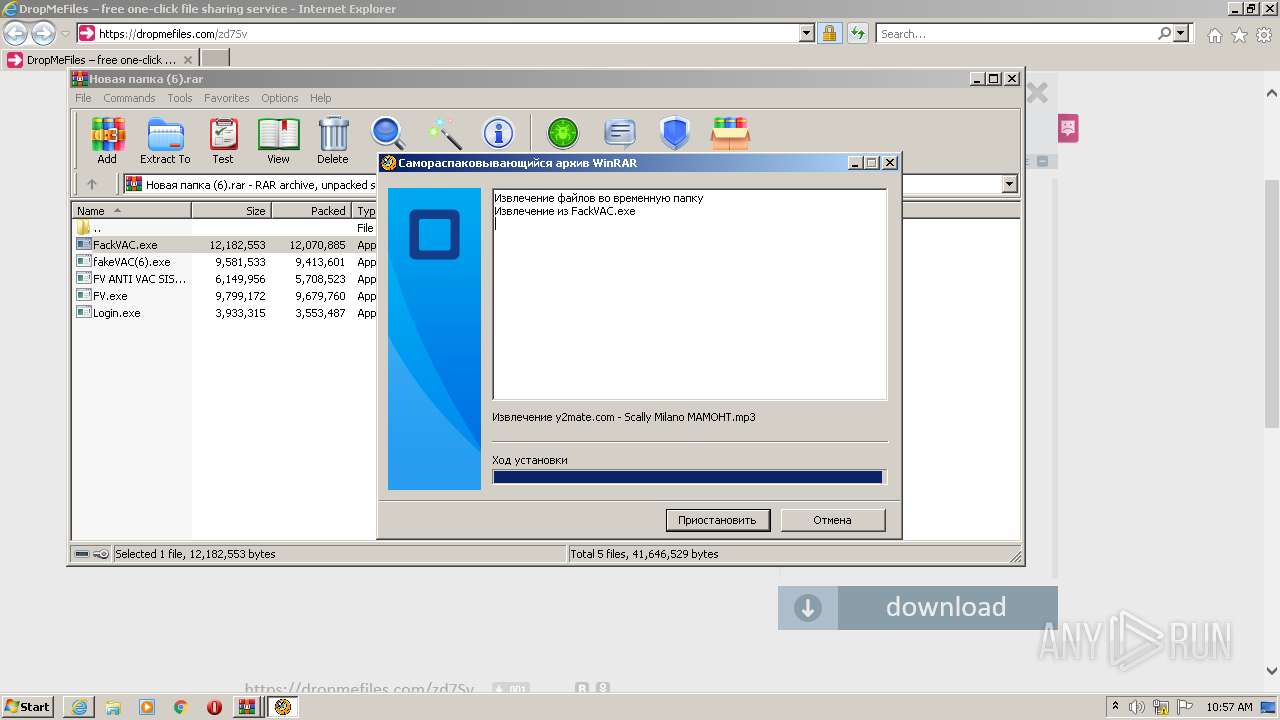
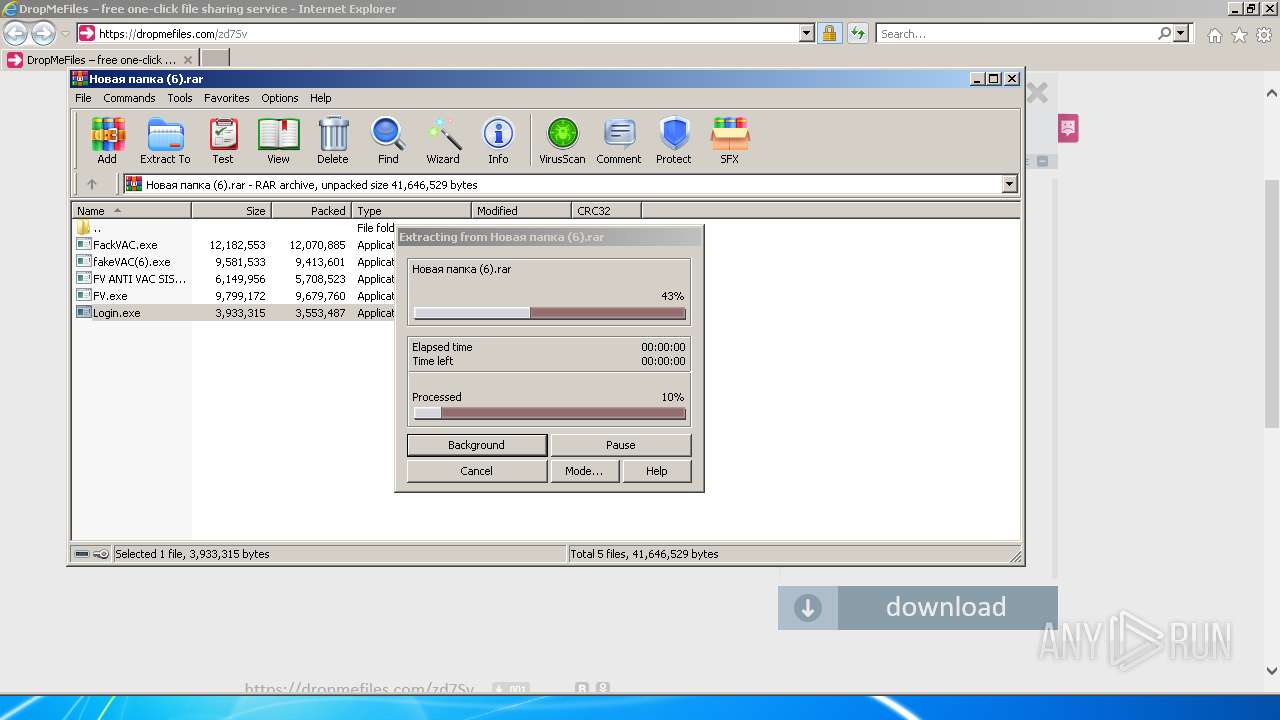
Drops executable file immediately after starts
- WinRAR.exe (PID: 2456)
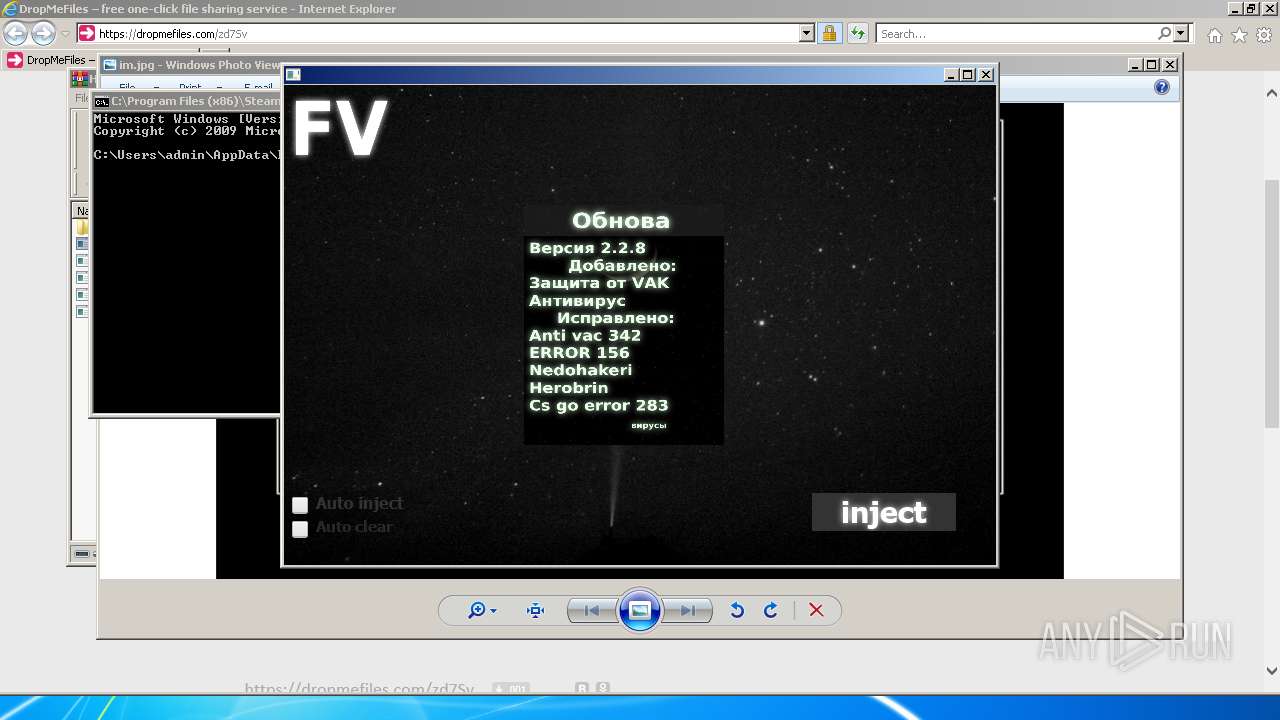
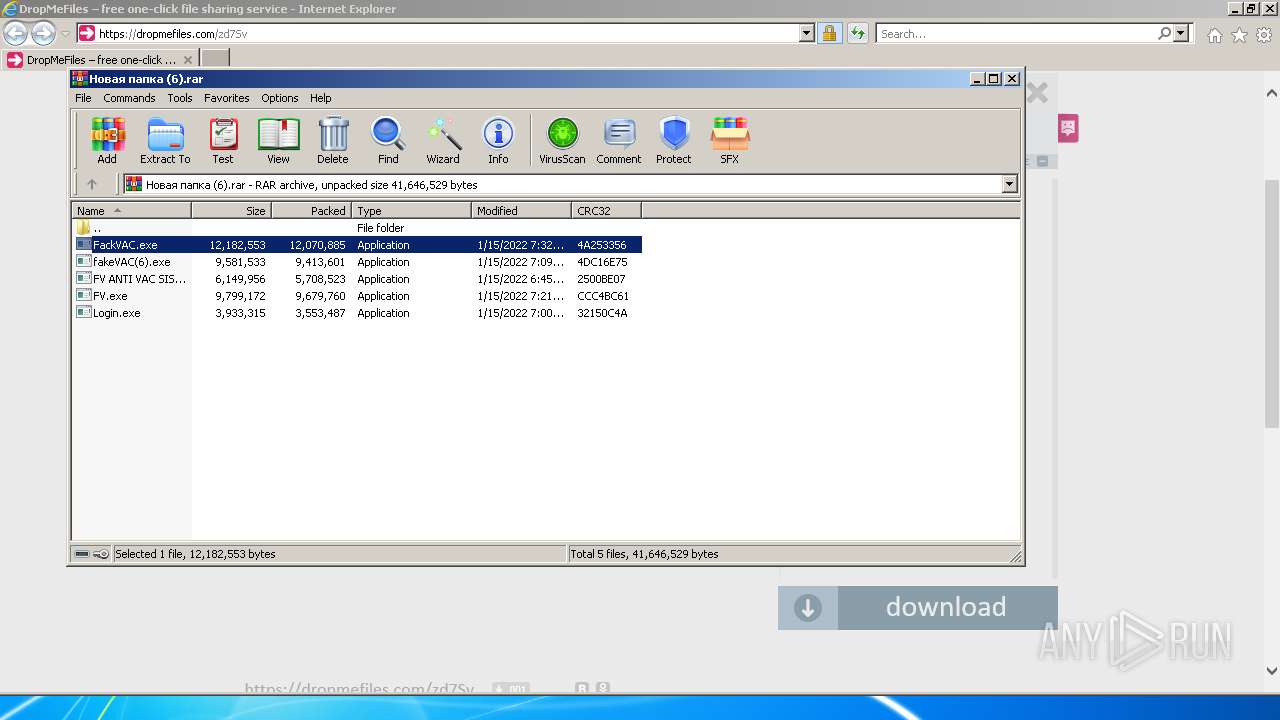
- FackVAC.exe (PID: 3484)
- FV.exe (PID: 588)
- fakeVAC(6).exe (PID: 1332)
- amigo_setup.exe (PID: 3944)
- FV.exe (PID: 124)
- fakeVAC(6).exe (PID: 3804)
Application was dropped or rewritten from another process
- FackVAC.exe (PID: 3484)
- FV.exe (PID: 588)
- fakeVAC(6).exe (PID: 1332)
- FV ANTI VAC SISTEM.exe (PID: 2100)
- Login.exe (PID: 3792)
- Login.exe (PID: 3640)
- amigo_setup.exe (PID: 3944)
- amigo_setup.exe (PID: 3788)
- FV.exe (PID: 124)
- fakeVAC(6).exe (PID: 3804)
- FV ANTI VAC SISTEM.exe (PID: 2564)
- Login.exe (PID: 2092)
- FV ANTI VAC SISTEM.exe (PID: 3352)
Runs app for hidden code execution
- cmd.exe (PID: 1884)
- cmd.exe (PID: 3632)
Connects to CnC server
- amigo_setup.exe (PID: 3788)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3328)
Executed via COM
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3240)
- DllHost.exe (PID: 3460)
- DllHost.exe (PID: 2044)
Checks supported languages
- WinRAR.exe (PID: 3364)
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3240)
- WinRAR.exe (PID: 2456)
- FV.exe (PID: 588)
- FackVAC.exe (PID: 3484)
- cmd.exe (PID: 1884)
- fakeVAC(6).exe (PID: 1332)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 3384)
- FV ANTI VAC SISTEM.exe (PID: 2100)
- Login.exe (PID: 3792)
- javaw.exe (PID: 2332)
- javaw.exe (PID: 2356)
- Login.exe (PID: 3640)
- javaw.exe (PID: 3004)
- amigo_setup.exe (PID: 3944)
- amigo_setup.exe (PID: 3788)
- FV.exe (PID: 124)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 3872)
- cmd.exe (PID: 1828)
- FV ANTI VAC SISTEM.exe (PID: 2564)
- javaw.exe (PID: 3916)
- Login.exe (PID: 2092)
- fakeVAC(6).exe (PID: 3804)
- javaw.exe (PID: 3488)
- FV ANTI VAC SISTEM.exe (PID: 3352)
- javaw.exe (PID: 3596)
Reads the computer name
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3240)
- WinRAR.exe (PID: 3364)
- WinRAR.exe (PID: 2456)
- FackVAC.exe (PID: 3484)
- FV.exe (PID: 588)
- fakeVAC(6).exe (PID: 1332)
- javaw.exe (PID: 2356)
- javaw.exe (PID: 2332)
- javaw.exe (PID: 3004)
- amigo_setup.exe (PID: 3788)
- FV.exe (PID: 124)
- fakeVAC(6).exe (PID: 3804)
- javaw.exe (PID: 3916)
- javaw.exe (PID: 3596)
- javaw.exe (PID: 3488)
Creates files in the user directory
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3240)
- javaw.exe (PID: 2356)
- javaw.exe (PID: 3004)
- javaw.exe (PID: 3596)
Application launched itself
- WinRAR.exe (PID: 3364)
- cmd.exe (PID: 1884)
- cmd.exe (PID: 3632)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2456)
- FackVAC.exe (PID: 3484)
- FV.exe (PID: 588)
- fakeVAC(6).exe (PID: 1332)
- amigo_setup.exe (PID: 3944)
- FV.exe (PID: 124)
- fakeVAC(6).exe (PID: 3804)
Executable content was dropped or overwritten
- FackVAC.exe (PID: 3484)
- WinRAR.exe (PID: 2456)
- FV.exe (PID: 588)
- fakeVAC(6).exe (PID: 1332)
- amigo_setup.exe (PID: 3944)
- FV.exe (PID: 124)
- fakeVAC(6).exe (PID: 3804)
Starts itself from another location
- FackVAC.exe (PID: 3484)
- FV.exe (PID: 588)
- amigo_setup.exe (PID: 3944)
- FV.exe (PID: 124)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 1884)
- cmd.exe (PID: 3632)
Starts CMD.EXE for commands execution
- FV.exe (PID: 588)
- cmd.exe (PID: 1884)
- fakeVAC(6).exe (PID: 1332)
- FV.exe (PID: 124)
- cmd.exe (PID: 3632)
- fakeVAC(6).exe (PID: 3804)
Changes the desktop background image
- reg.exe (PID: 3692)
- reg.exe (PID: 3104)
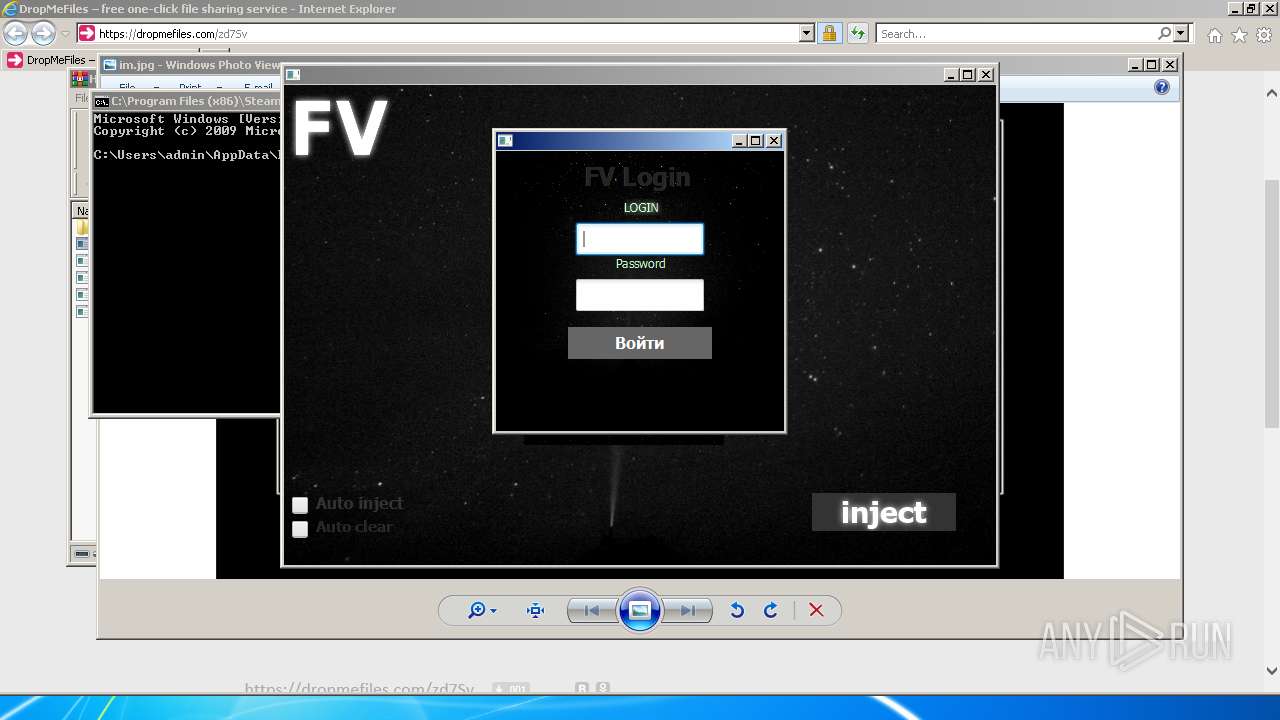
Executes JAVA applets
- FV ANTI VAC SISTEM.exe (PID: 2100)
- Login.exe (PID: 3792)
- Login.exe (PID: 3640)
- FV ANTI VAC SISTEM.exe (PID: 2564)
- Login.exe (PID: 2092)
- FV ANTI VAC SISTEM.exe (PID: 3352)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3384)
- cmd.exe (PID: 1828)
Check for Java to be installed
- FV ANTI VAC SISTEM.exe (PID: 2100)
- Login.exe (PID: 3792)
- Login.exe (PID: 3640)
- FV ANTI VAC SISTEM.exe (PID: 2564)
- Login.exe (PID: 2092)
- FV ANTI VAC SISTEM.exe (PID: 3352)
Creates files in the program directory
- javaw.exe (PID: 2332)
Uses ICACLS.EXE to modify access control list
- javaw.exe (PID: 2332)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2848)
Checks supported languages
- iexplore.exe (PID: 2848)
- iexplore.exe (PID: 3328)
- DllHost.exe (PID: 3460)
- reg.exe (PID: 3692)
- taskkill.exe (PID: 2124)
- icacls.exe (PID: 3300)
- DllHost.exe (PID: 2044)
- reg.exe (PID: 3104)
- taskkill.exe (PID: 2168)
Application launched itself
- iexplore.exe (PID: 2848)
Reads the computer name
- iexplore.exe (PID: 3328)
- iexplore.exe (PID: 2848)
- DllHost.exe (PID: 3460)
- taskkill.exe (PID: 2124)
- icacls.exe (PID: 3300)
- DllHost.exe (PID: 2044)
- taskkill.exe (PID: 2168)
Reads internet explorer settings
- iexplore.exe (PID: 3328)
Checks Windows Trust Settings
- iexplore.exe (PID: 2848)
- iexplore.exe (PID: 3328)
Reads settings of System Certificates
- iexplore.exe (PID: 2848)
- iexplore.exe (PID: 3328)
Reads CPU info
- iexplore.exe (PID: 3328)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2848)
Creates files in the user directory
- iexplore.exe (PID: 3328)
- iexplore.exe (PID: 2848)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2848)
Changes settings of System certificates
- iexplore.exe (PID: 2848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
81
Monitored processes
37
Malicious processes
12
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.22016\FV.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.22016\FV.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 588 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\FV.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\FV.exe | FackVAC.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1332 | "C:\Users\admin\AppData\Local\Temp\RarSFX1\fakeVAC(6).exe" | C:\Users\admin\AppData\Local\Temp\RarSFX1\fakeVAC(6).exe | FV.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1828 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX3\Bat.bat" " | C:\Windows\system32\cmd.exe | — | fakeVAC(6).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1884 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX1\Новый текстовый документ.bat" " | C:\Windows\system32\cmd.exe | — | FV.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2044 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2092 | "C:\Users\admin\AppData\Local\Temp\RarSFX3\Login.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX3\Login.exe | — | fakeVAC(6).exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2100 | "C:\Users\admin\AppData\Local\Temp\RarSFX2\FV ANTI VAC SISTEM.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX2\FV ANTI VAC SISTEM.exe | — | fakeVAC(6).exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2124 | taskkill -f -im explorer.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2168 | taskkill -f -im explorer.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
26 942
Read events
26 624
Write events
314
Delete events
4
Modification events
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960888 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 189243856 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960889 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2848) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
29
Suspicious files
26
Text files
115
Unknown types
51
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3328 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_86C2A03C133240EC4C95180B9FD368BB | binary | |
MD5:— | SHA256:— | |||
| 2848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3328 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\709A8EC0F6D3194AD001E9041914421F_1393D43F33EA5DF544C48FF754B269CF | der | |
MD5:— | SHA256:— | |||
| 3328 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_86C2A03C133240EC4C95180B9FD368BB | der | |
MD5:— | SHA256:— | |||
| 2848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 3328 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\zd7Sv[1].htm | html | |
MD5:— | SHA256:— | |||
| 3328 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\709A8EC0F6D3194AD001E9041914421F_1393D43F33EA5DF544C48FF754B269CF | binary | |
MD5:— | SHA256:— | |||
| 2848 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2848 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
120
DNS requests
40
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3328 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3328 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDwQ9JNOs3IcArkp%2FBu7NbU | US | der | 472 b | whitelisted |
3328 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAeYNgOt45kIIZygDCe8imw%3D | US | der | 471 b | whitelisted |
3328 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCdUrA%2FwvrytArhIvu6cF3d | US | der | 472 b | whitelisted |
2848 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3328 | iexplore.exe | GET | 200 | 104.126.37.35:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR5iK7tYk9tqQEoeQhZNkKcAol9bgQUjEPEy22YwaechGnr30oNYJY6w%2FsCEQCTkoVAAWVxX5R%2FKI%2FvyZso | US | der | 1.50 Kb | whitelisted |
3328 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR0tOcjGcdlkhVARHvHzj6Qwhh26wQUpI3lvnx55HAjbS4pNK0jWNz1MX8CEAjbH%2FOwnxbSbrWoFy7IWuU%3D | US | der | 471 b | whitelisted |
3328 | iexplore.exe | GET | 200 | 5.45.205.241:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEGlTKIPuh018TJJ9M3J8QXw%3D | RU | der | 1.48 Kb | whitelisted |
3328 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3328 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDExSUZ712qmxLhqE9UUaDV | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2848 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3328 | iexplore.exe | 176.99.128.18:443 | dropmefiles.com | Inetcom LLC | RU | suspicious |
2848 | iexplore.exe | 67.27.157.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
2848 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3328 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3328 | iexplore.exe | 176.99.128.38:443 | dropmefiles.com | Inetcom LLC | RU | suspicious |
3328 | iexplore.exe | 142.250.186.106:443 | imasdk.googleapis.com | Google Inc. | US | whitelisted |
3328 | iexplore.exe | 172.217.23.98:443 | www.googletagservices.com | Google Inc. | US | whitelisted |
3328 | iexplore.exe | 142.250.184.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3328 | iexplore.exe | 172.217.18.110:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dropmefiles.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
imasdk.googleapis.com |
| whitelisted |
www.googletagservices.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.google-analytics.com |
| whitelisted |
mc.yandex.ru |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3788 | amigo_setup.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
5 ETPRO signatures available at the full report