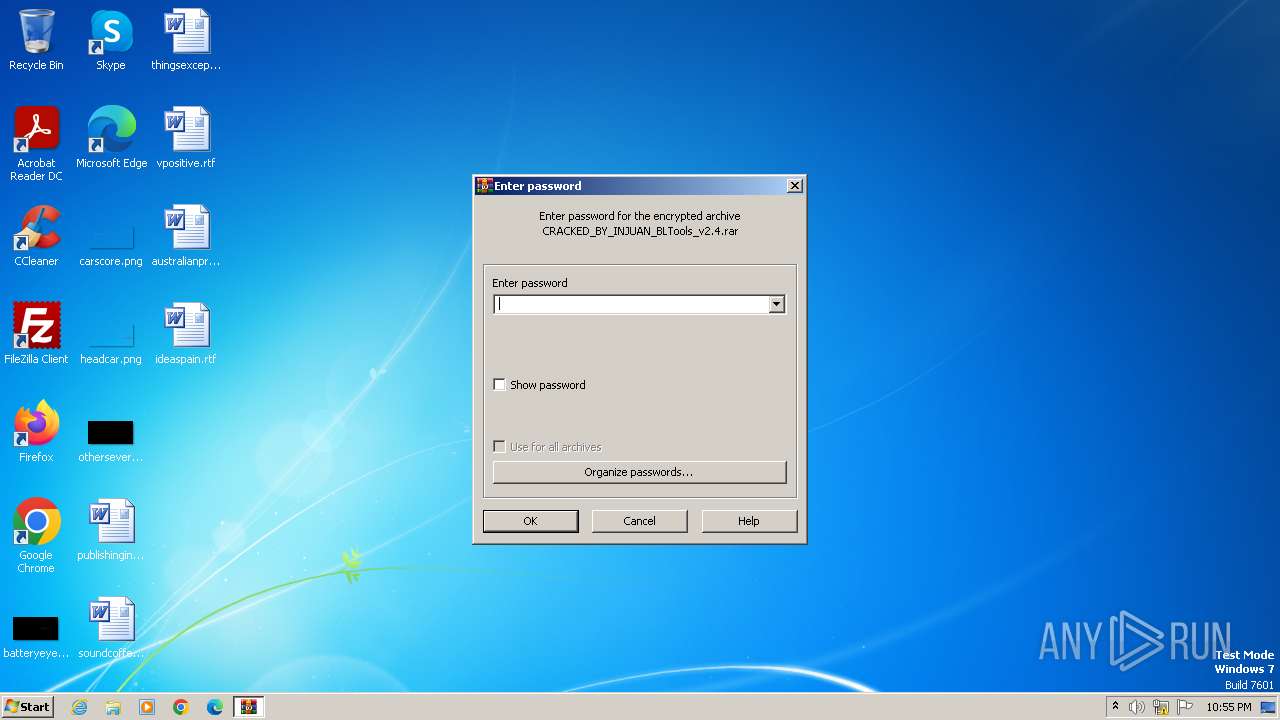
| download: | /software23577/11344556/downloads/CRACKED_BY_INJUAN_BLTools_v2.4.rar |
| Full analysis: | https://app.any.run/tasks/ef67b02b-3a80-41c6-9dc6-75846e1f3e33 |
| Verdict: | Malicious activity |
| Analysis date: | November 11, 2023, 22:55:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 452D856BC0865B6A5E1A1D56FC67B04A |
| SHA1: | F708F2C06EF54C6D30C279985C19908F8FE051EA |
| SHA256: | DD65F16472F795E637165587E1FE535ED13291FA0CA0568F97292209BF9E9585 |
| SSDEEP: | 98304:1dMmUiyTjMxezA6E+4YIAgGPE7nBAaDY0eKf1n/U3gBiTza3YuO9GOtj5GFjDLYx:TjI7 |
MALICIOUS
Adds path to the Windows Defender exclusion list
- LZMYBCTLTD.exe (PID: 1760)
- BLTools v2.4.exe (PID: 3964)
- LZMYBCTLTD.exe (PID: 1904)
- LZMYBCTLTD.exe (PID: 2736)
Uses Task Scheduler to run other applications
- LZMYBCTLTD.exe (PID: 1760)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3416)
Reads the BIOS version
- BLTools v2.4.exe (PID: 3408)
- BLTools v2.4.exe (PID: 3964)
- LZMYBCTLTD.exe (PID: 1760)
- LZMYBCTLTD.exe (PID: 1904)
- LZMYBCTLTD.exe (PID: 2736)
Reads the Internet Settings
- BLTools v2.4.exe (PID: 3408)
- LZMYBCTLTD.exe (PID: 1760)
- LZMYBCTLTD.exe (PID: 1904)
- LZMYBCTLTD.exe (PID: 2736)
- BLTools v2.4.exe (PID: 3964)
Starts POWERSHELL.EXE for commands execution
- BLTools v2.4.exe (PID: 3964)
- LZMYBCTLTD.exe (PID: 1760)
- LZMYBCTLTD.exe (PID: 1904)
- LZMYBCTLTD.exe (PID: 2736)
Application launched itself
- BLTools v2.4.exe (PID: 3408)
Script adds exclusion path to Windows Defender
- BLTools v2.4.exe (PID: 3964)
- LZMYBCTLTD.exe (PID: 1904)
- LZMYBCTLTD.exe (PID: 1760)
- LZMYBCTLTD.exe (PID: 2736)
Starts CMD.EXE for commands execution
- BLTools v2.4.exe (PID: 3964)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 756)
Powershell version downgrade attack
- powershell.exe (PID: 4060)
- powershell.exe (PID: 4052)
- powershell.exe (PID: 2300)
- powershell.exe (PID: 2332)
- powershell.exe (PID: 2056)
- powershell.exe (PID: 1352)
- powershell.exe (PID: 1848)
- powershell.exe (PID: 2788)
Executing commands from a ".bat" file
- BLTools v2.4.exe (PID: 3964)
The process executes via Task Scheduler
- LZMYBCTLTD.exe (PID: 1904)
- LZMYBCTLTD.exe (PID: 2736)
INFO
Manual execution by a user
- BLTools v2.4.exe (PID: 3408)
Reads the computer name
- BLTools v2.4.exe (PID: 3408)
- BLTools v2.4.exe (PID: 3964)
- LZMYBCTLTD.exe (PID: 1760)
- LZMYBCTLTD.exe (PID: 1904)
- LZMYBCTLTD.exe (PID: 2736)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3416)
Checks supported languages
- BLTools v2.4.exe (PID: 3408)
- BLTools v2.4.exe (PID: 3964)
- LZMYBCTLTD.exe (PID: 1760)
- LZMYBCTLTD.exe (PID: 2736)
- LZMYBCTLTD.exe (PID: 1904)
Process checks are UAC notifies on
- BLTools v2.4.exe (PID: 3964)
- LZMYBCTLTD.exe (PID: 1760)
- LZMYBCTLTD.exe (PID: 1904)
- LZMYBCTLTD.exe (PID: 2736)
Create files in a temporary directory
- BLTools v2.4.exe (PID: 3964)
Creates files in the program directory
- BLTools v2.4.exe (PID: 3964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
67
Monitored processes
17
Malicious processes
14
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\Windows\System32\schtasks.exe" /create /sc MINUTE /mo 1 /RL HIGHEST /tn "LZMYBCTLTD" /tr C:\ProgramData\active\LZMYBCTLTD.exe /f | C:\Windows\System32\schtasks.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 756 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\s324.0.bat" " | C:\Windows\System32\cmd.exe | — | BLTools v2.4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1352 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Roaming' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1760 | "C:\ProgramData\active\LZMYBCTLTD.exe" | C:\ProgramData\active\LZMYBCTLTD.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Logon Application Exit code: 0 Version: 10.0.17134.1 Modules
| |||||||||||||||
| 1848 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\ProgramData' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1904 | C:\ProgramData\active\LZMYBCTLTD.exe | C:\ProgramData\active\LZMYBCTLTD.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Logon Application Exit code: 0 Version: 10.0.17134.1 Modules
| |||||||||||||||
| 2056 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\ProgramData' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2060 | timeout 3 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2300 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\ProgramData' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2332 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Roaming' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | LZMYBCTLTD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
12 265
Read events
11 726
Write events
539
Delete events
0
Modification events
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
7
Suspicious files
24
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3416.31384\[CRACKED BY INJUAN] BLTools v2.4\BLTools v2.4.exe | — | |
MD5:— | SHA256:— | |||
| 3964 | BLTools v2.4.exe | C:\ProgramData\active\LZMYBCTLTD.exe | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3416.31384\[CRACKED BY INJUAN] BLTools v2.4\AlphaFS.dll | executable | |
MD5:F2F6F6798D306D6D7DF4267434B5C5F9 | SHA256:837F2CEAB6BBD9BC4BF076F1CB90B3158191888C3055DD2B78A1E23F1C3AAFDD | |||
| 3416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3416.31384\[CRACKED BY INJUAN] BLTools v2.4\System.ServiceModel.Internals.dll | executable | |
MD5:BC3DBD339745E51C60DBD0A095EB50D5 | SHA256:0BE5890DEE0DC8CCD1444781287DFEED46BBFBDBF4EE289E564EA98EA94E006D | |||
| 3416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3416.31384\[CRACKED BY INJUAN] BLTools v2.4\License.dll | text | |
MD5:B08A5C34CF0A06615DA2CA89010D8B4F | SHA256:04CC5B3B49A7E9E9B6C66C7BE59A20992BF2653746B5D43829C383FB233F88FA | |||
| 4052 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\C8T2SUX7P1U1QSMLWQOP.temp | binary | |
MD5:EA4F1F6997ED9429F7B363B55F163E87 | SHA256:D9A7DF5C82CD40803161A0FB312B27508C4A23DA8F66418F59739310F6D0310F | |||
| 4052 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:EA4F1F6997ED9429F7B363B55F163E87 | SHA256:D9A7DF5C82CD40803161A0FB312B27508C4A23DA8F66418F59739310F6D0310F | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF16e45a.TMP | binary | |
MD5:C681106A4168B935996B10134404F885 | SHA256:89AB4ECFBB5C1FD07CF99465E36B1A08F51E2512AA60DDD616D4A37753FC112D | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2SL8P6FBMLPKD1CZZUJQ.temp | binary | |
MD5:EA4F1F6997ED9429F7B363B55F163E87 | SHA256:D9A7DF5C82CD40803161A0FB312B27508C4A23DA8F66418F59739310F6D0310F | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:EA4F1F6997ED9429F7B363B55F163E87 | SHA256:D9A7DF5C82CD40803161A0FB312B27508C4A23DA8F66418F59739310F6D0310F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |