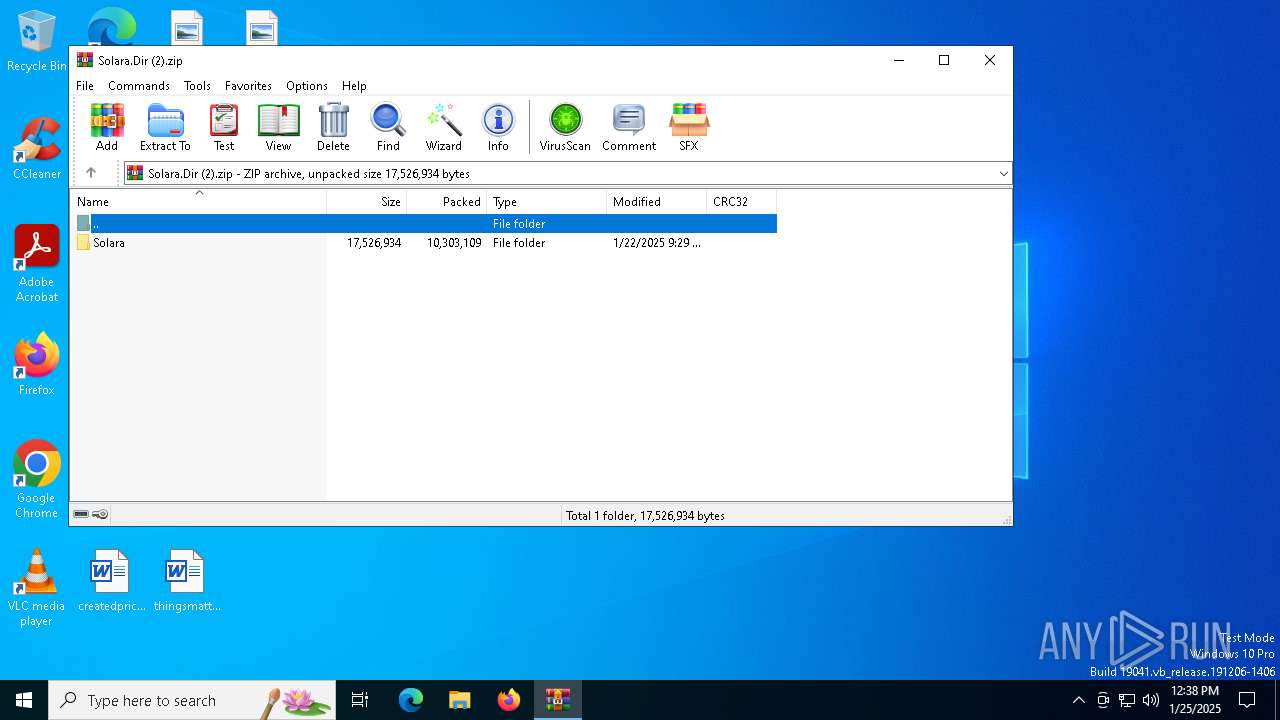
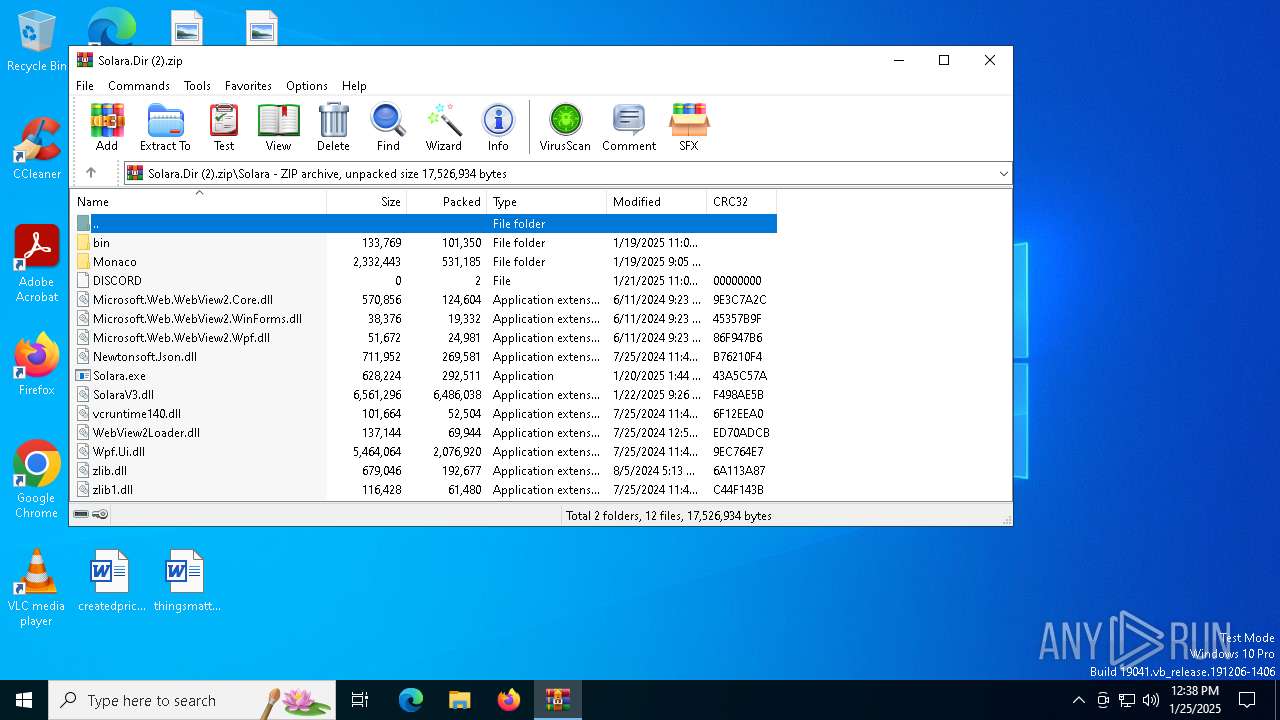
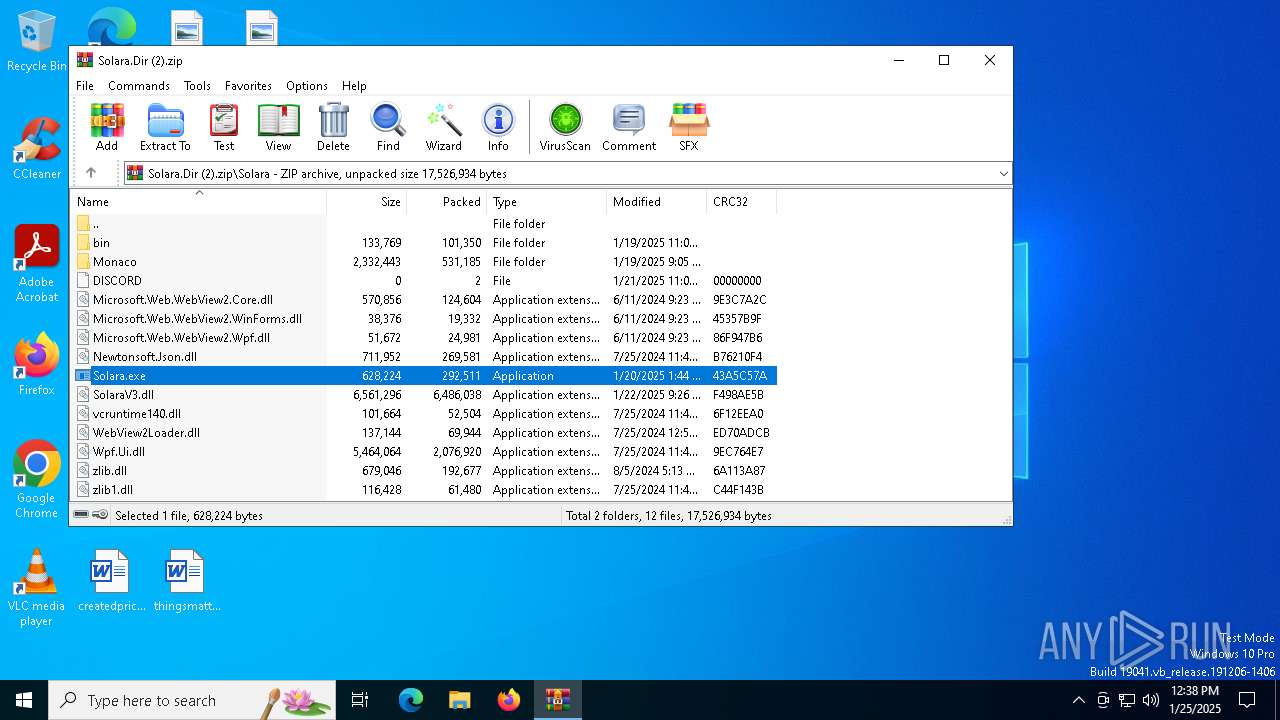
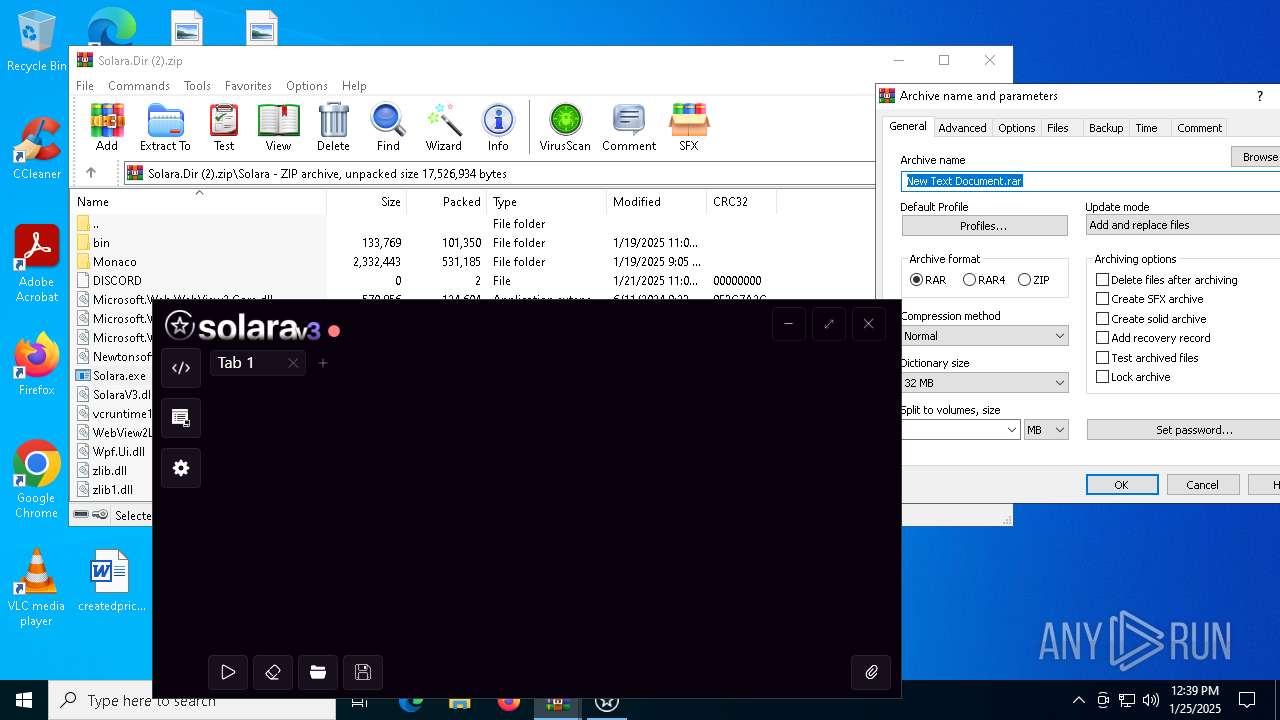
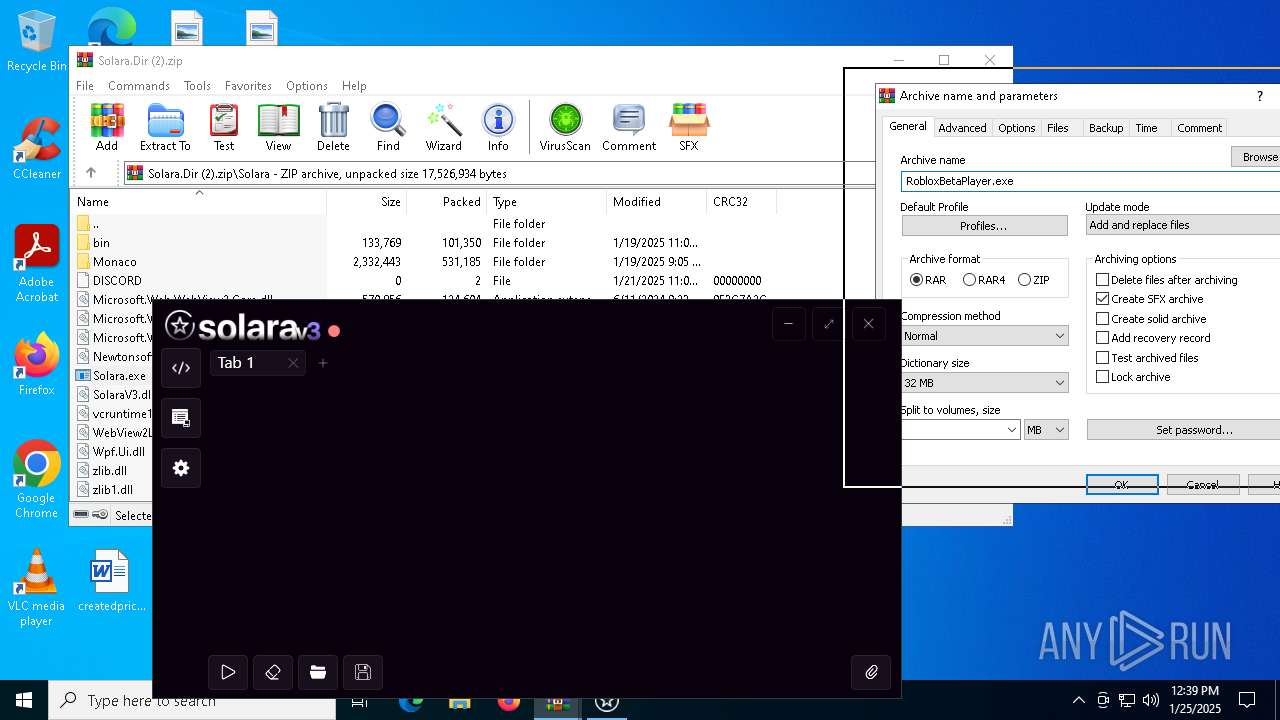
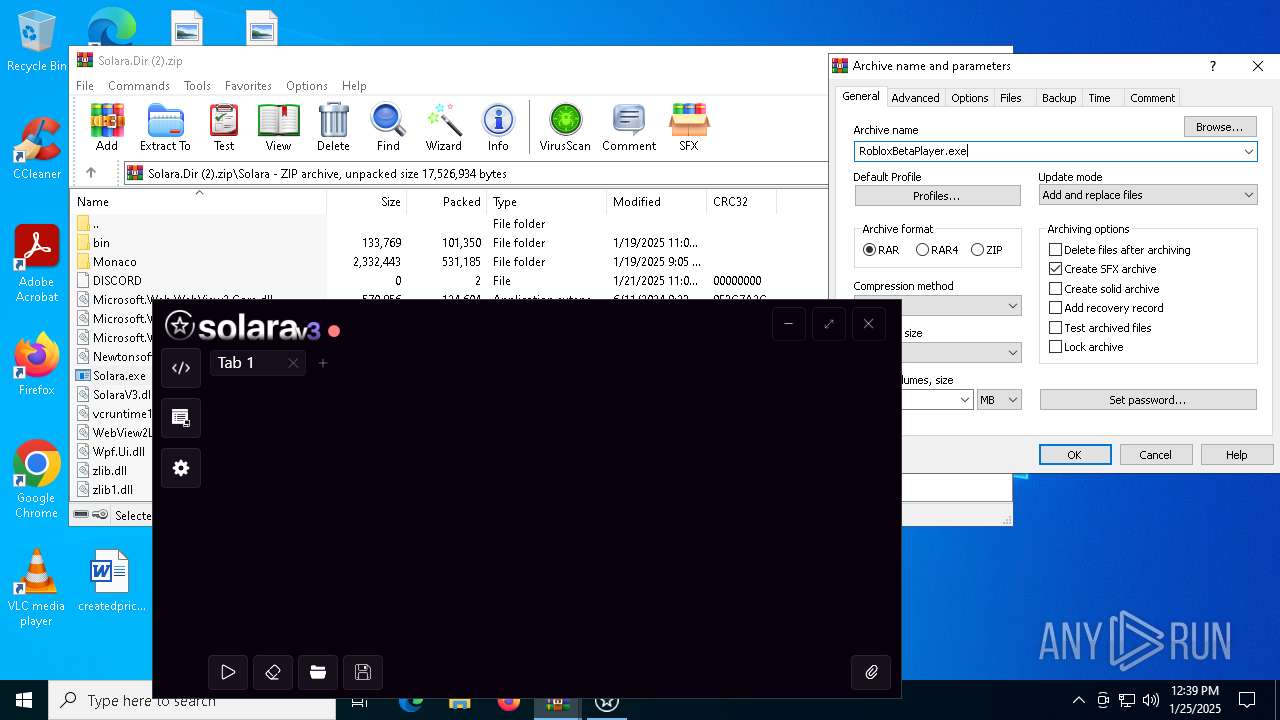
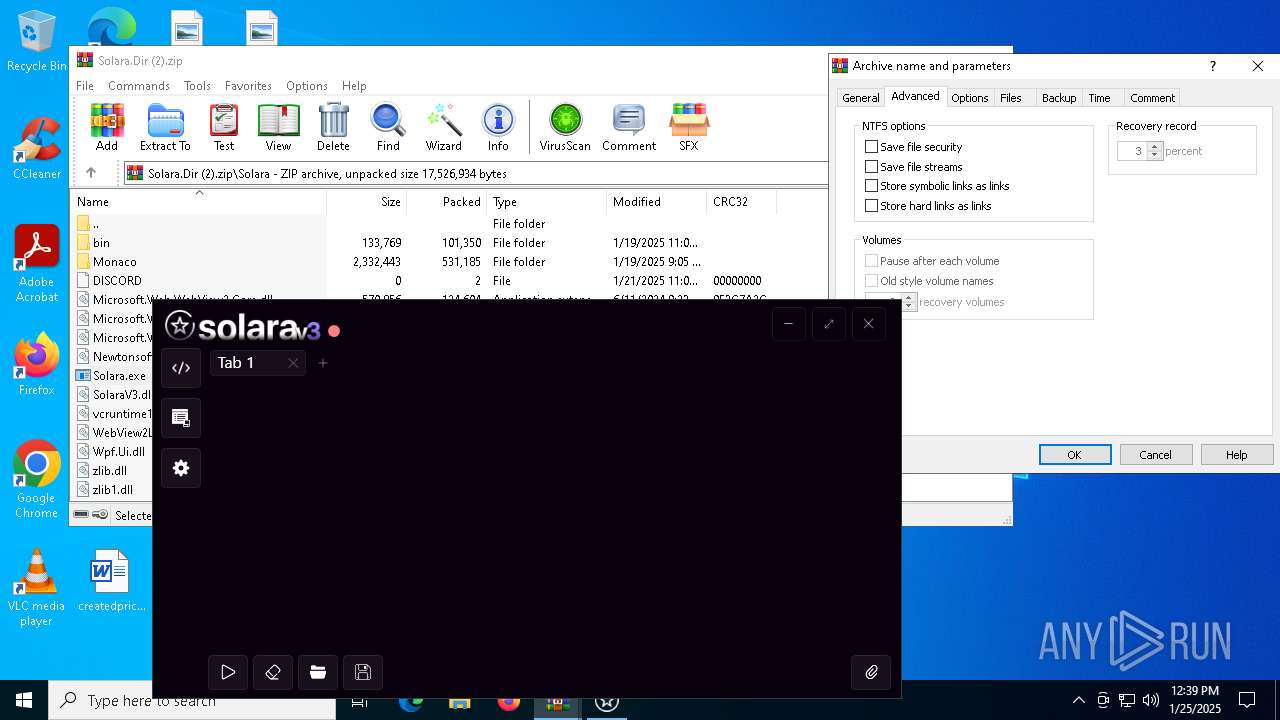
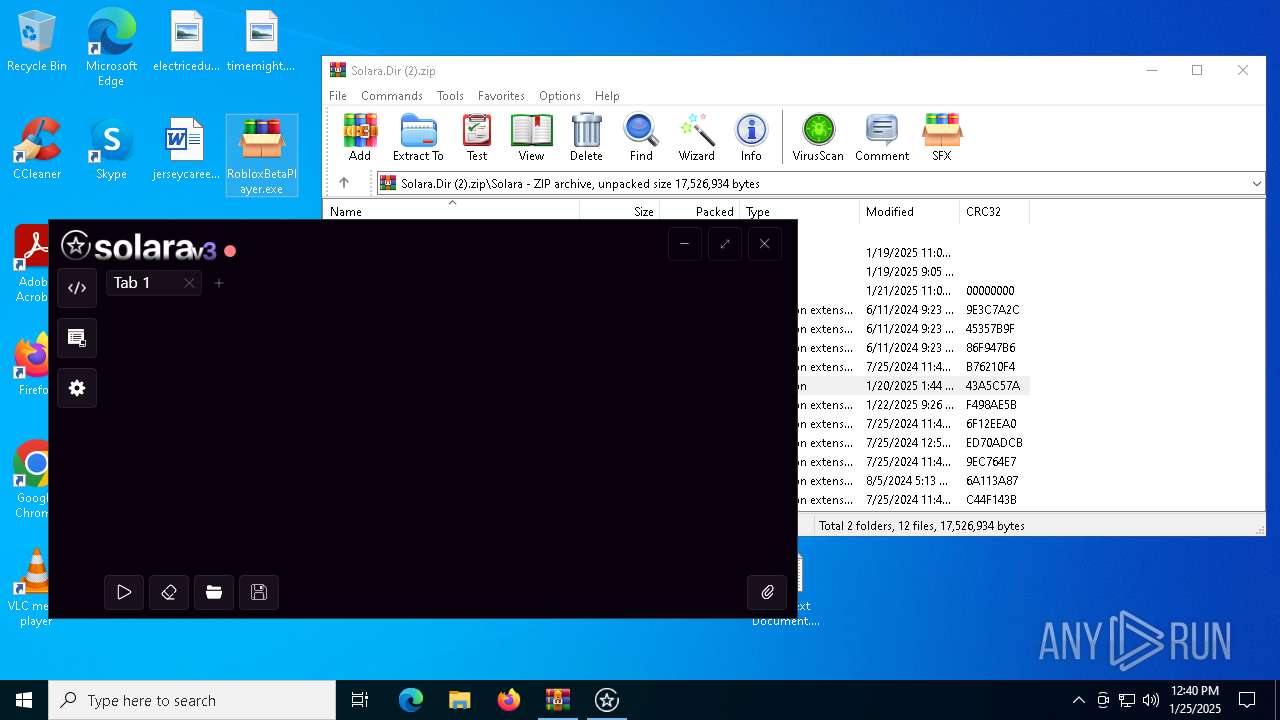
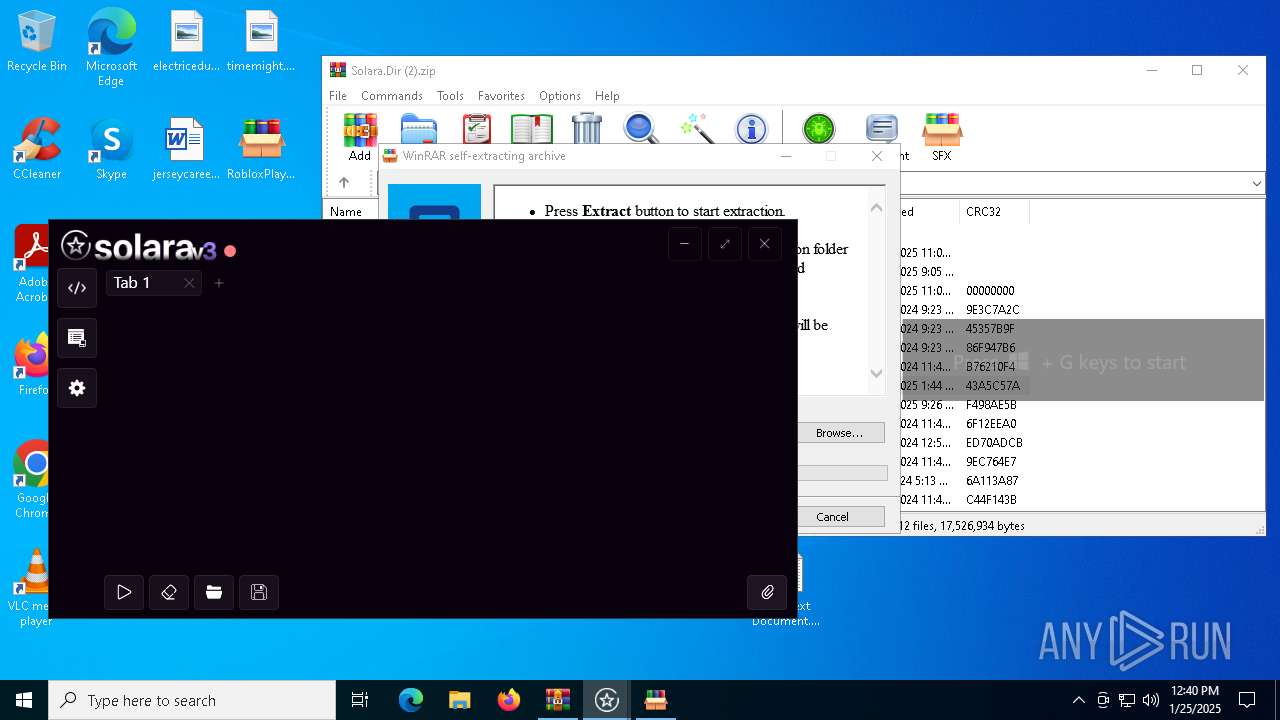
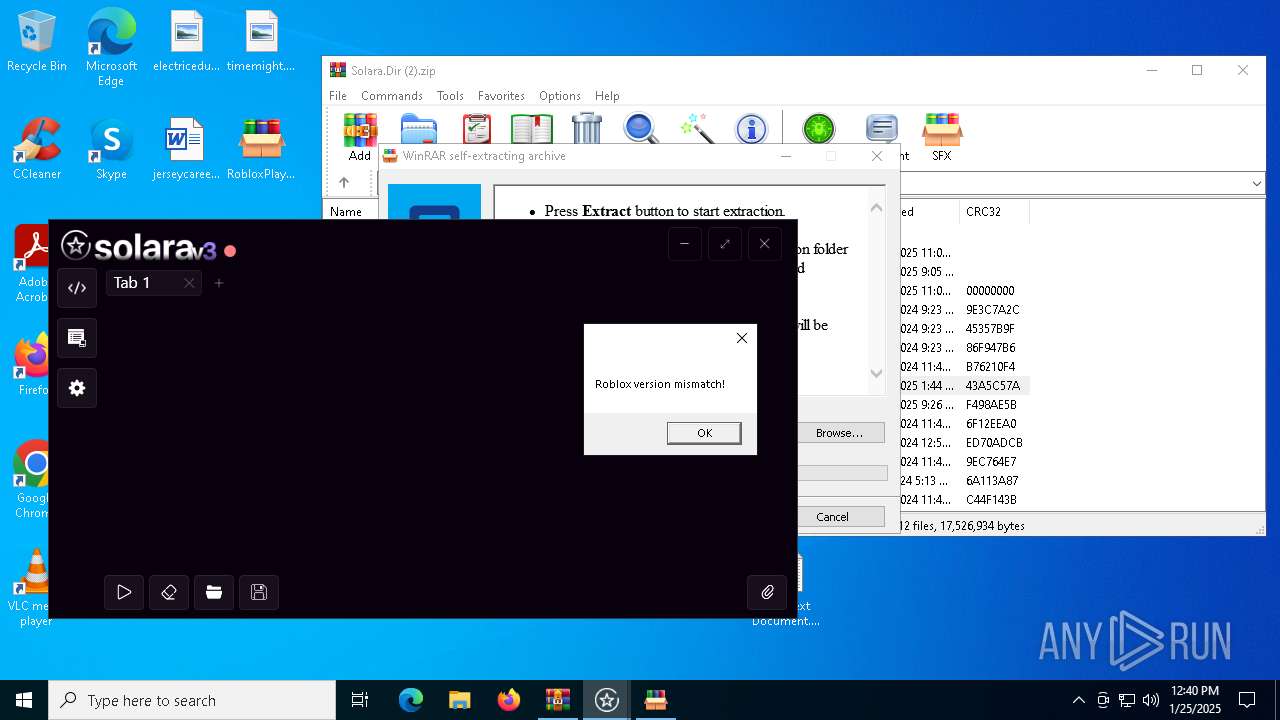
| File name: | Solara.Dir (2).zip |
| Full analysis: | https://app.any.run/tasks/5316dbed-ac30-4792-bdc2-d6e92c20b84d |
| Verdict: | Malicious activity |
| Analysis date: | January 25, 2025, 12:38:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 153592D87C302460C3DE8F9685AED725 |
| SHA1: | 712C59A6357E9AEC9CBB8A35DE7A154B21EDAF0F |
| SHA256: | DD5B887A938C82962FE97009A1582309C69929E0F58D29B4B05583EC19B00CA3 |
| SSDEEP: | 98304:F1CbMI6cpgP9RxScIqoXB/s+jMkHOH7/qC3DkDr9ac1rryOfaVID/xDV5Dsq06HG:FGjwUOg/2A/ieyIjjNm0dMxGbAoTAOI |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6032)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6032)
- Solara.exe (PID: 6384)
- RobloxBetaPlayer.exe (PID: 5240)
- RobloxPlayerBeta.exe (PID: 6316)
- GameBar.exe (PID: 2164)
Reads the BIOS version
- Solara.exe (PID: 6384)
Reads Microsoft Outlook installation path
- RobloxBetaPlayer.exe (PID: 5240)
- RobloxPlayerBeta.exe (PID: 6316)
Reads Internet Explorer settings
- RobloxBetaPlayer.exe (PID: 5240)
- RobloxPlayerBeta.exe (PID: 6316)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6032)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6032)
- WinRAR.exe (PID: 904)
Reads the machine GUID from the registry
- Solara.exe (PID: 6384)
Checks supported languages
- Solara.exe (PID: 6384)
- RobloxBetaPlayer.exe (PID: 5240)
- RobloxPlayerBeta.exe (PID: 6316)
- GameBar.exe (PID: 2164)
Reads the computer name
- Solara.exe (PID: 6384)
- RobloxBetaPlayer.exe (PID: 5240)
- RobloxPlayerBeta.exe (PID: 6316)
- GameBar.exe (PID: 2164)
Disables trace logs
- Solara.exe (PID: 6384)
Create files in a temporary directory
- Solara.exe (PID: 6384)
Checks proxy server information
- Solara.exe (PID: 6384)
- RobloxBetaPlayer.exe (PID: 5240)
- RobloxPlayerBeta.exe (PID: 6316)
Reads Environment values
- Solara.exe (PID: 6384)
Reads the software policy settings
- Solara.exe (PID: 6384)
Themida protector has been detected
- Solara.exe (PID: 6384)
Manual execution by a user
- WinRAR.exe (PID: 904)
- RobloxBetaPlayer.exe (PID: 5240)
- RobloxPlayerBeta.exe (PID: 6316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:22 16:29:02 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Solara/ |
Total processes
134
Monitored processes
8
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
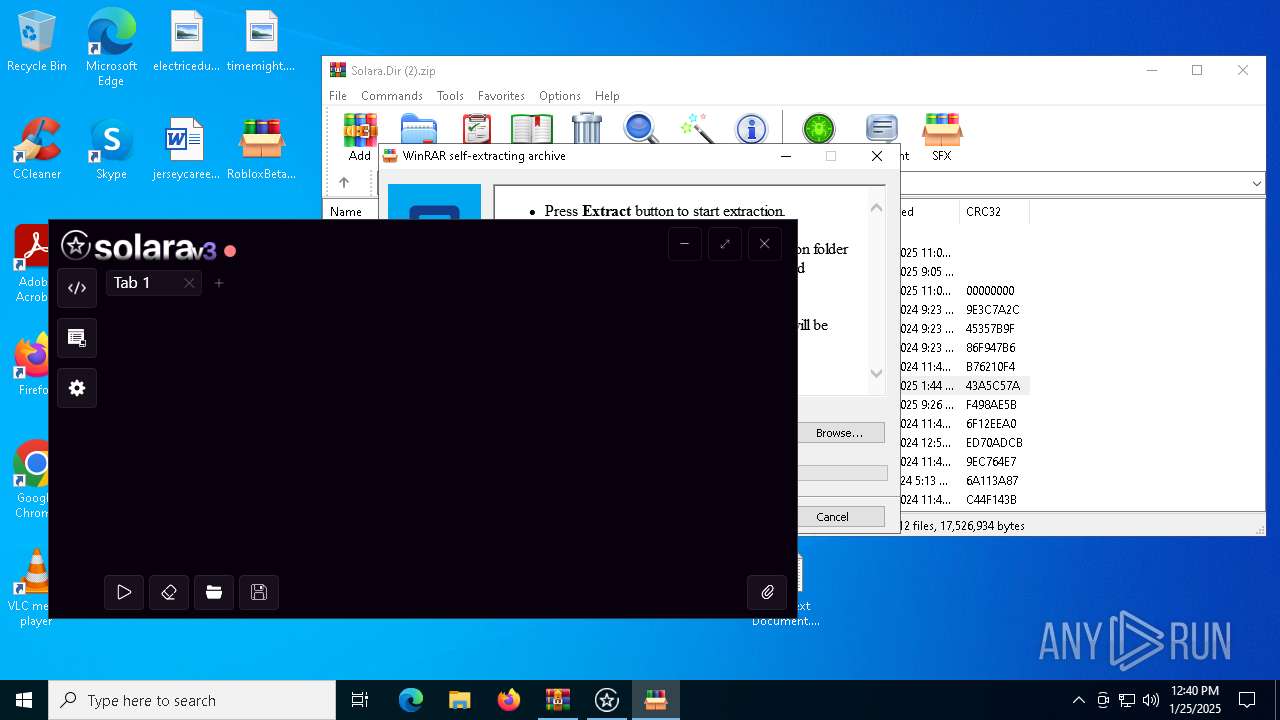
| 904 | "C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -- . "C:\Users\admin\Desktop\New Text Document.txt" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2164 | "C:\Program Files\WindowsApps\Microsoft.XboxGamingOverlay_2.34.28001.0_x64__8wekyb3d8bbwe\GameBar.exe" -ServerName:App.AppXbdkk0yrkwpcgeaem8zk81k8py1eaahny.mca | C:\Program Files\WindowsApps\Microsoft.XboxGamingOverlay_2.34.28001.0_x64__8wekyb3d8bbwe\GameBar.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
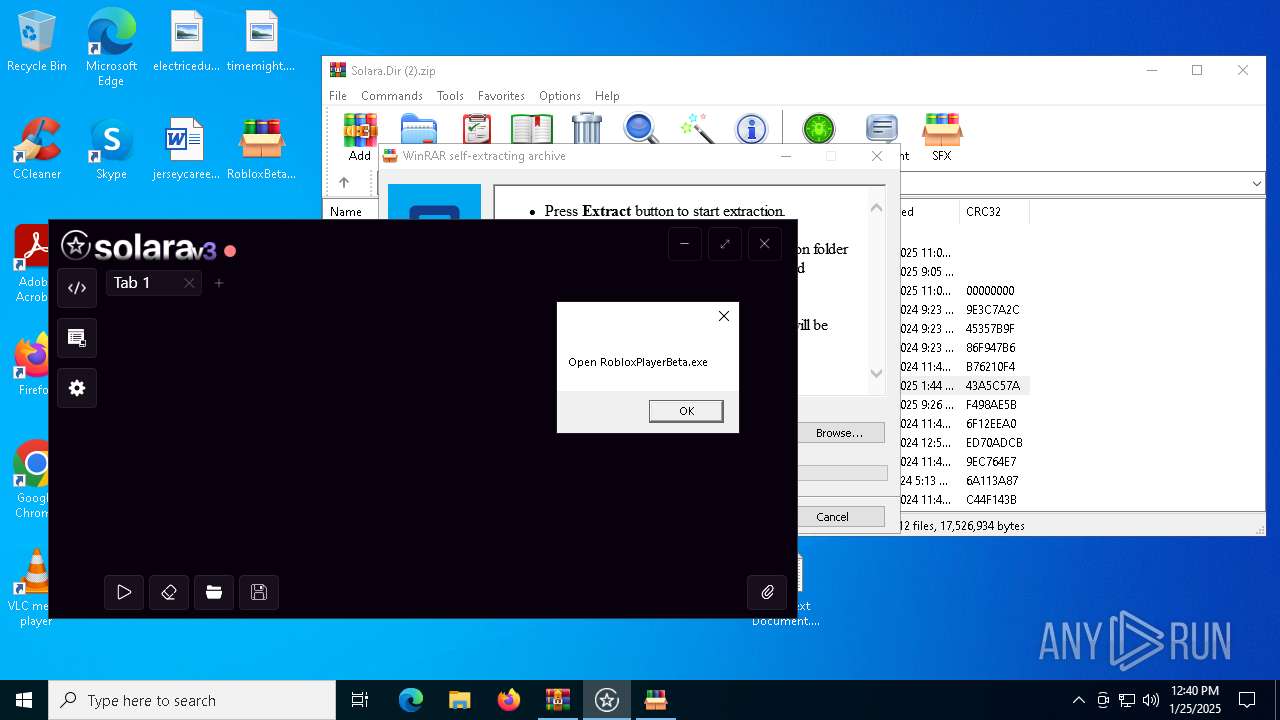
| 5240 | "C:\Users\admin\Desktop\RobloxBetaPlayer.exe" | C:\Users\admin\Desktop\RobloxBetaPlayer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 255 Modules
| |||||||||||||||
| 6032 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Solara.Dir (2).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6316 | "C:\Users\admin\Desktop\RobloxPlayerBeta.exe" | C:\Users\admin\Desktop\RobloxPlayerBeta.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 255 Modules
| |||||||||||||||
| 6348 | "C:\Windows\System32\GameBarPresenceWriter.exe" -ServerName:Windows.Gaming.GameBar.Internal.PresenceWriterServer | C:\Windows\System32\GameBarPresenceWriter.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Gamebar Presence Writer Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
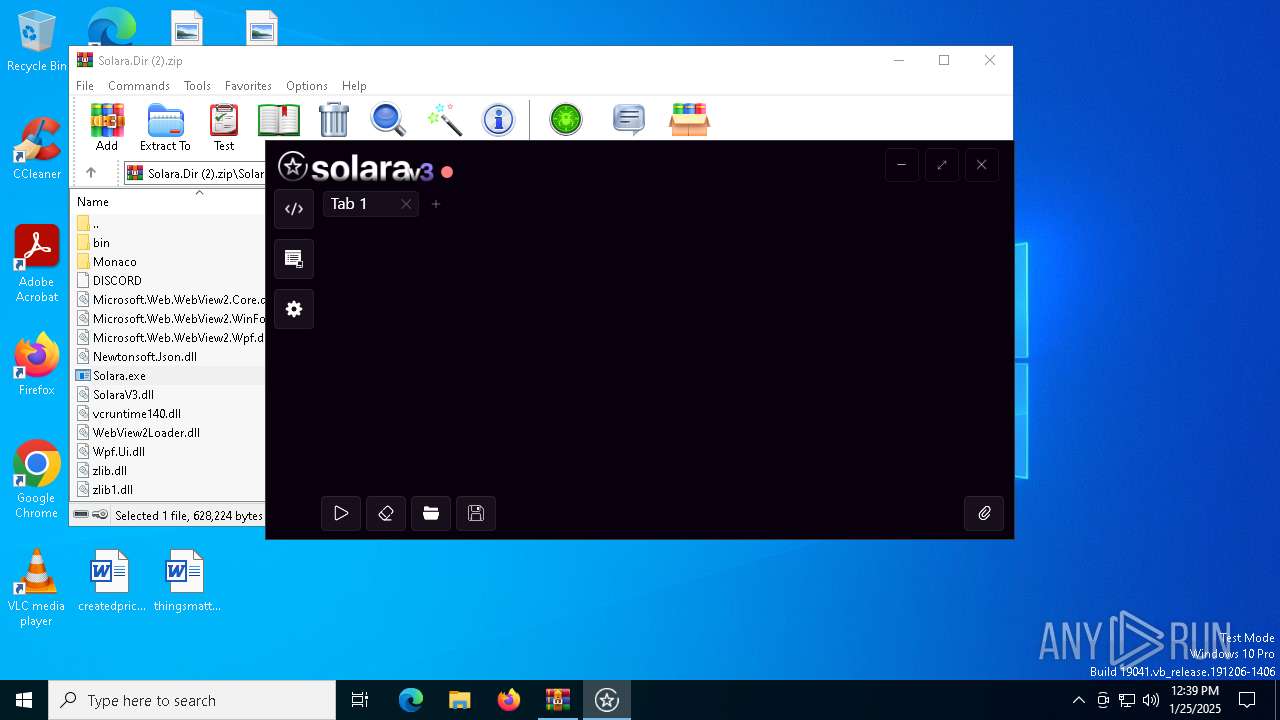
| 6384 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Solara.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Solara.exe | WinRAR.exe | ||||||||||||
User: admin Company: CMD Softworks Integrity Level: MEDIUM Description: Solara V3 Version: 3.0.0.0 Modules
| |||||||||||||||
Total events
5 751
Read events
5 705
Write events
42
Delete events
4
Modification events
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Solara.Dir (2).zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6384) Solara.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Solara_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6384) Solara.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Solara_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
11
Suspicious files
4
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\bin\version.txt | text | |
MD5:E6B89EDBAD2989172F959188AE8A6D0B | SHA256:A4F7BA76DB1A09F402A4C5061F8AD16C038F6515DC7AD2A200EC68941F27440C | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Newtonsoft.Json.dll | executable | |
MD5:195FFB7167DB3219B217C4FD439EEDD6 | SHA256:E1E27AF7B07EEEDF5CE71A9255F0422816A6FC5849A483C6714E1B472044FA9D | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Monaco\vs\basic-languages\lua\lua.js | binary | |
MD5:8706D861294E09A1F2F7E63D19E5FCB7 | SHA256:FC2D6FB52A524A56CD8AC53BFE4BAD733F246E76DC73CBEC4C61BE32D282AC42 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Monaco\index.html | html | |
MD5:610EB8CECD447FCF97C242720D32B6BD | SHA256:107D8D9D6C94D2A86AC5AF4B4CEC43D959C2E44D445017FEA59E2E0A5EFAFDC7 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Microsoft.Web.WebView2.Wpf.dll | executable | |
MD5:E107C88A6FC54CC3CEB4D85768374074 | SHA256:8F821F0C818F8D817B82F76C25F90FDE9FB73FF1AE99C3DF3EAF2B955653C9C8 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Monaco\vs\editor\editor.main.css | text | |
MD5:6AF9C0D237B31C1C91F7FAA84B384BDF | SHA256:FB2CBF2EE64286BC010A6C6FE6A81C6C292C145A2F584D0240C674F56E3015B0 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Monaco\combined.html | html | |
MD5:2C2053ACBF1F8A49E82722FA3344F9C8 | SHA256:4990B715406B19374EE9A6A0255AEBBC18CA2FA6E1292B3C292E9A6275D24C26 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Microsoft.Web.WebView2.WinForms.dll | executable | |
MD5:C7000FAA6C6040188C8CD8EF28B6DEDA | SHA256:E4F695B72F99024E3EE5D5F26A367E664F4E120BD5D90AA87A8BC0509C365EC8 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Microsoft.Web.WebView2.Core.dll | executable | |
MD5:B037CA44FD19B8EEDB6D5B9DE3E48469 | SHA256:11E88B2CA921E5C88F64567F11BD83CBC396C10365D40972F3359FCC7965D197 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6032.4424\Solara\Monaco\vs\editor\editor.main.js | binary | |
MD5:9399A8EAA741D04B0AE6566A5EBB8106 | SHA256:93D28520C07FBCA09E20886087F28797BB7BD0E6CF77400153AAB5AE67E3CE18 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
41
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2092 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2092 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 142.250.74.195:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 142.250.74.195:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7064 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7064 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6516 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2092 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2092 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.23.227.215:443 | — | Ooredoo Q.S.C. | QA | unknown |
2092 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6384 | Solara.exe | 104.20.4.235:443 | pastebin.com | CLOUDFLARENET | — | shared |
5064 | SearchApp.exe | 2.23.227.208:443 | — | Ooredoo Q.S.C. | QA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
pastebin.com |
| shared |
clientsettings.roblox.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
getsolara.dev |
| malicious |
c.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |