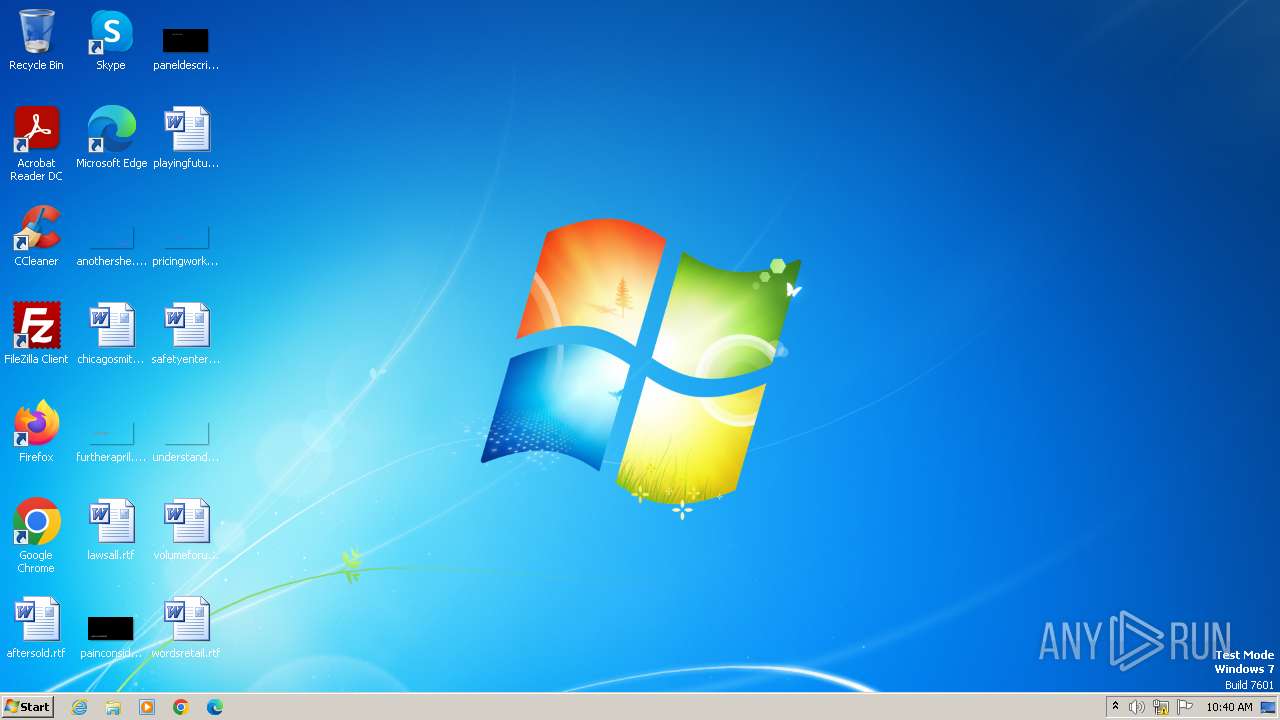
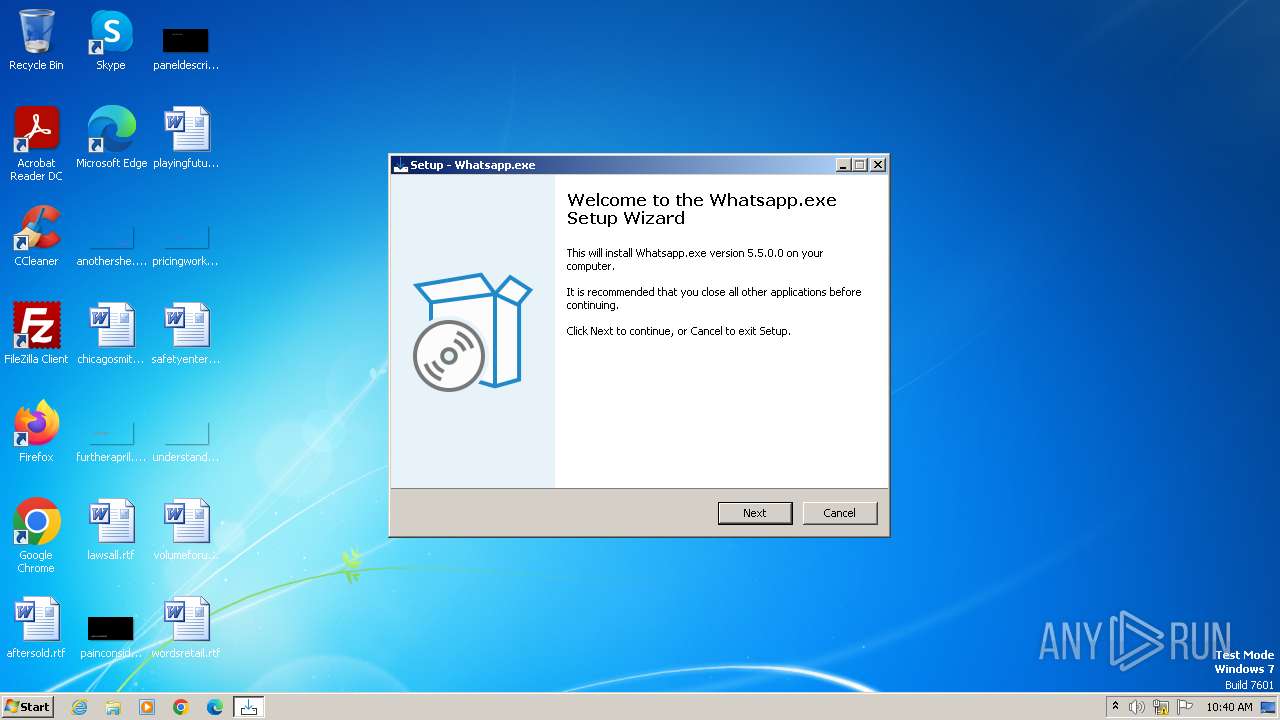
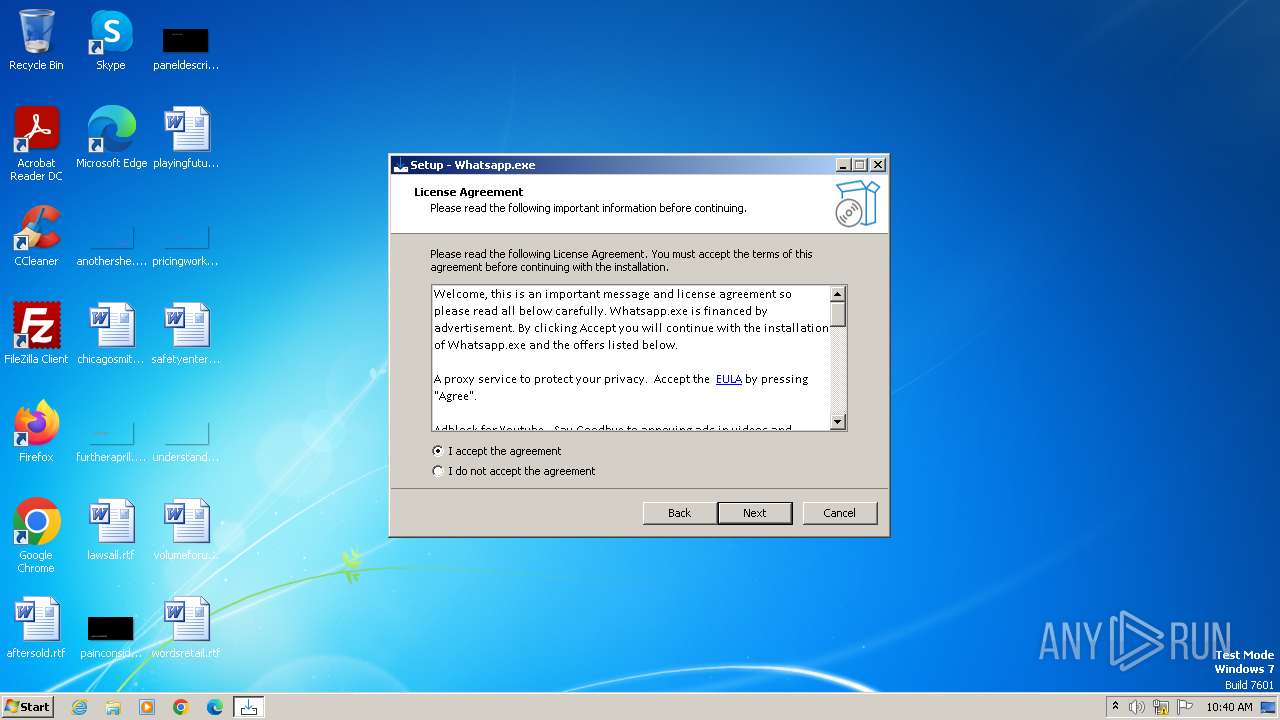
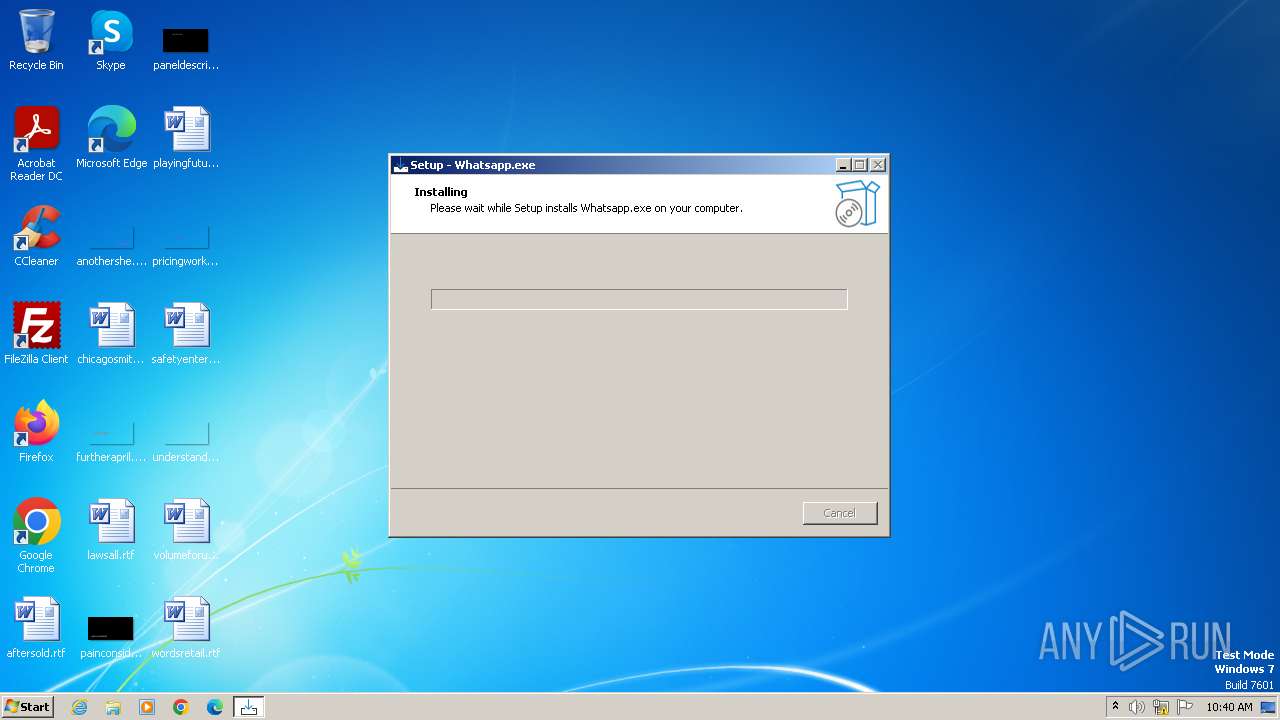
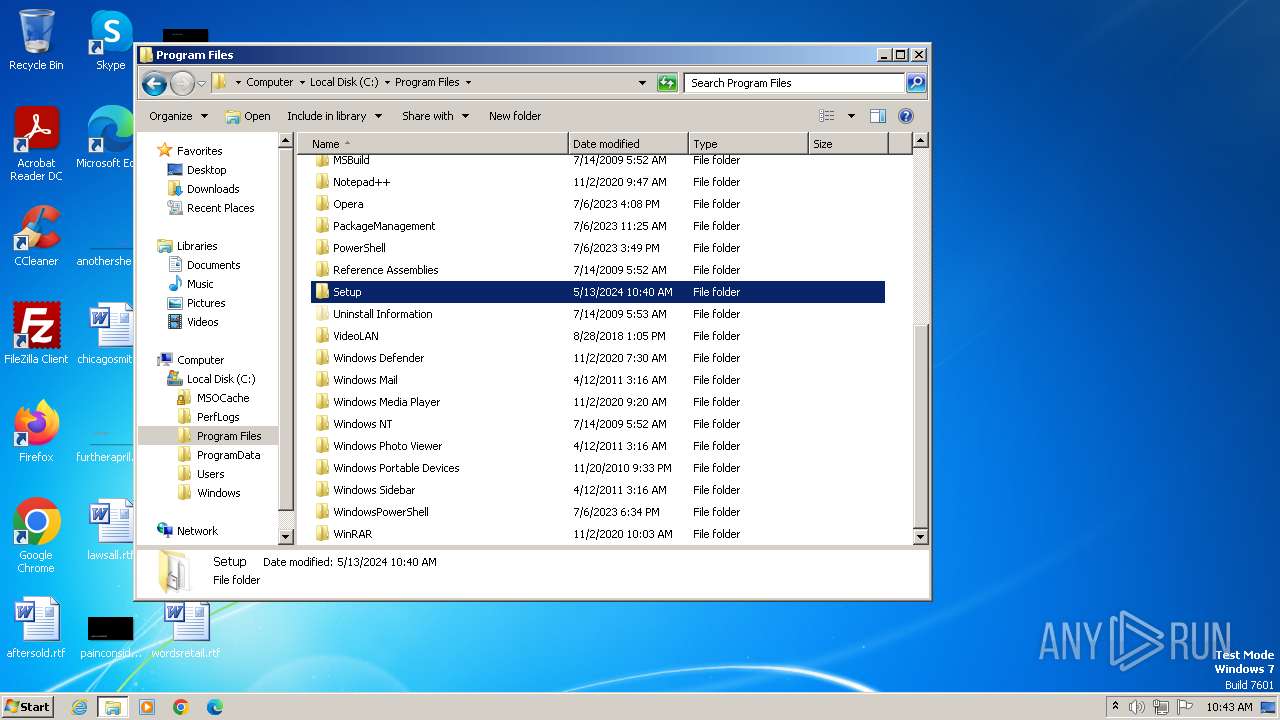
| File name: | Whatsapp.exe |
| Full analysis: | https://app.any.run/tasks/1516fae7-5580-485c-be80-5480b75aa0df |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2024, 09:40:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 327A39AC1345C7BB3EE48056260C993C |
| SHA1: | E29B2572885203A5EA57476AA48802A38C1F834C |
| SHA256: | DD593E0A9E87A49ED6A59164D472D0DCB075E0E3ECB2EBB4E3652223895BC856 |
| SSDEEP: | 49152:+7HecD4dnbibBlFSYUJ/9XidjsbmLApne0Fop4R2uXB3iyLT/ex4XrL7P42DpJXQ:m+cD4dnmwpidIkWnXFopLQ3iUrex4vk5 |
MALICIOUS
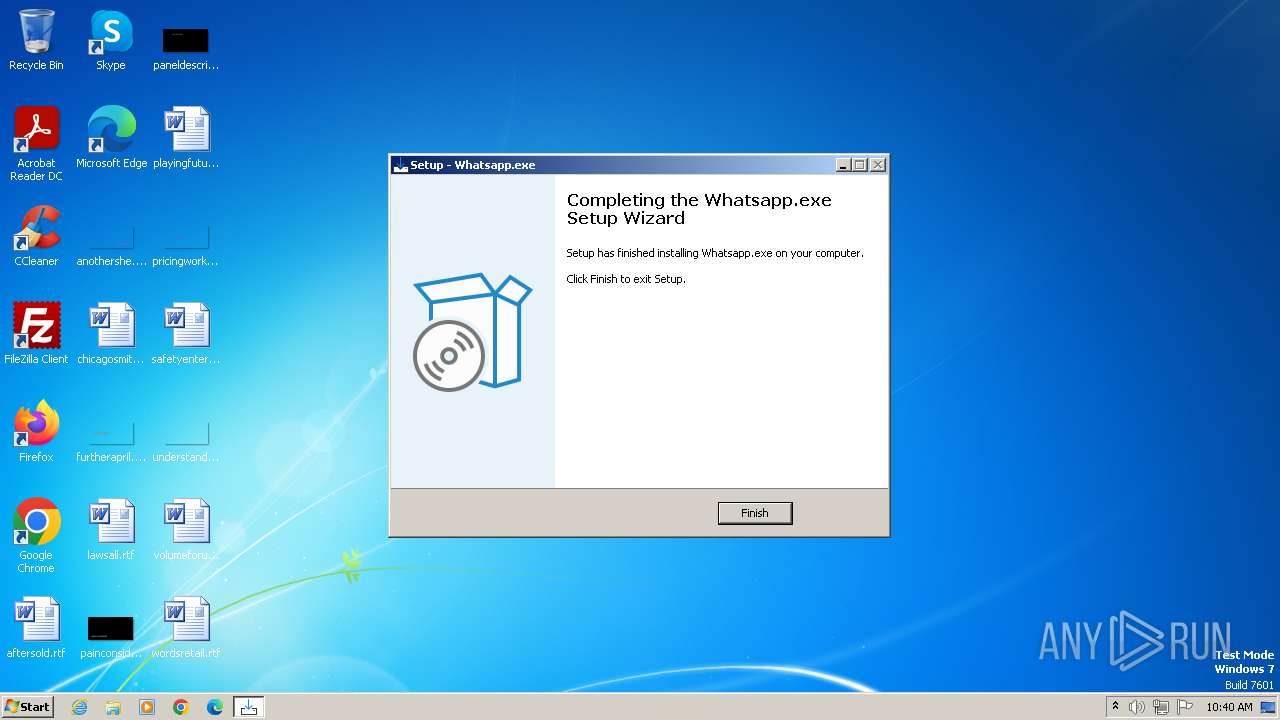
Drops the executable file immediately after the start
- Whatsapp.exe (PID: 3964)
- Whatsapp.exe (PID: 2072)
- Whatsapp.tmp (PID: 1200)
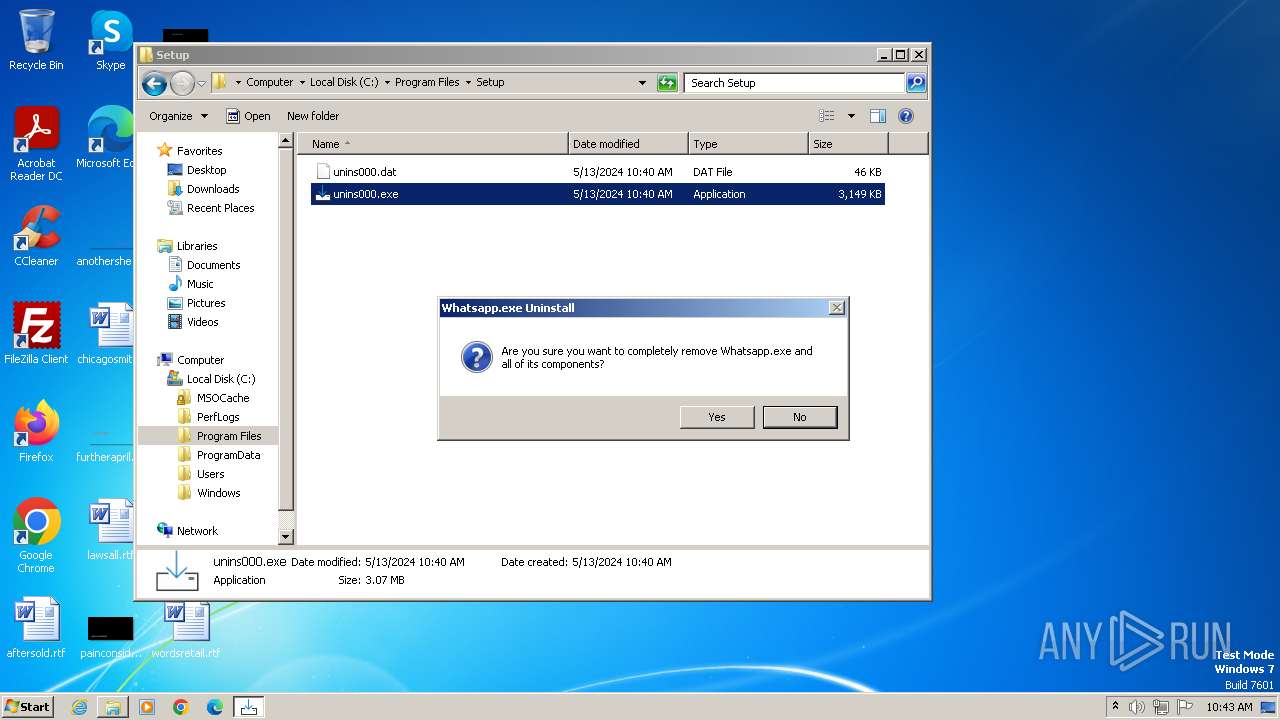
- unins000.exe (PID: 2108)
SUSPICIOUS
Executable content was dropped or overwritten
- Whatsapp.exe (PID: 2072)
- Whatsapp.exe (PID: 3964)
- Whatsapp.tmp (PID: 1200)
- unins000.exe (PID: 2108)
Reads the Windows owner or organization settings
- Whatsapp.tmp (PID: 1200)
- _unins.tmp (PID: 4072)
Reads the Internet Settings
- Whatsapp.tmp (PID: 1200)
Reads security settings of Internet Explorer
- Whatsapp.tmp (PID: 1200)
Checks Windows Trust Settings
- Whatsapp.tmp (PID: 1200)
Reads settings of System Certificates
- Whatsapp.tmp (PID: 1200)
Starts application with an unusual extension
- unins000.exe (PID: 2108)
Starts itself from another location
- unins000.exe (PID: 2108)
Application launched itself
- unins000.exe (PID: 3916)
INFO
Checks supported languages
- Whatsapp.exe (PID: 3964)
- Whatsapp.tmp (PID: 3980)
- Whatsapp.exe (PID: 2072)
- Whatsapp.tmp (PID: 1200)
- wmpnscfg.exe (PID: 2136)
- _unins.tmp (PID: 4072)
- unins000.exe (PID: 3916)
- unins000.exe (PID: 2108)
Reads the computer name
- Whatsapp.tmp (PID: 3980)
- Whatsapp.tmp (PID: 1200)
- wmpnscfg.exe (PID: 2136)
- unins000.exe (PID: 3916)
- _unins.tmp (PID: 4072)
- unins000.exe (PID: 2108)
Create files in a temporary directory
- Whatsapp.exe (PID: 3964)
- Whatsapp.exe (PID: 2072)
- Whatsapp.tmp (PID: 1200)
- unins000.exe (PID: 2108)
Checks proxy server information
- Whatsapp.tmp (PID: 1200)
Reads the machine GUID from the registry
- Whatsapp.tmp (PID: 1200)
Creates files in the program directory
- Whatsapp.tmp (PID: 1200)
Reads the software policy settings
- Whatsapp.tmp (PID: 1200)
Creates files or folders in the user directory
- Whatsapp.tmp (PID: 1200)
Application launched itself
- msedge.exe (PID: 1764)
- msedge.exe (PID: 1824)
Manual execution by a user
- wmpnscfg.exe (PID: 2136)
- msedge.exe (PID: 1824)
- rundll32.exe (PID: 372)
- explorer.exe (PID: 3136)
- unins000.exe (PID: 3916)
Creates a software uninstall entry
- Whatsapp.tmp (PID: 1200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.5.0.0 |
| ProductVersionNumber: | 5.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Whatsapp.exe Setup |
| FileVersion: | 5.5.0.0 |
| LegalCopyright: | Whatsapp.exe |
| OriginalFileName: | |
| ProductName: | Whatsapp.exe |
| ProductVersion: | 5.5.0.0 |
Total processes
68
Monitored processes
28
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Program Files\Setup\unins000.dat | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 660 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6e5ef598,0x6e5ef5a8,0x6e5ef5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3884 --field-trial-handle=1180,i,13836048934112899401,14089185457454297384,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 856 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2244 --field-trial-handle=1180,i,13836048934112899401,14089185457454297384,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1200 | "C:\Users\admin\AppData\Local\Temp\is-76R8Q.tmp\Whatsapp.tmp" /SL5="$3013A,922170,832512,C:\Users\admin\AppData\Local\Temp\Whatsapp.exe" /SPAWNWND=$20130 /NOTIFYWND=$20138 | C:\Users\admin\AppData\Local\Temp\is-76R8Q.tmp\Whatsapp.tmp | Whatsapp.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1640 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6e5ef598,0x6e5ef5a8,0x6e5ef5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
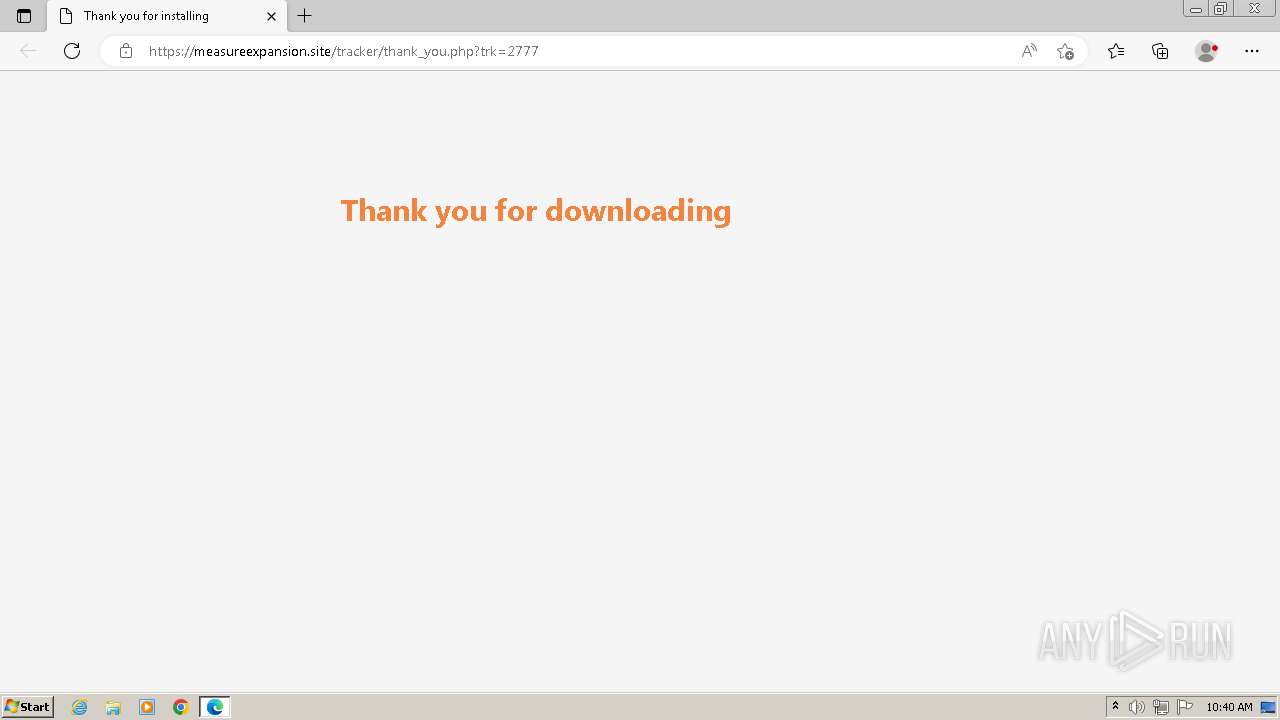
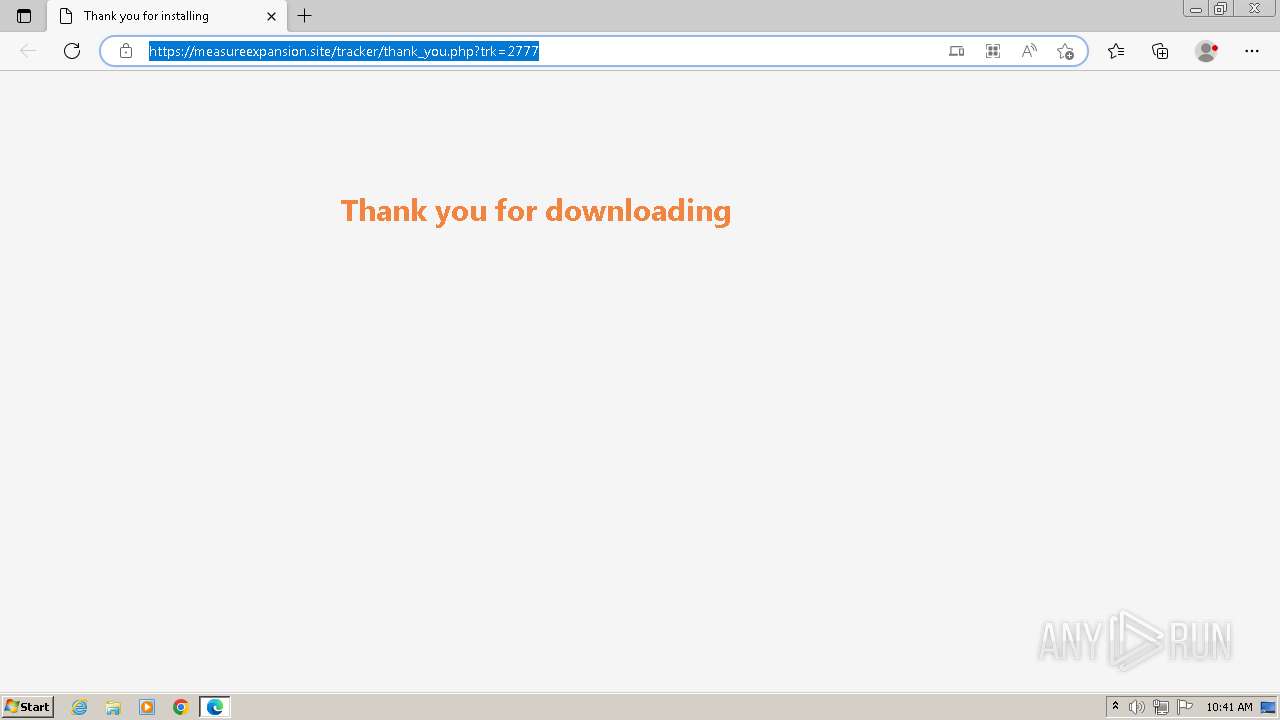
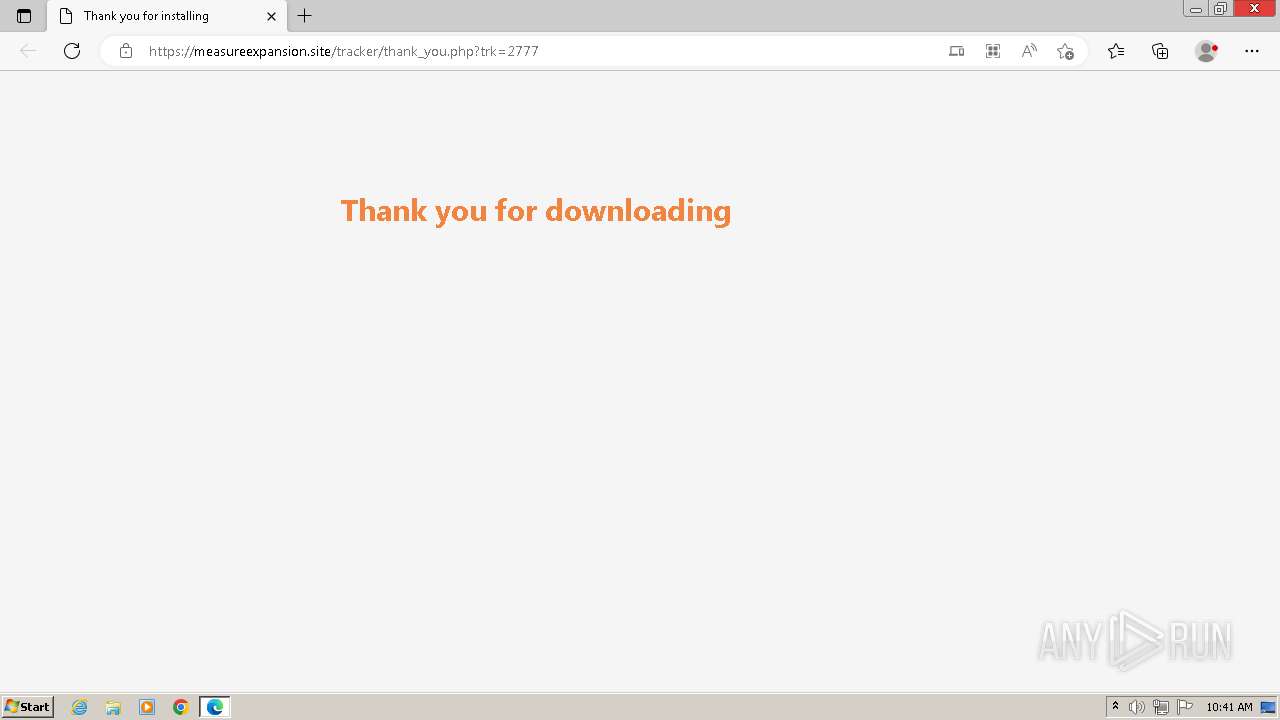
| 1764 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://measureexpansion.site/tracker/thank_you.php?trk=2777 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | Whatsapp.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1796 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1300 --field-trial-handle=1316,i,17078217209399652766,15258539189502583962,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1824 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --flag-switches-end --do-not-de-elevate https://measureexpansion.site/tracker/thank_you.php?trk=2777 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1836 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1424 --field-trial-handle=1316,i,17078217209399652766,15258539189502583962,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
12 254
Read events
12 129
Write events
105
Delete events
20
Modification events
| (PID) Process: | (1200) Whatsapp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: B0040000DACF279319A5DA01 | |||
| (PID) Process: | (1200) Whatsapp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: D42015F8C0C5E8BA7556954B5E89D48D01ADCAF2FDBB6C8F4EEE90A120D90079 | |||
| (PID) Process: | (1200) Whatsapp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1200) Whatsapp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1200) Whatsapp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (1200) Whatsapp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (1200) Whatsapp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (1200) Whatsapp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (1200) Whatsapp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1200) Whatsapp.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
5
Suspicious files
71
Text files
42
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1200 | Whatsapp.tmp | C:\Program Files\Setup\is-S91MS.tmp | — | |
MD5:— | SHA256:— | |||
| 1764 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | — | |
MD5:— | SHA256:— | |||
| 1764 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\c283f745-a273-49bb-9c7e-dd85b5db5ecf.tmp | — | |
MD5:— | SHA256:— | |||
| 1764 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State~RF10af2d.TMP | — | |
MD5:— | SHA256:— | |||
| 1764 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\6a6eb1cc-ee21-46c8-b380-4ba23a571240.tmp | — | |
MD5:— | SHA256:— | |||
| 1764 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State~RF10af3d.TMP | — | |
MD5:— | SHA256:— | |||
| 1640 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 1824 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b076.TMP | — | |
MD5:— | SHA256:— | |||
| 1824 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1200 | Whatsapp.tmp | C:\Users\admin\AppData\Local\Temp\is-2T87B.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
22
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1200 | Whatsapp.tmp | GET | 304 | 184.51.252.176:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0fd705b4979870b9 | unknown | — | — | unknown |
1200 | Whatsapp.tmp | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
1200 | Whatsapp.tmp | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1200 | Whatsapp.tmp | 172.67.185.120:443 | measureexpansion.site | CLOUDFLARENET | US | unknown |
1200 | Whatsapp.tmp | 184.51.252.176:80 | ctldl.windowsupdate.com | Akamai International B.V. | SE | unknown |
1200 | Whatsapp.tmp | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1824 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
1900 | msedge.exe | 172.67.185.120:443 | measureexpansion.site | CLOUDFLARENET | US | unknown |
1900 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
measureexpansion.site |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
stackpath.bootstrapcdn.com |
| whitelisted |
www.bing.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1900 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |