| File name: | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55 |
| Full analysis: | https://app.any.run/tasks/63fdd465-1050-43d7-a413-77bd0d51522e |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | April 13, 2025, 03:57:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 78C802B7CED01A823BE54EDC23110F64 |
| SHA1: | E00F33883FDD3BA69D2A1BB112FE355972A50082 |
| SHA256: | DD4A987DD3A15DDE96899705CA05061F4C77FB26F681C091D1B1A85D943E6C55 |
| SSDEEP: | 49152:xhWb/uvl+mfOFHfWITcxMXP1zKJ1/0LYT:xcVzF+ITcxMXP1WT0L |
MALICIOUS
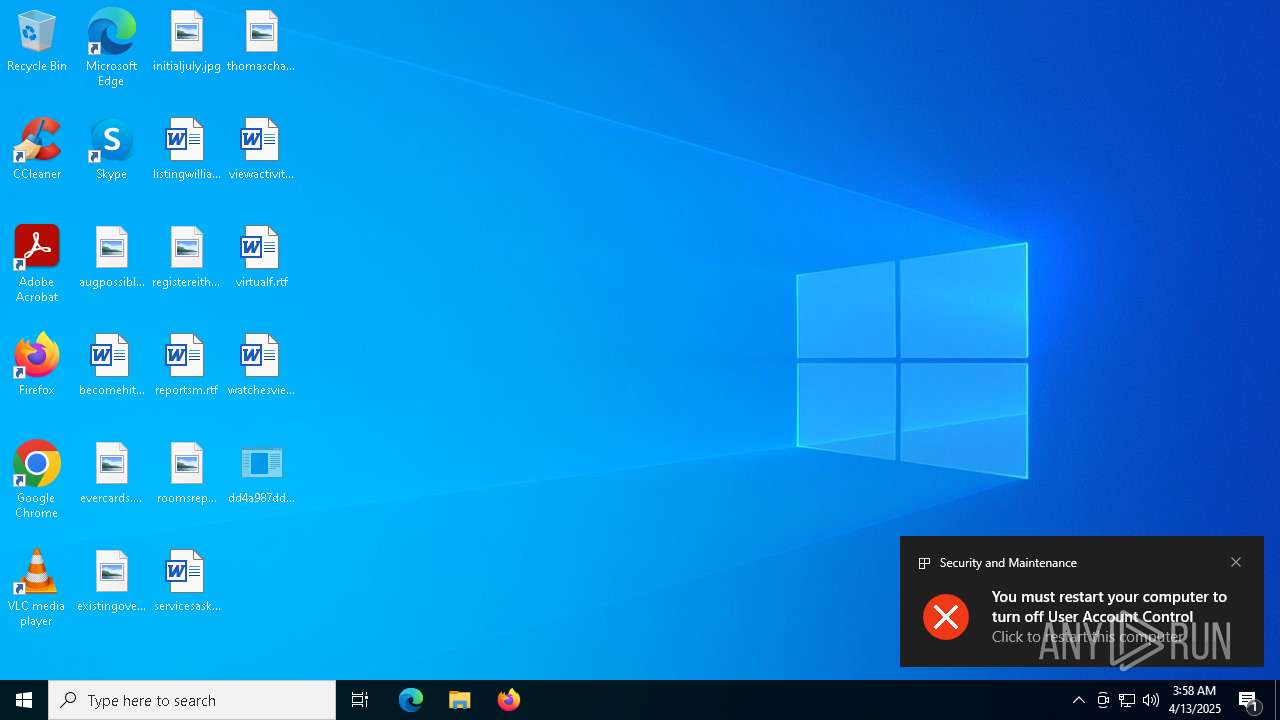
UAC/LUA settings modification
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
XORed URL has been found (YARA)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
DCRAT has been detected (YARA)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Changes Windows Defender settings
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Adds path to the Windows Defender exclusion list
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 9088)
- wscript.exe (PID: 9132)
- wscript.exe (PID: 7432)
- wscript.exe (PID: 8852)
- wscript.exe (PID: 1676)
- wscript.exe (PID: 8036)
DARKCRYSTAL has been detected (SURICATA)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Deletes a file (SCRIPT)
- wscript.exe (PID: 9088)
- wscript.exe (PID: 8852)
SUSPICIOUS
Reads security settings of Internet Explorer
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7652)
- ShellExperienceHost.exe (PID: 7984)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Reads the date of Windows installation
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7652)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Starts CMD.EXE for commands execution
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7652)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Modifies hosts file to alter network resolution
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Executed via WMI
- schtasks.exe (PID: 8176)
- schtasks.exe (PID: 6620)
- schtasks.exe (PID: 2140)
- schtasks.exe (PID: 6048)
- schtasks.exe (PID: 5380)
- schtasks.exe (PID: 7196)
- schtasks.exe (PID: 904)
- schtasks.exe (PID: 1812)
- schtasks.exe (PID: 1244)
- schtasks.exe (PID: 864)
- schtasks.exe (PID: 2564)
- schtasks.exe (PID: 6872)
- schtasks.exe (PID: 6028)
- schtasks.exe (PID: 6644)
- schtasks.exe (PID: 7036)
- schtasks.exe (PID: 4408)
- schtasks.exe (PID: 1020)
- schtasks.exe (PID: 4724)
- schtasks.exe (PID: 4976)
- schtasks.exe (PID: 5528)
- schtasks.exe (PID: 2980)
- schtasks.exe (PID: 7420)
- schtasks.exe (PID: 7272)
- schtasks.exe (PID: 7260)
- schtasks.exe (PID: 7444)
- schtasks.exe (PID: 1276)
- schtasks.exe (PID: 7556)
- schtasks.exe (PID: 7468)
- schtasks.exe (PID: 7472)
- schtasks.exe (PID: 7544)
- schtasks.exe (PID: 7484)
- schtasks.exe (PID: 7532)
- schtasks.exe (PID: 7600)
- schtasks.exe (PID: 7148)
- schtasks.exe (PID: 3176)
- schtasks.exe (PID: 6488)
- schtasks.exe (PID: 1272)
- schtasks.exe (PID: 6036)
- schtasks.exe (PID: 7620)
The process creates files with name similar to system file names
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Executable content was dropped or overwritten
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ApplicationFrameHost.exe (PID: 8468)
There is functionality for taking screenshot (YARA)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Executing commands from a ".bat" file
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Script adds exclusion path to Windows Defender
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Starts POWERSHELL.EXE for commands execution
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 3176)
The process executes VB scripts
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 9088)
- wscript.exe (PID: 9132)
- wscript.exe (PID: 7432)
- wscript.exe (PID: 8852)
- wscript.exe (PID: 1676)
- wscript.exe (PID: 8036)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 9088)
- wscript.exe (PID: 8852)
- wscript.exe (PID: 1676)
Runs shell command (SCRIPT)
- wscript.exe (PID: 9088)
- wscript.exe (PID: 8852)
Connects to the server without a host name
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 9088)
- wscript.exe (PID: 8852)
INFO
Reads the machine GUID from the registry
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7652)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
The sample compiled with english language support
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7652)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ApplicationFrameHost.exe (PID: 8468)
Reads Environment values
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7652)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Reads the computer name
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7652)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ShellExperienceHost.exe (PID: 7984)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Checks supported languages
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7652)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ShellExperienceHost.exe (PID: 7984)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Process checks computer location settings
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7652)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Process checks whether UAC notifications are on
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Creates files in the program directory
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Create files in a temporary directory
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Confuser has been detected (YARA)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Potential library load (Base64 Encoded 'LoadLibrary')
- dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe (PID: 7856)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7736)
- powershell.exe (PID: 5072)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 8176)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 6132)
- powershell.exe (PID: 2136)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 7192)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 6404)
- powershell.exe (PID: 4652)
- powershell.exe (PID: 6244)
- powershell.exe (PID: 7812)
Reads Microsoft Office registry keys
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8176)
- powershell.exe (PID: 4652)
- powershell.exe (PID: 2136)
- powershell.exe (PID: 6244)
- powershell.exe (PID: 7736)
- powershell.exe (PID: 6404)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 5072)
- powershell.exe (PID: 7812)
- powershell.exe (PID: 7944)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 6132)
- powershell.exe (PID: 7192)
Checks proxy server information
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- slui.exe (PID: 5204)
- ApplicationFrameHost.exe (PID: 7820)
Disables trace logs
- ApplicationFrameHost.exe (PID: 8468)
- ApplicationFrameHost.exe (PID: 3300)
- ApplicationFrameHost.exe (PID: 7820)
Reads the software policy settings
- slui.exe (PID: 5204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:10:06 20:59:48+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 1982464 |
| InitializedDataSize: | 1536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e5f9e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 821.390.381.228 |
| ProductVersionNumber: | 410.849.918.488 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | i5utMcfpUgTGwWN1WAguvwF9 |
| CompanyName: | NzlDlnoRuQMmMVUWSnGAgXBKWC0Q7 |
| InternalName: | F0.exe |
| LegalCopyright: | u9B5ydmxn4FACJhU |
| Comments: | tf99Tm |
| OriginalFileName: | okh8STyLWTjWSwvMQPme6.exe |
| ProductVersion: | 410.849.918.488 |
| FileVersion: | 821.390.381.228 |
Total processes
209
Monitored processes
85
Malicious processes
10
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | schtasks.exe /create /tn "RegistryR" /sc MINUTE /mo 14 /tr "'C:\Recovery\Logs\Registry.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | schtasks.exe /create /tn "Registry" /sc ONLOGON /tr "'C:\Recovery\Logs\Registry.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | schtasks.exe /create /tn "audiodga" /sc MINUTE /mo 8 /tr "'C:\Users\Default\audiodg.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | schtasks.exe /create /tn "ctfmon" /sc ONLOGON /tr "'C:\Windows\ShellExperiences\ctfmon.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | schtasks.exe /create /tn "WmiPrvSEW" /sc MINUTE /mo 5 /tr "'C:\Users\All Users\Comms\WmiPrvSE.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | schtasks.exe /create /tn "csrssc" /sc MINUTE /mo 9 /tr "'C:\Program Files (x86)\Mozilla Maintenance Service\logs\csrss.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\4efd538f-4e69-4ea5-b4b2-fc8c62ac43c3.vbs" | C:\Windows\System32\wscript.exe | — | ApplicationFrameHost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
90 660
Read events
90 618
Write events
42
Delete events
0
Modification events
| (PID) Process: | (7856) dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (7856) dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (7856) dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | PromptOnSecureDesktop |
Value: 0 | |||
| (PID) Process: | (7856) dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000000000000 | |||
| (PID) Process: | (7856) dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\2889f16de45eafd896db721b7188686d |
| Operation: | write | Name: | 2889f16de45eafd896db721b7188686d |
Value: 2889f16de45eafd896db721b7188686d | |||
| (PID) Process: | (7984) ShellExperienceHost.exe | Key: | \REGISTRY\A\{6b705428-70fb-29ca-28f7-cd97166aa035}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000FE0D244528ACDB01 | |||
| (PID) Process: | (7856) dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (7856) dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (8468) ApplicationFrameHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (8468) ApplicationFrameHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
Executable files
55
Suspicious files
1
Text files
51
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7856 | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | C:\Users\admin\3D Objects\UserOOBEBroker.exe | executable | |
MD5:78C802B7CED01A823BE54EDC23110F64 | SHA256:DD4A987DD3A15DDE96899705CA05061F4C77FB26F681C091D1B1A85D943E6C55 | |||
| 7856 | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | C:\Users\admin\3D Objects\7ccfebd9e92364 | text | |
MD5:5C176272525C97738447582A2535BFDC | SHA256:8CA17CD8FD2564CF3375F13E99AE3D4C784107D17A0064F94DB59DC45A454FCD | |||
| 7856 | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | C:\Windows\System32\drivers\etc\hosts | text | |
MD5:737F605A2CFE61105E6FD84A08F579E5 | SHA256:CC95904F8880B5D833381355305C749F71B1CFC3135CABEB44F70B650A46A7CD | |||
| 7856 | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | C:\Windows\Branding\shellbrd\eddb19405b7ce1 | text | |
MD5:151D61347B5DAC6B5D0477D0EF03517A | SHA256:0CDC328DD7885E70C02108B935CDD2573E3771B86D531EAF440BE4666D89059C | |||
| 7856 | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | C:\Windows\Branding\shellbrd\backgroundTaskHost.exe | executable | |
MD5:78C802B7CED01A823BE54EDC23110F64 | SHA256:DD4A987DD3A15DDE96899705CA05061F4C77FB26F681C091D1B1A85D943E6C55 | |||
| 7856 | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | C:\Windows\ShellExperiences\26c12092da979c | text | |
MD5:C7C314FF0F39B7697D5883E511ACE3C2 | SHA256:1F1FF6CE61F44ABF443CCEFC54CDF6E91EFE9AFEAB5D4F091B5BD4C9F6BE34A8 | |||
| 7856 | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | C:\Recovery\Logs\ee2ad38f3d4382 | text | |
MD5:2D536654C2BB583B2F29EDB8020F54D3 | SHA256:37E6F616DEDFDED94BD1975BDEAC1BEA7B97F9D8E7CAACCE197B9C21A4ED01BB | |||
| 7856 | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | C:\Windows\ShellExperiences\ctfmon.exe | executable | |
MD5:78C802B7CED01A823BE54EDC23110F64 | SHA256:DD4A987DD3A15DDE96899705CA05061F4C77FB26F681C091D1B1A85D943E6C55 | |||
| 7856 | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | C:\Recovery\OEM\ApplicationFrameHost.exe | executable | |
MD5:78C802B7CED01A823BE54EDC23110F64 | SHA256:DD4A987DD3A15DDE96899705CA05061F4C77FB26F681C091D1B1A85D943E6C55 | |||
| 7856 | dd4a987dd3a15dde96899705ca05061f4c77fb26f681c091d1b1a85d943e6c55.exe | C:\Recovery\Logs\Registry.exe | executable | |
MD5:78C802B7CED01A823BE54EDC23110F64 | SHA256:DD4A987DD3A15DDE96899705CA05061F4C77FB26F681C091D1B1A85D943E6C55 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
48
DNS requests
14
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
8468 | ApplicationFrameHost.exe | GET | — | 46.3.197.86:80 | http://46.3.197.86/Dlecdnpacket/PipevmUniversal2/4Private/jsWordpress/PrivateFlower7Local/videovmbasecentraldownloads.php?rYtCoexlROEtg18mJ5gPvzqYcPpVLET=A3ereB742Nm0Q8F&SxsUmiM1sUkZ=cZN4msnWQHH7mWiNzIeKTDYV8z&rn9KbiEaxY5oQb9=qk&414eeb0107326dd986561ec27a2ee7c8=4196fc1763b756c5b765c04c7dbb8cfd&372b0e0063cedabcf31f231235853905=QMjBjN2QTOxUWN4YTOwI2MjhDN1YDZ0EmMhVDNxUGZxM2M4gDM4AjM&rYtCoexlROEtg18mJ5gPvzqYcPpVLET=A3ereB742Nm0Q8F&SxsUmiM1sUkZ=cZN4msnWQHH7mWiNzIeKTDYV8z&rn9KbiEaxY5oQb9=qk | unknown | — | — | malicious |
8468 | ApplicationFrameHost.exe | GET | — | 46.3.197.86:80 | http://46.3.197.86/Dlecdnpacket/PipevmUniversal2/4Private/jsWordpress/PrivateFlower7Local/videovmbasecentraldownloads.php?rYtCoexlROEtg18mJ5gPvzqYcPpVLET=A3ereB742Nm0Q8F&SxsUmiM1sUkZ=cZN4msnWQHH7mWiNzIeKTDYV8z&rn9KbiEaxY5oQb9=qk&414eeb0107326dd986561ec27a2ee7c8=4196fc1763b756c5b765c04c7dbb8cfd&372b0e0063cedabcf31f231235853905=QMjBjN2QTOxUWN4YTOwI2MjhDN1YDZ0EmMhVDNxUGZxM2M4gDM4AjM&rYtCoexlROEtg18mJ5gPvzqYcPpVLET=A3ereB742Nm0Q8F&SxsUmiM1sUkZ=cZN4msnWQHH7mWiNzIeKTDYV8z&rn9KbiEaxY5oQb9=qk | unknown | — | — | malicious |
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
8284 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8284 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
8284 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8284 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8284 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8284 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
8284 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8284 | SIHClient.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
8284 | SIHClient.exe | 23.38.73.129:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
8284 | SIHClient.exe | 20.3.187.198:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8468 | ApplicationFrameHost.exe | 46.3.197.86:80 | — | Adman LLC | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
8468 | ApplicationFrameHost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
8468 | ApplicationFrameHost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
8468 | ApplicationFrameHost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
8468 | ApplicationFrameHost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
3300 | ApplicationFrameHost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
3300 | ApplicationFrameHost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
3300 | ApplicationFrameHost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
3300 | ApplicationFrameHost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
7820 | ApplicationFrameHost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |