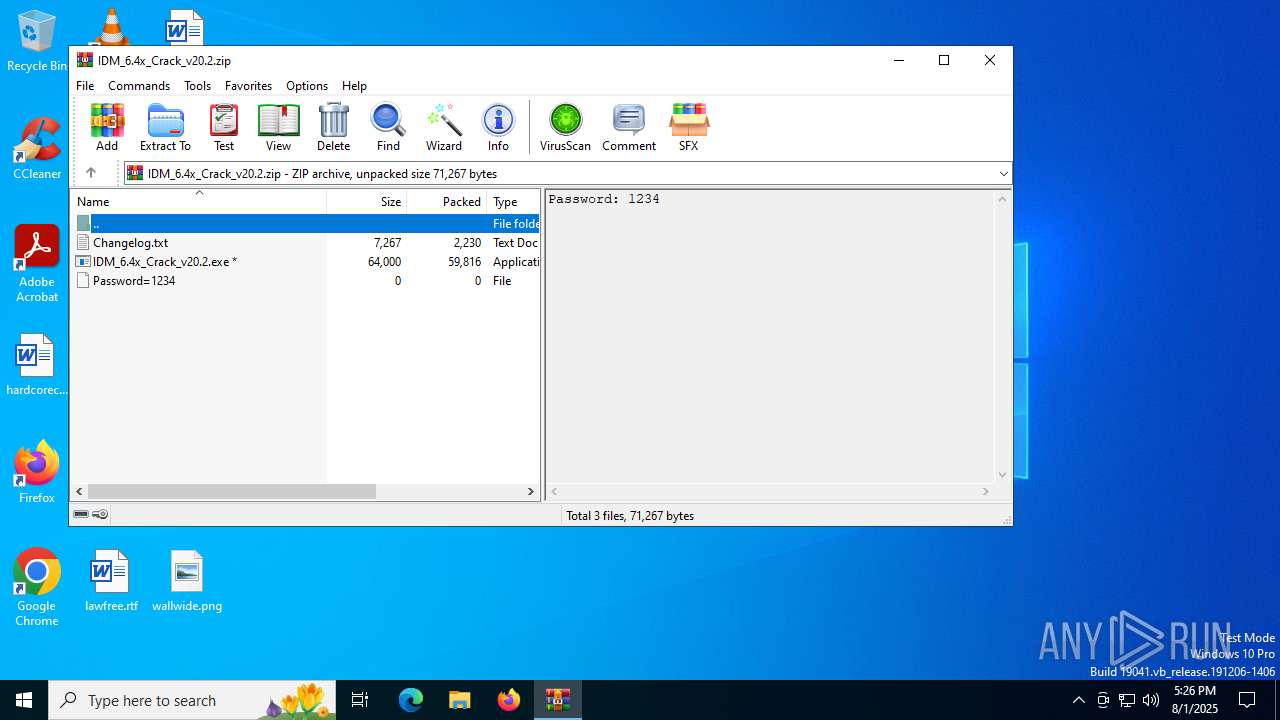
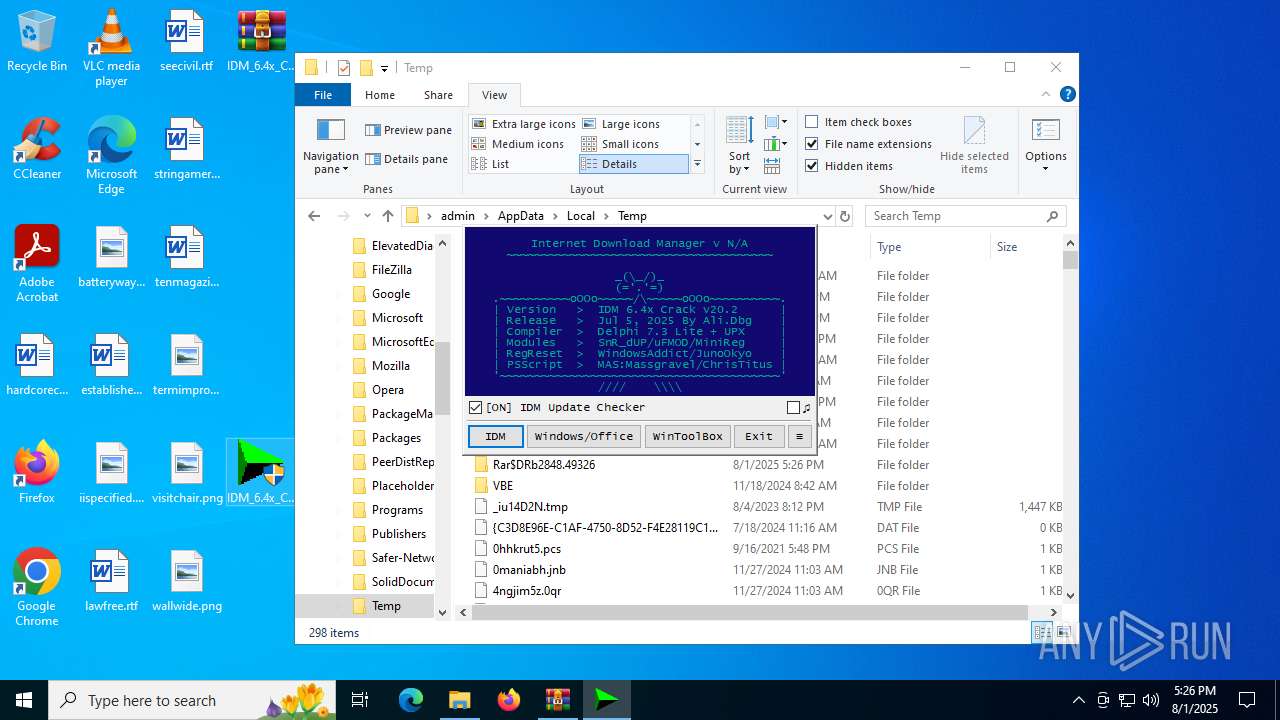
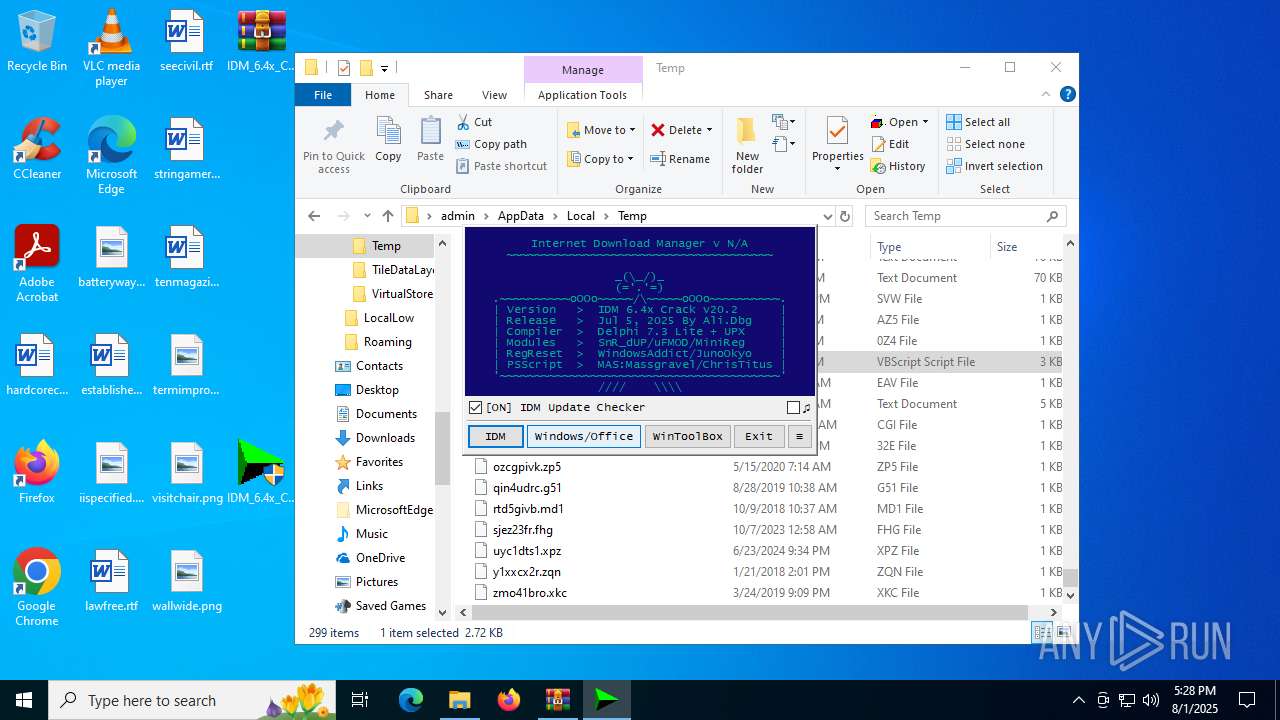
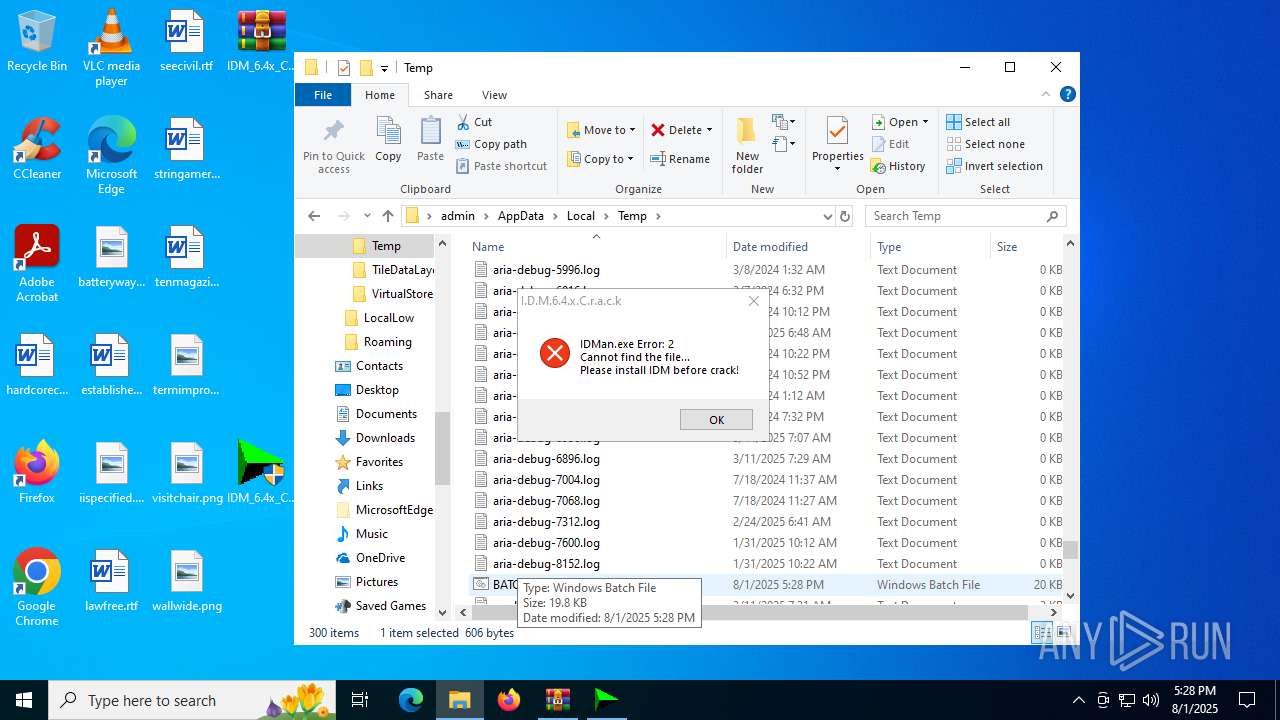
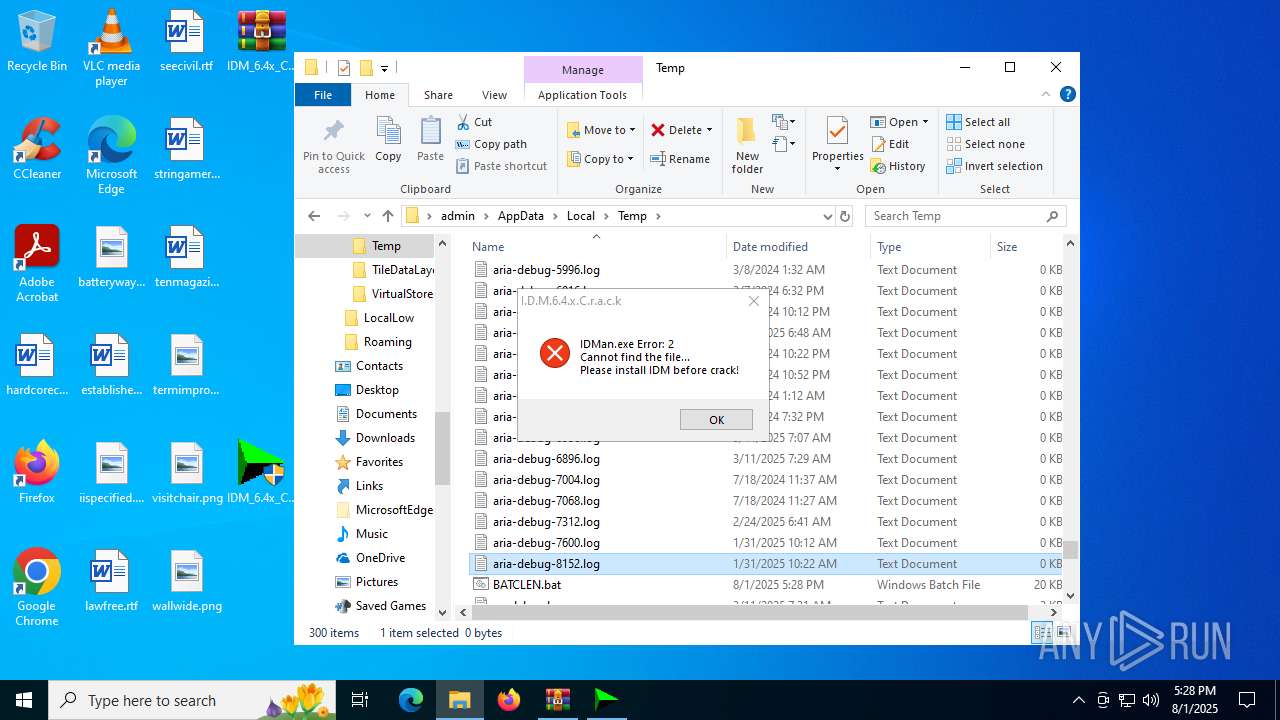
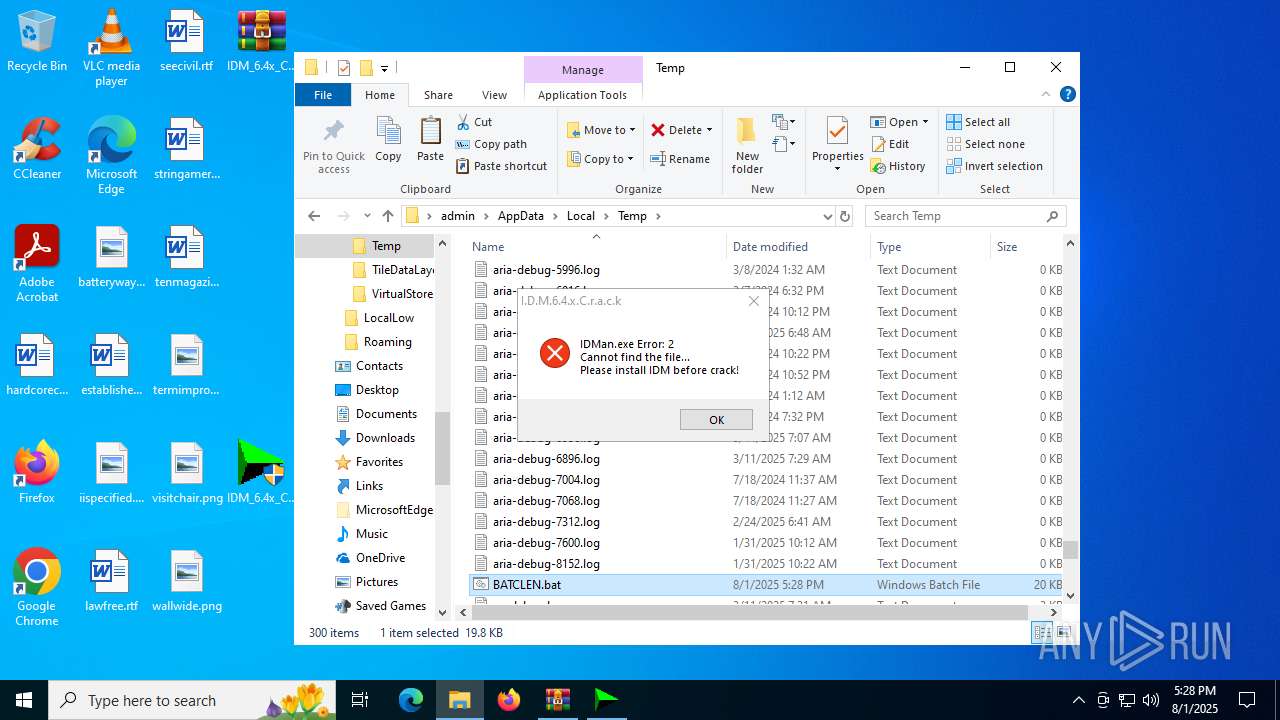
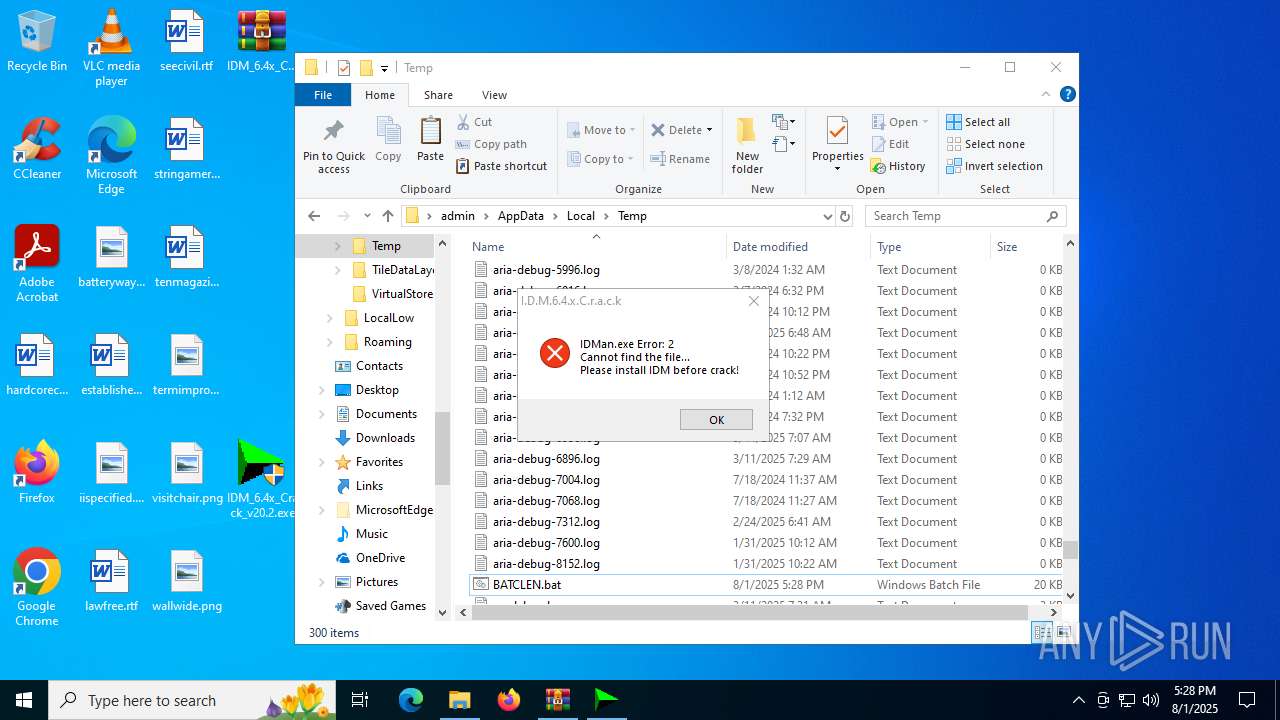
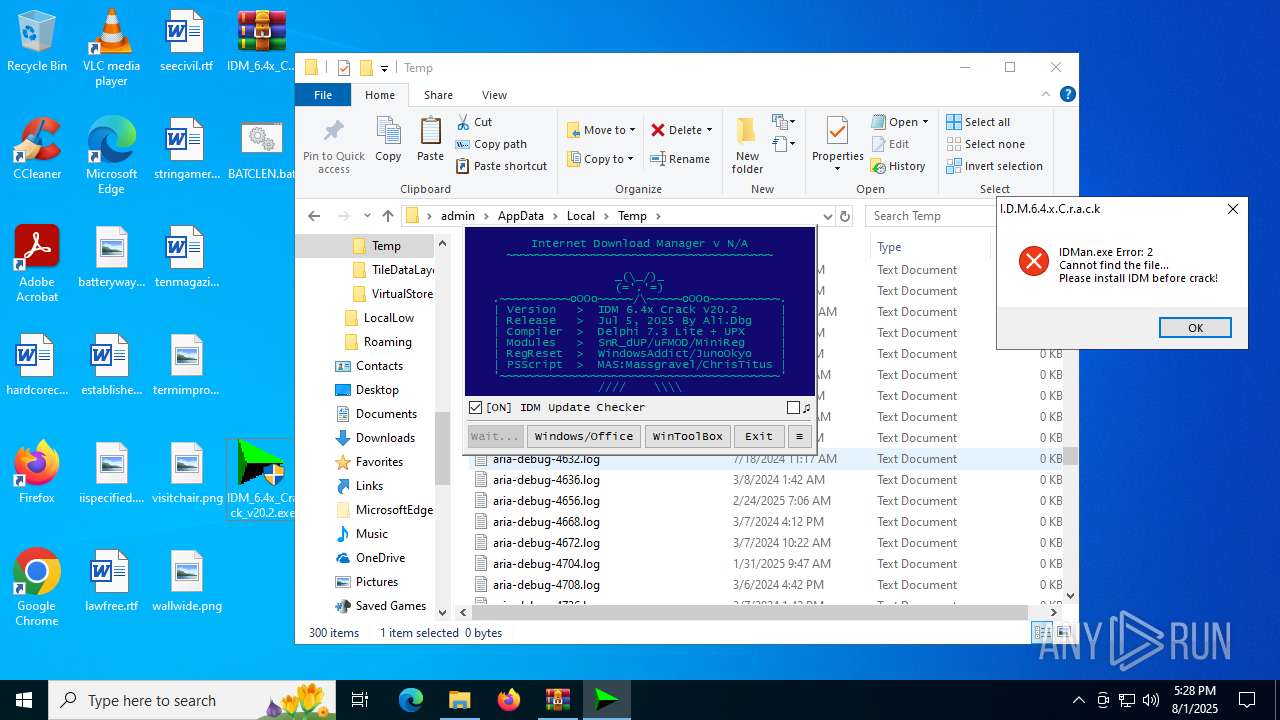
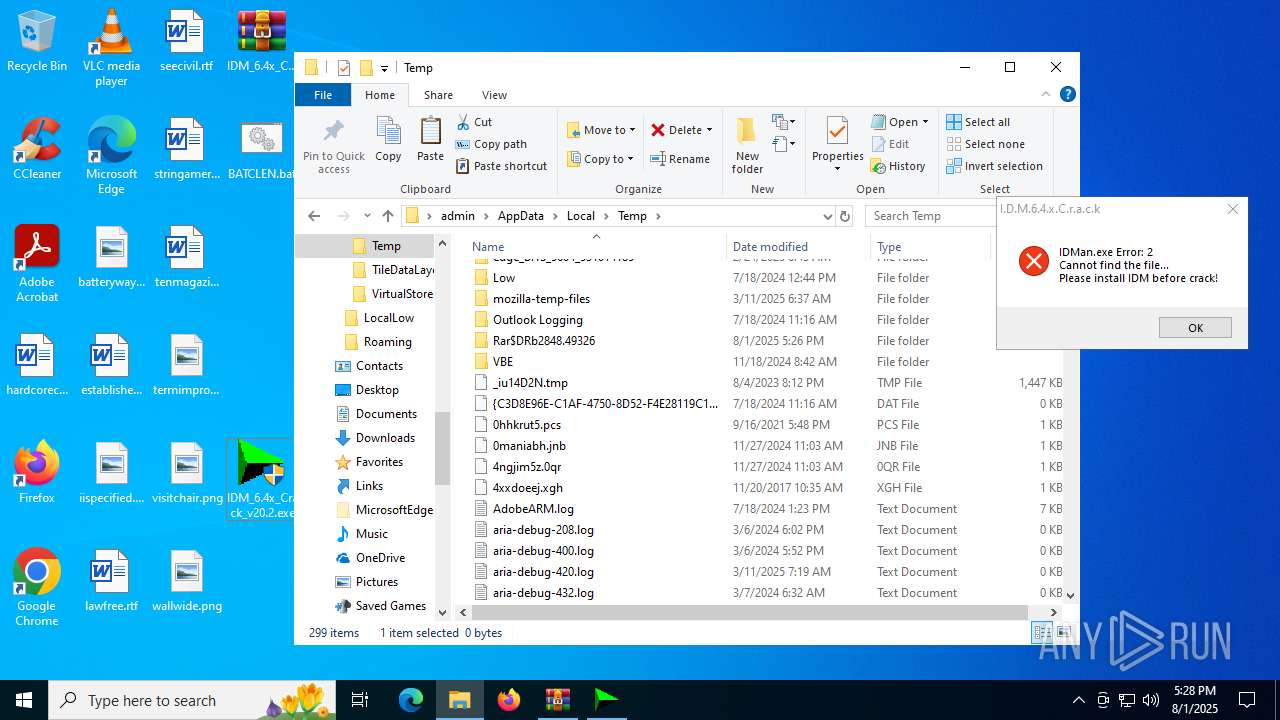
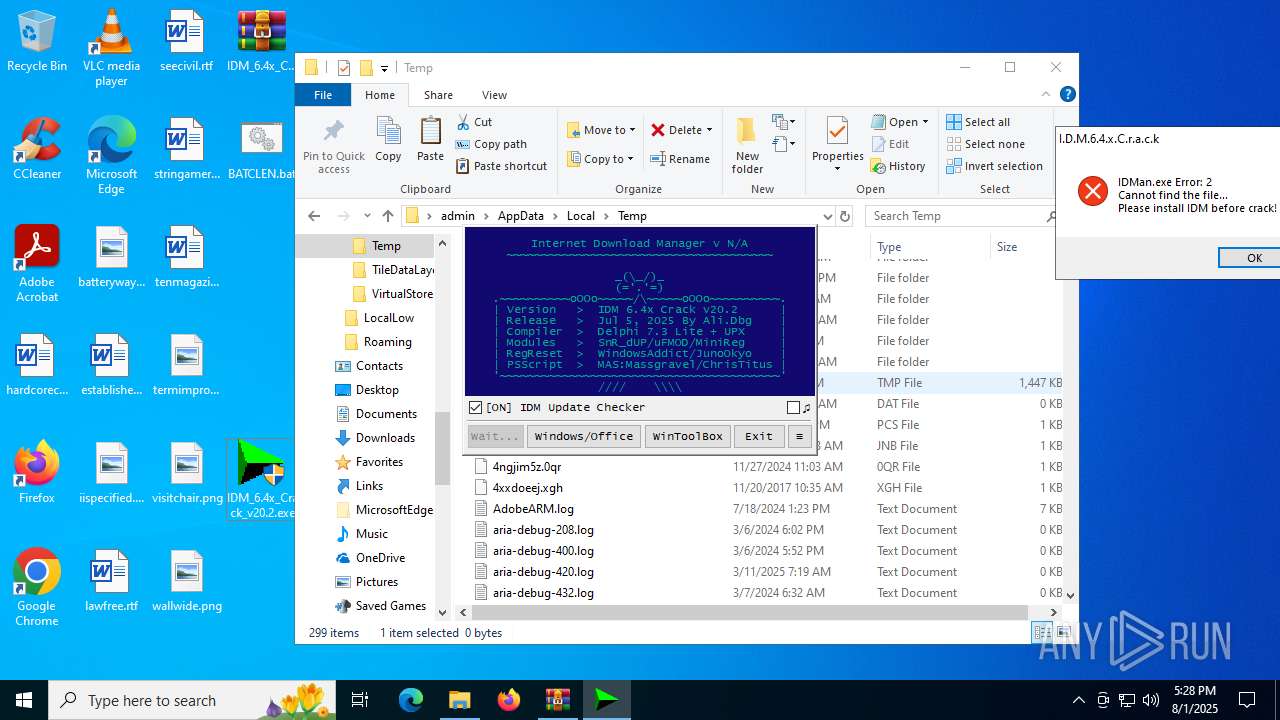
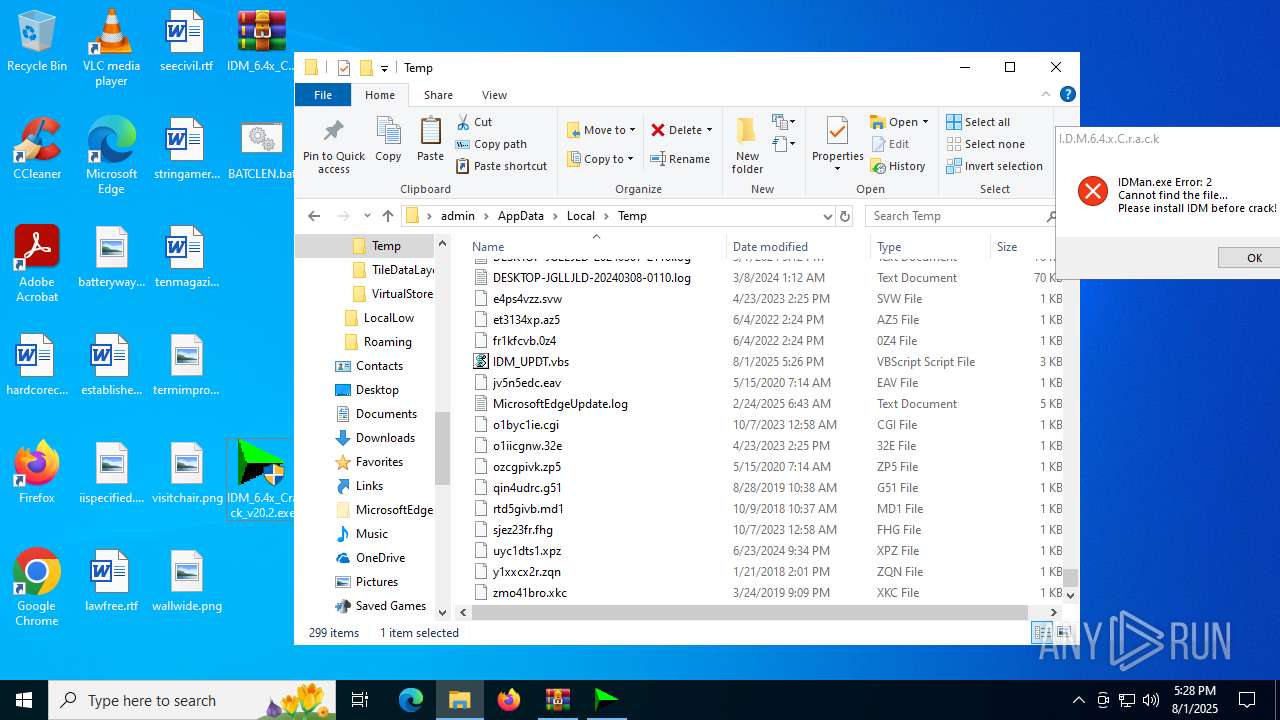
| File name: | IDM_6.4x_Crack_v20.2.zip |
| Full analysis: | https://app.any.run/tasks/fc2a4d4b-5b73-415a-a697-39464d416599 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2025, 17:26:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | DF11314121570C3420D0E161366CBC12 |
| SHA1: | 47E2546D9EB4591ECA512ADB145D1BD0B2BD2AB0 |
| SHA256: | DD3C5782032EF7244DF8F00107B1A9035720EA843F8482429F1C312DA004A276 |
| SSDEEP: | 1536:LbB+v3vnJBFeOKv4PE2/4On8zYp/K9obakAKzgW:L0nJDyv4PERYRK9obaRTW |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 6796)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 6796)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 6796)
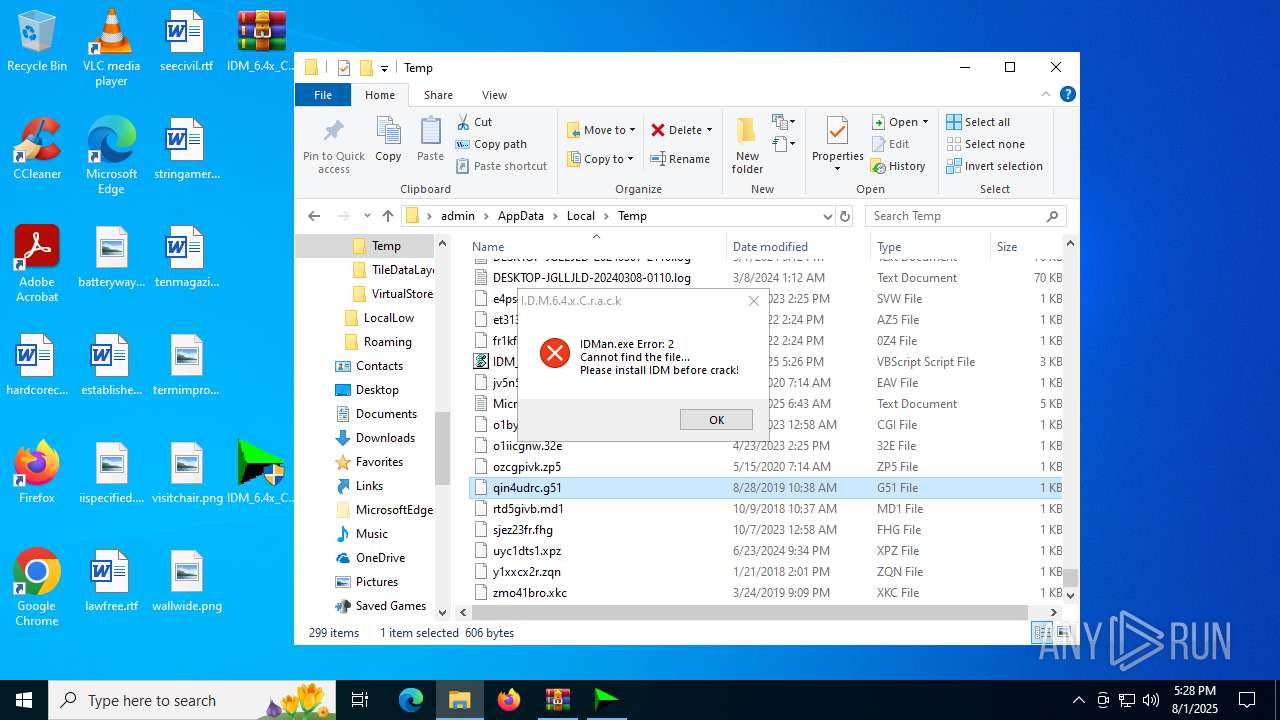
Deletes a file (SCRIPT)
- wscript.exe (PID: 6796)
SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2848)
The process executes VB scripts
- IDM_6.4x_Crack_v20.2.exe (PID: 6180)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6796)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 6796)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 6796)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 6796)
Uses REG/REGEDIT.EXE to modify registry
- IDM_6.4x_Crack_v20.2.exe (PID: 6180)
- cmd.exe (PID: 4460)
- cmd.exe (PID: 1160)
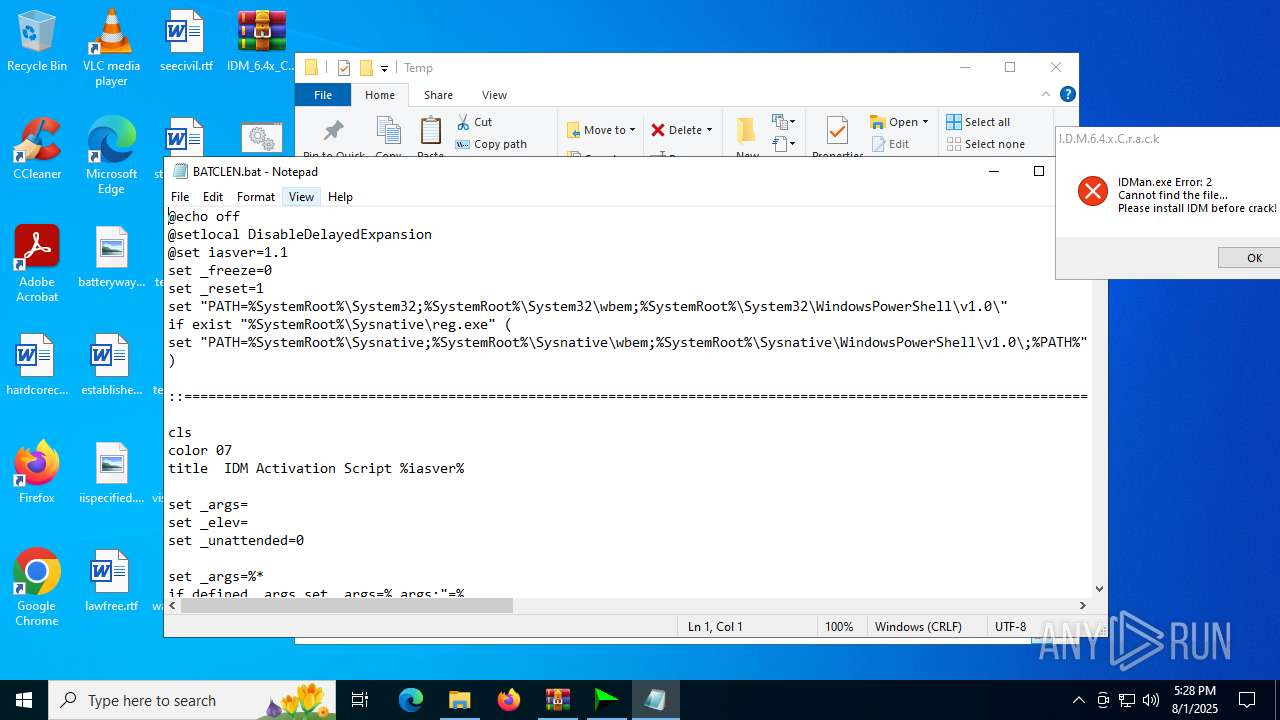
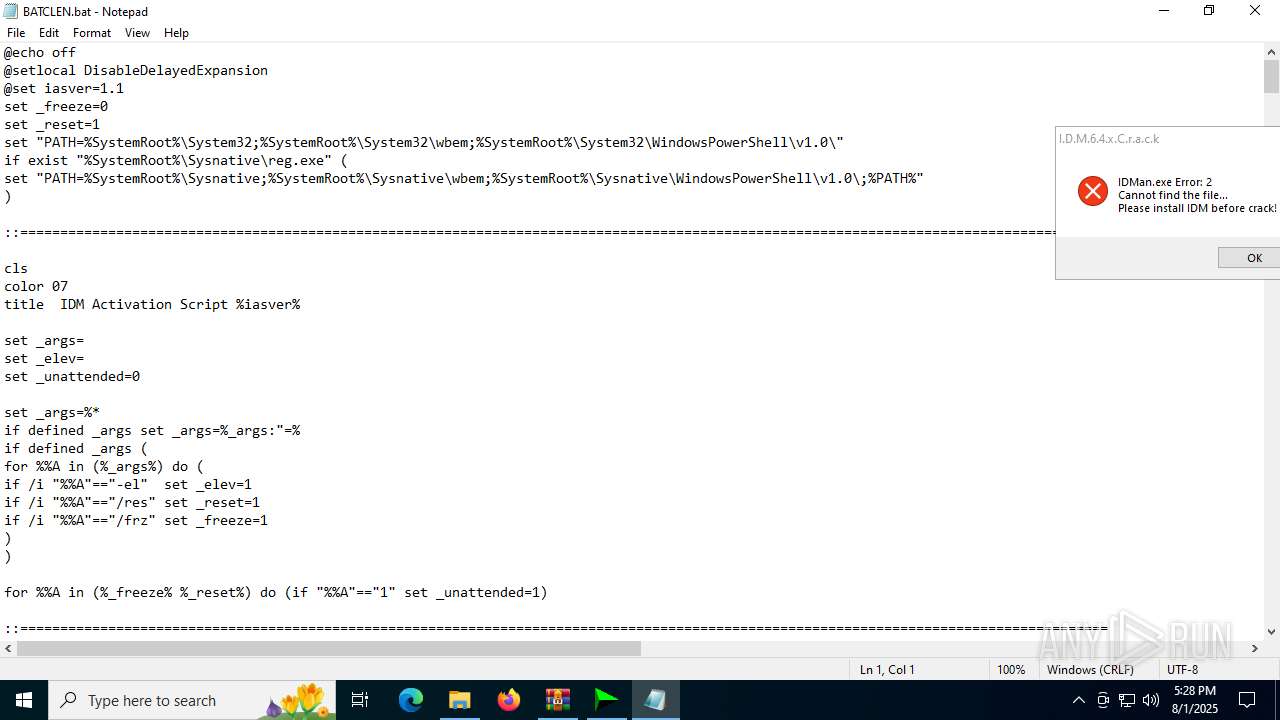
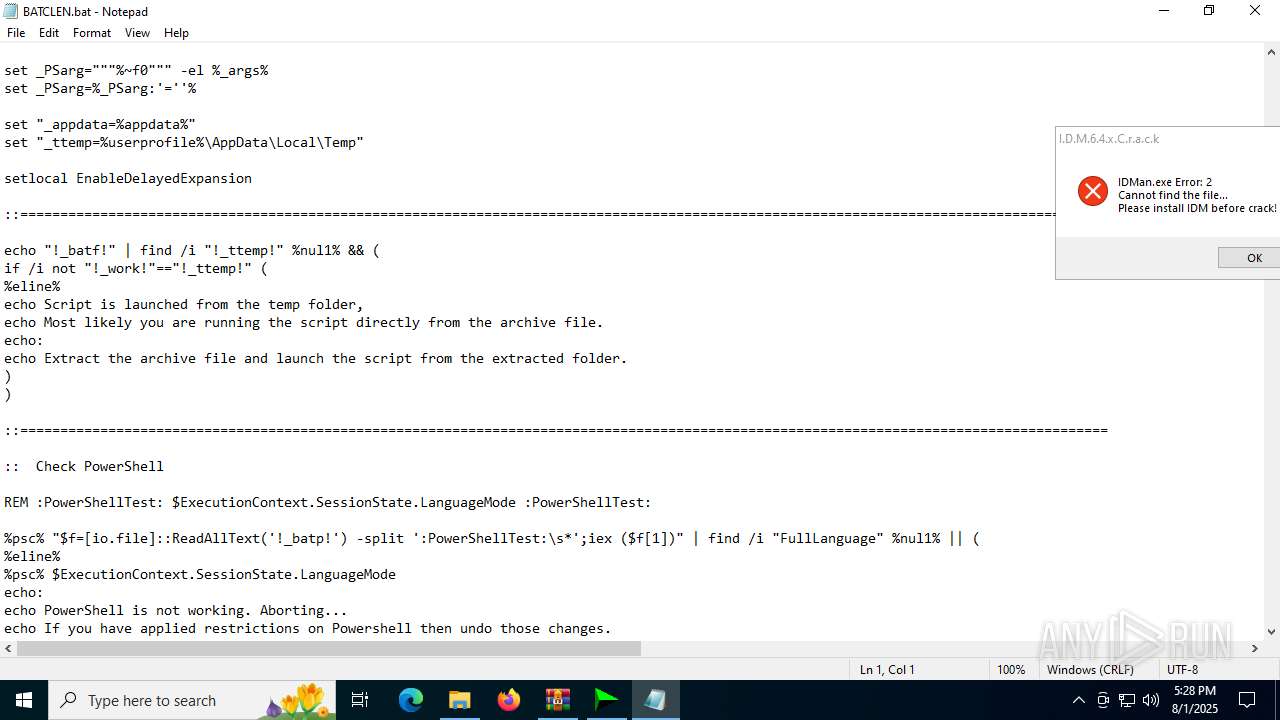
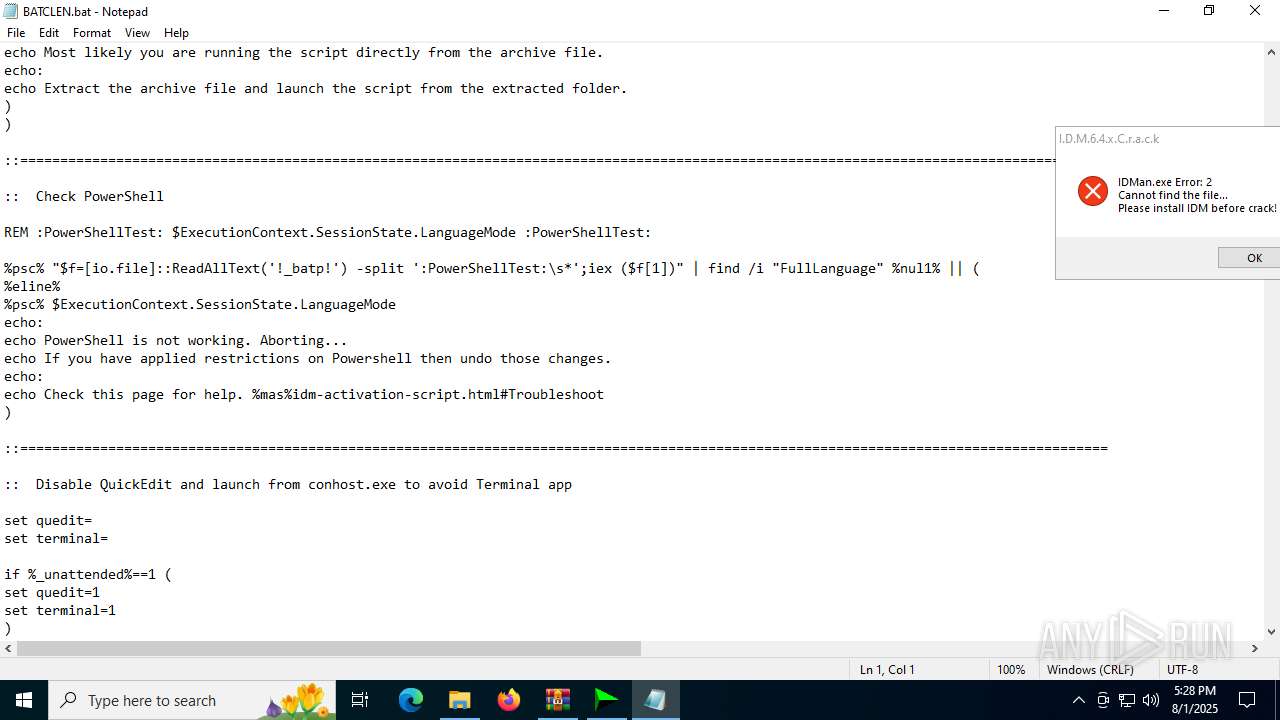
Executing commands from a ".bat" file
- IDM_6.4x_Crack_v20.2.exe (PID: 6180)
- cmd.exe (PID: 4460)
Starts CMD.EXE for commands execution
- IDM_6.4x_Crack_v20.2.exe (PID: 6180)
- cmd.exe (PID: 4460)
- cmd.exe (PID: 1828)
Application launched itself
- cmd.exe (PID: 4460)
- cmd.exe (PID: 1828)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 4460)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4560)
- cmd.exe (PID: 828)
- cmd.exe (PID: 4460)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 4460)
Hides command output
- cmd.exe (PID: 828)
- cmd.exe (PID: 1160)
Starts application with an unusual extension
- cmd.exe (PID: 4460)
INFO
Manual execution by a user
- IDM_6.4x_Crack_v20.2.exe (PID: 3100)
- IDM_6.4x_Crack_v20.2.exe (PID: 6180)
- notepad++.exe (PID: 1636)
- notepad.exe (PID: 3672)
Creates files or folders in the user directory
- IDM_6.4x_Crack_v20.2.exe (PID: 6180)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2848)
Checks supported languages
- IDM_6.4x_Crack_v20.2.exe (PID: 6180)
- chcp.com (PID: 6676)
Reads the computer name
- IDM_6.4x_Crack_v20.2.exe (PID: 6180)
Create files in a temporary directory
- IDM_6.4x_Crack_v20.2.exe (PID: 6180)
- reg.exe (PID: 1576)
Checks proxy server information
- wscript.exe (PID: 6796)
- slui.exe (PID: 5884)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6320)
- powershell.exe (PID: 2356)
Checks operating system version
- cmd.exe (PID: 4460)
Reads the software policy settings
- slui.exe (PID: 5884)
Changes the display of characters in the console
- cmd.exe (PID: 4460)
Reads security settings of Internet Explorer
- notepad.exe (PID: 3672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:07:05 16:10:10 |
| ZipCRC: | 0xc46c2076 |
| ZipCompressedSize: | 59816 |
| ZipUncompressedSize: | 64000 |
| ZipFileName: | IDM_6.4x_Crack_v20.2.exe |
Total processes
205
Monitored processes
60
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | reg query "HKU\S-1-5-21-1693682860-607145093-2874071422-1001\Software\DownloadManager" /v ExePath | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 828 | C:\WINDOWS\system32\cmd.exe /c powershell.exe "([System.Security.Principal.NTAccount](Get-WmiObject -Class Win32_ComputerSystem).UserName).Translate([System.Security.Principal.SecurityIdentifier]).Value" 2>nul | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | reg delete HKU\S-1-5-21-1693682860-607145093-2874071422-1001\IAS_TEST /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "C:\Users\admin\AppData\Local\Temp\BATCLEN.bat" " | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1160 | C:\WINDOWS\system32\cmd.exe /c reg query "HKU\S-1-5-21-1693682860-607145093-2874071422-1001\Software\DownloadManager" /v ExePath 2>nul | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1212 | reg query "HKCU\Console" /v ForceV2 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1332 | reg add HKCU\IAS_TEST | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | REG ADD "HKCU\Software\DownloadManager" /v "nLst" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 679
Read events
27 626
Write events
38
Delete events
15
Modification events
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\IDM_6.4x_Crack_v20.2.zip | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
3
Text files
24
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6796 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:8EAC3AD6C64E368D40135EA3A7B01E63 | SHA256:C7A7AFDEEA81BDC5828F20FFA127E40A52F6FB81CF144A0CD71CD07C7277D6B5 | |||
| 1636 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
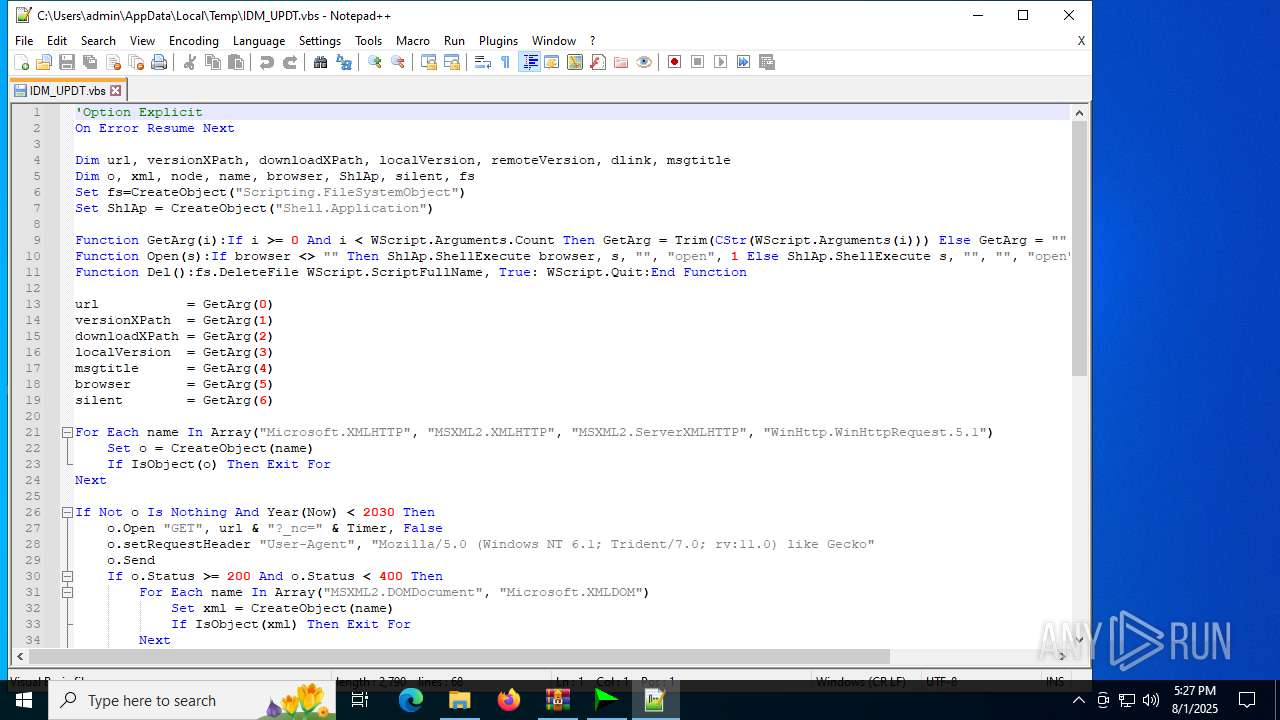
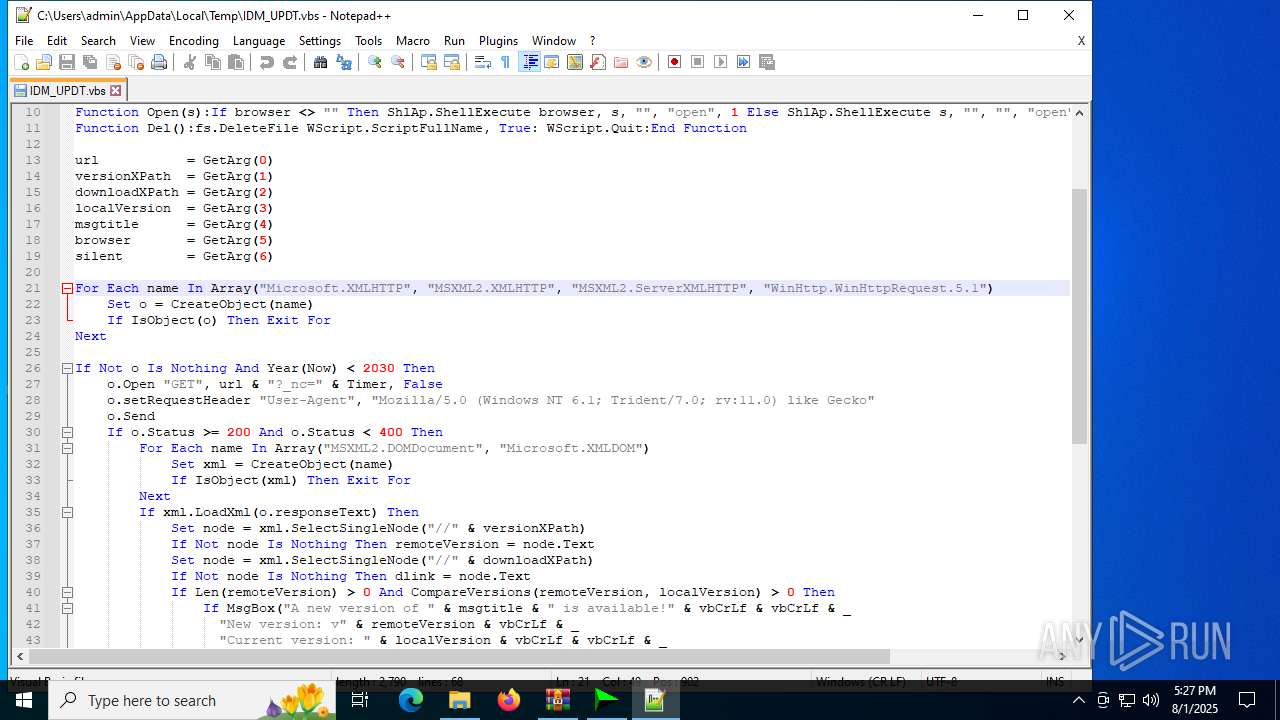
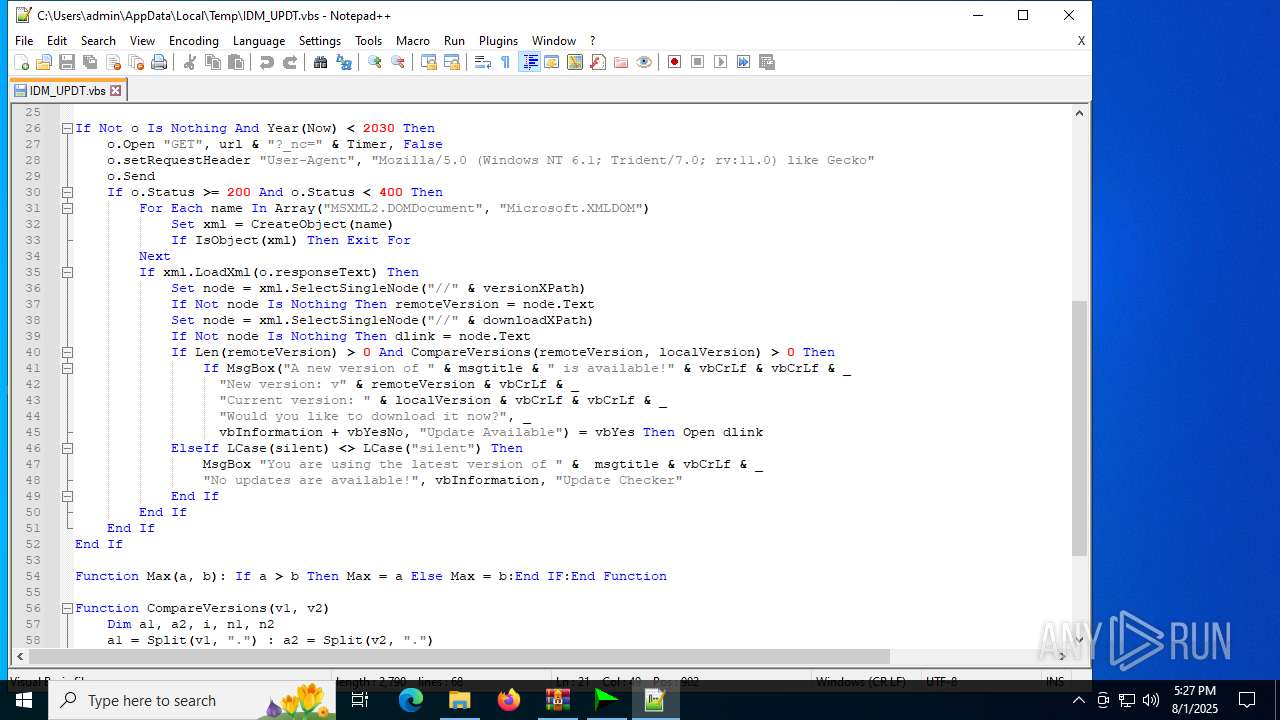
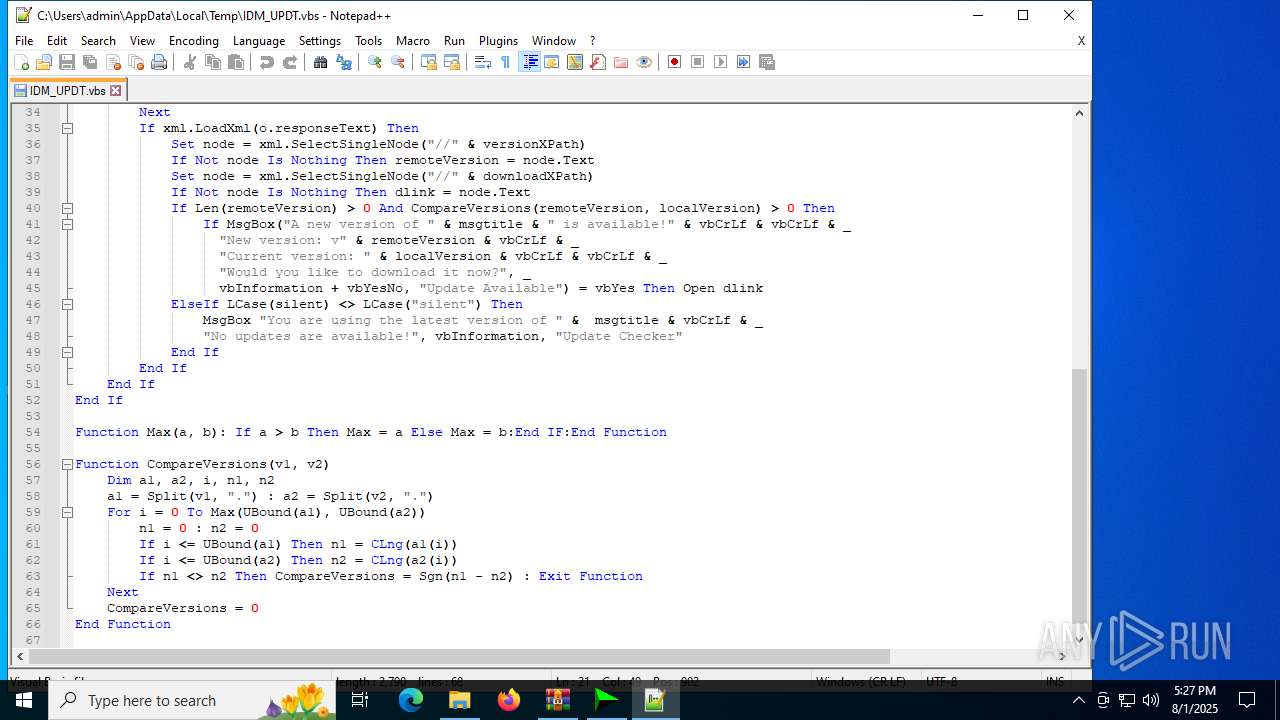
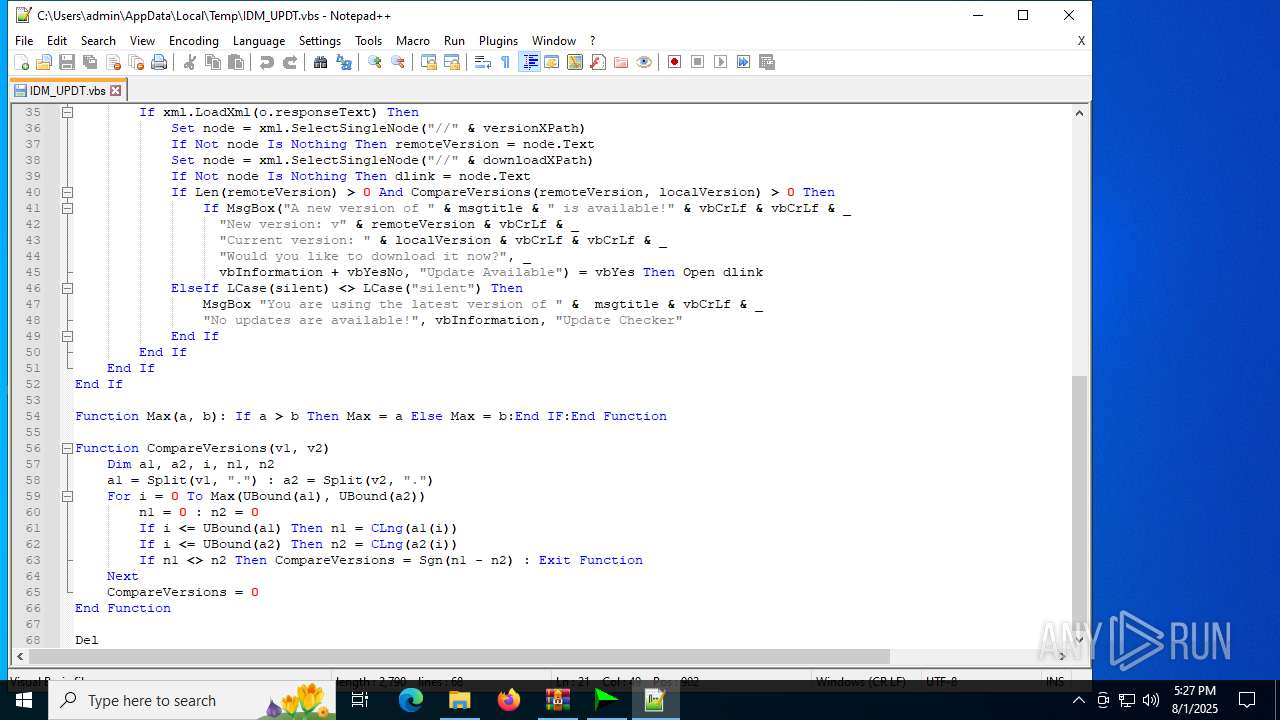
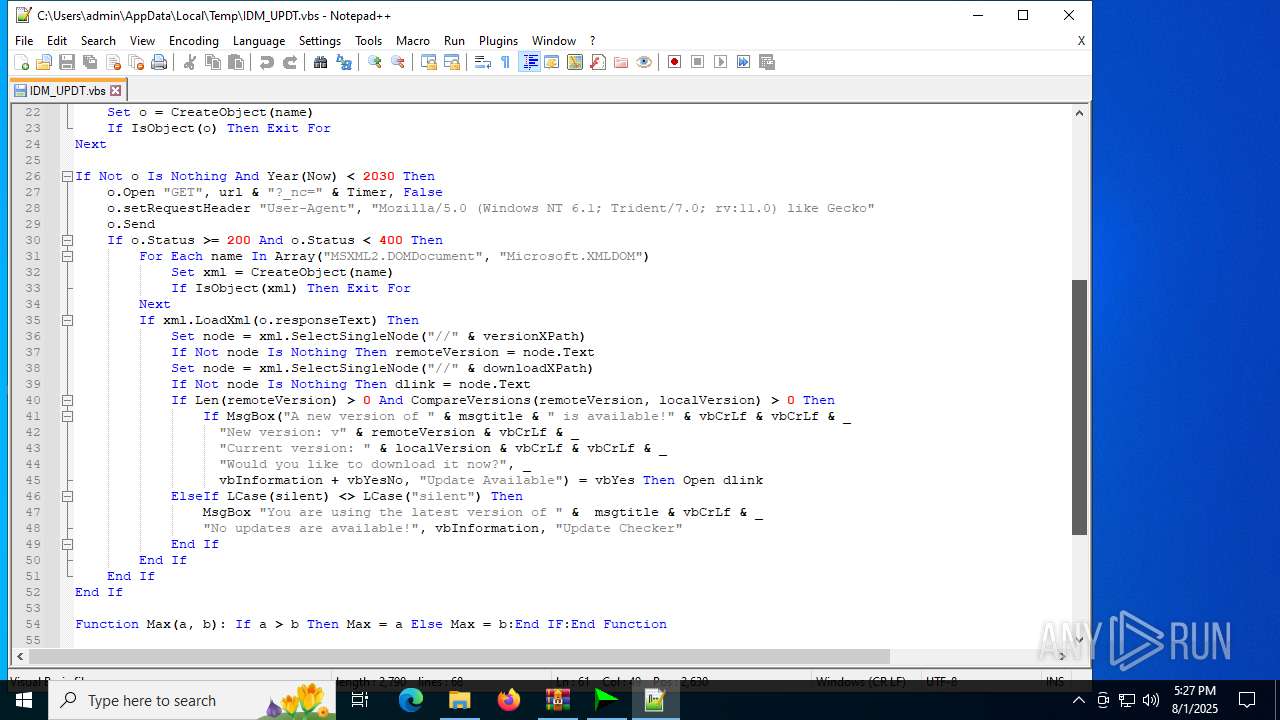
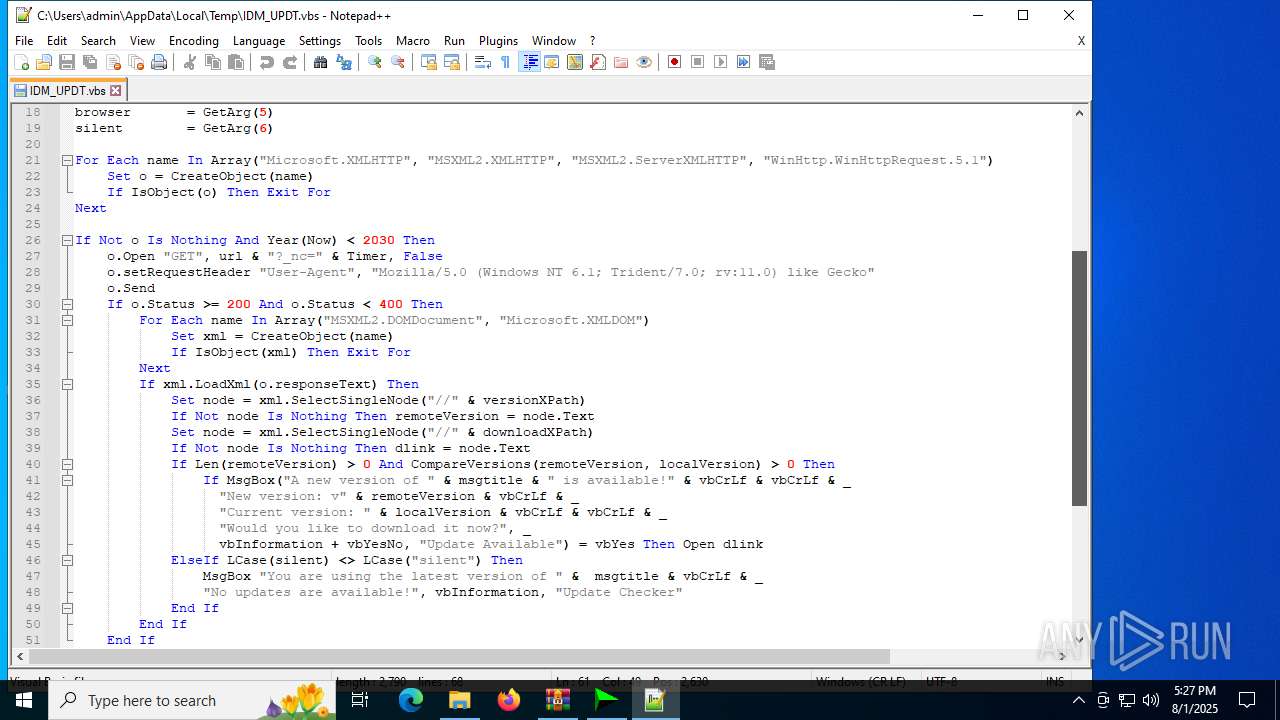
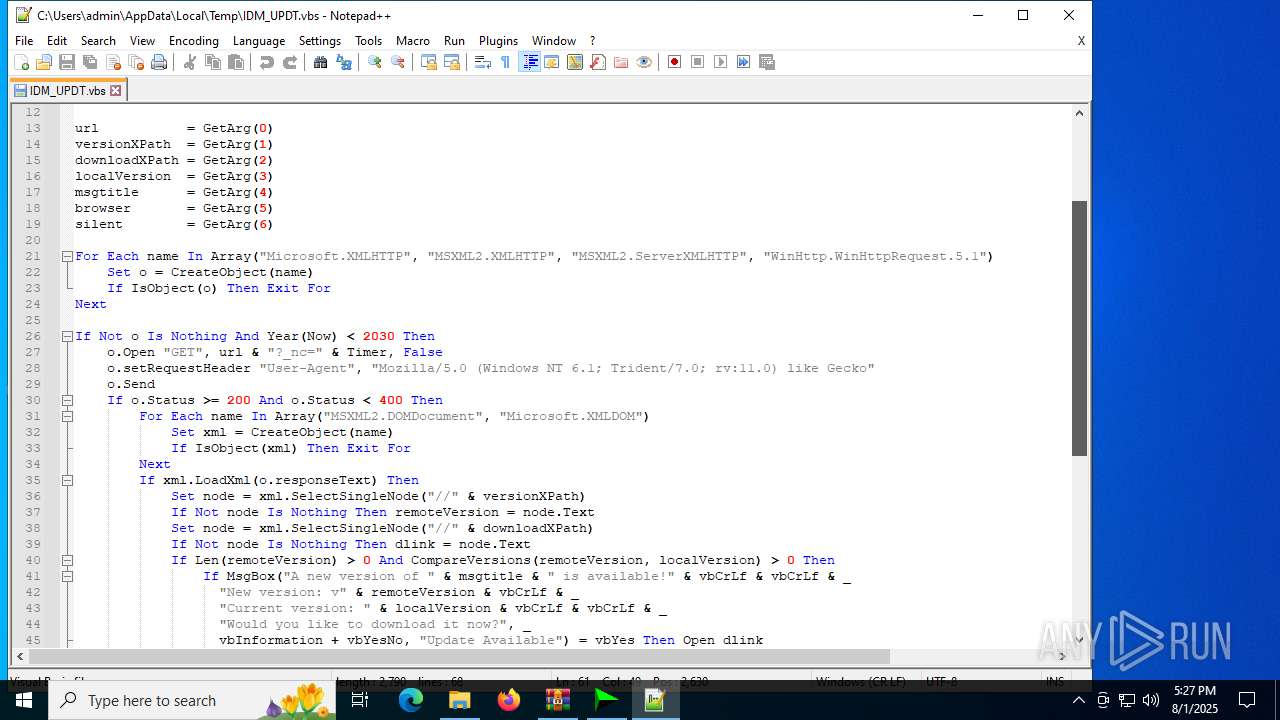
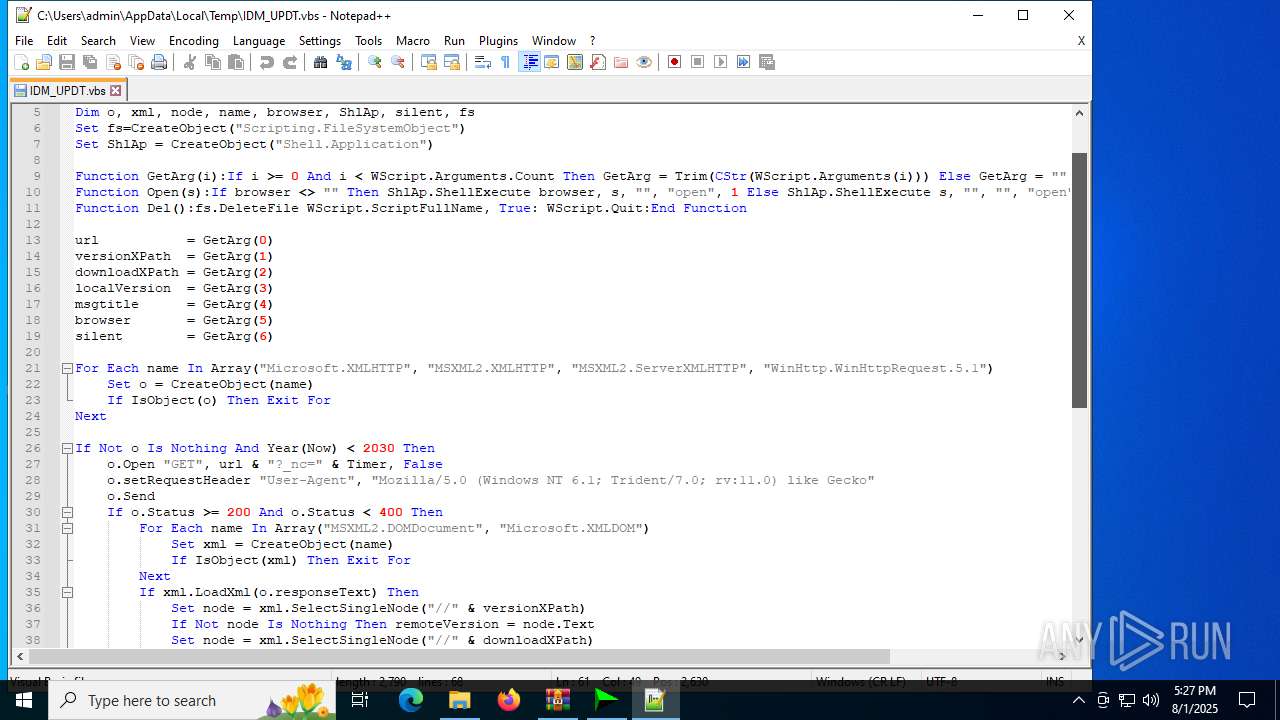
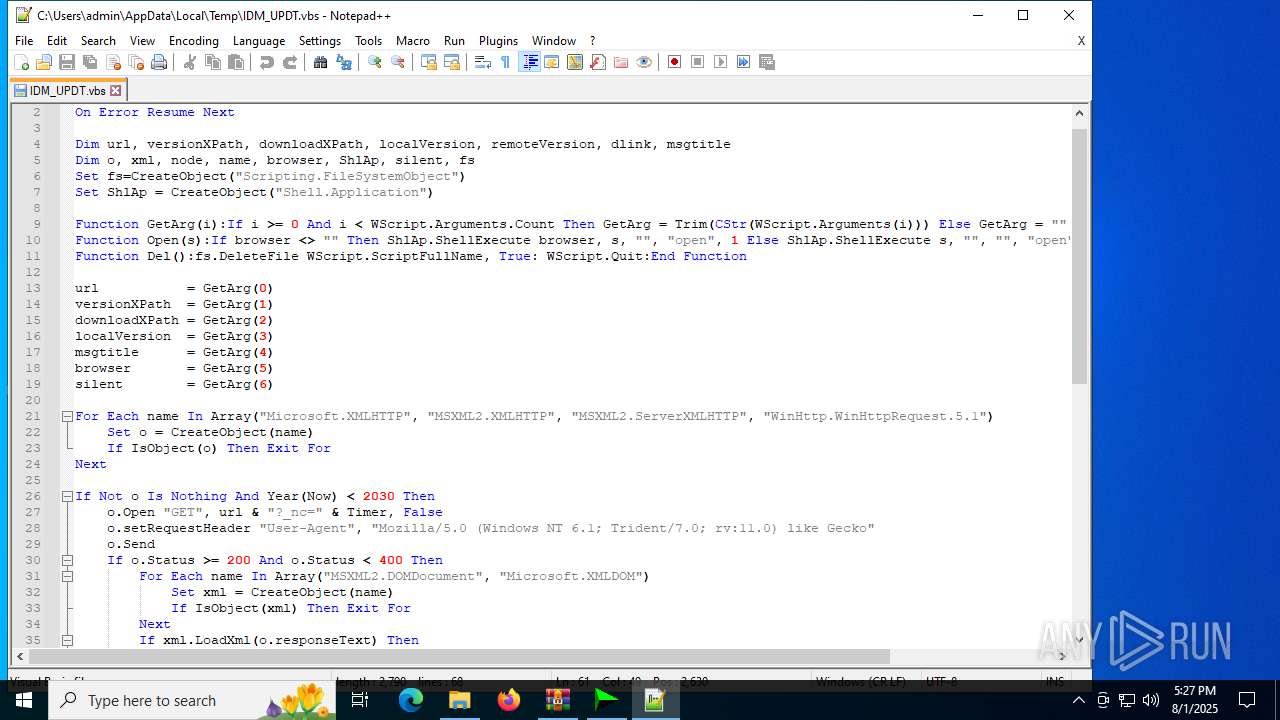
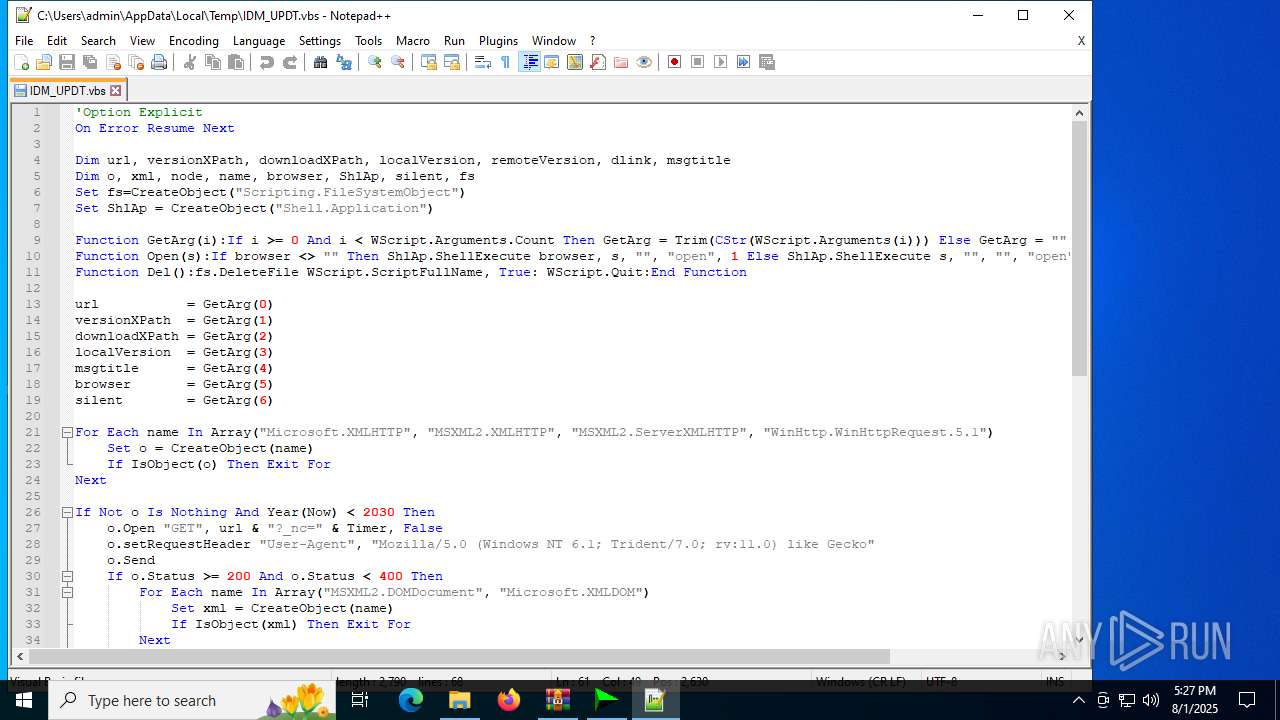
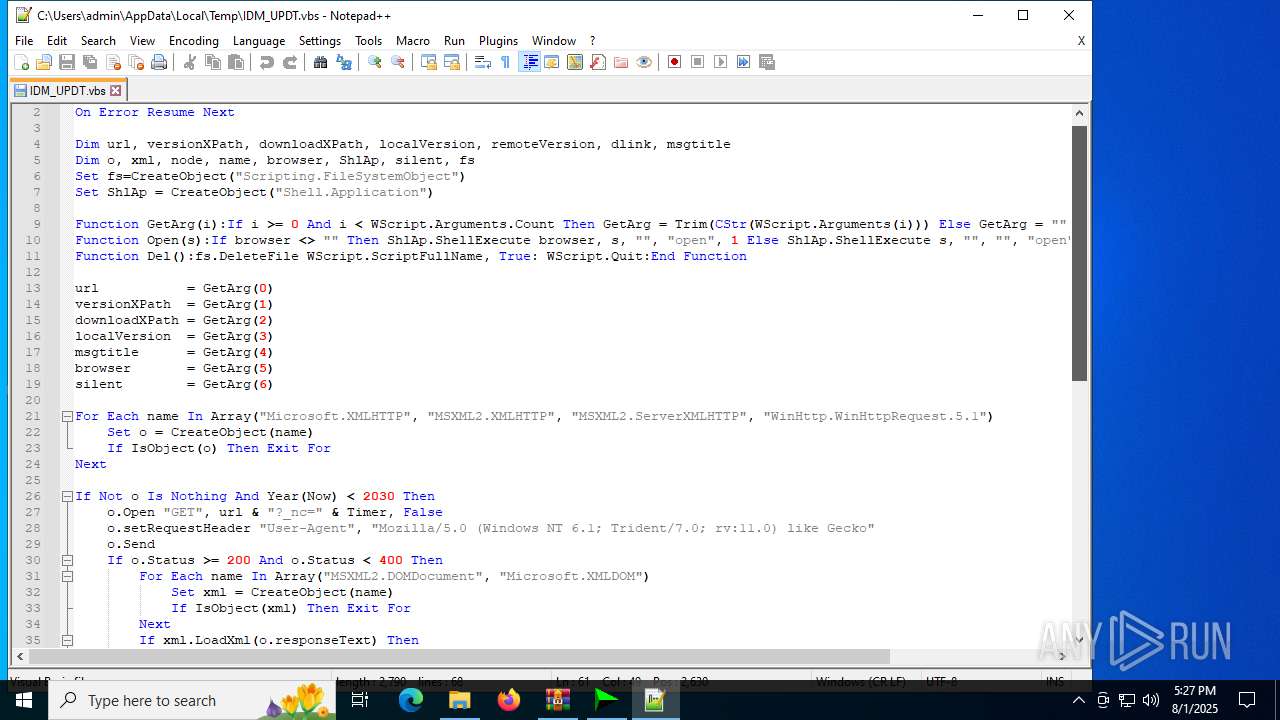
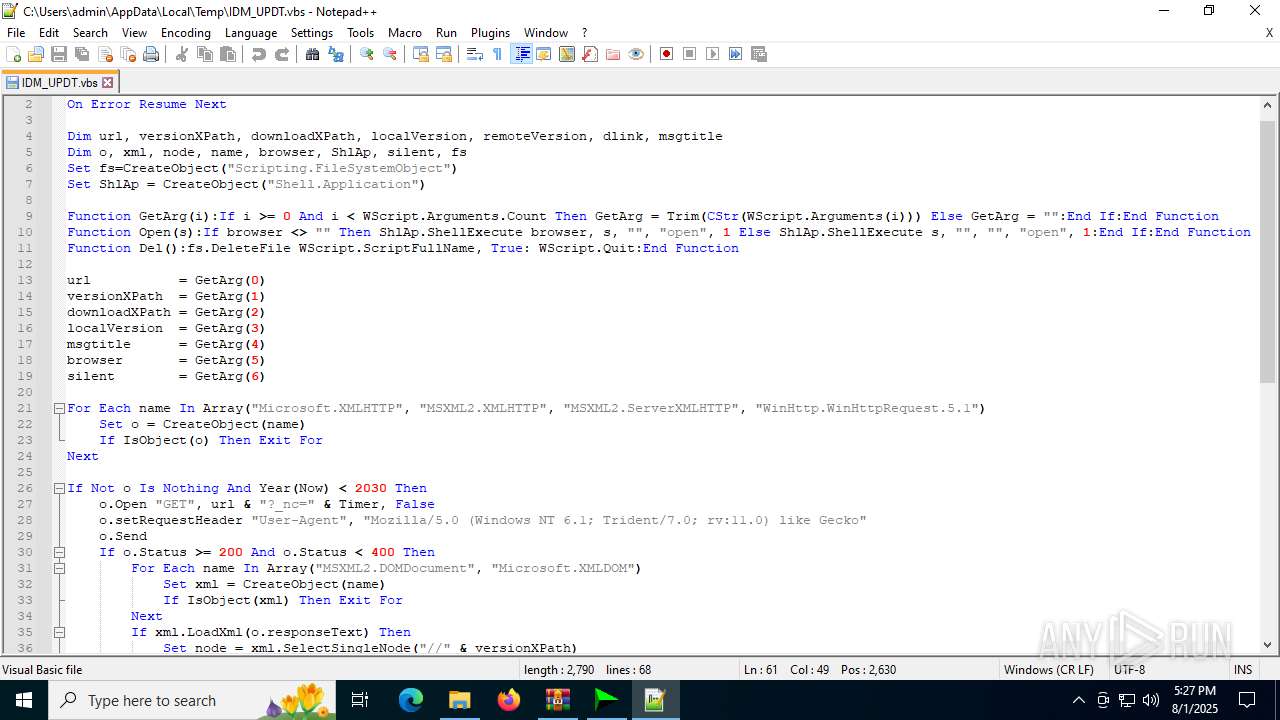
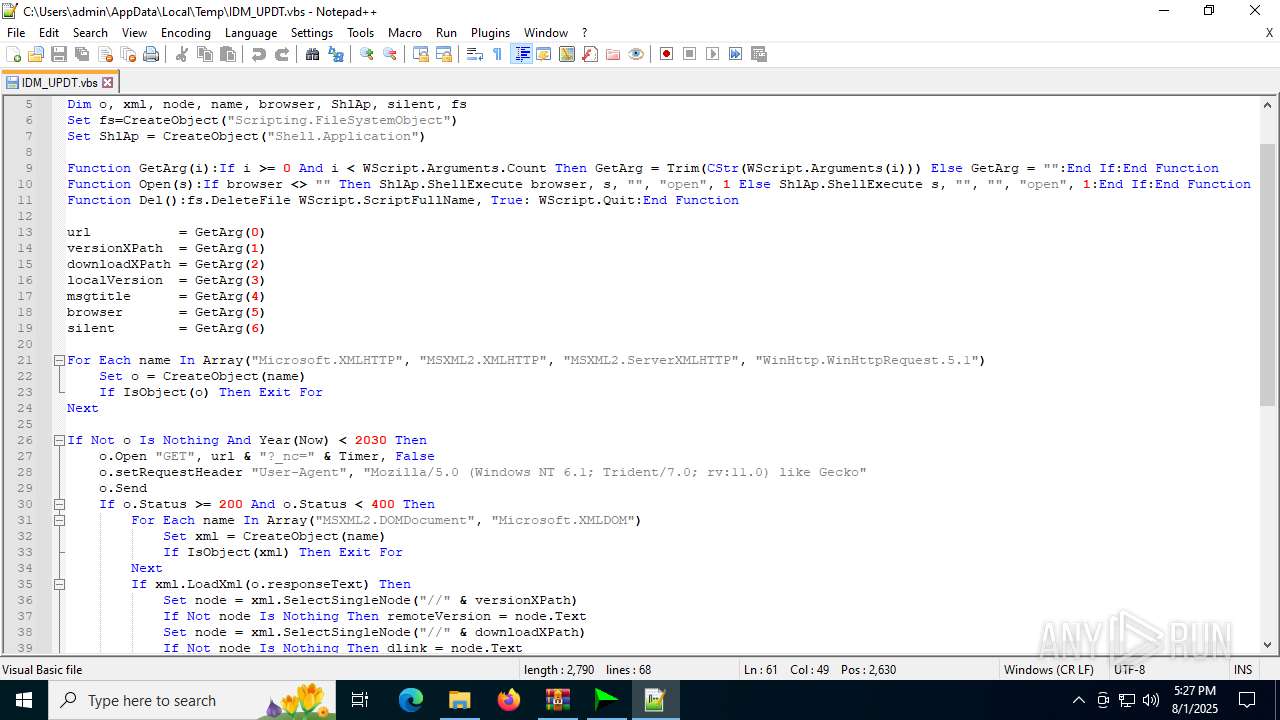
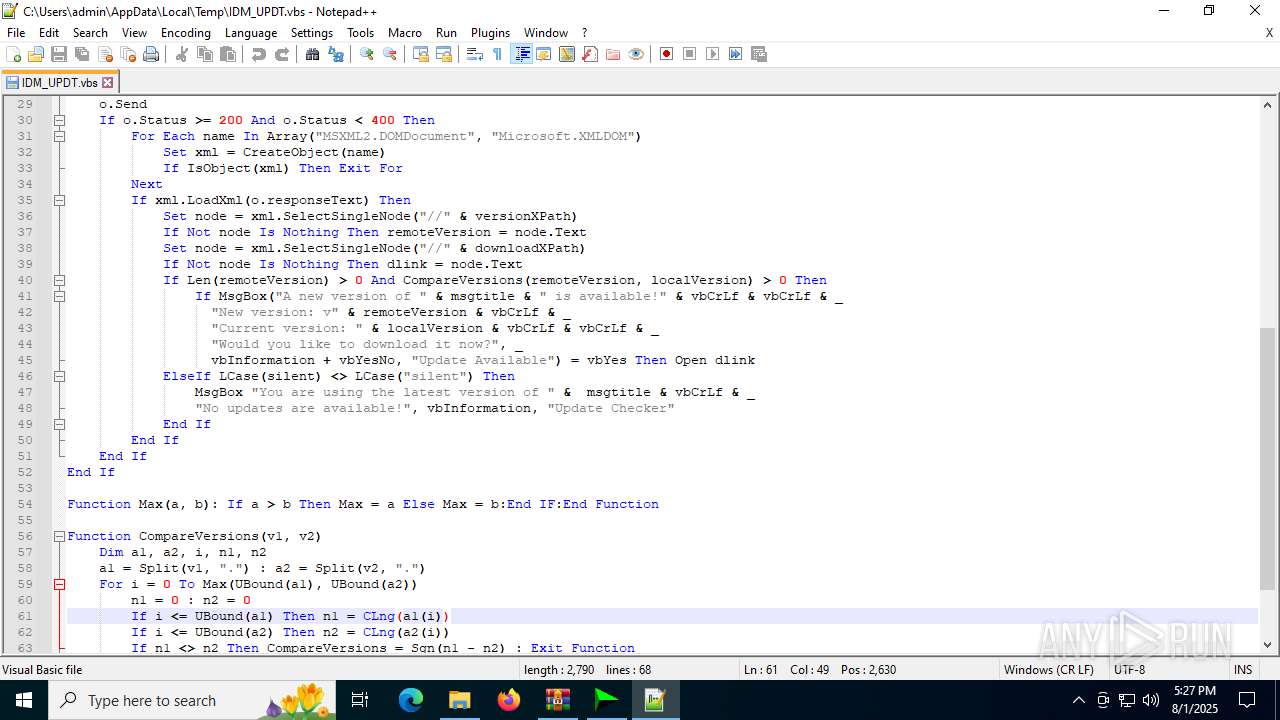
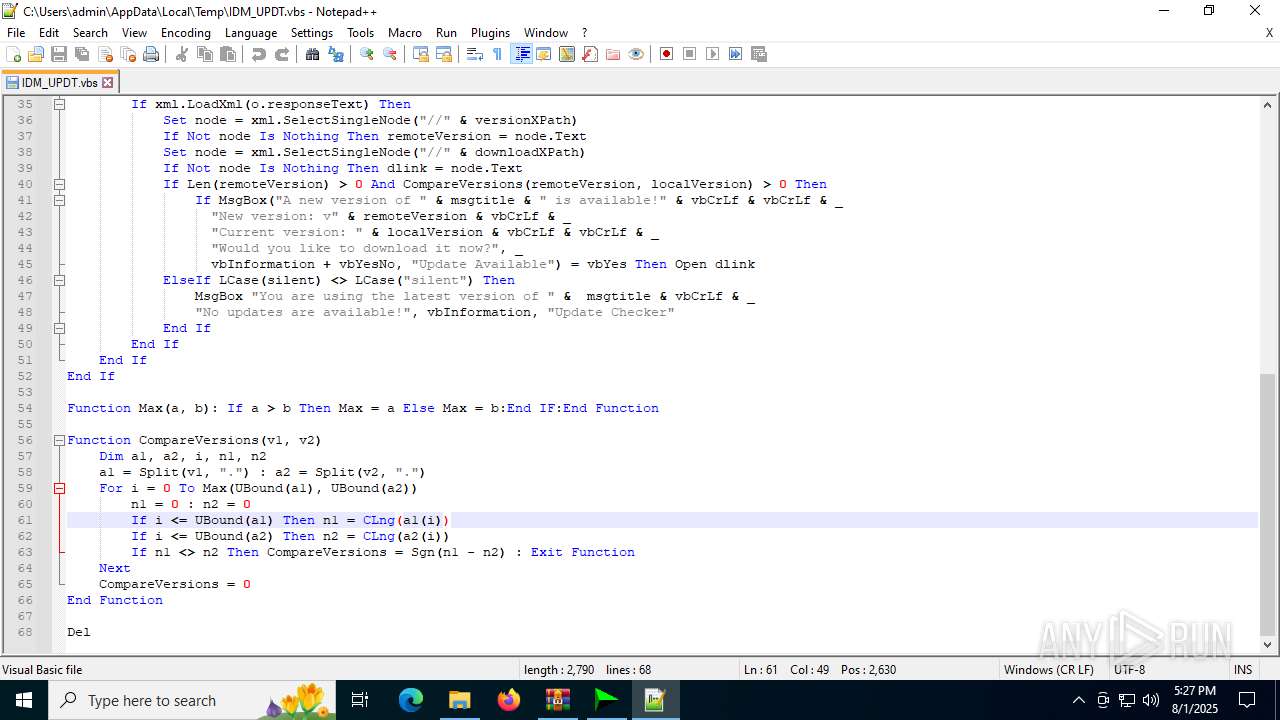
| 6180 | IDM_6.4x_Crack_v20.2.exe | C:\Users\admin\AppData\Local\Temp\CRK_UPDT.vbs | text | |
MD5:B91C1157D6F1E605CC965D092551B307 | SHA256:92FE72CCEB630C7EFF3B2D3BED9C6969F53E5B9DFF1F481888754E59B3C76AB7 | |||
| 6796 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | der | |
MD5:CA8A9BDCA7AD59F5C8B7E1AA63160039 | SHA256:81B7FA53B692B4D26E2E8943F2DDA2F9563CFCB0E11F48679EB2BE4F8C375B90 | |||
| 6180 | IDM_6.4x_Crack_v20.2.exe | C:\Users\admin\AppData\Roaming\WinRAR\rarreg.key | text | |
MD5:CC72935D4E4BD54DB0ED6BF4701FDC9E | SHA256:2ABE74BB821BA46762AFDB23EAC95454EC7155D5379E3CD56385D900C34CB1BF | |||
| 1636 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
| 1636 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:1CC81EAFCDE5D3AD60B08A2A3F7A0915 | SHA256:E190D45E410667802D96406361B382EB693B0188099AC662FAC420948BD3303B | |||
| 6796 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:7A1092A281373C719645E59EC47F1C5C | SHA256:F84E5B72BCF48B55003510FE98DA8C83BF2310A6EBEF7707C761DDD8E7E6B9FC | |||
| 6796 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | der | |
MD5:1FBB37F79B317A9A248E7C4CE4F5BAC5 | SHA256:9BF639C595FE335B6F694EE35990BEFD2123F5E07FD1973FF619E3FC88F5F49F | |||
| 1636 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:633F78751D72E9FE359255C055858159 | SHA256:C0844216186ABB900E88D9E3D688F696D7D3AAEAF236B04BFCD6FC62E2117AA0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
35
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.21:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5644 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6796 | wscript.exe | GET | 200 | 172.217.18.3:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6796 | wscript.exe | GET | 200 | 172.217.18.3:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
6736 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4196 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2032 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2032 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4700 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.21:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5644 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
idm.0dy.ir |
| unknown |
c.pki.goog |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|