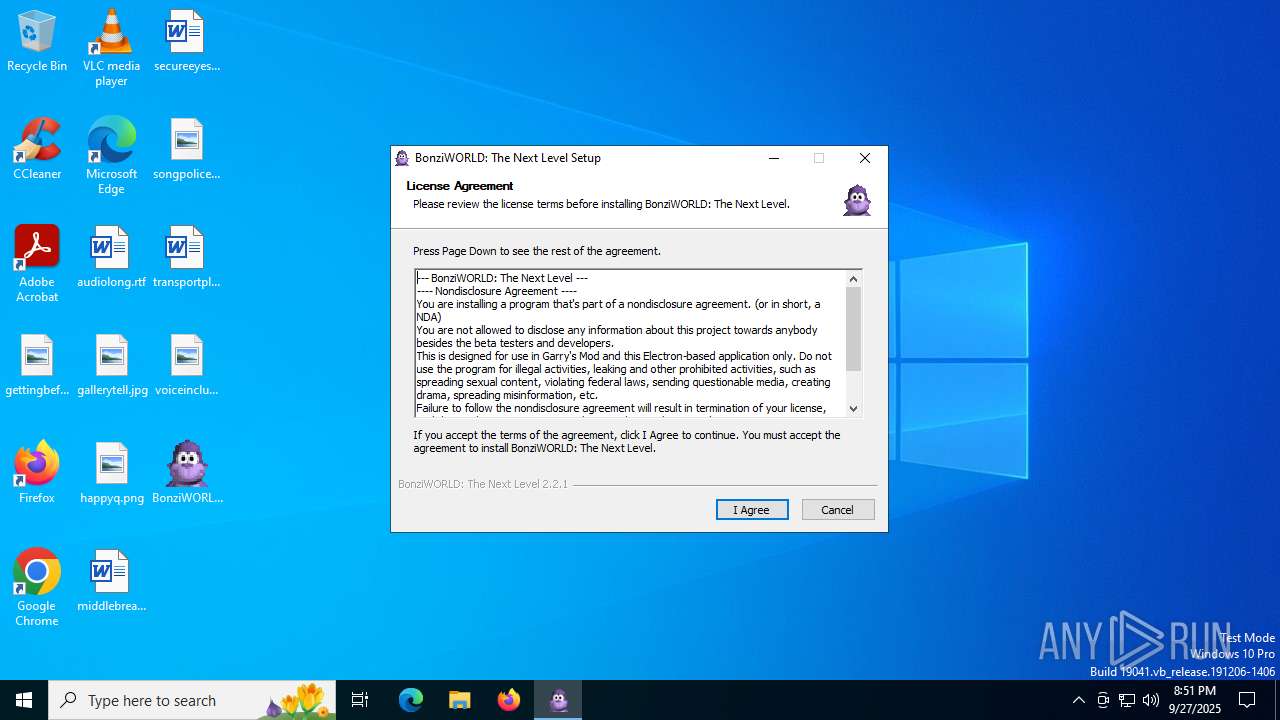
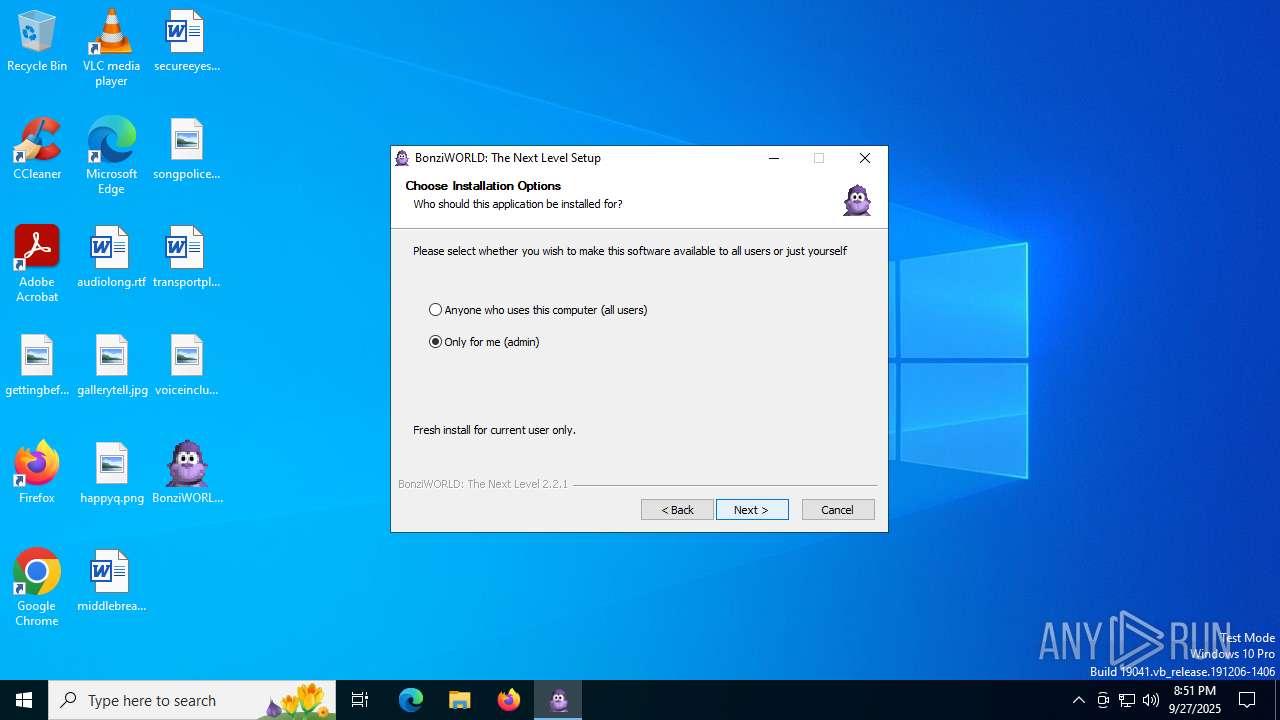
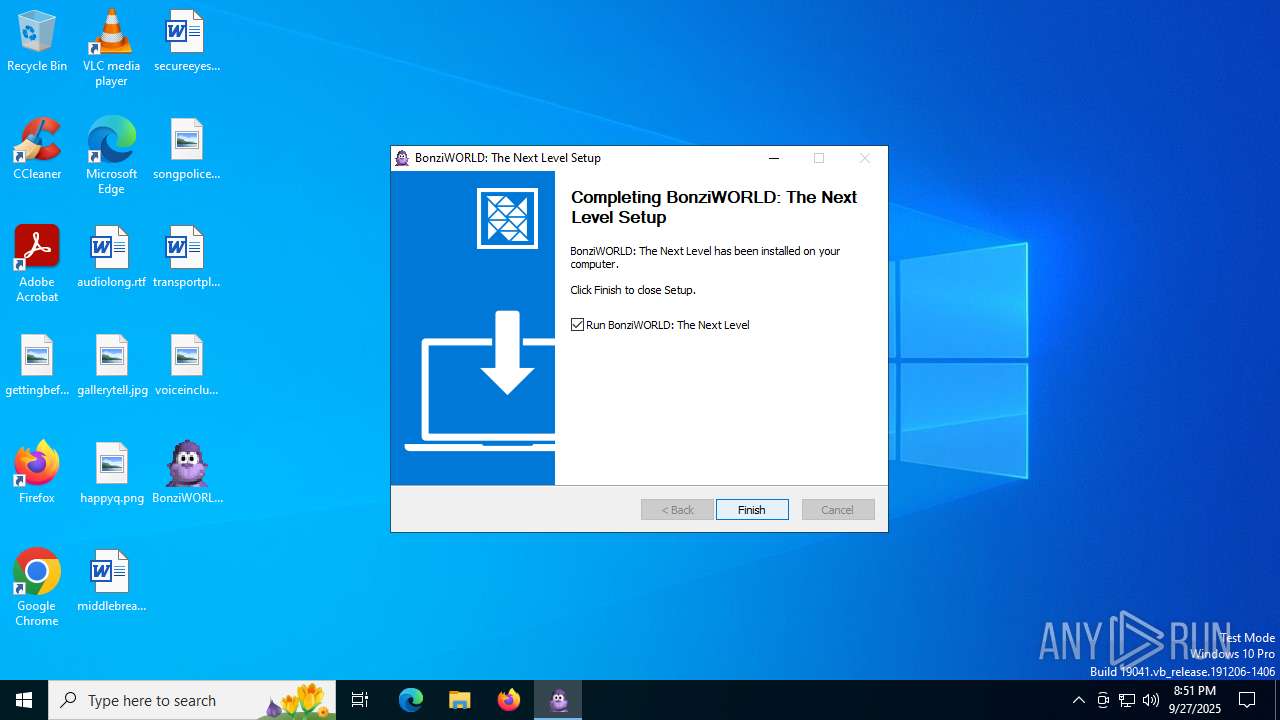
| File name: | BonziWORLDTheNextLevel_2.2.1.exe |
| Full analysis: | https://app.any.run/tasks/bebecb40-74e7-422b-9f9f-0e08b6785666 |
| Verdict: | Malicious activity |
| Analysis date: | September 27, 2025, 20:50:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 46F0B8988E05EF801082519492256896 |
| SHA1: | 11994F18B7AC3F5510E4BD542DD36FE9C4743BF2 |
| SHA256: | DD3038161349DCD7E786D7AEBD76892F04F6DFD59D1D1D5E7BE113DFD4FE7A6D |
| SSDEEP: | 393216:MBI6ueOoW4G4Tpy/7FyRwcH1eUl+j+0MM1d56e4ARGFNsmDfjGLin/WSacCvz1X5:zo+4sjFYzV0MMX4i1mD7Z/WLr+hNXRxo |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
Malware-specific behavior (creating "System.dll" in Temp)
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
The process creates files with name similar to system file names
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
Starts CMD.EXE for commands execution
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
Drops 7-zip archiver for unpacking
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
Process drops legitimate windows executable
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
Get information on the list of running processes
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
- cmd.exe (PID: 4540)
Reads security settings of Internet Explorer
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
There is functionality for taking screenshot (YARA)
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
Creates a software uninstall entry
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
Application launched itself
- BonziWORLD The Next Level.exe (PID: 2356)
INFO
The sample compiled with english language support
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
Reads the computer name
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
- BonziWORLD The Next Level.exe (PID: 2356)
- BonziWORLD The Next Level.exe (PID: 6540)
- BonziWORLD The Next Level.exe (PID: 5416)
Create files in a temporary directory
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
- BonziWORLD The Next Level.exe (PID: 2356)
Creates files or folders in the user directory
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
- BonziWORLD The Next Level.exe (PID: 2356)
- BonziWORLD The Next Level.exe (PID: 6540)
Manual execution by a user
- BonziWORLD The Next Level.exe (PID: 2356)
Checks supported languages
- BonziWORLD The Next Level.exe (PID: 5416)
- BonziWORLD The Next Level.exe (PID: 2356)
- BonziWORLD The Next Level.exe (PID: 6540)
- BonziWORLD The Next Level.exe (PID: 2428)
- BonziWORLDTheNextLevel_2.2.1.exe (PID: 1204)
Reads the software policy settings
- BonziWORLD The Next Level.exe (PID: 6540)
- slui.exe (PID: 1160)
Checks proxy server information
- BonziWORLD The Next Level.exe (PID: 2356)
- slui.exe (PID: 1160)
Node.js compiler has been detected
- BonziWORLD The Next Level.exe (PID: 2356)
Process checks computer location settings
- BonziWORLD The Next Level.exe (PID: 2428)
- BonziWORLD The Next Level.exe (PID: 2356)
Reads the machine GUID from the registry
- BonziWORLD The Next Level.exe (PID: 6540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.2.1.0 |
| ProductVersionNumber: | 2.2.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | thatbankeywordguy@gmail.com |
| FileDescription: | BonziWORLD: The Next Level |
| FileVersion: | 2.2.1 |
| LegalCopyright: | Copyright © 2024 thatbankeywordguy@gmail.com |
| ProductName: | BonziWORLD: The Next Level |
| ProductVersion: | 2.2.1 |
Total processes
137
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1160 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | "C:\Users\admin\Desktop\BonziWORLDTheNextLevel_2.2.1.exe" | C:\Users\admin\Desktop\BonziWORLDTheNextLevel_2.2.1.exe | explorer.exe | ||||||||||||
User: admin Company: thatbankeywordguy@gmail.com Integrity Level: MEDIUM Description: BonziWORLD: The Next Level Exit code: 0 Version: 2.2.1 Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\BonziWORLD The Next Level.exe" | C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\BonziWORLD The Next Level.exe | — | explorer.exe | |||||||||||
User: admin Company: thatbankeywordguy@gmail.com Integrity Level: MEDIUM Description: BonziWORLD: The Next Level Version: 2.2.1 Modules
| |||||||||||||||
| 2428 | "C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\BonziWORLD The Next Level.exe" --type=renderer --no-sandbox --field-trial-handle=1612,15831248924669192774,8135185027408990384,131072 --enable-features=WebComponentsV0Enabled --disable-features=CookiesWithoutSameSiteMustBeSecure,SameSiteByDefaultCookies,SpareRendererForSitePerProcess --lang=en-US --app-path="C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\resources\app" --enable-plugins --no-sandbox --no-zygote --context-isolation --background-color=#fff --enable-spellcheck --enable-websql --disable-electron-site-instance-overrides --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2064 /prefetch:1 | C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\BonziWORLD The Next Level.exe | — | BonziWORLD The Next Level.exe | |||||||||||
User: admin Company: thatbankeywordguy@gmail.com Integrity Level: MEDIUM Description: BonziWORLD: The Next Level Version: 2.2.1 Modules
| |||||||||||||||
| 4540 | "C:\WINDOWS\system32\cmd.exe" /c tasklist /FI "USERNAME eq %USERNAME%" /FI "IMAGENAME eq BonziWORLD The Next Level.exe" /FO csv | "C:\WINDOWS\system32\find.exe" "BonziWORLD The Next Level.exe" | C:\Windows\SysWOW64\cmd.exe | — | BonziWORLDTheNextLevel_2.2.1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5416 | "C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\BonziWORLD The Next Level.exe" --type=gpu-process --field-trial-handle=1612,15831248924669192774,8135185027408990384,131072 --enable-features=WebComponentsV0Enabled --disable-features=CookiesWithoutSameSiteMustBeSecure,SameSiteByDefaultCookies,SpareRendererForSitePerProcess --no-sandbox --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1616 /prefetch:2 | C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\BonziWORLD The Next Level.exe | — | BonziWORLD The Next Level.exe | |||||||||||
User: admin Company: thatbankeywordguy@gmail.com Integrity Level: MEDIUM Description: BonziWORLD: The Next Level Version: 2.2.1 Modules
| |||||||||||||||
| 6540 | "C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\BonziWORLD The Next Level.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1612,15831248924669192774,8135185027408990384,131072 --enable-features=WebComponentsV0Enabled --disable-features=CookiesWithoutSameSiteMustBeSecure,SameSiteByDefaultCookies,SpareRendererForSitePerProcess --lang=en-US --service-sandbox-type=network --no-sandbox --mojo-platform-channel-handle=1668 /prefetch:8 | C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\BonziWORLD The Next Level.exe | BonziWORLD The Next Level.exe | ||||||||||||
User: admin Company: thatbankeywordguy@gmail.com Integrity Level: MEDIUM Description: BonziWORLD: The Next Level Version: 2.2.1 Modules
| |||||||||||||||
| 6768 | tasklist /FI "USERNAME eq admin" /FI "IMAGENAME eq BonziWORLD The Next Level.exe" /FO csv | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6900 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7084 | "C:\WINDOWS\system32\find.exe" "BonziWORLD The Next Level.exe" | C:\Windows\SysWOW64\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 946
Read events
8 915
Write events
13
Delete events
18
Modification events
| (PID) Process: | (1204) BonziWORLDTheNextLevel_2.2.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\fb239a0a-e5a3-5fe6-b21d-5f032827c9b3 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level | |||
| (PID) Process: | (1204) BonziWORLDTheNextLevel_2.2.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\fb239a0a-e5a3-5fe6-b21d-5f032827c9b3 |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (1204) BonziWORLDTheNextLevel_2.2.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\fb239a0a-e5a3-5fe6-b21d-5f032827c9b3 |
| Operation: | write | Name: | ShortcutName |
Value: BonziWORLD The Next Level | |||
| (PID) Process: | (1204) BonziWORLDTheNextLevel_2.2.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\fb239a0a-e5a3-5fe6-b21d-5f032827c9b3 |
| Operation: | write | Name: | DisplayName |
Value: BonziWORLD: The Next Level 2.2.1 | |||
| (PID) Process: | (1204) BonziWORLDTheNextLevel_2.2.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\fb239a0a-e5a3-5fe6-b21d-5f032827c9b3 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\Uninstall BonziWORLD The Next Level.exe" /currentuser | |||
| (PID) Process: | (1204) BonziWORLDTheNextLevel_2.2.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\fb239a0a-e5a3-5fe6-b21d-5f032827c9b3 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\Uninstall BonziWORLD The Next Level.exe" /currentuser /S | |||
| (PID) Process: | (1204) BonziWORLDTheNextLevel_2.2.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\fb239a0a-e5a3-5fe6-b21d-5f032827c9b3 |
| Operation: | write | Name: | DisplayVersion |
Value: 2.2.1 | |||
| (PID) Process: | (1204) BonziWORLDTheNextLevel_2.2.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\fb239a0a-e5a3-5fe6-b21d-5f032827c9b3 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Local\Programs\BonziWORLD The Next Level\BonziWORLD The Next Level.exe,0 | |||
| (PID) Process: | (1204) BonziWORLDTheNextLevel_2.2.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\fb239a0a-e5a3-5fe6-b21d-5f032827c9b3 |
| Operation: | write | Name: | Publisher |
Value: thatbankeywordguy@gmail.com | |||
| (PID) Process: | (1204) BonziWORLDTheNextLevel_2.2.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\fb239a0a-e5a3-5fe6-b21d-5f032827c9b3 |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
Executable files
28
Suspicious files
671
Text files
222
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1204 | BonziWORLDTheNextLevel_2.2.1.exe | C:\Users\admin\AppData\Local\Temp\nsmEAC9.tmp\app-64.7z | — | |
MD5:— | SHA256:— | |||
| 1204 | BonziWORLDTheNextLevel_2.2.1.exe | C:\Users\admin\AppData\Local\Temp\nsmEAC9.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 1204 | BonziWORLDTheNextLevel_2.2.1.exe | C:\Users\admin\AppData\Local\Temp\nsmEAC9.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 1204 | BonziWORLDTheNextLevel_2.2.1.exe | C:\Users\admin\AppData\Local\Temp\nsmEAC9.tmp\UAC.dll | executable | |
MD5:ADB29E6B186DAA765DC750128649B63D | SHA256:2F7F8FC05DC4FD0D5CDA501B47E4433357E887BBFED7292C028D99C73B52DC08 | |||
| 1204 | BonziWORLDTheNextLevel_2.2.1.exe | C:\Users\admin\AppData\Local\Temp\nsmEAC9.tmp\7z-out\locales\ar.pak | binary | |
MD5:985EFAD36A2C07C95FC304319D6CD1F1 | SHA256:1CDEF40BA8343E7F826C2020906915EFAAC5E56F543CD2ED6EBF704882525D8C | |||
| 1204 | BonziWORLDTheNextLevel_2.2.1.exe | C:\Users\admin\AppData\Local\Temp\nsmEAC9.tmp\nsis7z.dll | executable | |
MD5:80E44CE4895304C6A3A831310FBF8CD0 | SHA256:B393F05E8FF919EF071181050E1873C9A776E1A0AE8329AEFFF7007D0CADF592 | |||
| 1204 | BonziWORLDTheNextLevel_2.2.1.exe | C:\Users\admin\AppData\Local\Temp\nsmEAC9.tmp\7z-out\chrome_100_percent.pak | binary | |
MD5:06BAF0AD34E0231BD76651203DBA8326 | SHA256:5AE14147992A92548BCAD76867DD88CDFCDB69D951C8720920CCE6FB135E3189 | |||
| 1204 | BonziWORLDTheNextLevel_2.2.1.exe | C:\Users\admin\AppData\Local\Temp\nsmEAC9.tmp\7z-out\chrome_200_percent.pak | binary | |
MD5:57C27201E7CD33471DA7EC205FE9973C | SHA256:DD8146B2EE289E4D54A4A0F1FD3B2F61B979C6A2BAABA96A406D96C3F4FDB33B | |||
| 1204 | BonziWORLDTheNextLevel_2.2.1.exe | C:\Users\admin\AppData\Local\Temp\nsmEAC9.tmp\7z-out\LICENSE.electron.txt | text | |
MD5:45574510C534A8195F53B30E3810239E | SHA256:C44607A865E7A6DB05552BAA0EF71F9887D96ACD00D123854B44996BC27C0E33 | |||
| 1204 | BonziWORLDTheNextLevel_2.2.1.exe | C:\Users\admin\AppData\Local\Temp\nsmEAC9.tmp\7z-out\locales\am.pak | binary | |
MD5:E1B02B36CE38A843A12867D2700A1BEE | SHA256:E9C78C2410D5C81E0CD5D122462E852143EEA15CA69CD01B85322CEDE1E10806 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
50
DNS requests
19
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.72.36.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.72.36.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 204 b | unknown |
5944 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.72.36.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | unknown |
— | — | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.75:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 204 b | unknown |
— | — | POST | 400 | 40.126.31.69:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.72.36.90:80 | crl.microsoft.com | Akamai International B.V. | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.72.36.90:80 | crl.microsoft.com | Akamai International B.V. | IE | whitelisted |
— | — | 23.72.36.90:80 | crl.microsoft.com | Akamai International B.V. | IE | whitelisted |
1268 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
jlm5pubfmy69rgtvxjcrtvdpqbzhx7ec4w3snaas.onrender.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Host dynamic web apps service (.onrender .com) |
2200 | svchost.exe | Misc activity | ET INFO DNS Query to Online Application Hosting Domain (onrender .com) |
6540 | BonziWORLD The Next Level.exe | Misc activity | ET INFO Observed Online Application Hosting Domain (onrender .com in TLS SNI) |