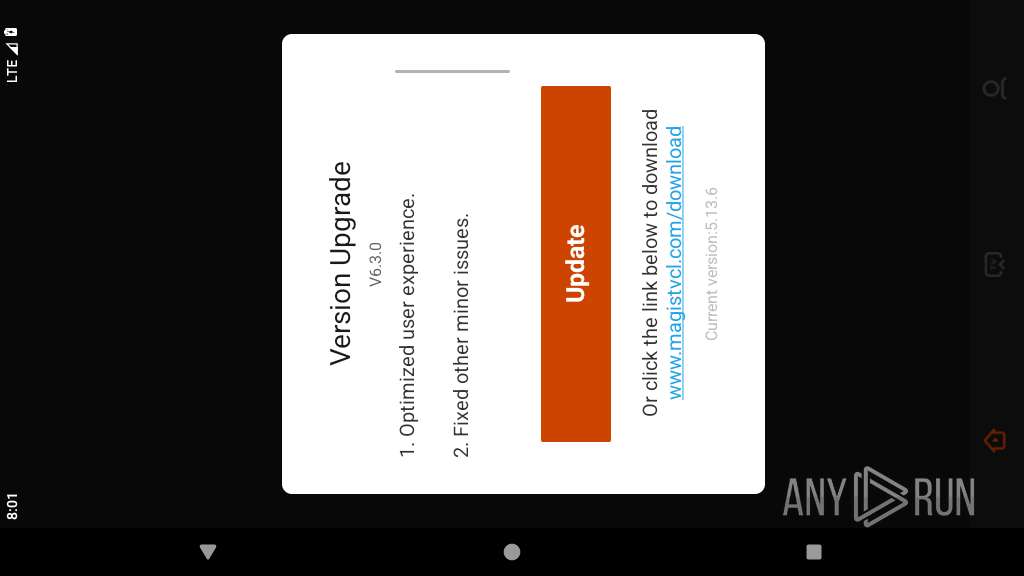
| URL: | https://links.magis-tv.tv/down.mgssm |
| Full analysis: | https://app.any.run/tasks/b5d7a14c-cc14-4547-8420-ab3e54287e03 |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2025, 20:00:50 |
| OS: | Android 14 |
| Tags: | |
| Indicators: | |
| MD5: | D79C81A9709CD8FEEE78443C786E6734 |
| SHA1: | 13AE4A083E49ED8F10FECC9A0918F2D82DD138AB |
| SHA256: | DD2A0FED0C632E5EEC953FF317D0B5820CE5404D0C30442AE610C5E1FA311721 |
| SSDEEP: | 3:N8MLPP1LRN48Zn:2MjN4Kn |
MALICIOUS
Executes system commands or scripts
- app_process64 (PID: 2545)
SUSPICIOUS
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2545)
Detects Xposed framework for modifications
- app_process64 (PID: 2545)
Uses encryption API functions
- app_process64 (PID: 2545)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2545)
Establishing a connection
- app_process64 (PID: 2545)
Accesses system-level resources
- app_process64 (PID: 2545)
Retrieves a list of running application processes
- app_process64 (PID: 2545)
Returns the name of the current network operator
- app_process64 (PID: 2545)
Detects when screen powers off
- app_process64 (PID: 2545)
Starts a service
- app_process64 (PID: 2545)
Accesses external device storage files
- app_process64 (PID: 2545)
Launches a new activity
- app_process64 (PID: 2545)
Accesses memory information
- app_process64 (PID: 2545)
INFO
Dynamically registers broadcast event listeners
- app_process64 (PID: 2545)
Dynamically loads a class in Java
- app_process64 (PID: 2545)
Loads a native library into the application
- app_process64 (PID: 2545)
Verifies whether the device is connected to the internet
- app_process64 (PID: 2545)
Retrieves the value of a secure system setting
- app_process64 (PID: 2545)
Listens for connection changes
- app_process64 (PID: 2545)
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2545)
Stores data using SQLite database
- app_process64 (PID: 2545)
Returns elapsed time since boot
- app_process64 (PID: 2545)
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2545)
Attempting to connect via WebSocket
- app_process64 (PID: 2545)
Detects device power status
- app_process64 (PID: 2545)
Gets the display metrics associated with the device's screen
- app_process64 (PID: 2545)
Gets file name without full path
- app_process64 (PID: 2545)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
151
Monitored processes
28
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2213 | <pre-initialized> | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2258 | org.chromium.chrome_zygote | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2274 | org.chromium.chrome_zygote | /system/bin/app_process64 | — | app_process64 |
User: u0_a73 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2310 | org.chromium.chrome:privileged_process0 | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2331 | <pre-initialized> | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2400 | org.chromium.chrome_zygote | /system/bin/app_process64 | — | app_process64 |
User: u0_a73 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2529 | /apex/com.android.art/bin/artd | /apex/com.android.art/bin/artd | — | init |
User: artd Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2532 | /apex/com.android.art/bin/dex2oat32 --zip-fd=6 --zip-location=/data/app/~~lCClePvHZ8nrUEuS2-lZRA==/com.msandroid.mobile-QNr8SIqyNL9042AR2635Mg==/base.apk --oat-fd=7 --oat-location=/data/app/~~lCClePvHZ8nrUEuS2-lZRA==/com.msandroid.mobile-QNr8SIqyNL9042AR2635Mg==/oat/arm64/base.odex --output-vdex-fd=8 --swap-fd=9 --class-loader-context=PCL[] --classpath-dir=/data/app/~~lCClePvHZ8nrUEuS2-lZRA==/com.msandroid.mobile-QNr8SIqyNL9042AR2635Mg== --instruction-set=arm64 --instruction-set-features=default --instruction-set-variant=cortex-a53 --compiler-filter=verify --compilation-reason=install --compact-dex-level=none --max-image-block-size=524288 --resolve-startup-const-strings=true --generate-mini-debug-info --runtime-arg -Xtarget-sdk-version:33 --runtime-arg -Xhidden-api-policy:enabled --runtime-arg -Xms64m --runtime-arg -Xmx512m --comments=app-version-name:5.13.6,app-version-code:51306,art-version:340090000 | /apex/com.android.art/bin/dex2oat32 | — | artd |
User: artd Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2545 | com.msandroid.mobile | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2597 | getprop debug.dns.enable | /system/bin/toolbox | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 15 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
78
Text files
172
Unknown types
75
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2545 | app_process64 | /data/data/com.msandroid.mobile/files/PersistedInstallation1588987864910930046tmp | binary | |
MD5:— | SHA256:— | |||
| 2545 | app_process64 | /data/data/com.msandroid.mobile/files/PersistedInstallation.W0RFRkFVTFRd+MToxODc2NzUyNDY3NTphbmRyb2lkOmM3NGYwM2Y4YTg2ODE1YzUzNWY1ZjY.json | binary | |
MD5:— | SHA256:— | |||
| 2545 | app_process64 | /data/data/com.msandroid.mobile/shared_prefs/FirebaseHeartBeatW0RFRkFVTFRd+MToxODc2NzUyNDY3NTphbmRyb2lkOmM3NGYwM2Y4YTg2ODE1YzUzNWY1ZjY.xml | xml | |
MD5:— | SHA256:— | |||
| 2545 | app_process64 | /data/data/com.msandroid.mobile/shared_prefs/com.google.firebase.crashlytics.xml | xml | |
MD5:— | SHA256:— | |||
| 2545 | app_process64 | /data/data/com.msandroid.mobile/shared_prefs/com.google.firebase.messaging.xml | xml | |
MD5:— | SHA256:— | |||
| 2545 | app_process64 | /data/data/com.msandroid.mobile/no_backup/androidx.work.workdb-journal | binary | |
MD5:— | SHA256:— | |||
| 2545 | app_process64 | /data/data/com.msandroid.mobile/no_backup/androidx.work.workdb-wal | binary | |
MD5:— | SHA256:— | |||
| 2597 | toolbox | /data/data/com.msandroid.mobile/no_backup/androidx.work.workdb-wal | binary | |
MD5:— | SHA256:— | |||
| 2597 | toolbox | /data/data/com.msandroid.mobile/databases/com.google.android.datatransport.events | sqlite | |
MD5:— | SHA256:— | |||
| 2597 | toolbox | /data/data/com.msandroid.mobile/no_backup/androidx.work.workdb-shm | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
54
DNS requests
54
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 142.250.186.67:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
2213 | app_process64 | GET | 200 | 142.250.186.142:80 | http://clients2.google.com/time/1/current?cup2key=9:YUZQXvFpfOG5DDC83CdnHOY9LkLj4M-PC6iheQrArE8&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2545 | app_process64 | POST | 200 | 172.67.194.18:80 | http://skc2r.plracsimf.com/api/adserver/v2/get_content | unknown | — | — | unknown |
2545 | app_process64 | GET | 200 | 104.21.96.1:80 | http://jktgr.ludgwoxhe.com/MarketServer/update?action=checkUpdate&packagenamesAndVersioncodes=com.msandroid.mobile%2C51306&language=en&sn=vDedjnhT2IA%3D&userId=unknown | unknown | — | — | unknown |
2545 | app_process64 | GET | 200 | 188.114.97.3:80 | http://pwel.sdxpkgyaq.com/media/adsys/02b070c2-a37b-40ca-966e-c2a1fceead4c.png | unknown | — | — | unknown |
2545 | app_process64 | GET | 200 | 188.114.97.3:80 | http://pwel.sdxpkgyaq.com/media/adsys/53e19d30-bcec-4e4a-ae65-1004a30bb771.gif | unknown | — | — | unknown |
2545 | app_process64 | GET | 200 | 188.114.97.3:80 | http://pwel.sdxpkgyaq.com/media/adsys/2ca52e36-0e53-4bf8-84dc-d5a1cb62c963.jpg | unknown | — | — | unknown |
2545 | app_process64 | GET | 200 | 188.114.97.3:80 | http://pwel.sdxpkgyaq.com/media/adsys/cee8fe1d-1f20-45ab-a089-46f49e333d9e.jpg | unknown | — | — | unknown |
2545 | app_process64 | GET | 200 | 188.114.97.3:80 | http://pwel.sdxpkgyaq.com/media/adsys/c725ebdd-c681-4f8a-9ed7-8a7262d50f34.jpg | unknown | — | — | unknown |
2545 | app_process64 | GET | 200 | 188.114.97.3:80 | http://pwel.sdxpkgyaq.com/media/adsys/5546b26c-0405-46bb-adde-ef02d8937311.jpg | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
446 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 216.239.35.12:123 | time.android.com | — | — | whitelisted |
— | — | 216.58.206.36:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.67:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 74.125.133.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
2213 | app_process64 | 142.250.186.142:80 | clients2.google.com | GOOGLE | US | whitelisted |
2213 | app_process64 | 104.21.48.1:443 | links.magis-tv.tv | — | — | unknown |
2213 | app_process64 | 216.58.206.36:443 | www.google.com | — | — | whitelisted |
2213 | app_process64 | 74.125.71.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2213 | app_process64 | 104.21.5.210:443 | app.magistvcl.com | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
links.magis-tv.tv |
| unknown |
accounts.google.com |
| whitelisted |
app.magistvcl.com |
| unknown |
androidchromeprotect.pa.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
2213 | app_process64 | Generic Protocol Command Decode | SURICATA Applayer Wrong direction first Data |
2213 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2213 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2213 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2213 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2213 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2213 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2213 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2213 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |