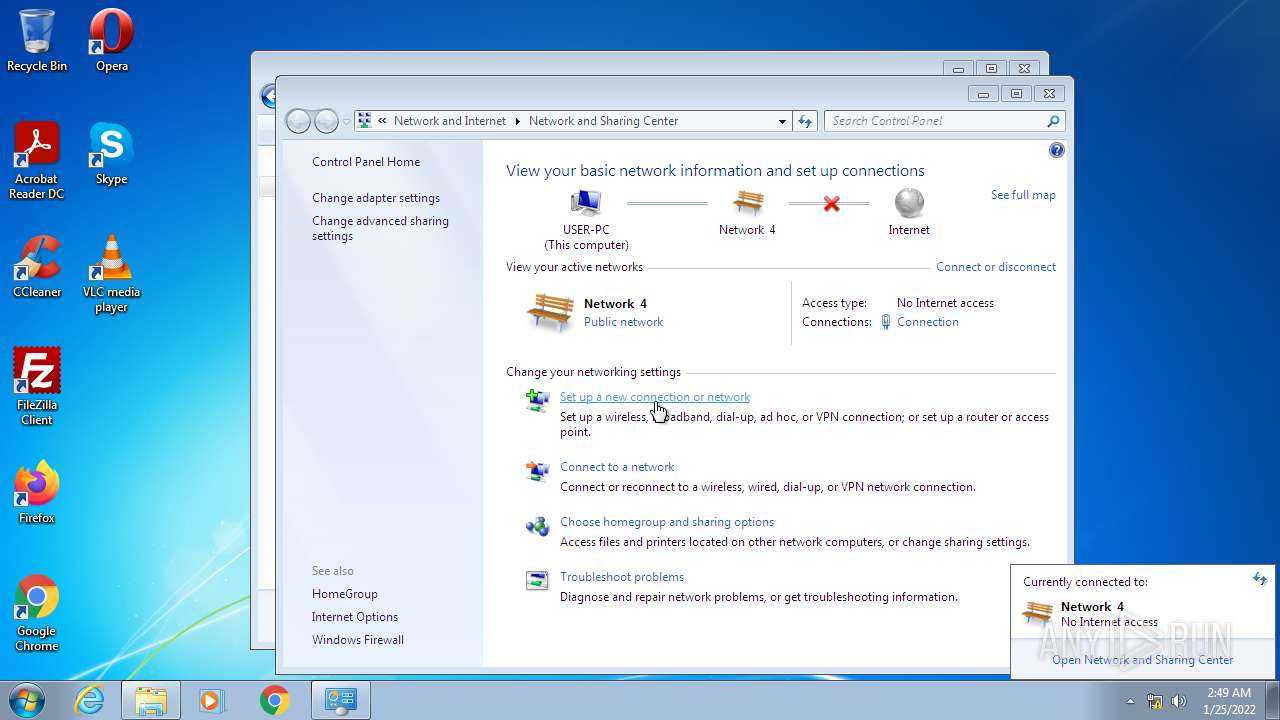
| File name: | 7Clicker (1).jar |
| Full analysis: | https://app.any.run/tasks/62b0d2ae-1b1b-4092-bc94-490d7013c565 |
| Verdict: | Malicious activity |
| Analysis date: | January 25, 2022, 02:46:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | 8FD172F85EE2111BB2C796F255DFCA77 |
| SHA1: | E9DBBE9A7AC5D9829F62597469F4053B01721DCE |
| SHA256: | DD21FB853285D3CE6738A32E82B1727DED2CC569883F0E85A407EF4E1C15C40B |
| SSDEEP: | 6144:7nhVBkJYJjEJ7WtPbnxG1Rh/dCwfmb/Oy+z0ph7u0c+nQXLWnFYmDG7i5m6JeCh1:7hpsEPGl0SIkz2hS0vnQticaeCh1 |
MALICIOUS
Loads dropped or rewritten executable
- javaw.exe (PID: 2256)
Changes internet zones settings
- ie4uinit.exe (PID: 3976)
Loads the Task Scheduler COM API
- rundll32.exe (PID: 4016)
Changes the autorun value in the registry
- unregmp2.exe (PID: 392)
- reg.exe (PID: 3948)
- sidebar.exe (PID: 3892)
Changes the Startup folder
- regsvr32.exe (PID: 2512)
Writes to a start menu file
- regsvr32.exe (PID: 2512)
Steals credentials from Web Browsers
- pingsender.exe (PID: 2644)
- pingsender.exe (PID: 3248)
- pingsender.exe (PID: 3192)
Actions looks like stealing of personal data
- pingsender.exe (PID: 2644)
- pingsender.exe (PID: 3248)
- pingsender.exe (PID: 3192)
SUSPICIOUS
Creates files in the program directory
- javaw.exe (PID: 2256)
- ie4uinit.exe (PID: 3976)
- chrmstp.exe (PID: 2684)
Checks supported languages
- javaw.exe (PID: 2256)
- chrmstp.exe (PID: 2684)
- chrmstp.exe (PID: 3340)
- imkrmig.exe (PID: 3280)
- IMEKLMG.EXE (PID: 3692)
- IMEKLMG.EXE (PID: 3220)
- jusched.exe (PID: 3056)
- pingsender.exe (PID: 3248)
- pingsender.exe (PID: 2644)
- pingsender.exe (PID: 3192)
- Skype.exe (PID: 3580)
- Skype.exe (PID: 2560)
- Skype.exe (PID: 3952)
- Skype.exe (PID: 1740)
- Skype.exe (PID: 3340)
- Skype.exe (PID: 1096)
- Skype.exe (PID: 1888)
- sidebar.exe (PID: 3892)
Uses ICACLS.EXE to modify access control list
- javaw.exe (PID: 2256)
Executable content was dropped or overwritten
- javaw.exe (PID: 2256)
Drops a file that was compiled in debug mode
- javaw.exe (PID: 2256)
Reads the computer name
- javaw.exe (PID: 2256)
- chrmstp.exe (PID: 2684)
- IMEKLMG.EXE (PID: 3220)
- IMEKLMG.EXE (PID: 3692)
- pingsender.exe (PID: 2644)
- pingsender.exe (PID: 3248)
- pingsender.exe (PID: 3192)
- Skype.exe (PID: 3580)
- Skype.exe (PID: 3952)
- Skype.exe (PID: 1740)
- Skype.exe (PID: 2560)
- Skype.exe (PID: 3340)
- Skype.exe (PID: 1888)
- Skype.exe (PID: 1096)
- sidebar.exe (PID: 3892)
Executed via Task Scheduler
- sipnotify.exe (PID: 2300)
Executed as Windows Service
- taskhost.exe (PID: 2224)
- EOSNotify.exe (PID: 3220)
Application launched itself
- ie4uinit.exe (PID: 3976)
- rundll32.exe (PID: 4016)
- chrmstp.exe (PID: 2684)
- Skype.exe (PID: 3580)
- Skype.exe (PID: 3952)
Reads internet explorer settings
- ie4uinit.exe (PID: 3976)
- sidebar.exe (PID: 3892)
Reads Microsoft Outlook installation path
- ie4uinit.exe (PID: 3976)
- sidebar.exe (PID: 3892)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 3976)
- rundll32.exe (PID: 4016)
Writes to a desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 3976)
- unregmp2.exe (PID: 392)
- regsvr32.exe (PID: 2512)
Reads Environment values
- unregmp2.exe (PID: 392)
Changes default file association
- unregmp2.exe (PID: 392)
- Skype.exe (PID: 3580)
Check for Java to be installed
- jusched.exe (PID: 3056)
Creates files in the Windows directory
- chrmstp.exe (PID: 3340)
Reads the date of Windows installation
- chrmstp.exe (PID: 2684)
Loads DLL from Mozilla Firefox
- pingsender.exe (PID: 2644)
- pingsender.exe (PID: 3248)
- pingsender.exe (PID: 3192)
Reads CPU info
- Skype.exe (PID: 3580)
Uses REG.EXE to modify Windows registry
- Skype.exe (PID: 3580)
INFO
Checks supported languages
- icacls.exe (PID: 1936)
- chrome.exe (PID: 2368)
- chrome.exe (PID: 3228)
- chrome.exe (PID: 2812)
- chrome.exe (PID: 2236)
- chrome.exe (PID: 4060)
- chrome.exe (PID: 3424)
- chrome.exe (PID: 1088)
- chrome.exe (PID: 1200)
- chrome.exe (PID: 3128)
- chrome.exe (PID: 1248)
- chrome.exe (PID: 3064)
- chrome.exe (PID: 4036)
- chrome.exe (PID: 3424)
- chrome.exe (PID: 3916)
- chrome.exe (PID: 2816)
- chrome.exe (PID: 684)
- firefox.exe (PID: 1044)
- firefox.exe (PID: 2852)
- firefox.exe (PID: 2520)
- firefox.exe (PID: 3476)
- firefox.exe (PID: 3792)
- firefox.exe (PID: 1284)
- firefox.exe (PID: 188)
- taskhost.exe (PID: 2224)
- sipnotify.exe (PID: 2300)
- ie4uinit.exe (PID: 3976)
- ie4uinit.exe (PID: 3732)
- rundll32.exe (PID: 3648)
- rundll32.exe (PID: 4016)
- RunDll32.exe (PID: 2368)
- RunDll32.exe (PID: 3556)
- ie4uinit.exe (PID: 3576)
- unregmp2.exe (PID: 392)
- regsvr32.exe (PID: 2512)
- firefox.exe (PID: 2232)
- firefox.exe (PID: 2300)
- firefox.exe (PID: 2320)
- firefox.exe (PID: 1888)
- firefox.exe (PID: 3780)
- ie4uinit.exe (PID: 520)
- explorer.exe (PID: 3128)
- reg.exe (PID: 3948)
- reg.exe (PID: 1472)
- firefox.exe (PID: 4008)
- firefox.exe (PID: 4036)
- EOSNotify.exe (PID: 3220)
- firefox.exe (PID: 628)
- firefox.exe (PID: 3008)
- firefox.exe (PID: 1992)
- firefox.exe (PID: 2504)
- firefox.exe (PID: 1828)
- firefox.exe (PID: 4060)
- firefox.exe (PID: 1272)
- firefox.exe (PID: 3380)
Reads the computer name
- icacls.exe (PID: 1936)
- chrome.exe (PID: 3228)
- chrome.exe (PID: 2368)
- chrome.exe (PID: 2236)
- chrome.exe (PID: 1200)
- chrome.exe (PID: 3128)
- firefox.exe (PID: 2852)
- firefox.exe (PID: 2520)
- firefox.exe (PID: 1284)
- firefox.exe (PID: 3792)
- taskhost.exe (PID: 2224)
- firefox.exe (PID: 3476)
- firefox.exe (PID: 188)
- sipnotify.exe (PID: 2300)
- ie4uinit.exe (PID: 3976)
- rundll32.exe (PID: 3648)
- rundll32.exe (PID: 4016)
- RunDll32.exe (PID: 2368)
- RunDll32.exe (PID: 3556)
- unregmp2.exe (PID: 392)
- regsvr32.exe (PID: 2512)
- ie4uinit.exe (PID: 3732)
- firefox.exe (PID: 2320)
- firefox.exe (PID: 2300)
- firefox.exe (PID: 3380)
- firefox.exe (PID: 628)
- EOSNotify.exe (PID: 3220)
- firefox.exe (PID: 4036)
- firefox.exe (PID: 1888)
- firefox.exe (PID: 3780)
- explorer.exe (PID: 3128)
- firefox.exe (PID: 1992)
- firefox.exe (PID: 1272)
- firefox.exe (PID: 2504)
- firefox.exe (PID: 1828)
- firefox.exe (PID: 4060)
- firefox.exe (PID: 3008)
Manual execution by user
- chrome.exe (PID: 3228)
- firefox.exe (PID: 1044)
- ie4uinit.exe (PID: 3976)
- ie4uinit.exe (PID: 3576)
- unregmp2.exe (PID: 392)
- ie4uinit.exe (PID: 520)
- regsvr32.exe (PID: 2512)
- chrmstp.exe (PID: 2684)
- IMEKLMG.EXE (PID: 3692)
- IMEKLMG.EXE (PID: 3220)
- jusched.exe (PID: 3056)
- firefox.exe (PID: 2232)
- explorer.exe (PID: 3128)
- Skype.exe (PID: 3580)
- sidebar.exe (PID: 3892)
- firefox.exe (PID: 4008)
Application launched itself
- chrome.exe (PID: 3228)
- firefox.exe (PID: 1044)
- firefox.exe (PID: 2852)
- firefox.exe (PID: 2232)
- firefox.exe (PID: 2300)
- firefox.exe (PID: 4008)
- firefox.exe (PID: 3008)
Reads the hosts file
- chrome.exe (PID: 3228)
- chrome.exe (PID: 2236)
- Skype.exe (PID: 3580)
Reads settings of System Certificates
- chrome.exe (PID: 2236)
- pingsender.exe (PID: 3248)
- pingsender.exe (PID: 2644)
- pingsender.exe (PID: 3192)
- Skype.exe (PID: 3580)
Reads CPU info
- firefox.exe (PID: 2852)
- firefox.exe (PID: 2300)
- firefox.exe (PID: 3008)
Creates files in the user directory
- firefox.exe (PID: 2852)
Reads the date of Windows installation
- firefox.exe (PID: 2852)
- firefox.exe (PID: 2300)
Creates files in the program directory
- firefox.exe (PID: 2852)
- firefox.exe (PID: 2300)
- firefox.exe (PID: 3008)
Checks Windows Trust Settings
- pingsender.exe (PID: 3248)
- pingsender.exe (PID: 2644)
- pingsender.exe (PID: 3192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | META-INF/MANIFEST.MF |
|---|---|
| ZipUncompressedSize: | 218 |
| ZipCompressedSize: | 156 |
| ZipCRC: | 0xa651ba9f |
| ZipModifyDate: | 2016:02:28 13:45:26 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0808 |
| ZipRequiredVersion: | 20 |
Total processes
131
Monitored processes
73
Malicious processes
4
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2852.27.2065262144\482224717" -childID 4 -isForBrowser -prefsHandle 3908 -prefMapHandle 3904 -prefsLen 7378 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2852 "\\.\pipe\gecko-crash-server-pipe.2852" 3920 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 392 | "C:\Windows\System32\unregmp2.exe" /FirstLogon /Shortcuts /RegBrowsers /ResetMUI | C:\Windows\System32\unregmp2.exe | Explorer.EXE | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Media Player Setup Utility Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 520 | "C:\Windows\System32\ie4uinit.exe" -DisableSSL3 | C:\Windows\System32\ie4uinit.exe | — | Explorer.EXE | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 628 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2300.13.2103248148\783215661" -childID 2 -isForBrowser -prefsHandle 4812 -prefMapHandle 4808 -prefsLen 1796 -prefMapSize 228868 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2300 "\\.\pipe\gecko-crash-server-pipe.2300" 4824 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: Administrator Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,222303760808231005,13077140600850888874,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2136 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,222303760808231005,13077140600850888874,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1920 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --disable-databases --service-pipe-token=72ABC8AD99EAD000246F6EA021E79F0C --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\WebViewPreload.js" --guest-instance-id=1 --enable-blink-features --disable-blink-features --context-id=1 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=72ABC8AD99EAD000246F6EA021E79F0C --renderer-client-id=8 --mojo-platform-channel-handle=2696 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: Administrator Company: Skype Technologies S.A. Integrity Level: HIGH Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 1200 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1052,222303760808231005,13077140600850888874,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2800 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1248 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,222303760808231005,13077140600850888874,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2544 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
54 252
Read events
52 767
Write events
1 479
Delete events
6
Modification events
| (PID) Process: | (2256) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
| (PID) Process: | (3228) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3228) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3228) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3228) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3228) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3228) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3228) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3228) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3228) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
4
Suspicious files
273
Text files
236
Unknown types
103
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61EF649A-C9C.pma | — | |
MD5:— | SHA256:— | |||
| 2256 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:— | SHA256:— | |||
| 2256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+~JF8064025612974338247.tmp | otf | |
MD5:51B4A619FAB5E1A38643657191A85AA5 | SHA256:3329FFAF627F1AA8862880401FF964F0F59998B802B403C12593FDB865176831 | |||
| 2256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\jar_cache303597327243616237.tmp | java | |
MD5:105B2B56BF43F91BAD6715211A407F6E | SHA256:D5F84AE5BC8B335C5A85D47EDC839425FF183C61F7A75AF60B39D762B807BE32 | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF141200.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
| 2256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JNativeHook-FCBC1DC5993F3B7C153159E29CD4364927BC9517.dll | executable | |
MD5:B4CE035F926531D6B4DFA8477C6477E4 | SHA256:F6FFEAD3B5F3DB5A7A00D1FEF874C3D3ED7ECF095DA2D981EBD691FDFA685716 | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:7721CDA9F5B73CE8A135471EB53B4E0E | SHA256:DD730C576766A46FFC84E682123248ECE1FF1887EC0ACAB22A5CE93A450F4500 | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 2812 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF1411f0.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
267
TCP/UDP connections
179
DNS requests
157
Threats
295
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
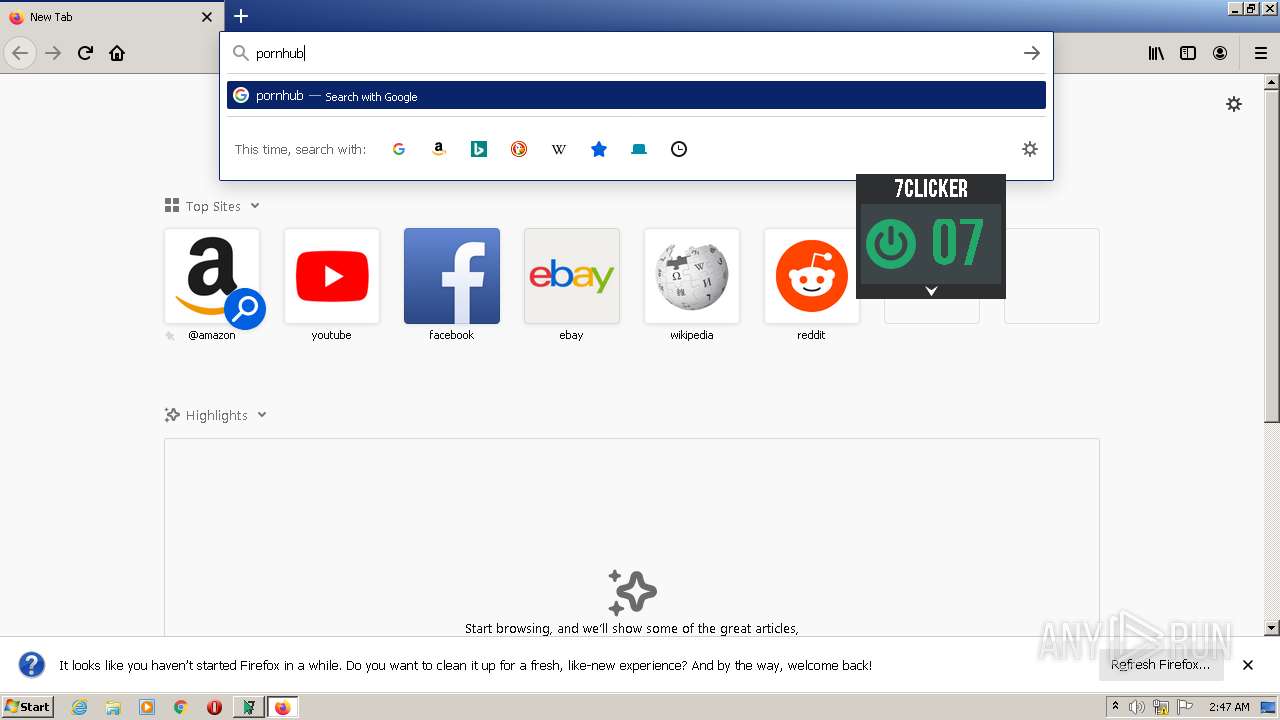
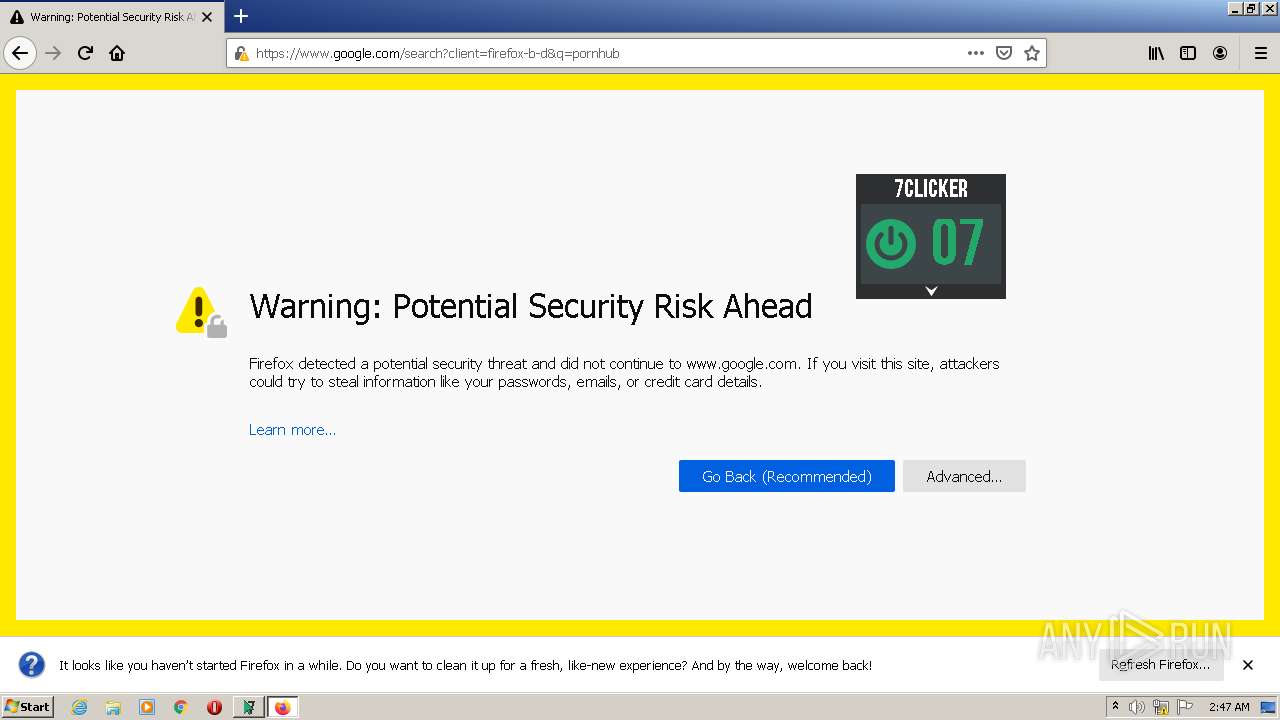
2236 | chrome.exe | GET | 404 | 66.254.114.41:80 | http://pornhub.com/ | US | xml | 341 b | whitelisted |
2852 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2236 | chrome.exe | GET | 404 | 66.254.114.41:80 | http://pornhub.com/favicon.ico | US | xml | 341 b | whitelisted |
2852 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2236 | chrome.exe | GET | 404 | 50.87.195.134:80 | http://krunker.com/ | US | xml | 341 b | malicious |
2852 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2852 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2236 | chrome.exe | GET | 404 | 142.250.179.163:80 | http://www.gstatic.com/generate_204 | US | xml | 341 b | whitelisted |
2852 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2852 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2236 | chrome.exe | 142.250.186.77:443 | accounts.google.com | Google Inc. | US | suspicious |
2236 | chrome.exe | 142.250.186.68:443 | www.google.com | Google Inc. | US | whitelisted |
2236 | chrome.exe | 142.250.179.142:443 | clients2.google.com | Google Inc. | US | whitelisted |
— | — | 142.250.186.68:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 142.251.39.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2236 | chrome.exe | 50.87.195.134:80 | krunker.com | Unified Layer | US | malicious |
2236 | chrome.exe | 142.250.186.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2236 | chrome.exe | 142.250.179.163:80 | www.gstatic.com | Google Inc. | US | whitelisted |
2236 | chrome.exe | 66.254.114.41:80 | pornhub.com | Reflected Networks, Inc. | US | malicious |
2236 | chrome.exe | 142.250.185.138:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
accounts.google.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
krunker.com |
| unknown |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
support.google.com |
| whitelisted |
pornhub.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
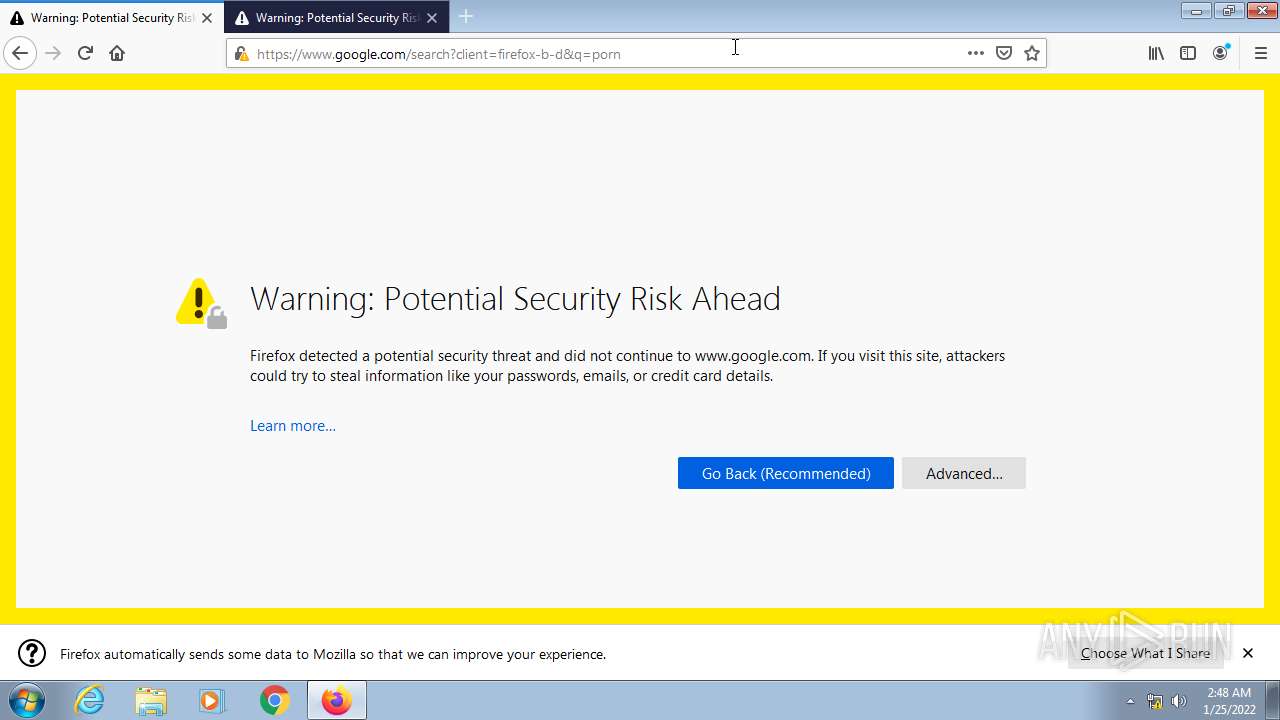
2852 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2852 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2852 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2852 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2852 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2852 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2852 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2852 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2852 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2852 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
39 ETPRO signatures available at the full report